Tarzan A PeertoPeer Anonymizing Network Layer Michael J










- Slides: 42

Tarzan: A Peer-to-Peer Anonymizing Network Layer Michael J. Freedman, NYU Robert Morris, MIT ACM CCS 2002 http: //pdos. lcs. mit. edu/tarzan/ November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer

The Grail of Anonymization • Participant can communicate anonymously with non-participant User ? • User can talk to CNN. com • Nobody knows who user is November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 2

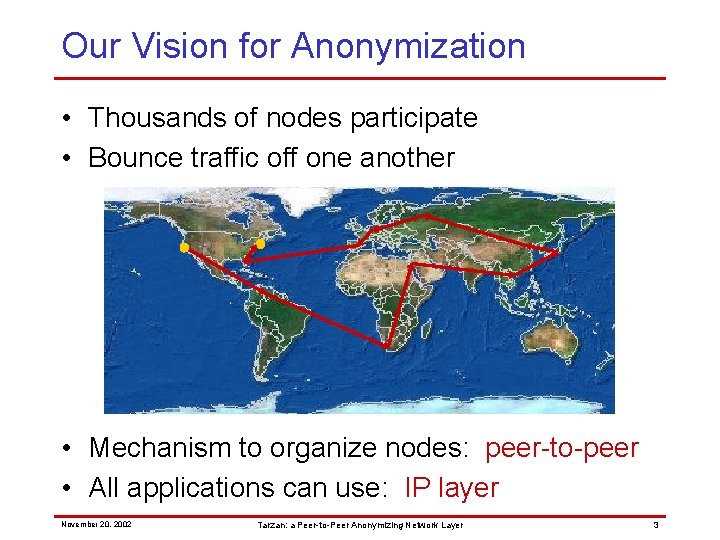
Our Vision for Anonymization • Thousands of nodes participate • Bounce traffic off one another • Mechanism to organize nodes: peer-to-peer • All applications can use: IP layer November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 3

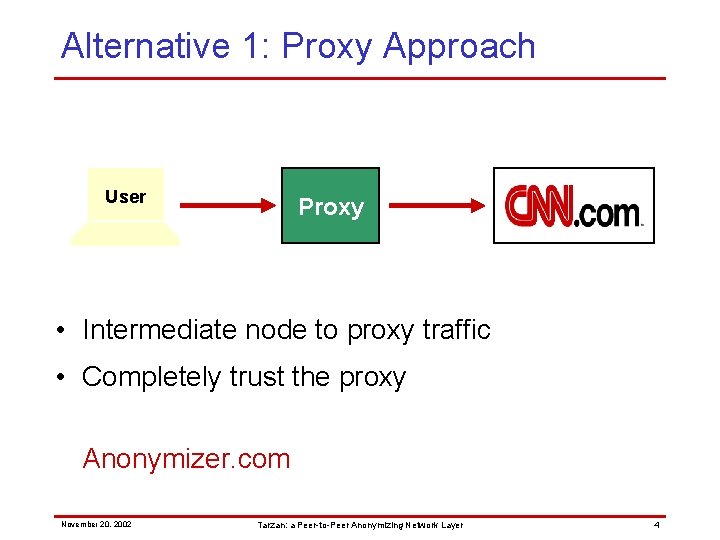
Alternative 1: Proxy Approach User Proxy • Intermediate node to proxy traffic • Completely trust the proxy Anonymizer. com November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 4

Threat model • Corrupt proxy(s) – Adversary runs proxy(s) – Adversary targets proxy(s) and compromises, possibly adaptively • Network links observed – Limited, localized network sniffing – Wide-spread (even global) eavesdropping e. g. , Carnivore, Chinese firewall, ISP search warrants November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 5

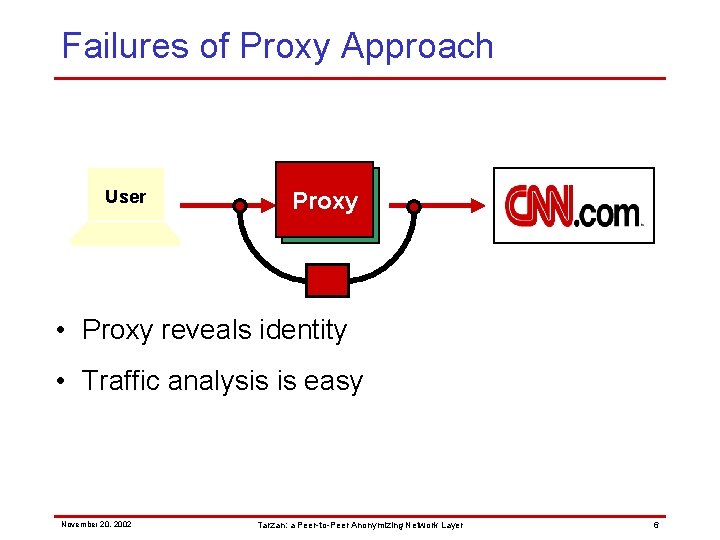
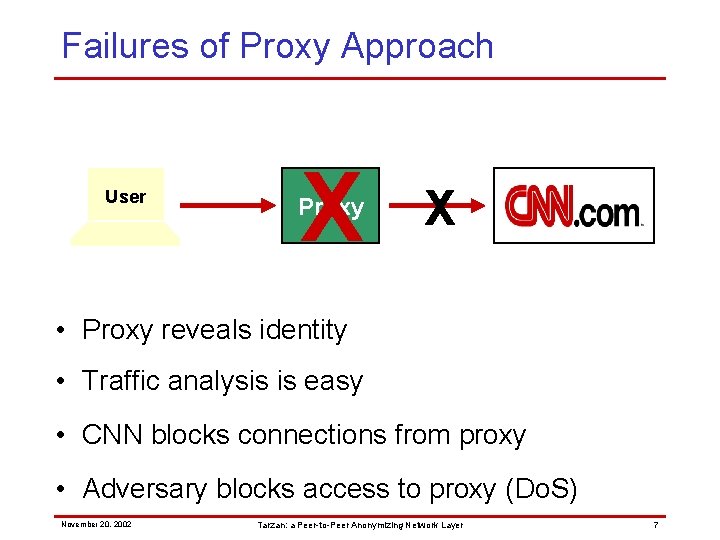
Failures of Proxy Approach User Proxy • Proxy reveals identity • Traffic analysis is easy November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 6

