Telecommunication and Network Security The CISSP Prep Guide

































- Slides: 67

Telecommunication and Network Security The CISSP Prep Guide 2 E. - Mastering the CISSP and ISSEP Exams by Ronald L. Krutz and Russell Dean Vines P. 166 – P. 192 Presented by Franson 2020/12/6 Optimization LAB, Department of Information Management, NTU 1

Outline l l l Intrusion Detection and Response Network Attacks and Abuses Probing and Scanning Malicious Code Web Security 2020/12/6 Optimization LAB, Department of Information Management, NTU 2

Intrusion Detection and Response 2020/12/6 Optimization LAB, Department of Information Management, NTU 3

Intrusion Detection&Response l l l Firewall can only block by services, but Intrusion Detection can response by packets. Intrusion Detection (ID) and Response is the task of monitoring systems for evidence of an intrusion or an inappropriate usage and responding to the intrusion. ID is not a preventive control; it is a detective control. 2020/12/6 Optimization LAB, Department of Information Management, NTU 4

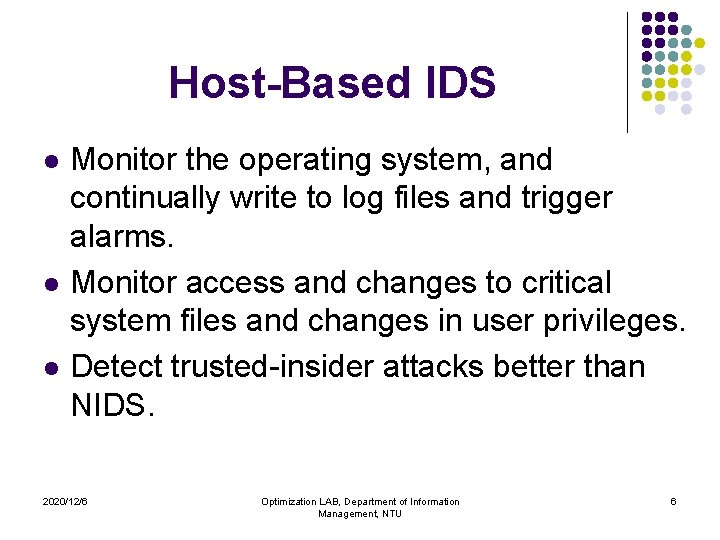
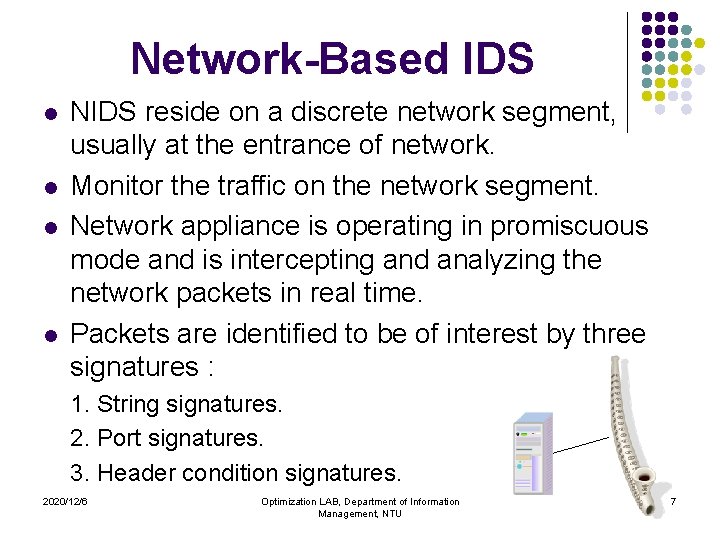
Type of ID Systems l Host-Based IDS (HIDS) IDS operates on a specific host and detect malicious activity only on that host. HIDS l Network-Based IDS (NIDS) IDS operates on network segments and analyze that segment’s traffic. NIDS 2020/12/6 Optimization LAB, Department of Information Management, NTU 5

Host-Based IDS l l l Monitor the operating system, and continually write to log files and trigger alarms. Monitor access and changes to critical system files and changes in user privileges. Detect trusted-insider attacks better than NIDS. 2020/12/6 Optimization LAB, Department of Information Management, NTU 6

Network-Based IDS l l NIDS reside on a discrete network segment, usually at the entrance of network. Monitor the traffic on the network segment. Network appliance is operating in promiscuous mode and is intercepting and analyzing the network packets in real time. Packets are identified to be of interest by three signatures : 1. String signatures. 2. Port signatures. 3. Header condition signatures. 2020/12/6 Optimization LAB, Department of Information Management, NTU 7

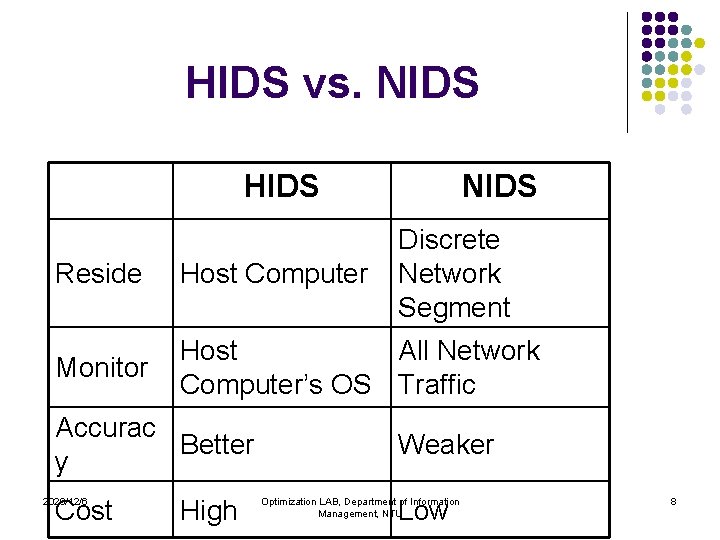
HIDS vs. NIDS HIDS NIDS Discrete Network Segment Reside Host Computer Monitor Host All Network Computer’s OS Traffic Accurac Better y Cost 2020/12/6 High Weaker Low Optimization LAB, Department of Information Management, NTU 8

