Tasks and Task Management Timecritical tasks Contending tasks



- Slides: 41

Tasks and Task Management : --Time-critical tasks --Contending tasks --Communicating tasks

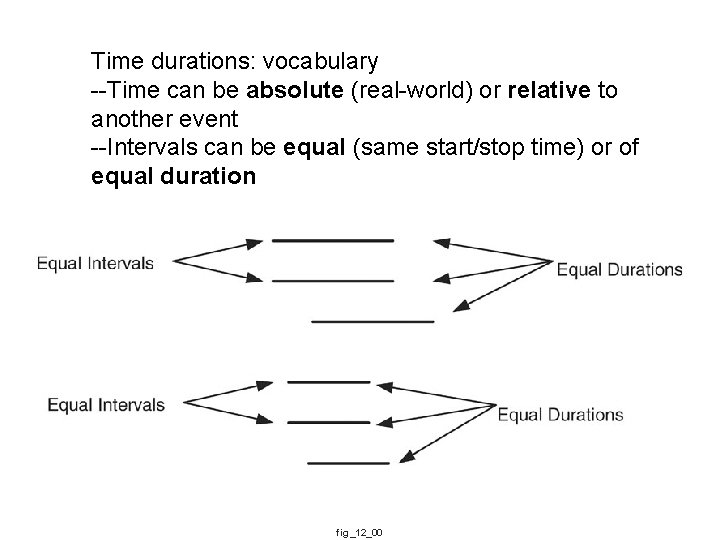
Time durations: vocabulary --Time can be absolute (real-world) or relative to another event --Intervals can be equal (same start/stop time) or of equal duration fig_12_00

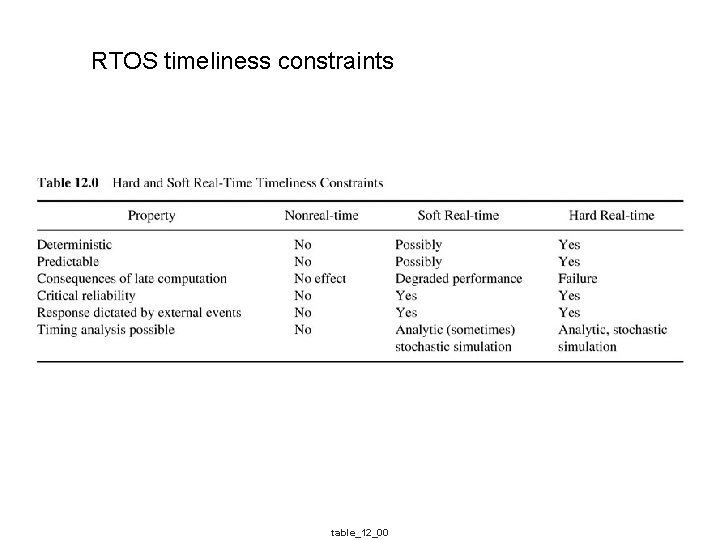
RTOS timeliness constraints table_12_00

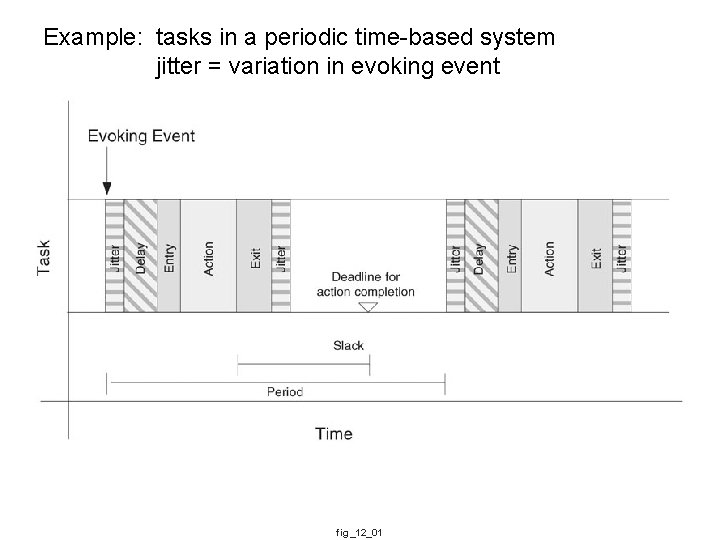
Example: tasks in a periodic time-based system jitter = variation in evoking event fig_12_01

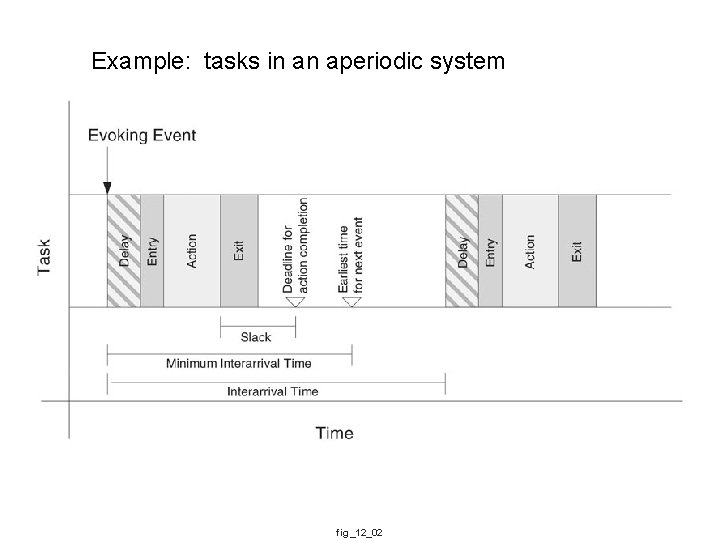
Example: tasks in an aperiodic system fig_12_02

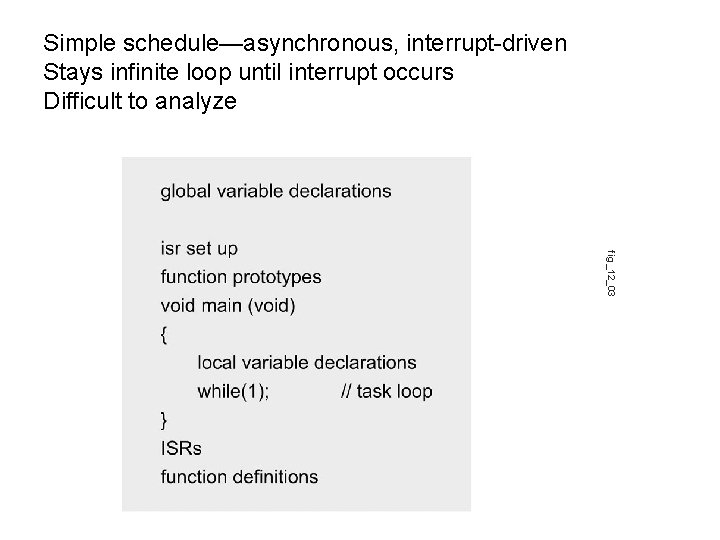
Simple schedule—asynchronous, interrupt-driven Stays infinite loop until interrupt occurs Difficult to analyze fig_12_03

