Symantec Web Isolation Secure Access to Uncategorized and

Symantec Web Isolation Secure Access to Uncategorized and Risky Sites Protect Your Most Privileged Users Prevent Phishing and Ransomware Attacks John Moore Senior Security Engineer July 10, 2018
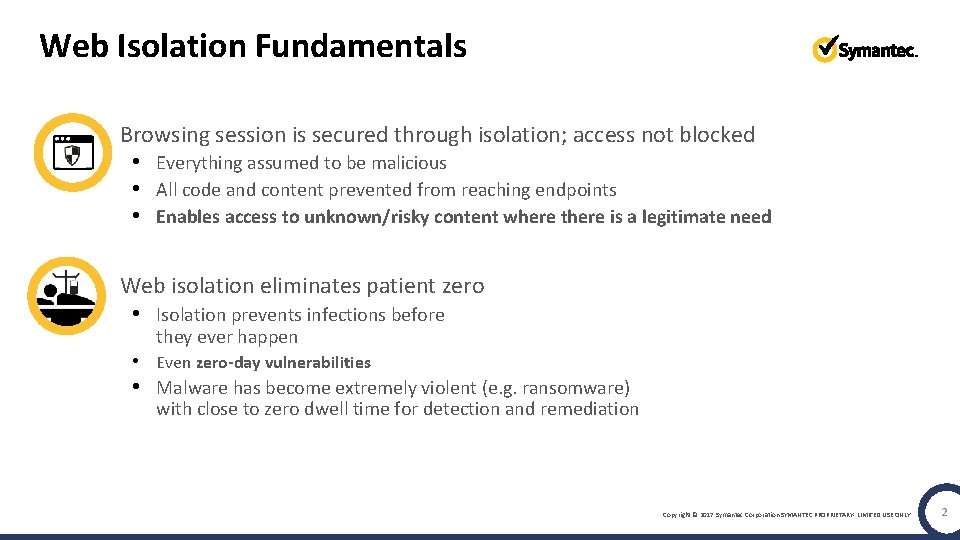
Web Isolation Fundamentals Browsing session is secured through isolation; access not blocked • Everything assumed to be malicious • All code and content prevented from reaching endpoints • Enables access to unknown/risky content where there is a legitimate need Web isolation eliminates patient zero • Isolation prevents infections before they ever happen • Even zero-day vulnerabilities • Malware has become extremely violent (e. g. ransomware) with close to zero dwell time for detection and remediation Copyright © 2017 Symantec Corporation SYMANTEC PROPRIETARY- LIMITED USE ONLY 2

Symantec Announces Fireglass Acquisition Web isolation changes the game for protecting against advanced threats • Fireglass web isolation • Established in 2014 • Leader in fast growing browser/web isolation market • Customer value – increased malware protection for web & mail • Integrates with Secure Web Gateway (Proxy. SG, ASG, VSWG) • • to allow safe access to uncategorized/risky sites Also can work with email on prem – parallel with Symantec SMG Offered stand-alone – cloud or on-prem Integrations underway with cloud-delivered Web Security Service and Symantec email security solutions (SMG, email. cloud) Integrate with 3 rd party proxies and NGFW’s Copyright © 2017 Symantec Corporation SYMANTEC PROPRIETARY- LIMITED USE ONLY 3
