TATA KELOLA SISTEM INFORMASI DAN KESEHATAN PERTEMUAN Ke








- Slides: 16

TATA KELOLA SISTEM INFORMASI DAN KESEHATAN PERTEMUAN Ke - 13 Manajemen Informasi Kesehatan Fakultas Ilmu Kesehatan

Learning Objectives • Define and use in context technical terms related to information technology architecture. • Distinguish between the hardware and software elements of an information system and provide illustrative examples. • Identify the elements of a computer network and give examples of various network structures. • Distinguish among operating systems, utility programs, and application software. • Introduce basic telecommunication concepts.

Computer Hardware • A computer is an electronic, digital device characterized by its ability to store a set of instructions, known as a program, and the data on which the instructions will operate.

Computer Software • Although for many people software is equated with applications, either general purpose or function specific, computer software also includes operating systems, utilities, programming languages, software development tools, and language translators. Software issues are important to healthcare managers at a number of levels. – First, although most healthcare organizations do little in-house development of software, the manager must be a knowledgeable participant in software acquisition. Managers must acknowledge that the quality of available software is variable, and in some cases software purchased at significant expense fails to meet expectations. Perhaps knowledgeable and informed managers participating in the evaluation, acquisition, and implementation of software will help ensure that installed systems meet their organizations’ needs.

Cont. – Second, allsoftwaremustbeappropriatelylicensed. Itiseasyforsomeone to copy software for personal use or to load a single-license program on multiple machines without any thought of impropriety. Policies should be in place emphasizing the organization’s strong stance on exclusive use of legally licensed software. – Third, managers should be aware of the rapid evolution of software versions. Operating systems and application software constantly being revised. Sometimes, users will campaign to upgrade a software package solely to have the most current version, even when the current version meets their needs. In other cases, the vendor might actually cease to support a given version, thereby forcing the user to upgrade. Again, knowledgeable participation by the manager is valuable in making upgrade decisions. – Finally, and perhaps most important in the current technology environment, the manager must understand the challenges created by the need for interfaces linking disparate software packages.

