thank you all as always 02 Cryptography Kai
































- Slides: 81

thank you all as always

02 Cryptography Kai Bu kaibu@zju. edu. cn http: //list. zju. edu. cn/kaibu/netsec 2020

Cryptography as you were told many times

Cryptography why?

Cryptography why: prevent third parties from reading private messages

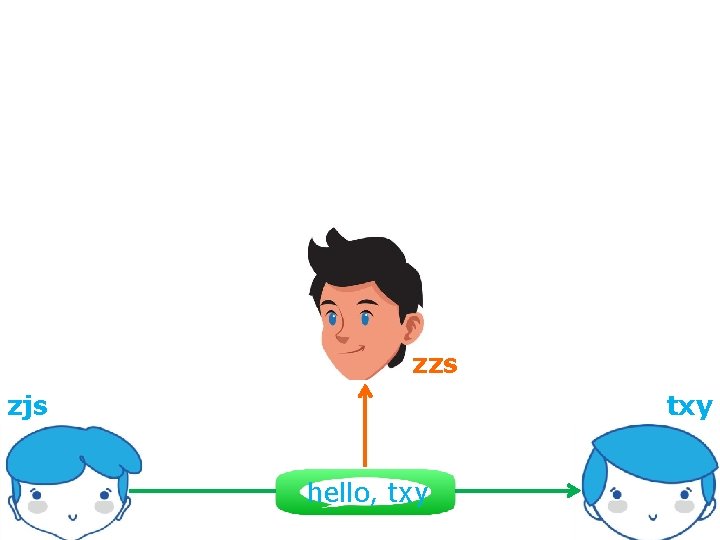
Cryptography how?

Cryptography how: encrypt messages before transmission; decrypt messages upon receipt; hello, txy asdfghjkl enc dec

Cryptography what?

Cryptography what: confidentiality integrity authentication non-repudiation

Cryptography what: confidentiality -- secrecy integrity -- accuracy authentication -- ascription non-repudiation -- liability

Cryptography which?

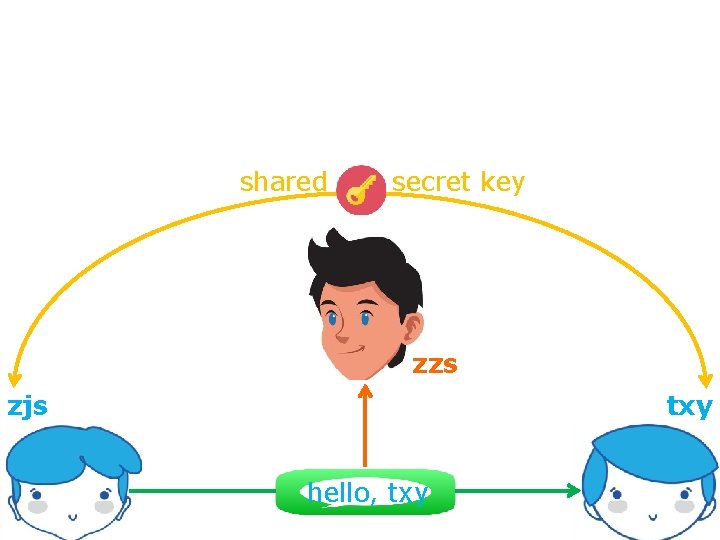
Cryptography hush, let’s start with a little secret

too many concepts ahead

zzs zjs txy hello, txy

shared secret key zzs zjs txy hello, txy

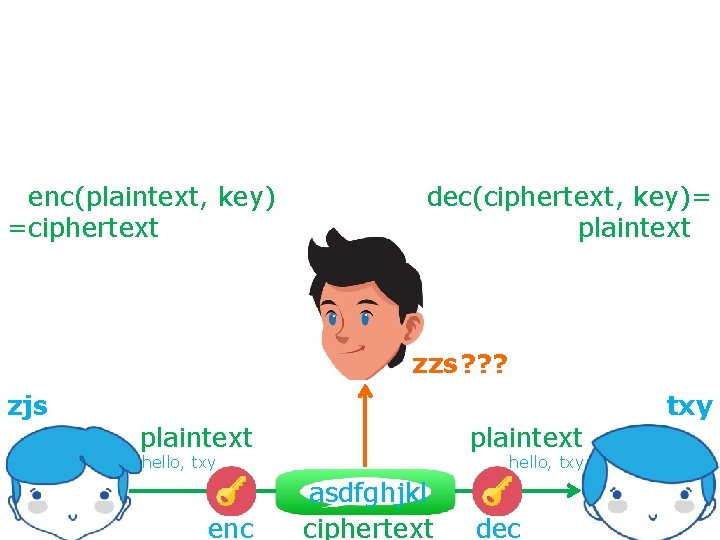
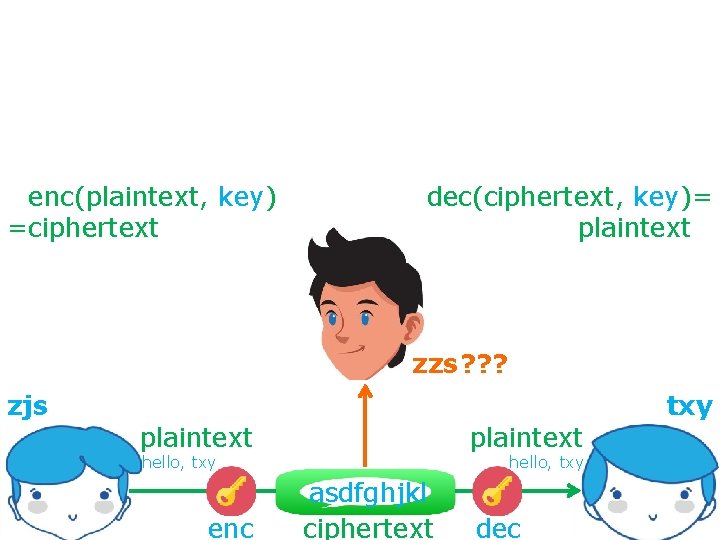
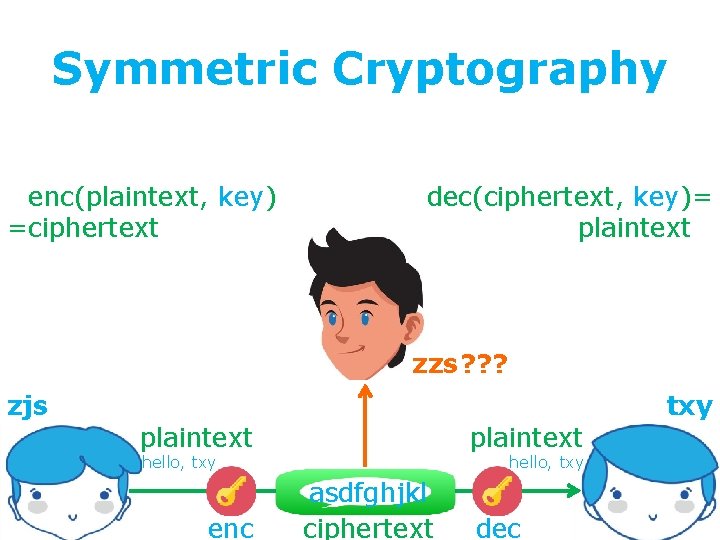
secure communication against adversaries =enc(plaintext, key) =ciphertext dec(ciphertext, key)= plaintext= zzs ? ? ? zjs txy plaintext hello, txy enc hello, txy asdfghjkl ciphertext dec

secure communication against adversaries =enc(plaintext, key) =ciphertext dec(ciphertext, key)= plaintext= zzs ? ? ? zjs txy plaintext hello, txy enc hello, txy asdfghjkl ciphertext dec

Symmetric Cryptography secure communication against adversaries =enc(plaintext, key) =ciphertext dec(ciphertext, key)= plaintext= zzs ? ? ? zjs txy plaintext hello, txy enc hello, txy asdfghjkl ciphertext dec

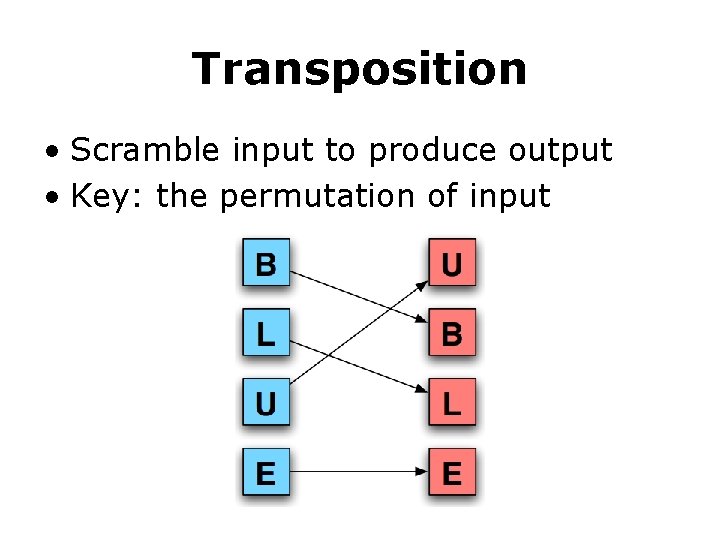
Transposition • Scramble input to produce output • Key: the permutation of input

