System Address RegistersMemory Management Registers Four memory management



- Slides: 35

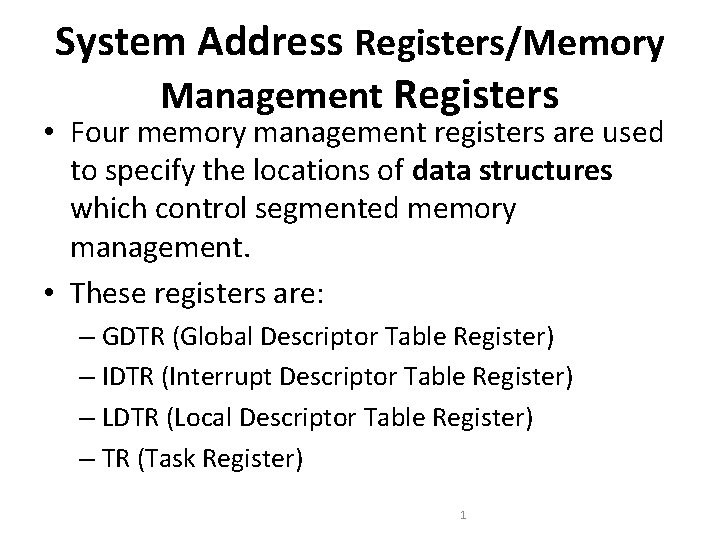
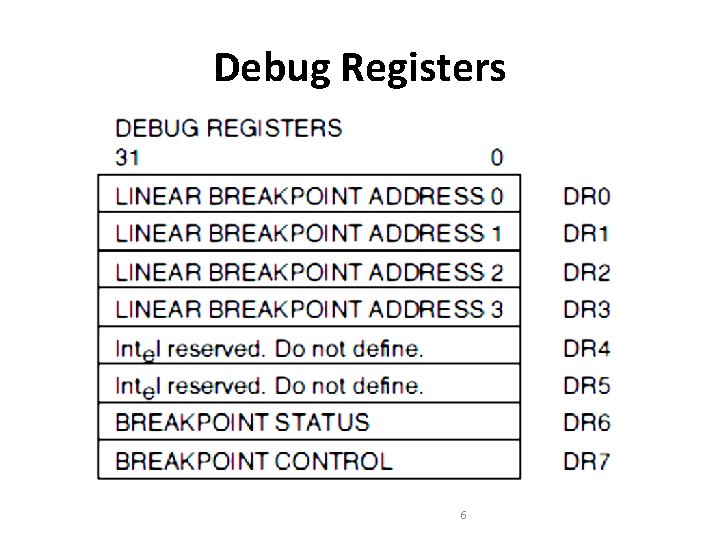
System Address Registers/Memory Management Registers • Four memory management registers are used to specify the locations of data structures which control segmented memory management. • These registers are: – GDTR (Global Descriptor Table Register) – IDTR (Interrupt Descriptor Table Register) – LDTR (Local Descriptor Table Register) – TR (Task Register) 1

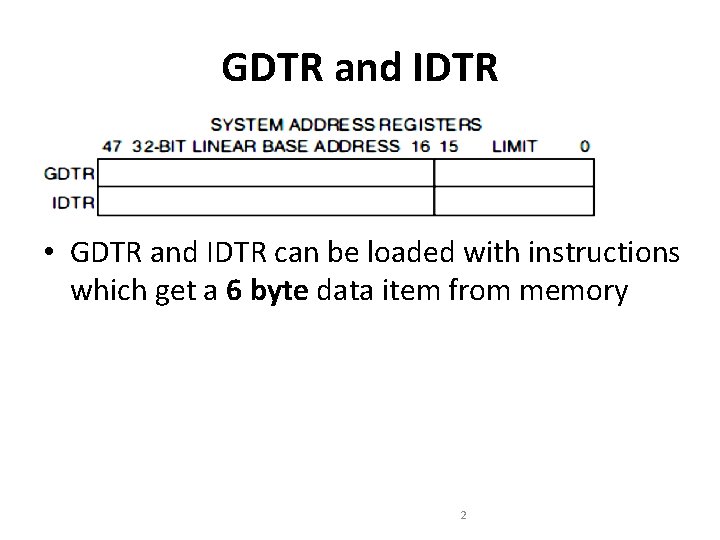
GDTR and IDTR • GDTR and IDTR can be loaded with instructions which get a 6 byte data item from memory 2

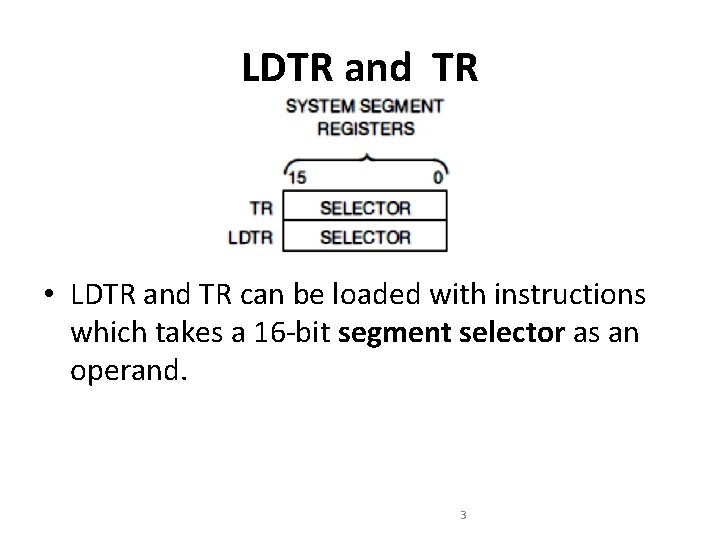
LDTR and TR • LDTR and TR can be loaded with instructions which takes a 16 -bit segment selector as an operand. 3

