Tamper evident encryption of integers using keyed Hash

![Related Work File system and application level integrity [21, 22] Forensic analysis and tamper Related Work File system and application level integrity [21, 22] Forensic analysis and tamper](https://slidetodoc.com/presentation_image/2d9589001f96de6d471852aba53164bd/image-6.jpg)
![Background - HMAC – keyed Hash Message Authentication Code [13] Produces a secure authentication Background - HMAC – keyed Hash Message Authentication Code [13] Produces a secure authentication](https://slidetodoc.com/presentation_image/2d9589001f96de6d471852aba53164bd/image-9.jpg)





![Element Key Transformation [3, 4, 9, 11] 19 Brad Baker - Master's Project Report Element Key Transformation [3, 4, 9, 11] 19 Brad Baker - Master's Project Report](https://slidetodoc.com/presentation_image/2d9589001f96de6d471852aba53164bd/image-19.jpg)


![Security Analysis HMAC can be attacked by forgery or key recovery attacks [3, 6] Security Analysis HMAC can be attacked by forgery or key recovery attacks [3, 6]](https://slidetodoc.com/presentation_image/2d9589001f96de6d471852aba53164bd/image-23.jpg)



![Performance analysis The performance of HTEE and the original scheme [1] are compared with Performance analysis The performance of HTEE and the original scheme [1] are compared with](https://slidetodoc.com/presentation_image/2d9589001f96de6d471852aba53164bd/image-33.jpg)





- Slides: 42

Tamper evident encryption of integers using keyed Hash Message Authentication Code Brad Baker November 16, 2009 UCCS Master’s Project Report 1 Brad Baker - Master's Project Report 11/16/2009

Agenda Introduction / Motivation Background Design Analysis Implementation Testing Conclusion / Future Work References 2 Brad Baker - Master's Project Report 11/16/2009

Section 1: Introduction 3 Brad Baker - Master's Project Report 11/16/2009

Introduction Confidentiality and integrity of data are important features in a database environment [16, 26] Integrity is also referred to as tamper detection for this project Database tampering is defined as loss of relationship between sensitive data and other data in the record Standard solutions exist including [16]: Symmetric and asymmetric encryption for confidentiality Message authentication codes and hash digests for integrity Standard solutions require end-user to build a complex process combining hash and encryption functions This project presents the “HMAC based Tamper Evident Encryption” scheme (HTEE) as an alternative solution 4 HMAC is Hashed Message Authentication Code Brad Baker - Master's Project Report 11/16/2009

Motivation Create an efficient and simple-use tamper evident encryption technique Single step, single column tamper detection Focus on processing numeric data in a database system Improve performance of the encryption operation compared to standard approaches Improve on previous work that introduced an HMAC based encryption/decryption process Investigate uses of HMAC as an encryption and key generation function 5 Brad Baker - Master's Project Report 11/16/2009
![Related Work File system and application level integrity 21 22 Forensic analysis and tamper Related Work File system and application level integrity [21, 22] Forensic analysis and tamper](https://slidetodoc.com/presentation_image/2d9589001f96de6d471852aba53164bd/image-6.jpg)
Related Work File system and application level integrity [21, 22] Forensic analysis and tamper detection [23] Notarization with hash function and reliance on audit log Analysis of how and when data was tampered Parallel encryption and authentication code [24, 25] Checksums, CRC, RAID Parity, Cryptographic file systems Open. SSL, Intrusion detection, Tripwire, Samhain Various implementations of encryption combined with MAC Original HMAC encryption scheme [1] 6 Integer encryption with HMAC Brad Baker - Master's Project Report Foundation for HTEE tamper detection 11/16/2009