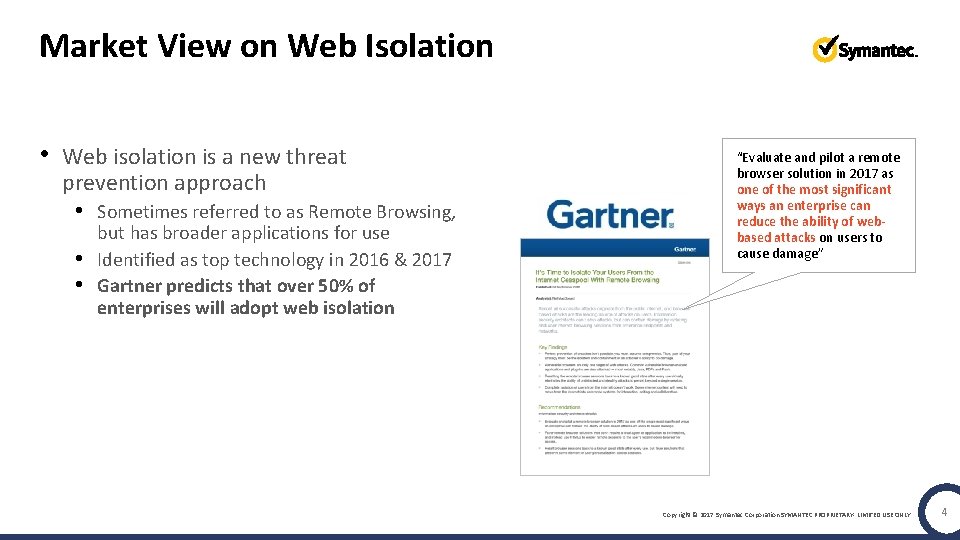
Market View on Web Isolation • Web isolation is a new threat prevention approach • Sometimes referred to as Remote Browsing, • • but has broader applications for use Identified as top technology in 2016 & 2017 Gartner predicts that over 50% of enterprises will adopt web isolation “Evaluate and pilot a remote browser solution in 2017 as one of the most significant ways an enterprise can reduce the ability of webbased attacks on users to cause damage” Copyright © 2017 Symantec Corporation SYMANTEC PROPRIETARY- LIMITED USE ONLY 4

90% of Cyber Attacks Come Through Web and Email Web Threats 1, 400+ Email & Phishing Threats 83% New browser & plug-in vulnerabilities per year Growth in active phishing URLs 78% 55% Every 4 seconds an unknown malware is downloaded 12% of sites can be used to deliver malware Source: Verizon DBIR, Symantec ISTR, Gartner of Large Enterprise were targeted by spear phishing of users click untrusted links or attachments Copyright © 2017 Symantec Corporation SYMANTEC PROPRIETARY- LIMITED USE ONLY 5
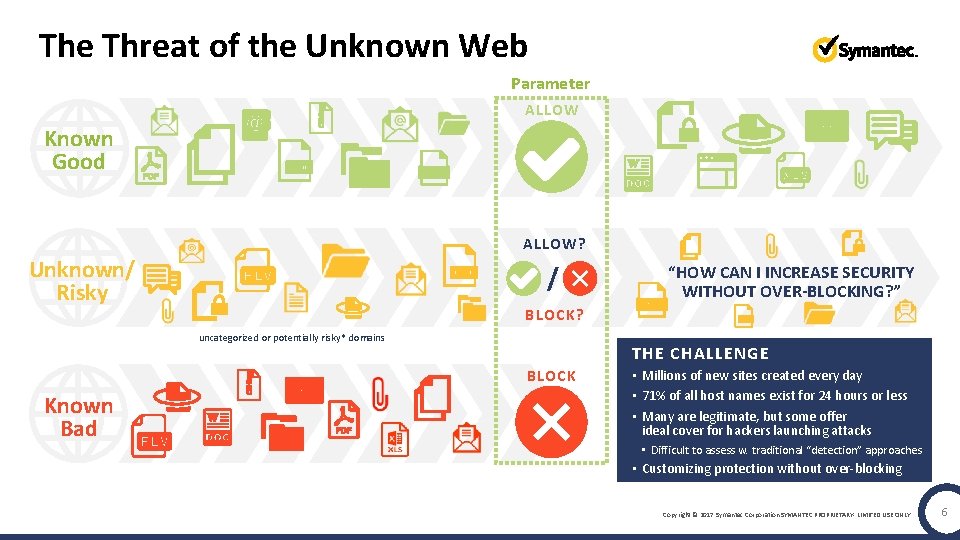
The Threat of the Unknown Web Parameter ALLOW Known Good ALLOW? Unknown/ Risky / BLOCK? uncategorized or potentially risky* domains THE CHALLENGE BLOCK Known Bad “HOW CAN I INCREASE SECURITY WITHOUT OVER-BLOCKING? ” • Millions of new sites created every day • 71% of all host names exist for 24 hours or less • Many are legitimate, but some offer ideal cover for hackers launching attacks • Difficult to assess w. traditional “detection” approaches • Customizing protection without over-blocking Copyright © 2017 Symantec Corporation SYMANTEC PROPRIETARY- LIMITED USE ONLY 6
