Strategy To Filter And Blocking Traffic Create By
Strategy To Filter And Blocking Traffic Create By Anti-Censorship Software In LAN by Kamal harmoni kamal Ariff kamal@kamalharmoni. com “Human Knowledge Belong To The World” 1

Outline Chapter 1. Introduction i. iii. iv. v. vi. Overview Problem Statement Research Question Research Objective Scope And Limitation Significant Of The Study Chapter 2. Literature Review i. Fundamental of anti-censorship software ii. Why Ultrasurf iii. About Ultrasurf iv. Why Ultrasurf difficult to detect ? v. Any firewall can block Ultrasurf? Chapter 3. Research Design i. Methodology ii. Form Hypothesis iii. Perform experiment and data collection iv. Analyze data v. Interpreter and draw Conclusion vi. Propose Strategy vii. Validate The Hypothesis

Outline Chapter 4. Experimental Result i. Form Hypothesis ii. Perform experiment and collect data iii. Analyze data iv. Interpreter and draw Conclusion v. Propose Strategy vi. Validate The Hypothesis Chapter 5. Conclusion and future work i. Recommendation and Possible Future Developments. References

Overview Chapter 1 • Computer technology change tremendously. • Internet access are commonly as an essential to everybody. • Internet policy become common to organization. • Prevent user from : • Accessing pornography web site • Conduct internet activities such as downloading movie, songs, etc • Network administrator need to • Filter traffic • Monitor trafic • Block trafic • War between users and network administrator never end. • Users will find away to bypass firewall
Problem Statement Chapter 1 By using Ultrasurf user able to bypass firewall. Ayacock (2008), Ultrasurf is extremely difficult to block. Xia (2004) Uses http and https from local computer to external proxies. Only commercial firewal with DPI able to block. Becchi & Crowley, (2007) They have a thousands of proxies and proxies IP always change. Cannot block by IP. Cannot block port 80 & 443 and firewall with DPI is expensive. SOLUTION: This project presents a better way for filtering and blocking Ultrasurf at affordable cost.

Research Question Chapter 1 • How to filter and block traffic that create by Ultrasurf ? • How Ultrasurf connected to internet? • How to filter traffic created by Ultrasurf? • How to block traffic created by Ultrasurf?

Research Objective Chapter 1 • The aim of this study is to filter and blocking traffic created by Ultrasurf from LAN to internet. In order to achieve the main objective, the specific objective has been planned as follows: • To identify how Ultrasurf connected to internet. • To produce at lease 1 strategy that are able to block Ultrasurf. • To evaluate the strategies that are able to block trafic from Ultrasurf without disturbing others trafic.
Scope and Limitation Chapter 1 • Scope • Focus only on Ultrasurf since Ultrasurf was the “possible as the best proxy server, 2008” Kaiser, (2008) and the most commontly use (GIFC, 2010) • These project used Linux Squid proxies to filter and block Ultrasurf. • Data Source (Wireshark captured data) • Tools ( Wireshark , Ultrasurf ) - Gerry (2009) and Vasil (2008), “ Wireshark is the best free tool for protocol analyzer ” • Limitation • Time (need to be complete within 2 month)
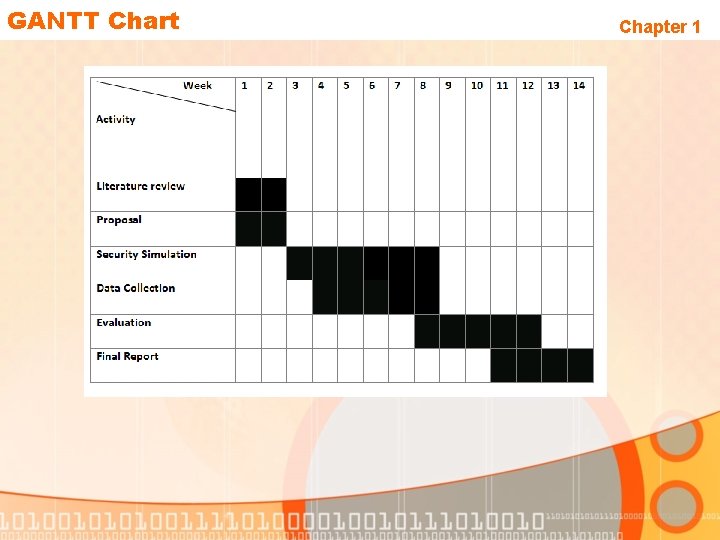
GANTT Chart Chapter 1

Significant of The Study Chapter 1 The purpose of this research are as stated below : • Allow network administrator to use an enhance propose technique and new strategies to filter and block traffic created by Ultrasurf. • Provide a worthy traffic for the benefit used in the organization. • Solution on overcome the weakness occurred in the firewall connection to access the restricted web sites.

