Structural Holes Weak Ties Overview Granovetter Strength of












- Slides: 31

Structural Holes & Weak Ties Overview Granovetter: Strength of Weak Ties What are ‘weak ties’? why are they ‘strong’? Burt: Structural Holes What are they? What do they do? How do they work? Methods & Measures: 1) Go Over assignment 1 2) Moving data around SAS Data steps 3) Calculating Ego-Network Measures From Ego-network modules From Global Networks

The Strength of Weak Ties Granovetter argues that, under many circumstances, strong ties are less useful than weak ties. Why? Redundancy Local Density, Global Fragmentation

The Strength of Weak Ties What are the implications? For individuals? For Communities?

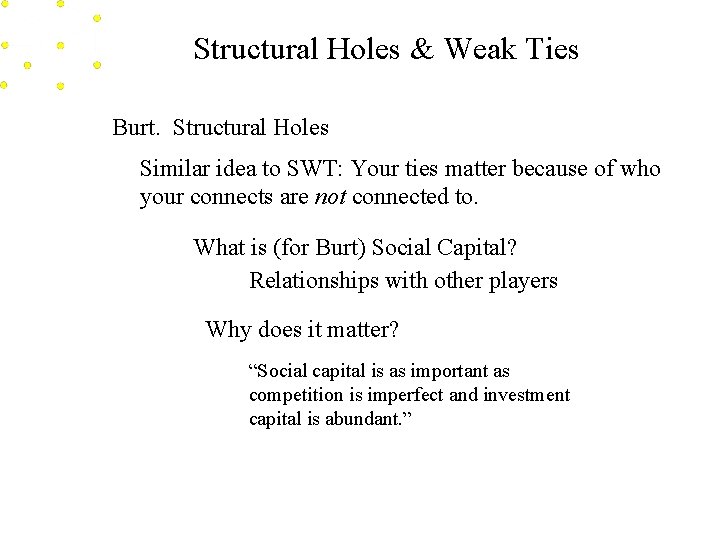
Structural Holes & Weak Ties Burt. Structural Holes Similar idea to SWT: Your ties matter because of who your connects are not connected to. What is (for Burt) Social Capital? Relationships with other players Why does it matter? “Social capital is as important as competition is imperfect and investment capital is abundant. ”

Structural Holes & Weak Ties A structural Hole is a buffer: a space between the people you are connected to. 2 ways: Cohesion Structural Equivalence

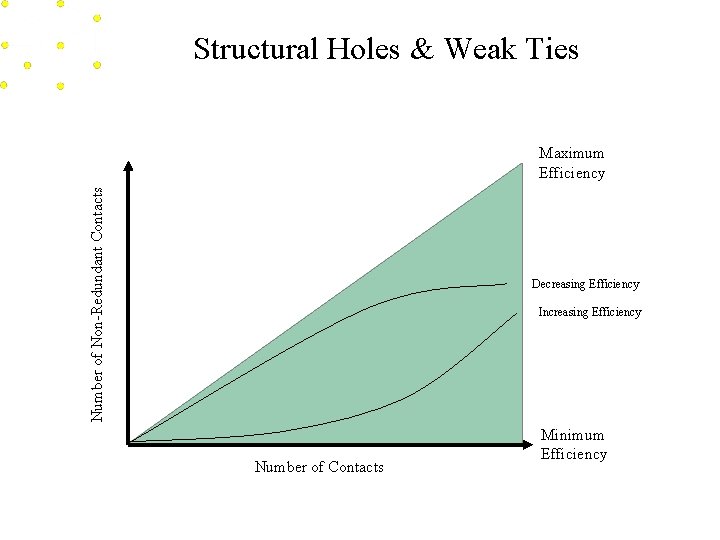
Structural Holes & Weak Ties Efficiency Maximize the number of non-redundant contacts Effectiveness Draw your primary contacts from different social worlds

Structural Holes & Weak Ties Number of Non-Redundant Contacts Maximum Efficiency Decreasing Efficiency Increasing Efficiency Number of Contacts Minimum Efficiency

Structural Holes & Weak Ties Difference between SWT & SH: Burt’s claim is that he focuses directly on the causal agent active in Granovetter.

