Technical Control Standards for Security Configuration Developed Via


































- Slides: 43

Technical Control Standards for Security Configuration Developed Via Public / Private Partnership • Bert Miuccio, Vice President • The Center for Internet Security

Information Security Controls (NIST Pub 800 -53) § Management Controls § Operational Controls § Technical Controls

Security Controls (NIST Pub 800 -53) § Management Controls - address the assessment and management of risk related to information systems

Security Controls (NIST Pub 800 -53) § Operational Controls – address security risks and recommendations primarily related to the people who use information systems (as opposed to the systems themselves) – describe “what” to do in broad terms, and some times describe “when” and by “whom”

Security Controls (NIST Pub 800 -53) § Technical Controls – define in detailed technical terms “how” to implement the requirements of the higher level guidance within specific systems (operating systems, applications, devices / Microsoft, Sun, Cisco, Oracle, etc)

Current Information Security Guidance: • High level management controls-based guidance - OECD and GAISP • Mid-level operational controls-based guidance – ISO 17799 – FISMA – Cob. IT (ISACA) – Standards of Good Practice (ISF) • Detailed technical controls guidance – CIS Consensus Benchmarks and Scoring Tools – NSA, DISA, NIST, and security service / software vendors

Most vulnerabilities being exploited by attackers exist because of: • Software defects – Fixed with vendor patches • Inadequate technical security controls – Fixed by settings which enable or disable security features of the software or network device

Examples of security requirements/policies activated via technical controls • Password length, complexity • Account lockout after X attempts • Log what system events? • Idle time before workstation logoff • Who is allowed to install printer drivers? • What unneeded services to disable?

We have met the enemy, and it is us! “Through 2005, 90 percent of cyber attacks will continue to exploit known security flaws for which a patch is available or a preventive measure known. ” » Gartner Group, May 6, 2002

Why are vendors shipping unsecured systems? • “Our customers don’t want security; they want features and performance. When they do want security, we’ll deliver it. ” • “Every customer wants something different. We can’t be expected to deliver and maintain thousands of different configurations. ”

Recognizing the challenge • Cosmos Club meeting Aug 2000 • Need to develop and proliferate detailed operational best practices – The only true solution is to raise the bar everywhere-globally – Private sector won’t trust gov’t to do it – Private sector companies don’t trust each other because of competitive self-interest

The Center for Internet Security (CIS) • Formed in October 2000 • A not-for-profit consortium of users • Focused on the common needs of the global Internet community – Knowledge transfer from haves to have-nots • Convenes and facilitates consensus teams that develop detailed operational best practices

Some participants in the consensus effort: Government: • National Institute of Standards and Technology • Infocomm Development Authority of Singapore • Naval Surface Warfare Center • US Treasury Financial Management Service • Washington State Dept. of Health • US Army Corps of Engineers • Defense Info Sys Agency • Federal Reserve System • State of Maryland • • • NASA Australian Nat’l Audit Ofc US Dept of Justice Library of Congress Royal Canadian Mounted Police Communications Security Establishment (Canada) Canadian CERT GSA NSA DHS Fed. CIRC

Some Participants (cont’d): Commercial: • Dun and Bradstreet • Electric Power Research Inst. • SASKTel • Fidelity National Financial • LG&E Energy • Hospital Corp. of America • Duetsche Telekom T-Com • Intel • Bank of Montreal • Pfizer • Caterpillar • Intuit • Anadarko Petroleum • Batelle • Swiss Reinsurance Company • University Health System Consortium • Humana • Nu Skin Enterprises • Online Resources • Phelps Dodge Corporation • STERIS Corporation • Thomson Holdings • Wachovia Corporation • Agilent Technologies • Shell Info. Tech. Int’l • People. Soft • News Corporation

Some Participants (cont’d): Universities: • Institute for Security Technology Studies at Dartmouth • Virginia Tech • Monash University (Australia) • Duke University • University of Missouri • Blenkinge Inst. of Technology (Sweden) • Utah State University • University of California, SF • New York University • Illinois Institute of Technology • College of William and Mary Consulting/Service: • IBM Consulting • Configuresoft • ISS • Symantec • Bind. View • Sequation • Net. IQ • Solutionary • RDA Corporation • Belarc • GFM Consulting

Vendors are fully engaged as team members, working alongside government and private sector users • Microsoft • Sun • HP • Cisco • Oracle • AOL

The consensus process • Teams are formed with security experts from member organizations • An initial benchmark draft is obtained or developed • Consensus is established via email and conference call discussion • A scoring tool is developed • They are made available free to all users globally via the CIS website (www. cisecurity. org)

What has collaboration among the participants achieved so far?