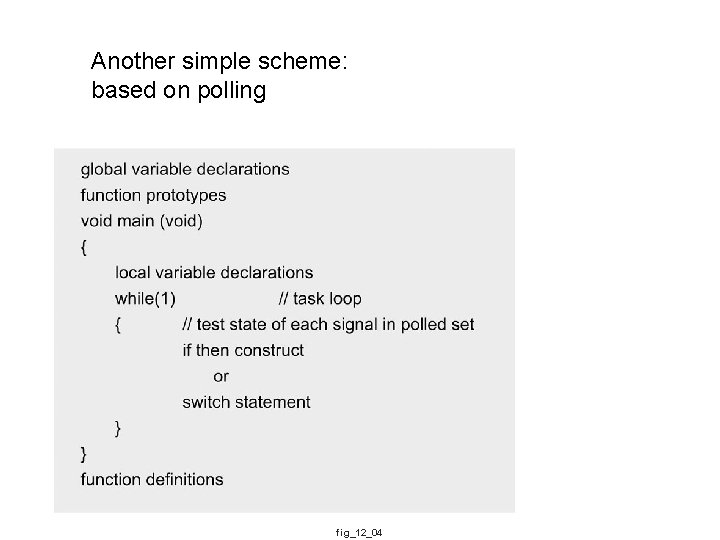
Another simple scheme: based on polling fig_12_04

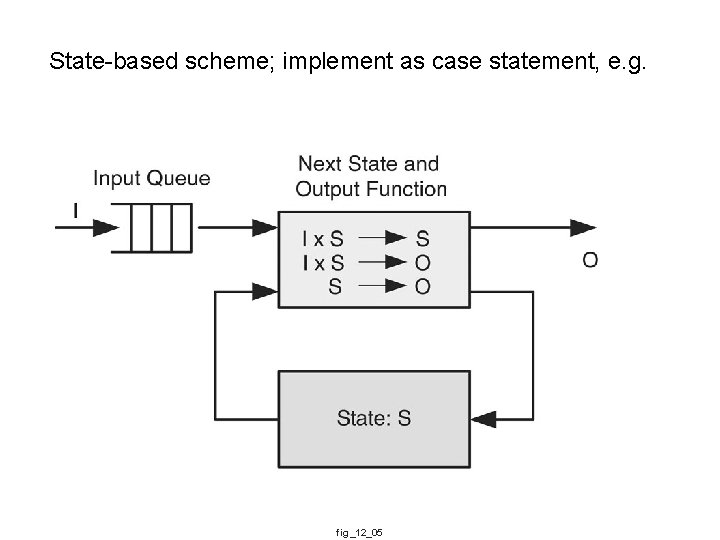
State-based scheme; implement as case statement, e. g. fig_12_05

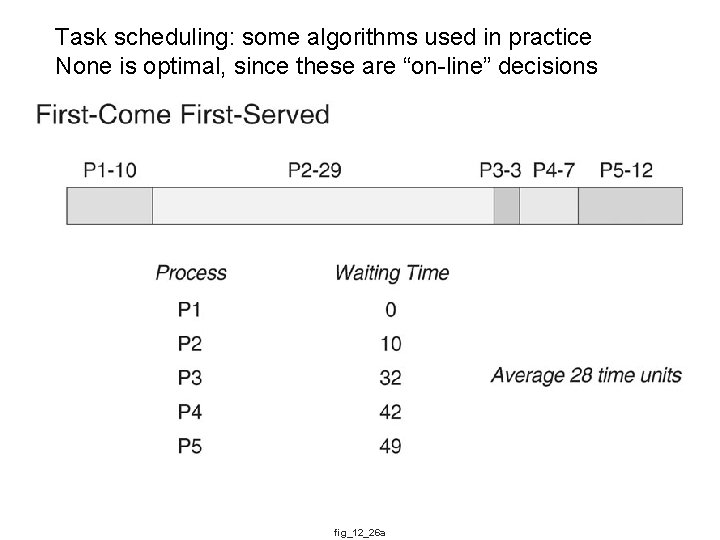
Task scheduling: some algorithms used in practice None is optimal, since these are “on-line” decisions fig_12_26 a