IDS Approach l Knowledge-Based ID Use database of previous attacks and known system vulnerabilities. l Advantage l l l WAN IDS Drawback l l 2020/12/6 Low false alarm rates Standard and clear alarms to understand Resource-intensive Unnoticed of new, unique, or original attacks Optimization LAB, Department of Information Management, NTU LAN 9

IDS Approach l Behavior-Based ID Alarm is trigger when an activity is considered intrusive. l Advantage l l l Drawback l l l 2020/12/6 Adapt to new, unique, or original vulnerabilities Detect abuse-of-privileges type of attacks High false alarm rates User’s behavior is not static Network is attacked at the same time the IDS learning Optimization LAB, Department of Information Management, NTU 10

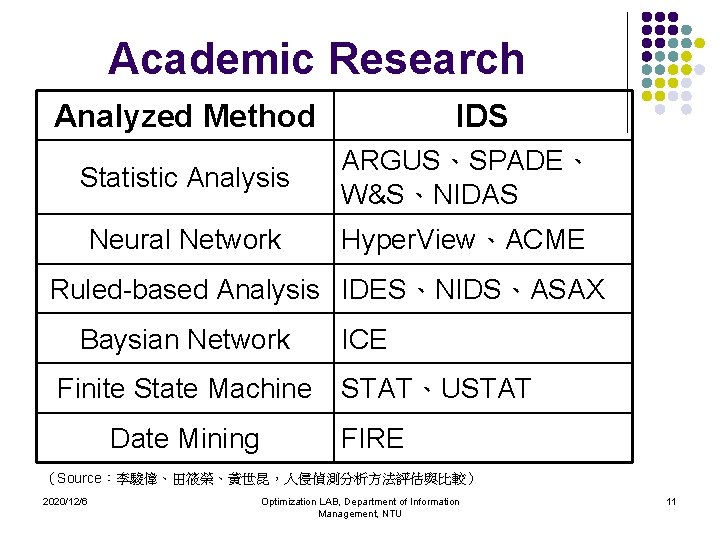
Academic Research Analyzed Method IDS Statistic Analysis ARGUS、SPADE、 W&S、NIDAS Neural Network Hyper. View、ACME Ruled-based Analysis IDES、NIDS、ASAX Baysian Network Finite State Machine Date Mining ICE STAT、USTAT FIRE (Source:李駿偉、田筱榮、黃世昆,入侵偵測分析方法評估與比較) 2020/12/6 Optimization LAB, Department of Information Management, NTU 11

Layered Security Approach l The more elements, or layers, of security that can be added to protect the data. l l l Security policies, procedures, standards, and guidelines. Perimeter security, like routers, firewalls. Hardware and/or software host security products. Auditing, monitoring, intrusion detection, and response. The defeat of any one layer should not lead to a failure protection. 2020/12/6 Optimization LAB, Department of Information Management, NTU 12

IDS with Hubs and Switches l Hub l l l The packets come in on and echo to every port on the hub. IDS sensor can be placed almost anywhere in the infrastructure. Switch l l 2020/12/6 A temporary connection in the switch is first made to the destination port, and then the packets are forward. It must take more care to ensure IDS sensor is able to see all of network traffic. Optimization LAB, Department of Information Management, NTU 13

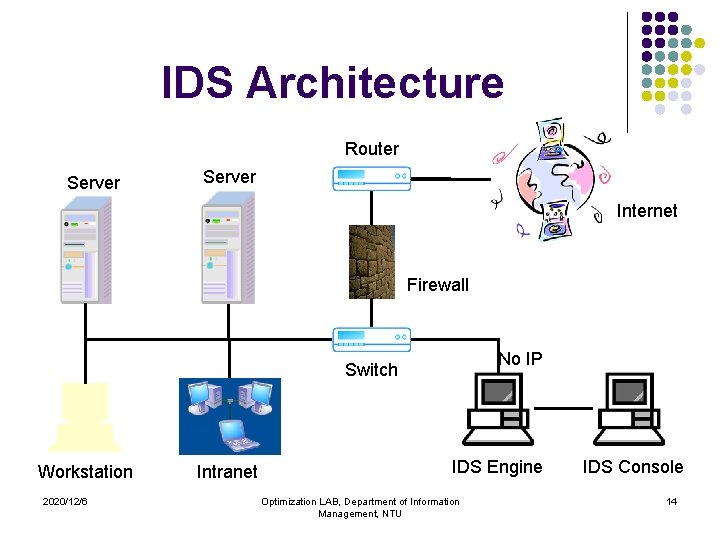
IDS Architecture Router Server Internet Firewall No IP Switch Workstation 2020/12/6 Intranet IDS Engine Optimization LAB, Department of Information Management, NTU IDS Console 14

