Tamper Resistance and Lifecycle Attacks Nicholas Weaver Tamper





















- Slides: 37

Tamper Resistance and Lifecycle Attacks Nicholas Weaver Tamper Resistant Circuits, FPGAs, and Lifecycle Attacks Nicholas C Weaver nweaver at icsi dot berkeley dot edu © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains

Who Am I? Tamper Resistance and Lifecycle Attacks Nicholas Weaver • Ph. D. Researcher at the International Computer Science Institute in Berkeley – A 501(c)3 nonprofit research institution affiliated with UC Berkeley – Dissertation on FPGA architectures – Working in computer security • Work sponsored by: – NSF CNS-0433702 – NSF/DHS ANI-0335290 – DOE DE-FG 02 -04 ER 25638 • Obligatory: Opinions are my own, not of the funders – Ob. Disclosure: I have colleagues at both Xilinx and Altera, and Xilinx donates tools/IP cores to support some unrelated work of mine 2 © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains

We Want Some Circuit Security Properties Tamper Resistance and Lifecycle Attacks Nicholas Weaver • Consider all these properties as a whole, not just in isolation: – Tamper resistance • The circuit can’t be modified by an adversary – Only the functionality we intend exists – Activation • The circuit can’t work until activated by external authority – Revocation • A communicating authority can remove the ability of the circuit to operate – Secrecy • The attacker doesn’t know what the circuit is – Even if they can take apart the chip! – Updateability • An authorized authority can upgrade the design in the field – Cryptographically secured storage © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains 3

Outline Tamper Resistance and Lifecycle Attacks Nicholas Weaver • Attacks on Circuits: Lifecycle attacks – Lifecycle attacks on FPGAs – Lifecycle attacks on ASICs • Countering lifecycle attacks through verification – Ensure that what you got is what you want • Per project and per platform costs – Why “Tamper Resistant” circuits aren’t. • Given a lifecycle-attack-resistant FPGA flow, provide – Activation, tamper resistance, revocation, secrecy, secure storage and updates • A single mechanism for all properties – Using existing bitfile protection in a COTS FPGA • Xilinx Virtex 4 • Suggestions for implementation – Attacks on the resulting design © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains 4

Why this talk? Tamper Resistance and Lifecycle Attacks Nicholas Weaver • These are ideas I’ve had for a long time – But no interest in progressing beyond a paper design, too many other priorities • There appears to be a growing interest in tamper resistant circuits – Especially in the defense community, with “Secure ICs” and related topics – Including resistance to lifecycle attacks – But need to consider all objectives, not just lifecycle attack resistance • I don’t want to see a lot of money wasted – I don’t believe the goals can be met with ASICs • Costs significantly more to resist lifecycle attacks • Can’t meet some tamper resistance goals • Can’t meet upgradeability – I believe they can easily be met with FPGAs (Field Programmable Gate Arrays) • Engineering problems, not research problems • Can further harden FPGAs 5 © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains

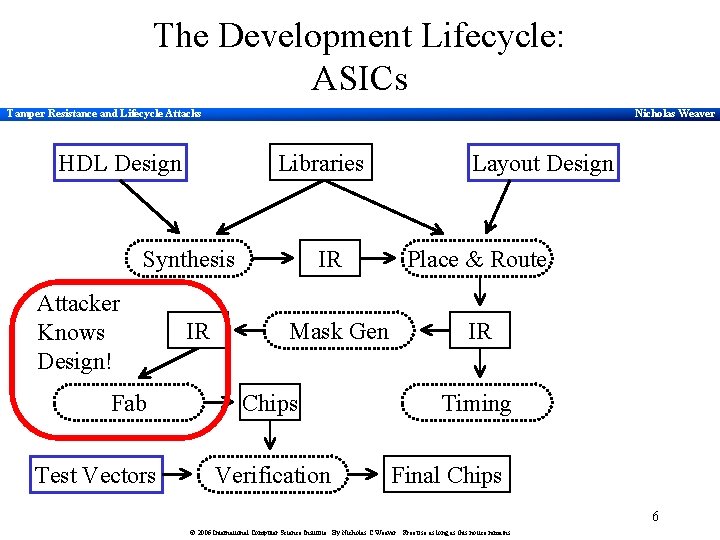
The Development Lifecycle: ASICs Tamper Resistance and Lifecycle Attacks Nicholas Weaver HDL Design Libraries Synthesis Attacker Knows Design! Fab Test Vectors IR IR Mask Gen Chips Verification Layout Design Place & Route IR Timing Final Chips 6 © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains

