Symantec DLP Roadmap Update Curtis Carroll Principal Product

















- Slides: 21

Symantec DLP Roadmap Update Curtis Carroll Principal Product Manager- DLP 1

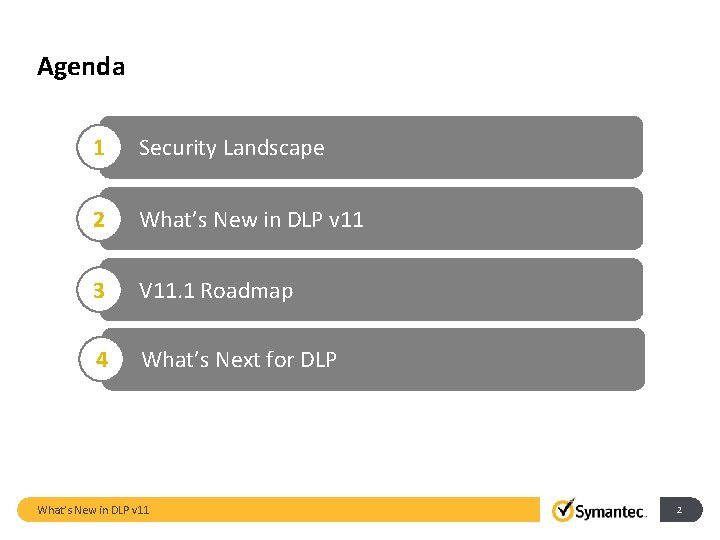
Agenda 1 Security Landscape 2 What’s New in DLP v 11 3 V 11. 1 Roadmap 4 What’s Next for DLP What’s New in DLP v 11 2

Security Landscape What’s New in DLP v 11 3

Key IT Security Trends Increasingly Sophisticated Threats What’s New in DLP v 11 Increasingly Complex, Heterogeneous Infrastructure Information Explosion High Cost/Damage From Breaches 4

So How Are Companies Addressing These Challenges? I. Upgrading Security Tools II. Vendor rationalization III. Prioritizing actions based on risk IV. Shift from an infrastructure-centric to an information-centric approach What’s New in DLP v 11 5

Symantec DLP Innovation Timeline 2004 v 3 2005 v 4 v 5 2006 v 6 2007 v 7 2008 v 8 2009 v 9 2010 v 10 2011 v 11 2012 v 12 Network: Monitor Network: Prevent Storage: Discover Storage: Protect Endpoint: Monitor & Prevent Endpoint: Discover DLP Open Platform DLP Data Insight Enforce (policies, detection, remediation, infrastructure) What’s New in DLP v 11 Symantec Proprietary & Confidential - This information is not a commitment, promise or legal obligation to deliver any material, code or functionality 6

What’s New in DLP v 11 7

What’s New – DLP v 11. 0 H 1 - 2010 H 2 - 2010 DLP 10. 5 H 1 - 2011 DLP 11. 1 H 2 - 2011 H 1 - 2012 Patriot Themes Feature Candidates Content-aware Enterprise • Content classification service EV integration • Control Compliance Suite Integration Data Protection Advances • Data Insight: Folder risk scoring and remediation • Endpoint Flex. Response • Endpoint Quarantine • Content Extraction API • Endpoint Trusted Devices • Application file access monitoring Performance & TCO Optimization • Rule Results Caching (i. e. , pre-detection) on the Endpoint • Custodian-based remediation for Discover • Enhanced agent configuration and troubleshooting • Customizable Policies (Edit Data Identifiers) • Windows high speed packet capture Expanded Enterprise Coverage • 64 -bit platform server support (Win 2 k 8 R 2, RHEL 5) • Hybrid support for Email Prevent • Symantec Web Gateway integration (May, 2011) What’s New in DLP v 11 8

DLP / Enterprise Vault Integration New in EV v 10. 0 Data Classification for Intelligent Archiving 1 ENFORCE Exchange Servers Create archival retention policies CONSOLE DLP 4 Inspect content & ACE matches policies DATA 3 CLASSIFICATION DLP 5 2 Forward message Provide retention tags 6 Pull message Archive intelligently EV Enterprise Vault Key Benefits: • Unified content-based classification policies across DLP and archiving • Automatic content-based email retention • Optimized archive storage and improved search efficiency What’s New in DLP v 11 9

