Symmetric Encryption Functions Lucifer DES 3 DES RC




























- Slides: 41

Symmetric Encryption. Functions Lucifer DES 3 DES RC 2 RC 4 Blowfish AES. . .

"I cannot forecast to you the action of Russia, " said Winston Churchil "It is a riddle wrapped inside a mystery inside an enigma”

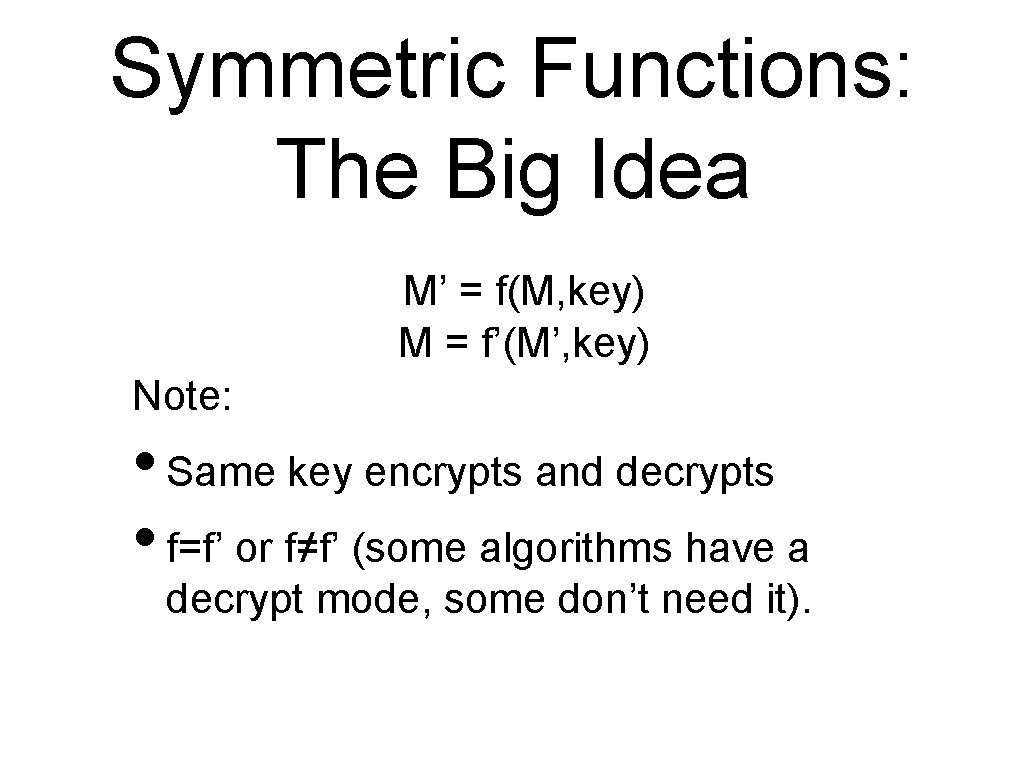
Symmetric Functions: The Big Idea M’ = f(M, key) M = f’(M’, key) Note: • Same key encrypts and decrypts • f=f’ or f≠f’ (some algorithms have a decrypt mode, some don’t need it).

Symmetric Algorithms: History • Pencil-and-paper Ciphers, Codebooks, and encryption machines were all symmetric. • Clearly, if you knew how to encrypt a message, you knew how to decrypt it, right?