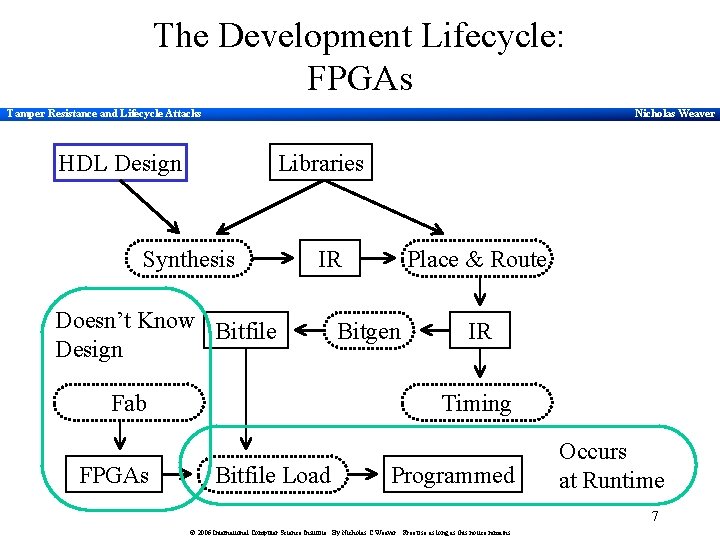
The Development Lifecycle: FPGAs Tamper Resistance and Lifecycle Attacks Nicholas Weaver HDL Design Libraries Synthesis Doesn’t Know Bitfile Design Fab FPGAs Place & Route IR Bitgen IR Timing Bitfile Load Programmed Occurs at Runtime 7 © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains

Relative Power of Lifecycle Attacks Tamper Resistance and Lifecycle Attacks Nicholas Weaver • A lifecycle attack is far more powerful if the attacker knows what he is targeting – Thus the lifecycle in the attack for an ASIC is more powerful than an attack on an FPGA • For the FPGA, the attacker can really only target common infrastructure – And lifecycle attacks on the general CAD tools are also less powerful • Ken Thompson knew the login program when he designed his famous lifecycle attack • Late-binding also ? may? have some advantages when authorizing a system for classified usages – You don’t need to export a classified design to the manufacturer 8 © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains

Resisting Lifecycle Attacks: Verification Tamper Resistance and Lifecycle Attacks Nicholas Weaver • Lifecycle attacks are very similar to the rootkit problem – From within a system, you can’t determine system integrity with perfect certainty • You need an exterior viewpoint • You need to measure something • Thus lifecycle attacks requires – Prevention: If you can’t trust your manufacturers, you may have a bigger problem – Detection: Is what you expect what is there? • By measuring some property that must be different if there is a lifecycle attack 9 © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains

Considering Costs Tamper Resistance and Lifecycle Attacks Nicholas Weaver • Need to consider cost per platform and cost per project – Per-platform cost can be spent once • A supply of parts to support multiple projects – Per-project costs need to be spent per design • Prefer per-platform costs over per-project costs – Enables sharing of effort over multiple projects • For per-project costs, prefer just computational tasks – If it requires physical examination, we have a problem • And you do need to care about cost, because your opponents do – “Quantity has a virtue all its own”: argues for cost-sensitive designs 10 © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains

Lifecycle Attacks on CAD Tools Tamper Resistance and Lifecycle Attacks Nicholas Weaver • Effectively need to develop a “verifier” tool for each step in the flow – Is the output of a processing step semantically equivalent to the input? – Requires understanding the tool’s operations and formats • But does not require tool source code – Can be done without file-format documentation, but documentation will make this substantially easier • And a simpler problem than actually reimplementing the tools • Per platform cost to implement – Need to build one for each tool in the suite • Per project cost to run: computation – Can be significantly slower than normal CAD tools: • Only run on the final design • Can run each step in parallel • The process is the same for FPGAs and ASICs – And CAD tool attacks are all “pre design” attacks • There is ongoing research in this area 11 © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains

