Strategic Information System Outline Systems Thinking System development
























































- Slides: 83

Strategic Information System

Outline • Systems Thinking • System development lifecycle -Problem Definition - Feasibility study - System Analysis - System design - System development and implementation • Major issues in implementation

Introduction • Systems whose importance to organizations extends beyond merely assisting to perform its existing functions efficiently. • Contribute significantly to the achievement of competitive and other strategic objectives.

What is Systems Thinking? • Seeing interrelationships among systems rather than linear cause-and-effect chains whenever events occur. • Seeing processes of change among systems rather than discrete snapshots of change, whenever changes occur

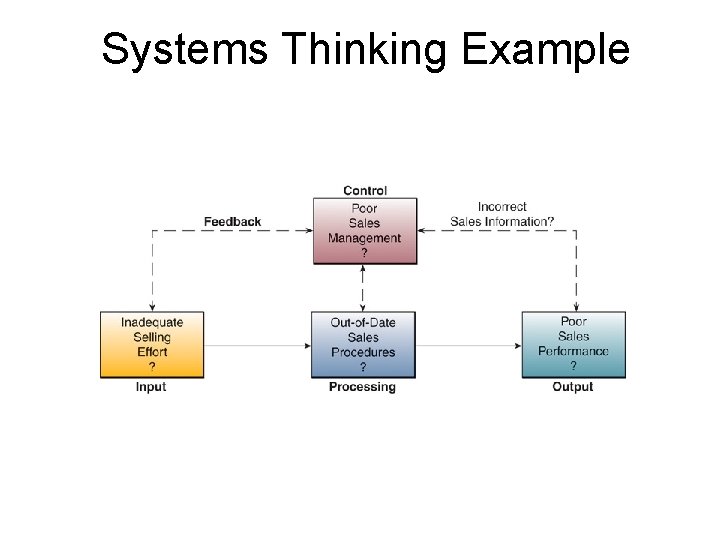
Systems Thinking Example

Systems Development Lifecycle (SDLC) 1. Problem Definition • Defining the problems in detail • Define user requirements and what they expect from the system. • Success of the system relies on how accurately the problem is defined. • Available resources, and constraints identified. • Approval of the project proposal.

Systems Development Lifecycle (SDLC) 2. Feasibility Study • Whether the system is practically feasible? • testing new system’s workability, fund requirements, technological know how, ability to meet user’s needs, impact on organization. • Problem is in-depth studied and all aspects analysed.

Systems Development Lifecycle (SDLC) 2. • • • Feasibility Study Costs compared with anticipated benefits. Written proposal prepared. Detailed specification of problem, major findings and suggestions, cost/benefit analysis etc.

Types of Feasibility Study Technical Feasibility • Proposed system evaluated from technical viewpoint. • Involves whether the problem can be solved with the help of computers and to what extent. • Volume of data need to be studied; computerized function satisfies user objectives or not.

Types of Feasibility Study Economical Feasibility • Deals with cost and expenses of proposed system. • Proposed system to justify cost and benefit criteria. • Involves cost of operations of existing and proposed systems, cost of development of the proposed system; value benefits of proposed system.

Types of Feasibility Study Operational Feasibility • Cost of educating, training, salary changes, job improvements, hidden costs. • Resistance to change and computerization requires retraining, change in job status and profiles.

Systems Development Lifecycle (SDLC) 3. System Analysis • Detailed appraisal of existing system; how the system works and what it does? Two steps: • Analyzing the existing system - determining the activities that are currently performed and which should be continued in the new system. – Documenting the current system – Current hardware needs examined.

Systems Development Lifecycle (SDLC) 3. System Analysis • Determining the needs of new system – Interviewing the users, observations, questionnaire etc. • • Results of analysis of existing system are merged with the needs of new system. Also defines the boundaries and scope of system.

Systems Development Lifecycle (SDLC) 4. System Design • Converts general requirements defined in analysis phase into detailed specifications for the new system. • Detailed specification include H/W needs, data descriptions, S/W needs etc. • Development of programs and their testing. • Sample input is tested for the output.

Systems Development Lifecycle (SDLC) 4. System Design- Two steps: • Conceptual Design - conceptual solutions proposed in feasibility study are looked in detail - new functions may be proposed and change the existing functions. - may need to take decisions on size of computer and software needed; which software to purchase and which new programs need to be developed.

