Supply Chain Risk Management SCRM Changing the Program











![SCRM Sample Contract Language (Section C) [SOWxxx 4] The contractor shall demonstrate that the SCRM Sample Contract Language (Section C) [SOWxxx 4] The contractor shall demonstrate that the](https://slidetodoc.com/presentation_image_h/882613177affc16b6448b87c3b48ac42/image-15.jpg)
![Sw. A Sample Contract Language (Section C) [SOWxx 10] The contractor shall develop, document, Sw. A Sample Contract Language (Section C) [SOWxx 10] The contractor shall develop, document,](https://slidetodoc.com/presentation_image_h/882613177affc16b6448b87c3b48ac42/image-16.jpg)


- Slides: 18

Supply Chain Risk Management (SCRM): Changing the Program Protection Paradigm Date: 3 April 2017 Presented by: Heath Ferry Professor of Cybersecurity Heath. ferry@dau. mil

Outline • • • The importance of the supply chain Supply Chain Risk Management (SCRM) Relevant guidance SCRM in contracts Summary References 2

F-35 and the Supply Chain “You would be hard-pressed to come up with a bigger supply chain challenge than the one created by Lockheed Martin Aeronautics Co. , when it took on the role of prime contractor for construction of the F-35 Joint Strike Fighter (JSF)”. The program includes more than 1, 300 suppliers from nine countries and 48 U. S. states, along with 40, 000 individual parts. 3

Wal-Mart and the Supply Chain • Stocks products made in more than 70 countries • Operates more than 11, 000 stores in 27 countries • Manages an average of $32 billion in inventory • • F-35 or Wal-Mart Which supply chain is more complex? Which supply chain has more risks? How are these 2 supply chains similar? Different? What can the Do. D learn from Wal-Mart? 4

Supply Chain Risk • • The Chinese government has adopted new regulations requiring companies that sell computer equipment to Chinese banks to turn over secret source code, submit to invasive audits and build so -called back doors into hardware and software In 2013 a Defense Science Board report accused Supply Chain Risk -the risk that an China of using cyber attacks to access information adversary may sabotage, maliciously from almost 40 Pentagon weapons programs introduce unwanted function, or Contractors may be removed from information technology procurements supporting national security systems for failure to satisfy standards related to supply chain risk, and in some cases they will be unable to protest their removal. Do. D rules governing Information Relating to Supply Chain Risk, 78 Fed. Register 69, 268 (Nov. 18, 2013), NDAA Section 806 otherwise subvert the design, integrity, manufacturing, production, distribution, installation, operation, or maintenance of a covered system so as to surveil, deny, disrupt, or otherwise degrade the function, use, or operation of such system. 5

Supply Chain Risk Management (SCRM) - A systematic process for managing supply chain risk by identifying susceptibilities, vulnerabilities and threats throughout Do. D’s “supply chain” and developing mitigation strategies to combat those threats whether presented by the supplier, the supplied product and its subcomponents, or the supply chain (e. g. , initial production, packaging, handling, storage, transport, mission operation, and disposal). Do. DI 5200. 44, November 5, 2012 - Protection of Mission Critical Functions to Achieve Trusted Systems and Networks (TSN) Four Aspects of SCRM • Security provides the confidentiality, integrity, and availability of information. • Integrity is focused on ensuring that the products or services in the supply chain are genuine and authentic and do not contain any unwanted functionality. • Resiliency is focused on ensuring that the supply chain will provide required products and services under stress. • Quality is focused on reducing unintentional vulnerabilities that may provide opportunities for exploitation. NIST Special Publication 800 -161 , SCRM, April 2015 6

We Live in a New Environment • • • Globalization of vendor supply chains Insider threat Counterfeits Malicious insertion And much, much more! Supply chain risk will never be resolved. It will be a continuous process to manage.

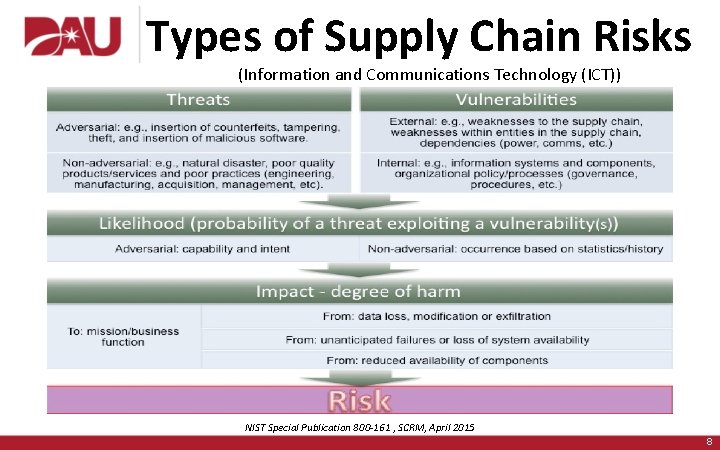
Types of Supply Chain Risks (Information and Communications Technology (ICT)) NIST Special Publication 800 -161 , SCRM, April 2015 8

