TAODV A Trusted AODV Routing Protocol for MANET

















- Slides: 37

TAODV: A Trusted AODV Routing Protocol for MANET Li Xiaoqi, Gi. Gi Term Presentation 2004 -4 -27

Outline Introduction n Framework of TAODV n Trust model for TAODV n Routing operations in TAODV n Analyses and simulations n Conclusion n 2

Now Comes to: Introduction n Framework of TAODV n Trust model for TAODV n Routing Operations in TAODV n Analyses and Simulations n Conclusion n 3

Introduction n Mobile Ad Hoc Network (MANET) ¨ No fixed infrastructure ¨ Multi-hop routing by cooperation of nodes in a self-organized way ¨ Nodes has high mobility ¨ Underlying medium is wireless ¨ Frequent link layer errors ¨ Vulnerable to kinds of attacks 4

Routing Protocols for MANET n DSR: ¨ The n Dynamic Source Routing Protocol DSDV: ¨ Destination-Sequenced n Distance Vector Protocol AODV: ¨ Ad Hoc On-Demand Distance Vector Protocol ¨ Two main routing messages: n n RREQ: Routing REQuest RREP: Routing REPly 5

Applications of MANET n n Personal area networking Meeting rooms Disaster relief Battlefield operations High Security Requirements 6

Previous Security Solutions for MANET n Secure routing protocol ¨ may perform digital signature authentication at each routing message ¨ huge overhead n Key management mechanism ¨ usually need a super-trusted third-party to issue certificates ¨ destroy the self-organization nature of MANET 7

Previous Security Solutions for MANET (con’d) n Intrusion detection mechanism ¨ Listen, collect and analyze all traffics on each node ¨ Huge process overhead Our aim is to design a secure routing protocol, called TAODV (Trusted AODV Routing Protocol), without introducing huge overhead or destroying the self-organization nature of MANET 8

Now Comes to: Introduction n Framework of TAODV n Trust model for TAODV n Routing Operations in TAODV n Analyses and Simulations n Conclusion n 9

Main Ideas of TAODV n n A secure routing protocol for MANET Use trust relationships among nodes for routing ¨ Employ a trust model derived from subjective logic ¨ Trust calculation is not very time-consuming ¨ Need not sign and verify digital signature at each routing message n Cooperate with a self-organized key management mechanism ¨ such n as some threshold solutions We take AODV for example to illustrate our idea 10

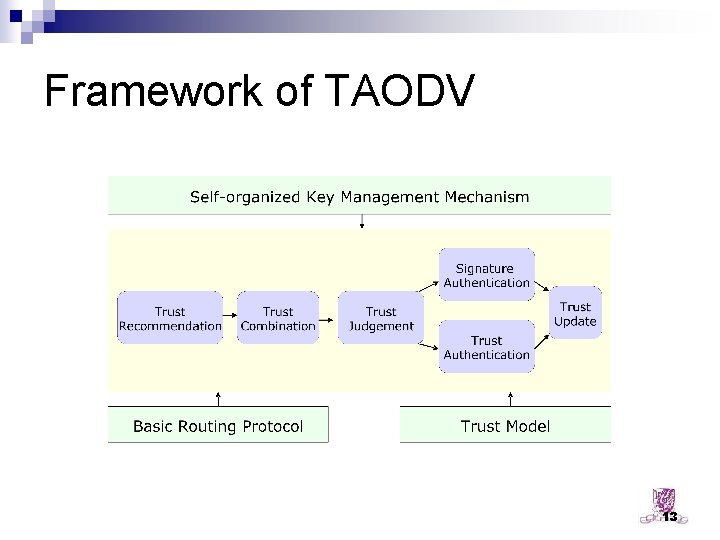
Four Modules of TAODV n n Basic routing protocol (AODV in this work) Trust model ¨ Define the algorithms or rules to combine, judge, and update trust information based on subjective logic n n Trusted routing protocol Self-organized key management mechanism ¨ generate a {secret, public} key pair for each node and distribute public keys in a secure self-organized way ¨ A pre-requisition, will not discuss it in this presentation 11

Module of Trusted Routing Protocol n Include operations of ¨ trust recommendation ¨ trust combination ¨ trust judgement ¨ trust update ¨ signature authentication ¨ trust authentication 12