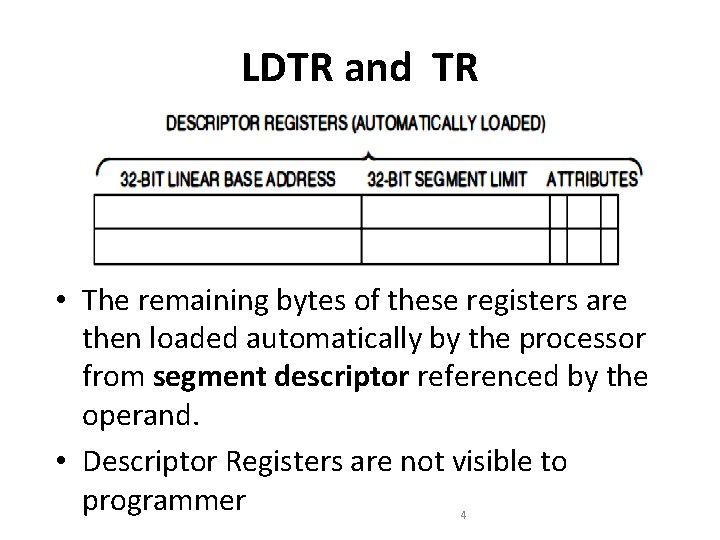
LDTR and TR • The remaining bytes of these registers are then loaded automatically by the processor from segment descriptor referenced by the operand. • Descriptor Registers are not visible to programmer 4

Debug Registers • Debugging of 80386 allows data access breakpoints as well as code execution breakpoints. • 80386 contains 6 debug registers to specify – 4 breakpoints – Breakpoint Control options – Breakpoint Status

Debug Registers 6

Linear Breakpoint Address Registers • The breakpoint addresses specified are 32 -bit linear addresses • While debugging, Intel 386 h/w continuously compares the linear breakpoint addresses in DR 0 -DR 3 with the linear addresses generated by executing software. 7

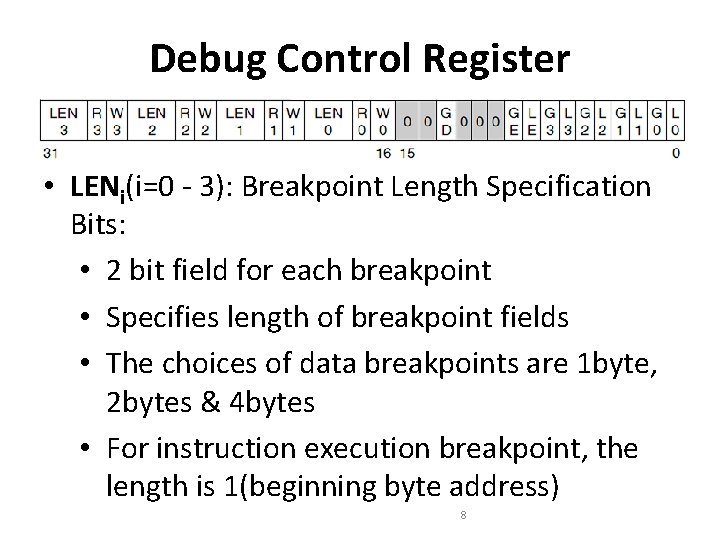
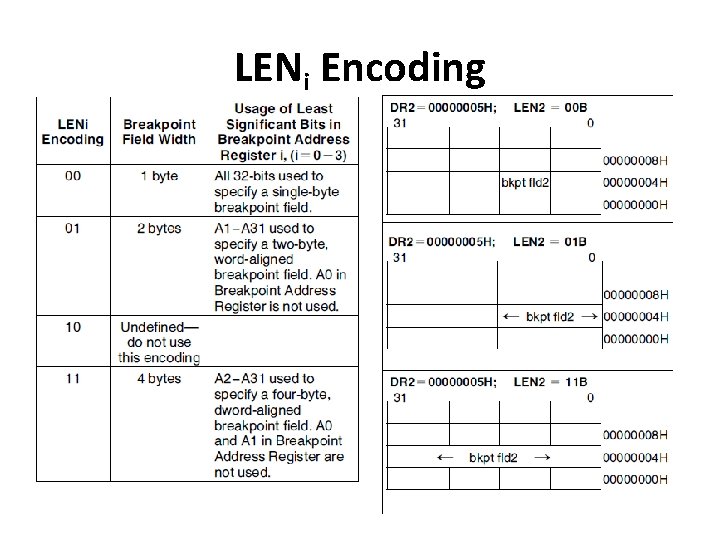
Debug Control Register • LENi(i=0 - 3): Breakpoint Length Specification Bits: • 2 bit field for each breakpoint • Specifies length of breakpoint fields • The choices of data breakpoints are 1 byte, 2 bytes & 4 bytes • For instruction execution breakpoint, the length is 1(beginning byte address) 8

