Subject Name MANAGEMENT INFORMATION SYSTEM Subject Code 10
Subject Name: MANAGEMENT INFORMATION SYSTEM Subject Code: 10 IS 72 Prepared By: HARKIRANPREET Department: ISE Date: 12 November, 2014 5/10/14

UNIT 7 SECURITY AND ETHICAL CHALLENGES 5/10/14

LEARNING OBJECTIVES • Identify several ethical issues regarding how the use of information technologies in business affects – Employment – Individuality – Working conditions – Privacy – Crime – Health – Solutions to societal problems 5/10/14

CONTD… ØIdentify several types of security management strategies and defenses • Explain how they can be used to ensure the security of business applications of information technology ØPropose ways that business managers and professionals can help lessen the harmful effects, and increase the beneficial effects, of the use of information technology 5/10/14

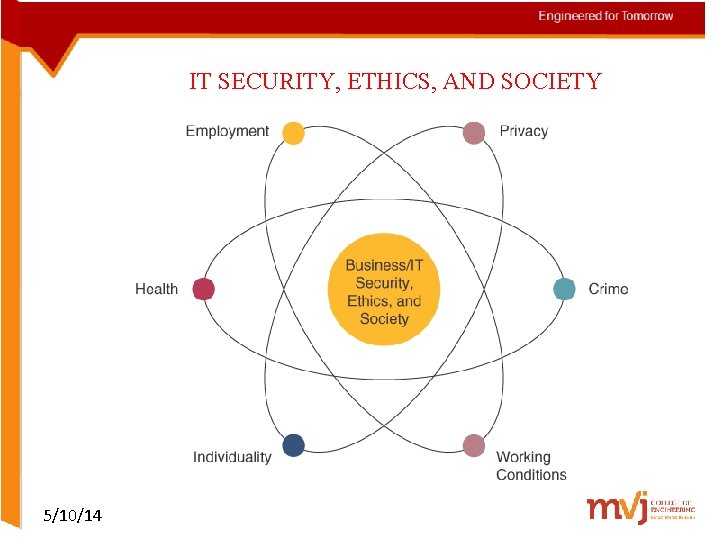
IT SECURITY, ETHICS, AND SOCIETY ØInformation technology has both beneficial and detrimental effects on society and people ØManage work activities to minimize the detrimental effects ØStrive to optimize the beneficial effects 5/10/14
BUSINESS ETHICS q. Ethical responsibilities of business professionals q. Promote ethical uses of information technology q. Accept the ethical responsibilities of your job q. Properly perform your role as a human resource q. Consider 5/10/14 the ethical dimensions of activities and decisions
IT SECURITY, ETHICS, AND SOCIETY 5/10/14
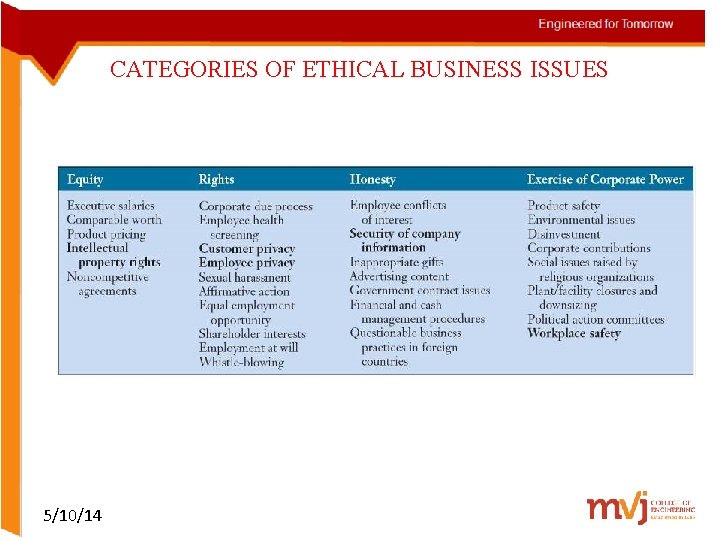
CATEGORIES OF ETHICAL BUSINESS ISSUES 5/10/14
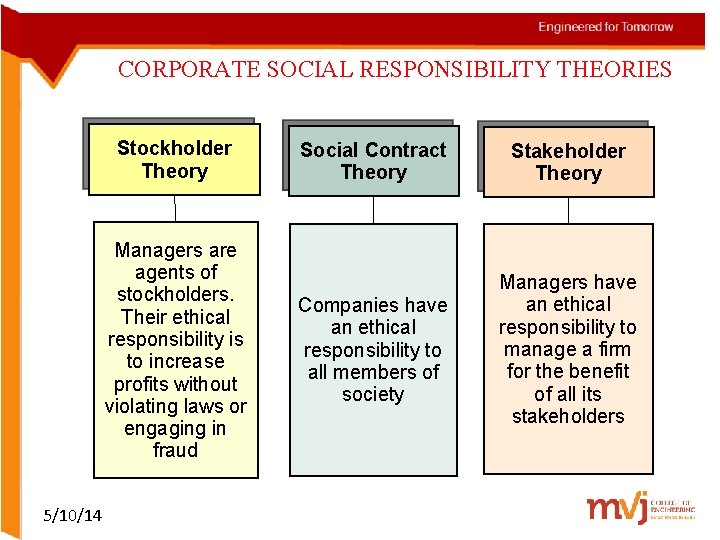
CORPORATE SOCIAL RESPONSIBILITY THEORIES Stockholder Theory Managers are agents of stockholders. Their ethical responsibility is to increase profits without violating laws or engaging in fraud 5/10/14 Social Contract Theory Stakeholder Theory Companies have an ethical responsibility to all members of society Managers have an ethical responsibility to manage a firm for the benefit of all its stakeholders