Systems Development Lifecycle (SDLC) 4. System Design- Two steps: • Detailed Design - database and program modules are designed. - input design, output design, database design and processing designs are documented. - objectives, cost and benefits along with documented designs presented to the management.

Systems Development Lifecycle (SDLC) 4. System Development and Implementation • Computer based system developed from specifications prepared in design phase. • Hardware is acquired and installed • All necessary procedures, software specifications and other documentations are completed.

Major Issues in Implementation • Conversion –- put the tested system into operation. –Involves training the operating staff and installing the system. –Implementation results are documented

Major Issues in Implementation • User Training –- user capabilities and nature of system installed analyzed. – user informed how the whole system works, objectives of the system and instructed how to perform new tasks. –Training the users of specific skills required in new job.

Major Issues in Implementation • Changeover –- new system evaluated whether it solves the original problem. –Changeover to new system takes place if the new system proves to the satisfaction of the system analyst.

Information system Development

Information system Development • IS critical to the organization. • Various functional areas may be using IS • Effective system development requires detailed planning and team work. • IS designed with specific performance and cost objectives.

System Investigation • Problems a new or modified system can handle. • Opportunities a new system can provide. • New H/W and S/W, databases, personnel , telecom networks etc. will be required • Potential costs- fixed and variable. • Associated risks.

Feasibility Analysis • Investigates practicality of proposed solution. • Focus on user’s needs and how the proposed system can meet them. • Resources available for new system. • Likely impact of proposed system on organization. • How the new system fit within the organization

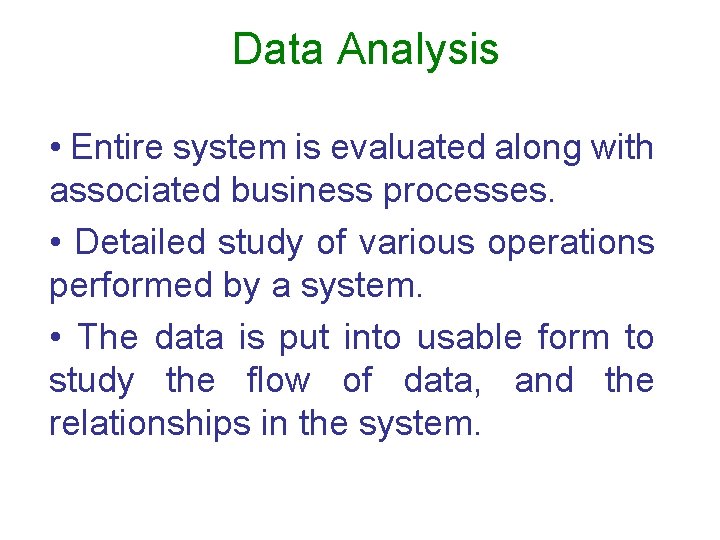
Data Analysis • Entire system is evaluated along with associated business processes. • Detailed study of various operations performed by a system. • The data is put into usable form to study the flow of data, and the relationships in the system.

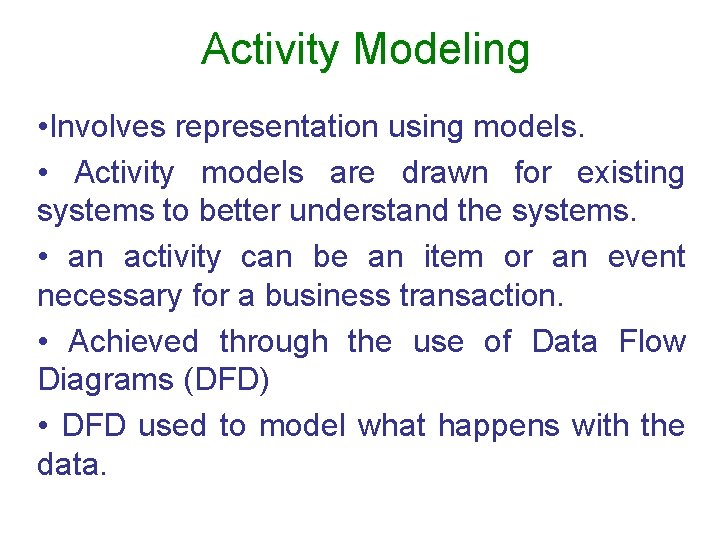
Activity Modeling • Involves representation using models. • Activity models are drawn for existing systems to better understand the systems. • an activity can be an item or an event necessary for a business transaction. • Achieved through the use of Data Flow Diagrams (DFD) • DFD used to model what happens with the data.