LENi Encoding

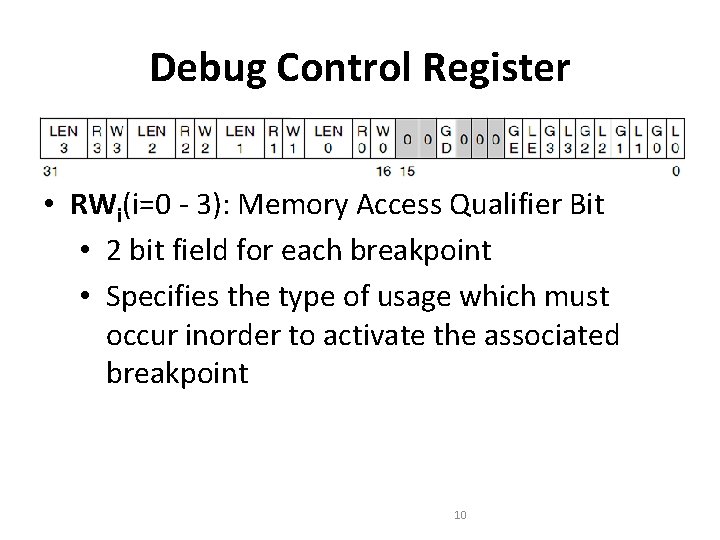
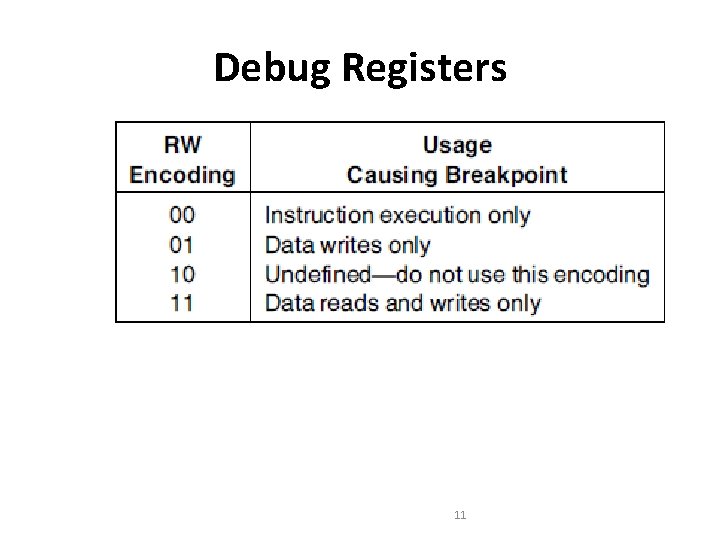
Debug Control Register • RWi(i=0 - 3): Memory Access Qualifier Bit • 2 bit field for each breakpoint • Specifies the type of usage which must occur inorder to activate the associated breakpoint 10

Debug Registers 11

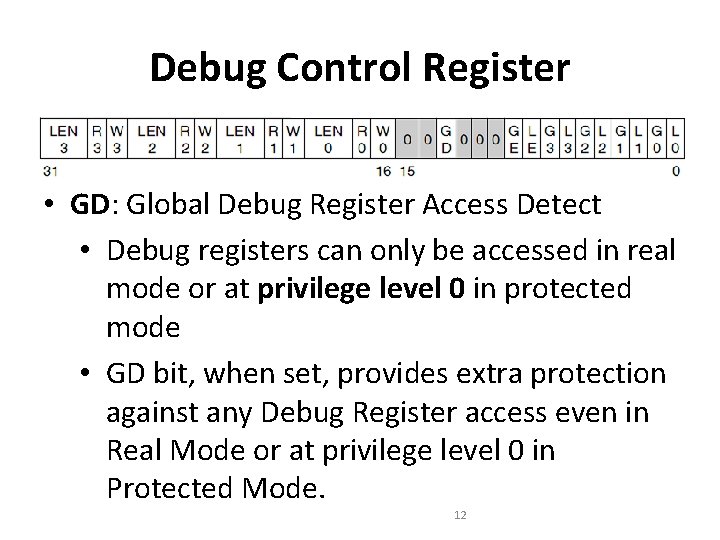
Debug Control Register • GD: Global Debug Register Access Detect • Debug registers can only be accessed in real mode or at privilege level 0 in protected mode • GD bit, when set, provides extra protection against any Debug Register access even in Real Mode or at privilege level 0 in Protected Mode. 12

Debug Control Register • GD: Global Debug Register Access Detect • This additional protection feature is provided to guarantee that a software debugger can have full control over the Debug Register resources when required. • The GD bit, when set, causes an exception 1 fault if an instruction attempts to read or write any Debug Register. • The GD bit is then automatically cleared when the exception 1 handler is invoked, allowing the exception 1 handler free access to the debug registers. 13

