Summary of Sessions 2 and 3 Matti Hiltunen


- Slides: 5

Summary of Sessions 2 and 3 Matti Hiltunen

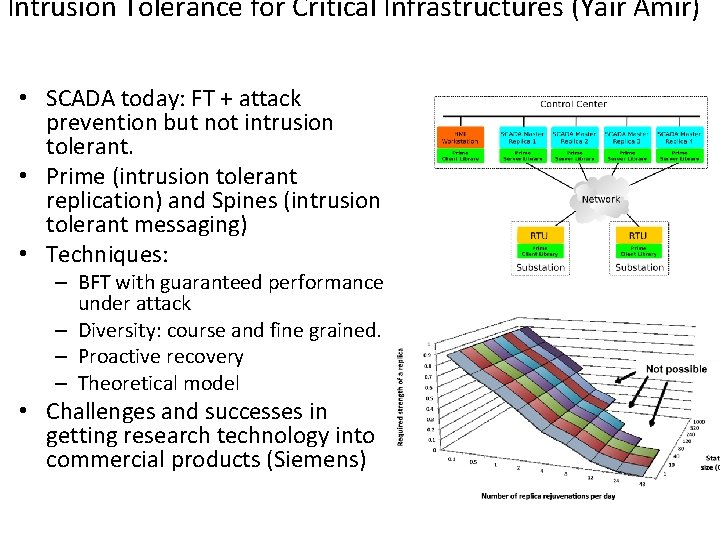
Intrusion Tolerance for Critical Infrastructures (Yair Amir) • SCADA today: FT + attack prevention but not intrusion tolerant. • Prime (intrusion tolerant replication) and Spines (intrusion tolerant messaging) • Techniques: – BFT with guaranteed performance under attack – Diversity: course and fine grained. – Proactive recovery – Theoretical model • Challenges and successes in getting research technology into commercial products (Siemens)

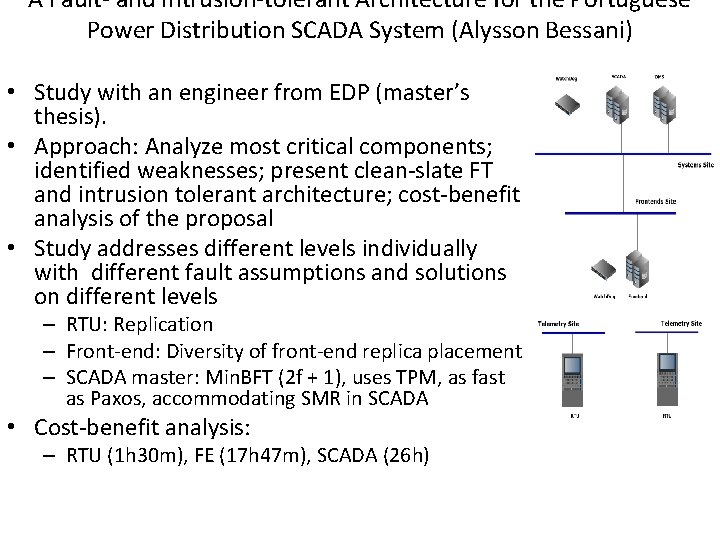
A Fault- and Intrusion-tolerant Architecture for the Portuguese Power Distribution SCADA System (Alysson Bessani) • Study with an engineer from EDP (master’s thesis). • Approach: Analyze most critical components; identified weaknesses; present clean-slate FT and intrusion tolerant architecture; cost-benefit analysis of the proposal • Study addresses different levels individually with different fault assumptions and solutions on different levels – RTU: Replication – Front-end: Diversity of front-end replica placement – SCADA master: Min. BFT (2 f + 1), uses TPM, as fast as Paxos, accommodating SMR in SCADA • Cost-benefit analysis: – RTU (1 h 30 m), FE (17 h 47 m), SCADA (26 h)

Conclusion of Session 2 • Combinations of techniques, even if not perfect • Both prevention and tolerance are necessary

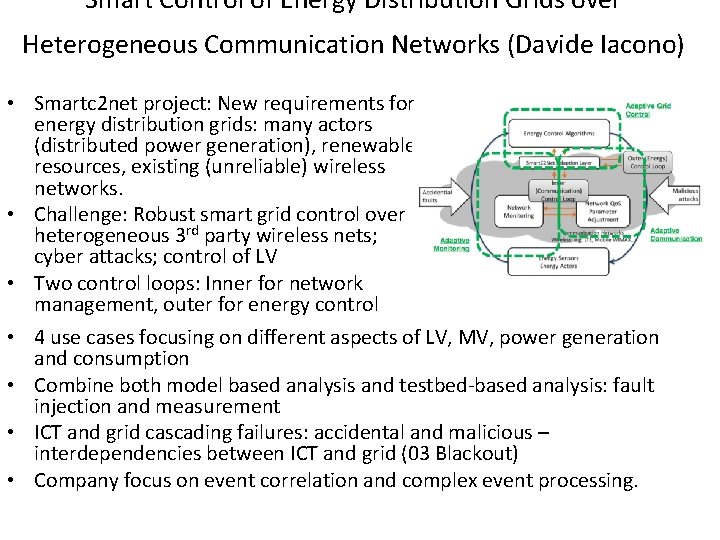
Smart Control of Energy Distribution Grids over Heterogeneous Communication Networks (Davide Iacono) • Smartc 2 net project: New requirements for energy distribution grids: many actors (distributed power generation), renewable resources, existing (unreliable) wireless networks. • Challenge: Robust smart grid control over heterogeneous 3 rd party wireless nets; cyber attacks; control of LV • Two control loops: Inner for network management, outer for energy control • 4 use cases focusing on different aspects of LV, MV, power generation and consumption • Combine both model based analysis and testbed-based analysis: fault injection and measurement • ICT and grid cascading failures: accidental and malicious – interdependencies between ICT and grid (03 Blackout) • Company focus on event correlation and complex event processing.