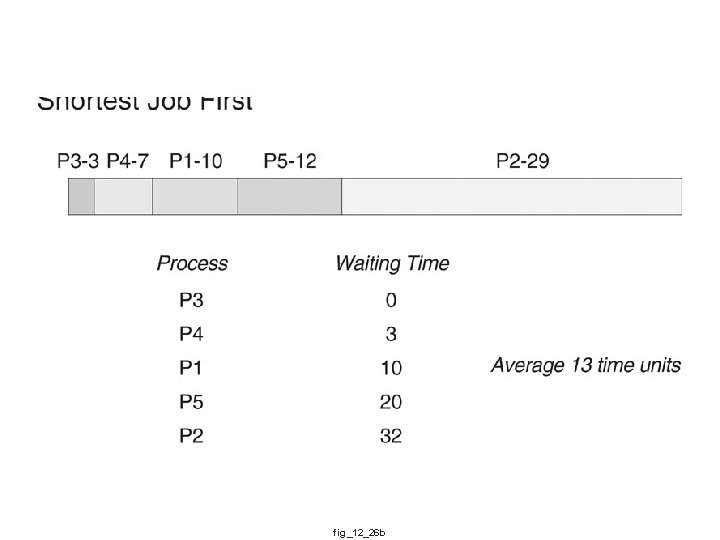
fig_12_26 b

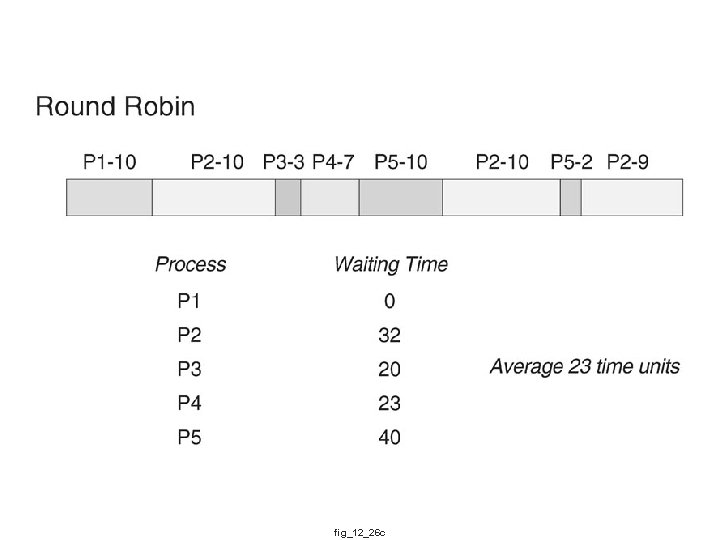
fig_12_26 c

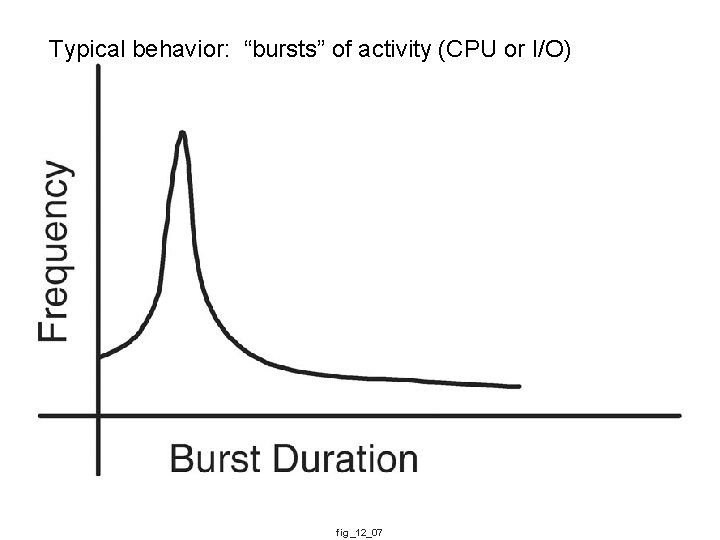
Typical behavior: “bursts” of activity (CPU or I/O) fig_12_07

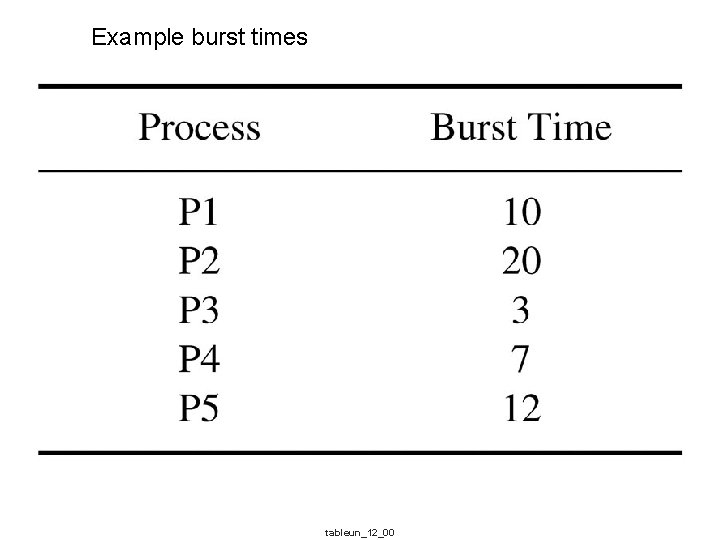
Example burst times tableun_12_00

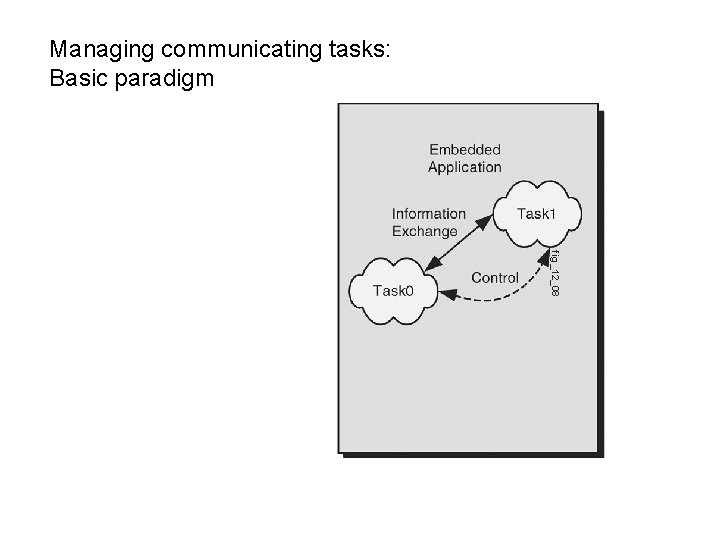
Managing communicating tasks: Basic paradigm fig_12_08

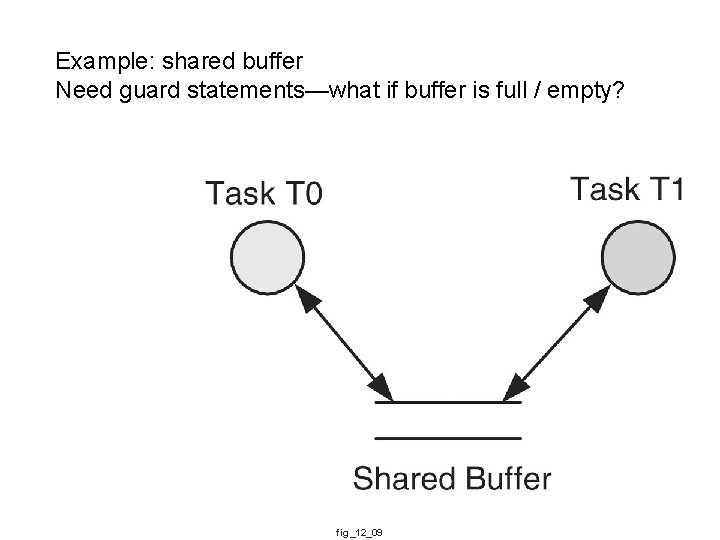
Example: shared buffer Need guard statements—what if buffer is full / empty? fig_12_09