IDS Performance l l There is a limit to the number of packets that a network ID sensor can accurately analyze in any given time period. The higher the network traffic level and the more complex the analysis, the more the IDS may experience high error rates. 2020/12/6 Optimization LAB, Department of Information Management, NTU 15

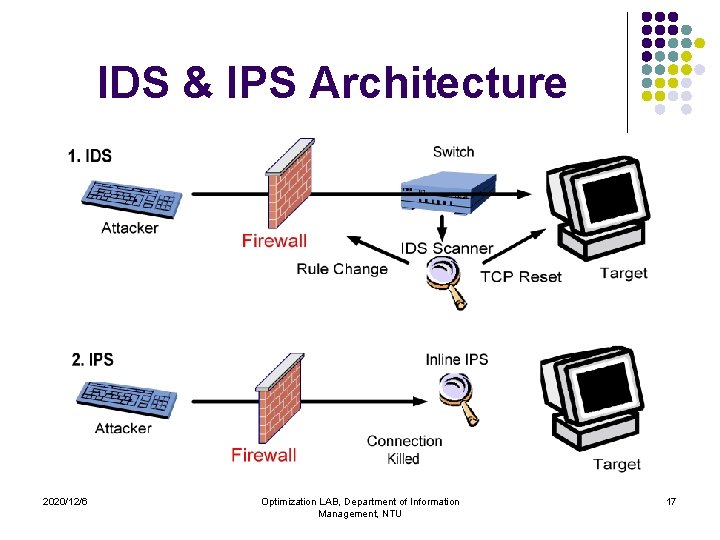
Brief talk about Intrusion Prevention System (IPS) l l The ability to detect attacks, both known and unknown, and prevent the attack from being successful. Advantage l l l Deep packet Inspection In-line mode Drawback l l 2020/12/6 False rates Limit to the number of packets Optimization LAB, Department of Information Management, NTU 16

IDS & IPS Architecture 2020/12/6 Optimization LAB, Department of Information Management, NTU 17

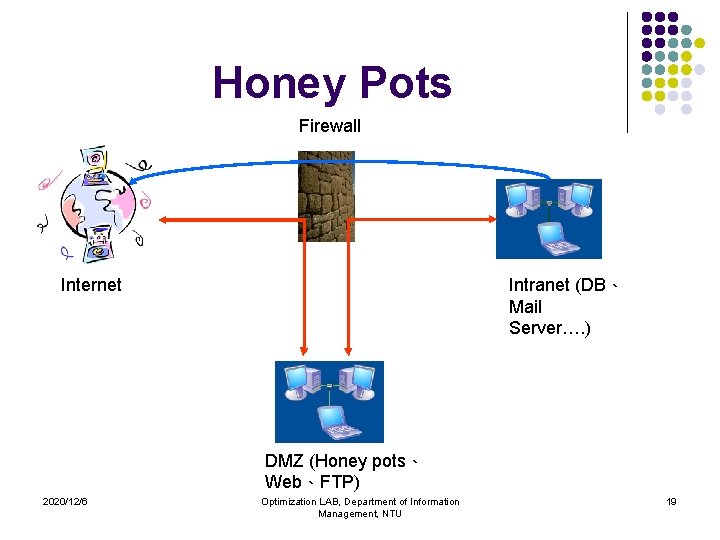
Honey Pots l l l Simulate one or more network services, hoping that an attacker will attempt an intrusion. Identify what the intruders are after, their skill level, and what tools they used. It should be placed in a DMZ. 2020/12/6 Optimization LAB, Department of Information Management, NTU 18

Honey Pots Firewall Intranet (DB、 Mail Server…. ) Internet DMZ (Honey pots、 Web、FTP) 2020/12/6 Optimization LAB, Department of Information Management, NTU 19

Network Attacks and Abuses 2020/12/6 Optimization LAB, Department of Information Management, NTU 20

Logon Abuse l l Legitimate users access service of a high security level that would normally be restricted to them. Masquerading is the term used when one user pretends to be another user. 2020/12/6 Optimization LAB, Department of Information Management, NTU 21

Inappropriate System Use l l Nonbusiness or personal use of network, such as Internet surfing to inappropriate content site. While most employers do not enforce extremely strict Web surfing rules, occasional harassment litigation resulting from employees operating private Web business using company’s infrastructure. 2020/12/6 Optimization LAB, Department of Information Management, NTU 22

Eavesdropping l Unauthorized interception of network traffic. l l l Passive Eavesdropping Active Eavesdropping Covert Channel Eavesdropping Using a hidden unauthorized network connection to communicate unauthorized information. l War Walking/Driving Scanning for 802. 11 -based wireless network information by either driving or walking with a laptop. 2020/12/6 Optimization LAB, Department of Information Management, NTU 23

Network Intrusion l l Unauthorized access to break into a network primarily from external source. Back doors Create several avenues into a network to be exploited later. l Piggy-backing Attacker gain unauthorized access to a system by using a legitimate user’s connection, such as leave the session open or incorrect log out. 2020/12/6 Optimization LAB, Department of Information Management, NTU 24

Denial of Service (Do. S) Attacks Use following techniques to overwhelm a target’s resource. l TCP Do. S Attack. l l l UDP Flood Do. S Attack DDo. S Attack ICMP Do. S Attack l 2020/12/6 Land Attack Teardrop Attack TCP SYN Attack l Ping of Death Smurf Attack Optimization LAB, Department of Information Management, NTU 25