Framework of TAODV 13

Now Comes to: Introduction n Framework of TAODV n Trust model for TAODV n Routing Operations in TAODV n Analyses and Simulations n Conclusion n 14

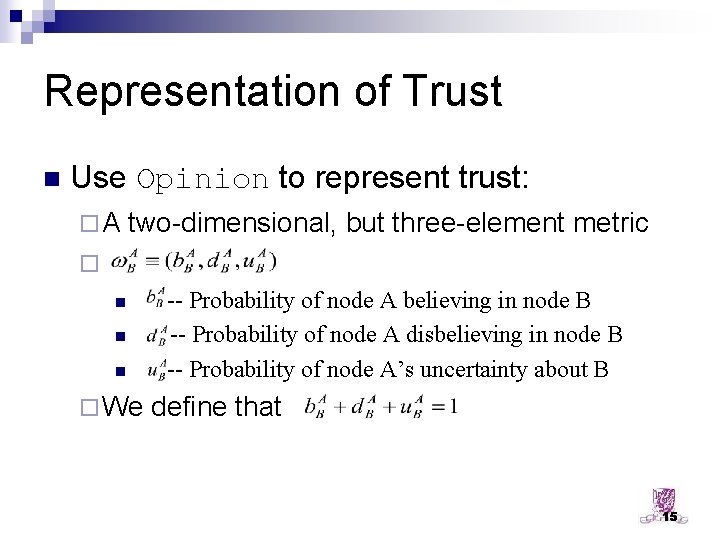
Representation of Trust n Use Opinion to represent trust: ¨A two-dimensional, but three-element metric ¨ n n n ¨ We -- Probability of node A believing in node B -- Probability of node A disbelieving in node B -- Probability of node A’s uncertainty about B define that 15

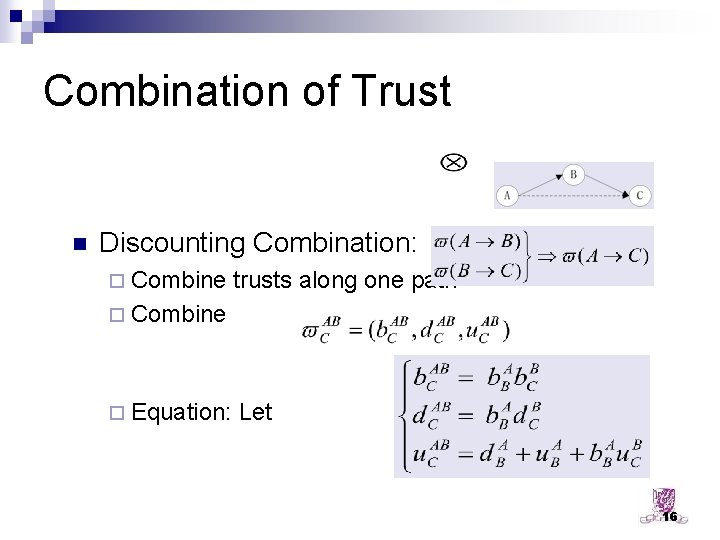
Combination of Trust n Discounting Combination: ¨ Combine trusts along one path ¨ Combine ¨ Equation: Let 16

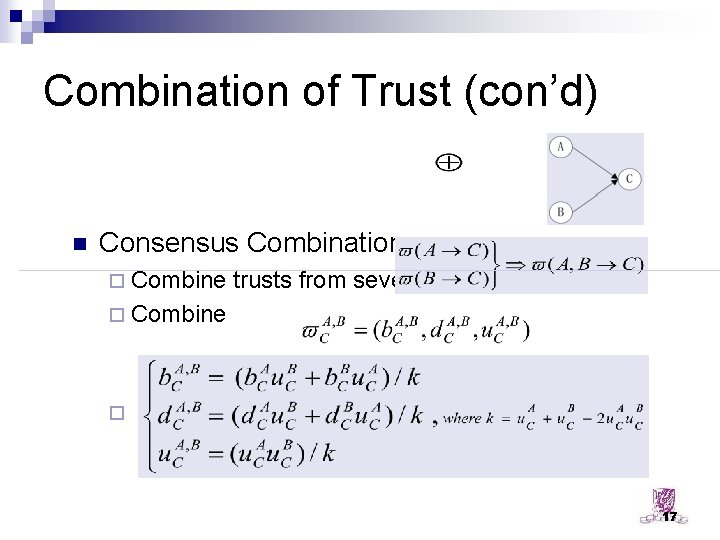
Combination of Trust (con’d) n Consensus Combination: ¨ Combine trusts from several paths ¨ Combine ¨ Equation: Let 17