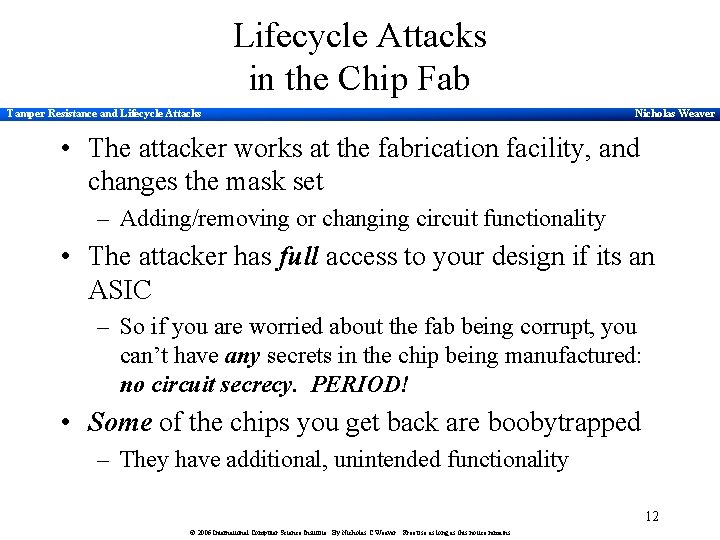
Lifecycle Attacks in the Chip Fab Tamper Resistance and Lifecycle Attacks Nicholas Weaver • The attacker works at the fabrication facility, and changes the mask set – Adding/removing or changing circuit functionality • The attacker has full access to your design if its an ASIC – So if you are worried about the fab being corrupt, you can’t have any secrets in the chip being manufactured: no circuit secrecy. PERIOD! • Some of the chips you get back are boobytrapped – They have additional, unintended functionality 12 © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains

How to Detect Fabrication Attacks Tamper Resistance and Lifecycle Attacks Nicholas Weaver • The only way to be sure: You need to know that the circuits produced are the circuits requested – You know what the mask set should be • After all, you designed the part – You get a number of parts back • So how can you verify? – Take it apart with a Scanning Electron Microscope! – Sand the chip down, layer by layer, and reconstruct the mask set used to produce the chip • Have to sample and assume probabilistic protection – But can make the odds arbitrarily small by suitable sampling 13 © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains

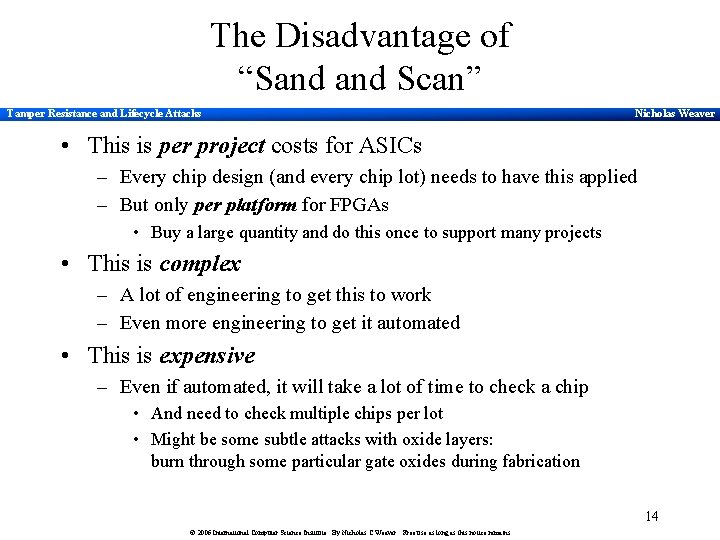
The Disadvantage of “Sand Scan” Tamper Resistance and Lifecycle Attacks Nicholas Weaver • This is per project costs for ASICs – Every chip design (and every chip lot) needs to have this applied – But only per platform for FPGAs • Buy a large quantity and do this once to support many projects • This is complex – A lot of engineering to get this to work – Even more engineering to get it automated • This is expensive – Even if automated, it will take a lot of time to check a chip • And need to check multiple chips per lot • Might be some subtle attacks with oxide layers: burn through some particular gate oxides during fabrication 14 © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains