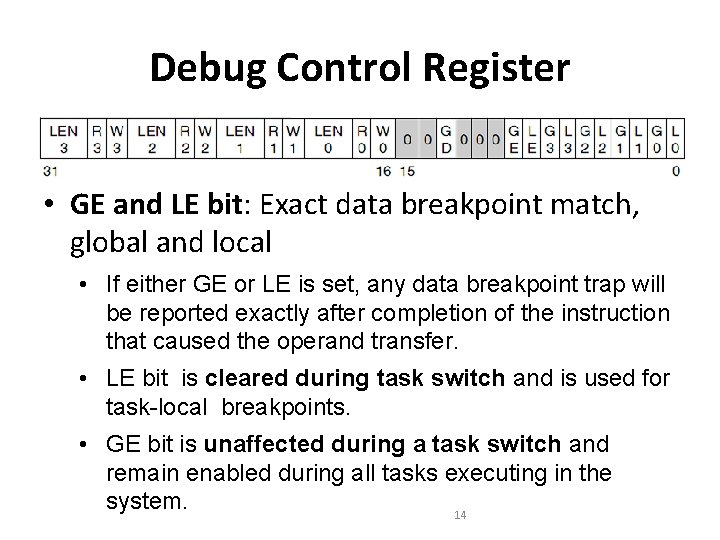
Debug Control Register • GE and LE bit: Exact data breakpoint match, global and local • If either GE or LE is set, any data breakpoint trap will be reported exactly after completion of the instruction that caused the operand transfer. • LE bit is cleared during task switch and is used for task-local breakpoints. • GE bit is unaffected during a task switch and remain enabled during all tasks executing in the system. 14

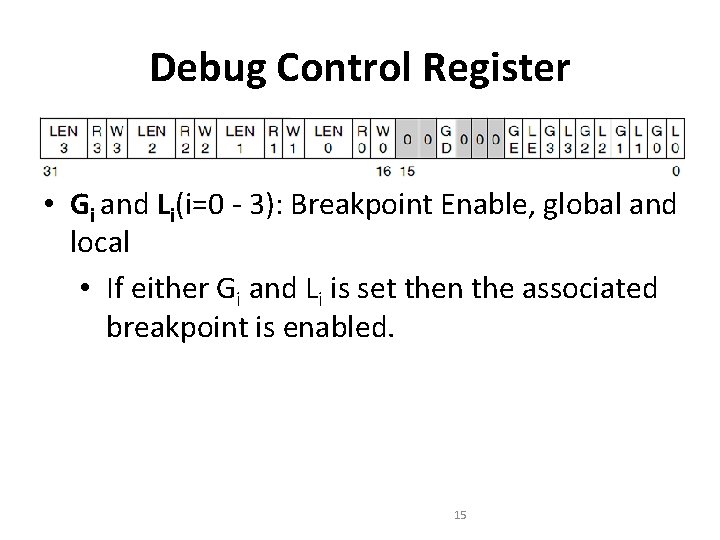
Debug Control Register • Gi and Li(i=0 - 3): Breakpoint Enable, global and local • If either Gi and Li is set then the associated breakpoint is enabled. 15

Debug Status Register • A Debug Status Register allows the exception 1 handler to easily determine why it was invoked. • It can be invoked as a result of one of several events: 1) DR 0 Breakpoint fault/trap. 2) DR 1 Breakpoint fault/trap. 3) DR 2 Breakpoint fault/trap. 4) DR 3 Breakpoint fault/trap. 5) Single-step (TF) trap. 6) Task switch trap. 7) Fault due to attempted debug register access when GD = 1.

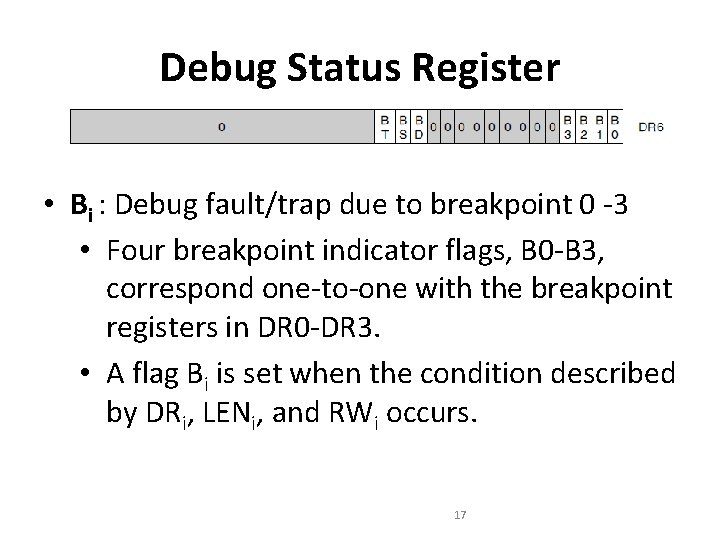
Debug Status Register • Bi : Debug fault/trap due to breakpoint 0 -3 • Four breakpoint indicator flags, B 0 -B 3, correspond one-to-one with the breakpoint registers in DR 0 -DR 3. • A flag Bi is set when the condition described by DRi, LENi, and RWi occurs. 17