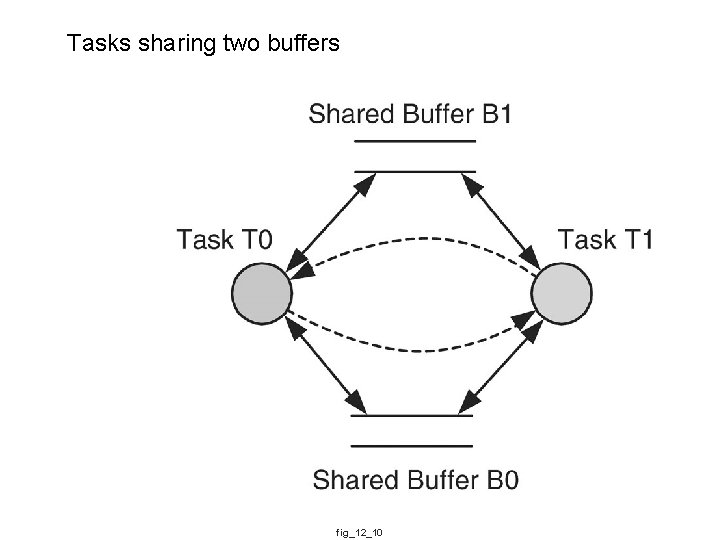
Tasks sharing two buffers fig_12_10

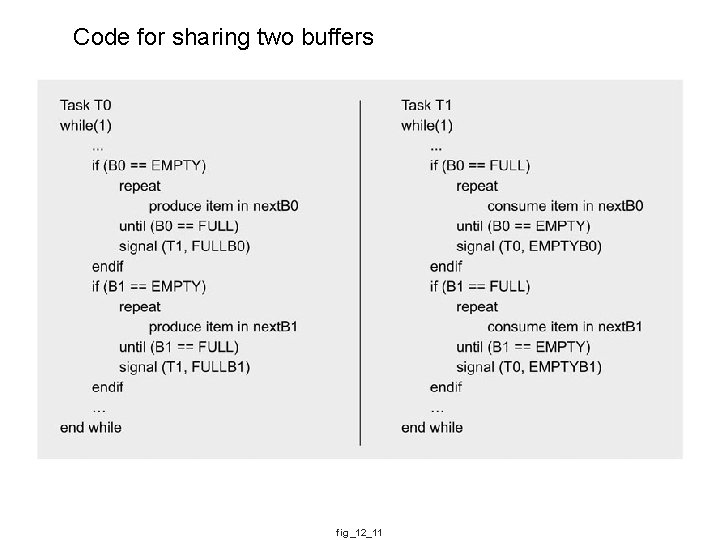
Code for sharing two buffers fig_12_11

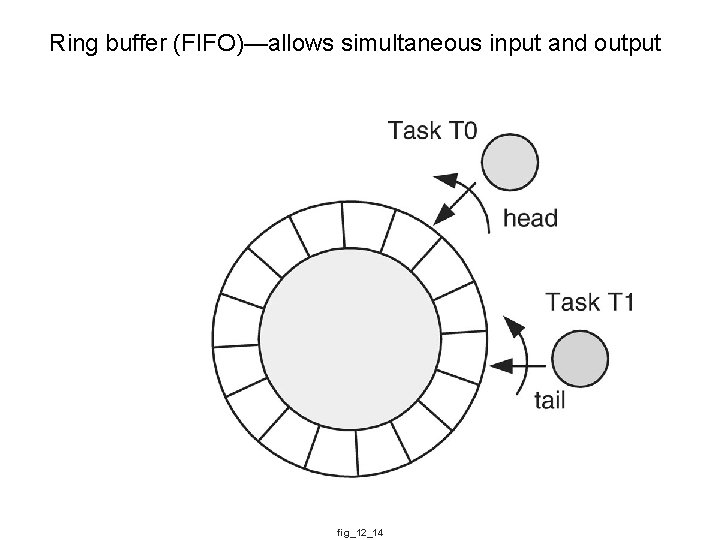
Ring buffer (FIFO)—allows simultaneous input and output fig_12_14

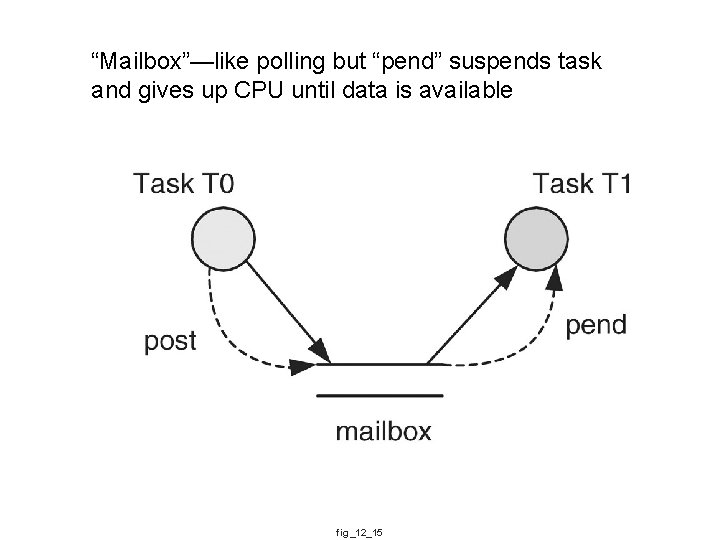
“Mailbox”—like polling but “pend” suspends task and gives up CPU until data is available fig_12_15

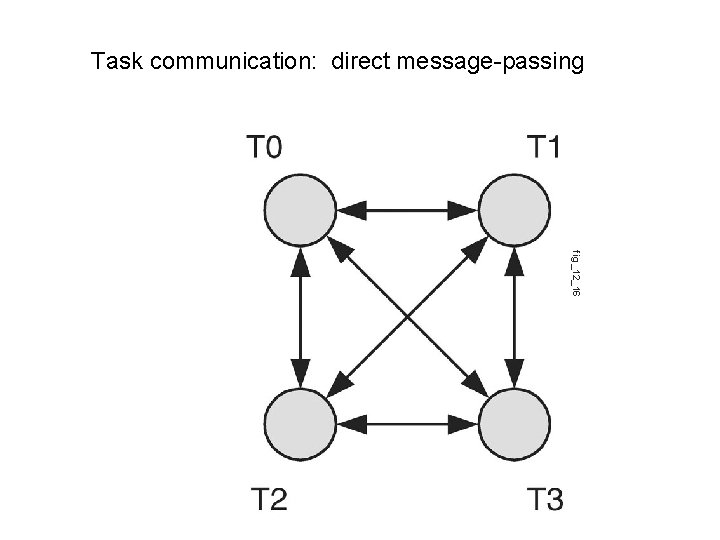
Task communication: direct message-passing fig_12_16

