Stronger Password Authentication Using Browser Extensions Blake Ross

Stronger Password Authentication Using Browser Extensions Blake Ross, Collin Jackson, Nick Miyake, Dan Boneh, John Mitchell Stanford University http: //crypto. stanford. edu/Pwd. Hash
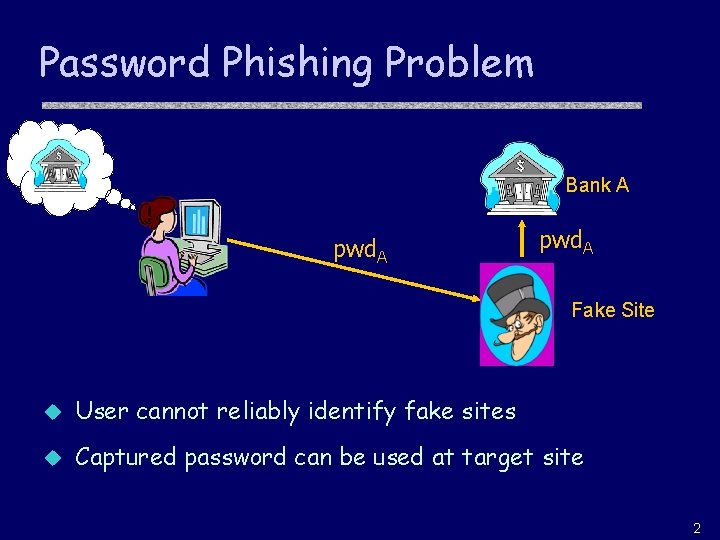
Password Phishing Problem Bank A pwd. A Fake Site u User cannot reliably identify fake sites u Captured password can be used at target site 2
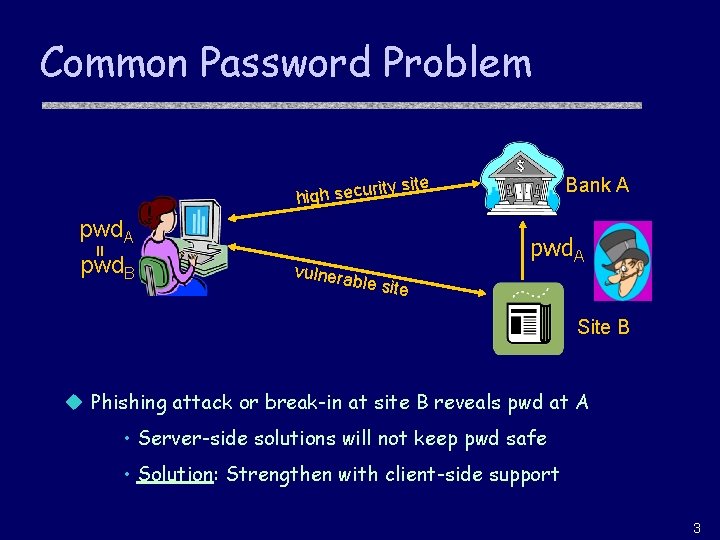
Common Password Problem rit high secu y site = pwd. A pwd. B vulnera ble site Bank A pwd. A Site B u Phishing attack or break-in at site B reveals pwd at A • Server-side solutions will not keep pwd safe • Solution: Strengthen with client-side support 3

Our Solution: Pwd. Hash u Lightweight browser extension u Impedes password theft u Invisible to server Pwd Hashing u Invisible to user Pwd Prefix 4
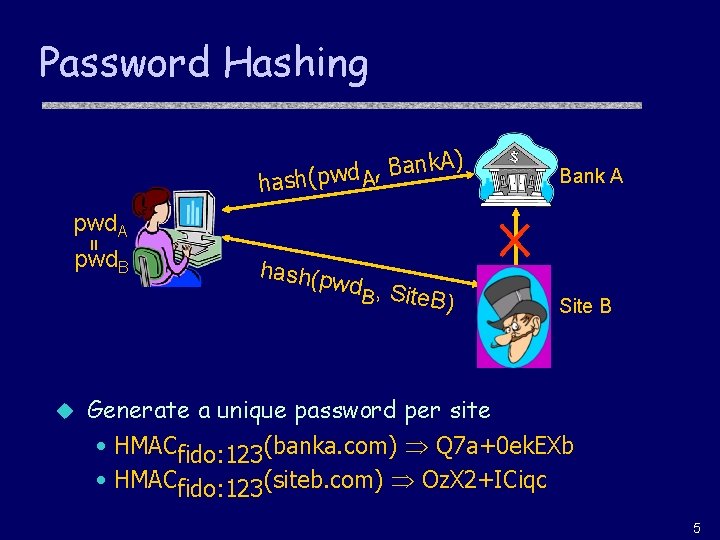
Password Hashing nk. A) a B , d w hash(p A Bank A = pwd. A pwd. B u hash(p wd , S B ite. B) Site B Generate a unique password per site • HMACfido: 123(banka. com) Q 7 a+0 ek. EXb • HMACfido: 123(siteb. com) Oz. X 2+ICiqc 5