Fundamental of anti-censorship Chapter 2 • In this studies it define as “Software that has been used to bypass firewall that provides censorship system”. • Capable to hide user information such as user’s IP address, transmitting or receiving content. • Example of anti-censorship software Ultrasurf, Freegate, Gpass, Garden, GTunnel, and Fire. Phoenix. • User used this anti-censorship software absolutely to bypass firewall, in order for them accessing the prohibited web sites.
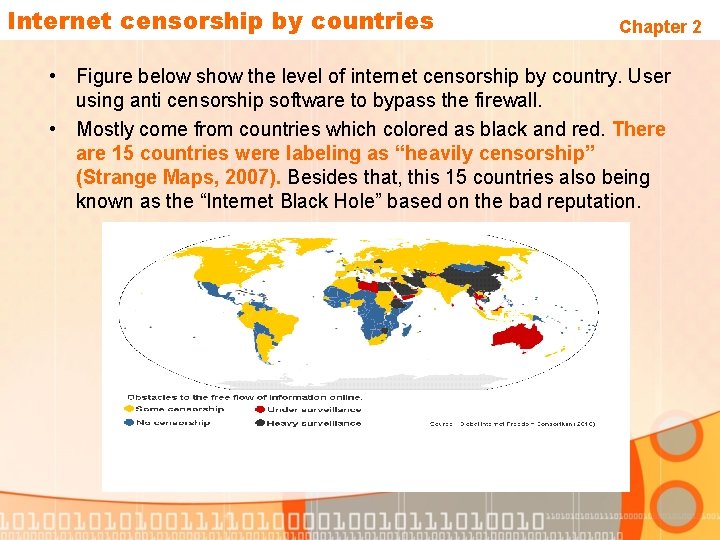
Internet censorship by countries Chapter 2 • Figure below show the level of internet censorship by country. User using anti censorship software to bypass the firewall. • Mostly come from countries which colored as black and red. There are 15 countries were labeling as “heavily censorship” (Strange Maps, 2007). Besides that, this 15 countries also being known as the “Internet Black Hole” based on the bad reputation.
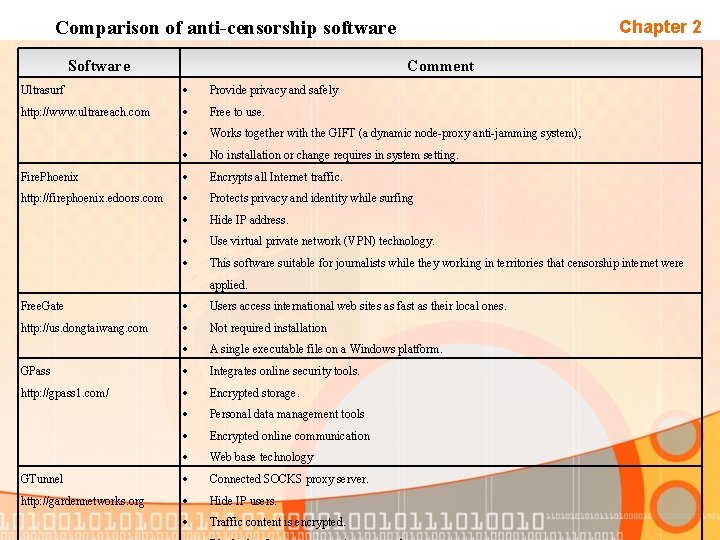
Comparison of anti-censorship software Software Chapter 2 Comment Ultrasurf Provide privacy and safely http: //www. ultrareach. com Free to use. Works together with the GIFT (a dynamic node-proxy anti-jamming system); No installation or change requires in system setting. Fire. Phoenix Encrypts all Internet traffic. http: //firephoenix. edoors. com Protects privacy and identity while surfing Hide IP address. Use virtual private network (VPN) technology. This software suitable for journalists while they working in territories that censorship internet were applied. Free. Gate Users access international web sites as fast as their local ones. http: //us. dongtaiwang. com Not required installation A single executable file on a Windows platform. GPass Integrates online security tools. http: //gpass 1. com/ Encrypted storage. Personal data management tools Encrypted online communication Web base technology GTunnel Connected SOCKS proxy server. http: //gardennetworks. org Hide IP users. Traffic content is encrypted.

Why Ultrasurf ? • “Ultrasurf are the most commonly used”(GIFC, 2010) • “Possible as The Best Proxy Server, 2008”. Kaiser (2008), Chapter 2

About Ultrasurf Chapter 2 The overview and the idea on Ultrasurf being implemented • Pioneer of Ultrasurf was Ultrareach, who one of a member of Global Internet Freedom Consortium. • Being developed originally to gain the privacy, security and freedom in surfing the internet. • Strongly against the internet censorship in China as on that moment, goverment imposed strictly controlled on web content and accessing. • According to Tan, Mueller & Foster in 1997, “In February 1996, all internet users are required to register with ministry of Public Security and their activities may be monitored by police”. Under China golden shield project and as reported by Reuters (2007).

Why Ultrasurf difficult to detect ? Chapter 2 • According to Xia (2004), “Ultrasurf is extremely difficult to block”. • Ultrasurf is using port 9666 to communicate from web browser to the Ultrasurf services, but communication using this port only at local computer that can’t be block. • Ultrasurf also use a secure socket layer (SSL) to communicate from local computer to their proxies. • Due to thousand of proxies and the IP address that increasing from time to time, the blocking of IP address is not practical at this circumstances. • Ultrasurf also use Port 80 and 443 to communicate with external proxies and should not block by firewall.

Any firewall can block Ultrasurf ? Chapter 2 • “Filteration can be done by using SSL interceptor and perform DPI (deep packet inspection)”. Kumar, Turner, & Williams (2006) and Piyachon & Luo (2006), • Firewalls that have DPI capabilities are able to filter traffic that come from anti-censorship software. • Sonic Wall and Symantec firewall are example of firewall that capable to prevent anti-censorship but the price is extremely expensive for small organization to buy.