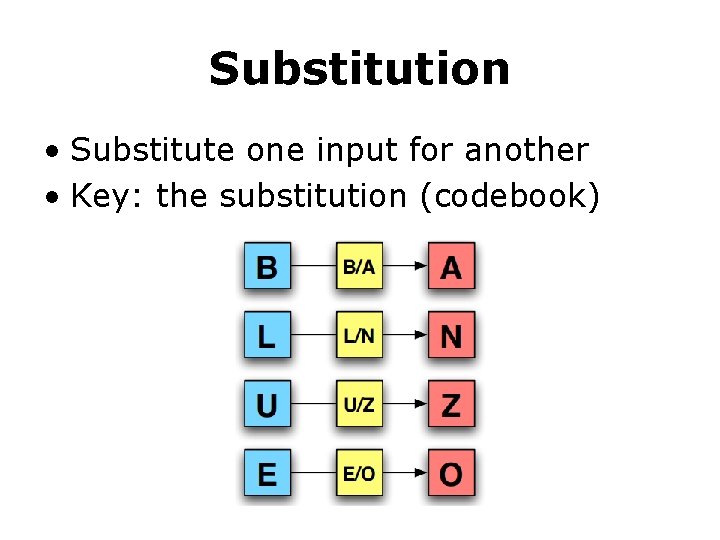
Substitution • Substitute one input for another • Key: the substitution (codebook)

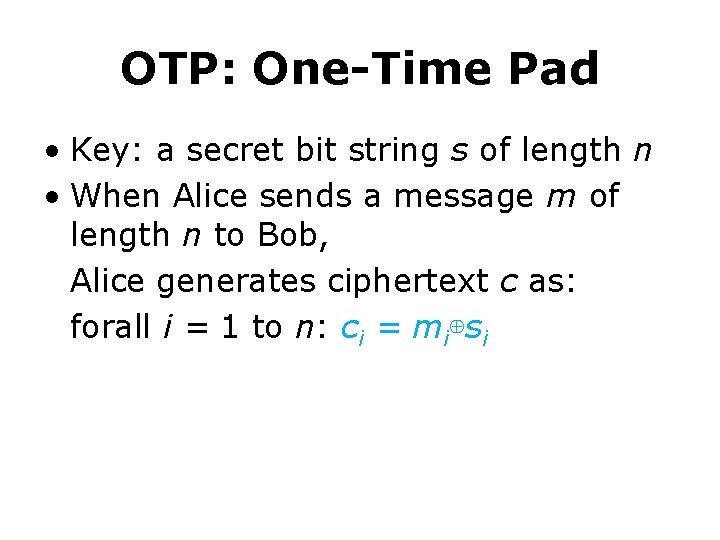
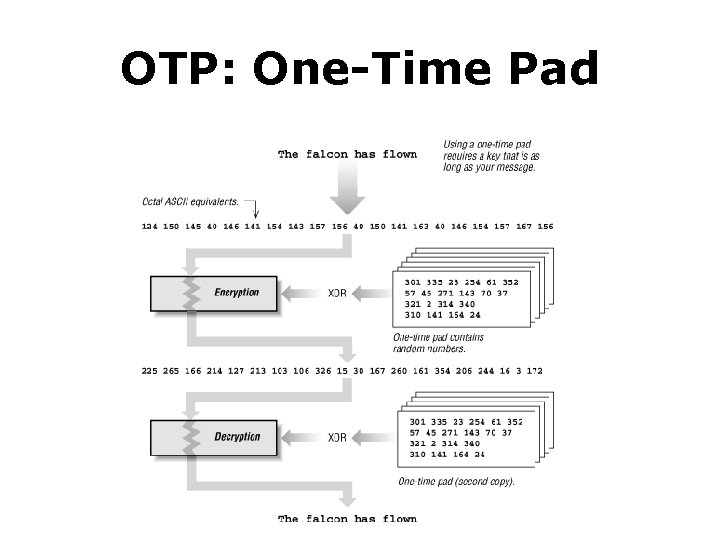
OTP: One-Time Pad • Key: a secret bit string s of length n • When Alice sends a message m of length n to Bob, Alice generates ciphertext c as: forall i = 1 to n: ci = mi⊕si

OTP: One-Time Pad

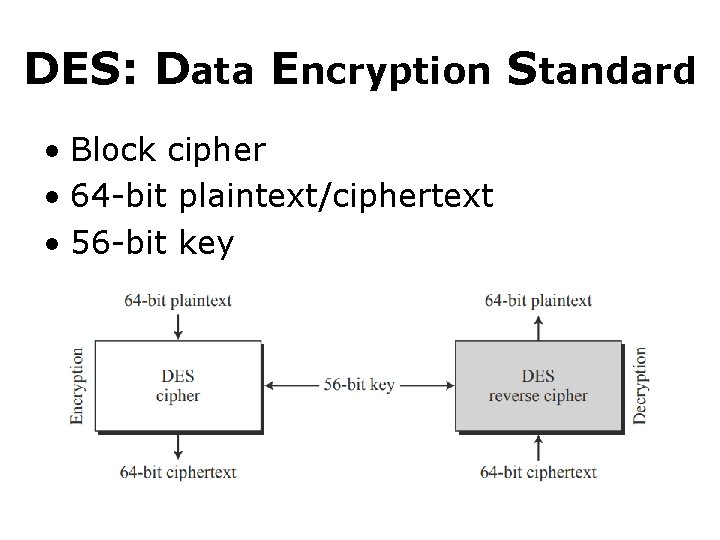
DES: Data Encryption Standard • Block cipher • 64 -bit plaintext/ciphertext • 56 -bit key

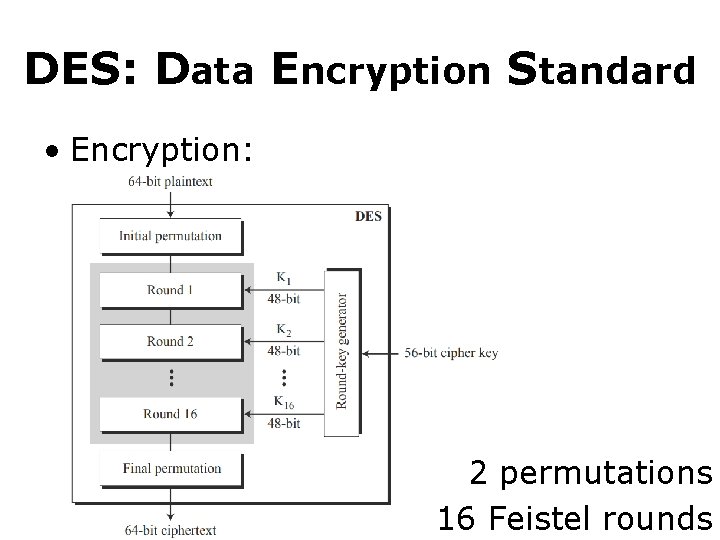
DES: Data Encryption Standard • Encryption: 2 permutations 16 Feistel rounds

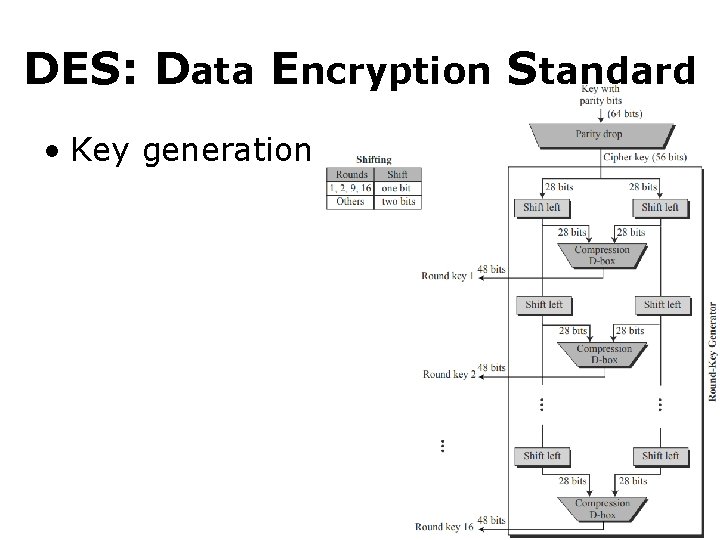
DES: Data Encryption Standard • Key generation