PRINCIPLES OF TECHNOLOGY ETHICS 5/10/14

ETHICAL GUIDELINES OF THE AITP 5/10/14

RESPONSIBLE PROFESSIONAL GUIDELINES A responsible professional Acts with integrity Increases personal competence Sets high standards of personal performance Accepts responsibility for his/her work Advances the health, privacy, and general welfare of the public 5/10/14
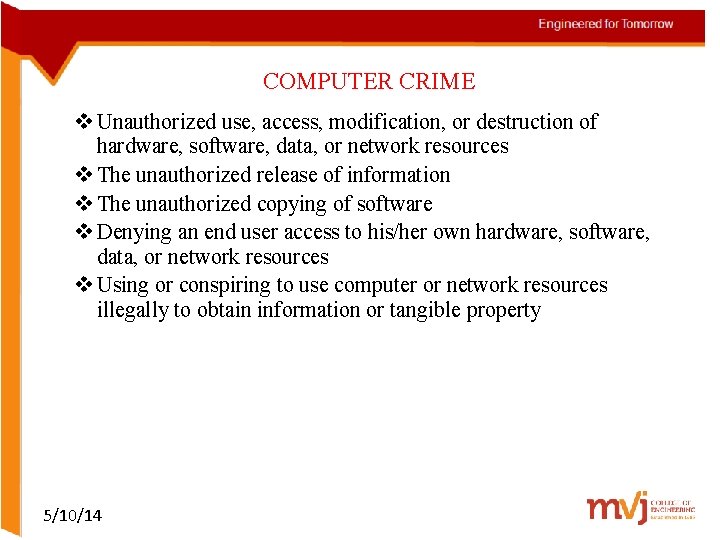
COMPUTER CRIME v Unauthorized use, access, modification, or destruction of hardware, software, data, or network resources v The unauthorized release of information v The unauthorized copying of software v Denying an end user access to his/her own hardware, software, data, or network resources v Using or conspiring to use computer or network resources illegally to obtain information or tangible property 5/10/14
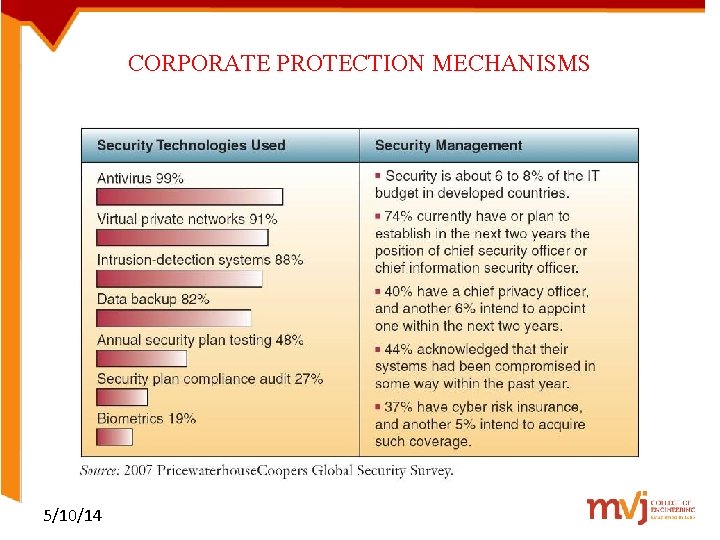
CORPORATE PROTECTION MECHANISMS 5/10/14
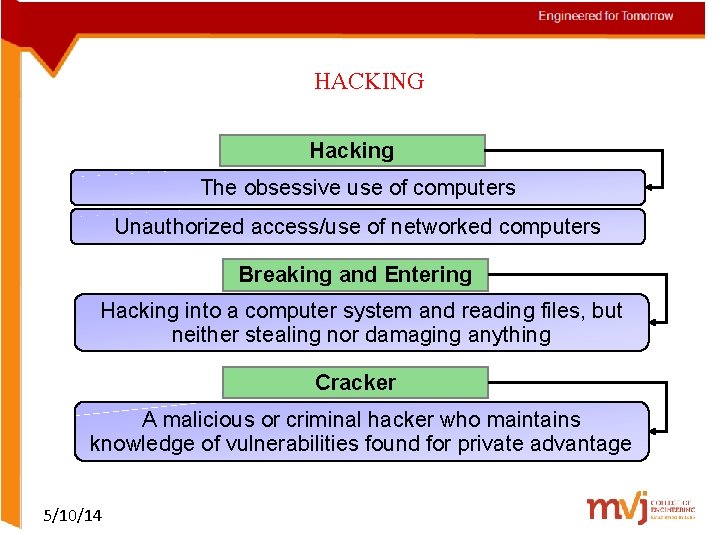
HACKING Hacking The obsessive use of computers Unauthorized access/use of networked computers Breaking and Entering Hacking into a computer system and reading files, but neither stealing nor damaging anything Cracker A malicious or criminal hacker who maintains knowledge of vulnerabilities found for private advantage 5/10/14