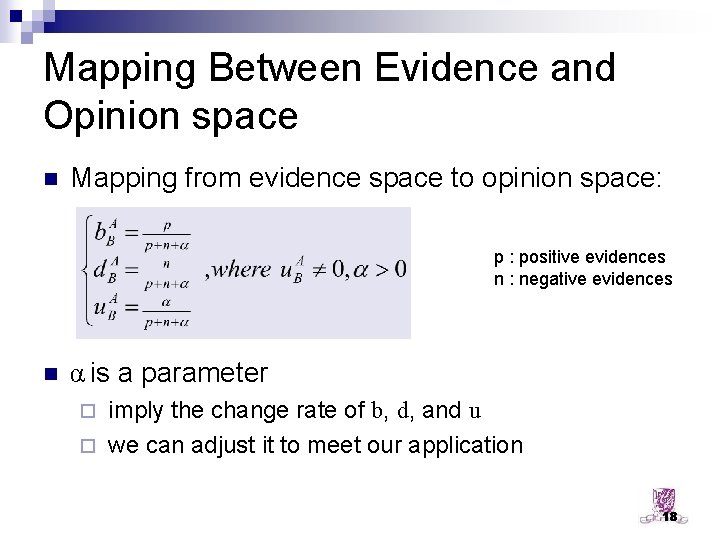
Mapping Between Evidence and Opinion space n Mapping from evidence space to opinion space: p : positive evidences n : negative evidences n α is a parameter imply the change rate of b, d, and u ¨ we can adjust it to meet our application ¨ 18

Mapping Between Evidence and Opinion space (con’d) n Mapping from opinion space to evidence space: n We can update trust information from evidence space mapping to opinion space, or vice versa 19

Now Comes to Introduction n Framework of TAODV n Trust model for TAODV n Routing Operations in TAODV n Analyses and Simulations n Conclusion n 20

Trust Recommendation Exchange trust information n Three types of message: n ¨ TREQ: Trust REQuest ¨ TREP: Trust REPly ¨ TWARN: Trust WARNing n Broadcast TWARN when a node’s disbelief value is zero 21

Trust Recommendation (con’d) n Message Structure ¨ TREQ ¨ TREP 22

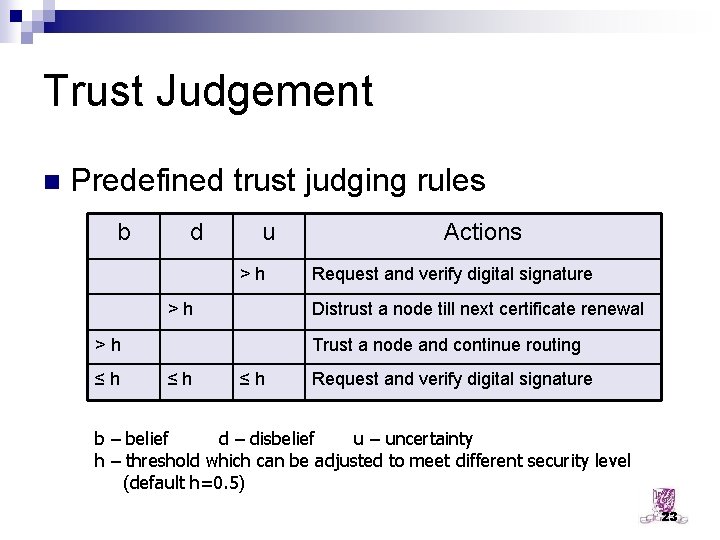
Trust Judgement n Predefined trust judging rules b d u >h >h Request and verify digital signature Distrust a node till next certificate renewal >h ≤h Actions Trust a node and continue routing ≤h ≤h Request and verify digital signature b – belief d – disbelief u – uncertainty h – threshold which can be adjusted to meet different security level (default h=0. 5) 23