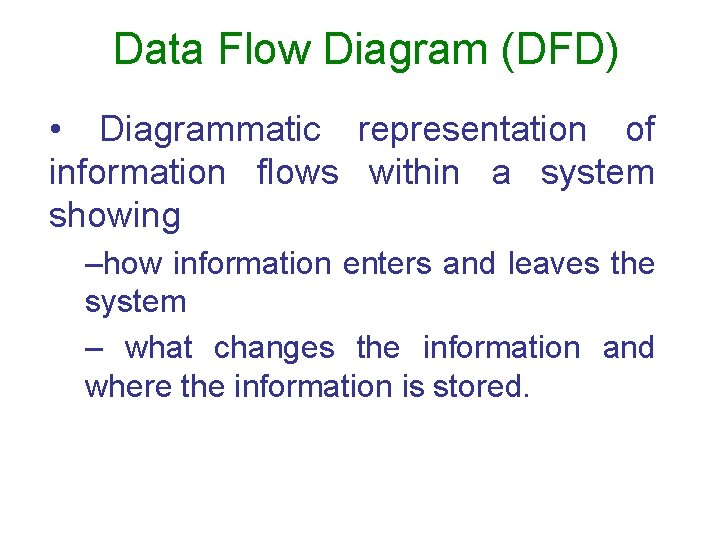
Data Flow Diagram (DFD) • Diagrammatic representation of information flows within a system showing –how information enters and leaves the system – what changes the information and where the information is stored.

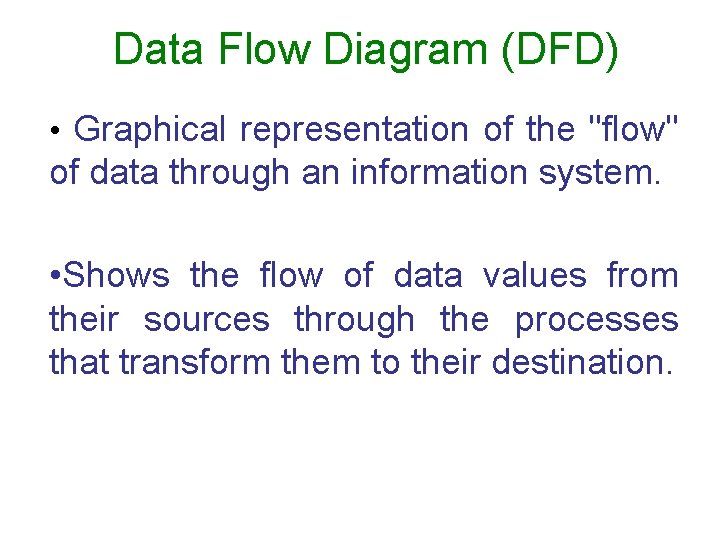
Data Flow Diagram (DFD) • Graphical representation of the "flow" of data through an information system. • Shows the flow of data values from their sources through the processes that transform them to their destination.

Data Flow Diagram (DFD) • Shows the flow of data values from their sources through the processes that transform them to their destination. • Easy to understand requires no technical knowledge. • Shows at a glance the scope, boundaries and interface with other systems.

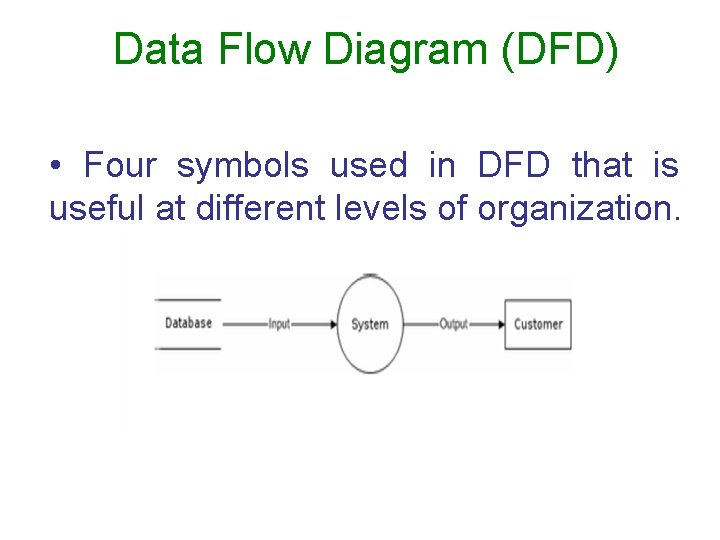
Data Flow Diagram (DFD) • Four symbols used in DFD that is useful at different levels of organization.