COMMON HACKING TACTICS 5/10/14

CYBER THEFT Many computer crimes involve theft of money Most are “inside jobs” that involve unauthorized network entry and alteration of databases to cover the tracks of the employees involved Many attacks occur through the Internet Most companies don’t reveal that they have been targets or victims of cyber crime 5/10/14
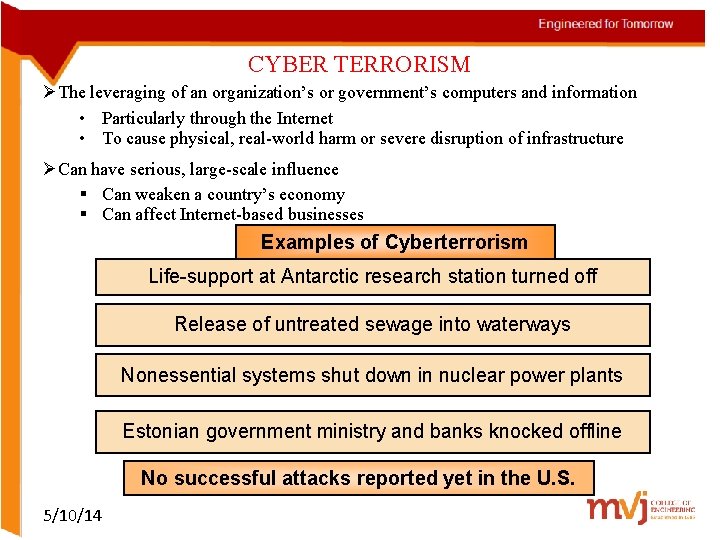
CYBER TERRORISM ØThe leveraging of an organization’s or government’s computers and information • Particularly through the Internet • To cause physical, real-world harm or severe disruption of infrastructure ØCan have serious, large-scale influence § Can weaken a country’s economy § Can affect Internet-based businesses Examples of Cyberterrorism Life-support at Antarctic research station turned off Release of untreated sewage into waterways Nonessential systems shut down in nuclear power plants Estonian government ministry and banks knocked offline No successful attacks reported yet in the U. S. 5/10/14
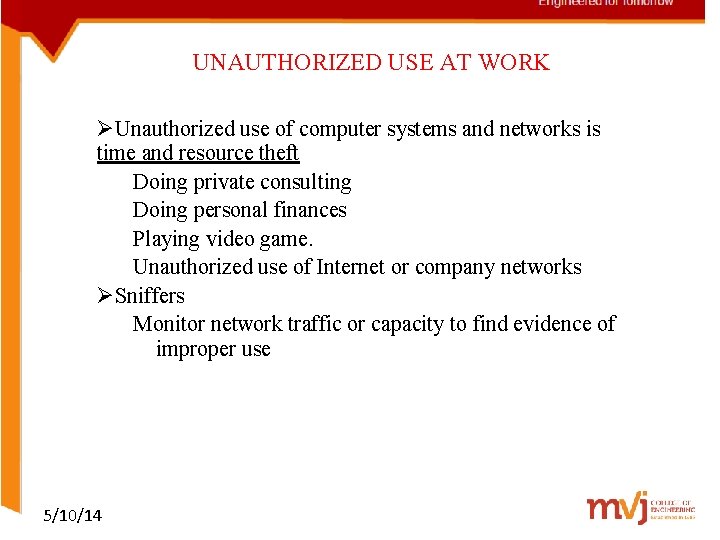
UNAUTHORIZED USE AT WORK ØUnauthorized use of computer systems and networks is time and resource theft Doing private consulting Doing personal finances Playing video game. Unauthorized use of Internet or company networks ØSniffers Monitor network traffic or capacity to find evidence of improper use 5/10/14
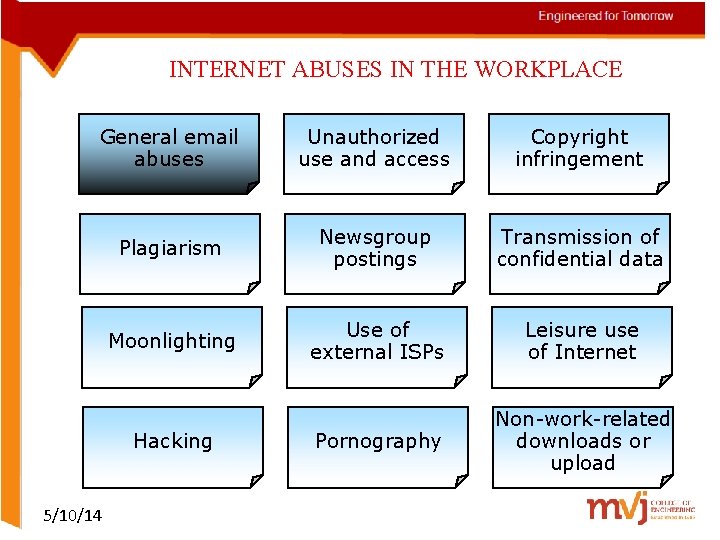
INTERNET ABUSES IN THE WORKPLACE General email abuses Unauthorized use and access Copyright infringement Plagiarism Newsgroup postings Transmission of confidential data Moonlighting Use of external ISPs Leisure use of Internet Pornography Non-work-related downloads or upload Hacking 5/10/14