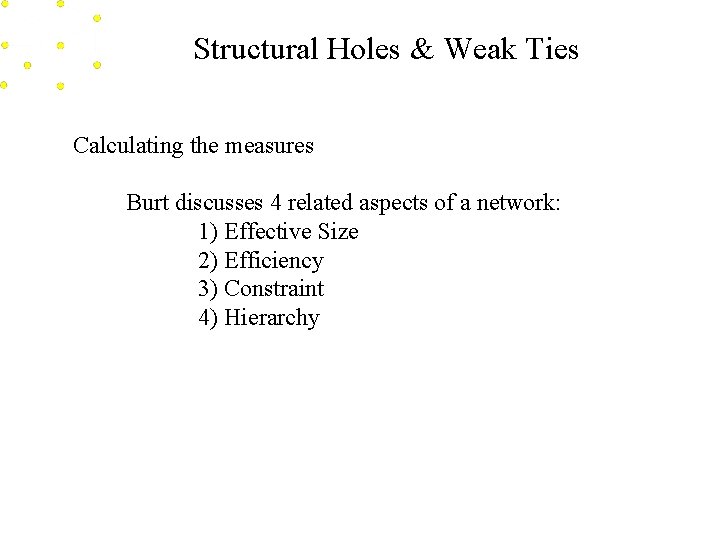
Structural Holes & Weak Ties Calculating the measures Burt discusses 4 related aspects of a network: 1) Effective Size 2) Efficiency 3) Constraint 4) Hierarchy

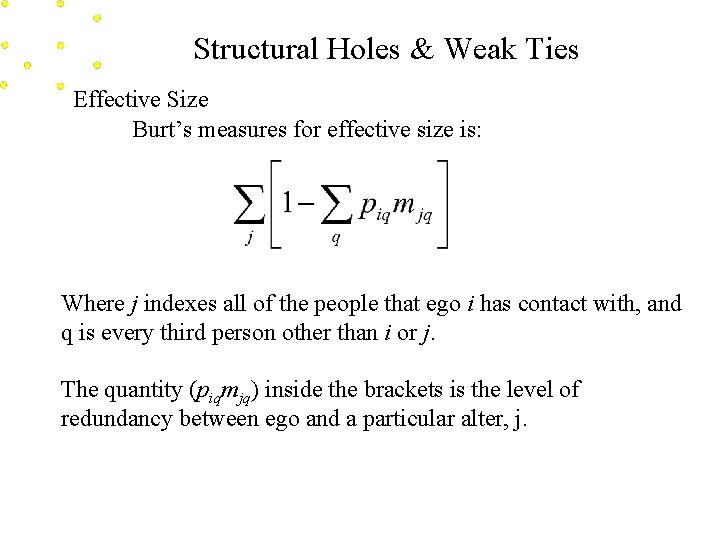
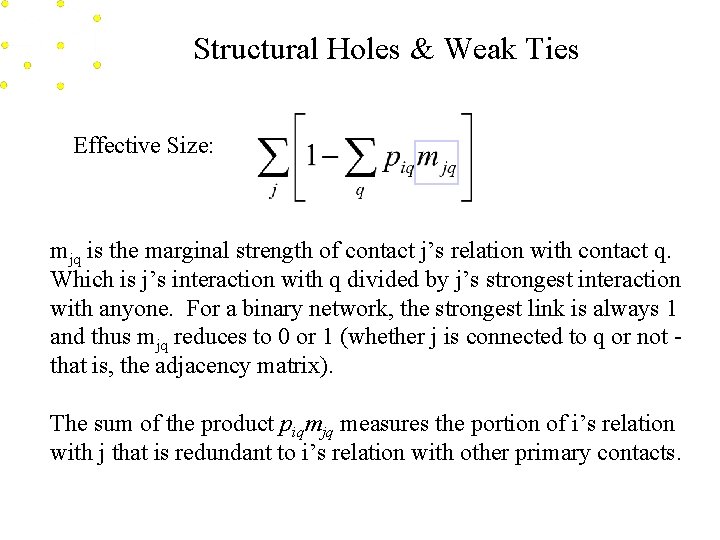
Structural Holes & Weak Ties Effective Size Conceptually the effective size is the number of people ego is connected to, minus the redundancy in the network, that is, it reduces to the non-redundant elements of the network. Effective size = Size - Redundancy

Structural Holes & Weak Ties Effective Size Burt’s measures for effective size is: Where j indexes all of the people that ego i has contact with, and q is every third person other than i or j. The quantity (piqmjq) inside the brackets is the level of redundancy between ego and a particular alter, j.