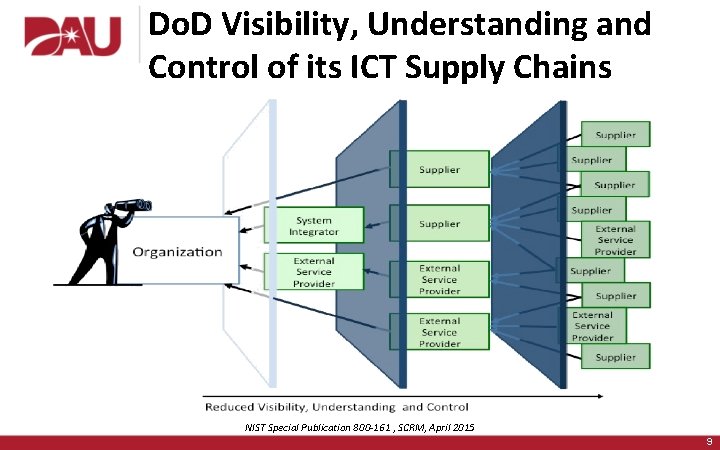
Do. D Visibility, Understanding and Control of its ICT Supply Chains NIST Special Publication 800 -161 , SCRM, April 2015 9

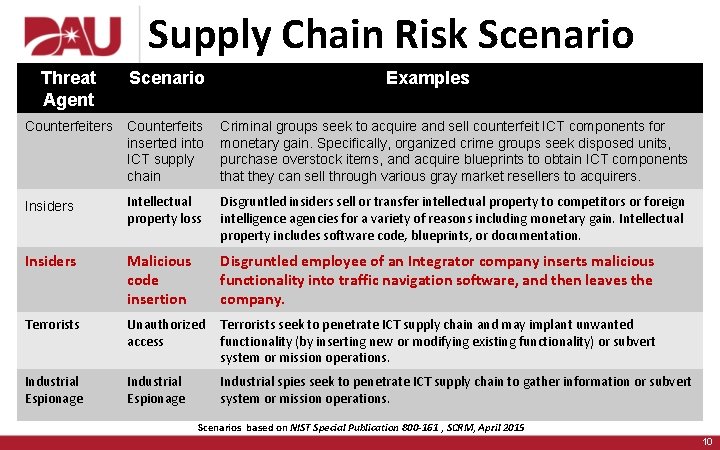
Supply Chain Risk Scenario Threat Agent Scenario Examples Counterfeiters Counterfeits inserted into ICT supply chain Criminal groups seek to acquire and sell counterfeit ICT components for monetary gain. Specifically, organized crime groups seek disposed units, purchase overstock items, and acquire blueprints to obtain ICT components that they can sell through various gray market resellers to acquirers. Insiders Intellectual property loss Disgruntled insiders sell or transfer intellectual property to competitors or foreign intelligence agencies for a variety of reasons including monetary gain. Intellectual property includes software code, blueprints, or documentation. Insiders Malicious code insertion Disgruntled employee of an Integrator company inserts malicious functionality into traffic navigation software, and then leaves the company. Terrorists Unauthorized access Terrorists seek to penetrate ICT supply chain and may implant unwanted functionality (by inserting new or modifying existing functionality) or subvert system or mission operations. Industrial Espionage Industrial spies seek to penetrate ICT supply chain to gather information or subvert system or mission operations. Scenarios based on NIST Special Publication 800 -161 , SCRM, April 2015 10

Supply Chain Risk Scenario (Continued) Threat Source Integrator– Malicious Code Insertion Vulnerability Minimal oversight of integrator activities - no checks and balances for any individual inserting a small piece of code. Threat Event Description Disgruntled employee of an Integrator company inserts malicious functionality into traffic navigation software, and then leaves the company. Existing Practices Integrator: peer-review process Acquirer: Contract that sets down time, cost, and functionality requirements Outcome 50 large metro locations and 500 instances affected by malware. When activated, the malware causes major disruptions to traffic. Impact/ Likelihood High/ High – Traffic disruptions are major and last for two weeks while a work-around is created. Malicious code is not discovered and remains a vulnerability. Potential Mitigating Strategies / SCRM Controls AC-1 (Access Control Policy & Procedures); AC-2 (Account Management); CM-3 (Configuration Change Control); IR-4 (Incident Handling); SA-12(11) (Supply Chain Protection); SA 14(1) (Criticality Analysis) SA-12 SUPPLY CHAIN PROTECTION Control: The organization protects against supply chain threats to the information system, system component, or information system service by employing [Assignment: organization-defined security safeguards] as part of a comprehensive, defense-in-breadth information security strategy. (11) Supply Chain Protection | Penetration Testing / Analysis Of Elements, Processes, And Actors - The organization employs [Selection (one or more): organizational analysis, independent third-party analysis, organizational penetration testing, independent third-party penetration testing] of [Assignment: organizationdefined supply chain elements, processes, and actors] associated with the information system, system component, or information system service. NIST SP 800 -53 Rev 4 , April 2013 11