Currently available: • Level I Configuration Benchmarks – Solaris – Linux – HP-UX – Windows NT – Windows 2000 – Windows XP – Cisco Router IOS – Oracle Database

A Level I Benchmark: • Can be implemented by a sysadmin of any level of security expertise • Can be monitored by a compliance tool • Is not likely to “break” any function • Represents a baseline level of security

Currently available: • Level II Benchmarks – Windows 2000 Professional – Windows 2000 Server – Windows XP – CISCO Router IOS Level – Oracle Database

Currently available: • Configuration Scoring Tools – Available for each Benchmark – Scan only (don’t automatically change settings) – Host based (not network scanners) – Compare configuration of the scanned system with the corresponding benchmark, score it on a scale of 1 -10 – Configure a newly deployed system and monitor configuration of the computers on which they are installed

Under development: • Benchmarks and Scoring Tools for: – – – – – Apache Windows IIS Catalyst Switches PIX Firewall Check Point FW-1 Server 2003 SQL Server Juniper Router and others

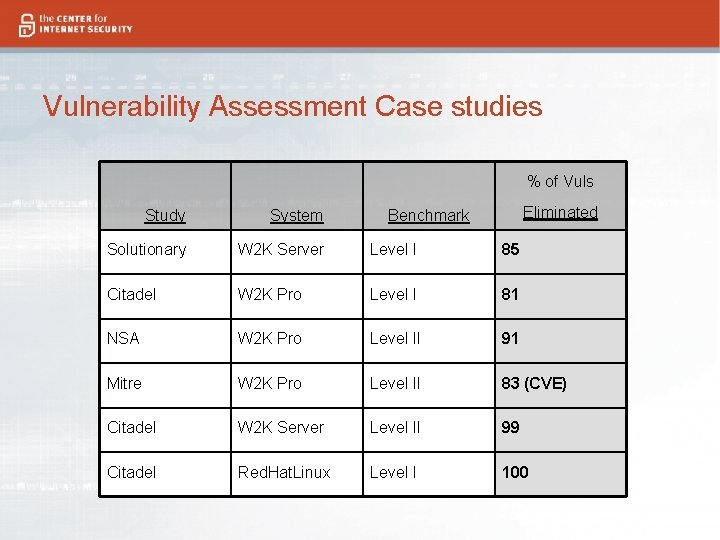
The impact… Case studies show that 80 -90% of known vulnerabilities are blocked by the security settings in the consensus benchmarks…….

Case Study Methodology • (1) Scan a system “out of the box” and list identified vulnerabilities • (2) Configure the system with the appropriate benchmark • (3) Rescan the system and note the vulnerabilities remaining

Vulnerability Assessment Case studies % of Vuls Eliminated Study System Benchmark Solutionary W 2 K Server Level I 85 Citadel W 2 K Pro Level I 81 NSA W 2 K Pro Level II 91 Mitre W 2 K Pro Level II 83 (CVE) Citadel W 2 K Server Level II 99 Citadel Red. Hat. Linux Level I 100

IA Newsletter describing the NSA and Mitre studies • Vol 5, Number 3, Fall 2002 • http: //iac. dtic. mil/iatac/IAnewsletter/Vol 5_No 3. pdf

NSA Red/Blue Team Conference Oct 2003 • These teams are the security experts whose job is to discover weaknesses in Do. D networks by attempting to penetrate them

At that conference: • During four days of trying, these security experts were unable to break into a Microsoft Windows network with up-to-date patches and configured with the consensus benchmark technical controls