Data Flow Diagram (DFD) Limitations • Do not show the sequence in which processes occur and the time interval at which processes occur. • Do not highlight the structure of processes and data stores. • can not make out how often the process is repeated.

Elements of Data Flow Diagram Four basic elements: • Data flow –Set of data being transmitted between the objects on DFD. -Flow used to describe movement of information from one of the system to another. -flow represents data in motion while the stores indicate data at rest. - An arrow into or out of a process shows flow graphically.

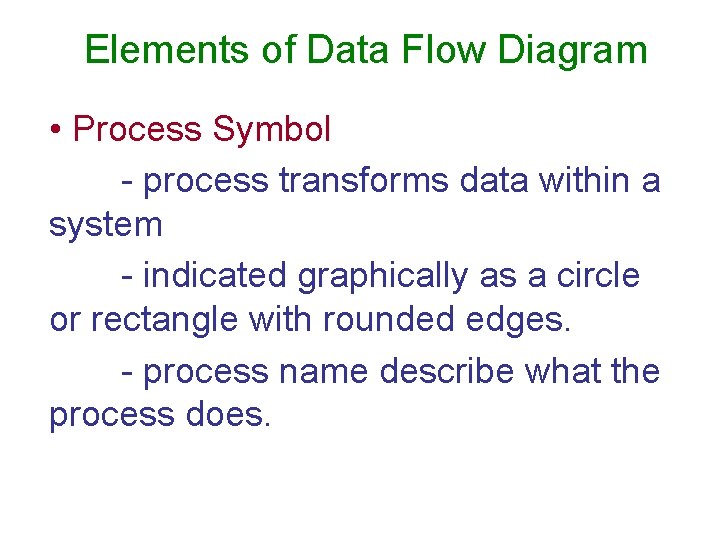
Elements of Data Flow Diagram • Process Symbol - process transforms data within a system - indicated graphically as a circle or rectangle with rounded edges. - process name describe what the process does.

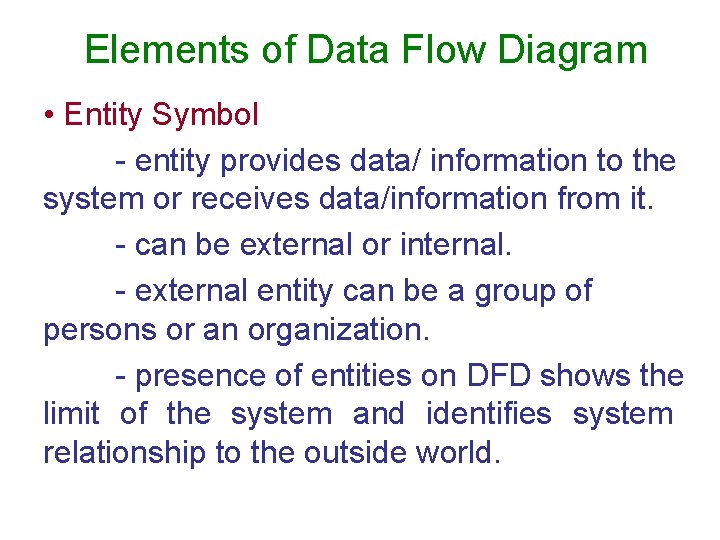
Elements of Data Flow Diagram • Entity Symbol - entity provides data/ information to the system or receives data/information from it. - can be external or internal. - external entity can be a group of persons or an organization. - presence of entities on DFD shows the limit of the system and identifies system relationship to the outside world.