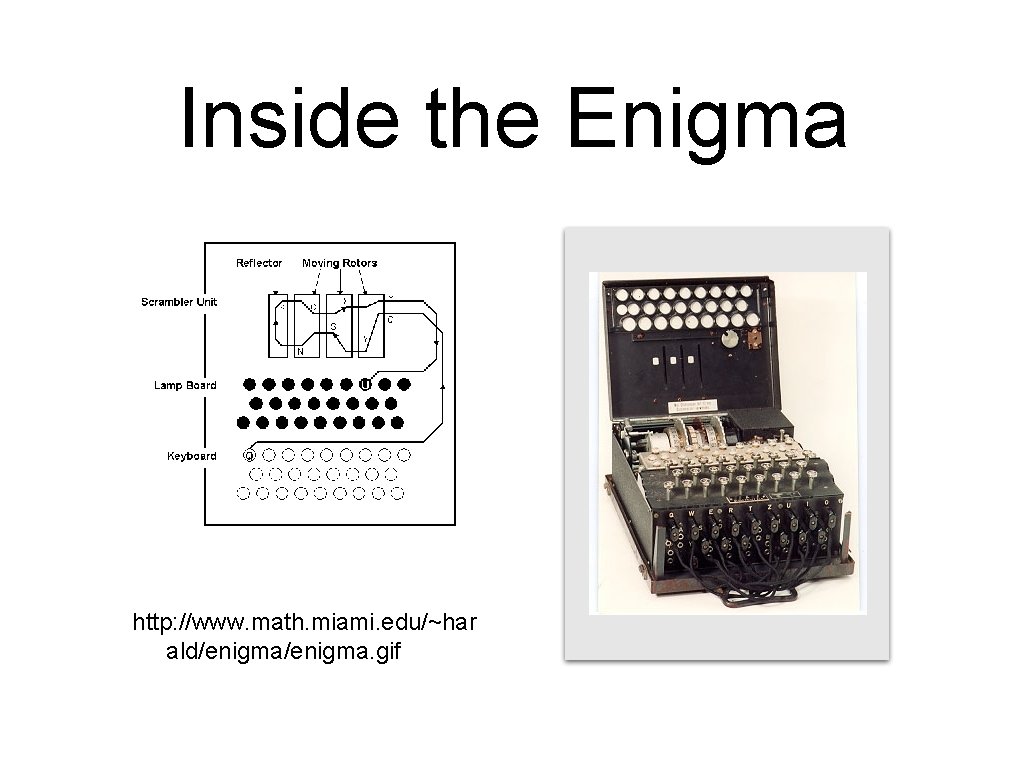
German Enigma Machine • Set “code of the day” on dials. • Later models: Set additional code with plugs and wires. • Press a button with the letter to encrypt; the encrypted letter lights up. • Each key press advances the dials

Inside the Enigma http: //www. math. miami. edu/~har ald/enigma. gif

Cryptography after WW 2 • Academia largely disinterested • NSA Largest Employer of mathematicians in the world.

Cryptography and IBM • IBM hired by Lloyds of London to arrange security for a cash dispensing network (early ATM machines. ) • IBM develops “Lucifer” cipher • Symmetric Algorithm • explicit encrypt/decrypt • 112 bit key • Substitution and transposition within 8 -character blocks

Cryptography and NBS • National Bureau of Standards request proposals for a “Data Encryption Standard. ” • IBM submits Lucifer to NBS • NBS submits Lucifer to NSA • NSA returns Lucifer with “tweaks” to substitution boxes and 56 -bit key

Can you trust DES? • NSA said they made it “better. ” • “Better” for who? • 56 bit key (was 112) • new sboxes (what was wrong with old ones? )

You could trust DES. • Lucifer was susceptible to differential cryptanalysis. • NSA couldn’t tell anybody! • Technique was secret until • • independently discovered by Adi Shamir sbox changes differential cryptanalysis useless against DES IBM published a paper on this in the 90 s.