Password Hashing: past attempts u Hash pwd with realm provided by remote site: • HTTP 1. 1 Digest Authentication • Kerberos 5 • Does not prevent phishing, common pwd u Hash pwd with network service name: • Abadi, Bharat, Marais [PTO ’ 97] Standalone. • Gabber, Gibbons, Mattias, Mayer [FC ’ 97]. Proxy. • Relies on intercepting traffic can’t handle https 6

Password Hashing: a popular idea u Recent password hashing projects: Password Composer Password Generator Extension Passwdlet Genpass Pwd. Hash Password Maker Site Password Magic Password Generator Similar hashing algorithms u Only Pwd. Hash defends against spoofing and is invisible to the user u 7
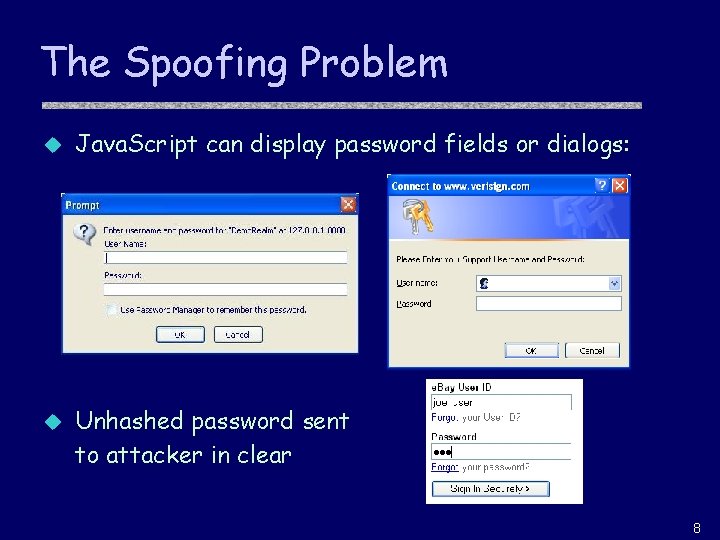
The Spoofing Problem u Java. Script can display password fields or dialogs: u Unhashed password sent to attacker in clear 8
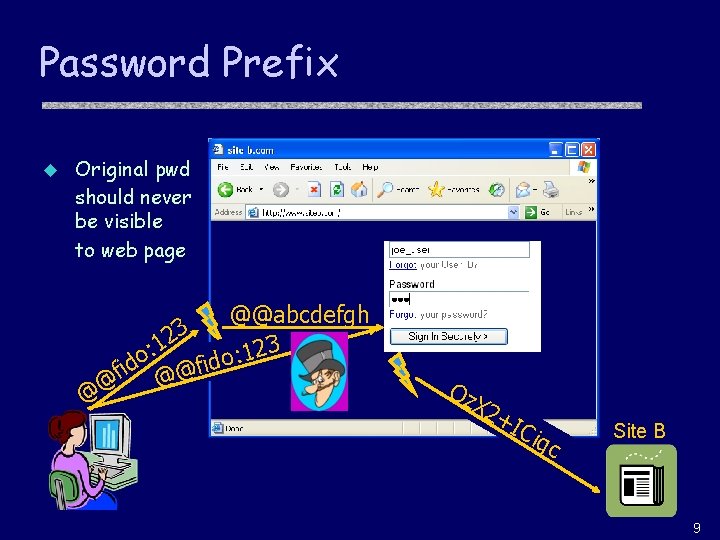
Password Prefix u Original pwd should never be visible to web page @ @ 3 2 : 1 o fid @@abcdefgh 3 o: 12 Oz X 2+ I Ciq c Site B 9
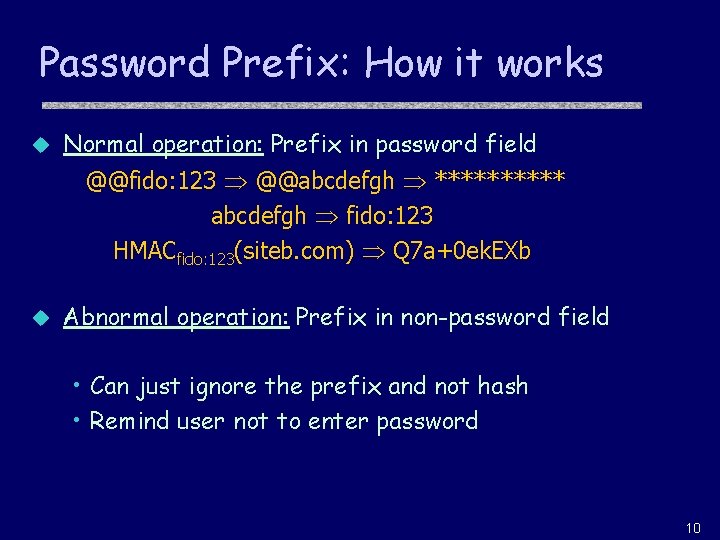
Password Prefix: How it works u Normal operation: Prefix in password field @@fido: 123 @@abcdefgh ***** abcdefgh fido: 123 HMACfido: 123(siteb. com) Q 7 a+0 ek. EXb u Abnormal operation: Prefix in non-password field • Can just ignore the prefix and not hash • Remind user not to enter password 10