Research Design Chapter 3 • This methodology is adapted from (Peisert & Bishop, 2007). This methodology has been used for “How To Design Computer Security Experiment ”. • The original methodology only has five phases which are : Ø Ø Ø Form hypothesis Perform experiment and collecting data Analyse the data Interpret data and draw the conclusion Depend on conclusion, return to #1 • The two phases “ Propose Strategy ” and “ Validate hypothesis” being added to meet this project requirement.
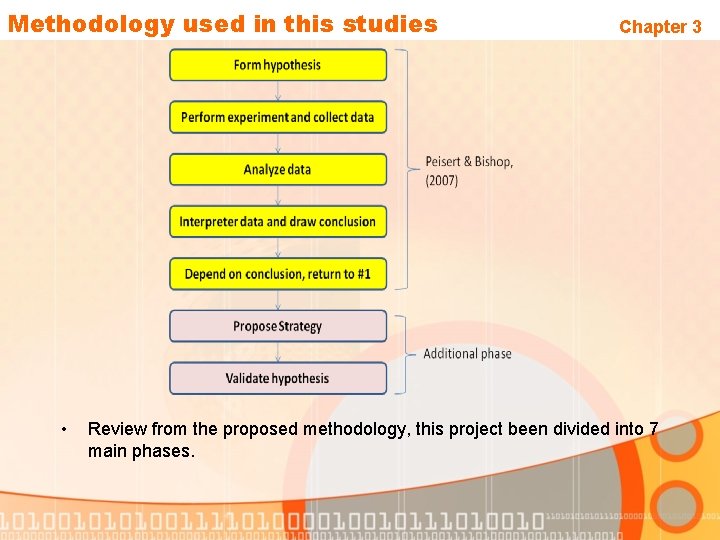
Methodology used in this studies • Chapter 3 Review from the proposed methodology, this project been divided into 7 main phases.
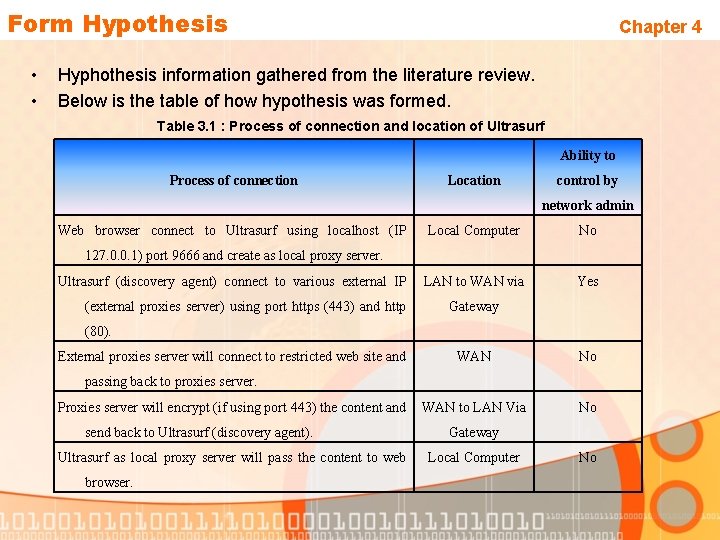
Form Hypothesis • • Chapter 4 Hyphothesis information gathered from the literature review. Below is the table of how hypothesis was formed. Table 3. 1 : Process of connection and location of Ultrasurf Ability to Process of connection Location control by network admin Web browser connect to Ultrasurf using localhost (IP Local Computer No LAN to WAN via Yes 127. 0. 0. 1) port 9666 and create as local proxy server. Ultrasurf (discovery agent) connect to various external IP (external proxies server) using port https (443) and http Gateway (80). External proxies server will connect to restricted web site and WAN No WAN to LAN Via No passing back to proxies server. Proxies server will encrypt (if using port 443) the content and send back to Ultrasurf (discovery agent). Ultrasurf as local proxy server will pass the content to web browser. Gateway Local Computer No
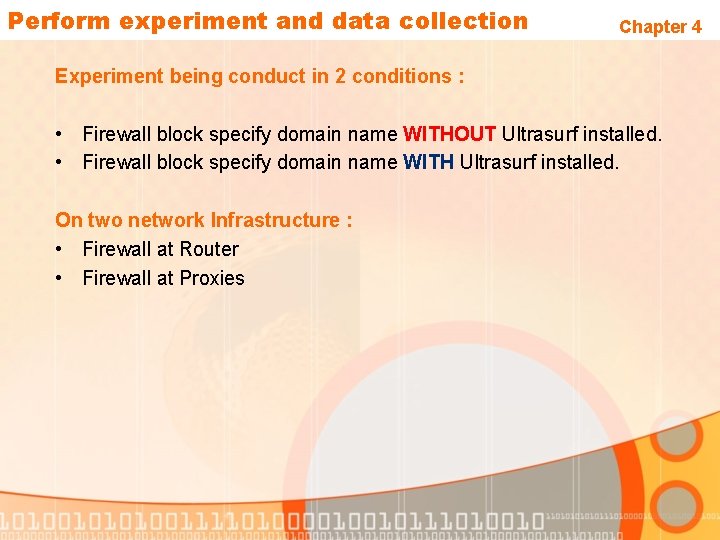
Perform experiment and data collection Chapter 4 Experiment being conduct in 2 conditions : • Firewall block specify domain name WITHOUT Ultrasurf installed. • Firewall block specify domain name WITH Ultrasurf installed. On two network Infrastructure : • Firewall at Router • Firewall at Proxies
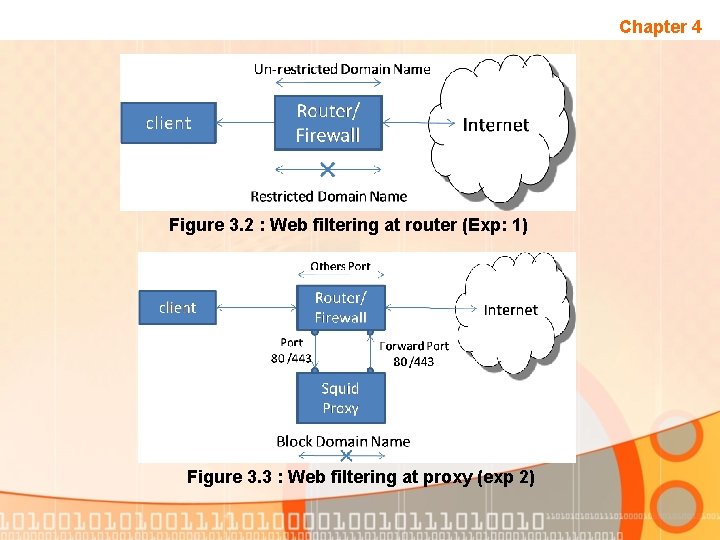
Chapter 4 Figure 3. 2 : Web filtering at router (Exp: 1) Figure 3. 3 : Web filtering at proxy (exp 2)
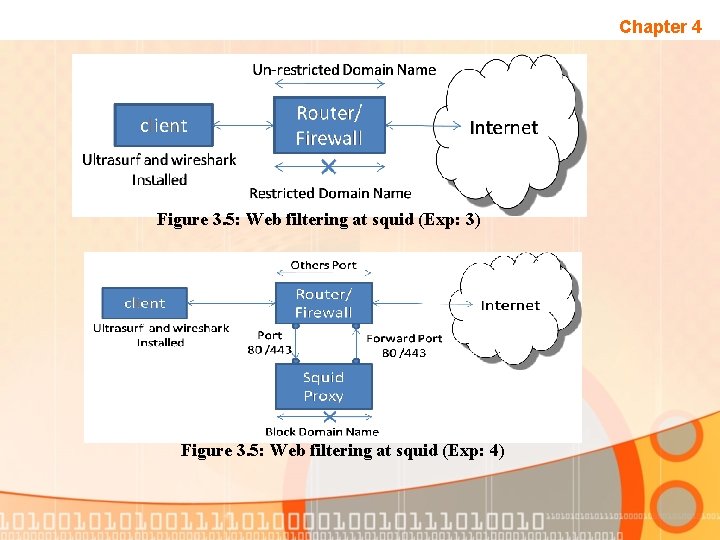
Chapter 4 Figure 3. 5: Web filtering at squid (Exp: 3) Figure 3. 5: Web filtering at squid (Exp: 4)
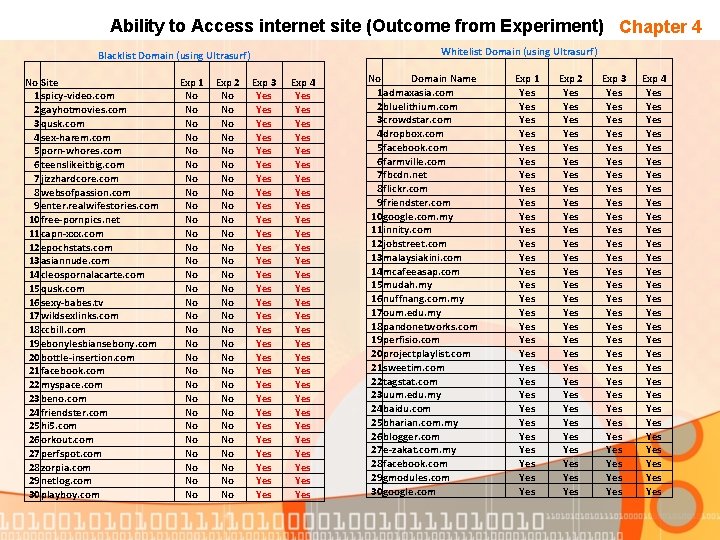
Ability to Access internet site (Outcome from Experiment) Chapter 4 Whitelist Domain (using Ultrasurf) Blacklist Domain (using Ultrasurf) No Site 1 spicy-video. com 2 gayhotmovies. com 3 qusk. com 4 sex-harem. com 5 porn-whores. com 6 teenslikeitbig. com 7 jizzhardcore. com 8 websofpassion. com 9 enter. realwifestories. com 10 free-pornpics. net 11 capn-xxx. com 12 epochstats. com 13 asiannude. com 14 cleospornalacarte. com 15 qusk. com 16 sexy-babes. tv 17 wildsexlinks. com 18 ccbill. com 19 ebonylesbiansebony. com 20 bottle-insertion. com 21 facebook. com 22 myspace. com 23 beno. com 24 friendster. com 25 hi 5. com 26 orkout. com 27 perfspot. com 28 zorpia. com 29 