STUXNET Summary What is Stuxnet Industial Control Systems





- Slides: 14

STUXNET

Summary • What is Stuxnet? • Industial Control Systems • The target/s of Stuxnet. • How Stuxnet spreads. • The impact of Stuxnet on PLC’s

3 Stuxnet: Overview • June 2010: A worm targeting Siemens Win. CC industrial control system. • Targets high speed variable-frequency programmable logic motor controllers from just two vendors: Vacon (Finland) and Fararo Paya (Iran) • Only when the controllers are running at 807 Hz to 1210 Hz. Makes the frequency of those controllers vary from 1410 Hz to 2 Hz to 1064 Hz.

Industrial Control Systems (ICS) • ICS are operated by a specialized assembly like code on programmable logic controllers (PLCs). • The PLCs are programmed typically from Windows computers. • The ICS are not connected to the Internet. • ICS usually consider availability and ease of maintenance first and security last.

5 Seimens SIMATIC PLCs

How it works. • Transferred through USB sticks. • Designed to be spread to non-online machines • Windows Explorer LNK file exploit • When scanned, it dropped a large. dll file containing the malicious code onto the computer. • Uses two stolen certificates to prevent unauthorized- access alarms. • Realtek Semiconductors • JMicron Technology Corp • Both in Taiwan, in close vicinity.

How it works cont’d… • Each time Stuxnet infected a system, it “phoned home” to one of two domains: • www. mypremierfutbol. com • www. todaysfutbol. com • hosted on servers in Malaysia and Denmark • Included internal & external IP addresses, OS, and if the machine was running step 7 • Stuxnet would spread from system to system within a LAN until it found a PLC. • The original s 7 otbxdx. dll is responsible for handling PLC block exchange between the programming device and the PLC. • By replacing this. dll file with its own, Stuxnet is able to perform the following actions: • Monitor PLC blocks being written to and read from the PLC. • Infect a PLC by inserting its own blocks

Stuxnet Overview • Components used • Multiple Zero-day exploits • Windows rootkit • PLC rootkit (first ever) • Antivirus evasion • Peer-to-Peer updates • Signed driver with a valid certificate • Command control interface • Stuxnet consists of a large. dll file • Designed to sabotage industrial processes controlled by Siemens SIMATIC Win. CC and PCS 7 systems.