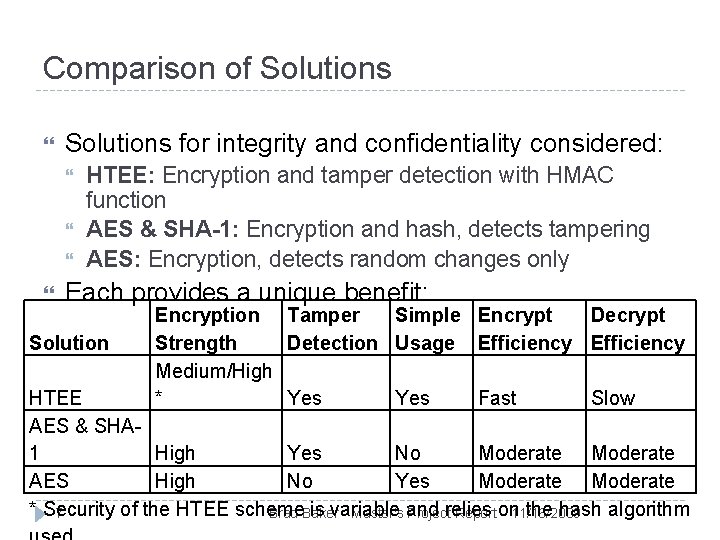
Comparison of Solutions for integrity and confidentiality considered: HTEE: Encryption and tamper detection with HMAC function AES & SHA-1: Encryption and hash, detects tampering AES: Encryption, detects random changes only Each provides a unique benefit: Solution Encryption Tamper Simple Encrypt Decrypt Strength Detection Usage Efficiency Medium/High * Yes Fast Slow HTEE AES & SHA 1 High Yes No Moderate AES High No Yes Moderate * Security of the HTEE scheme is variable and relies on the hash algorithm 7 Brad Baker - Master's Project Report 11/16/2009

Section 2: Background 8 Brad Baker - Master's Project Report 11/16/2009
![Background HMAC keyed Hash Message Authentication Code 13 Produces a secure authentication Background - HMAC – keyed Hash Message Authentication Code [13] Produces a secure authentication](https://slidetodoc.com/presentation_image/2d9589001f96de6d471852aba53164bd/image-9.jpg)
Background - HMAC – keyed Hash Message Authentication Code [13] Produces a secure authentication code (digest) using message and secret key, providing integrity and authenticity Proposed in [3], and standardized as FIPS PUB 198 [12] Unauthorized individual cannot generate digest without key Can use any underlying hash function, MD 5, SHA-1, etc. Function generates two keys from secret key The HMAC process is: 9 HMAC(key, msg) = Hash((key XOR opad) || Hash ((key XOR ipad) || msg) Where opad=“ 0 x 5 c 5 c…” and ipad=“ 0 x 3636…” Brad Baker - Master's Project Report 11/16/2009

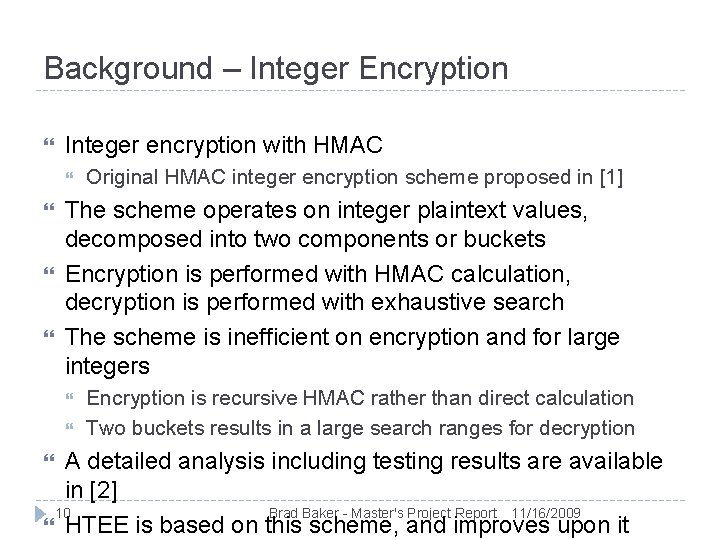
Background – Integer Encryption Integer encryption with HMAC Original HMAC integer encryption scheme proposed in [1] The scheme operates on integer plaintext values, decomposed into two components or buckets Encryption is performed with HMAC calculation, decryption is performed with exhaustive search The scheme is inefficient on encryption and for large integers Encryption is recursive HMAC rather than direct calculation Two buckets results in a large search ranges for decryption A detailed analysis including testing results are available in [2] 10 Brad Baker - Master's Project Report 11/16/2009 HTEE is based on this scheme, and improves upon it