Failures of Proxy Approach User X Proxy X • Proxy reveals identity • Traffic analysis is easy • CNN blocks connections from proxy • Adversary blocks access to proxy (Do. S) November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 7

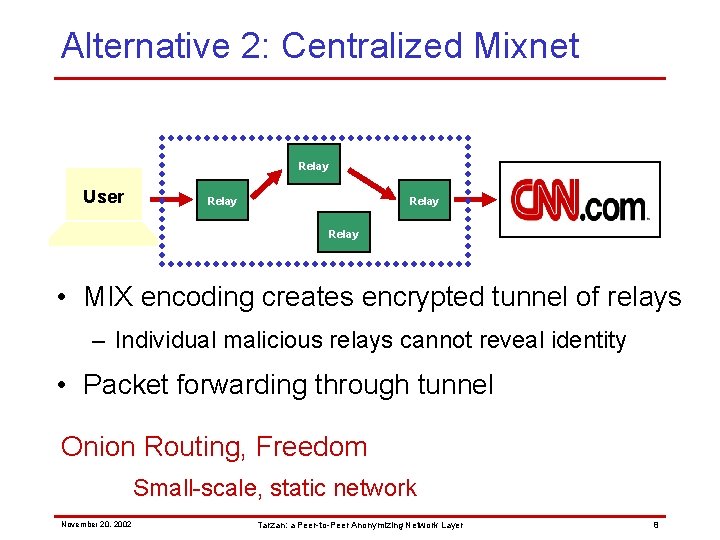
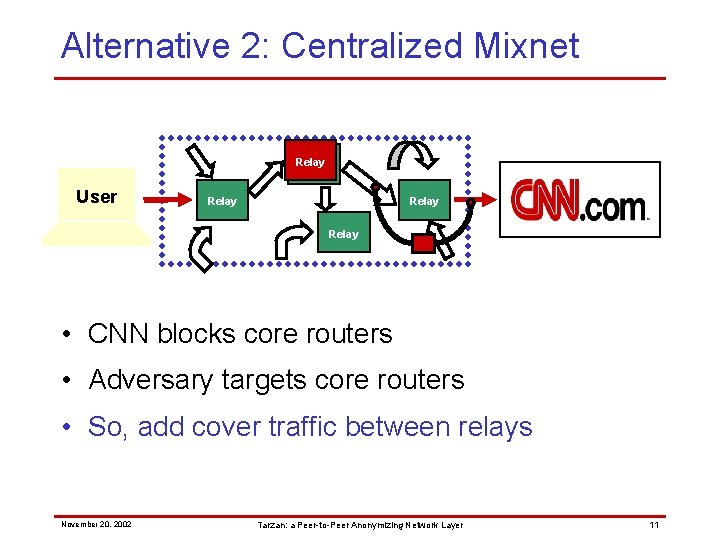
Alternative 2: Centralized Mixnet Relay User Relay • MIX encoding creates encrypted tunnel of relays – Individual malicious relays cannot reveal identity • Packet forwarding through tunnel Onion Routing, Freedom Small-scale, static network November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 8

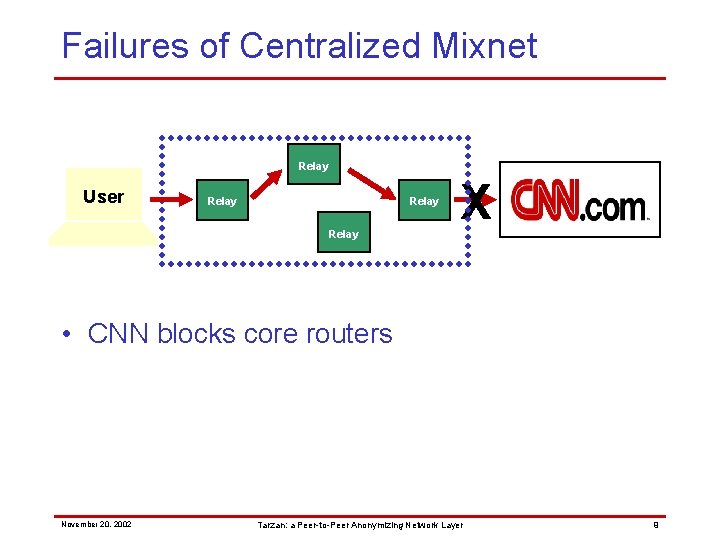
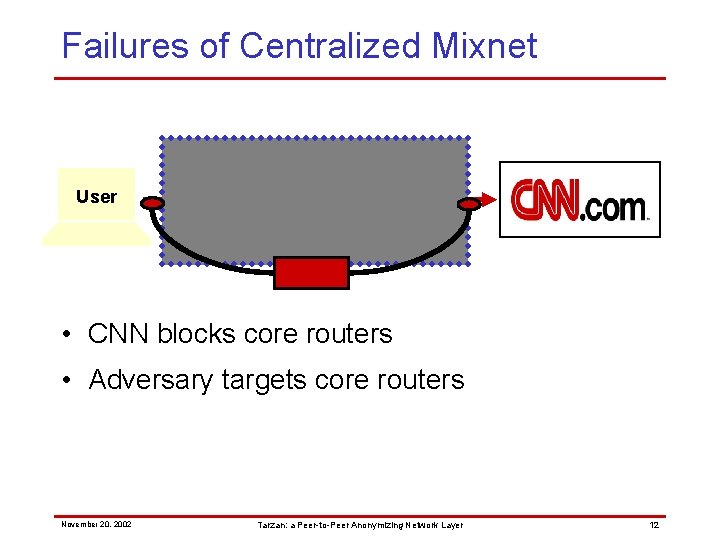
Failures of Centralized Mixnet Relay User Relay X • CNN blocks core routers November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 9