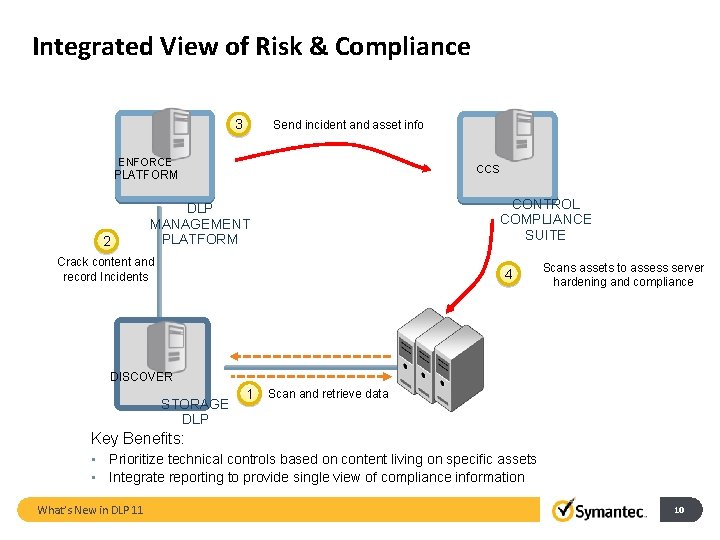
Integrated View of Risk & Compliance 3 Send incident and asset info ENFORCE CCS PLATFORM 2 CONTROL COMPLIANCE SUITE DLP MANAGEMENT PLATFORM Crack content and record Incidents 4 Scans assets to assess server hardening and compliance DISCOVER STORAGE DLP 1 Scan and retrieve data Key Benefits: • Prioritize technical controls based on content living on specific assets • Integrate reporting to provide single view of compliance information What’s New in DLP 11 10

Data at Rest Remediation Today 3 Distribute incidents for remediation ENFORCE PLATFORM 2 MANAGEMENT PLATFORM Crack Content and Record Incidents DISCOVER STORAGE 1 Scan and Retrieve Data DLP What’s New in DLP v 11 Targets 11

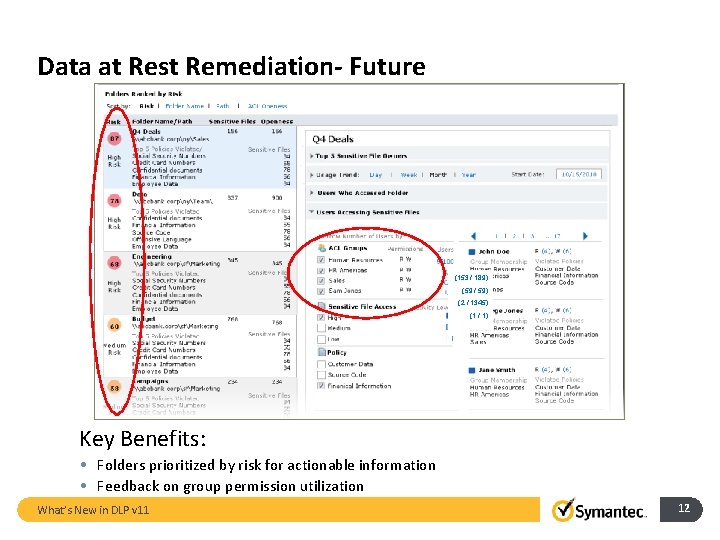
Data at Rest Remediation- Future (153 / 189) (59 / 59) (2 / 1345) (1 / 1) Key Benefits: • Folders prioritized by risk for actionable information • Feedback on group permission utilization What’s New in DLP v 11 12

DLP + SEE Removable Storage Encryption New in SEE v 8. 0. 1 ENFORCE PLATFORM MANAGEMENT PLATFORM 4 1 Incident created when user connects back to network User downloads sensitive file to hard drive 2 ENDPOINT PREVENT Connected Disconnected DISCOVER ENDPOINT 3 User disconnects from network and attempts to copy sensitive file to USB Based on policy, file is automatically encrypted with SEE RSE before it hits the usb Key Benefits: • File protection is automated without requiring user intervention • Wider range of data protection actions to fit customer needs What’s New in DLP v 11 13