Why “Tamper Resistant” Circuits Aren’t Tamper Resistance and Lifecycle Attacks Nicholas Weaver • The idea: Modify the ASIC’s circuit in such a way that, if the Fab is corrupt, the changes can be detected by observing circuit behavior – Short of taking the chip apart with a scanning electron microscope – Part of the push for “Secure ICs” • I don’t believe this is possible – Tampering can introduce very, very subtle changes in behavior • Changes can easily be below the variation in fabrication performance • And if you can’t measure it, you can’t detect it! 15 © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains

How I’d Tamper: Removing Functionality Tamper Resistance and Lifecycle Attacks Nicholas Weaver • Change a combination of gates to nonfunctional/different function – With same capacitive load in the same location • Can detect ONLY if there is an input test vector which can detect this change – Can NOT detect based on timing or capacitance, as these properties don’t change – But are you sure you have 100% test coverage? • Especially since the error is not a random error 16 © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains

How I’d Tamper: Reading Information Tamper Resistance and Lifecycle Attacks Nicholas Weaver • The tampering circuit needs to be able to read information from the victim circuit – Just tap a wire • Only thing electrically observed is additional capacitance – From the additional wire and a simple buffer • If not on the critical path, this won’t affect timing – Unlikely to affect timing if on the critical path, at least within the margin of circuit variation – Capacitive tap the wire: Run another wire parallel to the target signal • Capacitive coupling creates a signal to be read – Input into a sense-amp circuit • Produces far less load than the previous version • Depending on the scenario, this may be enough! – Tap and record all encryption keys into a ROM • Now if device is captured, can have full history © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains 17

How could you detect this electrically? Tamper Resistance and Lifecycle Attacks Nicholas Weaver • Measure timing of critical path – But how close to random variation is this? • Answer: probably below the manufacturing noise • And what if the taps are not on the critical paths? • Measure timing of all paths – Very difficult to do – Again, variation kills you • Measure capacitance – On every wire? And what if the capacitance detection circuits are tampered with? – What about process variation of many percent? • Measure power consumption – Again, can be in the noise! • Can’t check with test vectors! 18 © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains

How I’d tamper: Forced output Tamper Resistance and Lifecycle Attacks Nicholas Weaver • Add a single gate (or multiple gates) in an output path which allows me to inject communication – Even just injecting jitter may be enough: RF “noise” as signal • Effectively as hard to detect as the tap – Very slight change in timing, capacitance and power consumption, probably within fabrication noise • Can’t detect with test vectors – You don’t know what magic input sequence may trigger a change in output • This is now sufficient for all my tampering goals: – Can read and write signals, plus my own computation 19 © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains

What just might work at first glance: Constrained layout Tamper Resistance and Lifecycle Attacks Nicholas Weaver • If the design is truly optimally layed-out, it may be difficult to tap the design – No space to put the taps, no space to run the wires • Same thought as software-only attestation • Unlike software attestation, this needs to apply to the entire circuit, not just the attestation core – But this seems impossible for real circuits – CAD problems, such as circuit layout and routing, are NP-complete, and very large • CAD tools use approximation algorithms and heuristics, NO guarantee of optimality 20 © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains

So my belief: Just give up on ASICs Tamper Resistance and Lifecycle Attacks Nicholas Weaver • I don’t believe ASICs can economically resist fab attacks – Only solution appears to be take apart some samples • Tamper resistant schemes don’t seem to work – But taking apart the chips has a huge per project cost • Can’t provide circuit secrecy – Attacker who captures device can take it apart – Attacker in the fab knows this already • Activation is very difficult – Attacker can possibly probe and reactivate a captured device • Because you can’t provide circuit secrecy • Revocation is difficult but doable (fuse-based revocation) • Updates are impossible – Hardware function is fixed 21 © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains