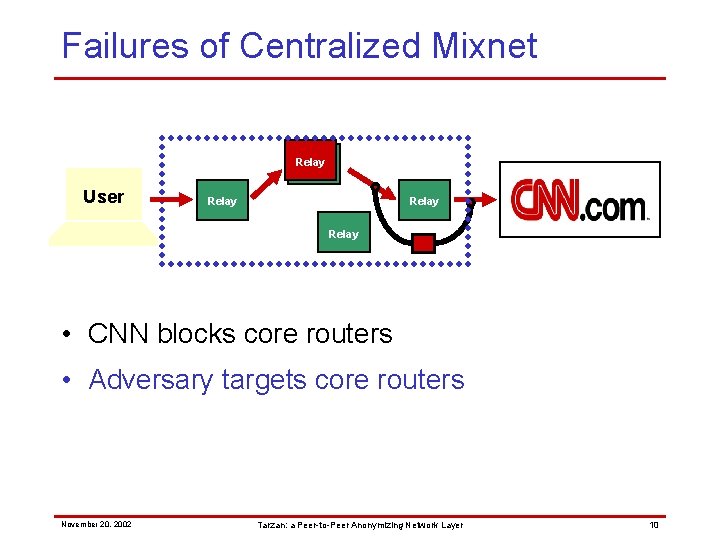
Failures of Centralized Mixnet Relay User Relay • CNN blocks core routers • Adversary targets core routers November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 10

Alternative 2: Centralized Mixnet Relay User Relay • CNN blocks core routers • Adversary targets core routers • So, add cover traffic between relays – Hides data traffic among cover November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 11

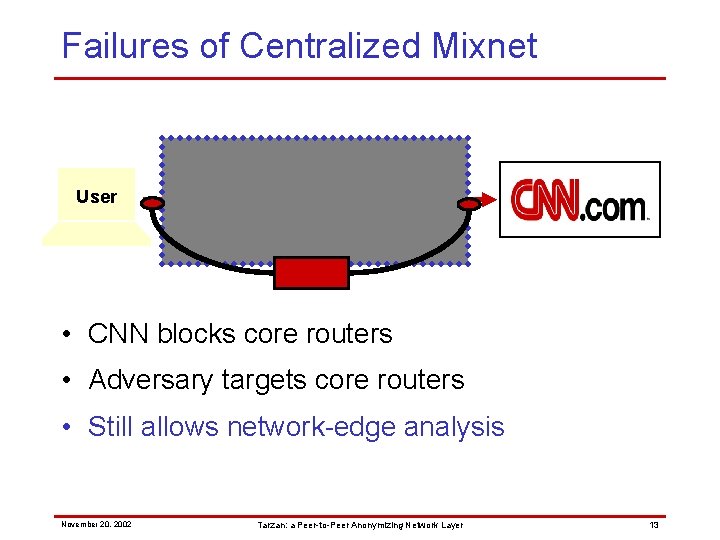
Failures of Centralized Mixnet Relay User Relay • CNN blocks core routers • Adversary targets core routers November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 12

Failures of Centralized Mixnet Relay User Relay Relay • CNN blocks core routers • Adversary targets core routers • Still allows network-edge analysis November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 13

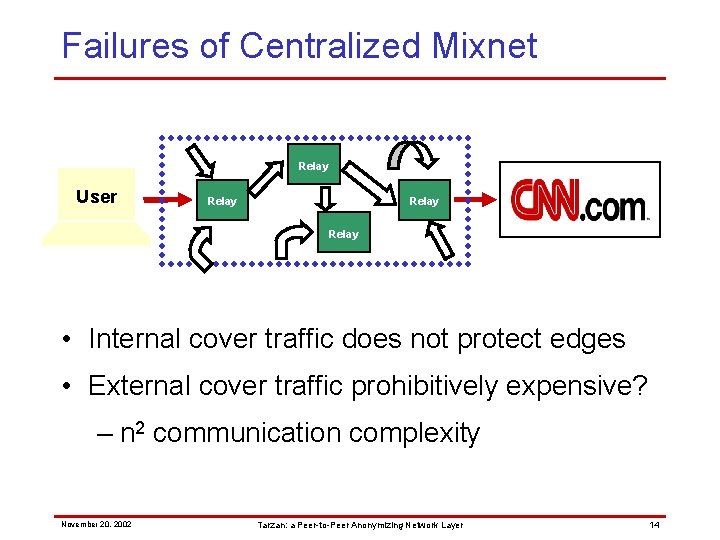
Failures of Centralized Mixnet Relay User Relay • Internal cover traffic does not protect edges • External cover traffic prohibitively expensive? – n 2 communication complexity November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 14

Tarzan goals • No distinction between anon proxies and clients – • • • Peer-to-peer model Anonymity against corrupt relays – MIX-net encoding – Robust tunnel selection – Prevent adversary spoofing or running many nodes Anonymity against global eavesdropping – Cover traffic protects all edges – Restrict topology to make cover practical – Choose neighbors in verifiably-random manner Application-independence – November 20, 2002 Low-latency IP-layer redirection Tarzan: a Peer-to-Peer Anonymizing Network Layer 15

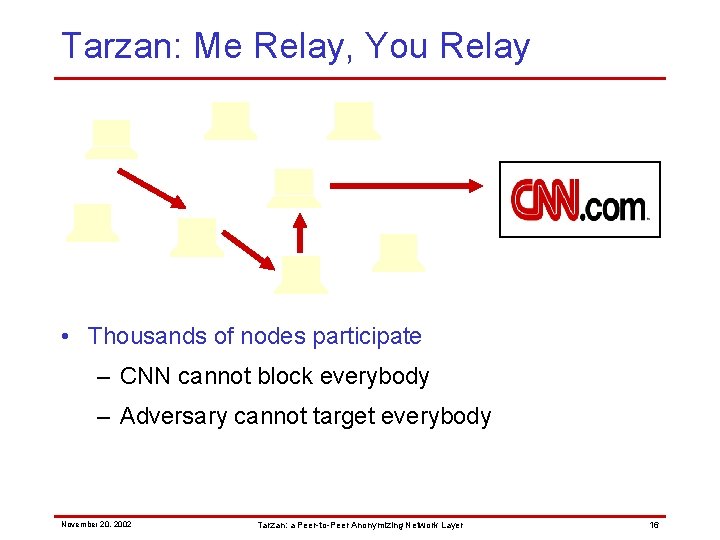
Tarzan: Me Relay, You Relay • Thousands of nodes participate – CNN cannot block everybody – Adversary cannot target everybody November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 16