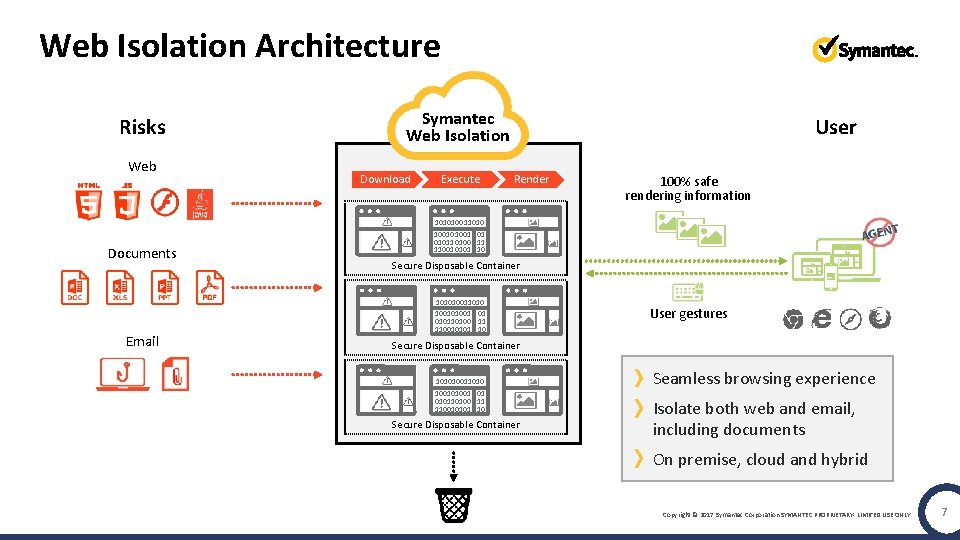
Web Isolation Architecture Risks Web Documents Email Symantec Web Isolation Download Execute User Render 100% safe rendering information 101010011010 100101001 01 010110100 11 110010101 10 Secure Disposable Container 101010011010 100101001 01 010110100 11 110010101 10 User gestures Secure Disposable Container 101010011010 100101001 01 010110100 11 110010101 10 Secure Disposable Container Seamless browsing experience Isolate both web and email, including documents On premise, cloud and hybrid Copyright © 2017 Symantec Corporation SYMANTEC PROPRIETARY- LIMITED USE ONLY 7

Demo Copyright © 2017 Symantec Corporation SYMANTEC PROPRIETARY- LIMITED USE ONLY

Key Use Cases Copyright © 2017 Symantec Corporation SYMANTEC PROPRIETARY- LIMITED USE ONLY
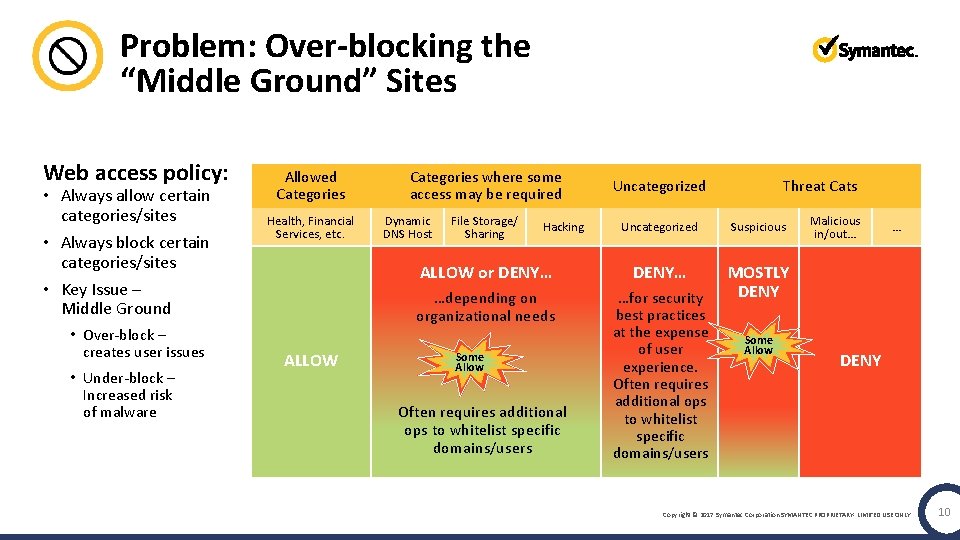
Problem: Over-blocking the “Middle Ground” Sites Web access policy: • Always allow certain categories/sites • Always block certain categories/sites • Key Issue – Middle Ground • Over-block – creates user issues • Under-block – Increased risk of malware Allowed Categories Health, Financial Services, etc. ALLOW Categories where some access may be required Dynamic DNS Host File Storage/ Sharing Hacking Uncategorized Threat Cats Uncategorized Suspicious ALLOW or DENY… …depending on organizational needs …for security best practices at the expense of user experience. Often requires additional ops to whitelist specific domains/users MOSTLY DENY Some Allow Often requires additional ops to whitelist specific domains/users Some Allow Malicious in/out… … DENY Copyright © 2017 Symantec Corporation SYMANTEC PROPRIETARY- LIMITED USE ONLY 10