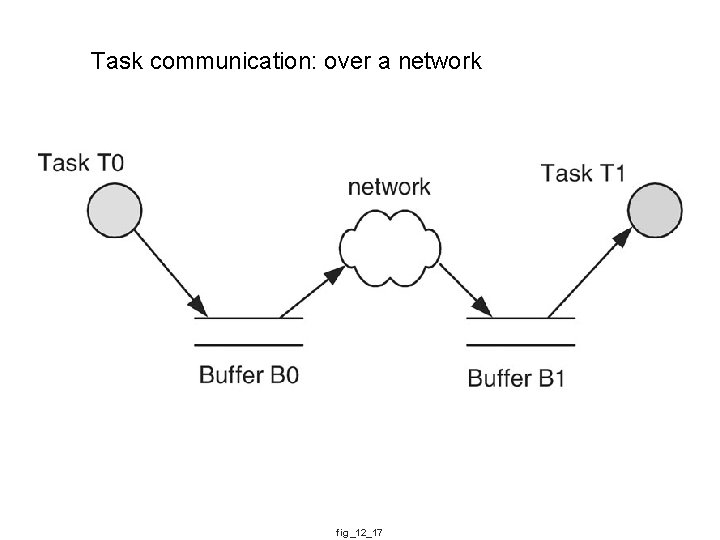
Task communication: over a network fig_12_17

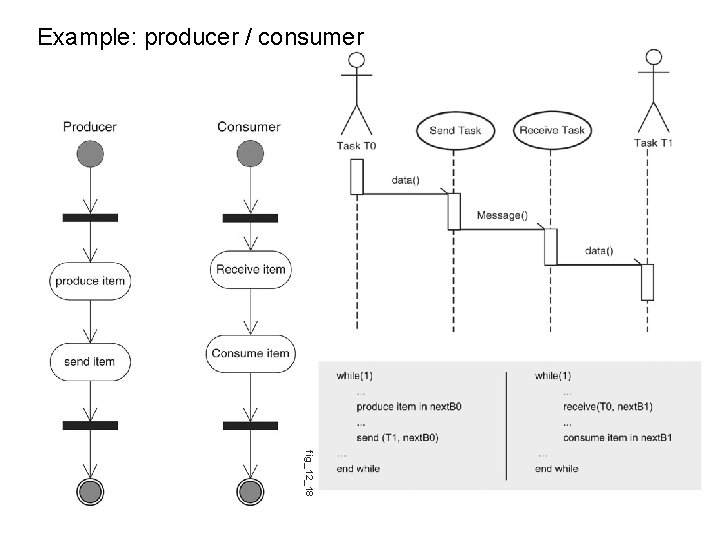
Example: producer / consumer fig_12_18

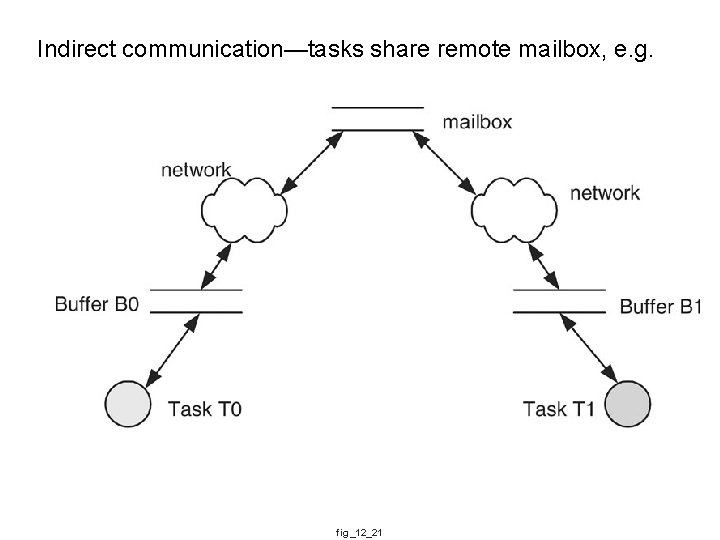
Indirect communication—tasks share remote mailbox, e. g. fig_12_21

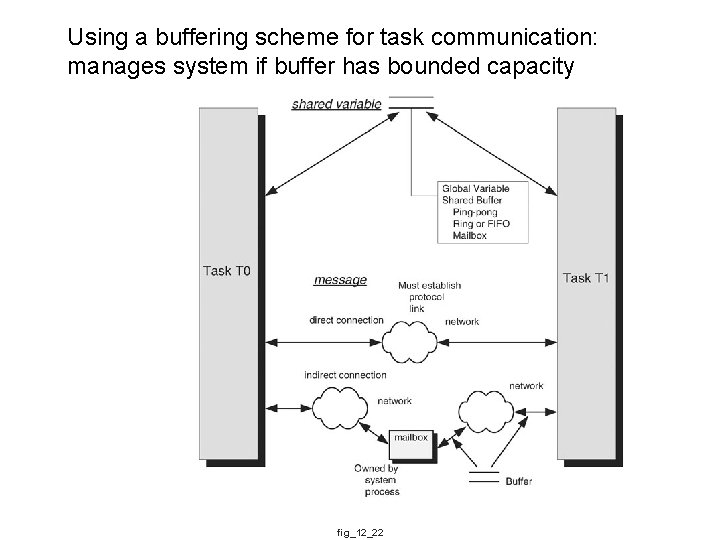
Using a buffering scheme for task communication: manages system if buffer has bounded capacity fig_12_22

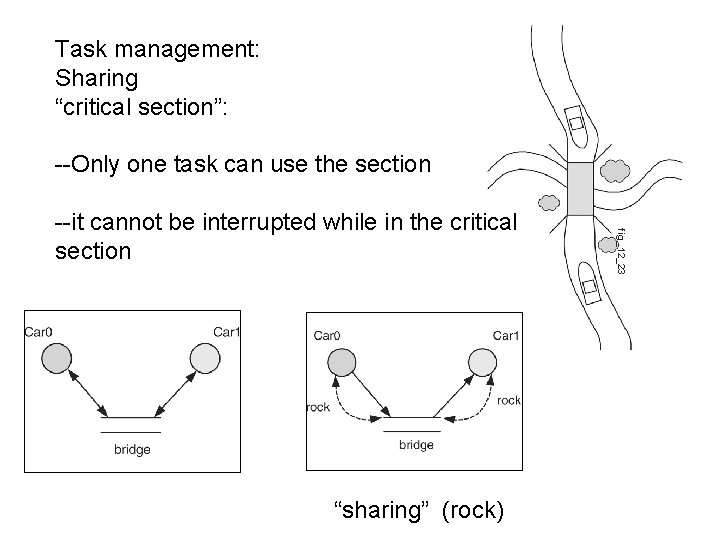
Task management: Sharing “critical section”: --Only one task can use the section “sharing” (rock) fig_12_23 --it cannot be interrupted while in the critical section