netlog. com 30 playboy. com Exp 1 No No No No No No No No Exp 2 No No No No No No No No Exp 3 Yes Yes Yes Yes Yes Yes Yes Yes Exp 4 Yes Yes Yes Yes Yes Yes Yes Yes No Domain Name 1 admaxasia. com 2 bluelithium. com 3 crowdstar. com 4 dropbox. com 5 facebook. com 6 farmville. com 7 fbcdn. net 8 flickr. com 9 friendster. com 10 google. com. my 11 innity. com 12 jobstreet. com 13 malaysiakini. com 14 mcafeeasap. com 15 mudah. my 16 nuffnang. com. my 17 oum. edu. my 18 pandonetworks. com 19 perfisio. com 20 projectplaylist. com 21 sweetim. com 22 tagstat. com 23 uum. edu. my 24 baidu. com 25 bharian. com. my 26 blogger. com 27 e-zakat. com. my 28 facebook. com 29 gmodules. com 30 google. com Exp 1 Yes Yes Yes Yes Yes Yes Yes Yes Exp 2 Yes Yes Yes Yes Yes Yes Yes Yes Exp 3 Yes Yes Yes Yes Yes Yes Yes Yes Exp 4 Yes Yes Yes Yes Yes Yes Yes Yes
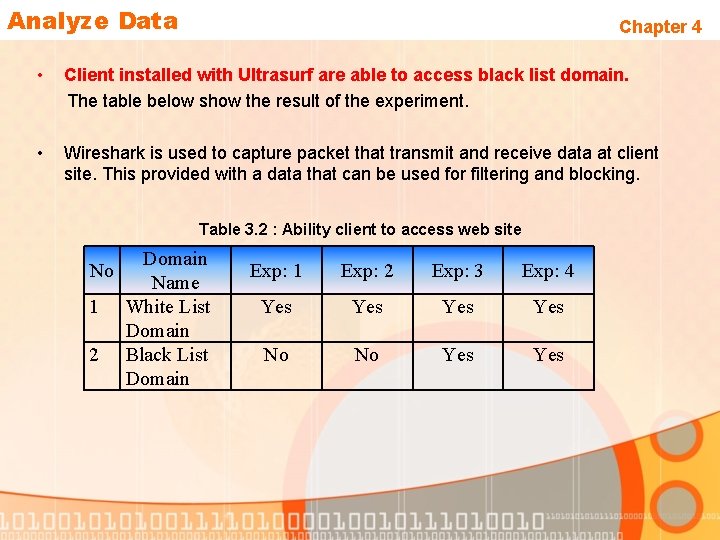
Analyze Data Chapter 4 • Client installed with Ultrasurf are able to access black list domain. The table below show the result of the experiment. • Wireshark is used to capture packet that transmit and receive data at client site. This provided with a data that can be used for filtering and blocking. Table 3. 2 : Ability client to access web site No 1 2 Domain Name White List Domain Black List Domain Exp: 1 Exp: 2 Exp: 3 Exp: 4 Yes Yes No No Yes
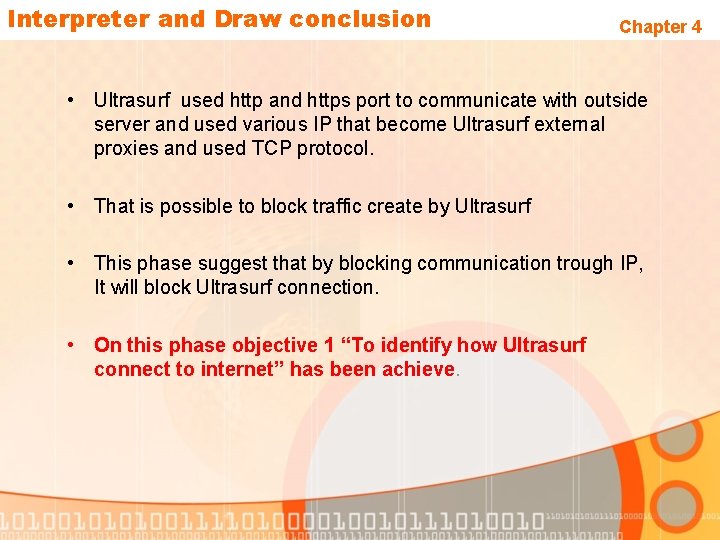
Interpreter and Draw conclusion Chapter 4 • Ultrasurf used http and https port to communicate with outside server and used various IP that become Ultrasurf external proxies and used TCP protocol. • That is possible to block traffic create by Ultrasurf • This phase suggest that by blocking communication trough IP, It will block Ultrasurf connection. • On this phase objective 1 “To identify how Ultrasurf connect to internet” has been achieve.
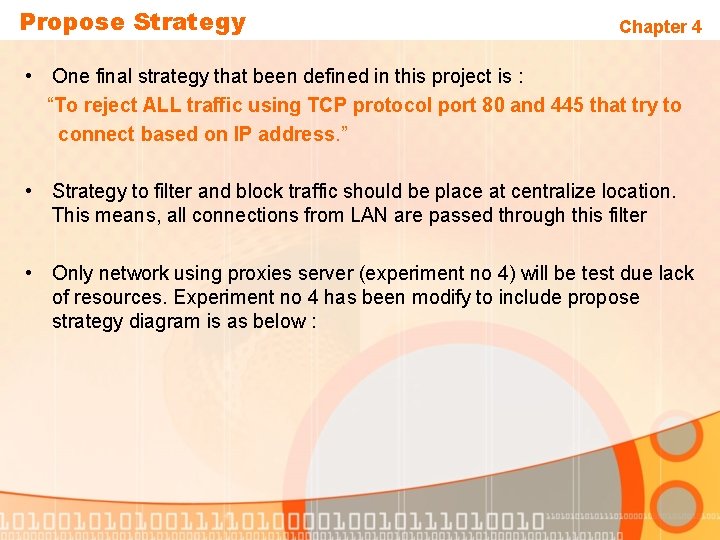
Propose Strategy Chapter 4 • One final strategy that been defined in this project is : “To reject ALL traffic using TCP protocol port 80 and 445 that try to connect based on IP address. ” • Strategy to filter and block traffic should be place at centralize location. This means, all connections from LAN are passed through this filter • Only network using proxies server (experiment no 4) will be test due lack of resources. Experiment no 4 has been modify to include propose strategy diagram is as below :
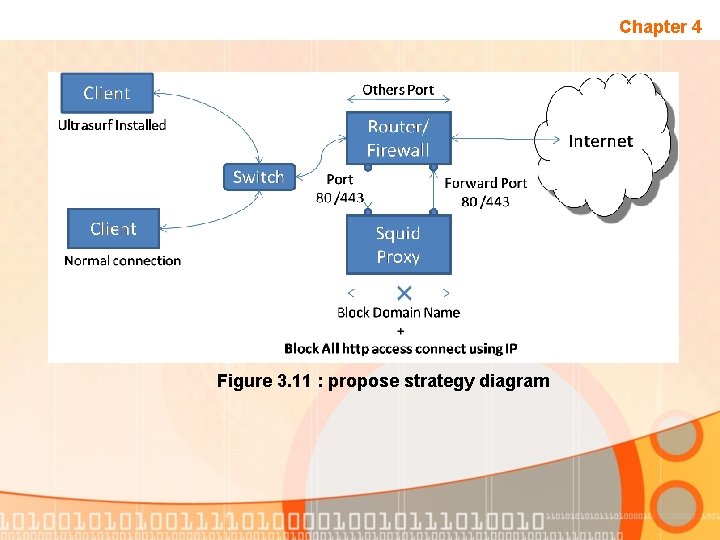
Chapter 4 Figure 3. 11 : propose strategy diagram
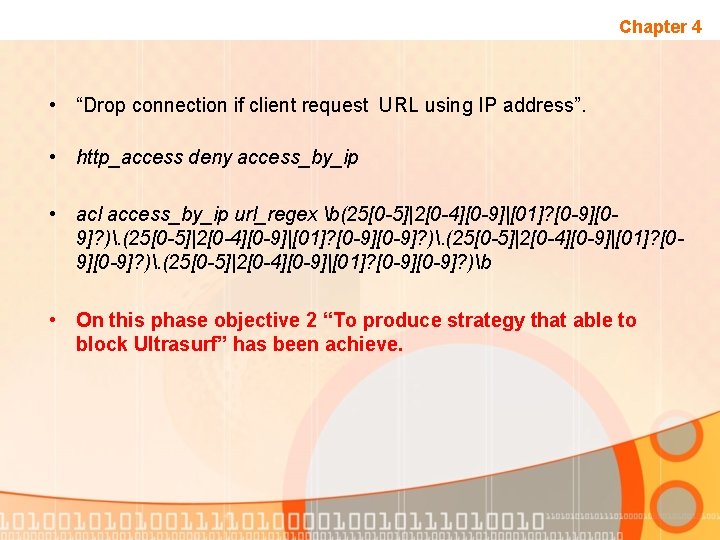
Chapter 4 • “Drop connection if client request URL using IP address”. • http_access deny access_by_ip • acl access_by_ip url_regex b(25[0 -5]|2[0 -4][0 -9]|[01]? [0 -9][09]? ). (25[0 -5]|2[0 -4][0 -9]|[01]? [0 -9]? ). (25[0 -5]|2[0 -4][0 -9]|[01]? [09][0 -9]? ). (25[0 -5]|2[0 -4][0 -9]|[01]? [0 -9]? )b • On this phase objective 2 “To produce strategy that able to block Ultrasurf” has been achieve.