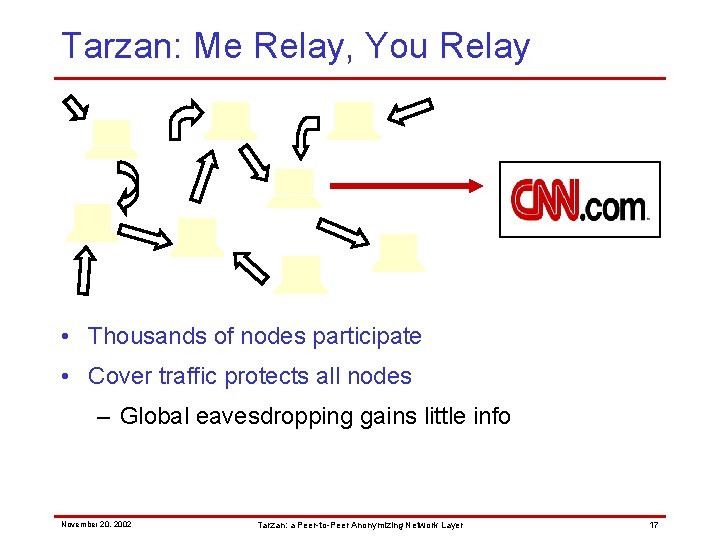
Tarzan: Me Relay, You Relay • Thousands of nodes participate • Cover traffic protects all nodes – Global eavesdropping gains little info November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 17

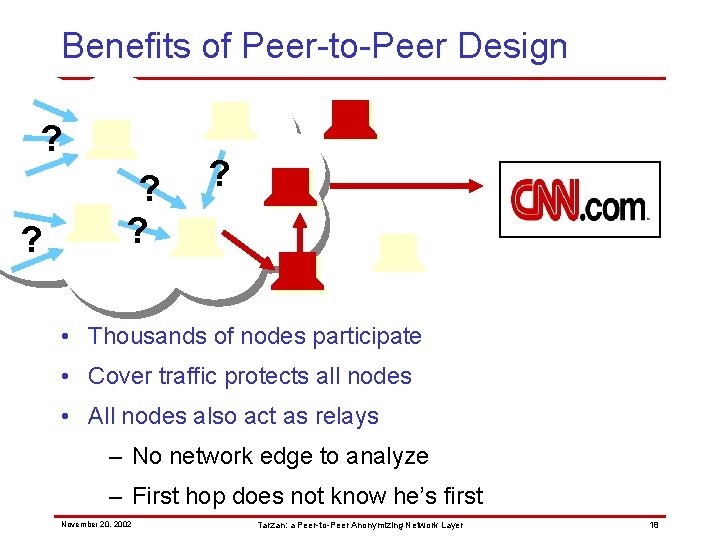
Benefits of Peer-to-Peer Design ? ? ? • Thousands of nodes participate • Cover traffic protects all nodes • All nodes also act as relays – No network edge to analyze – First hop does not know he’s first November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 18

Tarzan goals • No distinction between anon proxies and clients – • • • Peer-to-peer model Anonymity against corrupt relays – MIX-net encoding – Robust tunnel selection – Prevent adversary spoofing or running many nodes Anonymity against global eavesdropping – Cover traffic protects all nodes – Restrict topology to make cover practical – Choose neighbors in verifiably-random manner Application-independence – November 20, 2002 Low-latency IP-layer redirection Tarzan: a Peer-to-Peer Anonymizing Network Layer 19

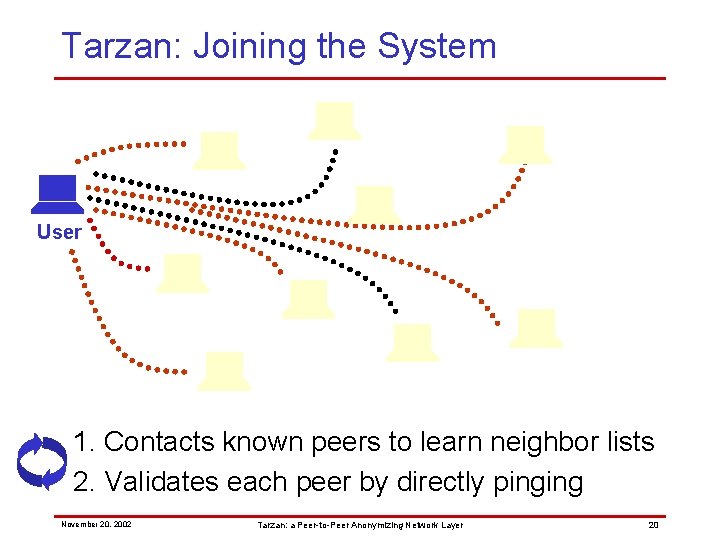
Tarzan: Joining the System User 1. Contacts known peers to learn neighbor lists 2. Validates each peer by directly pinging November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 20

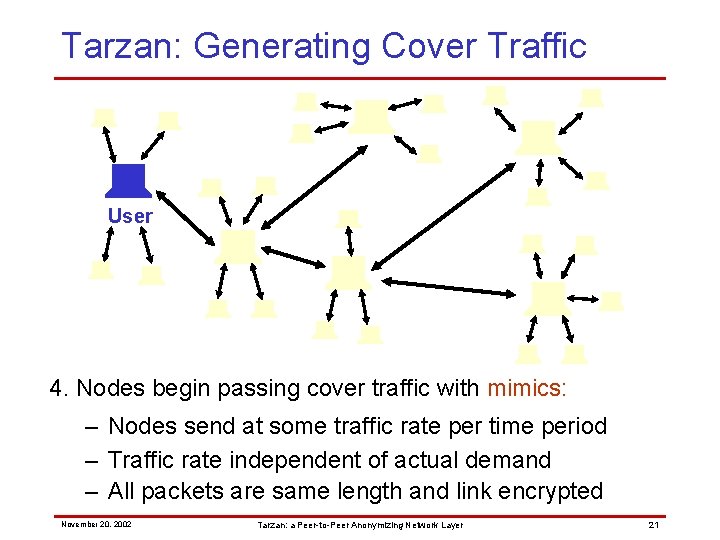
Tarzan: Generating Cover Traffic User 4. Nodes begin passing cover traffic with mimics: – Nodes send at some traffic rate per time period – Traffic rate independent of actual demand – All packets are same length and link encrypted November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 21