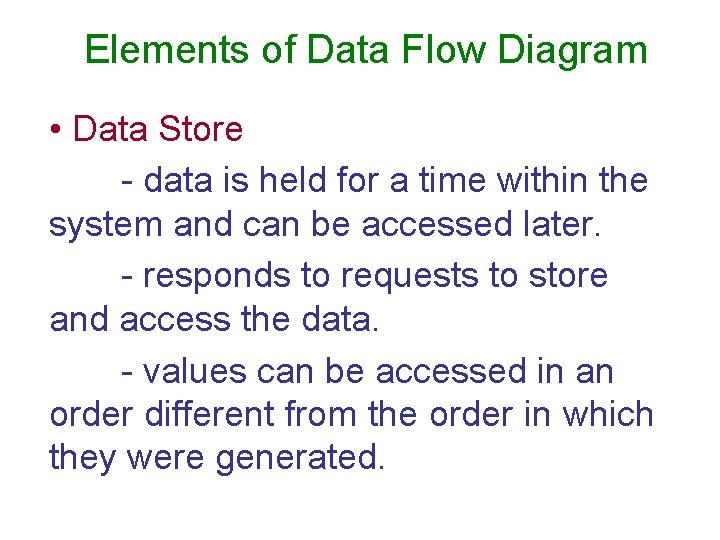
Elements of Data Flow Diagram • Data Store - data is held for a time within the system and can be accessed later. - responds to requests to store and access the data. - values can be accessed in an order different from the order in which they were generated.

Application Flowcharts • Graphical illustration of the steps and decisions in a procedure. • Visually represent the structure of information and show relationships between different steps and stages. • Describes chain of events that may or has occurred.

Requirement Analysis • Critical to the success of system development project. • Identifies users, stakeholders, organizational needs for the new system. • Involves studying problems with the current system and improving them. • Answers ‘what do the users need and want from the new system? ’

Requirement Analysis • Focus on determining the needs for a new or modified system, - taking into account of the conflicting requirements of the various stakeholders. • Measurable, testable, related to organizational needs.

Requirement Analysis Many Techniques • Direct questioning the users/ managers; Open or closed ended questions. • Brainstorming for generating new ideas and obtaining information requirements. • Group discussions and consensus.

Critical Success Factors (CSFs) • Critical factors or activities required for ensuring the success of a project or a business. • Involves identifying tasks and requirements needed for the success of an organization or a project. • Allows the firms to focus their efforts on building capabilities to meet the CSFs.

Critical Success Factors (CSFs) • Starts with a mission and vision statement. • Hierarchy of goals are developed and their success factors. • Corporate level information system goals and objectives are identified and prioritized. • Based on these, CSFs are defined for each major functional group within the organization.

Critical Success Factors (CSFs) • Prioritize and shape the requirements linked with information system projects.

IS Plan • Addresses long term system requirements. • Need for long range planning with information systems that are complex, require months and years to build. • Careful planning of IS that are embedded in organizations and add value to the products and business operations.

IS Plan • Planning for IS development done within the framework of organization’s overall MIS plan. • System development is a strategic decision and can have major implications. • First step in strategic planning is to state the MIS objectives clearly and the results expected.

IS Plan • MIS objectives must be in tune with the overall corporate plan, - types of systems and services to be offered, -role of users in system development and technology to be used. • MIS guidelines policies are defined as a guideline to be used in carrying out strategy.

Summary • Information system planning begins with the strategic plans of the organization. • The organizational strategic plans and the existing IT architecture provide the inputs for developing information systems strategic plans. • IS strategic plan may require a new IT architecture or the existing IT architecture may be sufficient.

Summary • System development cycle (SDLC) is a structured framework consisting of sequential processes: –Problem definition –Feasibility study –System analysis –System design –System development and implementation • These processes in turn consist of well defined tasks. • Some of these tasks may be present in most projects, while others in certain type of projects only.

Ethics

Ethics and IT Security • Moral choices made by individuals • Standards of acceptable behavior and rules governing members of society. • Business professionals have a responsibility to promote ethical uses of information technology in the workplace.