Why use Password Prefix? u u u Protection mechanism “built in” to password Does not rely on user to make a decision Same prefix works for everyone Distinguishes secure passwords from • normal passwords • social security numbers • PINs Only use it when you want to 11
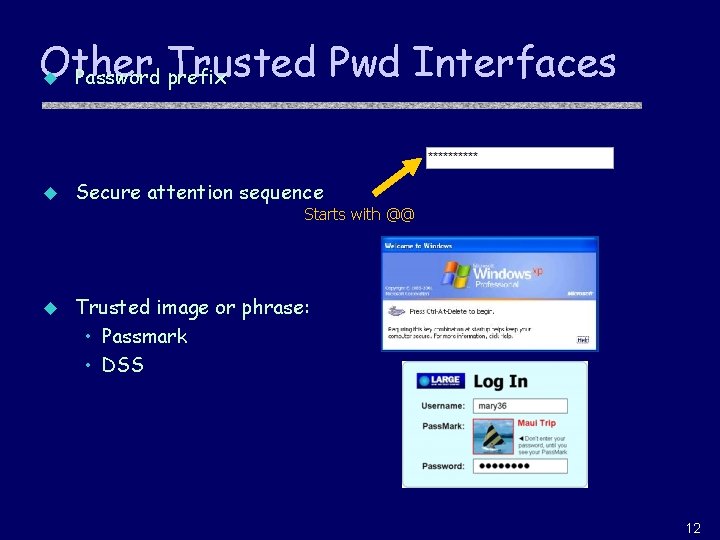
Other Pwd Interfaces u Password Trusted prefix u Secure attention sequence Starts with @@ u Trusted image or phrase: • Passmark • DSS 12

Other Challenges u Password Reset u Internet Cafes u Dictionary Attacks u Spyware, DNS poisoning (no protection) u Other issues (described in the paper) • Choosing salt for hash • Encoding hashed password • Additional attacks and defenses 13

Password Reset u u After install, Pwd. Hash can’t protect existing pwds • Only passwords starting with @@ are secure • User can choose where to use Pwd. Hash • User must enter old password unhashed into password reset page Pwd Prefix makes it easy • Old passwords won’t be accidentally hashed • New, secure passwords are Starts with @@ automatically hashed 14
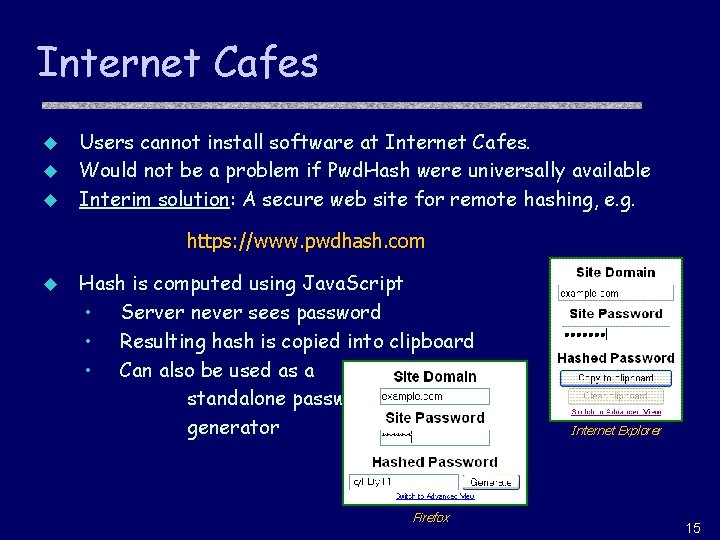
Internet Cafes Users cannot install software at Internet Cafes. u Would not be a problem if Pwd. Hash were universally available u Interim solution: A secure web site for remote hashing, e. g. u https: //www. pwdhash. com u Hash is computed using Java. Script • Server never sees password • Resulting hash is copied into clipboard • Can also be used as a standalone password generator Firefox Internet Explorer 15

Dictionary attacks u aardvark, abacus, abandon… After phishing attack or break-in to low security site, attacker can repeatedly guess password and check hash. • Succeeds on 15% of passwords (unlike 100% today) • Less effective on longer, stronger passwords u Solution: better authentication protocol (SPEKE, SRP, etc. ) • Requires server-side changes u Defense: user specifies a global pwd to strengthen all pwd hashes • Creates a new pwd management problem for shared machines u Defense: slow hash function (Halderman, Waters, Felten ‘ 05) • Increases time of dictionary attack 16

Pwd. Hash: Try it out u Prototype for Internet Explorer and Mozilla Firefox u Defends against spoofing u Invisible to user u Invisible to server u Complementary to other anti-phishing solutions u Only use it when you want to www. pwdhash. com 17
- Slides: 17