To begin with: Circuit Tampering is Less Powerful against FPGAs Tamper Resistance and Lifecycle Attacks Nicholas Weaver • The attacker doesn’t know what the circuit will actually be – The FPGA design is late-bound: determined after part manufacturing – FPGA tools are rather nondeterministic • The same circuit may be realized in vastly different ways between individual compilations of a design – Only the fixed logic is a-priori known to the attacker • But this can be significant. In particular, tampering with the encrypted bitfile functionality could be a problem • “Sand Scan” might be easier, because of FPGA’s regular structure – Can sample the FPGA array? – Can make the process quicker? – Can focus on critical fixed logic: • Lifecycle attacks in the fab will probably target the configuration path, not the general array 22 © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains

But we can do better! Tamper Resistance and Lifecycle Attacks Nicholas Weaver • Deploy a framework which supports all our primitives: – Secrecy, tamper resistant, activation, revocation, updates, and secure storage • On a commercial FPGA – Using existing bitfile protection mechanisms • Which could be enhanced • Resist lifecycle attacks with – CAD tool verification – “Sand Scan” chip lots • It sounds like I’m promising the moon, here. I’d be skeptical at this point myself… – Yet this should work, and is just engineering effort, not research effort! 23 © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains

How an FPGA actually works Tamper Resistance and Lifecycle Attacks Nicholas Weaver • The circuit being run is contained in the configuration bitfile • When the FPGA is powered on, it loads the configuration bitfile – This configuration then sets the state of the FPGA’s logic and interconnect, allowing the FPGA to implement the circuit • Within the FPGA, the configuration is stored in distributed SRAM cells throughout the chip – If you can copy the configuration (break circuit secrecy), you can clone the device as much as you want 24 © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains

The key: Bitfile Encryption Tamper Resistance and Lifecycle Attacks Nicholas Weaver • Current FPGAs support bitfile encryption – A secret key is stored in the FPGA • In static memory in the Altera Stratix series • In SRAM in the Xilinx Virtex series, with a separate Vbatt input – Will assume the Xilinx technique for this talk, its more powerful • The bitfile is stored off chip in an encrypted form – When the FPGA first loads, it decrypts the bitfile using the encryption key as it is read into the configuration • 256 b AES in current designs – The configuration is used to set the circuit function inside the FPGA • The keys and decrypted configuration only exist within the FPGA – To determine the configuration, need to break the FPGA encryption • Easiest is probably to extract the key stored in the FPGA • Designed to prevent piracy by providing circuit secrecy – Without circuit secrecy, FPGA piracy is trivial – With circuit secrecy, it is impossible 25 © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains

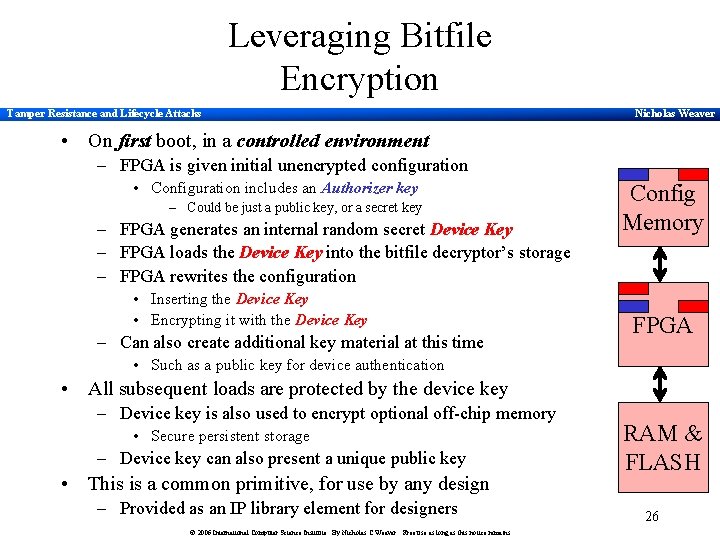
Leveraging Bitfile Encryption Tamper Resistance and Lifecycle Attacks Nicholas Weaver • On first boot, in a controlled environment – FPGA is given initial unencrypted configuration • Configuration includes an Authorizer key – Could be just a public key, or a secret key – FPGA generates an internal random secret Device Key – FPGA loads the Device Key into the bitfile decryptor’s storage – FPGA rewrites the configuration • Inserting the Device Key • Encrypting it with the Device Key – Can also create additional key material at this time Config Memory FPGA • Such as a public key for device authentication • All subsequent loads are protected by the device key – Device key is also used to encrypt optional off-chip memory • Secure persistent storage – Device key can also present a unique public key • This is a common primitive, for use by any design – Provided as an IP library element for designers © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains RAM & FLASH 26