SOFTWARE PIRACY ØSoftware Piracy • Unauthorized copying of computer programs ØLicensing • Purchasing software is really a payment for a license for fair use • Site license allows a certain number of copies • Public domain software is not copyrighted A third of the software industry’s revenues are lost to piracy 5/10/14

THEFT OF INTELLECTUAL PROPERTY ØIntellectual Property q Copyrighted material q Includes music, videos, and software images, articles, books, have made ØCopyright Infringement is Illegal q Peer-to-peer networking techniques it easy to trade pirated intellectual property ØPublishers Offer Inexpensive Online Music q Illegal downloading of music down and continues to drop 5/10/14 and video is

VIRUSES AND WORMS ØA virus is a program that cannot work without being inserted into another program • A worm is a distinct program that can run unaided ØThese programs copy annoying or destructive routines into networked computers • Copy routines spread the virus ØCommonly transmitted through • The Internet and online services • Email and file attachments • Disks from contaminated computers • Shareware 5/10/14
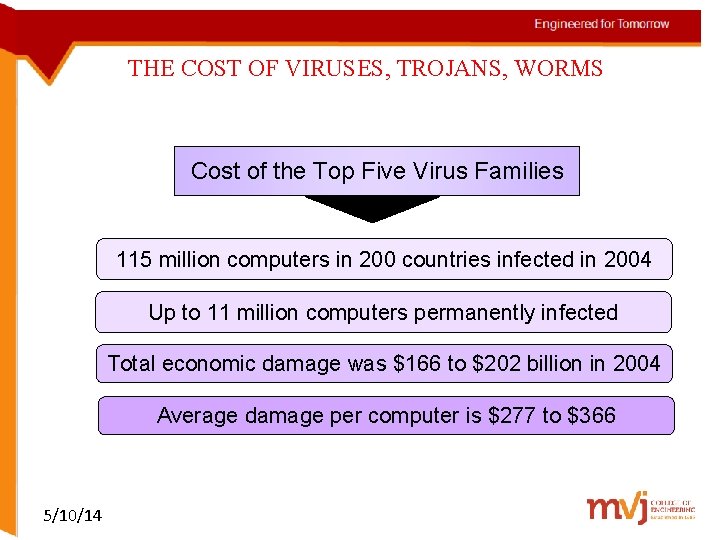
THE COST OF VIRUSES, TROJANS, WORMS Cost of the Top Five Virus Families 115 million computers in 200 countries infected in 2004 Up to 11 million computers permanently infected Total economic damage was $166 to $202 billion in 2004 Average damage per computer is $277 to $366 5/10/14
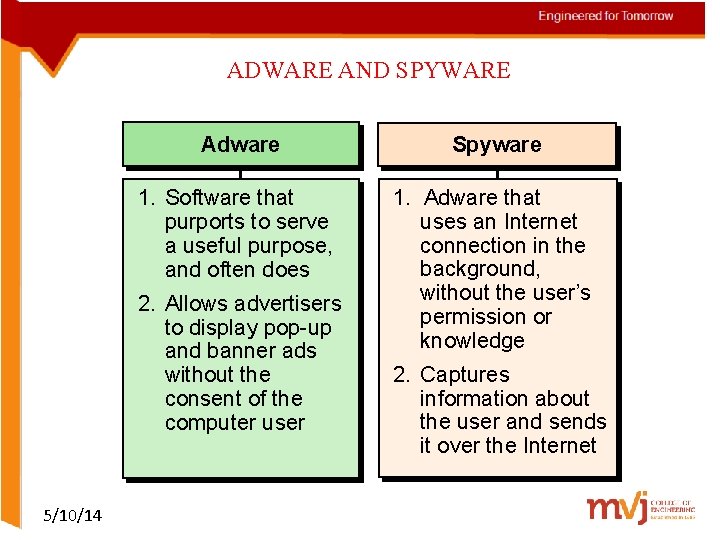
ADWARE AND SPYWARE Adware Spyware 1. Software that purports to serve a useful purpose, and often does 1. Adware that uses an Internet connection in the background, without the user’s permission or knowledge 2. Allows advertisers to display pop-up and banner ads without the consent of the computer user 5/10/14 2. Captures information about the user and sends it over the Internet

PRIVACY ISSUES ØThe power of information technology to store and retrieve information can have a negative effect on every individual’s right to privacy § Personal information is collected with every visit to a Web site § Confidential information stored by credit bureaus, credit card companies, and the government has been stolen or misused ØViolation of Privacy • Accessing individuals’ private email conversations and computer records • Collecting and sharing information about individuals gained from their visits to Internet websites ØComputer Monitoring • Always knowing where a person is • Mobile and paging services are becoming more closely associated with people than with places 5/10/14