SCRM Questions (From Program Protection Plan Outline & Guidance, July 2011) • How will the program manage supply chain risks to Critical Program Information (CPI) and critical functions and components? • Explain how supply chain threat assessments will be used to influence system design, development environment, and procurement practices. Who has this responsibility? • When will threat assessments be requested? • Trusted Suppliers – Will any Application Specific Integrated Circuits (ASICs) require trusted fabrication? – How will the program make use of accredited trusted suppliers of integrated circuit related services? • Counterfeit Prevention – What counterfeit prevention measures will be in place? How will the program mitigate the risk of counterfeit insertion during Operations and Maintenance? 12

SCRM Relevant Guidance • • Do. DI 5000. 02 – Countermeasures. Program managers will describe in their Program Protection Plan (PPP) the program’s critical program information and mission-critical functions and components; … Countermeasures should include … secure system design, supply chain risk management, software assurance, anti-counterfeit practices, procurement strategies, and other mitigations in accordance with Do. DI 5200. 39, Do. DI 5200. 44, and Do. DI 8500. 01 Do. DI 5200. 44 – Risk to the trust in applicable systems shall be managed throughout the entire system lifecycle. The application of risk management practices shall begin during the design of applicable systems and prior to the acquisition of critical components or their integration within applicable systems, . . – Risk management shall include Trusted Systems and Networks (TSN) process, tools, and techniques to: • (1) Reduce vulnerabilities in the system design through system security engineering. • (2) Control the quality, configuration, and security of software, firmware, hardware, and systems throughout their lifecycles, including components or subcomponents from secondary sources. Employ protections that manage risk in the supply chain for components or subcomponent products and services … 13

Security and Contracting “Ultimately, we believe that there is no alternative to making security a part of the software contracting. Currently, we believe that there are serious misunderstandings about the security of code being delivered under many software development contracts. This can only lead to expensive litigation and a decision made by individuals with little software experience or understanding. ” The Open Web Application Security Project (OWASP) Foundation 14
![SCRM Sample Contract Language Section C SOWxxx 4 The contractor shall demonstrate that the SCRM Sample Contract Language (Section C) [SOWxxx 4] The contractor shall demonstrate that the](https://slidetodoc.com/presentation_image_h/882613177affc16b6448b87c3b48ac42/image-15.jpg)
SCRM Sample Contract Language (Section C) [SOWxxx 4] The contractor shall demonstrate that the contractor has mechanisms in place to effectively monitor the supply chain for critical components, understands how supply chain risk can be introduced through those components, and has implemented or plans to implement countermeasures to mitigate such risks. • [SOWxxx 5] The contractor shall plan for and implement countermeasures that mitigate the risk of foreign intelligence or foreign influence, technology exploitation, supply chain and battlefield threats, and vulnerabilities that result in Level I and Level II protection failures of the system; countermeasures include the following: 1. The application of supply chain risk management best practices, … 2. The enumeration of potential suppliers of critical components, as they are identified, … • [SOWxxx 7] The contractor shall ensure that updated assumptions, rationale, and results related to the criticality analyses, vulnerability assessments, risk assessments, supply chain risk information, and risk mitigations are made available for Government review at each Systems Engineering Technical Review (SETR). • From “Suggested SSE Language for TSN in Do. D RFPs”, Jan 2014 15
![Sw A Sample Contract Language Section C SOWxx 10 The contractor shall develop document Sw. A Sample Contract Language (Section C) [SOWxx 10] The contractor shall develop, document,](https://slidetodoc.com/presentation_image_h/882613177affc16b6448b87c3b48ac42/image-16.jpg)
Sw. A Sample Contract Language (Section C) [SOWxx 10] The contractor shall develop, document, and update Table X software assurance plans and actuals in accordance with the table description provided in the Defense Acquisition Guidebook section 13. 7. 3 CAPEC: Common Attack Pattern Enumeration and Classification COTS: commercial off-the-shelf CVE: Common Vulnerabilities and Exposures CWE: Common Weakness Enumeration NDI: non-developmental item OEM: Original Equipment Manufacturer p/a: plan vs. actual Pen: penetration testing SW: software From “Suggested SSE Language for TSN in Do. D RFPs”, Jan 2014 16

Summary • Supply Chain Risk Management (SCRM) addresses vulnerabilities and threats throughout the Supply Chain and develops mitigation strategies • We must follow the relevant guidance provided to us • To be effective security SCRM must be included in the contracting process Do. DI 8500. 01 - Cybersecurity must be fully integrated into system life cycles so that it will be a visible element of organizational, joint, and Do. D Component architectures, capability identification and development processes, integrated testing, information technology portfolios, acquisition, operational readiness assessments, supply chain risk management, System Security Engineering (SSE), and operations and maintenance activities. 17

Additional Comments Questions? DAU is making great strides to increase it’s training efforts in the cybersecurity area. • CLE 074 “Cybersecurity Throughout Do. D Acquisition” – 5 hour Continuous Learning Module, Deployed April 2015 • ENG 160 and 260 – Program Protection Planning courses • ISA 220 – Risk Management Framework for Practitioners • DAU hired cybersecurity professionals in multiple locations to help write training material and provide consulting expertise. • Call Tim Denman at 256 -922 -8174 or • Email at tim. Denman@dau. mil or acquisition. cybersecurity@dau. mil