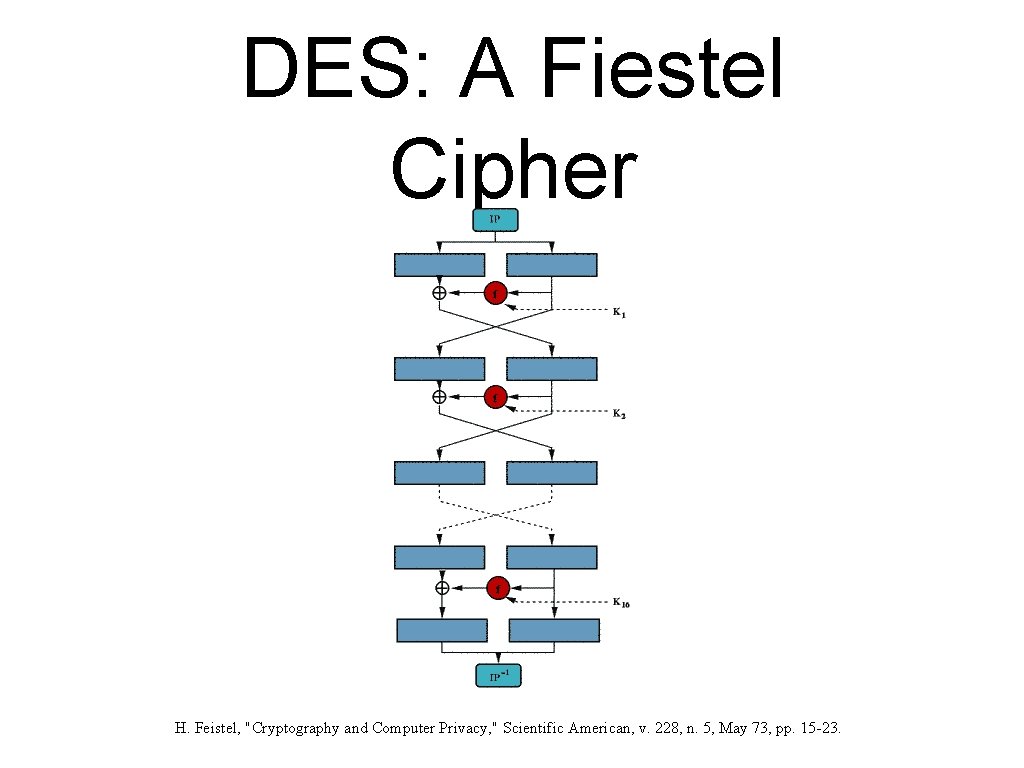
DES: A Fiestel Cipher H. Feistel, "Cryptography and Computer Privacy, " Scientific American, v. 228, n. 5, May 73, pp. 15 -23.

DES cracking • In the 1980 s, it was hypothesized that someone could build a DES-cracking machine for $1 M • In the 1990 s, John Gilmore and & EFF built one for $250 K. “Deep Crack. ” Time to crack a key: 4 -7 days. http: //www. eff. org/descracker • Nevertheless, DES is still widely used. Why?

Is weak crypto better than no crypto? weak crypto no crypto stops casual disclosure doesn’t give people a false sense of security gets people used to use gives people incentive to crypto move to strong crypto “Most people don’t need crypto anyway” “so why use it? ”

Strengthening DES • Triple DES (3 DES) • Encrypt, Decrypt, Encrypt • M’ = f(f’(f(M, K ), K ) • Set Key =Key for DES compatibility • 3 keys = 168 bits 1 1 2 2 3

RC 2, RC 4 • “Ron’s Code” #2 & #4 • Secret, proprietary algorithms from RSA Security

RC 2 • Block cipher. Keysize 40 -2048 bites • Revealed in 1996 in anonymous Usenet posting • Probably leaked by reverse engineering Lotus Notes • Widely used because of “ 40 -bit compromise” between Software Publisher’s Association and Commerce Department.

RC 4 • Very fast stream cipher - generates a pseudorandom stream used for XORing. • Keysize 40 -2048 bites • Revealed in 1994 in anonymous Usenet posting • Probably leaked by an engineer at Apple • Also part of the “ 40 -bit” compromise.

RC 5 • Invented by. . . Ron Rivest • Variable Key Size; Variable # of rounds • Largely academic curiosity