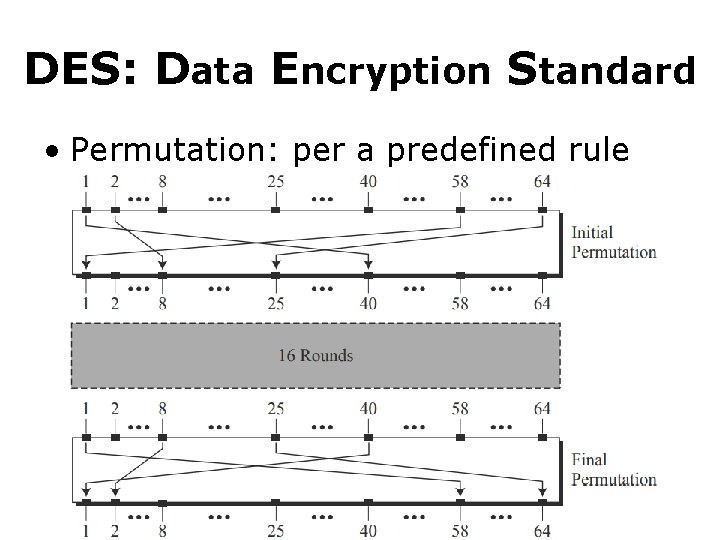
DES: Data Encryption Standard • Permutation: per a predefined rule

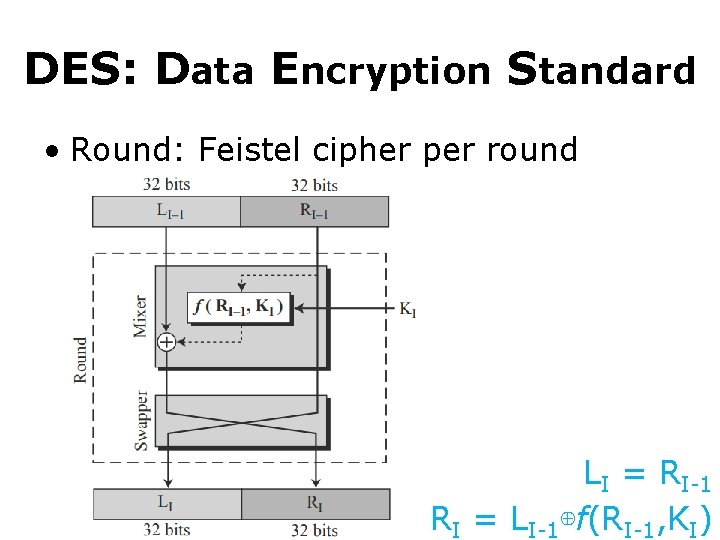
DES: Data Encryption Standard • Round: Feistel cipher per round LI = RI-1 RI = LI-1⊕f(RI-1, KI)

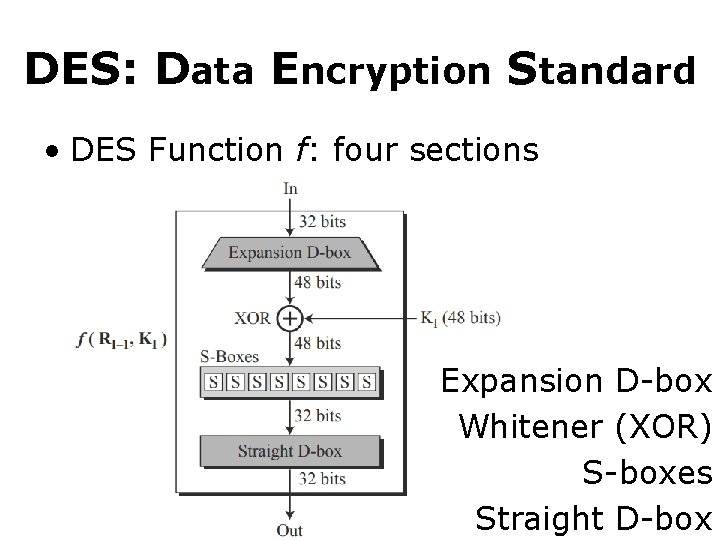
DES: Data Encryption Standard • DES Function f: four sections Expansion D-box Whitener (XOR) S-boxes Straight D-box

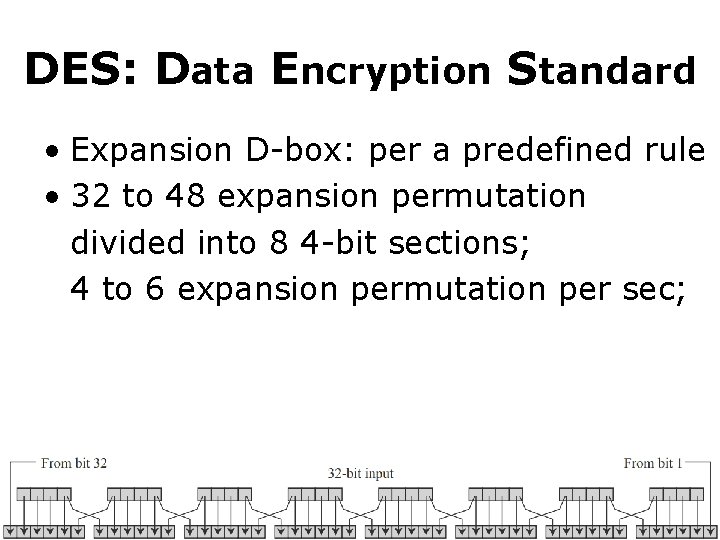
DES: Data Encryption Standard • Expansion D-box: per a predefined rule • 32 to 48 expansion permutation divided into 8 4 -bit sections; 4 to 6 expansion permutation per sec;

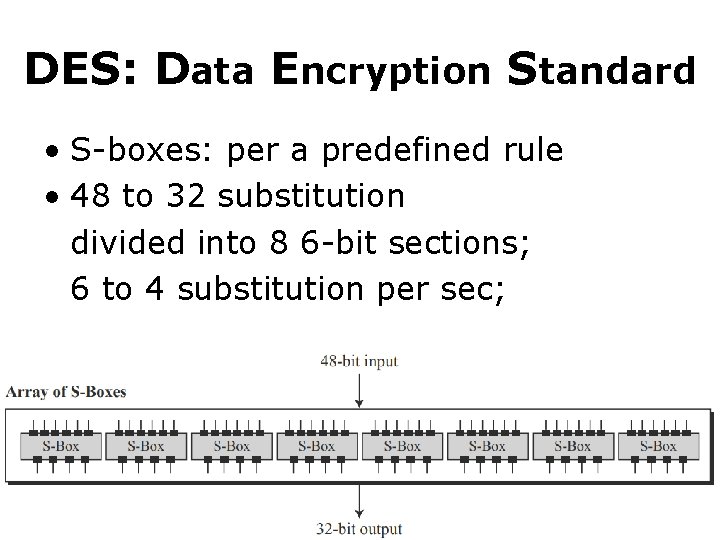
DES: Data Encryption Standard • S-boxes: per a predefined rule • 48 to 32 substitution divided into 8 6 -bit sections; 6 to 4 substitution per sec;

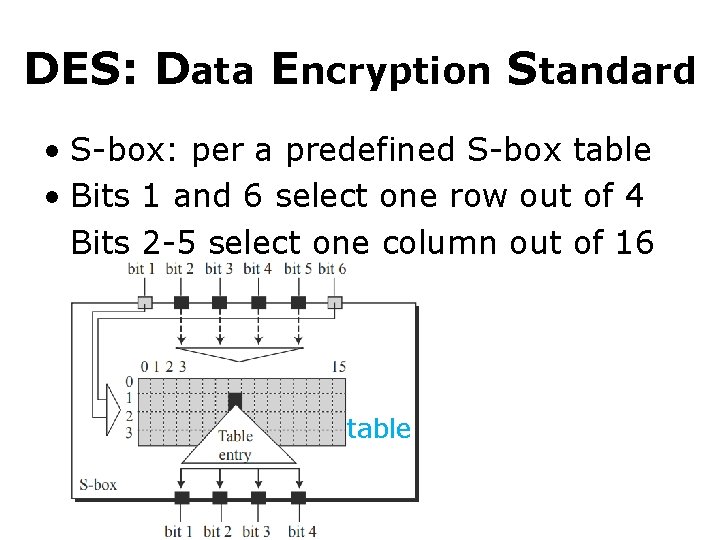
DES: Data Encryption Standard • S-box: per a predefined S-box table • Bits 1 and 6 select one row out of 4 Bits 2 -5 select one column out of 16 table

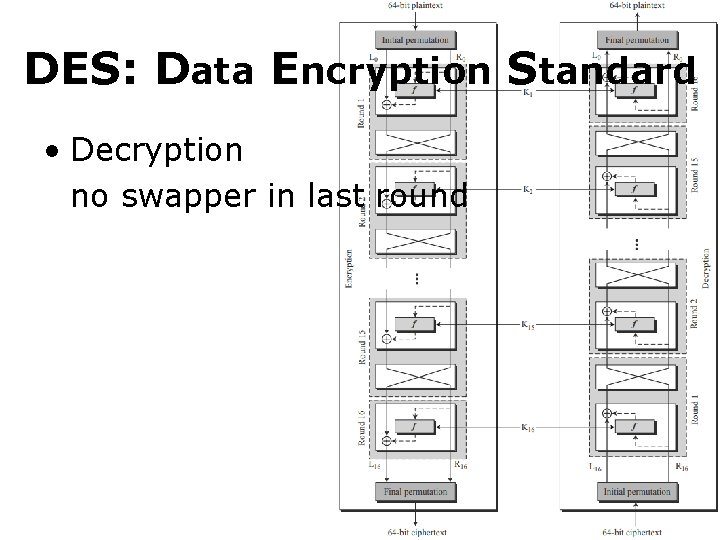
DES: Data Encryption Standard • Decryption no swapper in last round