PRIVACY LAWS • Electronic Communications Privacy Act and Computer Fraud and Abuse Act o Prohibit intercepting data communications messages, stealing or destroying data, or trespassing in federal computer systems • U. S. Computer Matching and Privacy Act o Regulates the matching of data held in federal agency files to verify eligibility for federal programs 5/10/14

COMPUTER LIBEL AND CENSORSHIP • The opposite side of the privacy debate… – Freedom of information, speech, and press • Biggest battlegrounds – Bulletin boards – Email boxes – Online files of Internet and public networks • Weapons used in this battle – Spamming – Flame mail – Libel laws – Censorship 5/10/14
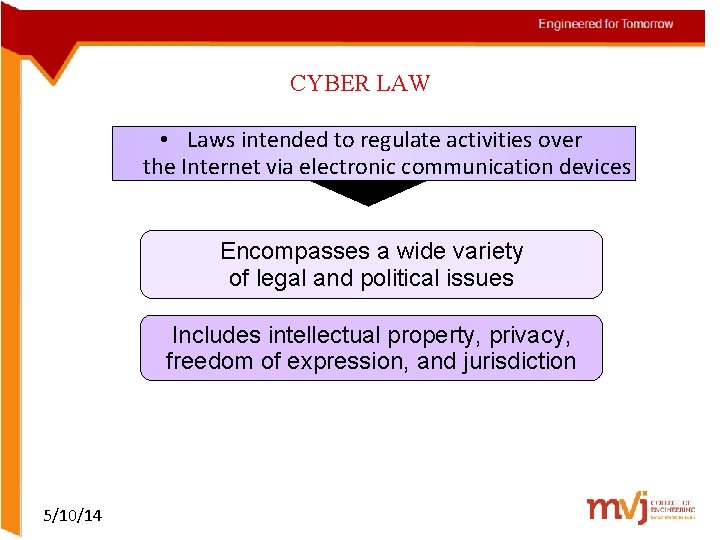
CYBER LAW • Laws intended to regulate activities over the Internet via electronic communication devices Encompasses a wide variety of legal and political issues Includes intellectual property, privacy, freedom of expression, and jurisdiction 5/10/14
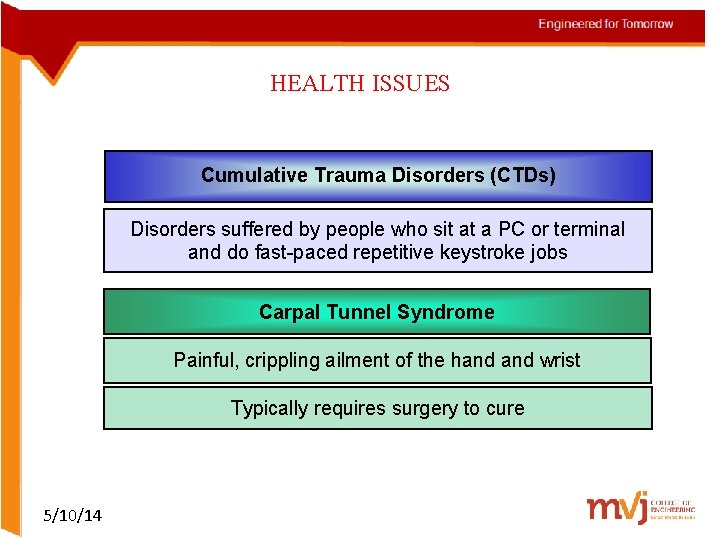
HEALTH ISSUES Cumulative Trauma Disorders (CTDs) Disorders suffered by people who sit at a PC or terminal and do fast-paced repetitive keystroke jobs Carpal Tunnel Syndrome Painful, crippling ailment of the hand wrist Typically requires surgery to cure 5/10/14
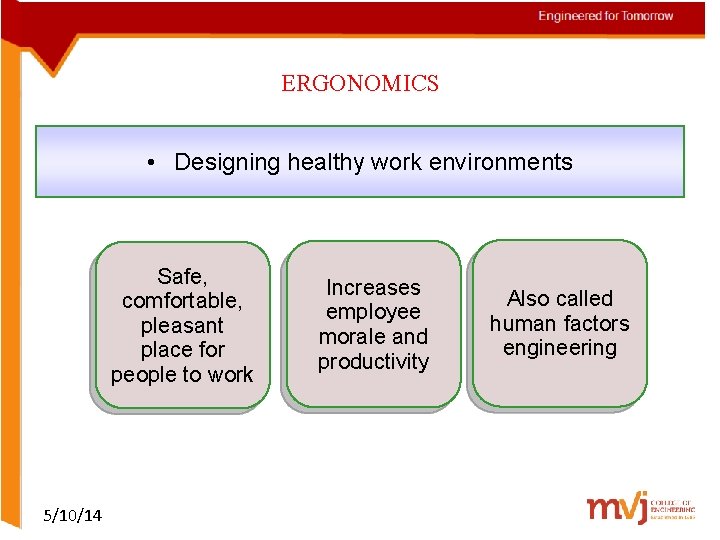
ERGONOMICS • Designing healthy work environments Safe, comfortable, pleasant place for people to work 5/10/14 Increases employee morale and productivity Also called human factors engineering
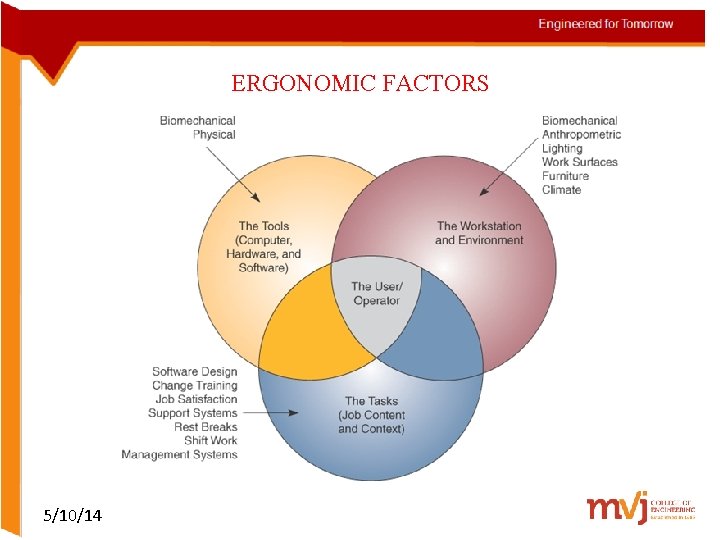
ERGONOMIC FACTORS 5/10/14
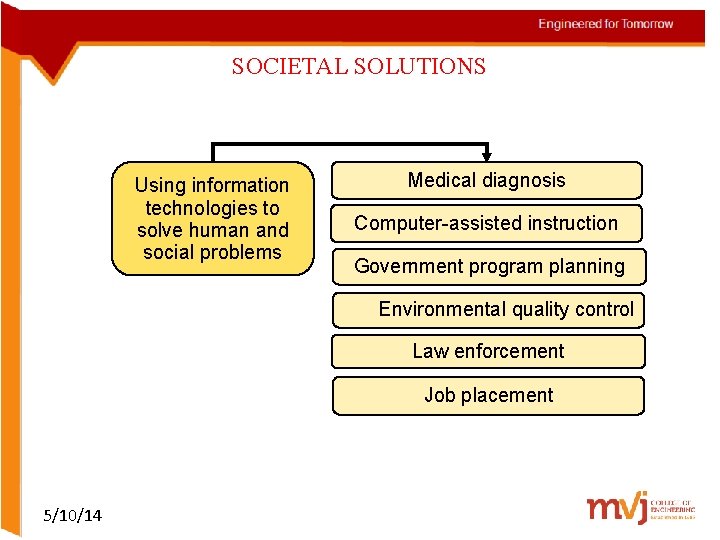
SOCIETAL SOLUTIONS Using information technologies to solve human and social problems Medical diagnosis Computer-assisted instruction Government program planning Environmental quality control Law enforcement Job placement 5/10/14