Session Hijacking Attacks Attacker substitute its IP address for that of the trusted client and the server continues the dialog believing it is communicating with the trusted client. l l 2020/12/6 IP Spoofing Attacks C 2 MYAZZ TCP Sequence Number Attacks DNS Poisoning Optimization LAB, Department of Information Management, NTU 26

IP Spoofing l l l Convince a system that it is communicating with a known entity. IP spoofing involves an alternation of a packet. Compare to Smurf attack Attacker fake the target server to send the broadcast signal to the router, then the router send this signal to all computers in the network segment. Those computers will dump ICMP Echo Reply back to the “Source”, and jam the network traffic. 2020/12/6 Optimization LAB, Department of Information Management, NTU 27

C 2 MYAZZ l l It intercepts a client LANMAN authentication logon and obtains the session’s logon credentials and password combination, transparently to the user. The weak of LAN Manager l l 2020/12/6 PW is short to 14 characters. PW is filled to 14 by spaces. PW is cased to capital letters. PW is separated to two 7 -character fragments. Optimization LAB, Department of Information Management, NTU 28

TCP Sequence Number Attack The intruder tricks the target into believing it is connected to a trusted host and then hijacks the session by predicting the target’s choice of an initial TCP sequence number. 2020/12/6 Optimization LAB, Department of Information Management, NTU 29

DNS Poisoning Distributing incorrect IP address information for a specific host with the intent to divert traffic from its true destination. 2020/12/6 Optimization LAB, Department of Information Management, NTU 30

Fragmentation Attacks Using varies IP datagram fragmentation to disguise their TCP packets from target’s IP filtering device. l l 2020/12/6 Tiny fragment attack Force some of the TCP header field form at c: into a second fragment. Overlapping fragment attack (like teardrop) Overwrite the initial packet’s destination address information, and then the second packet is passed by the target’s filtering device. Optimization LAB, Department of Information Management, NTU 31

Dial-Up Attacks l War dialing Call a large pool of telephone numbers to search for those that have a modem attached. l Demon dialing Attack one modem using brute force to guess the password and gain access. 2020/12/6 Optimization LAB, Department of Information Management, NTU 32

Probing and Scanning 2020/12/6 Optimization LAB, Department of Information Management, NTU 33

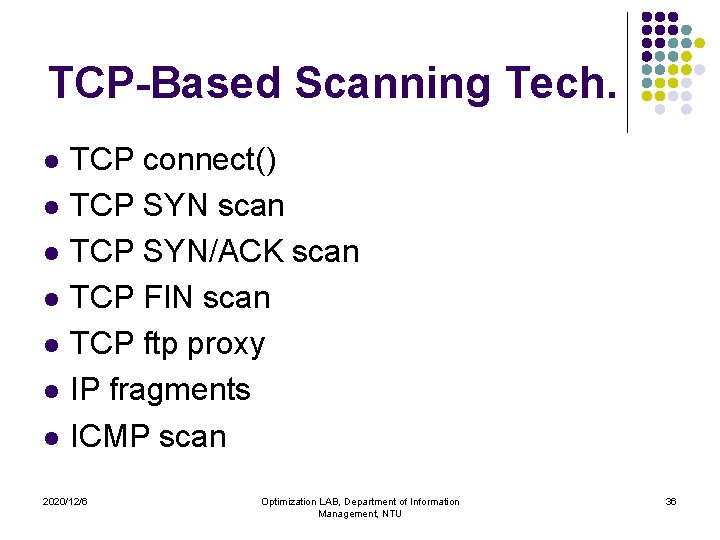
Vulnerability Scanning l Vulnerability scanning should be implemented by the security professional to help identify weaknesses in a system. l Discovery Scanning l l l Inventory scan – OS and available ports Classification process – Applications run on it Workstation Scanning Ensure software has the latest patches and locate uncontrolled or unauthorized software. l Server Scanning All services must be inspected for elements that may compromise security, such as default accounts, weak passwords and unauthorized programs like Trojan Horse may be identified. 2020/12/6 Optimization LAB, Department of Information Management, NTU 34

Port Scanning l l Sending a data packet to a port to gather information about the state of port. TCP/UDP Scanning Types l l 2020/12/6 Stealth Scans Evade or minimize the chances of detection, such as fragmenting the IP datagram within TCP header. Spoofed Scans Inducing a user or device into taking an incorrect action by giving it incorrect information. Optimization LAB, Department of Information Management, NTU 35

TCP-Based Scanning Tech. l l l l TCP connect() TCP SYN scan TCP SYN/ACK scan TCP FIN scan TCP ftp proxy IP fragments ICMP scan 2020/12/6 Optimization LAB, Department of Information Management, NTU 36

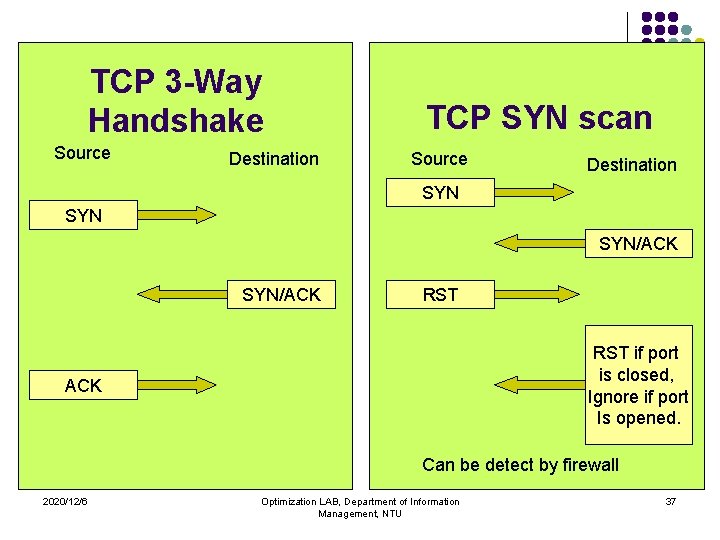
TCP 3 -Way Handshake Source Destination TCP SYN scan Source Destination SYN SYN/ACK RST if port is closed, Ignore if port Is opened. ACK Can be detect by firewall 2020/12/6 Optimization LAB, Department of Information Management, NTU 37