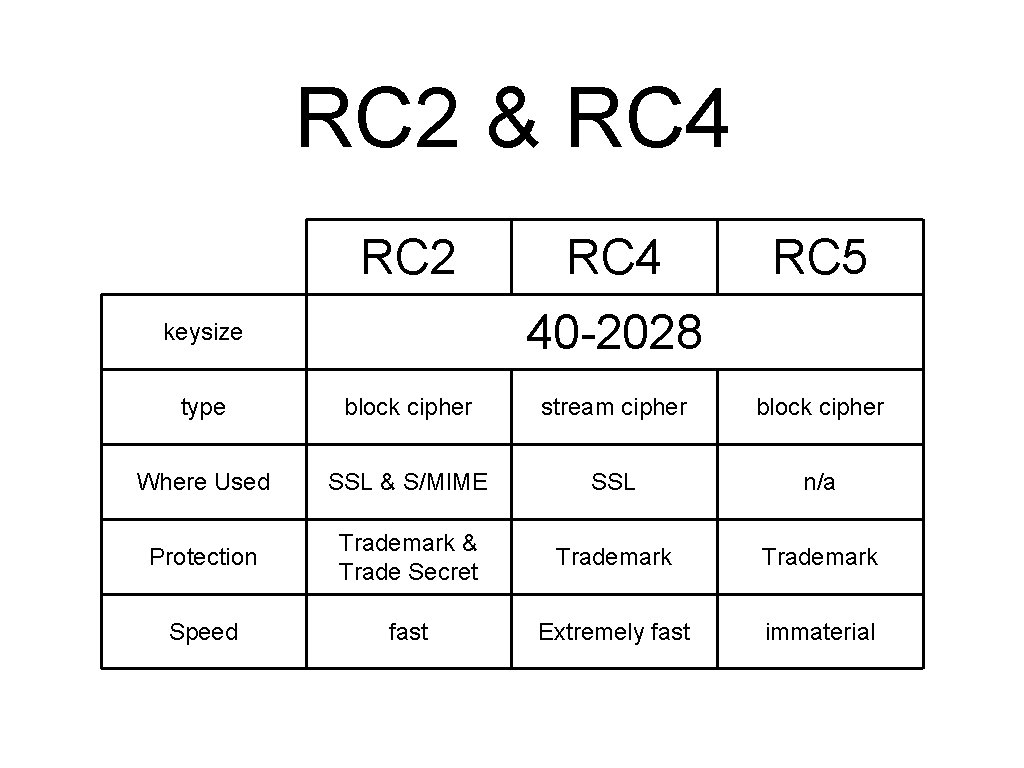
RC 2 & RC 4 RC 2 RC 4 RC 5 40 -2028 keysize type block cipher stream cipher block cipher Where Used SSL & S/MIME SSL n/a Protection Trademark & Trade Secret Trademark Speed fast Extremely fast immaterial

AES • Advanced Encryption Standard • Multi-year open competition • Requirements: • Block cipher. • Variable-length keys and blocks (128, 192, 256, etc. ) • Good in hardware or software.

AES Finalists Twofish - Bruce Schneier RC 5 - Ron Rivest MARS Rijndael - Vincent Rijmen and Joan Daemen

Interesting things to note about AES • US picked a foreign-designed cipher as its standard. • Not a Fiestel cipher. “New Math” • AES is faster than DES, even with longer keys!

Other Block Ciphers • CAST-128 (RFC-2144), 64 -bit block, 16 round, 128 -bit key • Blowfish (Schneider, 64 -bit block, 40448 bit key)

Openness in Design “Finally, I should note that publishing the design of a cipher inherently weakens it by providing an attacker with details of its operation. The most secure approach would be to design a cipher from scratch and keep both the algorithm and the keys secret. While designing a cryptosystem is fairly easy, evaluating it for loopholes is not. Governments and other very large institutions may have the resources to design and evaluate their own cryptosystem, but the rest of us are probably well advised to use published ciphers that have been publicly evaluated for weaknesses. ” http: //www. freesoft. org/CIE/Topics/135. htm

Modes of Operation • Defines how a block cipher is used on data longer than a block. • A strong cipher can be made less secure (not secure) with a bad mode of operation