Networking and Telecommunications

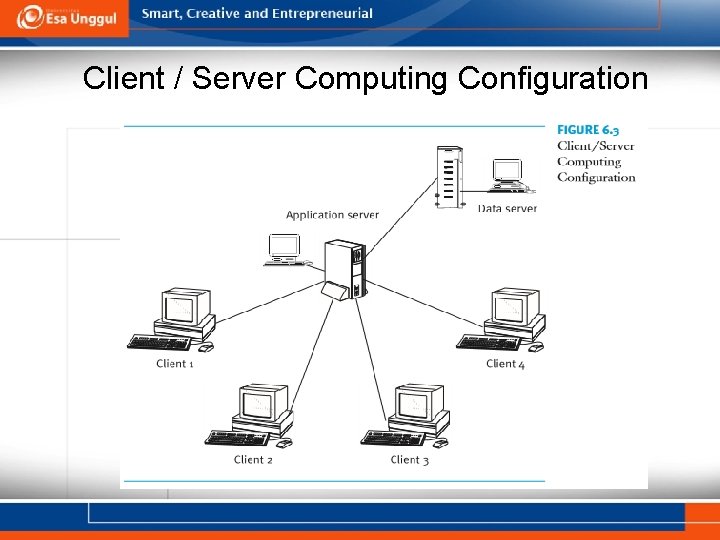
Client / Server Computing Configuration

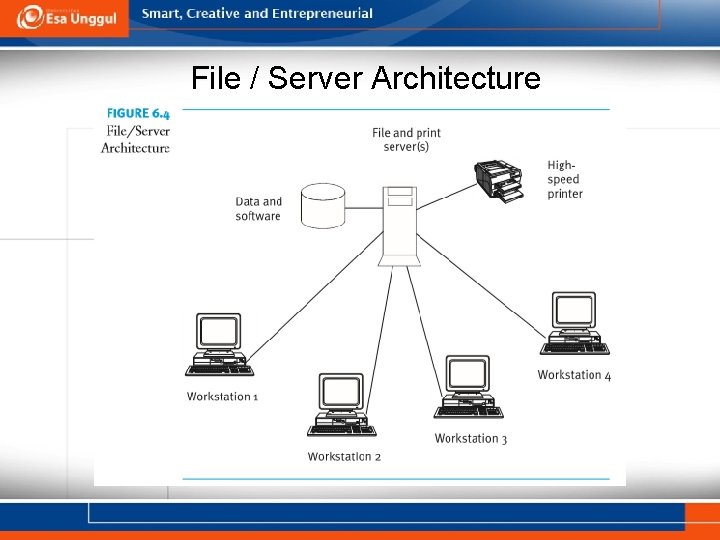
File / Server Architecture

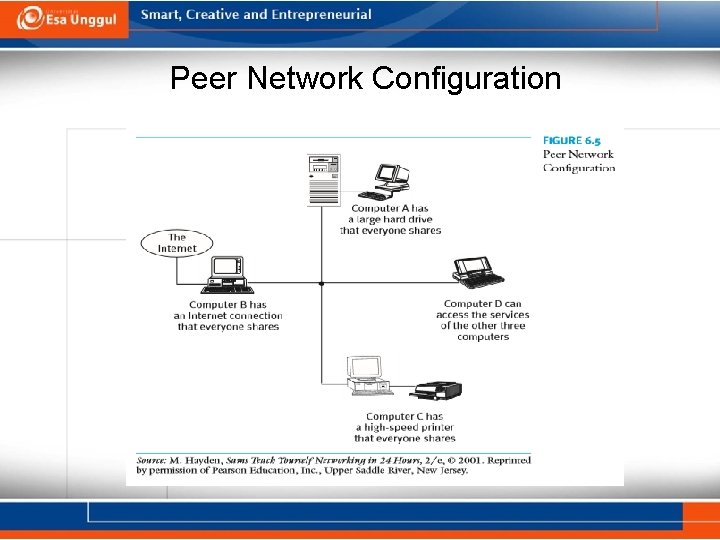
Peer Network Configuration

Network Components • Transmission Media – Wired Media – Fiber-Optic Media – Radio Media • Transmitters / Receivers – – Network Interface Cards Modems Multiplexers Bridges, Gateways and Routers • Network Controller / Servers A network controller is used in terminal-host networks consisting of a number of terminals connected to one or more mainframe host computers. The function of this controller, which can be a minicomputer or microcomputer, is to “direct” the communications traffic between the host and the terminals and peripheral devices.

Network Control Software / Network Operating Systems

Network Topologies • • • Bus Networks Ring Networks Star Networks Hybrid Networks Asynchronous Transfer Mode

Wireless Topologies • Spread Spectrum • Infrared Technology • Cellular Digital Packet Data

Communicating via Internet • Dial – up Services • Direct Network Connections

The Role of an Intranet Once the Internet infrastructure is in place, the same technology can also support communication within the organization; this structure is referred to as an intranet, or private network. When an organization shares part of its intranet with customers, strategic partners, and other stakeholders, the intranet becomes an extranet. An intranet or extranet uses the same protocols as the Internet and in general looks no different. A firewall is a security protocol to protect the intranet from outside access while permitting organizational access to the Internet. The firewall can also contain software that establishes a virtual private network that allows organizations to maintain privacy while sharing public networks for transmission of their data. Data are encrypted before they are sent through the public network and then decrypted at the receiving end. This methodology makes customers feel more comfortable about providing personal information, such as a credit card number, “online. ” Transmission of sensitive patient information can use this same protocol. As developments in intranet applications continue, healthcare managers should monitor how their organizations are using this technology. Special attention should be directed toward the security and confidentiality issues created by intranets. Chapter 5 addresses security and confidentiality.

Summary The trend toward the creation of integrated health systems and other industry environmental changes has made the information needs of healthcare organizations increasingly complex. Among the strategies necessary to respond to these changes are the development of interoperable computer networks and the use of telecommunications. These technologies are necessary for EDI between and among organizations. Networks also can be classified according to the manner in which the processing function is distributed among the devices comprising the network: (1) terminal-host systems, (2) a client/server network, (3) a file/server configuration, and (4) a peer network. Each alternative has its own strengths and weaknesses, and the appropriate configuration is dependent on the organization’s strategic direction.
 Definisi tata kelola perusahaan
Definisi tata kelola perusahaan Good clinical governance
Good clinical governance Tata kelola tik
Tata kelola tik Jardiknas adalah
Jardiknas adalah Tata kelola tik
Tata kelola tik Yang termasuk dalam prinsip humas pemerintah adalah
Yang termasuk dalam prinsip humas pemerintah adalah Definisi tata kelola perusahaan
Definisi tata kelola perusahaan Gambaran umum sistem
Gambaran umum sistem Sistem informasi sdm kesehatan
Sistem informasi sdm kesehatan Contoh aplikasi sik
Contoh aplikasi sik Pengelompokan data dasar menurut blum
Pengelompokan data dasar menurut blum Kebijakan sistem informasi kesehatan
Kebijakan sistem informasi kesehatan Kebijakan sistem informasi kesehatan
Kebijakan sistem informasi kesehatan Sistem informasi sumber daya informasi
Sistem informasi sumber daya informasi Pengertian asisten tenaga kesehatan
Pengertian asisten tenaga kesehatan Pengertian diagram batang daun
Pengertian diagram batang daun Sel adalah pertemuan antara titik-titik dan titik-titik
Sel adalah pertemuan antara titik-titik dan titik-titik