Circuit Secrecy Tamper Resistance and Lifecycle Attacks Nicholas Weaver • The design in the FPGA is now protected by the bitfile encryptor – Outside of the FPGA, the design is always encrypted with a key unique to the specific FPGA – The cleartext key NEVER leaves the FPGA once programmed • And is stored in volatile memory – Within the running FPGA, the design is decrypted internally and stored as distributed SRAM cells – All off-chip memory is encrypted • Provides encrypted storage • Protection equivalent to the anti-piracy mechanism – – – Anti-piracy is all about maintaining circuit secrecy Need to either extract the bitfile from SRAM from the running FPGA Or extract the bitfile key from the FPGA’s key storage Or perform a side channel attack on the bitfile loader Or bribe an engineer to give you the design… 27 © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains

Tamper Resistance and Lifecycle Attacks Nicholas Weaver • Attacker CAN run his own design in a stolen device – As she can always just overwrite/erase the configuration key stored in the FPGA and load the design of her choice • But if the attacker can’t modify the original bitfile (break the circuit secrecy), then the entire system can be tamper evident – The configuration can also contains a unique public/private key pair for the device as well as the Device Key • Device can now authenticate that it is running a valid bitfile to everyone else – Attacker’s design can’t access storage (its encrypted with the Device Key) or any external resources which require authentication • Only slightly less powerful than tamper resistance – But not by much, as the attacker still has to do her own design from scratch, so we can still probably call it fully Tamper Resistant 28 © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains

Activation and Updates Tamper Resistance and Lifecycle Attacks Nicholas Weaver • Present a new bitfile, signed (or encrypted by) the Authorizer key – Device authenticates that the new bitfile is valid • Pick your authorization/delegation scheme – Device decrypts the new bitfile internally, and reencrypts the bitfile using the Device Key • At this time, the new design is modified to include a copy of the Device Key • Unencrypted design never leaves the FPGA – New bitfile is written out to configuration storage • New design still contains the basic primitive blocks – Needed so further activation and updating can occur – So requires a persistent IP core across all designs • Engineering effort to design: best solution is probably to store all keys in a fixed Block. RAM on the FPGA • Thus ONLY authorized updates are allowed, and are semantically equivalent to activation – No limit on the number of upgrades or activations 29 © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains

Revocation Tamper Resistance and Lifecycle Attacks Nicholas Weaver • If in communication with the device, or after a specified time, we wish to remove some functionality… • Simply have the device overwrite/destroy the configuration state for the revoked design – Need to overwrite the whole data, to prevent a key compromise from recovering the revoked design – Need to include the notion of time in activation, to prevent reactivation of a revoked design • Perhaps also include a check in the persistent storage, so design could never be reactivated • Revoke the device completely – Overwrite the key storage and all designs stop working • But overwrite the configuration storage anyway – “Bricks” the system completely until it can be reprogrammed again in the secure environment 30 © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains

Problems: Side Channel Attacks Tamper Resistance and Lifecycle Attacks Nicholas Weaver • The FPGA configuration loaders are probably subject to sidechannel attacks – Power, noise, EMF, etc etc • I don’t know of any comprehensive study, but Xilinx has had a challenge-board outstanding which academics have played with, without success – May be vulnerable to a power attack on configuration loading • By looking at the power consumption in setting the configuration bits for the key storage Block. RAM and using this to seed a brute-force keyspace search – But there is a lot of “noise” going on in configuration loading – If you can break the configuration loader, you can break all the security • Need circuit secrecy for everything else to work 31 © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains