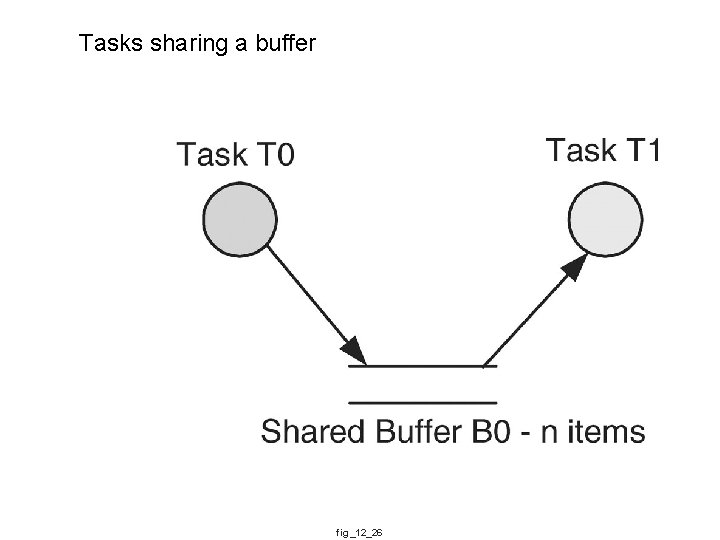
Tasks sharing a buffer fig_12_26

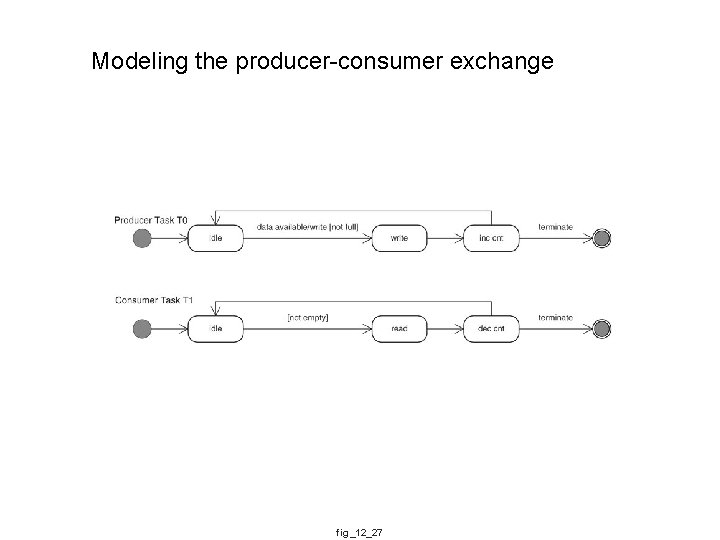
Modeling the producer-consumer exchange fig_12_27

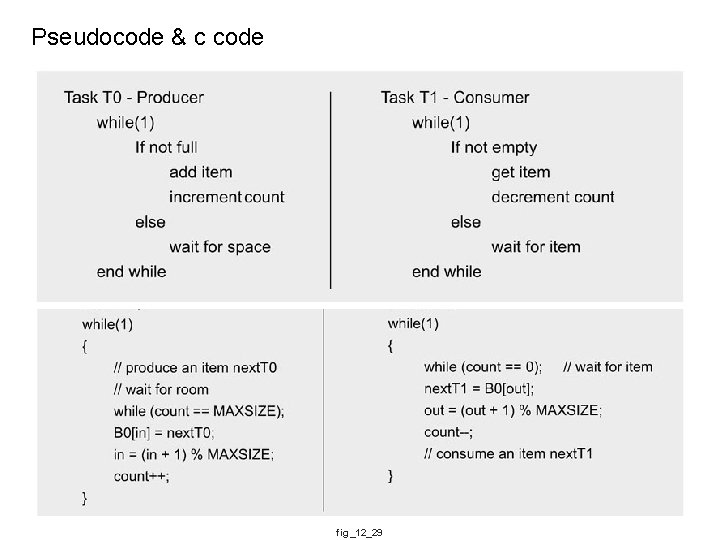
Pseudocode & c code fig_12_29

Critical section management: requirements: 1. Mutual exclusion 2. No deadlock 3. Must be progress through critical section 4. Must have bounded waiting

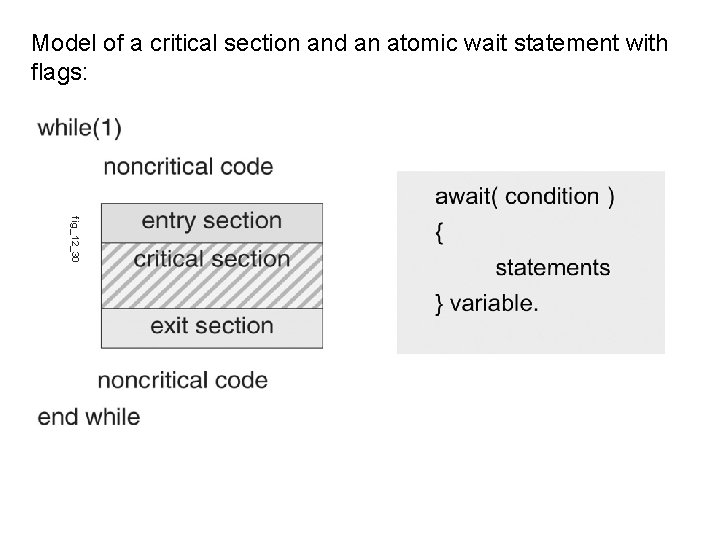
Model of a critical section and an atomic wait statement with flags: fig_12_30