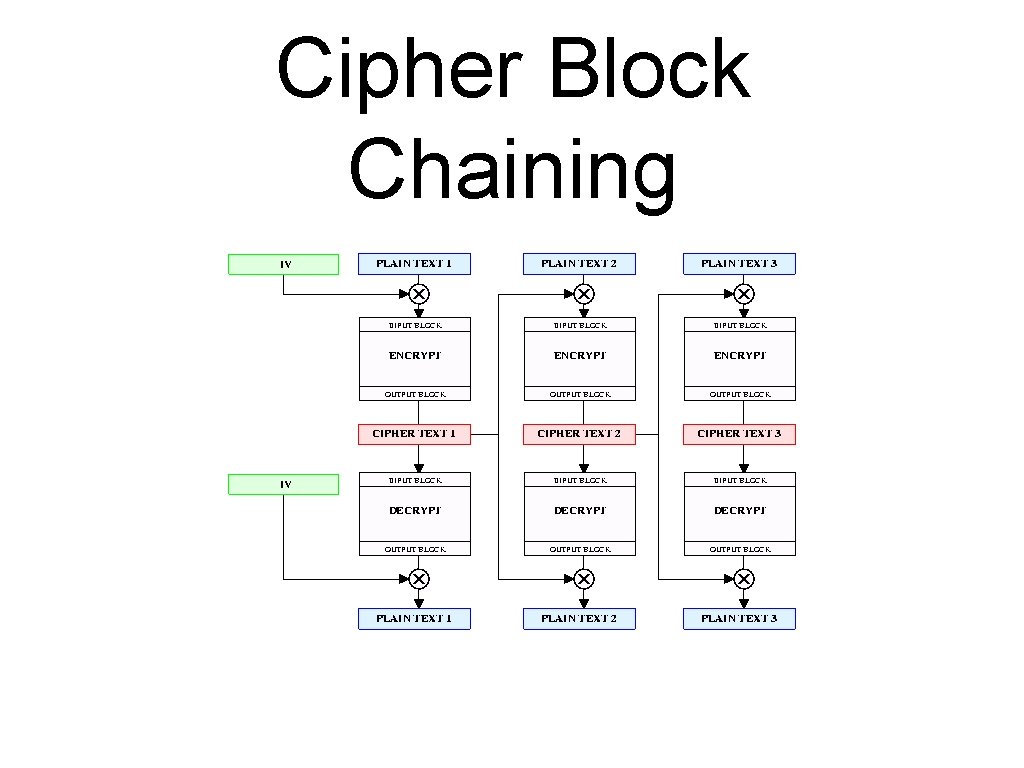
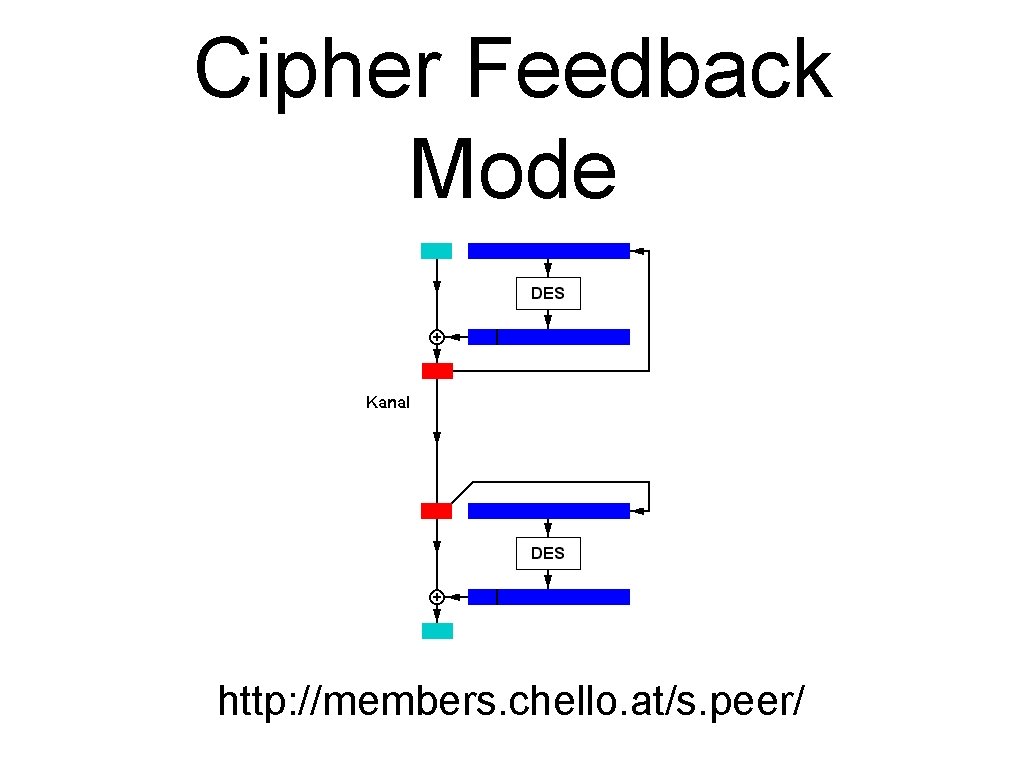
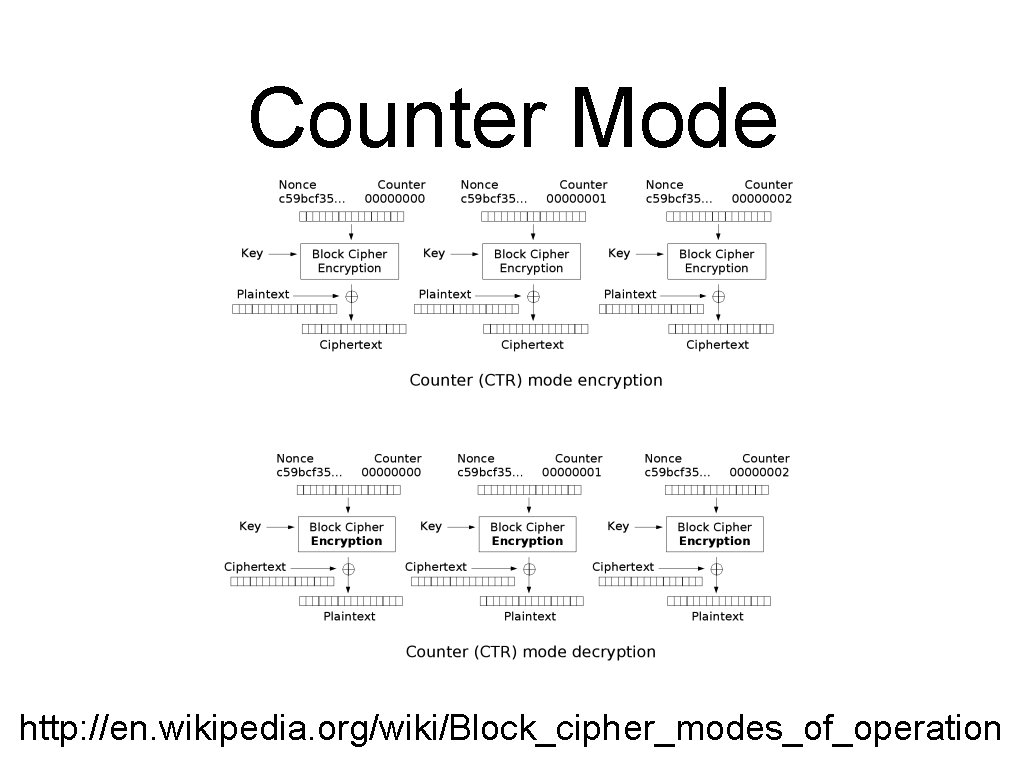
Most Important Modes • ECB - Electronic Code Book • CBC - Cipher Block Chaining • CFB - Cipher Feed Back (XOR generator) • Counter Mode