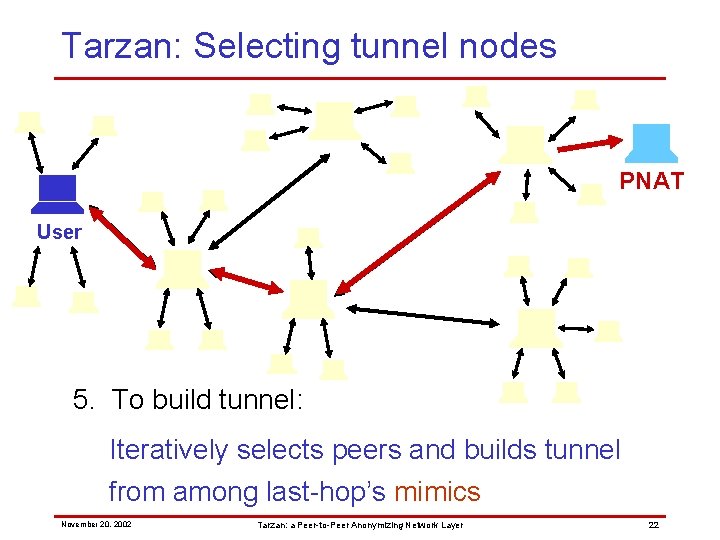
Tarzan: Selecting tunnel nodes PNAT User 5. To build tunnel: Iteratively selects peers and builds tunnel from among last-hop’s mimics November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 22

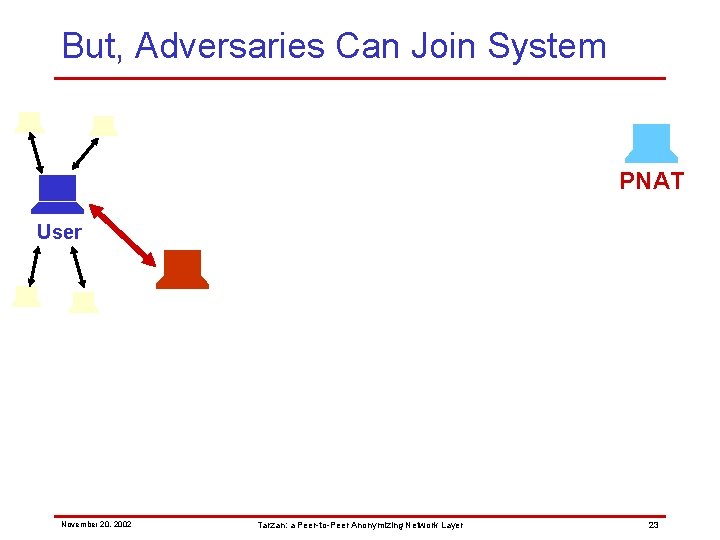
But, Adversaries Can Join System PNAT User November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 23

But, Adversaries Can Join System PNAT User • Adversary can join more than once by spoofing addresses outside its control ü Contact peers directly to validate IP addr and learn PK November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 24

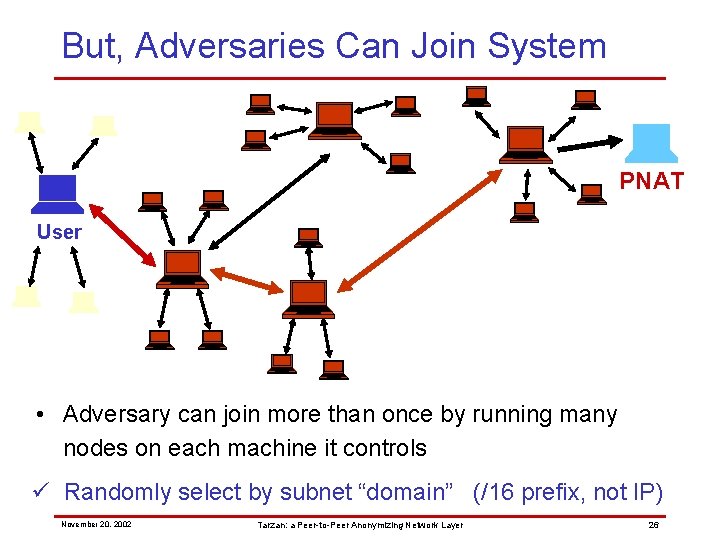
But, Adversaries Can Join System PNAT User • Adversary can join more than once by running many nodes on each machine it controls ü Randomly select by subnet “domain” (/16 prefix, not IP) November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 25

But, Adversaries Can Join System PNAT User • Adversary can join more than once by running many nodes on each machine it controls ü Randomly select by subnet “domain” (/16 prefix, not IP) November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 26

But, Adversaries Can Join System PNAT User • Colluding adversary can only select each other as neighbors ü Choose mimics in universally-verifiable random manner November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 27