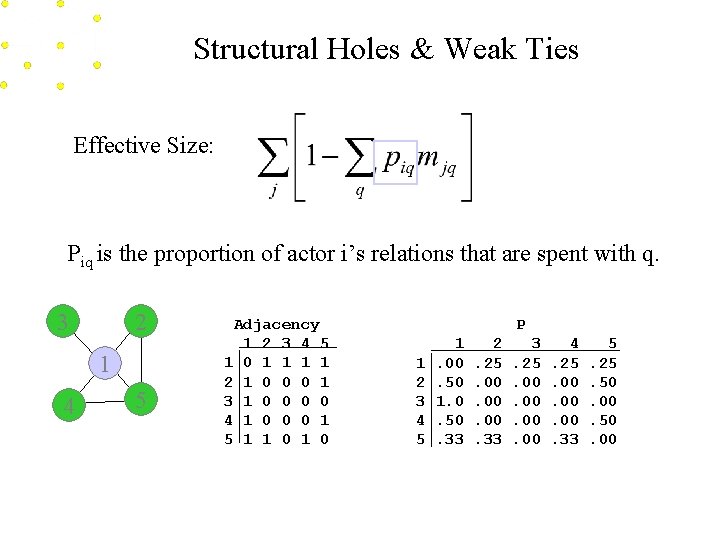
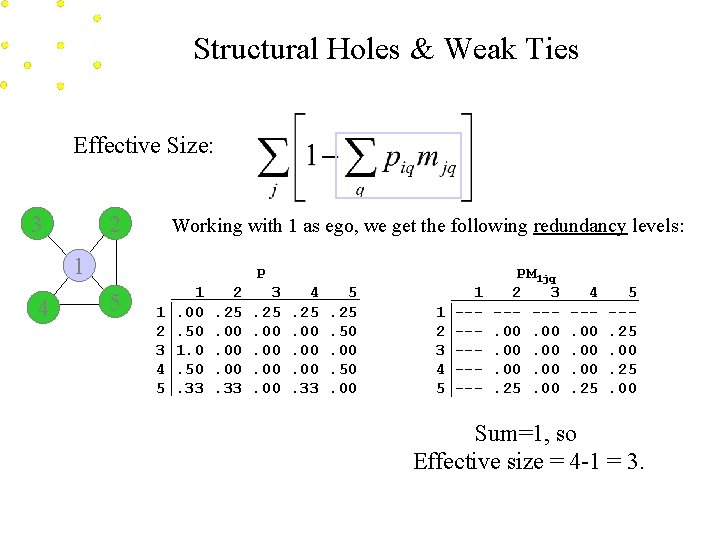
Structural Holes & Weak Ties Effective Size: Piq is the proportion of actor i’s relations that are spent with q. 3 2 1 4 5 Adjacency 1 2 3 4 5 1 0 1 1 2 1 0 0 0 1 3 1 0 0 4 1 0 0 0 1 5 1 1 0 P 1 2 3 4 5 1. 00. 50 1. 0. 50. 33 2. 25. 00. 00. 33 3. 25. 00. 00 4. 25. 00. 00. 33 5. 25. 50. 00

Structural Holes & Weak Ties Effective Size: mjq is the marginal strength of contact j’s relation with contact q. Which is j’s interaction with q divided by j’s strongest interaction with anyone. For a binary network, the strongest link is always 1 and thus mjq reduces to 0 or 1 (whether j is connected to q or not that is, the adjacency matrix). The sum of the product piqmjq measures the portion of i’s relation with j that is redundant to i’s relation with other primary contacts.

Structural Holes & Weak Ties Effective Size: 3 2 Working with 1 as ego, we get the following redundancy levels: 1 4 P 5 1 2 3 4 5 1. 00. 50 1. 0. 50. 33 2. 25. 00. 00. 33 3. 25. 00. 00 4. 25. 00. 00. 33 5. 25. 50. 00 1 2 3 4 5 1 ------ PM 1 jq 2 3 --- --. 00. 00. 00. 25. 00 4 --. 00. 00. 25 5 --. 25. 00 Sum=1, so Effective size = 4 -1 = 3.