Business Ethics • Questions that managers must confront as part of their daily business decision making including: – Equity – Rights – Honesty – Exercise of Corporate Power

Principles of Technology Ethics • Proportionality – the good achieved by the technology must outweigh the harm or risk • Informed Consent – those affected by the technology should understand accept the risks

Principles of Technology Ethics • Justice – the benefits and burdens of the technology should be distributed fairly • Minimized Risk – even if judged acceptable by the other three guidelines, the technology must be implemented so as to avoid all unnecessary risk

Ethical Guidelines • Acting with integrity • Increasing professional competence • Setting high standards of personal performance • Accepting responsibility for one’s own work • Advancing the health, privacy, and general welfare of the public

Computer Crime • The unauthorized use, access, modification, and destruction of hardware, software, data, or network resources • The unauthorized release of information • The unauthorized copying of software • Denying an end user access to his or her own hardware, software, data, or network resources • Using or conspiring to use computer or network resources illegally to obtain information or tangible property

Hacking • The process of achieving access to a computer or computer network without legal authorization • A program or device may be modified to give the user access to features that were otherwise unavailable

Hacking • Computer hackers are employed by many companies. • These hackers use their skills to find faults in company’s security system so that it can be repaired quickly.

Common Hacking Tactics • Denial of Service – hammering a website’s equipment with too many requests for information, clogging the system, slowing performance or even crashing the site. • Sniffer – programs that covertly search individual packets of data as they pass through the Internet, capturing passwords or entire contents

Common Hacking Tactics • Spoofing – faking an e-mail address or Web page to trick users into passing along critical information like passwords or credit card numbers • Trojan Horse – a program that, unknown to the user, contains instructions that exploit a known vulnerability in some software

Common Hacking Tactics • Malicious Applets – tiny programs that misuse your computer’s resources, modify files on the hard disk, send fake e-mail, or steal passwords • Password Crackers – software that can guess passwords

Common Hacking Tactics • Logic Bombs – an instruction in a computer program that triggers a malicious act • Dumpster Diving – sifting through a company’s garbage to find information to help break into their computers

Cyber Theft • Stealing of financial and/or personal information through the use of computers for making its fraudulent or other illegal use. • A number of computer viruses are designed in such a way to steal the personal information such as bank account numbers, credit cards data etc.

Piracy • Software Piracy – unauthorized copying of computer programs • Piracy of Intellectual Property – unauthorized copying of copyrighted material, - such as music, videos, images, articles, books and other written works vulnerable to copyright infringement.

Privacy Issues • Accessing individuals’ private e-mail conversations –computer records, – collecting and sharing information about individuals gained from their visits to Internet websites and newsgroups

Privacy Issues • Using customer information gained from many sources to market additional business services • Collecting telephone numbers, e-mail addresses, credit card numbers, and other personal information to build individual customer profiles

Privacy on the Internet • E-mail can be encrypted • Newsgroup postings can be sent through anonymous remailers • ISP can be asked not to sell your name and personal information to mailing list providers and other marketers • Decline to reveal personal data and interests on online service and website user profiles

Privacy Laws • Rules that regulate the collection and use of personal data by businesses

Electronic Surveillance • Observation by means of an electronic equipment or other technological means. • System surveillance is the process of monitoring the behavior of people, objects or processes within the system for conformity to expected or desired norms.

Electronic Surveillance • Means of monitoring the activities of staff, labor and trade union activist. • Organizations may use closed circuit television cameras. • Computers can be tapped by means of methods like installation of physical bugs, surveillance software.

Other Challenges • Employment – significant reductions in job opportunities as well as different types of skills required for new jobs • Computer Monitoring – computers used to monitor the productivity and behavior of employees as they work

Other Challenges • Working Conditions – jobs requiring a skilled craftsman have been replaced by jobs requiring routine, repetitive tasks or standby roles • Individuality – dehumanize and depersonalize activities because computers eliminate human relationships

Security Management • The goal of security management is the accuracy, integrity, and safety of all information system processes and resources.