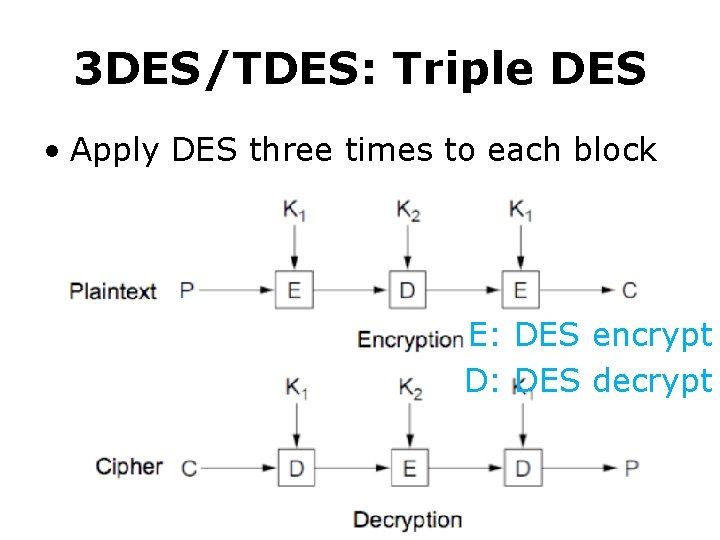
3 DES/TDES: Triple DES • Apply DES three times to each block E: DES encrypt D: DES decrypt

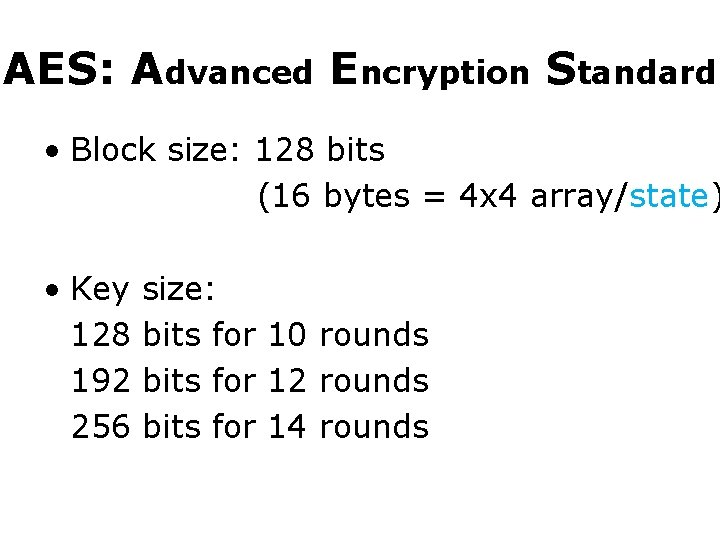
AES: Advanced Encryption Standard • Block size: 128 bits (16 bytes = 4 x 4 array/state) • Key size: 128 bits for 10 rounds 192 bits for 12 rounds 256 bits for 14 rounds

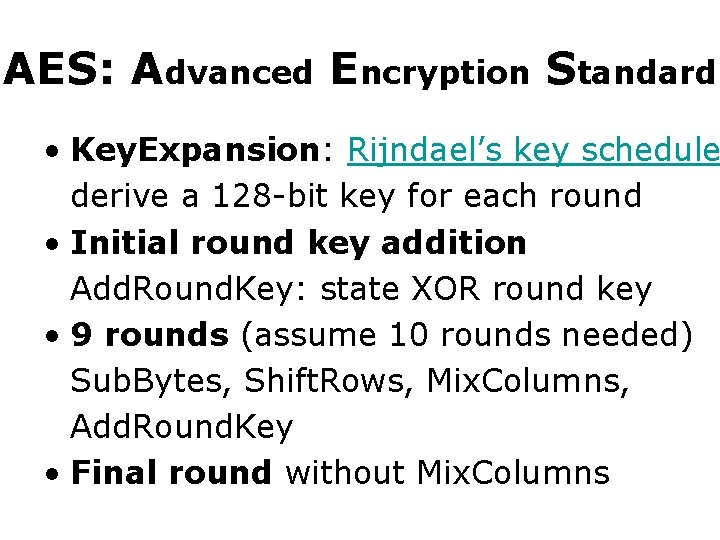
AES: Advanced Encryption Standard • Key. Expansion: Rijndael’s key schedule derive a 128 -bit key for each round • Initial round key addition Add. Round. Key: state XOR round key • 9 rounds (assume 10 rounds needed) Sub. Bytes, Shift. Rows, Mix. Columns, Add. Round. Key • Final round without Mix. Columns

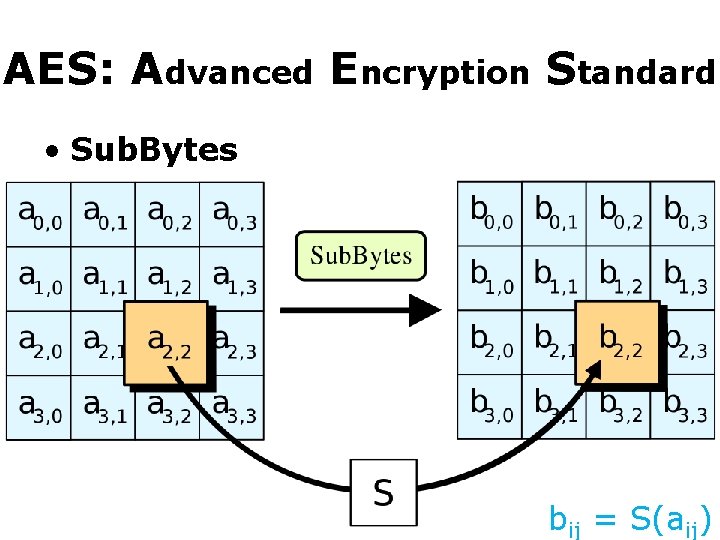
AES: Advanced Encryption Standard • Sub. Bytes bij = S(aij)

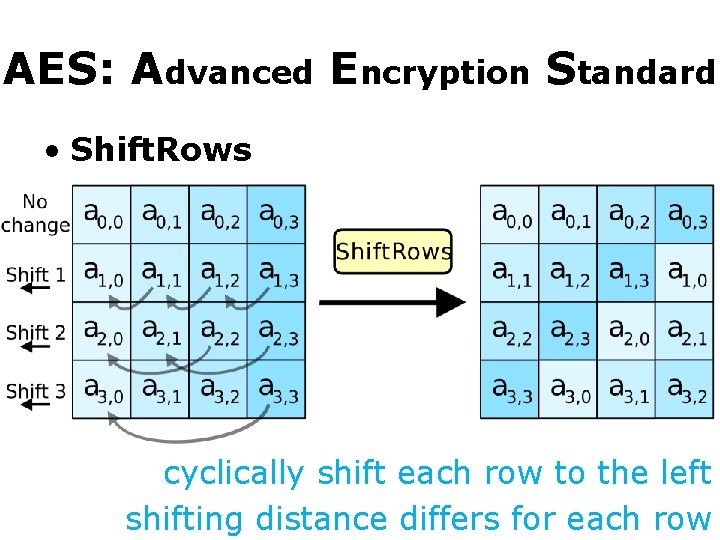
AES: Advanced Encryption Standard • Shift. Rows cyclically shift each row to the left shifting distance differs for each row

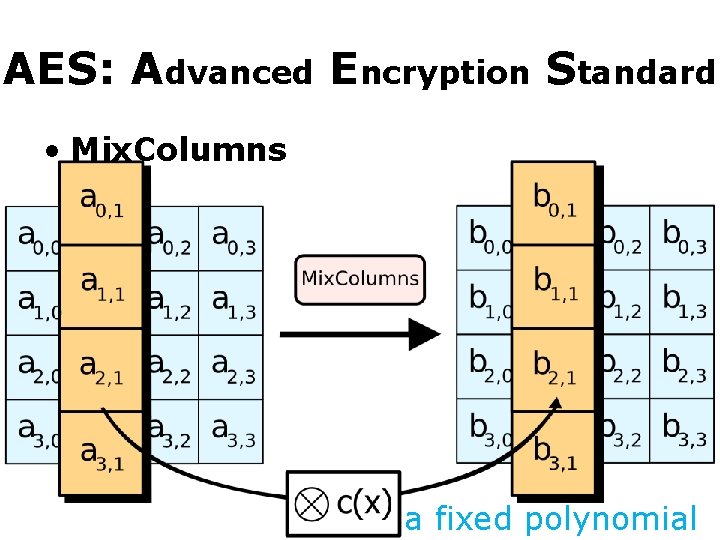
AES: Advanced Encryption Standard • Mix. Columns a fixed polynomial

