STORAGE AND RETRIEVAL CORE 2 Information systems and











- Slides: 18

STORAGE AND RETRIEVAL CORE 2: Information systems and Databases

STORAGE AND RETRIEVAL Storage and Retrieval of data occurs within all information systems, however it is particularly critical regarding large data stores. The performance of databases is centred on the efficiency of storage and retrieval systems. Storing and Retrieval is a two part process… § Storing saves data or information § Retrieving reloads data or information

STORAGE AND RETRIEVAL A database management system is used to provide secure and efficient methods for storage and retrieval of information from a database. DATABASE MANAGEMENT SYSTEM (DBMS)- is a software package that allows users to access a database so they can enter, maintain and view the data. In a DBMS data is organised into tables, viewed in forms, retrieved using queries and displayed in reports. DBMSs manipulate the data in ways such as searching and sorting. They also perform a number of tasks to help users develop and maintain a database : § § § organising the data using a data dictionary showing relationships between entities using schematic diagrams checking for identifiable errors in data entry allowing flexibility to change the definition of the database restricting access to the data to authorised people providing information about the performance of a database

STORAGE AND RETRIEVAL During this section of the course we will explore… 1. Types of Storage Hardware 2. Techniques for Data Security 3. Searching and Sorting

ACCESSING DATA: Before we look at types of hardware we need to remind ourselves of the different way data is accessed. SEQUENTIAL ACCESS occurs when data is accessed in a sequence. Data is accessed in the order it was stored. It does not require the exact location of the data item. Sequential is much slower than direct and impractical when immediate processing is required. It is the only method of accessing data stored on magnetic tape. (THINK CASSETTE TAPE) DIRECT ACCESS occurs when data is accessed without accessing previous data items. Data is stored in a particular storage location based on a mathematical procedure or algorithm. Direct access uses this algorithm to calculate the approximate location of the data. If the data is not found here the computer searches through successive locations until it is found. Direct data often requires the use of an index and this is called indexed access. (THINK COMPACT DISK)

ONLINE / OFFLINE STORAGE Offline refers to storage that cannot be accessed unless it is mounted on a drive. E. g. flash drive, CD’s, DVDs. Online data is available immediately to connected computers. E. g. A hard drive or H: drive. Cloud computing refers to storage of data through an external storage medium. For example, the gaming company Steam offers cloud saving of game data so that if your personal harddrive crashes your data will be safe in another location.

MAGNETIC STORAGE Magnetic storage is currently the most popular method for maintaining large quantities of data. It provides large storage capacity and can allow for direct access at high speeds for both storage and retrieval. Neither cloud nor optical storage can compete in terms of times required for storage and retrieval. We will look at the following examples… § § Hard Disks RAID (Redundant Array of Independent Disks) Cartridge and Tape Libraries

MAGNETIC STORAGE Example How it works Hard drive Store data magnetically on aluminium or glass. Data is arranged into tracks and sectors. Data is analysed through changes in magnetic fields representing 1 and O. Read/write heads use electromagnets to write data into the disk. RAID Stands for Redundant Array of Independent Disks. Utilises multiple hard disk drives together with a RAID controller. The computer sees the RAID drive as a single drive, when really the drive is a controller which mirrors or stripes the data onto multiple hard-drive-disks. • Mirroring involves backing up the same data onto every hard-drive. • Striping involves saving fragments of data across each hard-drive, allowing for faster access. Cartridge and Tape First appeared in 1950. Magnetic tape consists within small cassette cartridges. Can store up to 500 gb at only a couple of cents per gigabyte. Tape libraries are robotic controllers that automatically cycle through libraries of tape that can back-up information.