Original HMAC process 11 Brad Baker - Master's Project Report 11/16/2009

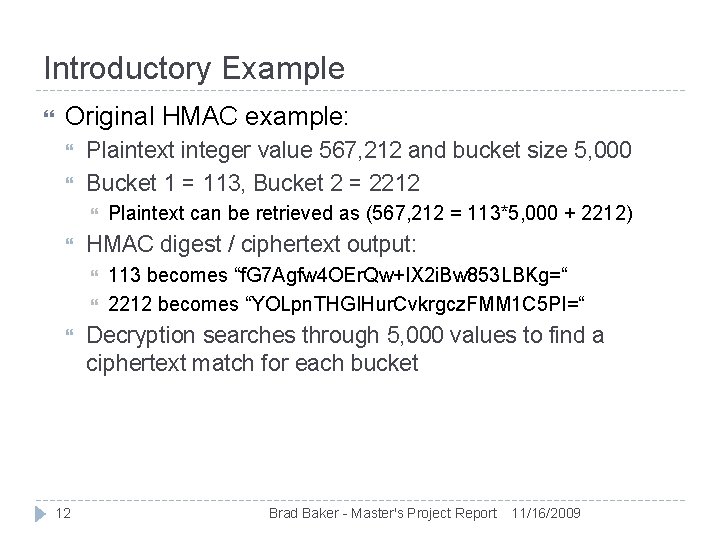
Introductory Example Original HMAC example: Plaintext integer value 567, 212 and bucket size 5, 000 Bucket 1 = 113, Bucket 2 = 2212 HMAC digest / ciphertext output: 12 Plaintext can be retrieved as (567, 212 = 113*5, 000 + 2212) 113 becomes “f. G 7 Agfw 4 OEr. Qw+IX 2 i. Bw 853 LBKg=“ 2212 becomes “YOLpn. THGIHur. Cvkrgcz. FMM 1 C 5 PI=“ Decryption searches through 5, 000 values to find a ciphertext match for each bucket Brad Baker - Master's Project Report 11/16/2009

Section 3: Design 13 Brad Baker - Master's Project Report 11/16/2009

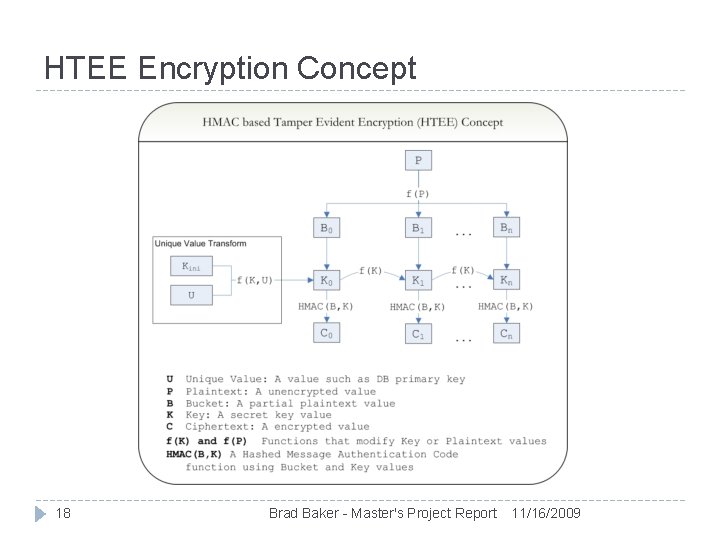
HTEE Design Processes positive integer values Decomposition of plaintext into multiple buckets of size 1, 000 For example: 2, 412, 345, 678 becomes four buckets: In the original scheme, a 50, 000 bucket size would make two buckets: Bucket 1 = 48246; Bucket 2 = 45678; Key transformation based on a unique value related to plaintext Bucket 1 = 2; Bucket 2 = 412; Bucket 3 = 345; Bucket 4 = 678; Each encryption operation uses a different key Encryption keys depend on original key and unique related data The unique value is any data that must remain the same in 14 Brad Baker - Master's Project Report 11/16/2009 relation to the plaintext, for example:

HTEE Design Encryption operation: Decryption operation: Search for digest match between ciphertext and all values (0999) Tamper detection: Calculate HMAC digest for each bucket Decryption operation cannot find matching value Two key transformation functions used: element and bucket Element transformation creates a key for each plaintext 15 HMAC executed recursively four times with unique value and original key Bucket transformation creates key for each bucket value HMAC executed iteratively with ciphertext output and original key Brad Baker - Master's Project Report 11/16/2009

HTEE Design HMAC digests for all buckets in a plaintext are concatenated to form ciphertext Decryption follows key generation process, plus an exhaustive search for ciphertext match. No match indicates data was tampered with, that the ciphertext or unique related data have changed The HTEE process is: 16 HTEE(Plaintext, Key, Unique) = HMAC(Bucket 1, f. Key(Key, Unique)) || HMAC(Bucket 2, f. Key(Key, Unique)) || … Bucket N Where {f. Key} is key transformation (element and bucket) and Bucket 1 through Bucket N are decomposed from Plaintext Brad Baker - Master's Project Report 11/16/2009

Example of HTEE Record contents (DATA value is sensitive, must be encrypted): ID = 1001; DATA = 654321 After decomposition of DATA value: bucket 1 = 654; bucket 2 = 321 Original Key, 512 bit: fw. We 6 MNL 5 WC 9 g. Rg. Cf. Vb. Usu. FLe. X 8 Ifw. Kbnk. Wml. Khj 5 Tx 2 Ods+Vkm. KS 73 Ae. Ft 0 Es. Xy+zmf. WEsy. OEa. KSx/o. YMSm. RA== Generated keys for buckets (dependent on ID value and original key): Bucket 1 key: qi 5 K 5 Jm. BNRf. Ou. Pf 8 q. Qvg. PVVZ 5 n. HZjlgo. Db 8 un 4 GS/Nx. Fhb. RNdn. E 5 B 80 k. Pe 3 rpq. Iv. HRDzd. Zsi. Empk+2 Ozcb 5 y. Xg== Bucket 2 key: yl. T 5 v. Ka. Gkdc 1 XMt. W 0 z+HOb 1 Td 2 eq. Lkrkm. YE 1 F 8649/yp. C+A 9 VVnmcdm. OWCg. Nvy 6 fg. ZL 83 EWFt. E 12 c. Tk. Hz. SQ 97 Q== Ciphertext result from HMAC (bucket, key): Bucket 1 cipher: Bucket 2 cipher: Final Ciphertext: Ziuytd 9 t 8 Vn 1 h 5 ldq. Zjv 57 s. Te 2 k= uk/ACt. Sc. X 2 ox. JUPy. EPd. PWSPCXQk= Ziuytd 9 t 8 Vn 1 h 5 ldq. Zjv 57 s. Te 2 k=uk/ACt. Sc. X 2 ox. JUPy. EPd. PWSPCXQk = Final Output: ID = 1001; CIPHER = Ziuytd 9 t 8 Vn 1 h 5 ldq. Zjv 57 s. Te 2 k=uk/ACt. Sc. X 2 ox. JUPy. EPd. PWSPCXQk= 17 Brad Baker - Master's Project Report 11/16/2009

HTEE Encryption Concept 18 Brad Baker - Master's Project Report 11/16/2009
![Element Key Transformation 3 4 9 11 19 Brad Baker Masters Project Report Element Key Transformation [3, 4, 9, 11] 19 Brad Baker - Master's Project Report](https://slidetodoc.com/presentation_image/2d9589001f96de6d471852aba53164bd/image-19.jpg)
Element Key Transformation [3, 4, 9, 11] 19 Brad Baker - Master's Project Report 11/16/2009