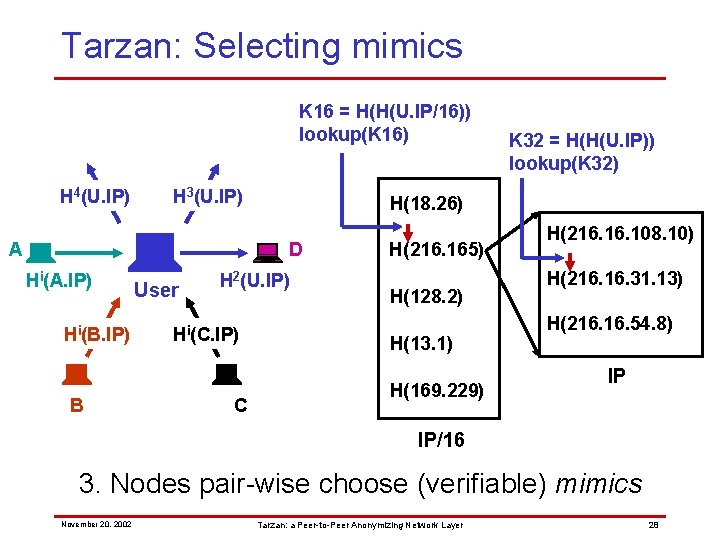
Tarzan: Selecting mimics K 16 = H(H(U. IP/16)) lookup(K 16) H 4(U. IP) H 3(U. IP) A H(18. 26) D Hi(A. IP) Hi(B. IP) B User H 2(U. IP) Hi(C. IP) C K 32 = H(H(U. IP)) lookup(K 32) H(216. 165) H(128. 2) H(13. 1) H(169. 229) H(216. 108. 10) H(216. 31. 13) H(216. 54. 8) IP IP/16 3. Nodes pair-wise choose (verifiable) mimics November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 28

Tarzan goals • No distinction between anon proxies and clients – • • • Peer-to-peer model Anonymity against corrupt relays – MIX-net encoding – Robust tunnel selection – Prevent adversary spoofing or running many nodes Anonymity against global eavesdropping – Cover traffic protects all nodes – Restrict topology to make cover practical – Choose neighbors in verifiably-random manner Application-independence – November 20, 2002 Low-latency IP-layer redirection Tarzan: a Peer-to-Peer Anonymizing Network Layer 29

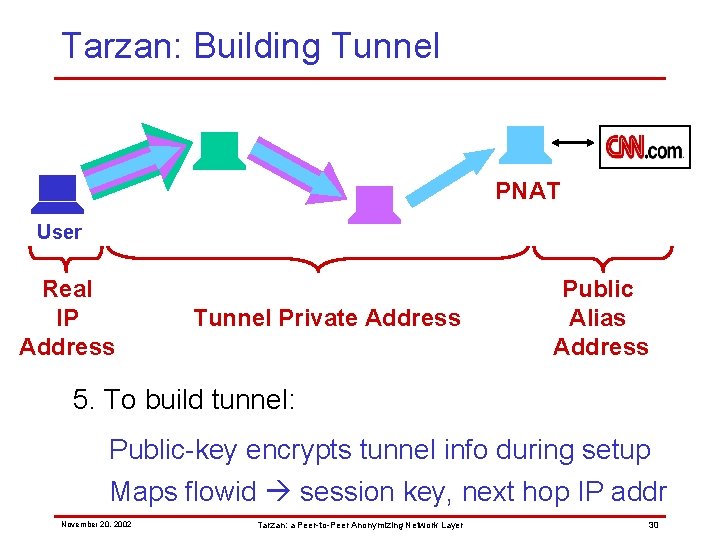
Tarzan: Building Tunnel PNAT User Real IP Address Tunnel Private Address Public Alias Address 5. To build tunnel: Public-key encrypts tunnel info during setup Maps flowid session key, next hop IP addr November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 30

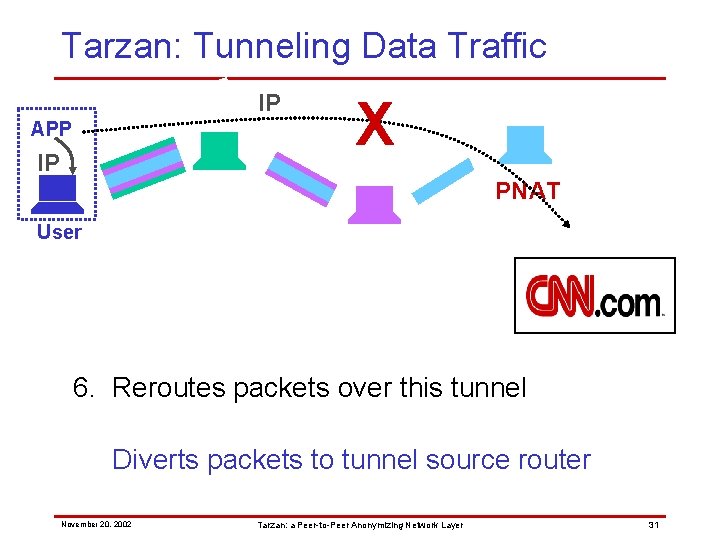
Tarzan: Tunneling Data Traffic IP APP IP X PNAT User 6. Reroutes packets over this tunnel Diverts packets to tunnel source router November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 31

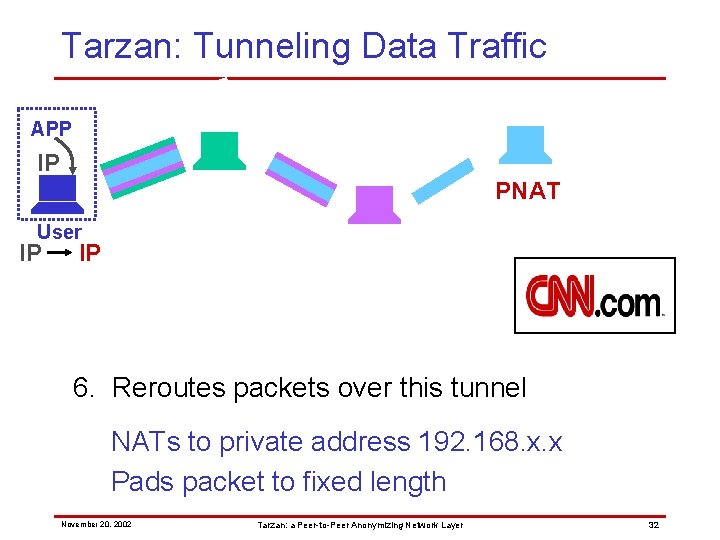
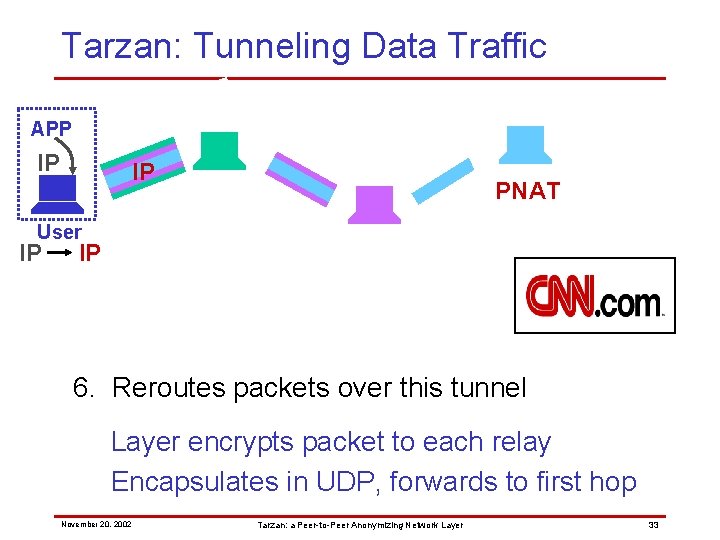
Tarzan: Tunneling Data Traffic APP IP PNAT User IP IP 6. Reroutes packets over this tunnel NATs to private address 192. 168. x. x Pads packet to fixed length November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 32