SECURITY MANAGEMENT OF IT ØThe Internet was developed for inter-operability, not impenetrability • Business managers and professionals alike are responsible for the security, quality, and performance of business information systems • Hardware, software, networks, and data resources must be protected by a variety of security measures 5/10/14
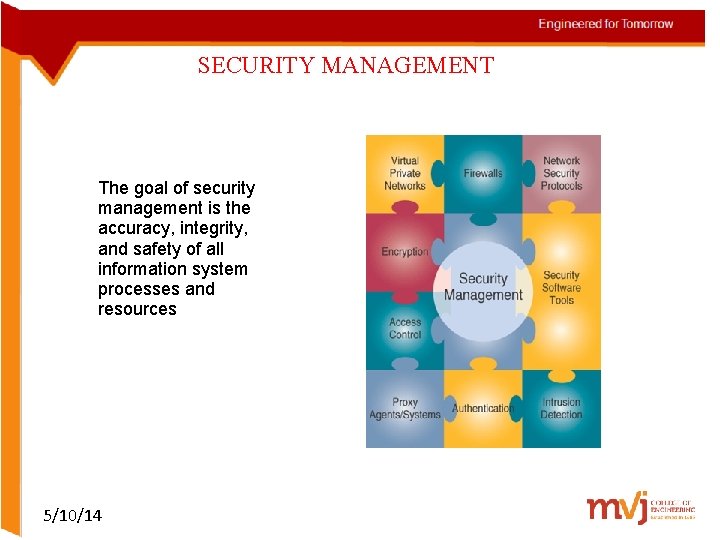
SECURITY MANAGEMENT The goal of security management is the accuracy, integrity, and safety of all information system processes and resources 5/10/14
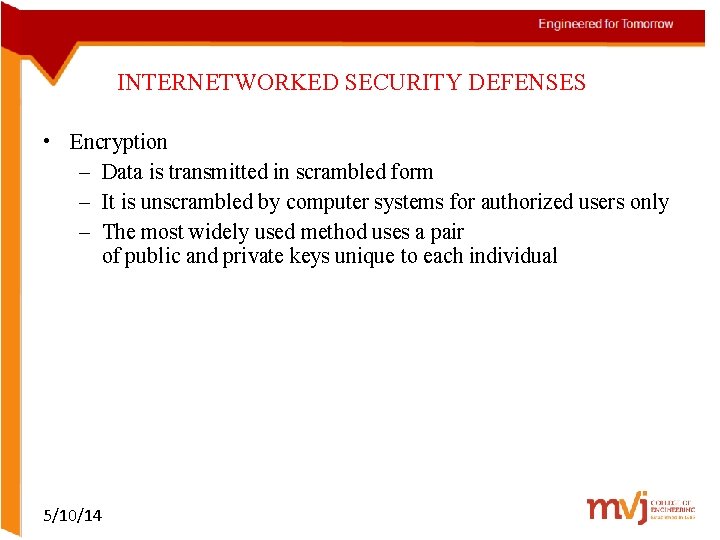
INTERNETWORKED SECURITY DEFENSES • Encryption – Data is transmitted in scrambled form – It is unscrambled by computer systems for authorized users only – The most widely used method uses a pair of public and private keys unique to each individual 5/10/14
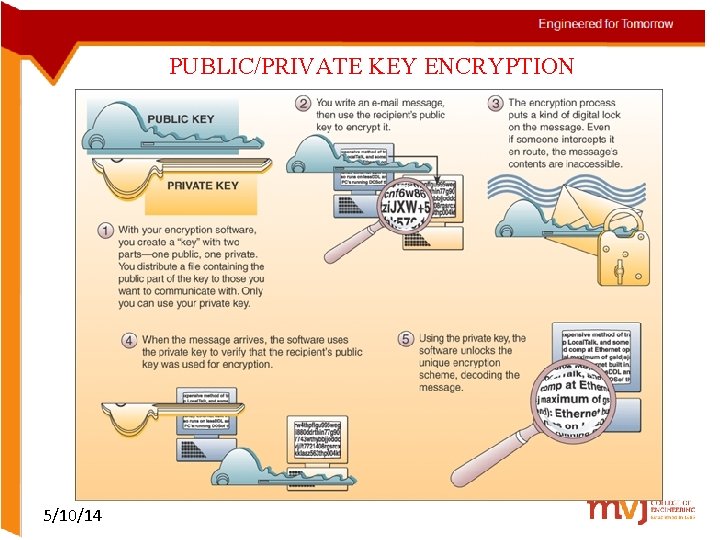
PUBLIC/PRIVATE KEY ENCRYPTION 5/10/14
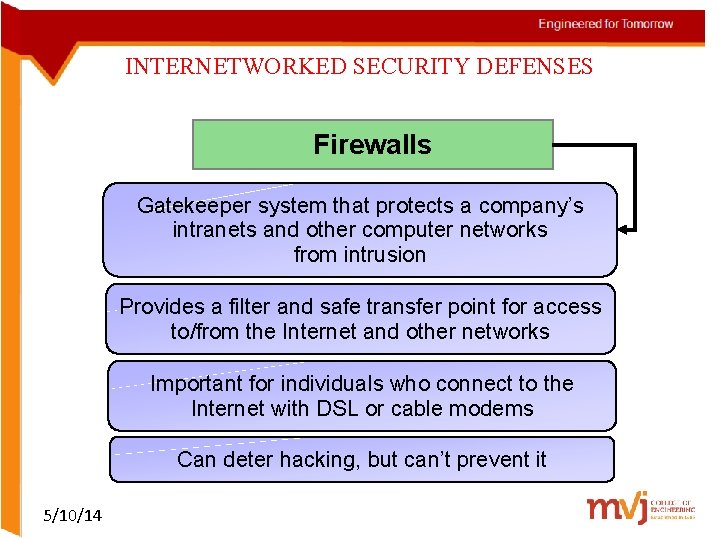