Bucket Key Transformation 20 Brad Baker - Master's Project Report 11/16/2009

Section 4: Analysis 21 Brad Baker - Master's Project Report 11/16/2009

Security Analysis Cryptographic strength of HTEE is based on HMAC Cryptographic strength of HMAC is based on underlying hash function [3, 4, 5] Key transformation and encryption use HMAC function For this project, SHA-1 is used as underlying hash Hash can be changed for additional security of HMAC [3] HMAC proven secure from forgery if hash compression operation is a pseudo-random function [4, 7, 11] HMAC is not susceptible to hash collision attacks that affect MD 5 and SHA-1 [3, 4, 5] 22 Collisions are still produced but more difficult to attack Brad Baker - Master's Project Report 11/16/2009
![Security Analysis HMAC can be attacked by forgery or key recovery attacks 3 6 Security Analysis HMAC can be attacked by forgery or key recovery attacks [3, 6]](https://slidetodoc.com/presentation_image/2d9589001f96de6d471852aba53164bd/image-23.jpg)
Security Analysis HMAC can be attacked by forgery or key recovery attacks [3, 6] The birthday paradox controls probability to find an HMAC collision [3, 5, 11, 15] Key recovery attacks typically have chosen or known plaintext For SHA-1, 280 (message, digest) pairs from HMAC are needed Research shows key recovery attacks that are better than brute force, but still worse than birthday attack [6, 7, 10] For the HTEE scheme key recovery attacks are the primary concern 23 Forgeries are less of a concern as they could only break a Brad Baker - Master's Project Report 11/16/2009 single record’s tamper detection capability

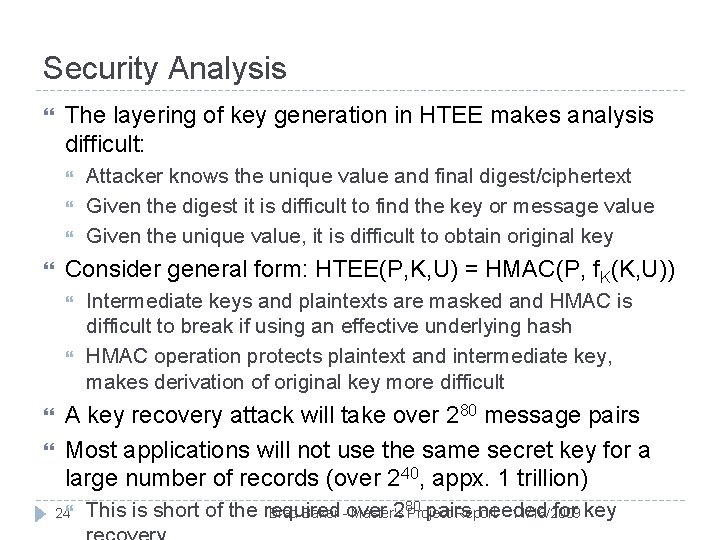
Security Analysis The layering of key generation in HTEE makes analysis difficult: Consider general form: HTEE(P, K, U) = HMAC(P, f. K(K, U)) Attacker knows the unique value and final digest/ciphertext Given the digest it is difficult to find the key or message value Given the unique value, it is difficult to obtain original key Intermediate keys and plaintexts are masked and HMAC is difficult to break if using an effective underlying hash HMAC operation protects plaintext and intermediate key, makes derivation of original key more difficult A key recovery attack will take over 280 message pairs Most applications will not use the same secret key for a large number of records (over 240, appx. 1 trillion) 24 80 pairs needed for key This is short of the required over 2 Brad Baker - Master's Project Report 11/16/2009

Tamper Detection Analysis HTEE creates a distinct key sequence based on the unique value related to plaintext Identical keys only occur on hash collisions If ciphertext or unique value are changed then the key sequence or HMAC output will differ This is improbable unless a very large number of records are processed Tamper detection will only fail if the original and changed HTEE process produce a collision Probability of collision for each bucket is appx. 3. 42 x 10 -43 25 Based on the birthday attack with 1, 000 values [15, 16] (-k^2/2 N)} with {k = 1000} and {N = Probability is{P = 1 – e Brad Baker - Master's Project Report 11/16/2009 160