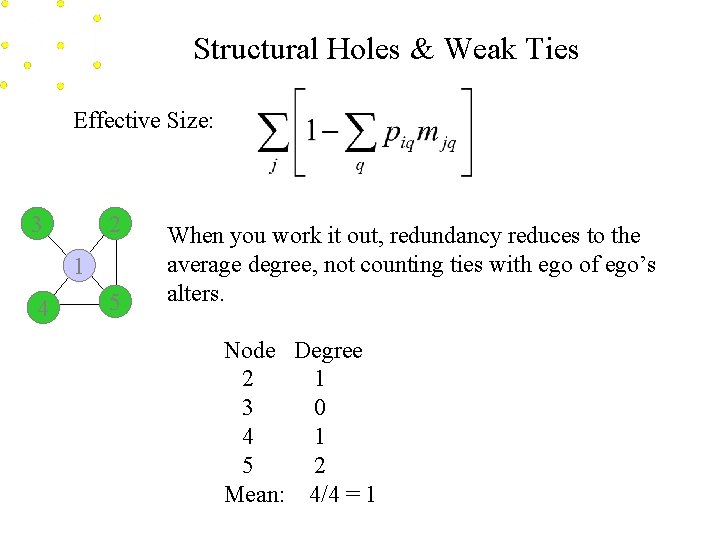
Structural Holes & Weak Ties Effective Size: 3 2 1 4 5 When you work it out, redundancy reduces to the average degree, not counting ties with ego of ego’s alters. Node Degree 2 1 3 0 4 1 5 2 Mean: 4/4 = 1

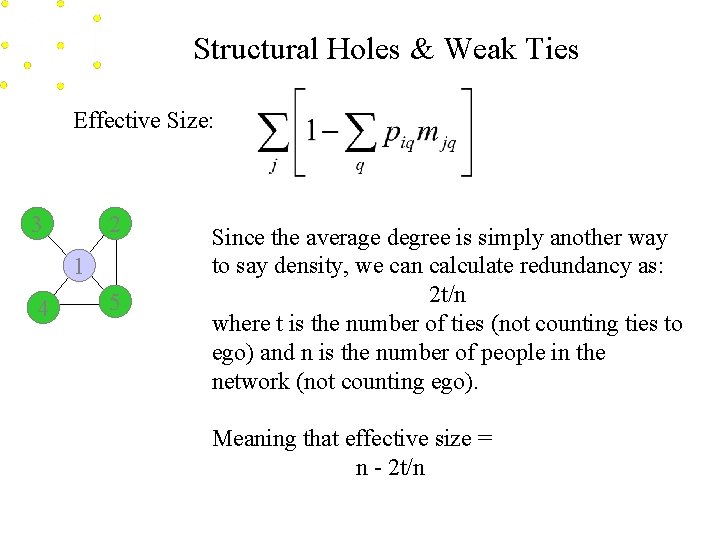
Structural Holes & Weak Ties Effective Size: 3 2 1 4 5 Since the average degree is simply another way to say density, we can calculate redundancy as: 2 t/n where t is the number of ties (not counting ties to ego) and n is the number of people in the network (not counting ego). Meaning that effective size = n - 2 t/n

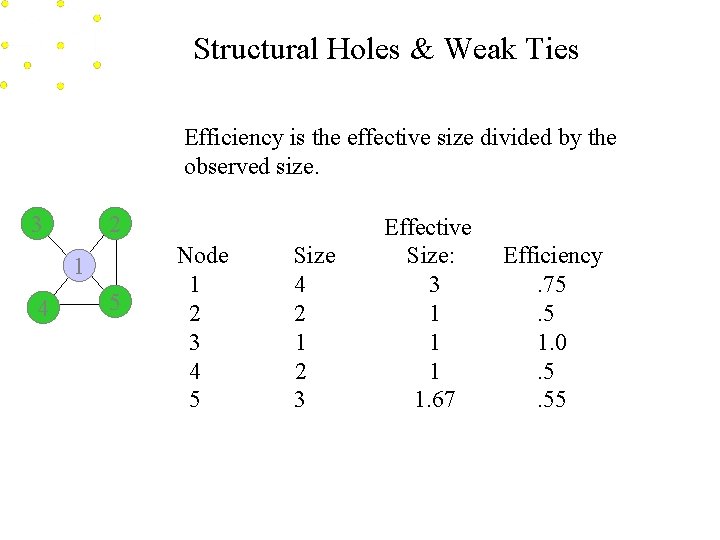
Structural Holes & Weak Ties Efficiency is the effective size divided by the observed size. 3 2 1 4 5 Node 1 2 3 4 5 Size 4 2 1 2 3 Effective Size: 3 1 1. 67 Efficiency. 75. 5 1. 0. 5. 55