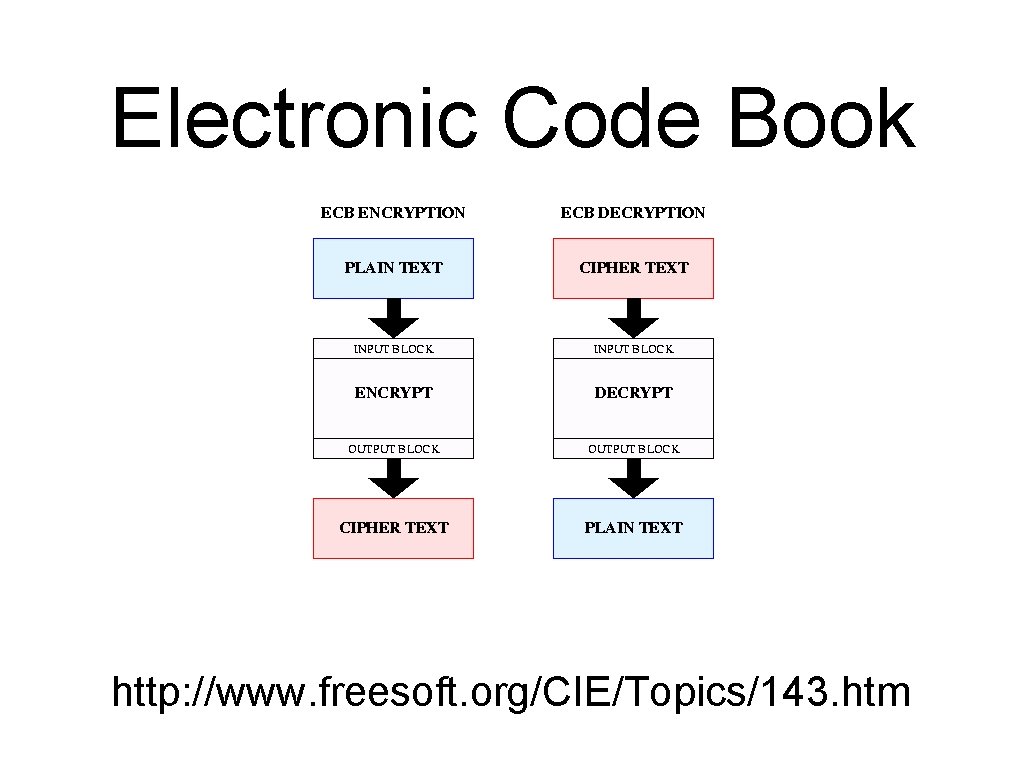
Electronic Code Book http: //www. freesoft. org/CIE/Topics/143. htm