Section 5: Implementation 26 Brad Baker - Master's Project Report 11/16/2009

Implementation HTEE process implemented as a Postgre. SQL add-on and a command line program Implemented versions: Encryption: htee_enc(plaintext, unique value) Decryption: htee_dec(ciphertext, unique value) Simple operation, example SQL for encryption: Command line program used for validation and flat file processing Postgre. SQL add-on is considered the primary implementation Two functions added to Postgre. SQL server: Built in the C language Microsoft Visual C++ 2008 Express Edition Postgre. SQL server versions 8. 3. 8 and 8. 4. 1 SELECT htee_enc(data, unique) FROM test Maximum of six buckets or 9 x 1017 integer value supported 27 Brad Baker - Master's Project Report 11/16/2009

Implementation SHA-1 used for underlying hash function Ciphertext output for six buckets is 168 bytes of base 64 encoded data Specifies use of 512 bit key, blocks of 160 bit ciphertext output Input key is 88 base 64 characters, output is 28 base 64 characters per bucket value Comparable AES output is 116 bytes, HTEE is a 44% increase Compared to plaintext data, a 21 -fold increase Several challenges encountered: 28 Extending Postgre. SQL in Windows environment Interfacing with the Postgre. SQL backend Brad Baker - Master's Project Report 11/16/2009

Section 6: Testing 29 Brad Baker - Master's Project Report 11/16/2009

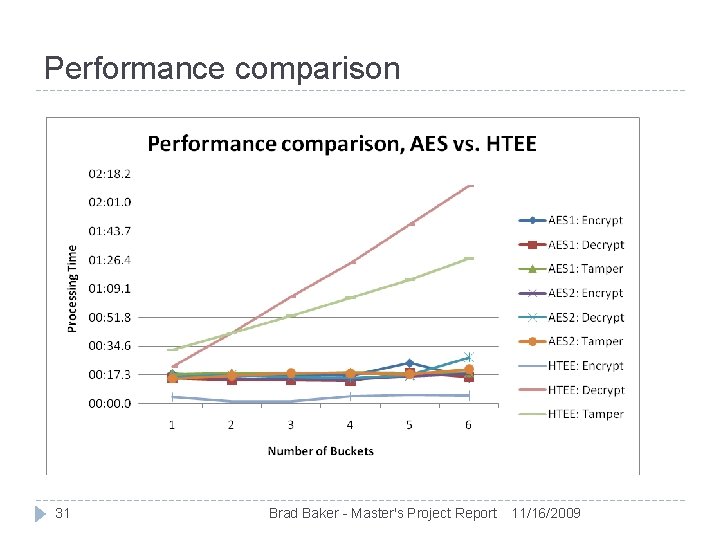
Testing Compared three methods for encryption: Tested six datasets, 20, 000 random integers in each Basic AES (aes 1): Does not provide tamper detection AES & unique value (aes 2): Provides tamper detection HTEE scheme: Provides tamper detection Each dataset with different number of buckets, one through six Results verified tamper detection with AES 2 and HTEE methods HTEE on average was four times faster on encryption but four times slower on decryption than AES 30 Brad Baker - Master's Project Report 11/16/2009

Performance comparison 31 Brad Baker - Master's Project Report 11/16/2009

HTEE performance details 32 Brad Baker - Master's Project Report 11/16/2009
![Performance analysis The performance of HTEE and the original scheme 1 are compared with Performance analysis The performance of HTEE and the original scheme [1] are compared with](https://slidetodoc.com/presentation_image/2d9589001f96de6d471852aba53164bd/image-33.jpg)
Performance analysis The performance of HTEE and the original scheme [1] are compared with algorithmic analysis HTEE is significantly more efficient on encryption, and decryption for large numbers [2] Original scheme increases with n 0. 5, HTEE increases with log 1000(n) Testing verifies that HTEE is much faster for similar datasets The large bucket size required for two buckets becomes Encryption prohibitively expensive to calculate decryption 33 Scheme Relative complexity HTEE Encryption 2*log 1000(n) Constant HTEE Decryption 1001*log 1000(n) Constant Original Encryption 2*n 0. 5 Polynomial 0. 5 Original Decryption 2*n Polynomial Brad Baker - Master's Project Report 11/16/2009