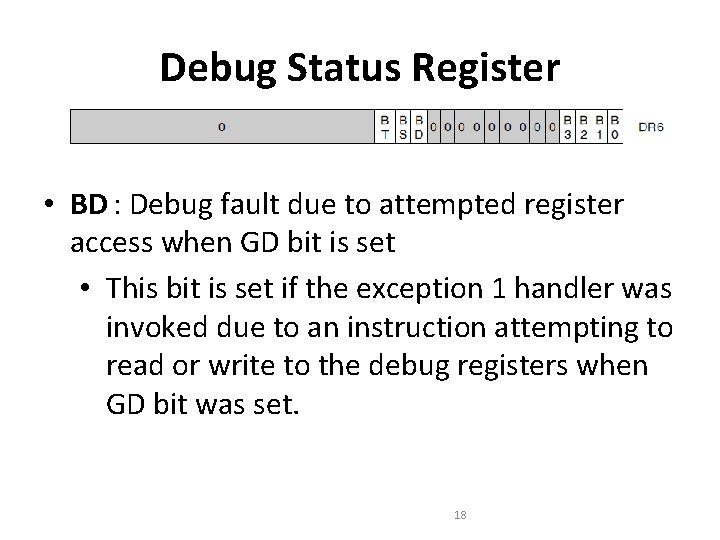
Debug Status Register • BD : Debug fault due to attempted register access when GD bit is set • This bit is set if the exception 1 handler was invoked due to an instruction attempting to read or write to the debug registers when GD bit was set. 18

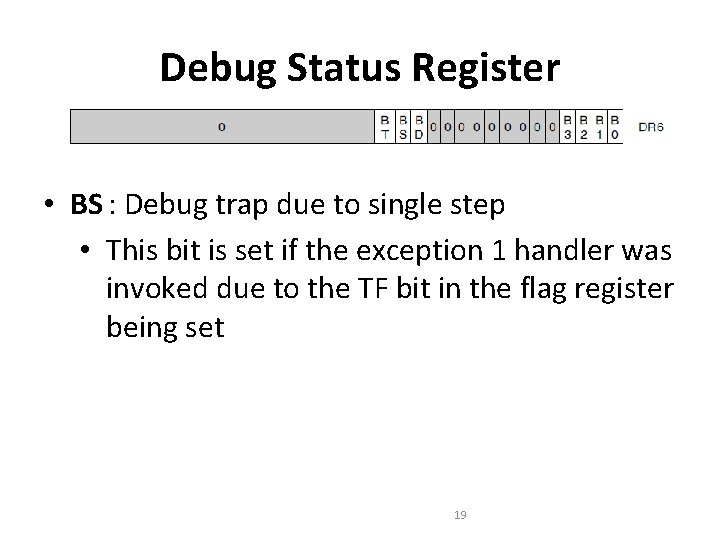
Debug Status Register • BS : Debug trap due to single step • This bit is set if the exception 1 handler was invoked due to the TF bit in the flag register being set 19

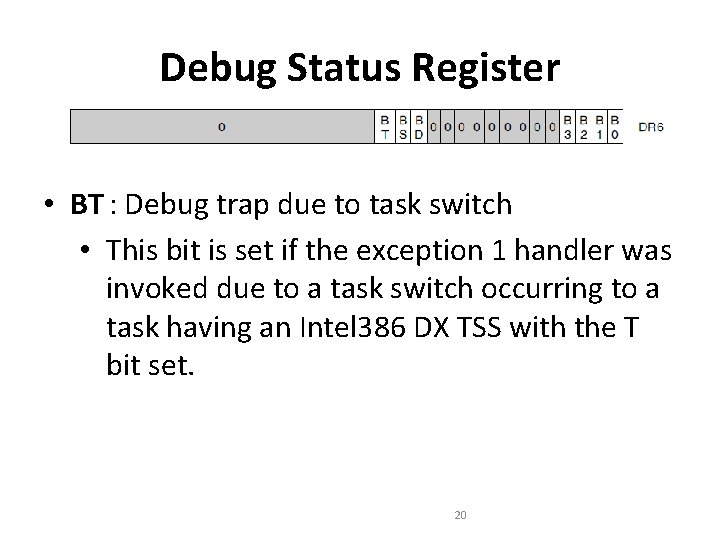
Debug Status Register • BT : Debug trap due to task switch • This bit is set if the exception 1 handler was invoked due to a task switch occurring to a task having an Intel 386 DX TSS with the T bit set. 20