Tarzan: Tunneling Data Traffic APP IP IP PNAT User IP IP 6. Reroutes packets over this tunnel Layer encrypts packet to each relay Encapsulates in UDP, forwards to first hop November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 33

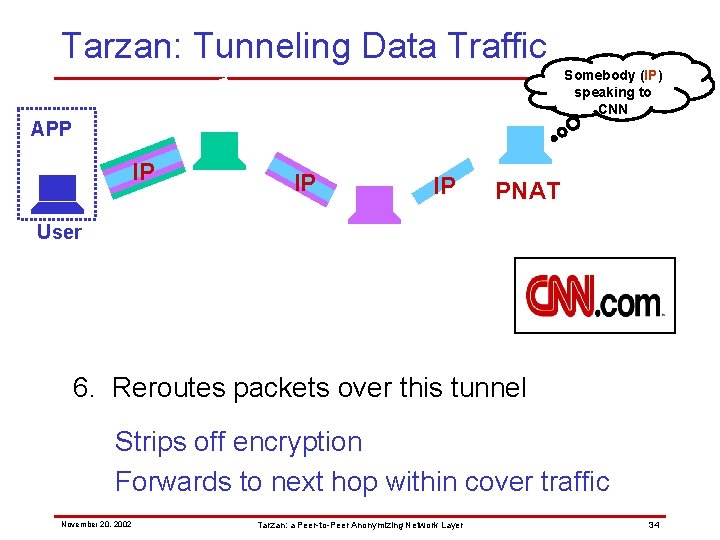
Tarzan: Tunneling Data Traffic Somebody (IP) speaking to CNN APP IP IP IP PNAT User 6. Reroutes packets over this tunnel Strips off encryption Forwards to next hop within cover traffic November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 34

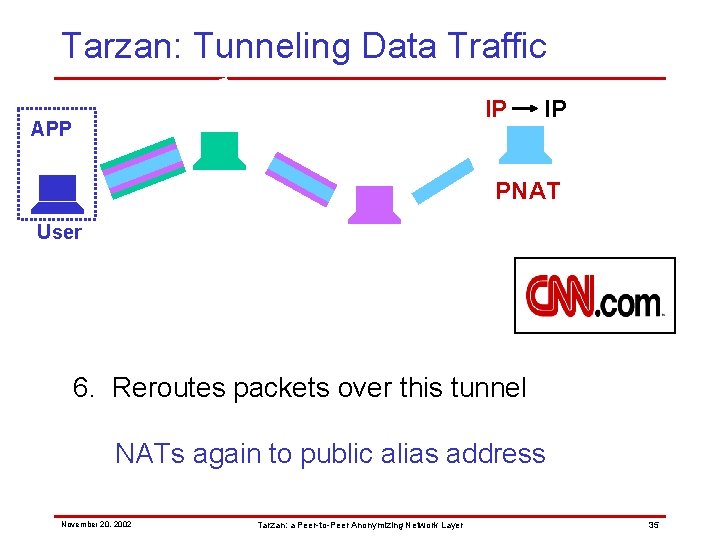
Tarzan: Tunneling Data Traffic IP APP IP PNAT User 6. Reroutes packets over this tunnel NATs again to public alias address November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 35

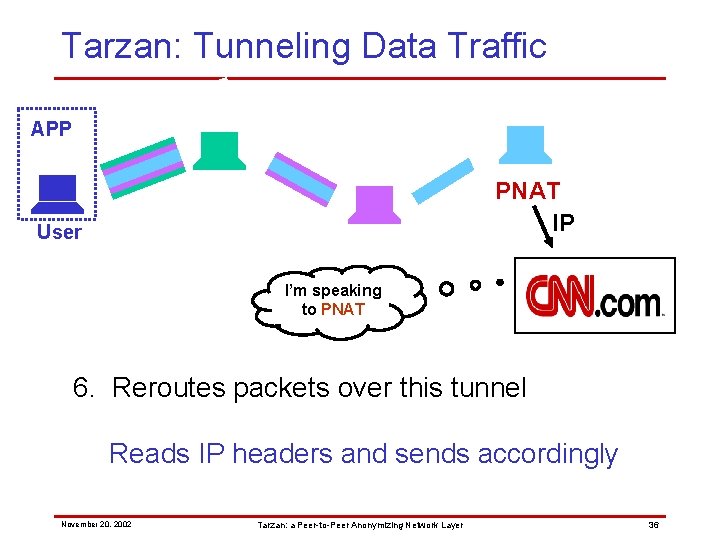
Tarzan: Tunneling Data Traffic APP PNAT IP User I’m speaking to PNAT 6. Reroutes packets over this tunnel Reads IP headers and sends accordingly November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 36