Chapter 4 squid. conf acl blacklist_domain_contain url_regex -i "/etc/squid/blacklist_domains_contain. acl" acl blacklist_domain dstdomain "/etc/squid/blacklist_domain. acl" acl access_by_ip url_regex b(25[0 -5]|2[0 -4][0 -9]|[01]? [0 -9][0 -9]? ). (25[0 -5]|2[0 -4][0 -9]|[01]? [0 -9]? ). (25[05]|2[0 -4][0 -9]|[01]? [0 -9]? )b http_access deny access_by_ip http_access deny blacklist_domain_contain http_access allow all
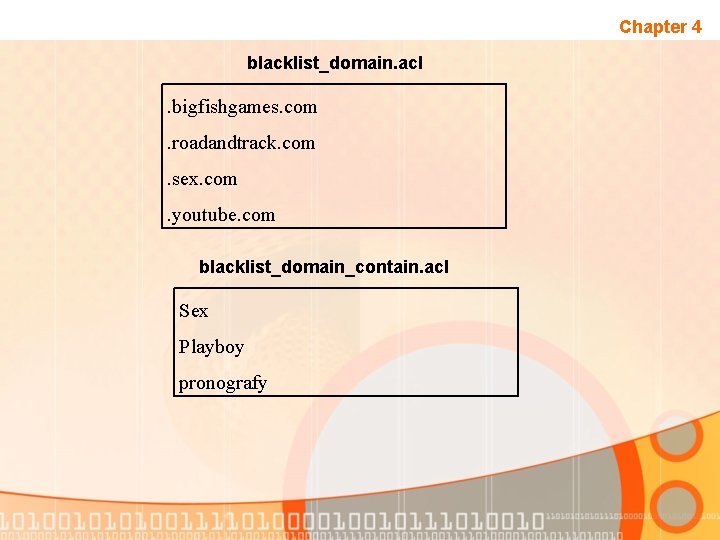
Chapter 4 blacklist_domain. acl . bigfishgames. com. roadandtrack. com. sex. com. youtube. com blacklist_domain_contain. acl Sex Playboy pronografy