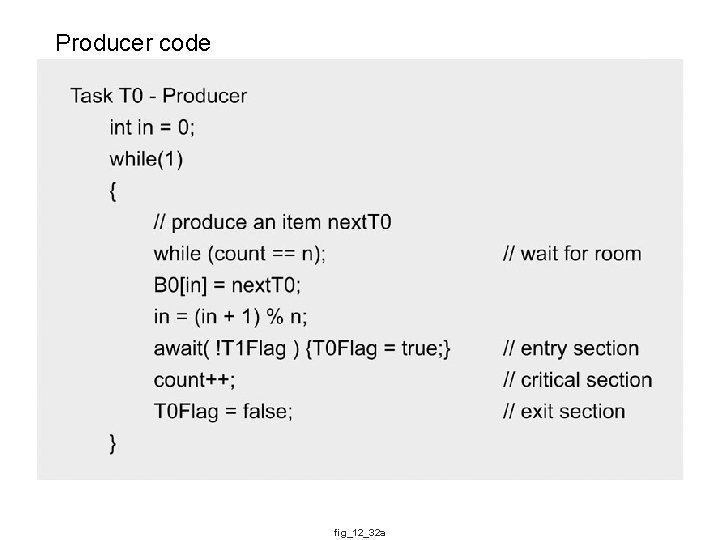
Producer code fig_12_32 a

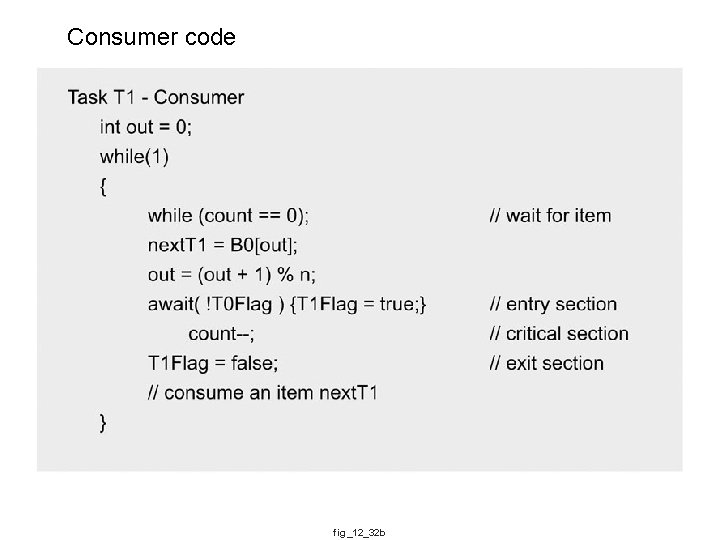
Consumer code fig_12_32 b

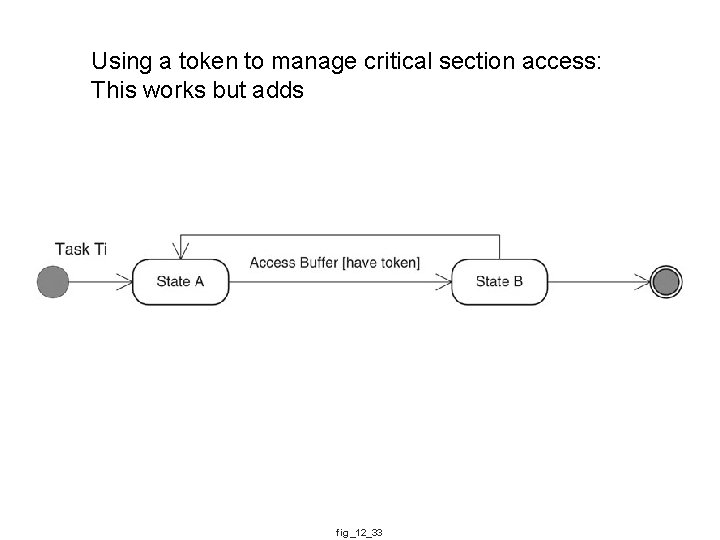
Using a token to manage critical section access: This works but adds fig_12_33