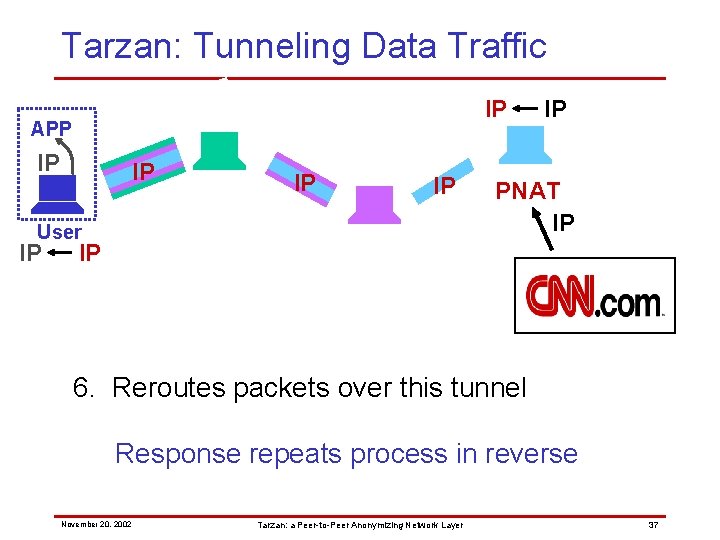
Tarzan: Tunneling Data Traffic IP APP IP IP User IP IP PNAT IP IP 6. Reroutes packets over this tunnel Response repeats process in reverse November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 37

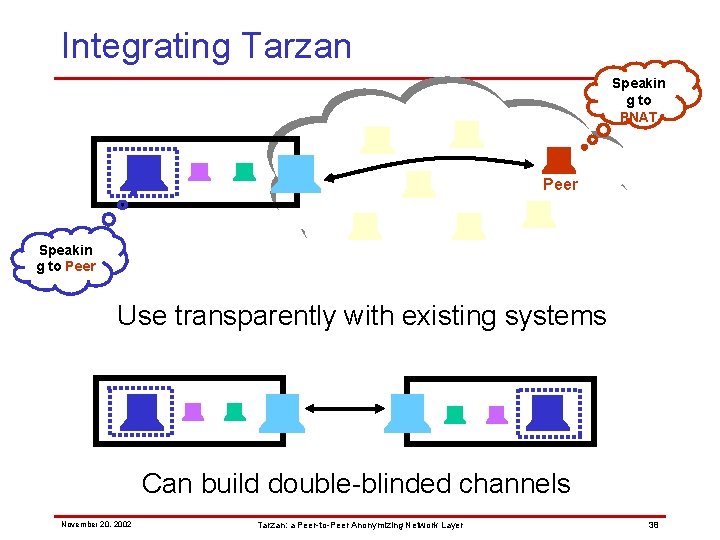
Integrating Tarzan Speakin g to PNAT Peer Speakin g to Peer Use transparently with existing systems Can build double-blinded channels November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 38

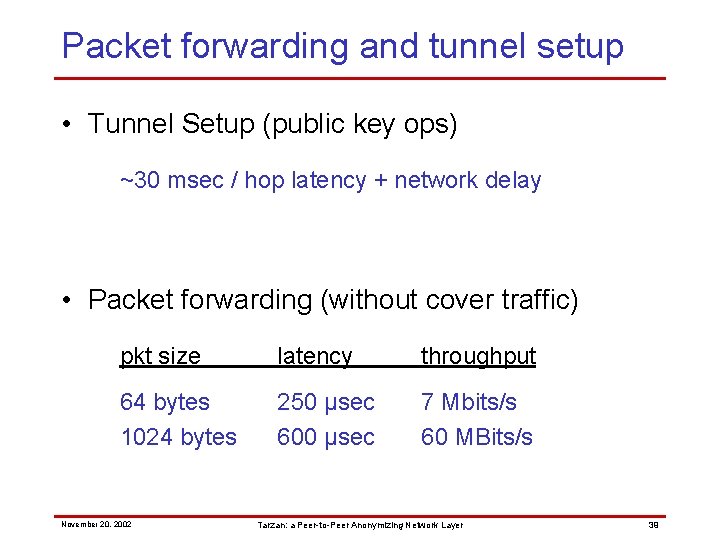
Packet forwarding and tunnel setup • Tunnel Setup (public key ops) ~30 msec / hop latency + network delay • Packet forwarding (without cover traffic) pkt size latency throughput 64 bytes 1024 bytes 250 µsec 600 µsec 7 Mbits/s 60 MBits/s November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 39

Summary • Application-independence at IP layer – • No network edge through peer-to-peer design – • • Previous systems for email, web, file-sharing, etc. Core routers can be blocked, targetted, or black-box analyzed Anonymity against corrupt relays and global eavesdropping – Cover traffic within restricted topology – MIX-net tunneling through verified mimics Scale to thousands – Towards a critical mass of users November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 40

http: //pdos. lcs. mit. edu/tarzan/ November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 41

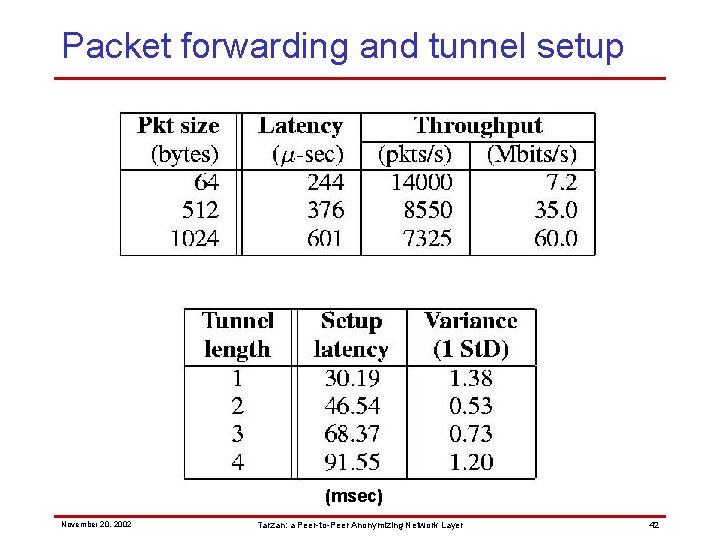
Packet forwarding and tunnel setup (msec) November 20, 2002 Tarzan: a Peer-to-Peer Anonymizing Network Layer 42