Validate the hypothesis • • • Chapter 4 This phase of the project is to show either the Ultrasurf blocking method that being used is working or not. Based on the proposed strategy that been used, Experiment 4 (Web filtering at squid with Ultrasurf Installed) has been conducted again to validate the requirement needed. It show that “it is possible to block Ultrasurf traffic” by using propose strategy derive from hypothesis Below is figure of Ultrasurf 9. 4 Vs Proposed strategy. On this phase objective 3 “To evaluate the strategy” has been achieve
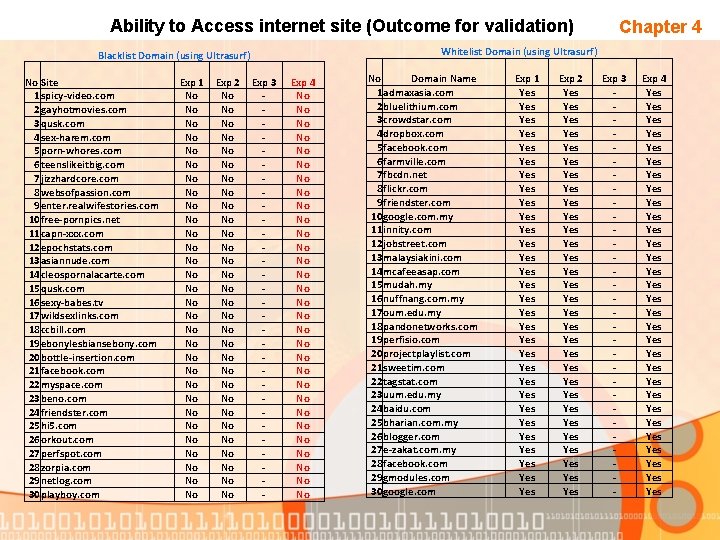
Ability to Access internet site (Outcome for validation) Whitelist Domain (using Ultrasurf) Blacklist Domain (using Ultrasurf) No Site 1 spicy-video. com 2 gayhotmovies. com 3 qusk. com 4 sex-harem. com 5 porn-whores. com 6 teenslikeitbig. com 7 jizzhardcore. com 8 websofpassion. com 9 enter. realwifestories. com 10 free-pornpics. net 11 capn-xxx. com 12 epochstats. com 13 asiannude. com 14 cleospornalacarte. com 15 qusk. com 16 sexy-babes. tv 17 wildsexlinks. com 18 ccbill. com 19 ebonylesbiansebony. com 20 bottle-insertion. com 21 facebook. com 22 myspace. com 23 beno. com 24 friendster. com 25 hi 5. com 26 orkout. com 27 perfspot. com 28 zorpia. com 29 netlog. com 30 playboy. com Exp 1 No No No No No No No No Exp 2 No No No No No No No No Chapter 4 Exp 3 - Exp 4 No No No No No No No No Domain Name 1 admaxasia. com 2 bluelithium. com 3 crowdstar. com 4 dropbox. com 5 facebook. com 6 farmville. com 7 fbcdn. net 8 flickr. com 9 friendster. com 10 google. com. my 11 innity. com 12 jobstreet. com 13 malaysiakini. com 14 mcafeeasap. com 15 mudah. my 16 nuffnang. com. my 17 oum. edu. my 18 pandonetworks. com 19 perfisio. com 20 projectplaylist. com 21 sweetim. com 22 tagstat. com 23 uum. edu. my 24 baidu. com 25 bharian. com. my 26 blogger. com 27 e-zakat. com. my 28 facebook. com 29 gmodules. com 30 google. com Exp 1 Yes Yes Yes Yes Yes Yes Yes Yes Exp 2 Yes Yes Yes Yes Yes Yes Yes Yes Exp 3 - Exp 4 Yes Yes Yes Yes Yes Yes Yes Yes
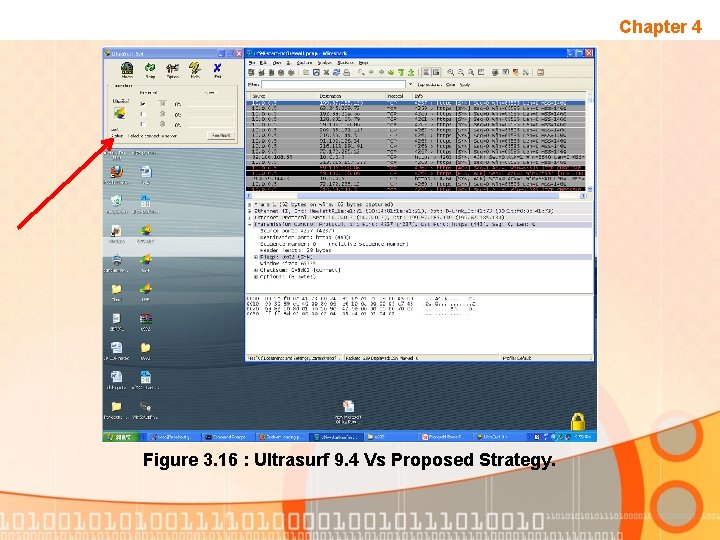
Chapter 4 Figure 3. 16 : Ultrasurf 9. 4 Vs Proposed Strategy.
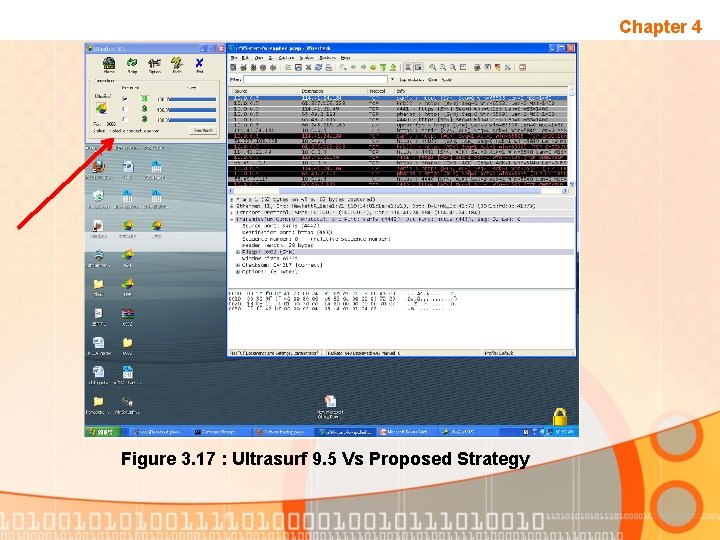
Chapter 4 Figure 3. 17 : Ultrasurf 9. 5 Vs Proposed Strategy
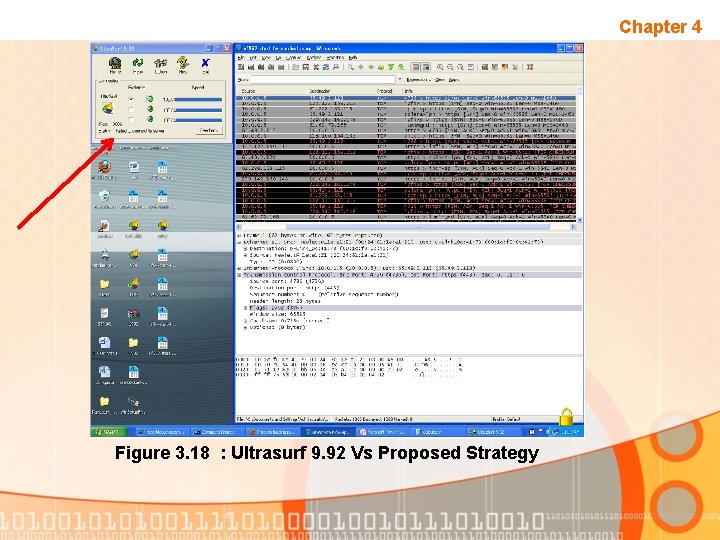