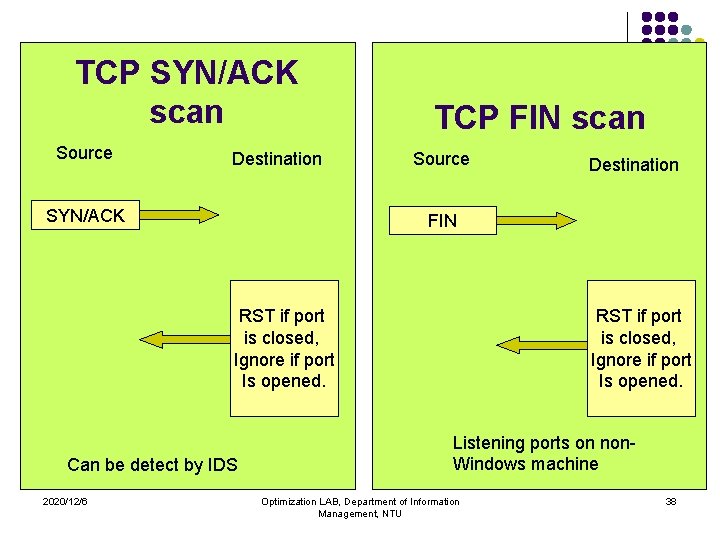
TCP SYN/ACK scan Source Destination SYN/ACK TCP FIN scan Source FIN RST if port is closed, Ignore if port Is opened. Can be detect by IDS 2020/12/6 Destination RST if port is closed, Ignore if port Is opened. Listening ports on non. Windows machine Optimization LAB, Department of Information Management, NTU 38

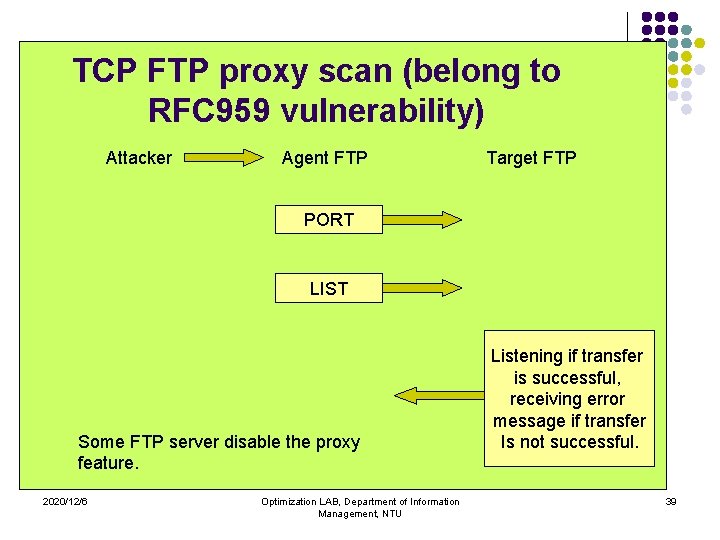
TCP FTP proxy scan (belong to RFC 959 vulnerability) Attacker Agent FTP Target FTP PORT LIST Some FTP server disable the proxy feature. 2020/12/6 Optimization LAB, Department of Information Management, NTU Listening if transfer is successful, receiving error message if transfer Is not successful. 39

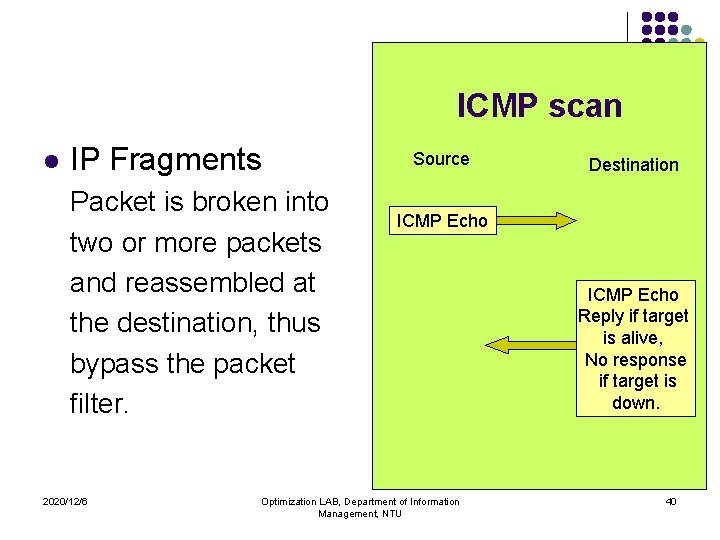
ICMP scan l IP Fragments Packet is broken into two or more packets and reassembled at the destination, thus bypass the packet filter. 2020/12/6 Source Destination ICMP Echo Optimization LAB, Department of Information Management, NTU ICMP Echo Reply if target is alive, No response if target is down. 40