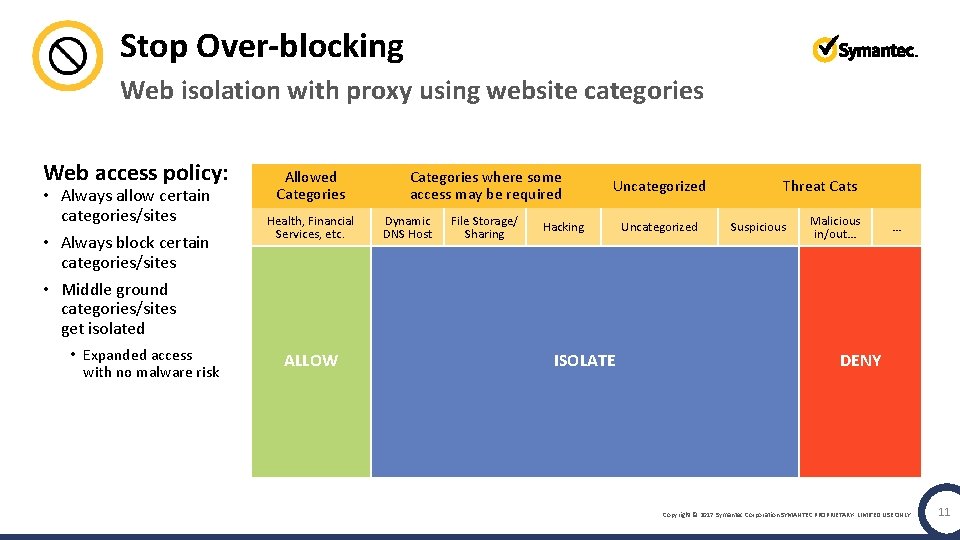
Stop Over-blocking Web isolation with proxy using website categories Web access policy: • Always allow certain categories/sites • Always block certain categories/sites • Middle ground categories/sites get isolated • Expanded access with no malware risk Allowed Categories Health, Financial Services, etc. ALLOW Categories where some access may be required Dynamic DNS Host File Storage/ Sharing Uncategorized Hacking ISOLATE Uncategorized Threat Cats Suspicious Malicious in/out… … DENY Copyright © 2017 Symantec Corporation SYMANTEC PROPRIETARY- LIMITED USE ONLY 11
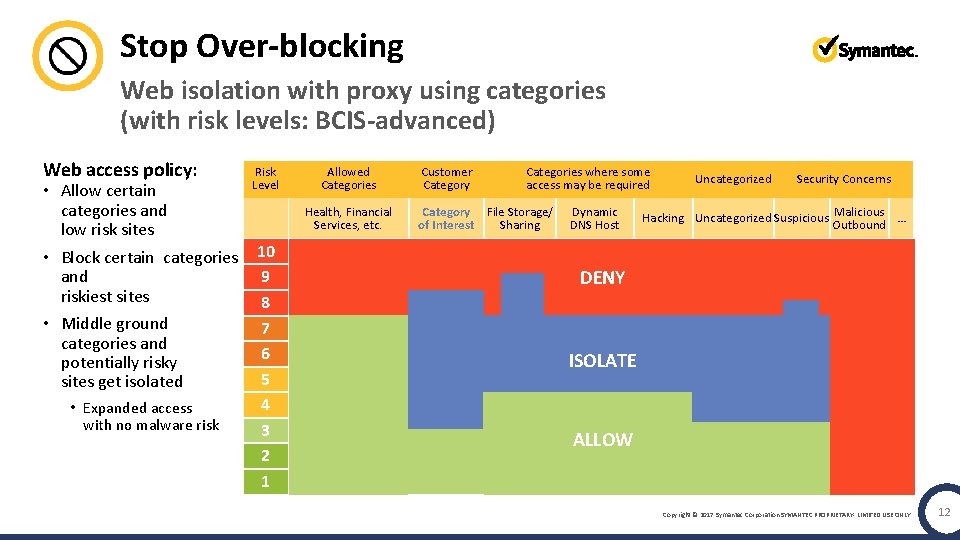
Stop Over-blocking Web isolation with proxy using categories (with risk levels: BCIS-advanced) Web access policy: Risk Level • Allow certain categories and low risk sites • Block certain categories 10 and 9 riskiest sites 8 • Middle ground 7 categories and 6 potentially risky 5 sites get isolated 4 • Expanded access with no malware risk 3 2 1 Allowed Categories Health, Financial Services, etc. Customer Category Categories where some access may be required Category File Storage/ of Interest Sharing Dynamic DNS Host Uncategorized Security Concerns Hacking Uncategorized Suspicious Malicious … Outbound DENY ISOLATE ALLOW Copyright © 2017 Symantec Corporation SYMANTEC PROPRIETARY- LIMITED USE ONLY 12
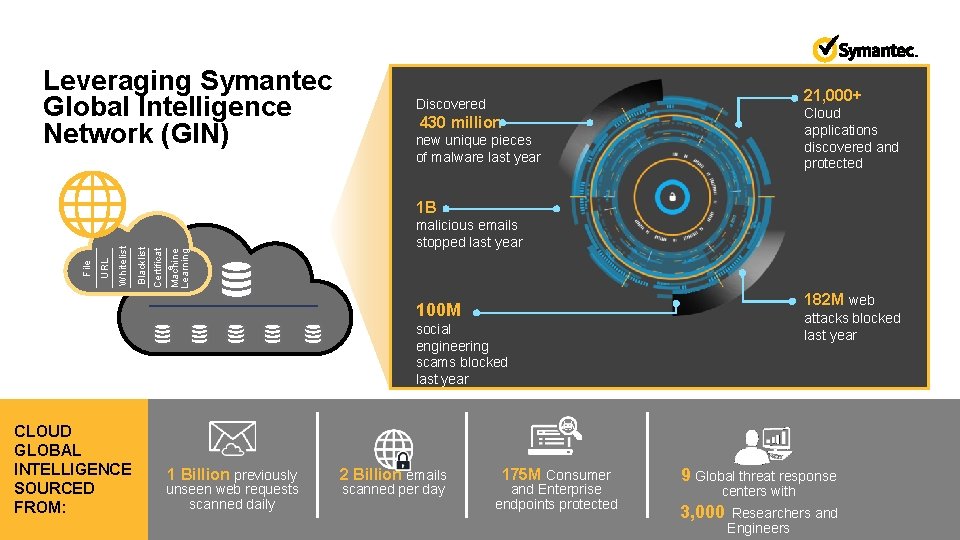