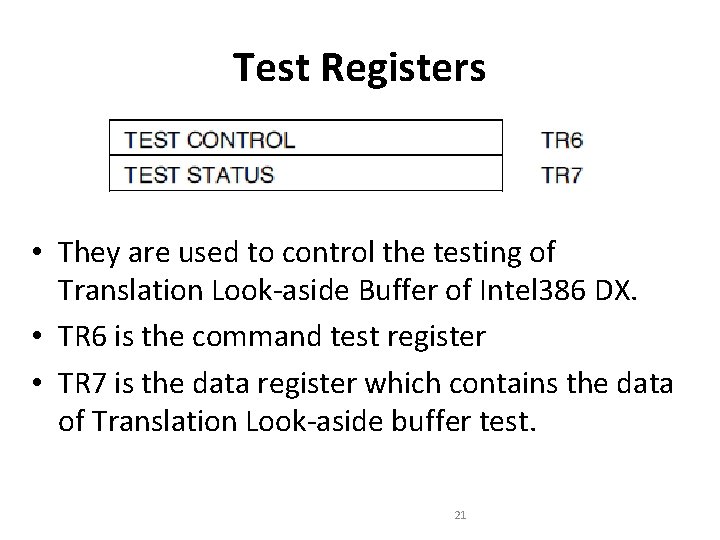
Test Registers • They are used to control the testing of Translation Look-aside Buffer of Intel 386 DX. • TR 6 is the command test register • TR 7 is the data register which contains the data of Translation Look-aside buffer test. 21

Programming Model • The basic programming model consists of the following aspects: – Registers – Instruction Set – Addressing Modes – Data Types – Memory Organization – Interrupts and Exceptions 22

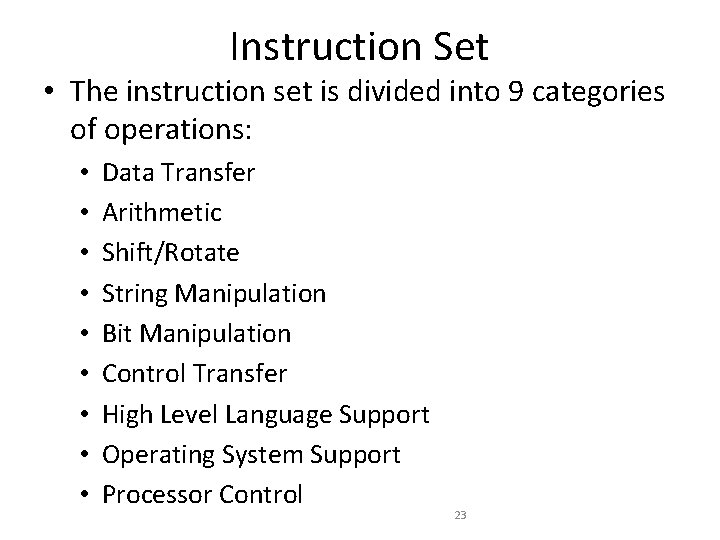
Instruction Set • The instruction set is divided into 9 categories of operations: • • • Data Transfer Arithmetic Shift/Rotate String Manipulation Bit Manipulation Control Transfer High Level Language Support Operating System Support Processor Control 23