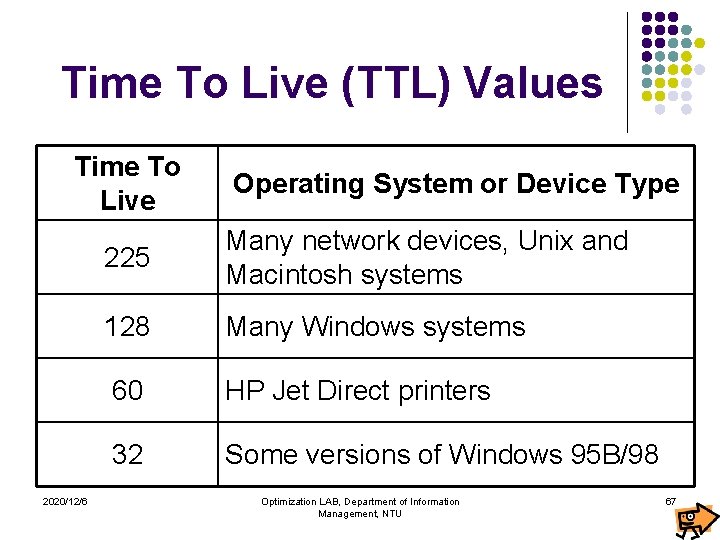
Determining the OS Type l l OS details can be found from Telnet banners, FTP server, TCP/IP stack fingerprinting, etc. Some of these difference include: l l 2020/12/6 Time To Live (TTL) Initial Window Size Don’t Fragment (DF) Bit Type Of Service (TOS) Optimization LAB, Department of Information Management, NTU 41

Malicious Code 2020/12/6 Optimization LAB, Department of Information Management, NTU 42

Viruses A virus infects the operating system in two way : l l l Completely replacing one or more of operating system’s programs. Attaching itself to existing operating system’s programs and altering functionality. Virus Lifecycle : l l l 2020/12/6 Replication – Hidden and do not interfere with normal system functions. Activation – Gradual or sudden destruction of the system. Optimization LAB, Department of Information Management, NTU 43

Macro Viruses l l Macro viruses attach themselves to the application’s initialization sequence, and then when the application is executed, the virus’s instructions execute before control is given to the application. MS Word、MS Excel、and VBScript. 2020/12/6 Optimization LAB, Department of Information Management, NTU 44

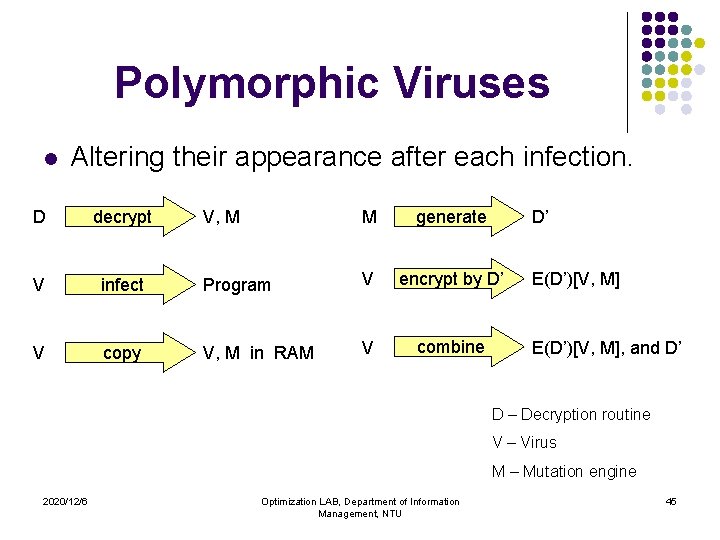
Polymorphic Viruses l Altering their appearance after each infection. D decrypt V, M M generate V infect Program V encrypt by D’ V copy V, M in RAM V combine D’ E(D’)[V, M], and D’ D – Decryption routine V – Virus M – Mutation engine 2020/12/6 Optimization LAB, Department of Information Management, NTU 45

Stealth Viruses l Attempt to hide their presence. l l Hiding the change in the file’s data and time. Hiding the increase in the infected file’s size. Encrypting themselves. They are similar to polymorphic viruses in that they are very hard to detect. 2020/12/6 Optimization LAB, Department of Information Management, NTU 46

Trojan Horses l l l They are not viruses, because they do not reproduce. Trojan horses hide malicious code inside a host program that seems to do something useful. The virus, worm, or other type of malicious code hidden in the Trojan horse, and it usually create a backdoor by opening a high-numbered port to allow access. 2020/12/6 Optimization LAB, Department of Information Management, NTU 47

What is Trojan Horse do? l l l Format disk Steal password Control the host remotely and launch the DDo. S attacks over the network. 2020/12/6 Optimization LAB, Department of Information Management, NTU 48

Logic Bombs l l They are malicious code added to an existing application to be executed at a later date. Can be triggered by l l 2020/12/6 Counter Time Replication number Disk space Optimization LAB, Department of Information Management, NTU 49

Worms l l l Unlike other malicious code, worms do not attach in host program. Worms attack a network by moving from device to device. Infiltrate legitimate data processing programs and alter or destroy the data. 2020/12/6 Optimization LAB, Department of Information Management, NTU 50