Leveraging Symantec Global Intelligence Network (GIN) 21, 000+ Discovered Cloud applications discovered and protected 430 million new unique pieces of malware last year Machine Learning Certificat e Blacklist Whitelist URL File 1 B malicious emails stopped last year 182 M web 100 M attacks blocked last year social engineering scams blocked last year CLOUD GLOBAL INTELLIGENCE SOURCED FROM: 1 Billion previously unseen web requests scanned daily 2 Billion emails scanned per day 175 M Consumer and Enterprise endpoints protected 9 Global threat response centers with 3, 000 Researchers and Engineers Copyright © 2017 Symantec Corporation SYMANTEC PROPRIETARY- LIMITED USE ONLY 13
Additional Protection for Privileged Users Safeguard Privileged Users Prevent Malware with Web Access • We have privileged users like executives, IT admins, HR, and finance that have extra permissions and access rights to sensitive data and systems C-Level Team Key IT Staff HR, Legal, Finance • I need to enable secure web browsing on those critical endpoints, and ensure internet delivered malware never impacts these devices Malware on these endpoints has severe consequences because of unique system privileges Copyright © 2017 Symantec Corporation SYMANTEC PROPRIETARY- LIMITED USE ONLY 14
Prevent Phishing Attacks by Isolating Risky Embedded URL Links Prevent malware/ransomware from phishing attacks Isolate websites launched from URLs embedded in email • Stop credential theft by preventing users from submitting corporate credentials and other sensitive information on unknown and malicious sites • Protect my users from embedded URLs that links to malicious websites Copyright © 2017 Symantec Corporation SYMANTEC PROPRIETARY- LIMITED USE ONLY 15

Thank You!
- Slides: 16