Section 7: Conclusion 34 Brad Baker - Master's Project Report 11/16/2009

Lessons Learned Encountered and solved implementation challenges Challenges in algorithm design Open. SSL package proved difficult to generate simple random strings Effect of implementation on security Properly protecting key information in the transformation process Adapting key transformation for a database environment Created custom key generation for random 512 bit keys Null bytes, memory management, hash processing Postgre. SQL extension in Windows environment Interfacing with Postgre. SQL backend, operating on data types Processing time exposing information about plaintext values Effect of small input values 35 Can be mitigated by expanding the size of the unique value Brad Baker - Master's Project Report 11/16/2009

Conclusion HTEE provides strong tamper detection and data integrity HTEE provides strong confidentiality Security based on the underlying HMAC and hash functions Can be improved with stronger hash functions For regulatory requirements recommend AES encryption HTEE is more efficient on encryption and less efficient on decryption than AES Ideal for encryption-heavy applications where tamper detection is needed Ciphertext and other related data are tied together Examples include archival and auditing systems, including financial information Additional information available: http: //cs. uccs. edu/~gsc/pub/master/bbaker/ 36 Brad Baker - Master's Project Report 11/16/2009

Future Work Plaintext value range: HTEE scheme is limited to positive integer values Future work can expand operation to negative values, floating point values, or ASCII encoded data Floating point can be encoded with multiplication by a positive factor of 10, the factor must be stored in the ciphertext data Security Proof A conceptual analysis of cryptographic strength is presented Future work can prove of the security of HTEE, focused on: 37 HMAC as a pseudo-random function Brad Baker - Master's Project Report 11/16/2009 Effect of unique value and bucket values on HMAC randomness

Questions? 38 Brad Baker - Master's Project Report 11/16/2009

References Dong Hyeok Lee; You Jin Song; Sung Min Lee; Taek Yong Nam; Jong Su Jang, "How to Construct a New Encryption Scheme Supporting Range Queries on Encrypted Database, " Convergence Information Technology, 2007. International Conference on , vol. , no. , pp. 1402 -1407, 21 -23 Nov. 2007 URI: http: //ieeexplore. ieee. org/stamp. jsp? arnumber=4420452&isnumber=44 20217 Brad Baker, "Analysis of an HMAC Based Database Encryption Scheme, " UCCS Summer 2009 Independent study July. 2009 URI: http: //cs. uccs. edu/~gsc/pub/master/bbaker/doc/final_paper_bbaker_cs 592. doc Mihir Bellare; Ran Canetti; Hugo Krawczyk; “Keying Hash Functions for Message Authentication”, IACR Crypto 1996 URI: http: //cseweb. ucsd. edu/users/mihir/papers/kmd 5. pdf Mihir Bellare, “New Proofs for NMAC and HMAC: Security without Collision. Resistance, ” IACR Crypto 2006 URI: http: //eprint. iacr. org/2006/043. pdf Mihir Bellare, “Attacks on SHA-1, ” 2005 URI: http: //www. openauthentication. org/pdfs/Attacks%20 on%20 SHA-1. pdf Pierre-Alain Fouque; Gaëtan Leurent; Phong Q. Nguyen, "Full Key-Recovery Attacks on HMAC/NMAC-MD 4 and NMAC-MD 5, " IACR Crypto 2007 URI: ftp: //ftp. di. ens. fr/pub/users/pnguyen/Crypto 07. pdf Scott Contini; Yiqun Lisa Yin, “Forgery and Partial Key-Recovery Attacks on HMAC and NMAC using Hash Collisions (Extended Version), ” 2006 URI: http: //eprint. iacr. org/2006/319. pdf 1. 2. 3. 4. 5. 6. 7. 39 Brad Baker - Master's Project Report 11/16/2009