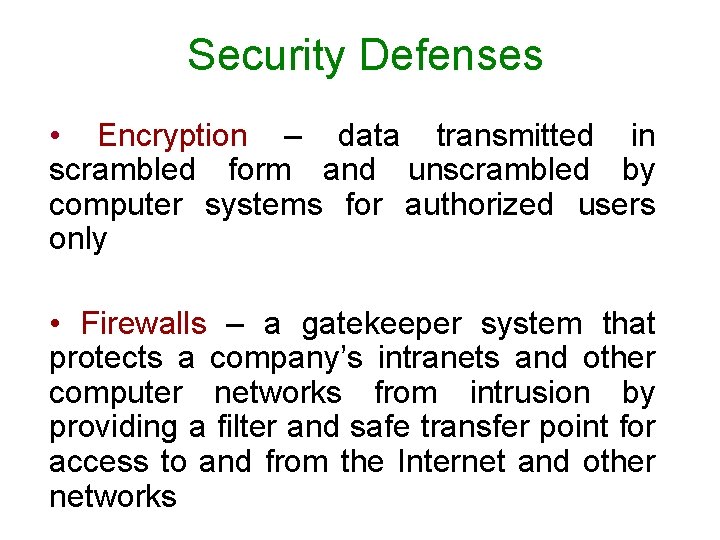
Security Defenses • Encryption – data transmitted in scrambled form and unscrambled by computer systems for authorized users only • Firewalls – a gatekeeper system that protects a company’s intranets and other computer networks from intrusion by providing a filter and safe transfer point for access to and from the Internet and other networks

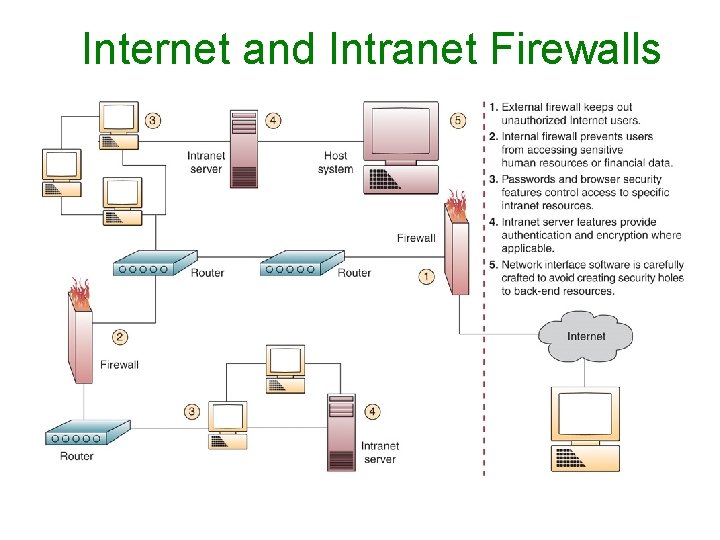
Internet and Intranet Firewalls

Security Defenses • E-mail Monitoring – use of content monitoring software that scans for troublesome words that might compromise corporate security • Virus Defenses – centralize the distribution and updating of antivirus software

Other Security Measures • Security Codes – multilevel password system used to gain access into the system • Backup Files – duplicate files of data or programs • Security Monitors – software that monitors the use of computer systems and networks and protects them from unauthorized use, fraud, and destruction

Other Security Measures • Biometrics – computer devices that measure physical traits that make each individual unique. • Computer Failure Controls – devices used to prevent computer failure or minimize its effects

Fault Tolerant Systems • Systems that have redundant processors, peripherals, and software that provide a: Fail-over capability to back up components in the event of system failure Fail-safe capability where the computer system continues to operate at the same level even if there is a major hardware or software failure

Disaster Recover • Formalized procedures to follow in the event a disaster occurs including: –Which employees will participate –What their duties will be –What hardware, software, and facilities will be used –Priority of applications that will be processed –Use of alternative facilities –Offsite storage of an organization’s databases

Auditing IT Security • IT security audits review and evaluate whether proper and adequate security measures and management policies have been developed and implemented. • This typically involves verifying the accuracy and integrity of the software used, as well as the input of data and output produced by business applications.

Summary • The vital role of information technologies and systems in society raises serious ethical and societal issues in terms of - their impact on employment, -individuality, -working conditions, -privacy, -health, and computer crime.

Summary • Business and IT activities involve many ethical considerations. • Basic principles of technology and business ethics can serve as guidelines when dealing with ethical business issues that may arise in the widespread use of information technology in business and society.

Summary • Most important responsibilities of the management of a company is to assure the security and quality of its IT-enabled business activities.

Summary • Security management tools and policies can ensure - the accuracy, integrity, safety of the information systems; - efficient use of resources of a company, minimize errors, fraud and security losses in their business activities.