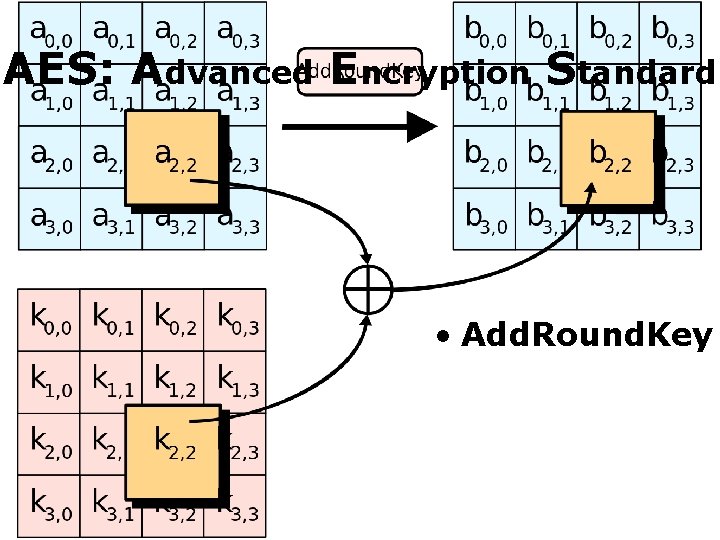
AES: Advanced Encryption Standard • Add. Round. Key

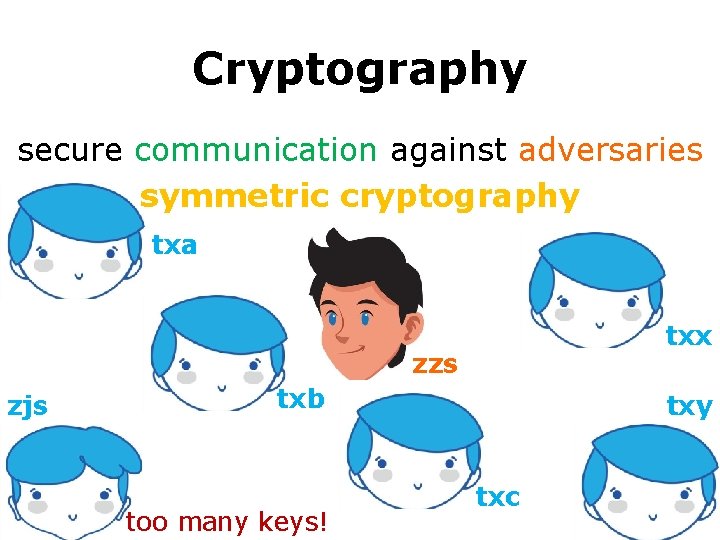
Cryptography secure communication against adversaries symmetric cryptography txa txx zzs zjs txb too many keys! txy txc

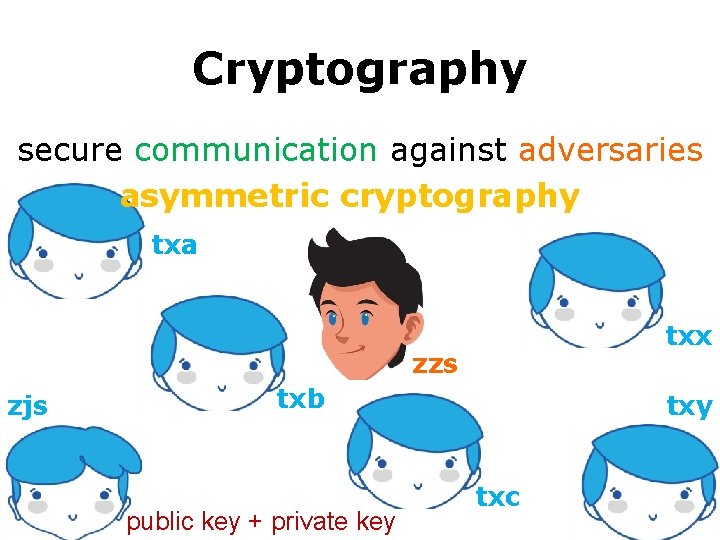
Cryptography secure communication against adversaries asymmetric cryptography txa txx zzs zjs txb public key + private key txc

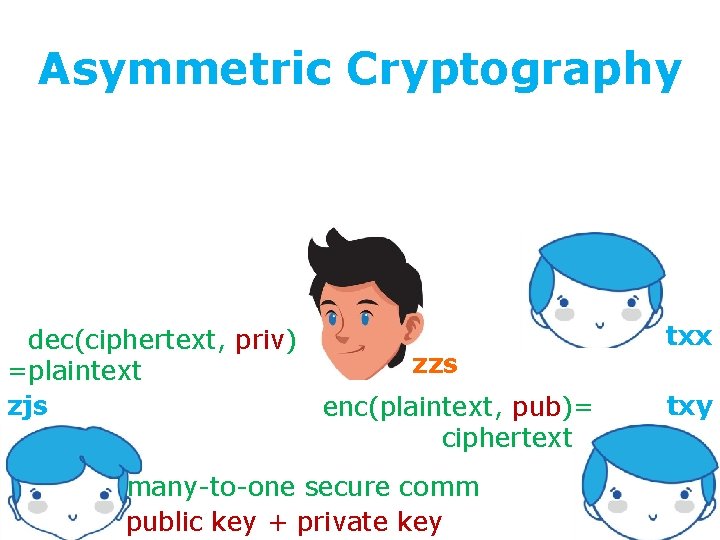
Asymmetric Cryptography =dec(ciphertext, priv) zzs =plaintext zjs enc(plaintext, pub)= ciphertext= many-to-one secure comm public key + private key txx txy

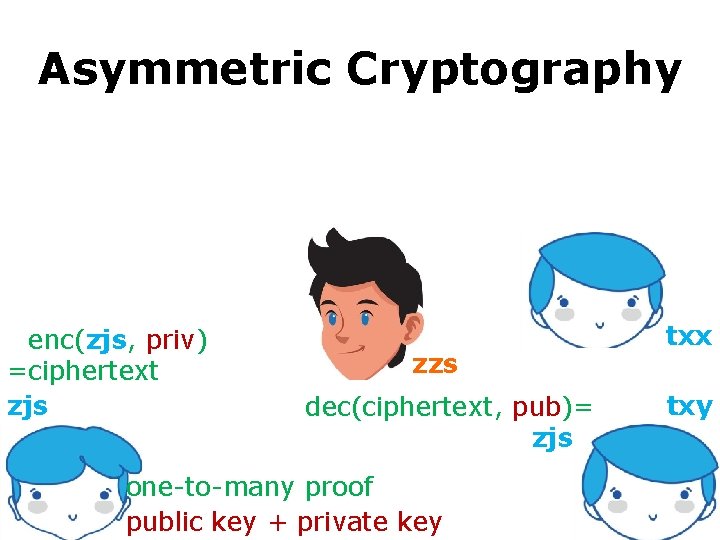
Asymmetric Cryptography =enc(zjs, priv) =ciphertext zjs zzs dec(ciphertext, pub)= zjs= one-to-many proof public key + private key txx txy

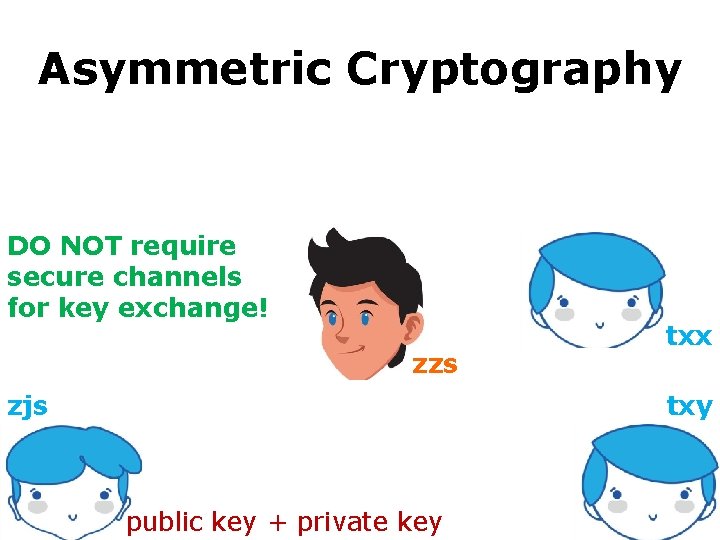
Asymmetric Cryptography secure communication against adversaries asymmetric cryptography DO NOT require secure channels for key exchange! zzs zjs txx txy public key + private key