Application File Access Monitoring 1 Add application to File Access Monitoring list (if not in pre-configured list) 3 ENFORCE PLATFORM MANAGEMENT PLATFORM 2 Application file access is monitored in real time Access to confidential file blocked according to policy Non-sensitive file Monitored application Monitor file open/read Confidential file ENDPOINT DLP Key Benefits: Access granted Access blocked Examples • Communication • Secure. Zip • Skype • General Apps • Office Communicator • Chrome • i. Tunes • Bluetooth • Black. Berry Desktop • Web. Ex/ Live. Meeting • IRC apps • Unauthorized encryption • Prevents information transmission over application-proprietary network protocols • Track and prevent obscuring of extremely sensitive information via unauthorized encryption • Broadly protect at app level without managing individual plug-ins What’s New in DLP v 11 Symantec Proprietary & Confidential - This information is not a commitment, promise or legal obligation to deliver any material, code or functionality 14

What’s New in v 11. 1 What’s New in DLP v 11. 1 15

What’s New – DLP v 11. 1 H 1 - 2010 H 2 - 2010 DLP 10. 5 H 1 - 2011 DLP 11. 1 H 2 - 2011 H 1 - 2012 Patriot Themes Feature Candidates Data Protection Advances • Vector Machine Learning • Automated Flex Response Public Sector Capabilities • Single Sign-On Support for Enforce, incl. CAC • FIPS 140 -2 • Common Criteria, EAL 2 Performance & TCO • Symantec Protection Center v 2 integration • Endpoint Server VM Support • Improved Agent Tamper Proofing Expanded Enterprise Coverage • Improved Citrix Performance for EP agents • Agent support for Win 2008 R 2 64 bit • Agent support for Citrix Xen. App 6, Xen. Desktop 4 Symantec Confidential - DLP v 11. 1 16 Symantec Proprietary & Confidential - This information is not a commitment, promise or legal obligation to deliver any material, code or functionality

Detecting Unstructured Data: The Challenge Today Describe • How do I identify relevant keywords? • How do I avoid false positives? • How do I tune policies? Symantec Confidential - DLP v 11. 1 Fingerprint • What if I can’t access all confidential docs? • How do I account for new docs? • How do I protect the endpoint? 17 Symantec Proprietary & Confidential - This information is not a commitment, promise or legal obligation to deliver any material, code or functionality

Vector Machine Learning: The Solution Learn Describe Fingerprint Automates keyword identification and enables easier tuning Improves accuracy, reduces false positives Detects new content without having to fingerprint it first Works everywhere, including the Endpoint Symantec Confidential - DLP v 11. 1 18 Symantec Proprietary & Confidential - This information is not a commitment, promise or legal obligation to deliver any material, code or functionality

Vector Machine Learning – How it Works Benefits • Easer than using described content (DCM) to generate accurate policies • Requires fewer samples than complete fingerprinting (IDM) • Results: Lower administration costs and improved accuracy Symantec Confidential - DLP v 11. 1 19

Use Case: Vector Machine Learning Use Cases Situation: Distributed environment; new intellectual property created too frequently for controls to keep up Create highly accurate policies for source code, wherever it resides Detect insurance claim forms that reside outside the reach of Info. Sec Automatically create policies to protect unstructured, textual data Protect product formulas that haven’t been created yet Symantec Confidential - DLP v 11. 1 20

Thank you! Curtis Carroll curtis_carroll@symantec. com Copyright © 2010 Symantec Corporation. All rights reserved. Symantec and the Symantec Logo are trademarks or registered trademarks of Symantec Corporation or its affiliates in the U. S. and other countries. Other names may be trademarks of their respective owners. This document is provided for informational purposes only and is not intended as advertising. All warranties relating to the information in this document, either express or implied, are disclaimed to the maximum extent allowed by law. The information in this document is subject to change without notice. 21