Malicious Code Prevention l l l Virus Scanner – use pattern-matching algorithms to scan for many different signatures at the same time. Virus Prevention – reside in memory and monitor system activity or filter income executable programs and specific file types. Virus Detection l l 2020/12/6 Short term – detect infection soon after it occurs. Long term – identify specific malicious code on a system that has already been infected for some time. Optimization LAB, Department of Information Management, NTU 51

Web Security 2020/12/6 Optimization LAB, Department of Information Management, NTU 52

Web Security l l Internet and the World Wide Web attacks involve nuisance attacks, criminal exploits, information warfare, and incapacitation of nation’s critical infrastructure. Three issues: l l l 2020/12/6 Confidentiality Integrity Availability Optimization LAB, Department of Information Management, NTU 53

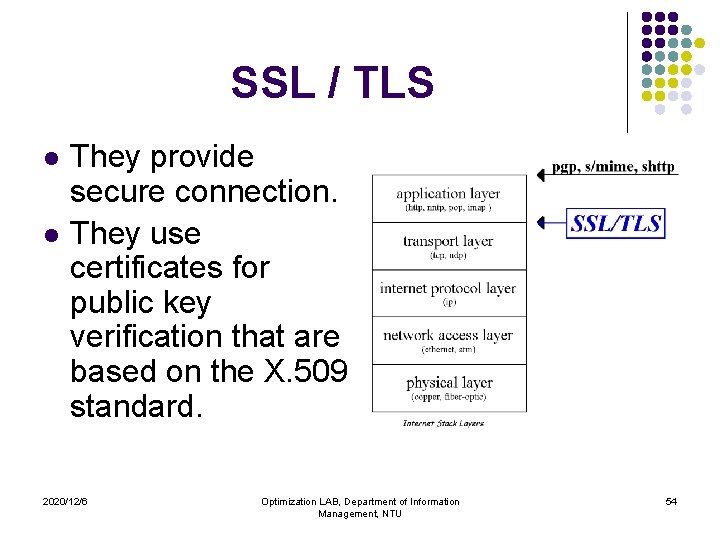
SSL / TLS l l They provide secure connection. They use certificates for public key verification that are based on the X. 509 standard. 2020/12/6 Optimization LAB, Department of Information Management, NTU 54

SSL 3. 0 l l SSL Handshake Protocol – client/server mutual authentication, negotiation of a cryptographic algorithm, and exchange of cryptographic keys. SSL Record Protocol – encapsulation of higher-level protocol, such as SSL Handshake Protocol. 2020/12/6 Optimization LAB, Department of Information Management, NTU 55

Three mechanism SSL provide. l l Mutual authentication – DSS and RSA Encryption of message – 3 DES, and RC 4. Integrity verification of message – MD 5 and SHA-1 Newer browser support 128 -bit encryption. 2020/12/6 Optimization LAB, Department of Information Management, NTU 56

TLS 1. 0 l l TLS Handshake Protocol – The authentication can be accomplished using asymmetric key cryptography. TLS Record Protocol – l l l The privacy is implemented by encryption using symmetric key cryptographic. Integrity is provided through the use of a keyed Message Authentication Code (MAC) using hash. TLS supports more key sizes, and provides different secure levels. 2020/12/6 Optimization LAB, Department of Information Management, NTU 57

S-HTTP l l l It provides secure messaging over HTTP. S-HTTP enabled can communicate with another entity that is not S-HTTP capable. It supports a symmetric key encryption only mode, but many kinds of cryptographic algorithm, encapsulation formats, and so on. 2020/12/6 Optimization LAB, Department of Information Management, NTU 58

Instant Messaging l l l The real time exchange of messages between two parties using the Internet. When IM client is logged on to the server, the server sends the IP addresses and ports numbers of all the others logging on to the server at that time to client software. The user’s message is sent directly to the intended recipient and does not have to go through the IM server. 2020/12/6 Optimization LAB, Department of Information Management, NTU 59

IM Vulnerability l l The drawback of the Instant Messaging is the lack of interoperability. The IM server is particularly vulnerable, because it contains both the messages and the connection information of the participants. 2020/12/6 Optimization LAB, Department of Information Management, NTU 60

8. 3 Naming Conventions l l DOS 8. 3 naming services 16 -bit applications. Hackers just need to guest 8 words then 20 words for a file name. NTFS has the capability to generate file names in the DOS 8. 3 naming. NTFS can optimization of available disk space, fault tolerance, and improved security features. Docum~1 bat . 2020/12/6 Optimization LAB, Department of Information Management, NTU 61

Thanks for Listening ! 2020/12/6 Optimization LAB, Department of Information Management, NTU 62

Reference https: //www. cert. org. tw/document/column/show. php? key=85 http: //www. symantec. com/region/tw/enterprise/article/intrusion_protection. h tml http: //linux. vbird. org/adsl/031 intranet_hubswitch. php http: //www. study-area. org/study. old/network_tcp. htm http: //www. iii. org. tw/adc/papers/thesis/00 B 02. htm http: //wp. netscape. com/eng/ssl 3/index. html http: //cyber. cs. ntou. edu. tw/~b 86207/pro 2. html http: //www. imacat. idv. tw/tech/sslcerts. html#sslx 509 http: //66. 102. 7. 104/search? q=cache: kf. Za. TICEzuk. J: www 2. tw. ibm. com/deve loper. Works/tutorial/Select. Tutorial. do%3 Ftutorial. Id%3 D 201+TLS&hl=zh. TW&lr=lang_zh-TW http: //www. microsoft. com/taiwan/technet/security/guidance/secmod 57. msp x#EEAA 2020/12/6 Optimization LAB, Department of Information Management, NTU 63