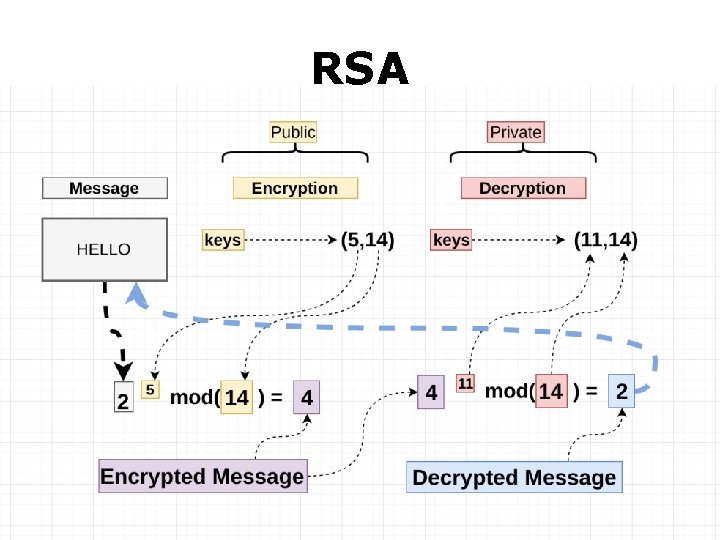
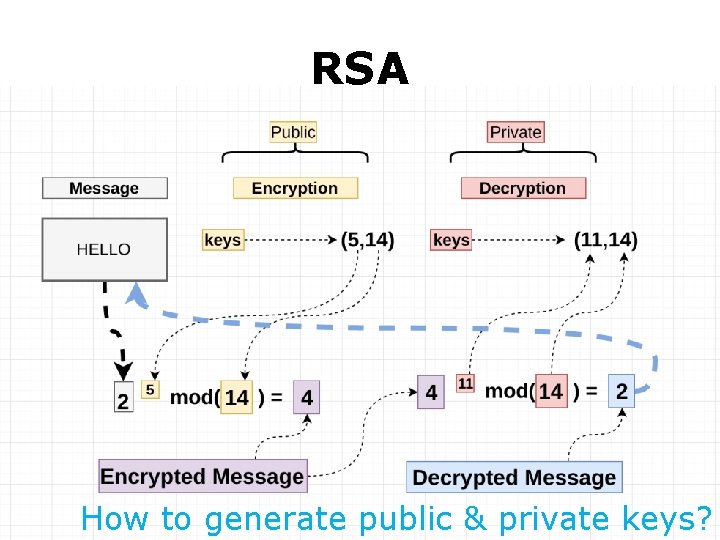
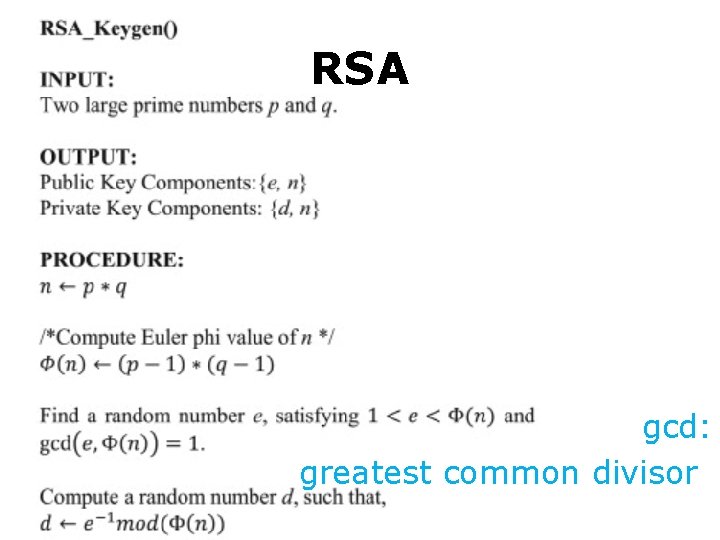
RSA

RSA How to generate public & private keys?

RSA gcd: greatest common divisor:

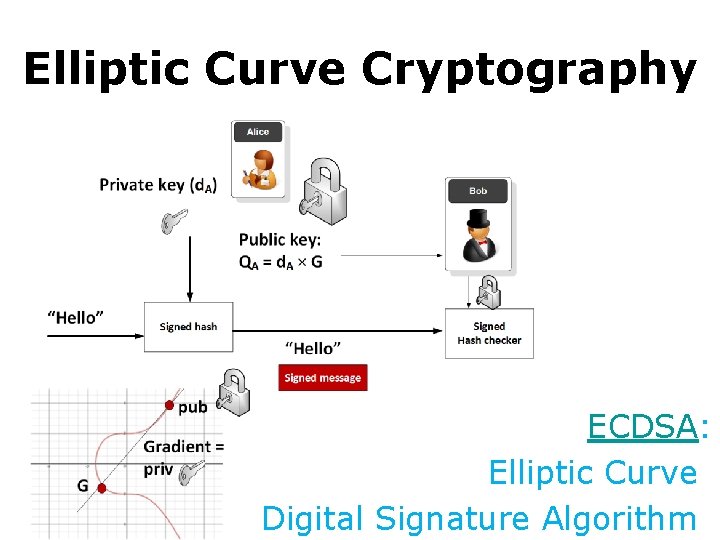
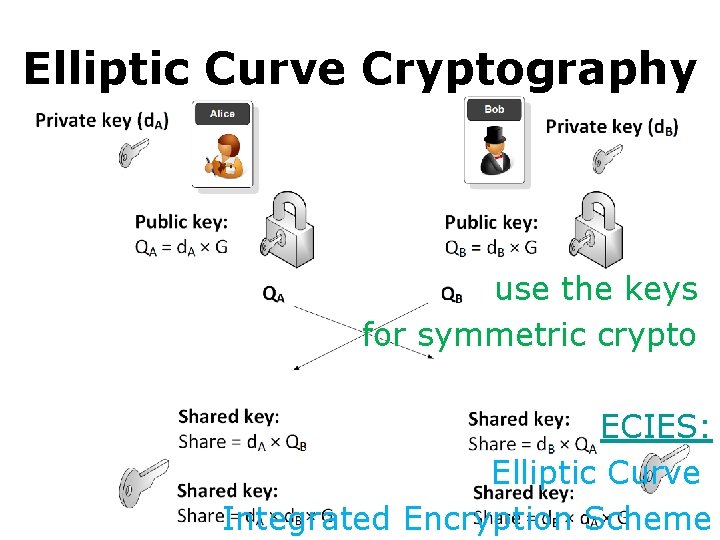
Elliptic Curve Cryptography ECDSA: Elliptic Curve: Digital Signature Algorithm:

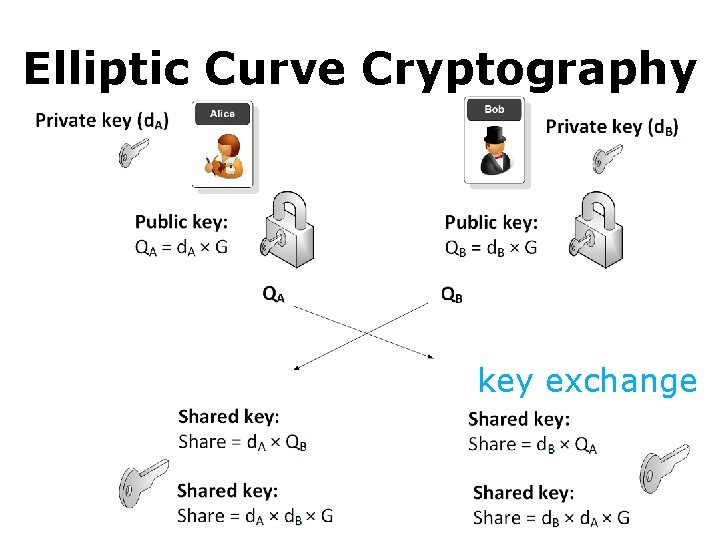
Elliptic Curve Cryptography key exchange: :

Elliptic Curve Cryptography use the keys: for symmetric crypto: ECIES: Elliptic Curve Integrated Encryption Scheme

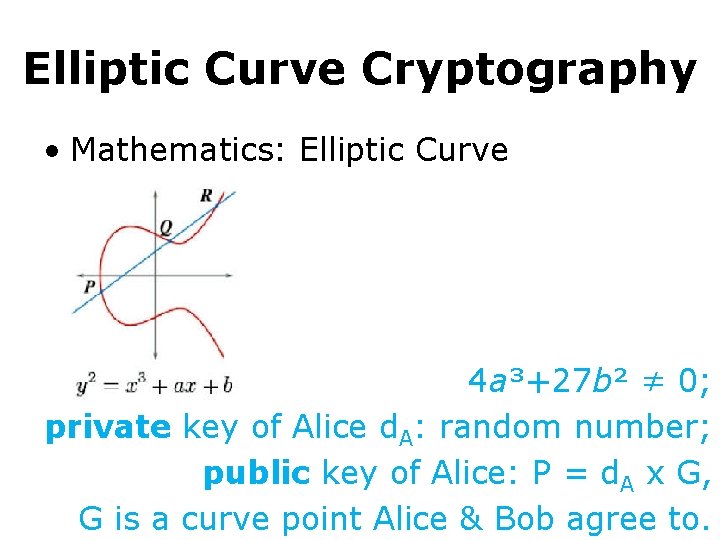
Elliptic Curve Cryptography • Mathematics: Elliptic Curve 4 a³+27 b² ≠ 0; private key of Alice d. A: random number; public key of Alice: P = d. A x G, G is a curve point Alice & Bob agree to.