Problem: Threat Model Needs Enhancement Tamper Resistance and Lifecycle Attacks Nicholas Weaver • Steve Trimberger at Xilinx: – “I designed the bitfile encryption to be harder to break than bribing an engineer” • Assumed cost of ~$100, 000 to break the system – On its own, the bitfile encryption is not designed to counter nation-state adversaries • E. G. If the adversary can read SRAM cells from a live device, by taking it apart while keeping it powered • Use system packaging to make the results more robust – Tamper detection wipe device key brick device – A “cheap and OK” system might involve running the Vbatt power through a wire maze/mesh around the design • Any break in the mesh or short would stop all power to the SRAM • Use system design to make tampering less valuable – E. G. For communication devices, even if the attacker can capture a device and break bitfile secrecy, that device is known missing and revoked from the network 32 © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains

Annoyance: No Internal Paths Tamper Resistance and Lifecycle Attacks Nicholas Weaver • On current (Virtex 4) FPGAs, you can’t – Write to the configuration key storage from within the chip • Thus the initialization has to be in a controlled environment, as it has to go outside the chip through the JTAG port – Also requires an external part, because as soon as a write is requested, the FPGA configuration is completely erased – Write the new configuration from within the chip when encryption is used • Only mildly annoying – Use partial reconfiguration • Have to reconfigure the whole FPGA at a time, can’t just swap out a section – Reconfiguration takes 1 -2 seconds • But if you have a bunch of applications and/or a big bucket of money, you can convince the FPGA vendors to add features to the FPGAs 33 © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains

Resource Requirements: Modest Tamper Resistance and Lifecycle Attacks Nicholas Weaver • 1 -2 Block. RAMs – To store key material • An AES encryption core – ~200 LUTs for a low performance core – ~1000 LUTs + 10 Block. RAMs for a high performance (>1 Gbps) • (Optionally) a public key core – Can be very slow and small • Some control logic – Complex but not large, assume ~1000 -2000 LUTs for a soft core • Thus resource requirement ~1 -5% of a typical FPGA • (Optional) an off-chip PLD to manage the JTAG key writing • Its not hard to build, it just takes engineering effort 34 © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains

Implementation Fabrics: Static-memory key storage Tamper Resistance and Lifecycle Attacks Nicholas Weaver • Altera uses static memory (fuse-based ROM) instead of SRAM to store keys – This is a big advantage for convenience: • No longer need a battery, or to worry about battery failure • Can set the key and then ship to manufacturing – But can’t change the key • But static memory is a big NO if you care about security in the face of a reasonably robust attacker – Attacker can buy as many parts as they want, to determine where the static bits are – Now just takes a single captured device, sands down the chip and probes the static cells • Breaks bitfile secrecy breaks all the security – In My Opinion: Cleartext keys should only be stored in on-chip SRAM, never in FLASH/ROM/etc 35 © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains

Implementation Fabrics: Antifuse FPGAs Tamper Resistance and Lifecycle Attacks Nicholas Weaver • Can’t provide updateability – Antifuse FPGAs aren’t reprogrammable • Can provide activation and revocation – But only a limited number of times – Might be bypassable, because of less robust circuit secrecy • Fair circuit secrecy – Better than unencrypted SRAM-based FPGAs, or FPGAs which store the key in non-volatile memory – Worse than SRAM-based encrypted bitfile FPGAs • Antifuse parts are static: can dismantle, probe, and read the state • Can’t store cryptographic keys robustly without battery backup • But some other advantages – Higher density, quick power-on time © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains 36

Conclusions Tamper Resistance and Lifecycle Attacks Nicholas Weaver • Give up on “Secure IC” ASICs – Can’t provide circuit secrecy – Can’t be updated – Incredibly vulnerable to lifecycle attacks in the fab • Economically intractible to solve this problem • Instead, focus on FPGAs – Can provide all properties: secrecy, tamper resistance, activation, revocation, updates, and persistent storage • Using ONLY existing anti-piracy tools built into current FPGAs – Design one IP core • Provide it to your communities to use – Buy a large lot of FPGAs • Verify them to prevent corruption/lifecycle attacks – Talk to the FPGA vendors to get them to improve their anti-piracy protection, now that you have applications to use it 37 © 2006 International Computer Science Institute. By Nicholas C Weaver. Free use as long as this notice remains