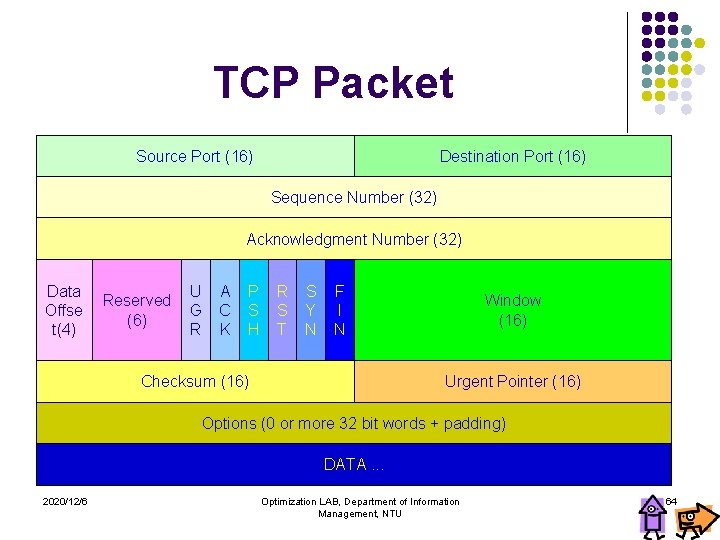
TCP Packet Source Port (16) Destination Port (16) Sequence Number (32) Acknowledgment Number (32) Data Offse t(4) Reserved (6) U G R A C K P S H R S T S Y N F I N Checksum (16) Window (16) Urgent Pointer (16) Options (0 or more 32 bit words + padding) DATA. . . 2020/12/6 Optimization LAB, Department of Information Management, NTU 64

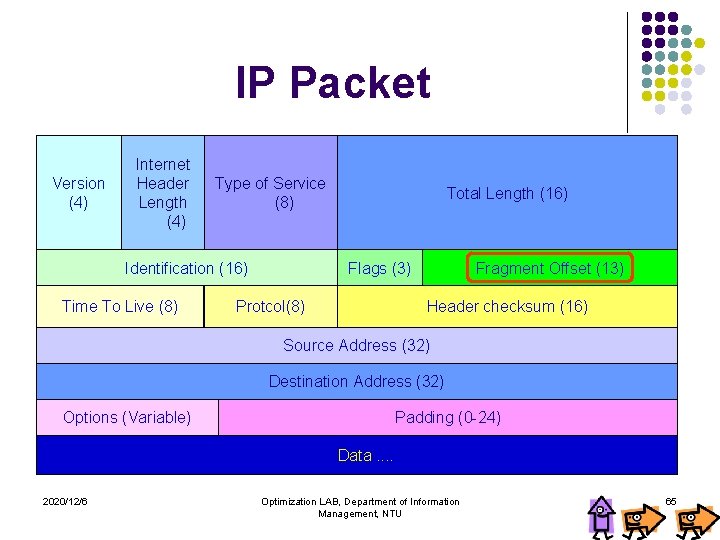
IP Packet Version (4) Internet Header Length (4) Type of Service (8) Identification (16) Time To Live (8) Total Length (16) Flags (3) Protcol(8) Fragment Offset (13) Header checksum (16) Source Address (32) Destination Address (32) Options (Variable) Padding (0 -24) Data. . 2020/12/6 Optimization LAB, Department of Information Management, NTU 65

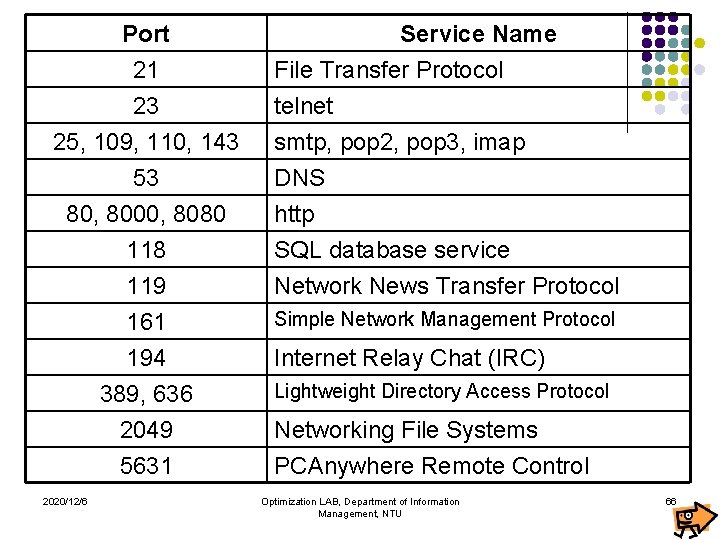
Port 21 23 25, 109, 110, 143 53 80, 8000, 8080 118 119 161 194 389, 636 2049 5631 2020/12/6 Service Name File Transfer Protocol telnet smtp, pop 2, pop 3, imap DNS http SQL database service Network News Transfer Protocol Simple Network Management Protocol Internet Relay Chat (IRC) Lightweight Directory Access Protocol Networking File Systems PCAnywhere Remote Control Optimization LAB, Department of Information Management, NTU 66

Time To Live (TTL) Values Time To Live 2020/12/6 Operating System or Device Type 225 Many network devices, Unix and Macintosh systems 128 Many Windows systems 60 HP Jet Direct printers 32 Some versions of Windows 95 B/98 Optimization LAB, Department of Information Management, NTU 67