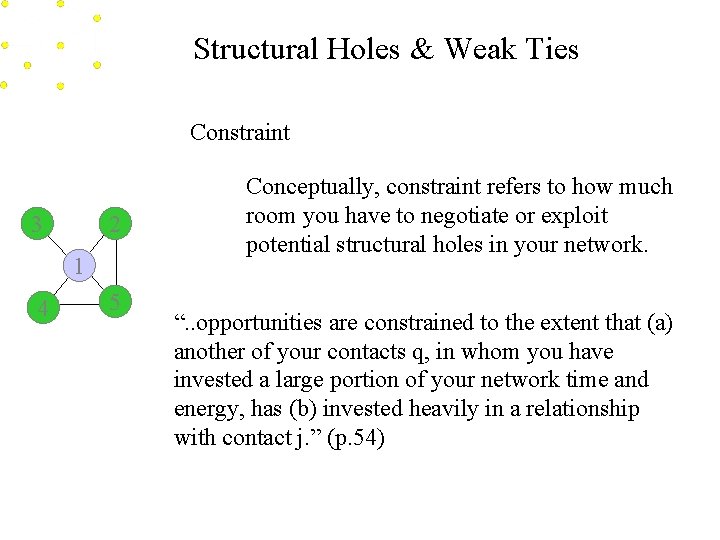
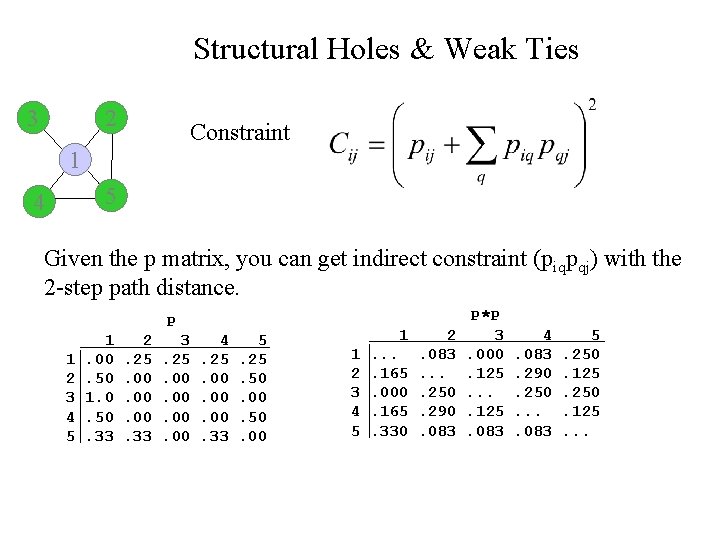
Structural Holes & Weak Ties Constraint 3 2 1 4 5 Conceptually, constraint refers to how much room you have to negotiate or exploit potential structural holes in your network. “. . opportunities are constrained to the extent that (a) another of your contacts q, in whom you have invested a large portion of your network time and energy, has (b) invested heavily in a relationship with contact j. ” (p. 54)

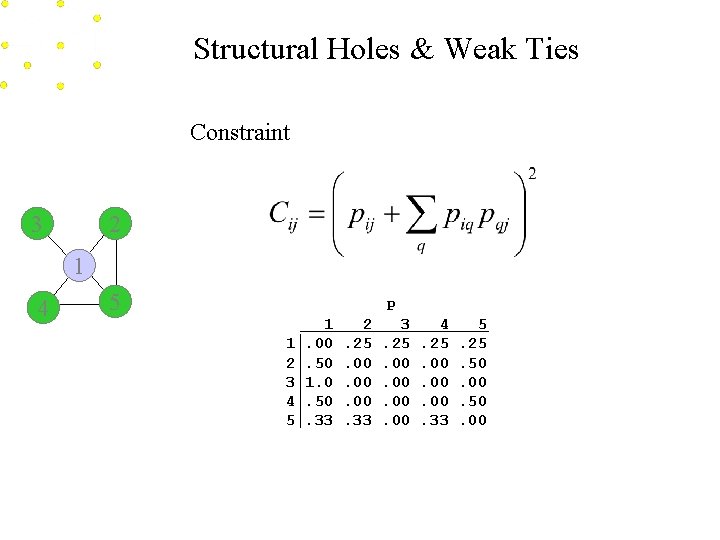
Structural Holes & Weak Ties Constraint 3 2 1 4 5 P 1 2 3 4 5 1. 00. 50 1. 0. 50. 33 2. 25. 00. 00. 33 3. 25. 00. 00 4. 25. 00. 00. 33 5. 25. 50. 00