References 8. Hyrum Mills; Chris Soghoian; Jon Stone; Malene Wang, “NMAC: Security Proof, ” 2004 URI: http: //www. cs. jhu. edu/~astubble/dss/proofslides. pdf 9. Ran Canetti, “The HMAC construction: A decade later, ” 2007 URI: http: //people. csail. mit. edu/canetti/materials/hmac-10. pdf 10. Yu Sasaki, “A Full Key Recovery Attack on HMAC-AURORA-512, ” 2009 URI: http: //eprint. iacr. org/2009/125. pdf 11. Jongsung Kim; Alex Biryukov; Bart Preneel; and Seokhie Hong, “On the Security of HMAC and NMAC Based on HAVAL, MD 4, MD 5, SHA-0 and SHA-1”, 2006 URI: http: //eprint. iacr. org/2006/187. pdf 12. NIST, March 2002. FIPS Pub 198 HMAC specification. URI = http: //csrc. nist. gov/publications/fips 198/fips-198 a. pdf 13. Wikipedia, October 2009. HMAC reference material. URI= http: //en. wikipedia. org/wiki/Hmac 14. Wikipedia, October 2009. SHA-1 reference material. URI= http: //en. wikipedia. org/wiki/SHA-1 40 Brad Baker - Master's Project Report 11/16/2009

References 15. 16. 17. 18. 19. 20. 21. 41 Wikipedia, October 2009. Birthday Attack reference. URI= http: //en. wikipedia. org/wiki/Birthday_attack Forouzan, Behrouz A. 2008. Cryptography and Network Security. Mc. Graw Hill higher Education. ISBN 978 -0 -07 -287022 -0 Simon Josefsson, 2006. GPL implementation of HMAC-SHA 1. URI= http: //www. koders. com/c/fid. F 9 A 73606 BEE 357 A 031 F 14689 D 03 C 089777847 EFE. as px Scott G. Miller, 2006. GPL implementation of SHA-1 hash. URI= http: //www. koders. com/c/fid 716 FD 533 B 2 D 3 ED 4 F 230292 A 6 F 9617821 C 8 FDD 3 D 4. a spx Bob Trower, August 2001. Open source base 64 encoding implementation, adapted for test program. URI= http: //base 64. sourceforge. net/b 64. c Postgre. SQL, October 2009. Server Documentation. URI= http: //www. postgresql. org/docs/8. 4/static/index. html Gopalan Sivathanu; Charles P. Wright; and Erez Zadok, “Ensuring data integrity in storage: techniques and applications, ” Workshop On Storage Security And Survivability, Nov. 2005 URI = http: //doi. acm. org/10. 1145/1103780. 1103784 Brad Baker - Master's Project Report 11/16/2009

References 22. Vishal Kher; Yongdae Kim, “Securing Distributed Storage: Challenges, Techniques, and Systems” Workshop On Storage Security And Survivability, Nov. 2005 URI = http: //doi. acm. org/10. 1145/1103780. 1103783 23. Kyriacos Pavlou; Richard Snodgrass, “Forensic Analysis of Database Tampering, ” ACM Transactions on Database Systems (TODS), 2008 URI = http: //doi. acm. org/10. 1145/1412331. 1412342 24. Elbaz, R. ; Torres, L. ; Sassatelli, G. ; Guillemin, P. ; Bardouillet, M. ; Rigaud, J. B. , "How to Add the Integrity Checking Capability to Block Encryption Algorithms, " Research in Microelectronics and Electronics 2006, Ph. D. , vol. , no. , pp. 369 -372, 0 -0 0 URI: http: //ieeexplore. ieee. org/stamp. jsp? arnumber=1689972&isnumber=35 631 25. Elbaz, R. ; Torres, L. ; Sassatelli, G. ; Guillemin, P. ; Bardouillet, M. , "PE-ICE: Parallelized Encryption and Integrity Checking Engine, " Design and Diagnostics of Electronic Circuits and systems, 2006 IEEE , vol. , no. , pp. 141 -142, 0 -0 0 URI: http: //ieeexplore. ieee. org/stamp. jsp? arnumber=1649595&isnumber=34 591 26. Wikipedia, October 2009. Information Security Reference. URI= http: //en. wikipedia. org/wiki/Information_security 42 Brad Baker - Master's Project Report 11/16/2009