OPTICAL STORAGE Optical Storage processes are based on the reflection of light. The difference between a good and a poor reflection is used to represent binary and as such – data. Due to the tightly packed data on optical storage lasers are used for their consistency and high focus. We will look at… § Compact Disc (CD) § Digital Versatile Disc (DVD) & § Bluray

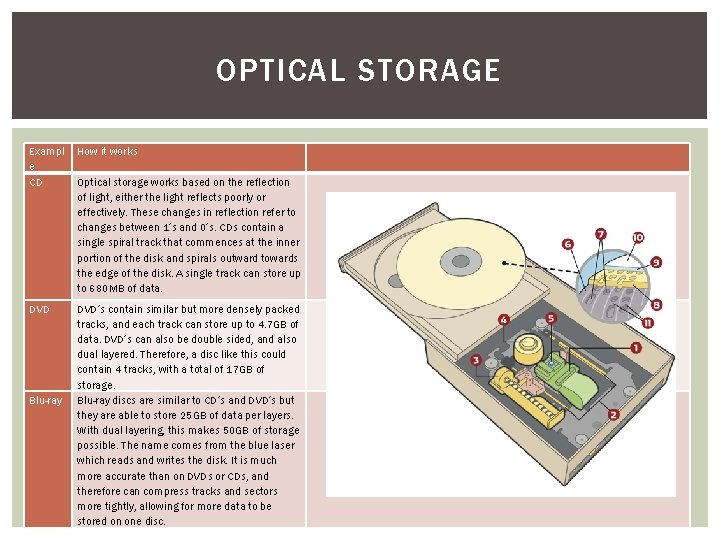
OPTICAL STORAGE Exampl e CD How it works DVD’s contain similar but more densely packed tracks, and each track can store up to 4. 7 GB of data. DVD’s can also be double sided, and also dual layered. Therefore, a disc like this could contain 4 tracks, with a total of 17 GB of storage. Blu-ray discs are similar to CD’s and DVD’s but they are able to store 25 GB of data per layers. With dual layering, this makes 50 GB of storage possible. The name comes from the blue laser which reads and writes the disk. It is much more accurate than on DVDs or CDs, and therefore can compress tracks and sectors more tightly, allowing for more data to be stored on one disc. Blu-ray Optical storage works based on the reflection of light, either the light reflects poorly or effectively. These changes in reflection refer to changes between 1’s and 0’s. CDs contain a single spiral track that commences at the inner portion of the disk and spirals outward towards the edge of the disk. A single track can store up to 680 MB of data.

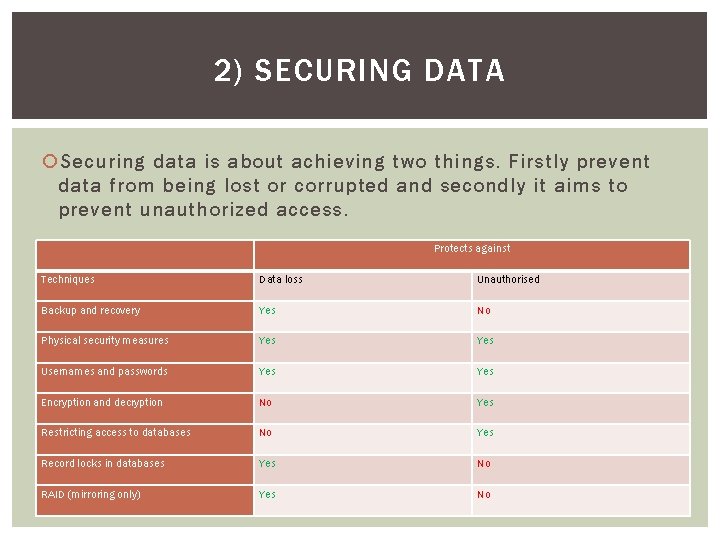
2) SECURING DATA Securing data is about achieving two things. Firstly prevent data from being lost or corrupted and secondly it aims to prevent unauthorized access. Protects against Techniques Data loss Unauthorised Backup and recovery Yes No Physical security measures Yes Usernames and passwords Yes Encryption and decryption No Yes Restricting access to databases No Yes Record locks in databases Yes No RAID (mirroring only) Yes No

2) SECURING DATA BACKUPS & RECOVERY Backup refers to copying files to a separate secondary storage device as a precaution in case the first device fails or data is lost. There are two types of backup that are commonly used : Full backups – Includes a backup of all files. Synchronises everything, every time that a backup is made. Partial backups – Only backs up files that have been created or edited since the last backup. These are identified using archive bits which are set to true once a file has been altered. Partial backups could be Incremental or Differential. Frequency of backups depends on how critical the data is to the organisation and how often data changes.