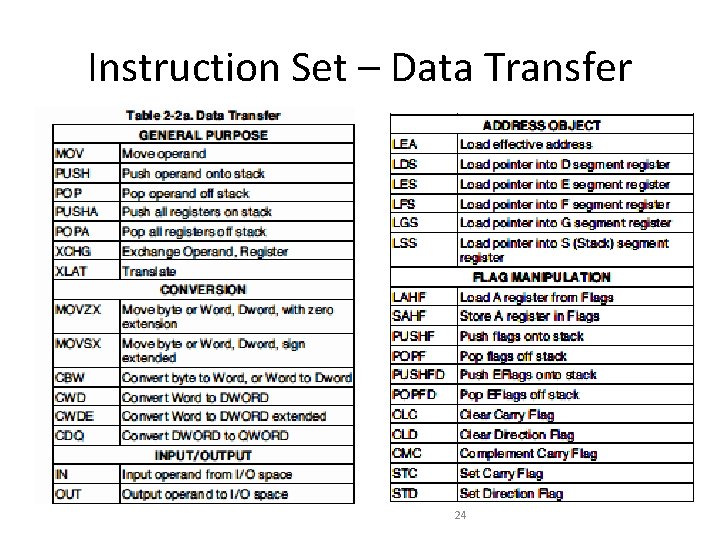
Instruction Set – Data Transfer 24

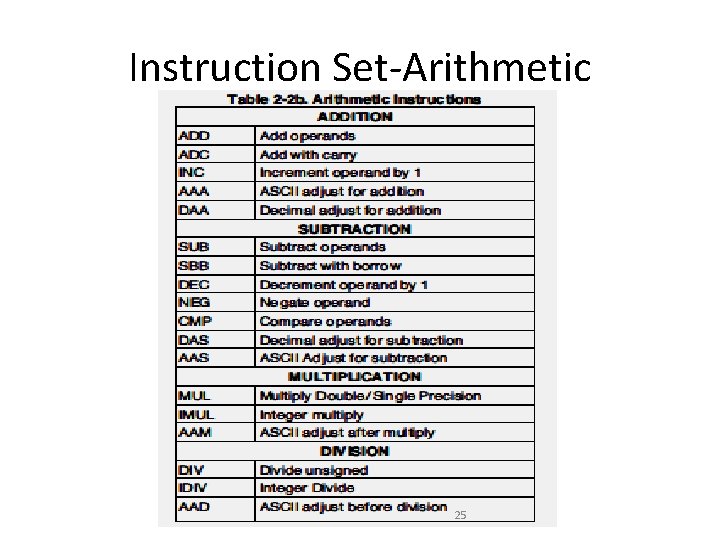
Instruction Set-Arithmetic 25

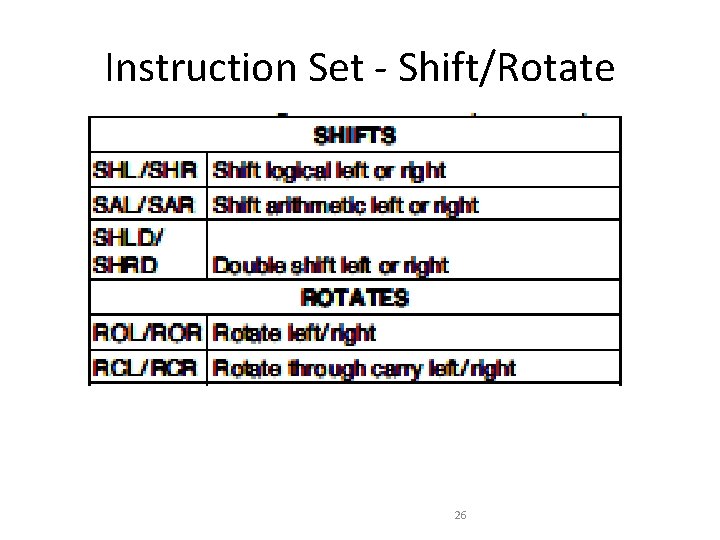
Instruction Set - Shift/Rotate 26

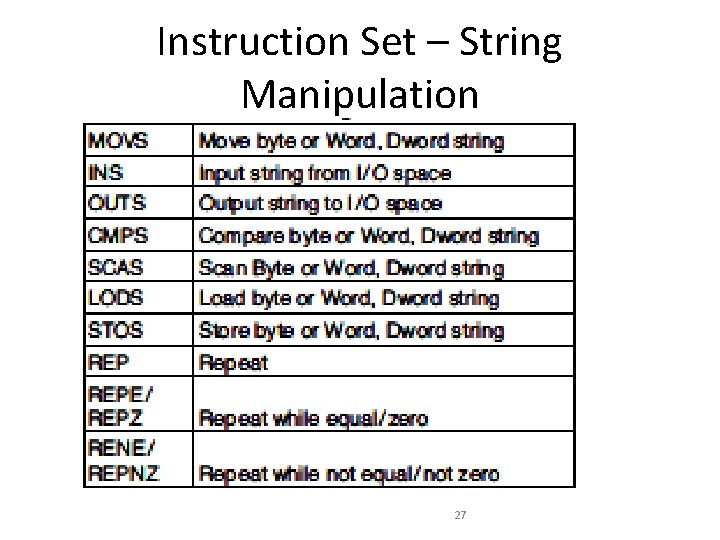
Instruction Set – String Manipulation 27