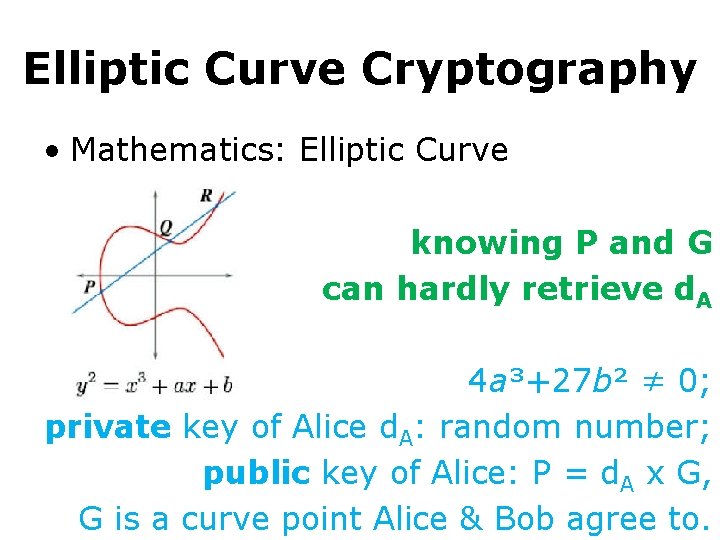
Elliptic Curve Cryptography • Mathematics: Elliptic Curve knowing P and G can hardly retrieve d. A 4 a³+27 b² ≠ 0; private key of Alice d. A: random number; public key of Alice: P = d. A x G, G is a curve point Alice & Bob agree to.

Cryptography as you were told many times

Cryptography like you’ve never heard before

Cryptography secure communication against adversaries reluctant to give out sensitive data?

Cryptography secure communication against adversaries reluctant to give out sensitive data? process data without revealing it

Homomorphic Cryptography • allow computation on encrypted data; • generate an encrypted result that, after decrypted, matches the result of the operations as if they had been performed on the plaintext

Homomorphic Cryptography • Application encrypted-data analysis on cloud

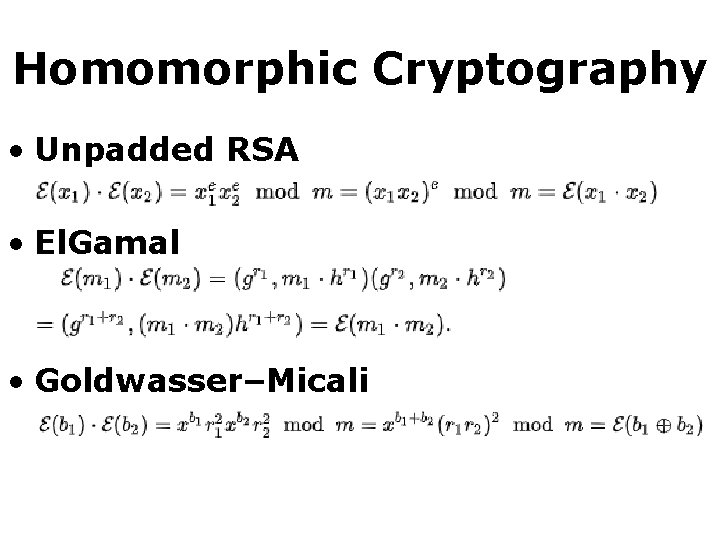
Homomorphic Cryptography • Unpadded RSA • El. Gamal • Goldwasser–Micali

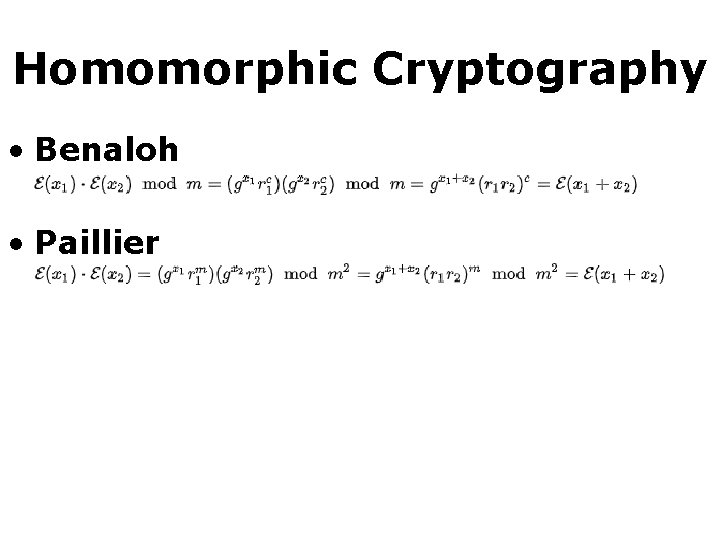
Homomorphic Cryptography • Benaloh • Paillier

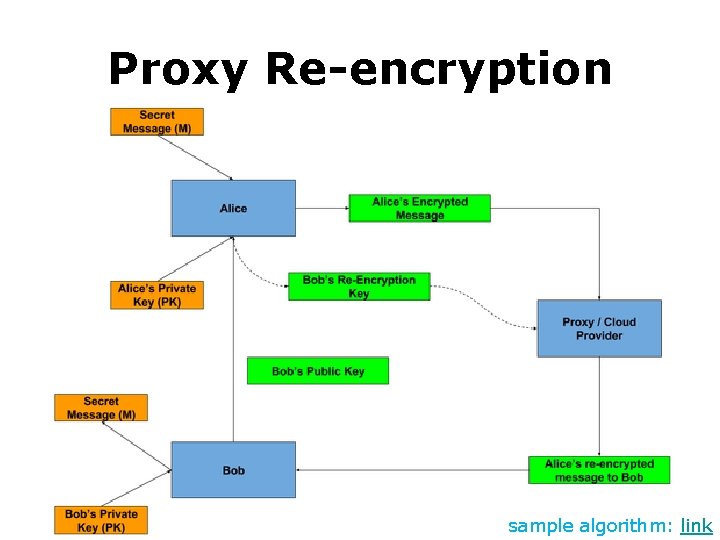
Proxy Re-encryption • Allow third parties (proxies) to alter a cipher text which has been encrypted for one party, so that it may be decrypted by another.

Proxy Re-encryption • Allow a proxy to transform a ciphertext computed under Alice’s public key into one that can be opened by Bob’s secret key.

Proxy Re-encryption • Allow a proxy to transform a ciphertext computed under Alice’s public key into one that can be opened by Bob’s secret key. • Why need it?

Proxy Re-encryption • Allow a proxy to transform a ciphertext computed under Alice’s public key into one that can be opened by Bob’s secret key. • Delegate untrusted proxy to do reencryption, without revealing message and secret keys to it.

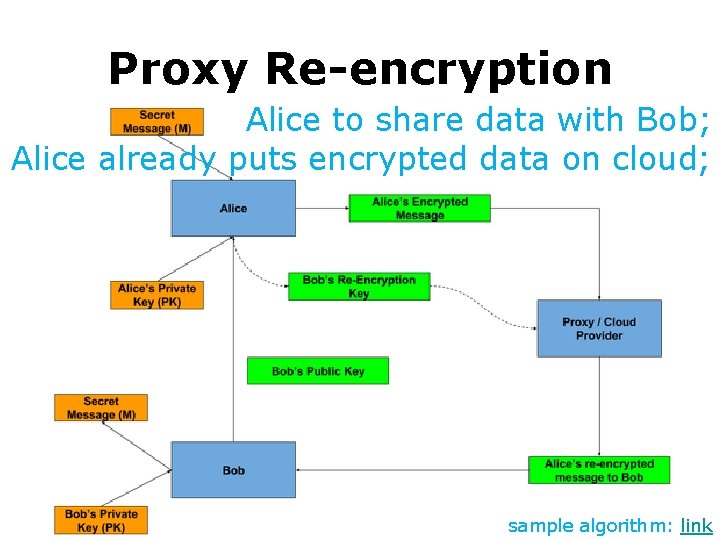
Proxy Re-encryption Alice to share data with Bob; Alice already puts encrypted data on cloud; sample algorithm: link

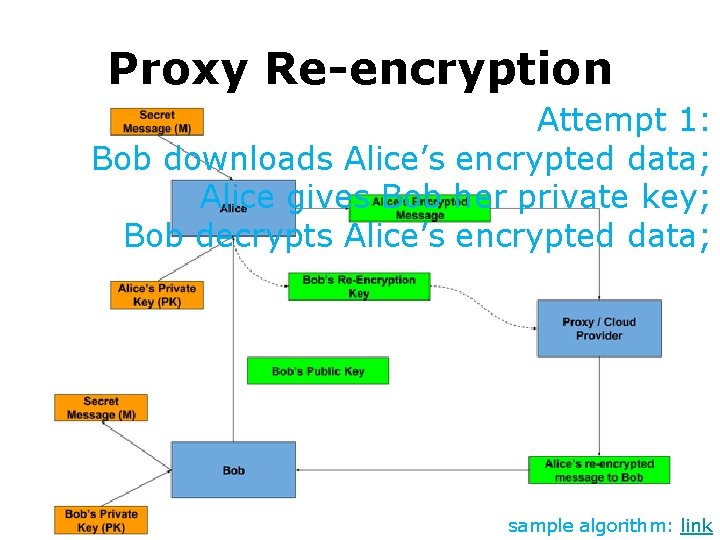
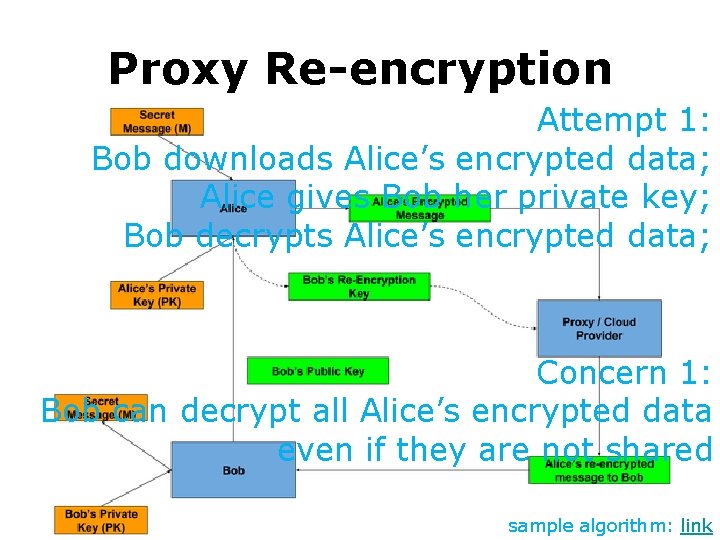
Proxy Re-encryption Attempt 1: Bob downloads Alice’s encrypted data; Alice gives Bob her private key; Bob decrypts Alice’s encrypted data; sample algorithm: link