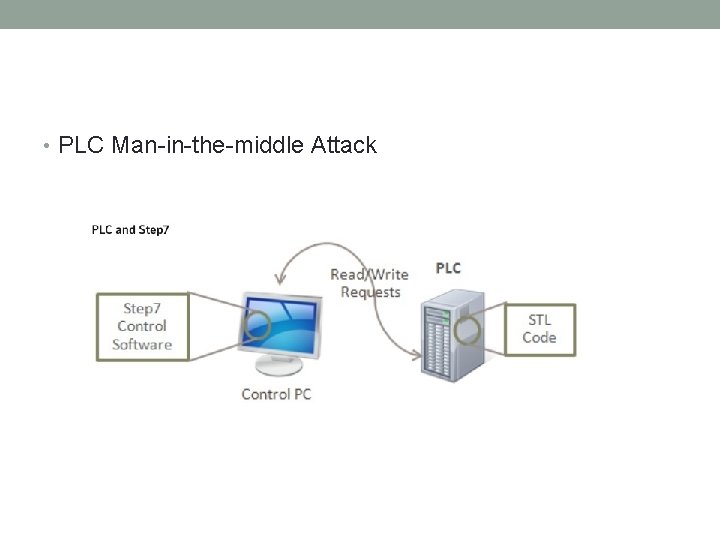
• PLC Man-in-the-middle Attack

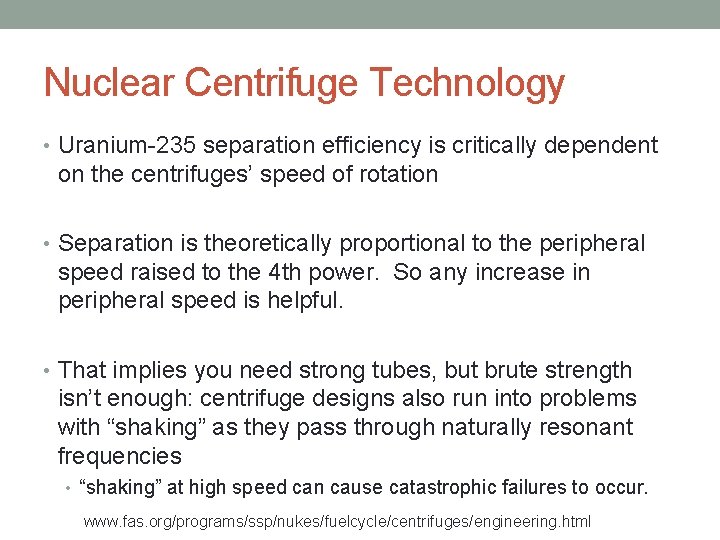
Nuclear Centrifuge Technology • Uranium-235 separation efficiency is critically dependent on the centrifuges’ speed of rotation • Separation is theoretically proportional to the peripheral speed raised to the 4 th power. So any increase in peripheral speed is helpful. • That implies you need strong tubes, but brute strength isn’t enough: centrifuge designs also run into problems with “shaking” as they pass through naturally resonant frequencies • “shaking” at high speed can cause catastrophic failures to occur. www. fas. org/programs/ssp/nukes/fuelcycle/centrifuges/engineering. html

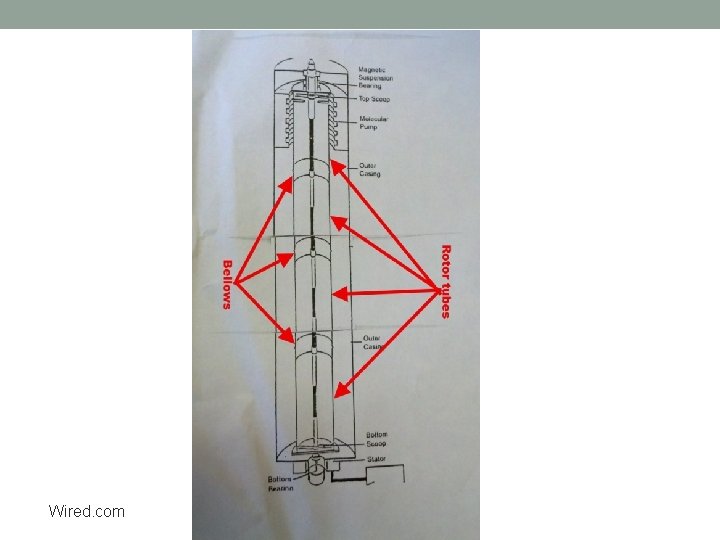
Wired. com

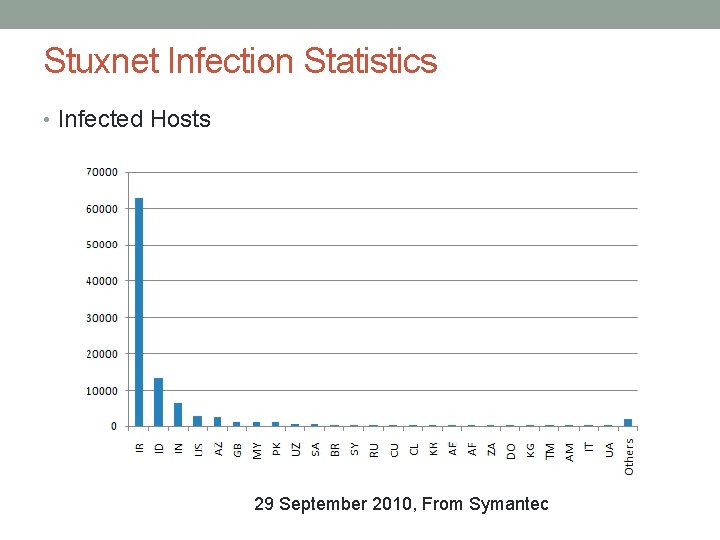
Stuxnet Infection Statistics • Infected Hosts 29 September 2010, From Symantec

Let’s watch it happen! • http: //www. youtube. com/watch? v=cf 0 jlz. VCy. OI

The Targets