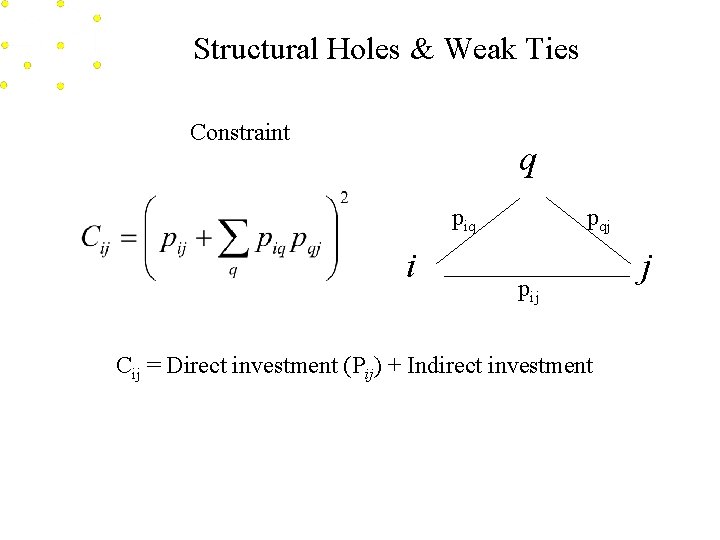
Structural Holes & Weak Ties Constraint q piq i pqj pij Cij = Direct investment (Pij) + Indirect investment j

Structural Holes & Weak Ties 3 2 Constraint 1 5 4 Given the p matrix, you can get indirect constraint (piqpqj) with the 2 -step path distance. P 1 2 3 4 5 1. 00. 50 1. 0. 50. 33 2. 25. 00. 00. 33 3. 25. 00. 00 4. 25. 00. 00. 33 5. 25. 50. 00 1 1 2 3 4 5 . . 165. 000. 165. 330 2. 083. . 250. 290. 083 P*P 3. 000. 125. 083 4. 083. 290. 250. . 083 5. 250. 125. . .

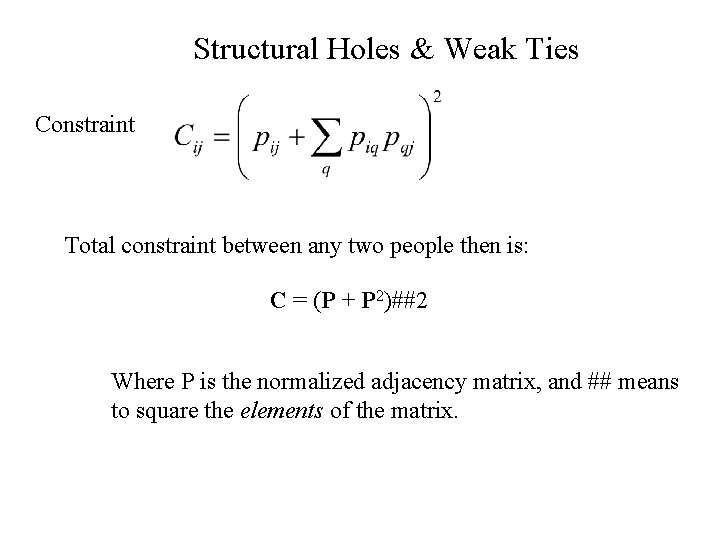
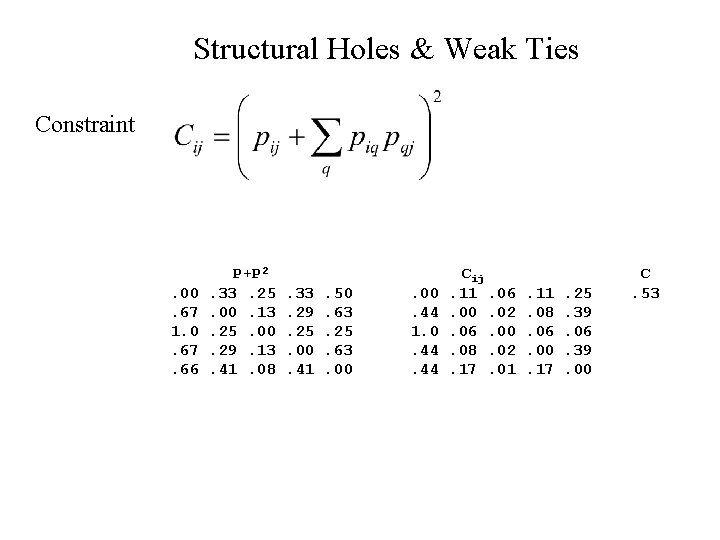
Structural Holes & Weak Ties Constraint Total constraint between any two people then is: C = (P + P 2)##2 Where P is the normalized adjacency matrix, and ## means to square the elements of the matrix.