Milestones in the consensus benchmark effort • Jul 02 – W 2 K Level-2 benchmark announced by NSA, DISA, NIST, GSA, SANS, and private sector participants • Oct 02 - U. S. government begins promulgating consensus benchmarks and tools via Fed. CIRC • Nov 02 – NSA reports that consensus benchmarks eliminate over 90% of known vulnerabilities • Dec 02 - VISA adopts benchmarks for its Cardholder Information Security Program Digital Dozen

Milestones in the consensus benchmark effort (Cont’d) • Jul 03 – Dell begins delivering Windows 2000 systems pre -configured with consensus benchmark settings • Sep 03 - U. S. Dept of Energy announces procurement requiring Oracle to pre-configure its software with the consensus benchmark settings • Dec 03 – AOL requests a benchmark for its users • June 04 – Dell will begin shipping configured XP systems

Factors driving adoption of the consensus benchmark practices • Private sector desire for liability protection via evidence of due care • Regulatory compliance – SOX, HIPAA, GLB, FISMA, etc • Incorporation in procurement req’ts by government and commercial buyers – Consensus on technical controls developed jointly with users enables vendors to deliver systems that are more secure by default

How can you become involved? • Download the Benchmarks and Scoring Tools. • Use them to configure your new installations. • Compare the configuration of your production systems. How do your systems measure up? • As necessary – improve your security configs. • Share your feedback – contribute to the consensus.

How else can you be involved? • Become a CIS member – help develop and proliferate the consensus benchmarks as common practice — thus making the Internet safer for you and everyone else.

Conclusions • Using the benchmarks and scoring tools available free at http: //www. cisecurity. org implements much of currently available high level guidance (SOX, HIPAA, GLB, FISMA, etc) • Users and vendors are working together to improve security practice • Detailed configuration practice offers substantial payoff for the effort expended

• Bert Miuccio • bmiuccio@cisecurity. org

Important Background Information “The Benefits of Membership” • The benchmarks & tools are periodically updated to – reflect consensus input from security professionals – keep pace with updated versions of the subject software – include technical controls that help defend against emerging threats and vulnerabilities • The Terms of Use prohibit redistribution of the benchmarks and software tools for the purpose of minimizing redistribution of outdated versions of the resources.

TOU on the CIS web site • Grant of Limited rights. “CIS hereby grants each user the following rights, but only so long as the user complies with all of the terms of these Agreed Terms of Use: – Except to the extent that we may have received additional authorization pursuant to a written agreement with CIS, each user may download, install and use each of the Products on a single computer; ”

“The Benefits of Membership” • #2. The right to distribute the benchmarks and tools within your organization. (User Members and Consulting Members only are entitled to this benefit)

Some problems with existing IS guidance • Requirements at various levels of abstraction that are – Structurally disconnected/fragmented • Some focus on principles; others on controls • Not readily scalable for different types and sizes of organizations • Developed and promoted by different professional communities vying for position – Different taxonomies and terminology • Detailed technical controls have been largely ignored

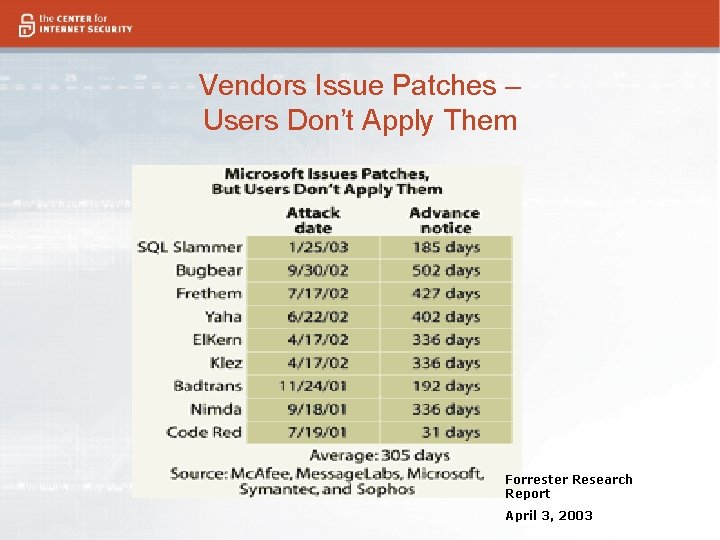
Vendors Issue Patches – Users Don’t Apply Them Forrester Research Report April 3, 2003