2) SECURING DATA PHYSICAL SECURITY MEASURES These measures are used for reducing data loss and unauthorised access. For example: server rooms should be locked so as to keep out curious or malicious personnel. These rooms should also be air conditioned to prevent overheating and climate control to reduce moisture. Government military computer facilities would be housed within a solid bomb proof concrete bunker.

2) SECURING DATA USERNAMES and PASSWORDS User names and passwords secure individual files, directories or storage devices. User names and passwords are used by operating systems and network software. User names identify admin levels. Passwords gain access to these levels.

2) SECURING DATA ENCRYPTION and DECRYPTION Encryption is the process of making data unreadable by those who do not possess the decryption key. Decryption is the process of decoding encrypted data using a key. The opposite of encryption. Single key encryption is used within companies etc where all computers are linked. Every computer has a code that is the same code to encrypt and decrypt. A public key system uses public and private keys or Two key systems. It works in that every user has a public and private key. When someone wants to send them an encrypted code, they tell them their public key. The person encrypts their message with this public key and sends the message. However the message can only be decrypted by the initial user with the private key. This means that it does not matter who knows your public key, so long as your private key is kept safe.

2) SECURING DATA RESTRICTING ACCESS by DBMS USERS VIEWS Users Views are essentially what users see when they access a database. The definition for a User view is: The restricted portion of a database made available to a user. For example: Online games may have scoreboards which show the names and servers of leading players. The databases that hold the names of these players are probably run by the company that owns the games, and therefore knows the players passwords. However, when a player views the leader boards, the only view that they get of the player with top score is their name, when realistically, the database probably knows a lot more. A user view does not change the organisation of layout of a database, it only restricts users from viewing complete attributes etc that are beyond their authorisation.

2) SECURING DATA RECORD LOCKS in DBMS This refers to when a databases locks a record so that it cannot be edited by two users at once. The two strategies are pessimistic and optimistic locking. Pessimistic involves the DBMS allowing the first to begin editing to have solo access to the record, while optimistic allows the user to decide to overwrite the edited record with their editing, or discard their editing.

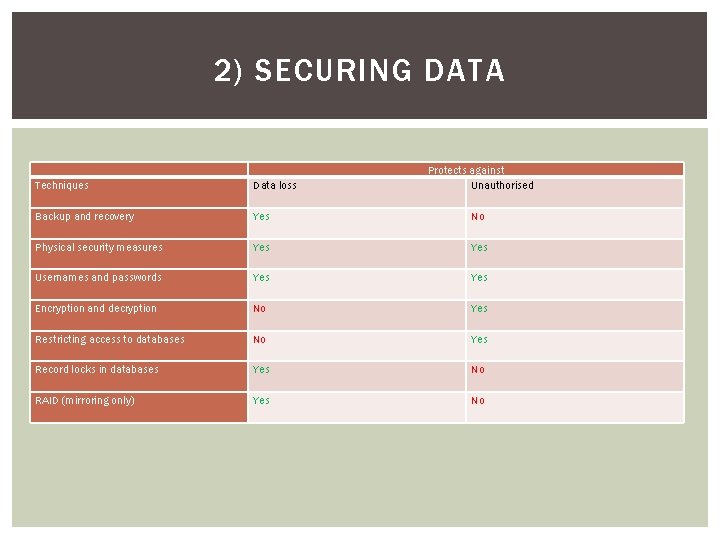
2) SECURING DATA Protects against Unauthorised Techniques Data loss Backup and recovery Yes No Physical security measures Yes Usernames and passwords Yes Encryption and decryption No Yes Restricting access to databases No Yes Record locks in databases Yes No RAID (mirroring only) Yes No