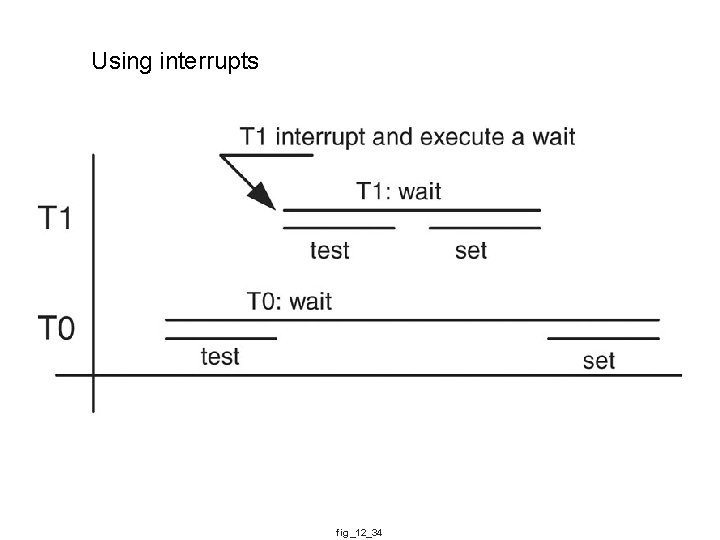
Using interrupts fig_12_34

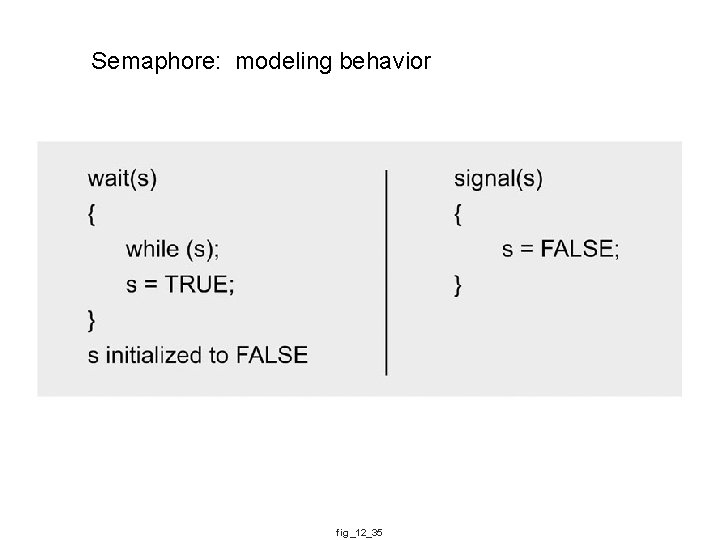
Semaphore: modeling behavior fig_12_35

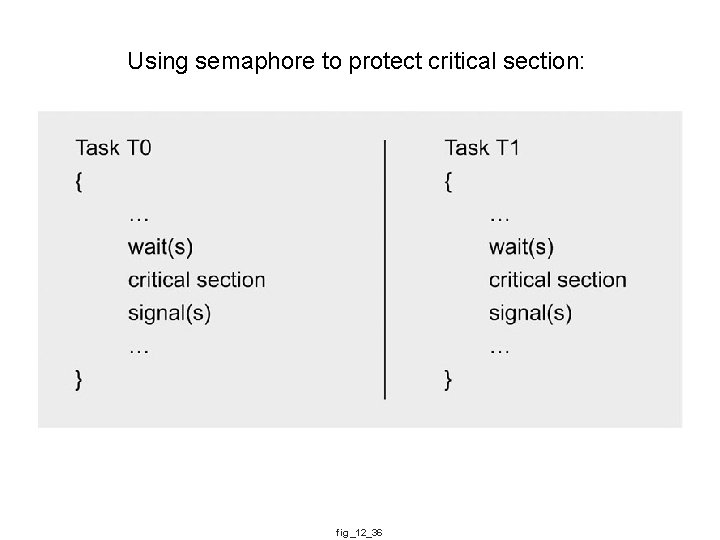
Using semaphore to protect critical section: fig_12_36

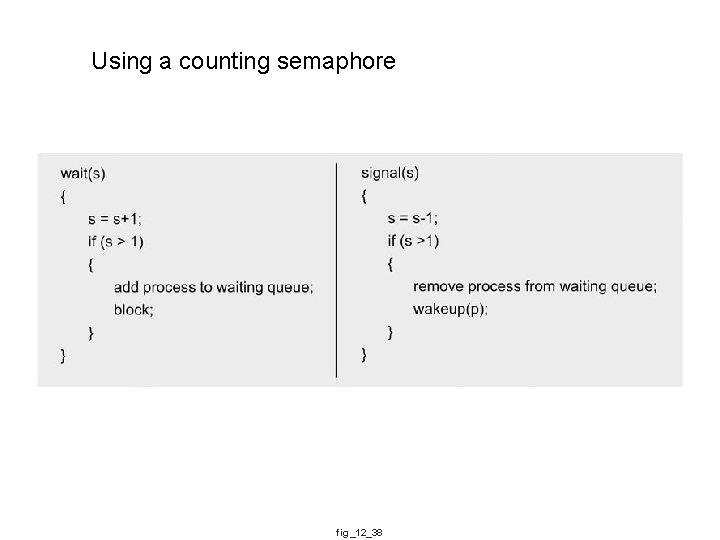
Using a counting semaphore fig_12_38

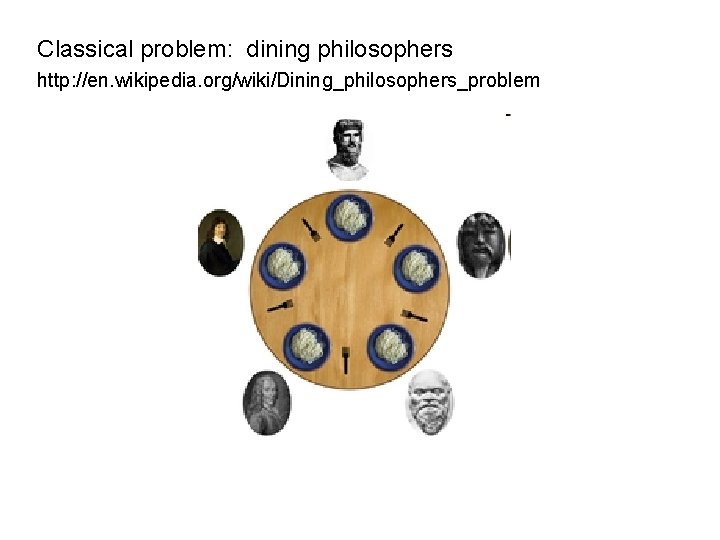
Classical problem: dining philosophers http: //en. wikipedia. org/wiki/Dining_philosophers_problem

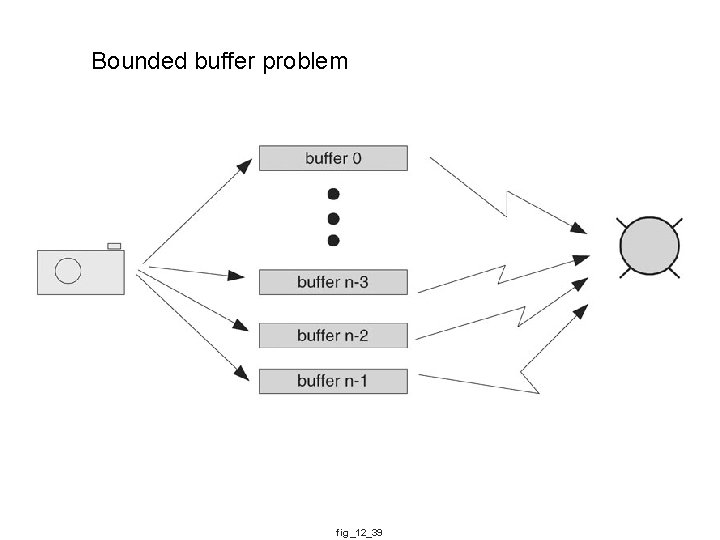
Bounded buffer problem fig_12_39

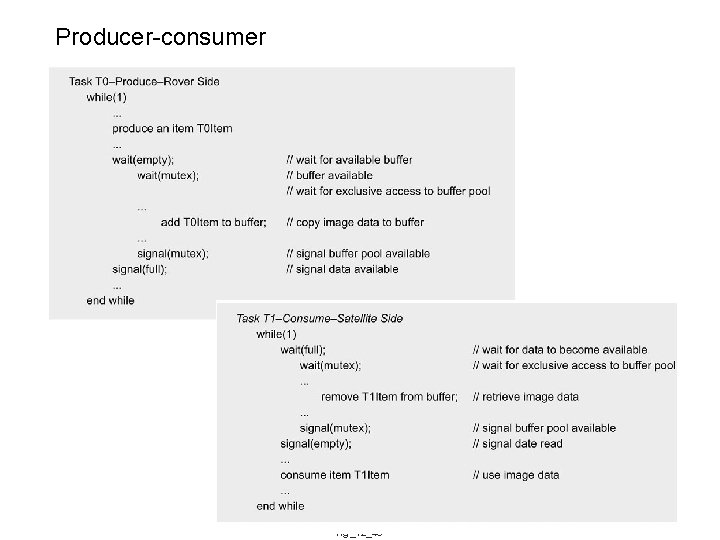
Producer-consumer fig_12_40

reader-writer fig_12_42