INTERNETWORKED SECURITY DEFENSES Firewalls Gatekeeper system that protects a company’s intranets and other computer networks from intrusion Provides a filter and safe transfer point for access to/from the Internet and other networks Important for individuals who connect to the Internet with DSL or cable modems Can deter hacking, but can’t prevent it 5/10/14
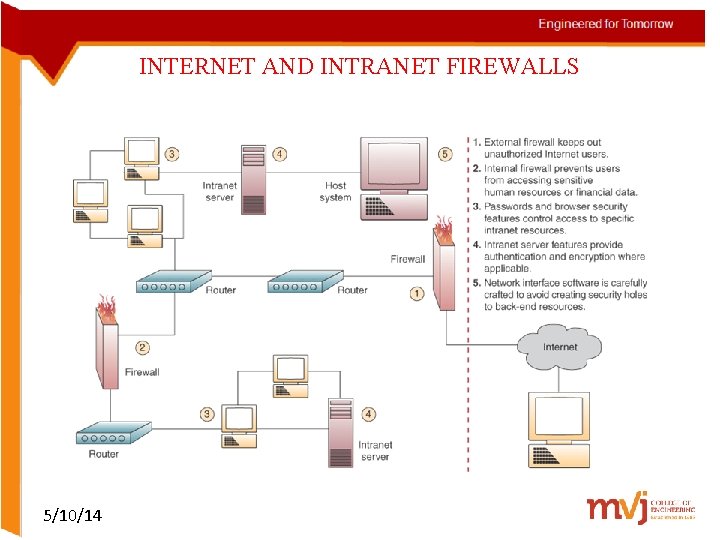
INTERNET AND INTRANET FIREWALLS 5/10/14
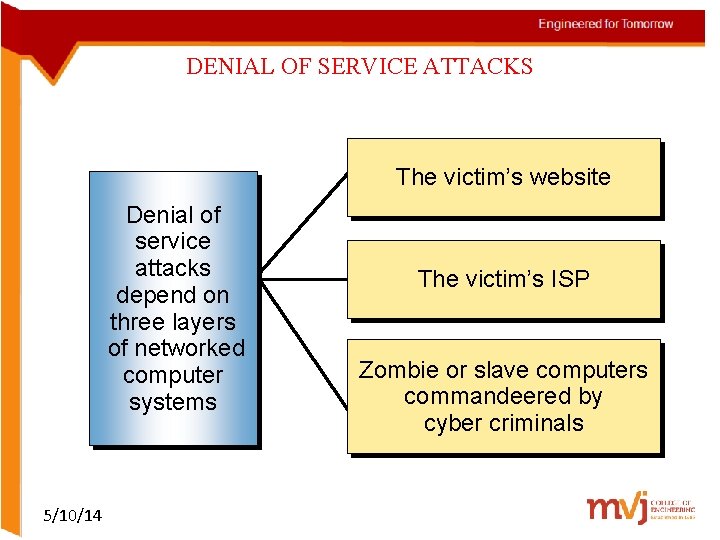
DENIAL OF SERVICE ATTACKS The victim’s website Denial of service attacks depend on three layers of networked computer systems 5/10/14 The victim’s ISP Zombie or slave computers commandeered by cyber criminals
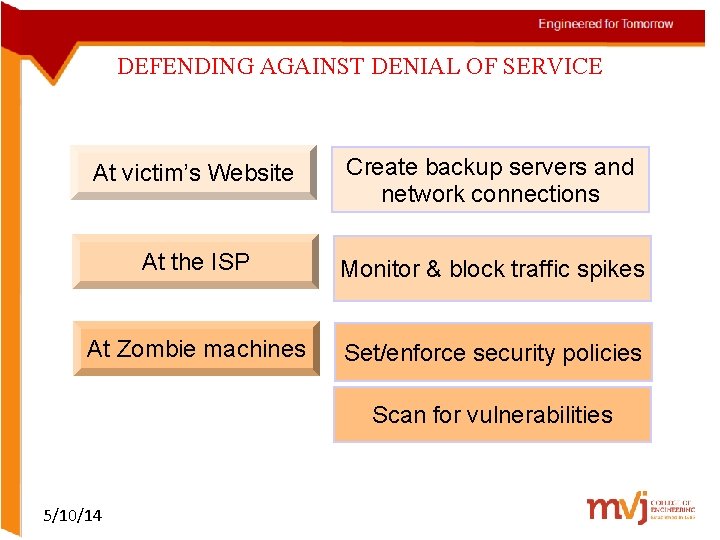
DEFENDING AGAINST DENIAL OF SERVICE At victim’s Website Create backup servers and network connections At the ISP Monitor & block traffic spikes At Zombie machines Set/enforce security policies Scan for vulnerabilities 5/10/14