Trust Update n Update of Evidences ¨ Successful Communication Positive events: p++ ¨ Failed Communication Negative events: n++ ¨ Mapping n from opinion space Update of opinion ¨ Combination from different recommendations ¨ Mapping from evidence space 24

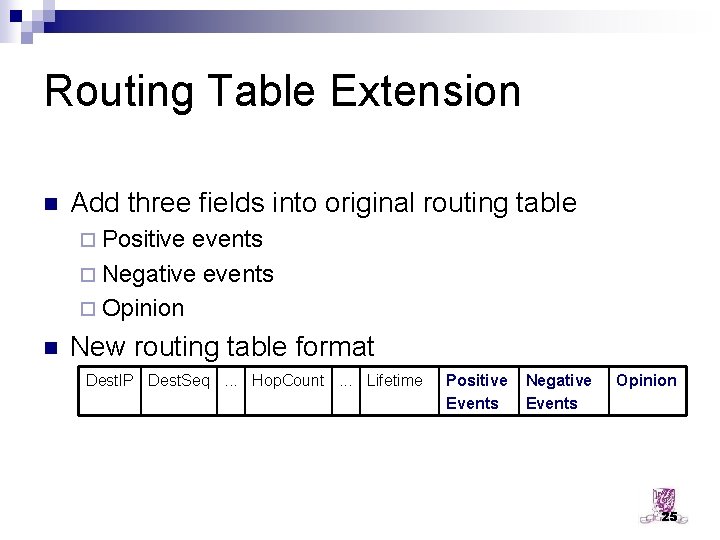
Routing Table Extension n Add three fields into original routing table ¨ Positive events ¨ Negative events ¨ Opinion n New routing table format Dest. IP Dest. Seq. . . Hop. Count. . . Lifetime Positive Events Negative Events Opinion 25

Routing Message Extension n Add such fields into original routing messages ¨ Trust information, or ¨ Digital signature information n RREQ TRREQ RREP TRREP Message structure: original routing information … trust information or signature information 26

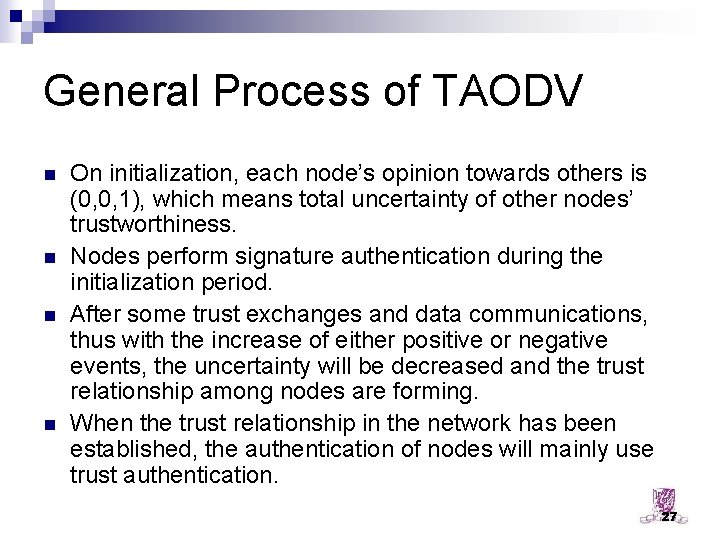
General Process of TAODV n n On initialization, each node’s opinion towards others is (0, 0, 1), which means total uncertainty of other nodes’ trustworthiness. Nodes perform signature authentication during the initialization period. After some trust exchanges and data communications, thus with the increase of either positive or negative events, the uncertainty will be decreased and the trust relationship among nodes are forming. When the trust relationship in the network has been established, the authentication of nodes will mainly use trust authentication. 27