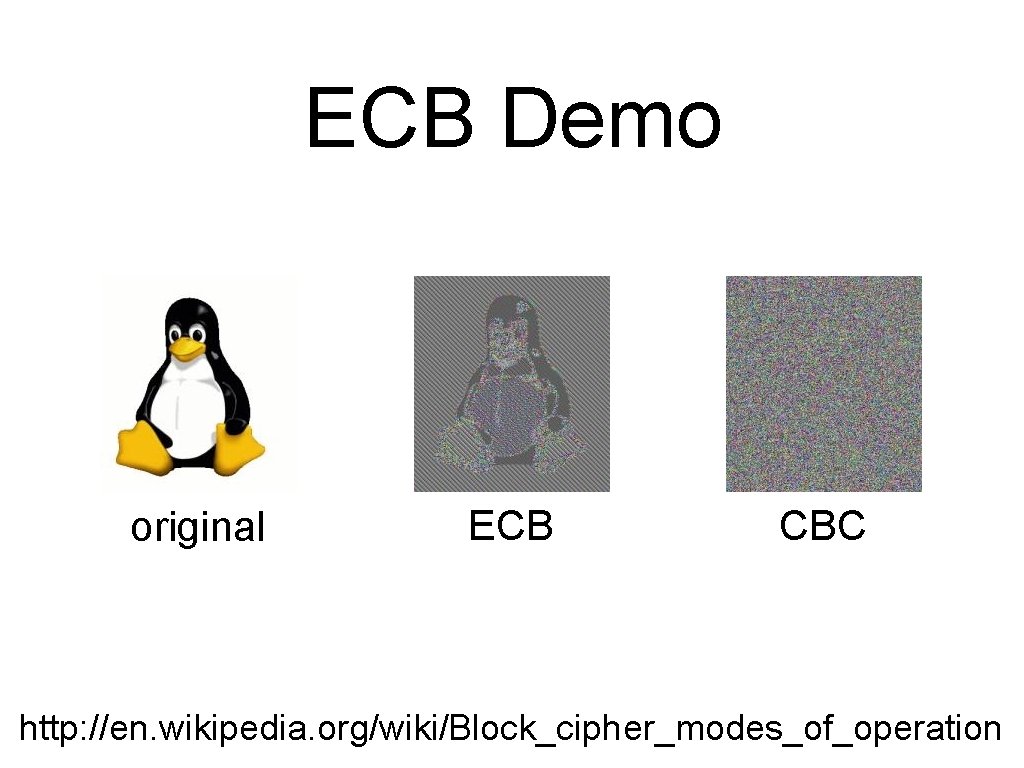
ECB Demo original ECB CBC http: //en. wikipedia. org/wiki/Block_cipher_modes_of_operation