INTERNETWORKED SECURITY DEFENSES • Email Monitoring – Use content monitoring software to scan for troublesome words • Virus Defenses – Centralize the updating and distribution of antivirus software – Use a security suite that integrates virus protection with firewalls, Web security, and content blocking features 5/10/14

contd… • Security Codes – Multilevel password system – Encrypted passwords – Smart cards with microprocessors • Backup Files – Duplicate files of data or programs • Security Monitors – Monitor the use of computers and networks – Protects them from unauthorized use, fraud, and destruction 5/10/14
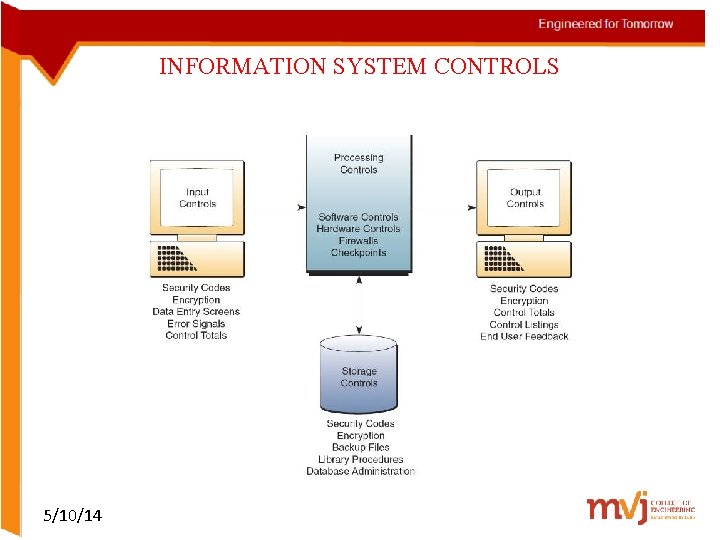
INFORMATION SYSTEM CONTROLS 5/10/14

AUDITING IT SECURITY • IT Security Audits – Performed by internal or external auditors – Review and evaluation of security measures and management policies – Goal is to ensure that proper and adequate measures and policies are in place 5/10/14

PROTECTING YOURSELF FROM CYBER CRIME 5/10/14

Thank you…. . 5/10/14
- Slides: 47