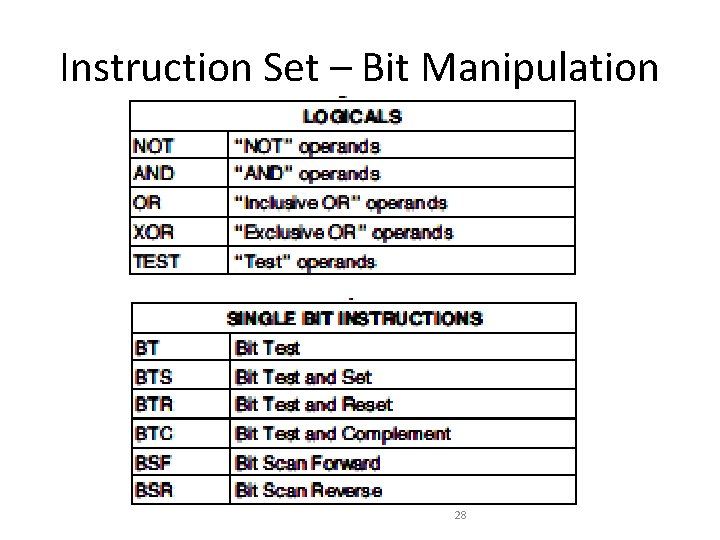
Instruction Set – Bit Manipulation 28

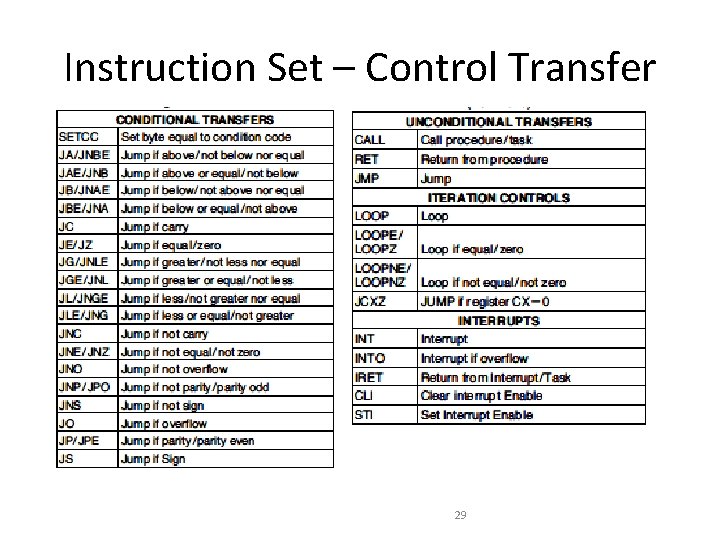
Instruction Set – Control Transfer 29

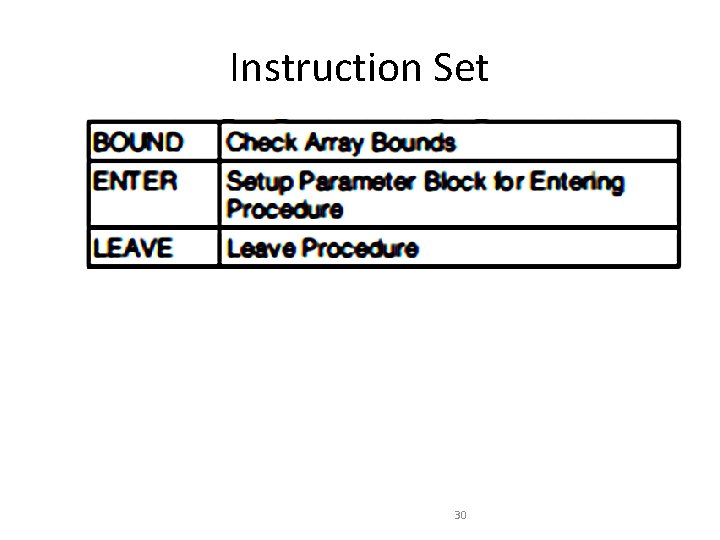
Instruction Set 30

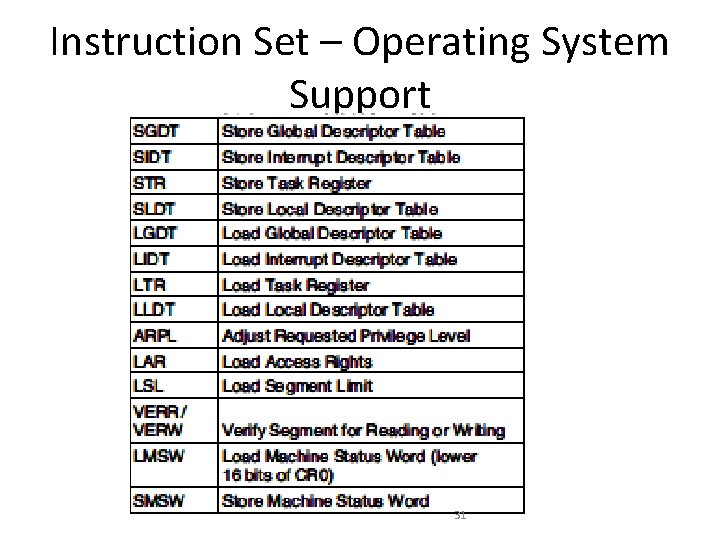
Instruction Set – Operating System Support 31

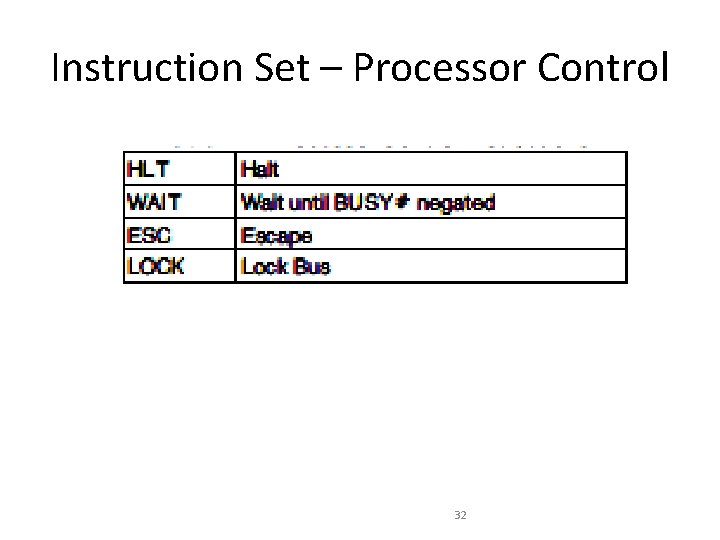
Instruction Set – Processor Control 32

Instruction Set • These instructions operate on either 0, 1, 2 or 4 operands • where an operand resides in – Register – Instruction itself – Memory • Most zero operand instructions take only one byte 33

Instruction Set • One operand instructions are generally two bytes long • The average instruction is 3. 2 bytes long • Since 80386 has a 16 -byte queue, an average of 5 instructions are prefetched. 34

Instruction Set • The use of 2 operands permits the following types of common instruction: – Register to Register – Memory to Register – Immediate to Register – Register to Memory – Immediate to Memory • The operands can be either 8, 16 or 32 bits long 35