System Models Outline Introduction Architectural models Fundamental models















- Slides: 27

System Models

Outline • • Introduction Architectural models Fundamental models Guideline

Introduction • An architectural model defines – the way in which the components of systems interact with one another and – the way in which they are mapped onto an underlying network of computers • There are three fundamental models that help to reveal key problems for the designers of distributed system.

Difficulties and threats for distributed systems

Difficulties and threats for distributed systems • Widely varying modes of use • Wide range of system environments • Internal problems: – non-synchronized clocks – conflicting data updates – many modes of hardware and software failure involving the individual components of a system

Architectural models • An architectural model of a distributed system – first simplifies and abstracts the functions of the individual components of a DS and – then it considers: • The placement of the components across a network of computers • The interrelationships between the components.

Architectural models (cont. ) • • • Software layers System architectures Variations on the client-server model Interfaces and objects Design requirements for distributed architectures

Software layers • • Applications, services Middleware Operating system Computer and network hardware

System architectures • • Client-server model Services provided by multiple servers Proxy srvers and caches Peer processes

Variations on the client-server model • • • Mobile code Mobile agents Network computers Thin client Mobile devices and spontaneous networking The X-11 window system

Design requirements for distributed architectures

Design requirements for distributed architectures • Performance issues • Use of caching and replication • Dependability issues

Performance issues

Performance issues • Responsiveness – Users of interactive aplication require a fast and consistent response to interaction. • Throughput – The rate at which computational work is done. • Quality of services – The ability to meet the deadlines of users need. • Balancing computer loads – In some case load balancing may involve moving partially-completed work as the loads on hosts changes.

Use of caching and replication • The performance issues often appear to be major obstacles to the successful deployment of DS, but much progress has been made in the design of systems that overcome them by the use of data replication and caching.

Dependability issues

Dependability issues • The dependability of computer systems as correctness, security and fault tolerance • Fault tolerance: reliability is achieved through redundancy. • Security: the architectural impact of the requirement for security concerns the need to locate sensitive data and other resources only in computers that can be effectively secured against attack

Fundamental Models • A) Interaction model • B) Failure model • C) Security model

A) Interaction model • • • Performance of communication channels Computer clocks and timing events Two variants of the interaction model Agreement in pepperland Event ordering

Performance of communication channels • Communication performance is often a limiting characteristic. • The delay between the sending of a message by one process and its receipt by another is referred to as latency. • Bandwidth • Jitter is the variation in the time taken to deliver a series of messages.

Computer clock and timing event • It is impossible to maintain a single global notion of time. • There are several approaches to correcting the times on computer clocks. (from GPS)

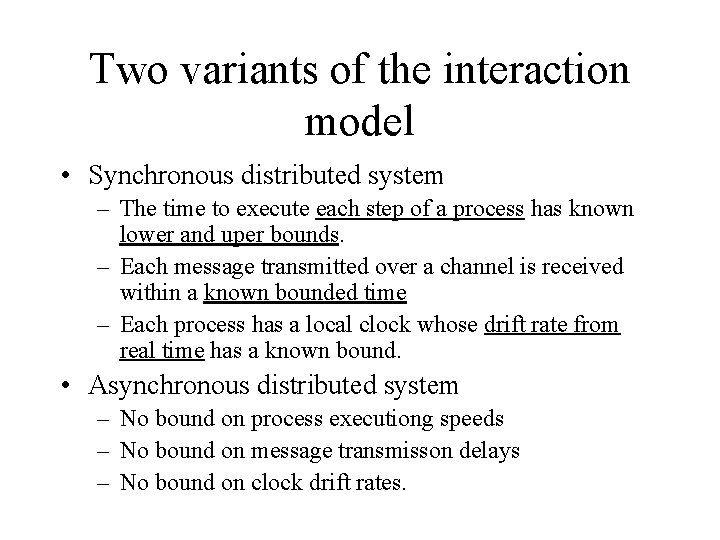
Two variants of the interaction model • Synchronous distributed system – The time to execute each step of a process has known lower and uper bounds. – Each message transmitted over a channel is received within a known bounded time – Each process has a local clock whose drift rate from real time has a known bound. • Asynchronous distributed system – No bound on process executiong speeds – No bound on message transmisson delays – No bound on clock drift rates.

Agreement in pepperland • The pepperland divisions need to agree on which of them will lead the charge against the Blue Meanies, and when the charge will take place. • In asynchronous pepperland, the messengers are very variable in their speed. • The divisions know some useful constraints: every message takes at least minutes and at most max minutes to arive. • The leading division sends a message ’charge!’, then waits for minutes, then it charges. • The other division’s charge is guaranteed to be after the leading division’s, but no more than (max-min) after it.

Event ordering • In many cases, we are interested in knowing whether an event (sending or receiving a message) at one process occurred before, after or concurrently with another event at another process. • The execution of a system can be described in terms of events and their ordering despite the lack of accurate clocks.

B) Failure model • • Omission failures Arbitrary failures Failure detection Impossibility of reaching agreement in the presence of failure • Masking failure • Reliability of one to one communication

C) Security model • • • Protecting objects Securing processes and their interactions The enemy Defeating security threats Other possible threats from the enemy The uses of security models

Guideline • Most DS are arranged according to one of a variety of architectural models. • The fundamental models – interaction, failure, and security – identify the common characteristics of the basic components from which distributed systems are constructed.