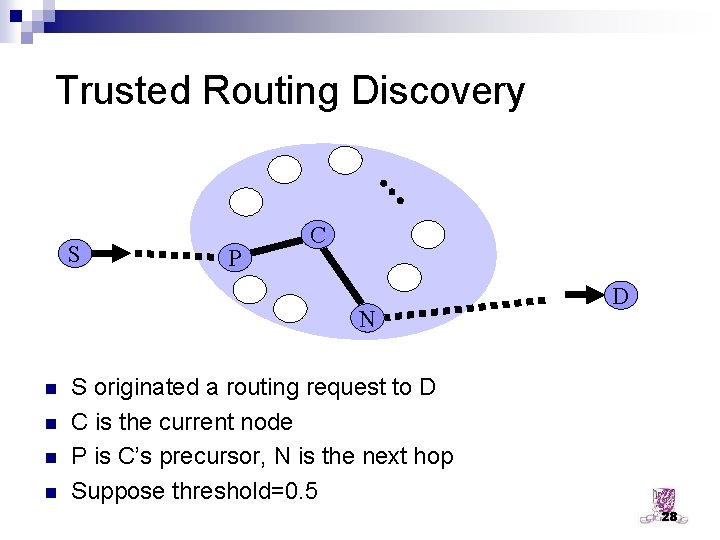
Trusted Routing Discovery S P C N n n D S originated a routing request to D C is the current node P is C’s precursor, N is the next hop Suppose threshold=0. 5 28

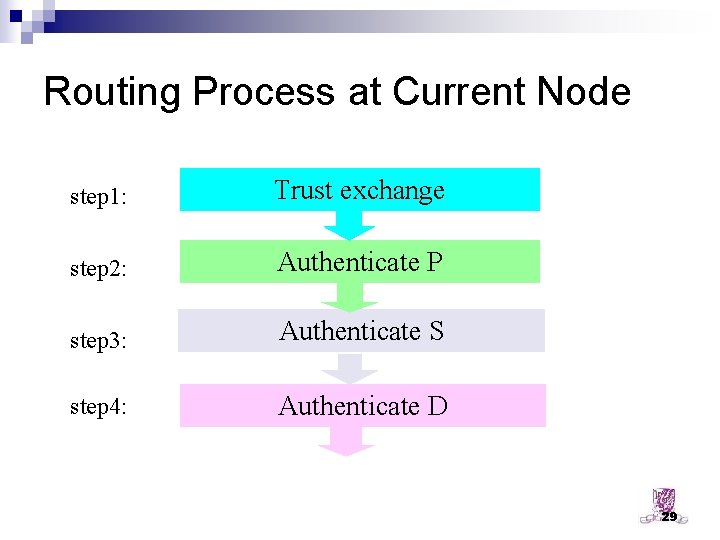
Routing Process at Current Node step 1: Trust exchange step 2: Authenticate P step 3: Authenticate S step 4: Authenticate D 29

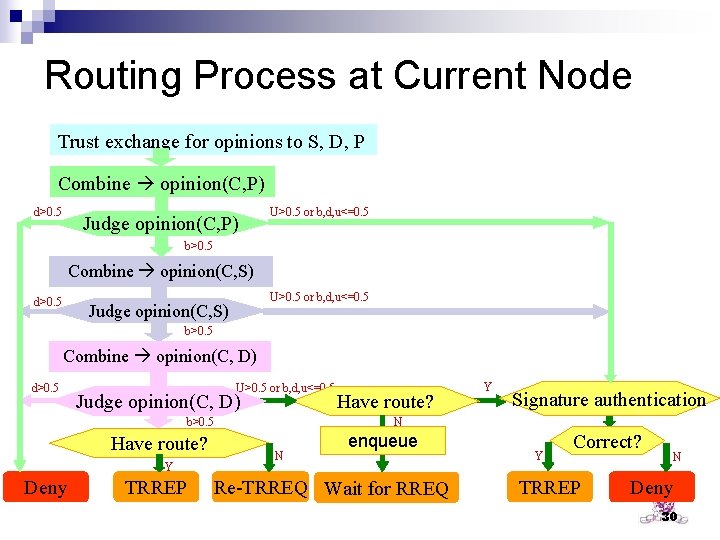
Routing Process at Current Node Trust exchange for opinions to S, D, P Combine opinion(C, P) d>0. 5 Judge opinion(C, P) U>0. 5 or b, d, u<=0. 5 b>0. 5 Combine opinion(C, S) d>0. 5 U>0. 5 or b, d, u<=0. 5 Judge opinion(C, S) b>0. 5 Combine opinion(C, D) d>0. 5 U>0. 5 or b, d, u<=0. 5 Judge opinion(C, D) b>0. 5 Have route? Y Deny TRREP Have route? Y Signature authentication N N enqueue Re-TRREQ Wait for RREQ Y Correct? TRREP N Deny 30