Structural Holes & Weak Ties Constraint . 00. 67 1. 0. 67. 66 P+P 2. 33. 25. 00. 13. 25. 00. 29. 13. 41. 08 . 33. 29. 25. 00. 41 . 50. 63. 25. 63. 00. 44 1. 0. 44 Cij. 11. 06. 00. 02. 06. 00. 08. 02. 17. 01 . 11. 08. 06. 00. 17 . 25. 39. 06. 39. 00 C. 53

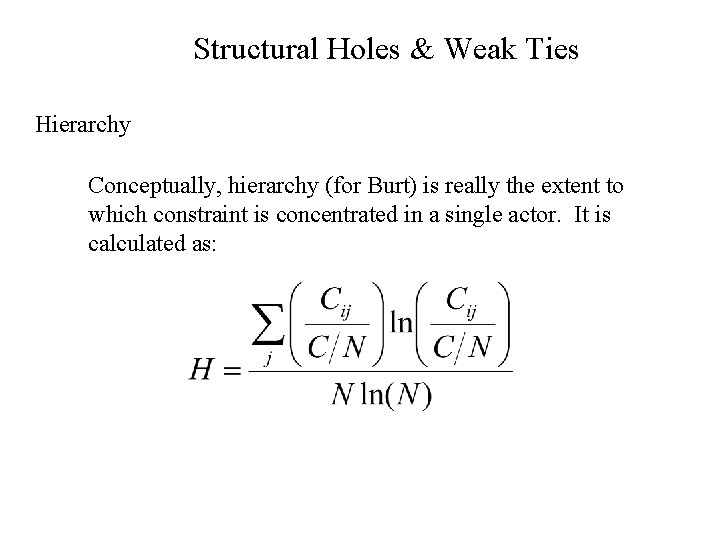
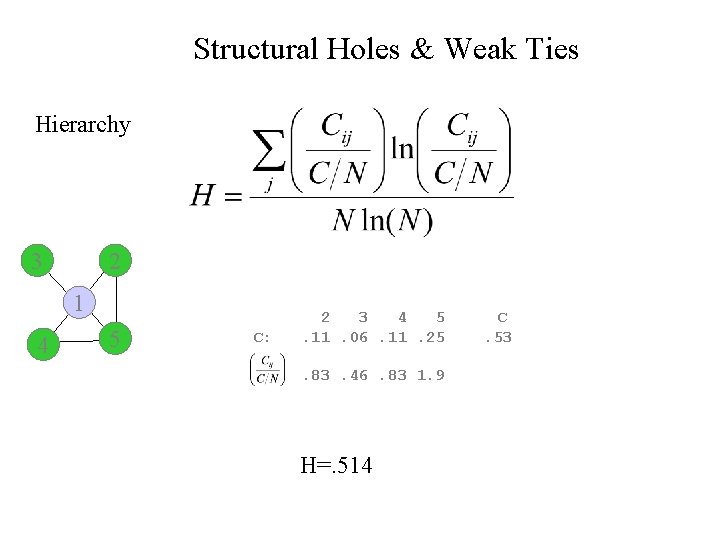
Structural Holes & Weak Ties Hierarchy Conceptually, hierarchy (for Burt) is really the extent to which constraint is concentrated in a single actor. It is calculated as:

Structural Holes & Weak Ties Hierarchy 3 2 1 4 5 C: 2 3 4 5. 11. 06. 11. 25. 83. 46. 83 1. 9 H=. 514 C. 53

Homework The solution program for assignment 1 can be found on the course data programs page, called ‘solutions 1. sas’ Look at this for the answers. http: //www. soc. sbs. ohio-state. edu/jwm/s 884/data. htm Common things people did: Typos in the original data matrix. Wrong data in, wrong answer out.