Chapter 4 Figure 3. 18 : Ultrasurf 9. 92 Vs Proposed Strategy
Chapter 4 Ultrasurf 95 Connect To Internet With Propose Strategy Applied No. Time Source Destination Proto col Info 114. 41. 24. 184 TCP saris > https [SYN] Seq=0 Win=65535 Len=0 MSS=1460 1 0 10. 0. 0. 5 2 0. 000017 10. 0. 0. 5 61. 227. 103. 228 TCP krb 524 > https [SYN] Seq=0 Win=65535 Len=0 MSS=1460 3 0. 000022 10. 0. 0. 5 114. 41. 21. 49 TCP 4441 > https [SYN] Seq=0 Win=65535 Len=0 MSS=1460 4 0. 000022 10. 0. 0. 5 65. 49. 2. 123 TCP pharos > https [SYN] Seq=0 Win=65535 Len=0 MSS=1460 5 0. 000082 10. 0. 0. 5 65. 49. 2. 115 TCP 4440 > https [SYN] Seq=0 Win=65535 Len=0 MSS=1460 6 0. 000137 10. 0. 0. 5 66. 245. 218. 168 TCP upnotifyp > https [SYN] Seq=0 Win=65535 Len=0 MSS=1460 7 0. 000431 114. 41. 24. 184 10. 0. 0. 5 TCP https > saris [SYN, ACK] Seq=0 Ack=1 Win=5840 Len=0 MSS=1460 8 0. 000449 10. 0. 0. 5 114. 41. 24. 184 TCP saris > https [ACK] Seq=1 Ack=1 Win=65535 Len=0 9 0. 000455 61. 227. 103. 228 10. 0. 0. 5 TCP https > krb 524 [SYN, ACK] Seq=0 Ack=1 Win=5840 Len=0 MSS=1460 10 0. 000465 10. 0. 0. 5 61. 227. 103. 228 TCP krb 524 > https [ACK] Seq=1 Ack=1 Win=65535 Len=0 11 0. 000468 114. 41. 21. 49 10. 0. 0. 5 TCP https > 4441 [SYN, ACK] Seq=0 Ack=1 Win=5840 Len=0 MSS=1460 12 0. 000476 10. 0. 0. 5 114. 41. 21. 49 TCP 4441 > https [ACK] Seq=1 Ack=1 Win=65535 Len=0 13 0. 000479 65. 49. 2. 123 10. 0. 0. 5 TCP https > pharos [SYN, ACK] Seq=0 Ack=1 Win=5840 Len=0 MSS=1460 14 0. 000486 10. 0. 0. 5 114. 41. 24. 184 TCP saris > https [FIN, ACK] Seq=1 Ack=1 Win=65535 Len=0 15 0. 000493 10. 0. 0. 5 65. 49. 2. 123 TCP pharos > https [ACK] Seq=1 Ack=1 Win=65535 Len=0 16 0. 000498 65. 49. 2. 115 10. 0. 0. 5 TCP https > 4440 [SYN, ACK] Seq=0 Ack=1 Win=5840 Len=0 MSS=1460
Conclusion Chapter 5 • This project has introduced a strategy to block user from accessing prohibited website via Ultrasurf. • Squid proxy server has ability to provide a blocking IP address based on http and https connection. • Below are the two strategies that being implemented in this project to block Ultrasurf :
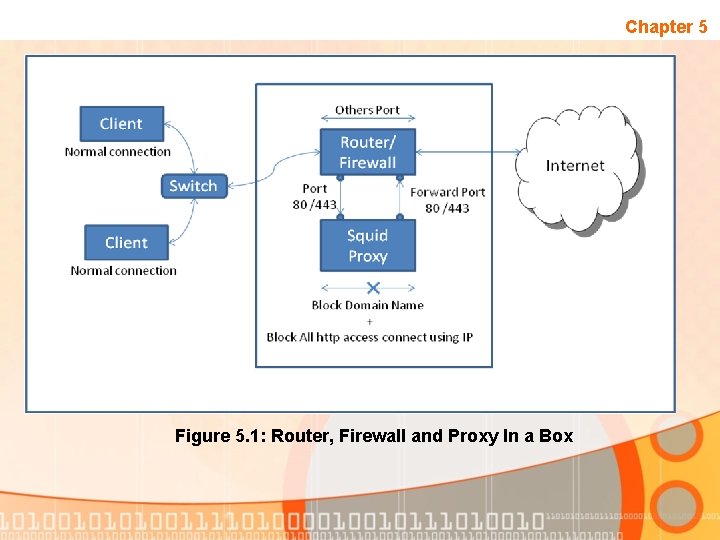
Chapter 5 Figure 5. 1: Router, Firewall and Proxy In a Box
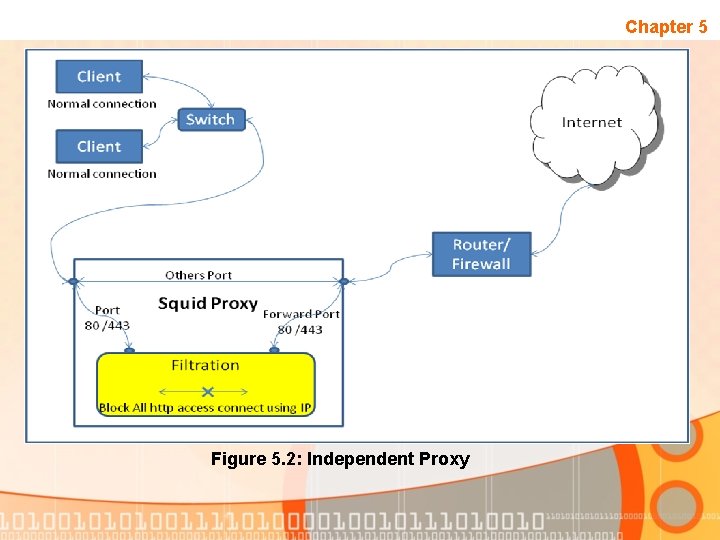
Chapter 5 Figure 5. 2: Independent Proxy