Proxy Re-encryption Attempt 1: Bob downloads Alice’s encrypted data; Alice gives Bob her private key; Bob decrypts Alice’s encrypted data; Concern 1: Bob can decrypt all Alice’s encrypted data even if they are not shared sample algorithm: link

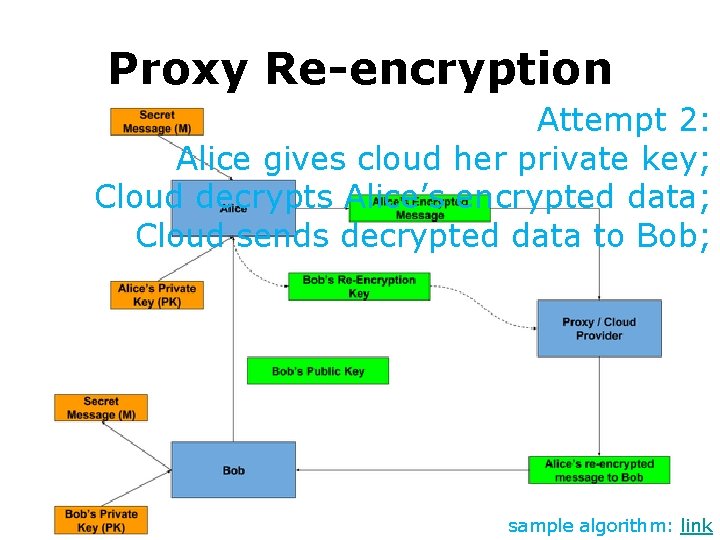
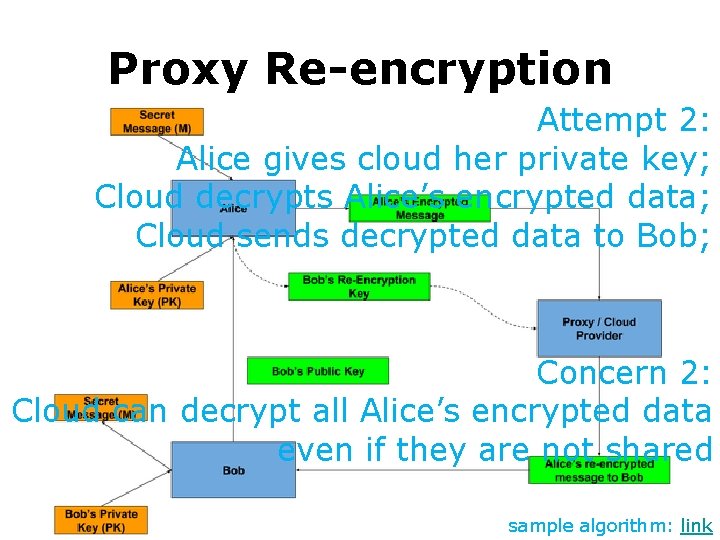
Proxy Re-encryption Attempt 2: Alice gives cloud her private key; Cloud decrypts Alice’s encrypted data; Cloud sends decrypted data to Bob; sample algorithm: link

Proxy Re-encryption Attempt 2: Alice gives cloud her private key; Cloud decrypts Alice’s encrypted data; Cloud sends decrypted data to Bob; Concern 2: Cloud can decrypt all Alice’s encrypted data even if they are not shared sample algorithm: link

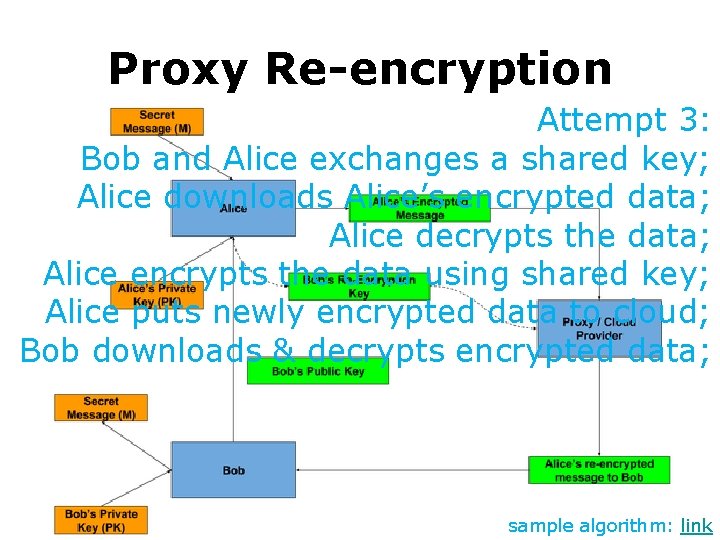
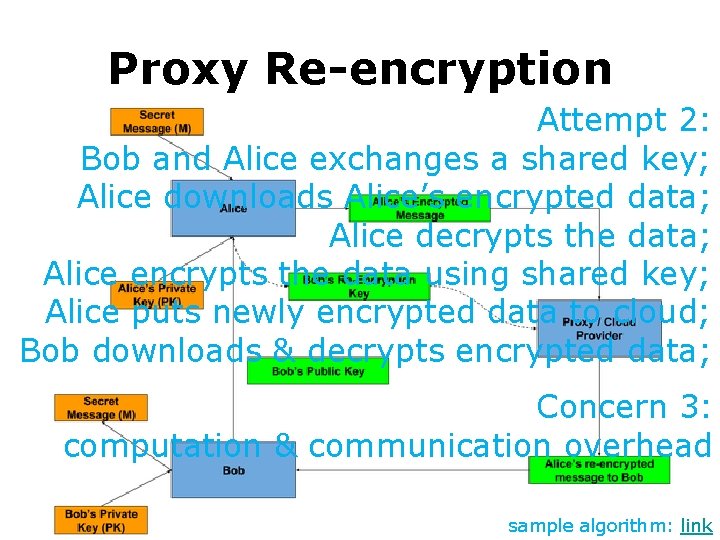
Proxy Re-encryption Attempt 3: Bob and Alice exchanges a shared key; Alice downloads Alice’s encrypted data; Alice decrypts the data; Alice encrypts the data using shared key; Alice puts newly encrypted data to cloud; Bob downloads & decrypts encrypted data; sample algorithm: link

Proxy Re-encryption Attempt 2: Bob and Alice exchanges a shared key; Alice downloads Alice’s encrypted data; Alice decrypts the data; Alice encrypts the data using shared key; Alice puts newly encrypted data to cloud; Bob downloads & decrypts encrypted data; Concern 3: computation & communication overhead sample algorithm: link

Proxy Re-encryption sample algorithm: link

Cryptography what if key leaked?

Cryptography what if key leaked? All previously keyed data leak!

Forward Secrecy • Session keys will not be compromised even if the private key of the server is compromised • By generating a unique session key for every session a user initiates, the compromise of a single session key will not affect any data other than that exchanged in the specific session protected by that particular key https: //en. wikipedia. org/wiki/Forward_secrecy

Review • Symmetric vs Asymmetric Cryptography • DES, AES • RSA, Elliptic Curve Crypto • Homomorphic Encryption • Proxy Re-encryption • Forward Secrecy

Announcement • Project Grouping 2020. 02. 25 – 2020. 03 • Proposal Presentation 2020. 03


Thank You be on the road

Reading • The Internet: Encryption & Public Keys by Mia Epner • Data Encryption Standard (DES) • The Wonderful World of Elliptic Curve Cryptography by Bill Buchanan OBE • Elliptic Curve Integrated Encryption Scheme (ECIES) by Bill Buchanan OBE • Elliptic Curve Cryptography Overview by John Wagnon

Reading • A Survey on Homomorphic Encryption Schemes: Theory and Implementation by A. Acar et al. • Proxy Re-encryption by David Vassallo • Perfect Forward Secrecy by John Wagnon