Homework Common things people did: Typos in the original data matrix. Wrong data in, wrong answer out. Adjacency lists should include a row for every node, even if they do not send any ties in the network What is the longest possible path in a network? How would you write a program to stop automatically? Many of you were able to identify the symmetric / asymmetric relations. But you left them as ‘ 2’ in the matrix. Usually you would add one more line (or use a slightly different syntax) to change them to ‘ 1’ as well.

Playing with data: Getting information from one program to another If our data are in one format (SAS, for example) how do we get it into a program like PAJEK or UCINET? 1) Type it in by hand. Too slow, error prone, impossible for very large networks 2) Write a program that moves data around for you automatically SPAN contains programs that write to: PAJEK UCINET NEGOPY STRUCTURE

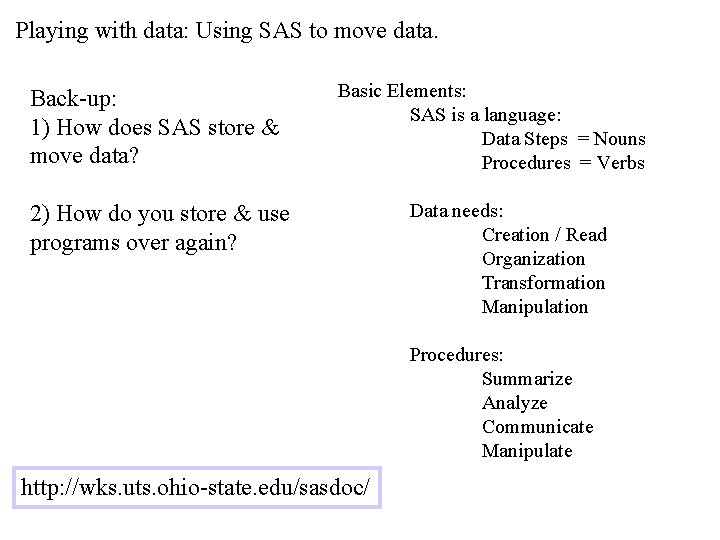
Playing with data: Using SAS to move data. Back-up: 1) How does SAS store & move data? Basic Elements: SAS is a language: Data Steps = Nouns Procedures = Verbs 2) How do you store & use programs over again? Data needs: Creation / Read Organization Transformation Manipulation Procedures: Summarize Analyze Communicate Manipulate http: //wks. uts. ohio-state. edu/sasdoc/

SAS The procedure we have been using is IML or the Interactive Matrix Language.

Data Libraries: Links to where data are stored Datasets: the actual data You refer to a data set by a two-level name: library. data
 Daning hu
Daning hu Granovetter strength of weak ties
Granovetter strength of weak ties Indirect ties vs direct ties
Indirect ties vs direct ties Mark s granovetter
Mark s granovetter Mark s. granovetter
Mark s. granovetter Weak acid and weak base reaction
Weak acid and weak base reaction Strong acods
Strong acods Weak acid strong base titration
Weak acid strong base titration You are strength when i am weak
You are strength when i am weak You are my strength when i am weak
You are my strength when i am weak Structural strength and stability
Structural strength and stability Difference between half strength and full strength darrow's
Difference between half strength and full strength darrow's Percentage strength w/w
Percentage strength w/w Tensile strength and yield strength
Tensile strength and yield strength How to calculate percentage strength w/v
How to calculate percentage strength w/v Forces and structures grade 5
Forces and structures grade 5 Family ties meaning
Family ties meaning The dangers of soul ties
The dangers of soul ties Intersegmental ties
Intersegmental ties Rigging an optimist
Rigging an optimist A new settlement that keeps close ties to its homeland
A new settlement that keeps close ties to its homeland What is aave
What is aave Mr tanen's tie trouble quiz
Mr tanen's tie trouble quiz Healthy peer relationships
Healthy peer relationships Ties column
Ties column Pediatric trach ties
Pediatric trach ties 7 ties to the oes obligation
7 ties to the oes obligation Islamic quotes on kinship
Islamic quotes on kinship Hjelp med airties
Hjelp med airties Ties behnke
Ties behnke Kodel saulei leidziantis ties horizontu ji matoma suplota
Kodel saulei leidziantis ties horizontu ji matoma suplota Where did stanley's great grandfather find refuge
Where did stanley's great grandfather find refuge