Future work Chapter 5 • This project will be a good resource and as a guide for the never ending enchantment in this method to block Ultrasurf. • The following pit points maybe useful for this project regarding the developing and finding the new approach in the future. Ø Performance. Ø What happen if 1000 user request at same time ? Ø Squid new technology. Ø working perfectly in all version of squid ? Ø Network model. Ø Can this applied at IPTables ? Ø Integrate into current firewall technology Ø incorporate this strategy into low end firewall ? Ø Others type of anti-censorship software Ø May the same strategy work on others anti-censorship software ?

References. Aycock, J. , & Maurushat, A. (2008, March ). "Good" worms and human rights. SIGCAS Computers and Society, Volume 38 Issue 1. Becchi, M. , & Crowley, P. (December 2007). A hybrid finite automaton for practical deep packet inspection. Co. NEXT '07: Proceedings of the 2007 ACM Co. NEXT conference. ACM. GIFC. (2010). Retrieved 01 05, 2010, from About Global Internet Freedom Consortium: http: //www. internetfreedom. org/ Hunter, C. D. (April 2000). Internet filter effectiveness (student paper panel): testing over and underinclusive blocking decisions of four popular filters. CFP '00: Proceedings of the tenth conference on Computers, freedom and privacy: challenging the assumptions. ACM. Kaiser, A. (2008, Aug 12). technopedia. Retrieved 01 05, 2010, from Ultra. Surf : Probably The Best Proxy Server Ever!!!: http: //technopedia. info/tech/2008/08/12/ultrasurf-probably-the-best-proxy-server. html Kumar, S. , Turner, J. , & Williams, J. (December 2006). Advanced algorithms for fast and scalable deep packet inspection. ANCS '06: Proceedings of the 2006 ACM/IEEE symposium on Architecture for networking and communications systems. ACM. Peisert, S. , & Bishop, M. (2007). how to Design Computer Security Experiments. Springer Boston. Volume 237/2007, pp. 141 -148. Springer Boston. Piyachon, P. , & Luo, Y. (December 2006 ). Efficient memory utilization on network processors for deep packet inspection. ANCS '06: Proceedings of the 2006 ACM/IEEE symposium on Architecture for networking and communications systems. ACM. Regular Expressions. info. (2010). Retrieved 4 20, 2010, from Sample Regular Expressions: http: //www. regular-expressions. info/examples. html Reuters. (2007, July 18). Retrieved 01 05, 2010, from Chinese Internet censors blamed for email chaos: http: //www. reuters. com/article/id. USPEK 9185520070718 Strange Maps. (2007, 8 3). Retrieved 3 20, 2010, from A Map of the Internet ’s Black Holes: http: //strangemaps. wordpress. com/2007/08/31/170 -a-map-of-the-internets-blackholes/ Tan, Z. A. , Mueller, M. , & Foster, W. (1997). China's new Internet regulations: two steps forward, one step back. Communications of the ACM archive , 11 - 16. Whitten, J. L. , Bentley, L. D. , & Dittman, K. (2004). System Analysis and Design Method. 6 th ed. Boston: Mc-Graw-Hill Education. Wikipedia. (2010). Retrieved 01 05, 2010, from Internet censorship: http: //en. wikipedia. org/wiki/Internet_censorship Wikipedia. (2010). Retrieved 4 20, 2010, from Regular_expression: http: //en. wikipedia. org/wiki/Regular_expression Xia, B. (2004). The Coming Crash Of The Matrix. China Right Forum , pp. 42 -44.

Thank You Q&A “Human Knowledge Belong To The World” 43
- Slides: 43