Now Comes to: Introduction n Framework of TAODV n Trust model for TAODV n Routing operations in TAODV n Analyses and simulations n Conclusion n 31

Performance Analysis Communication overheads can be sharply reduced by avoiding signature generation and verification at each routing message. n Bandwidth overheads can be largely reduced because of replacing 1024/2048 bit signatures to simple trust values. n 32

Security Analysis n n If no misbehavior, trust value will keep increasing. If an external malicious node, it will at once be denied due to not providing valid signature. We only consider to prevent external attacks. Internal attacks can be eased through certificates renewal. 33

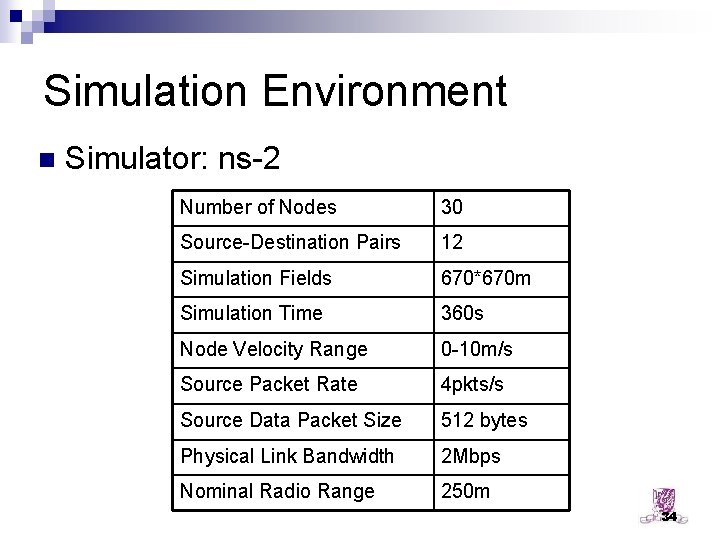
Simulation Environment n Simulator: ns-2 Number of Nodes 30 Source-Destination Pairs 12 Simulation Fields 670*670 m Simulation Time 360 s Node Velocity Range 0 -10 m/s Source Packet Rate 4 pkts/s Source Data Packet Size 512 bytes Physical Link Bandwidth 2 Mbps Nominal Radio Range 250 m 34

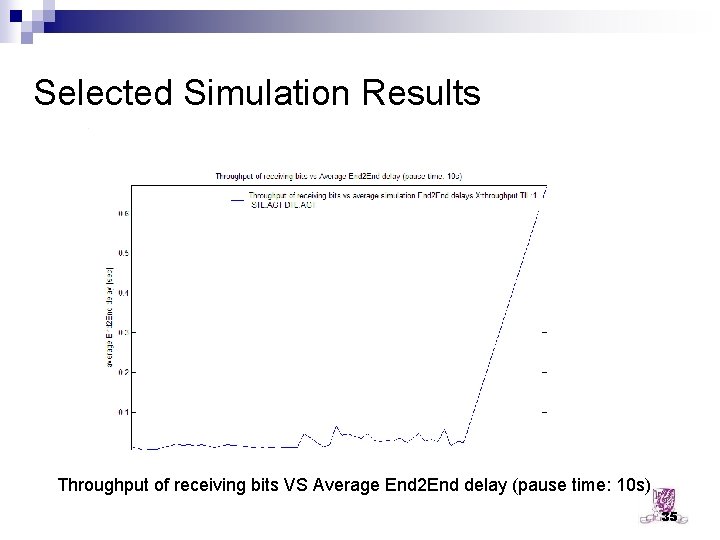
Selected Simulation Results Throughput of receiving bits VS Average End 2 End delay (pause time: 10 s) 35

Conclusion TAODV is a trusted routing protocol which cooperates with a self-organized key management mechanism. n It introduces less computation overheads than previous secure routing protocol solutions and also guarantee a certain security level. n It performs trusted routing in a selforganized way. n 36

Q&A Thank You!