Other problems with ECB • Replay attacks • Mauling “ 1” = 0011001 “ 9” = 0011101

Cipher Block Chaining

Cipher Feedback Mode http: //members. chello. at/s. peer/

Counter Mode http: //en. wikipedia. org/wiki/Block_cipher_modes_of_operation

Modes Demonstration http: //en. wikipedia. org/wiki/Block_cipher_modes_of_op eration

Privacy vs. Integrity • Need for the two to be distinguished was not evident back in the 1970 s. • In some cases, the ability to change encrypted data may be sufficient.

APIs!

RC 4: Easiest there Is void RC 4_set_key(RC 4_KEY *key, int len, const unsigned char *data); void RC 4(RC 4_KEY *key, unsigned long len, const unsigned char *indata, unsigned char *outdata); Note: Decrypt and Encrypt are the same operation!

RC 4 in Perl # Functional Style use Crypt: : RC 4; $encrypted = RC 4( $passphrase, $plaintext ); $decrypt = RC 4( $passphrase, $encrypted ); # OO Style use Crypt: : RC 4; $ref = Crypt: : RC 4 ->new( $passphrase ); $encrypted = $ref->RC 4( $plaintext ); $ref 2 = Crypt: : RC 4 ->new( $passphrase ); $decrypted = $ref 2 ->RC 4( $encrypted ); # process an entire file, $ref 3 = Crypt: : RC 4 ->new( $passphrase ); while (<FILE>) { print $ref 3 ->RC 4($_); }

RC 2: Block Encryption is Harder! void RC 2_set_key(RC 2_KEY *key, int len, const unsigned char *data, int bits); void RC 2_ecb_encrypt(const unsigned char *in, unsigned char *out, RC 2_KEY *key, int enc); void RC 2_encrypt(unsigned long *data, RC 2_KEY *key); void RC 2_decrypt(unsigned long *data, RC 2_KEY *key); void RC 2_cbc_encrypt(const unsigned char *in, unsigned char *out, long length, RC 2_KEY *ks, unsigned char *iv, int enc);

EVP: Open. SSL Generic Cipher Algorithms int EVP_Encrypt. Init(EVP_CIPHER_CTX *ctx, const EVP_CIPHER *type, unsigned char *key, unsigned char *iv); int EVP_Encrypt. Update(EVP_CIPHER_CTX *ctx, unsigned char *out, int *outl, unsigned char *in, int inl); int EVP_Encrypt. Final(EVP_CIPHER_CTX *ctx, unsigned char *out, int *outl); int EVP_Decrypt. Init(EVP_CIPHER_CTX *ctx, const EVP_CIPHER *type, unsigned char *key, unsigned char *iv); int EVP_Decrypt. Update(EVP_CIPHER_CTX *ctx, unsigned char *out, int *outl, unsigned char *in, int inl); int EVP_Decrypt. Final(EVP_CIPHER_CTX *ctx, unsigned char *outm, int *outl); int EVP_Cipher. Init(EVP_CIPHER_CTX *ctx, const EVP_CIPHER *type, unsigned char *key, unsigned char *iv, int enc); int EVP_Cipher. Update(EVP_CIPHER_CTX *ctx, unsigned char *out, int *outl, unsigned char *in, int inl); int EVP_Cipher. Final(EVP_CIPHER_CTX *ctx, unsigned char *outm, int *outl); int EVP_CIPHER_CTX_set_key_length(EVP_CIPHER_CTX *x, int keylen); int EVP_CIPHER_CTX_ctrl(EVP_CIPHER_CTX *ctx, int type, int arg, void *ptr); int EVP_CIPHER_CTX_cleanup(EVP_CIPHER_CTX *a);

Perl Modules for Symmetric Encryption Crypt: : Blowfish Crypt: : CAST 5 Crypt: : DES Crypt: : RC 4 Crypt: : RC 5 Crypt: : RC 6 Crypt: : Triple. DES Crypt: : Twofish