Steps towards a secured DNS Olaf M Kolkman















- Slides: 20

Steps towards a secured DNS Olaf M. Kolkman, Henk Uijterwaal, Daniel Karrenberg and Jürgen Pfleger Olaf M. Kolkman . Apricot 2003 , February 2003, Amsterdam . http: //www. ripe. net/disi

Who, why and what • RIPE NCC DISI project – RIPE NCC’s mission – DISI project • Deployment of Internet Security Infrastrucure • Identify, Implement and raise awareness of security infrastructure to improve quality of Internet in the RIPE region • Focus on DNSSEC • Goal of the presentation – This presentation is on steps one need to take to deploy DNSSEC in an organization. • Serves as DISI status report Olaf M. Kolkman . Apricot 2003 , February 2003, Amsterdam . http: //www. ripe. net/disi

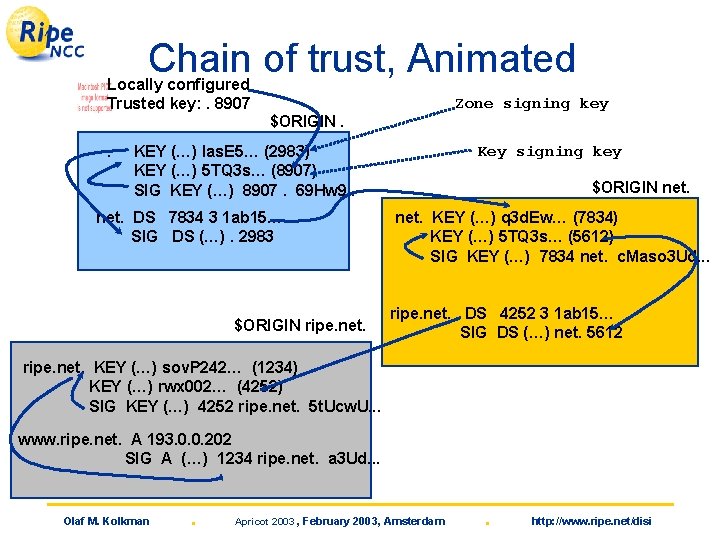
DNSSEC in a nutshell • Security is provided by signing RR sets using public key crypto • Keys are published in the DNS • Key infrastructure is build by delegating signing authority from parent to child. • RR sets are signed by zone signing keys, key RR sets are signed by key-signing keys, ‘pointers’ to the key-signing keys (DS) are signed by the parent Olaf M. Kolkman . Apricot 2003 , February 2003, Amsterdam . http: //www. ripe. net/disi

Chain of trust, Animated Locally configured Trusted key: . 8907 Zone signing key $ORIGIN. . Key signing key KEY (…) las. E 5… (2983) KEY (…) 5 TQ 3 s… (8907) SIG KEY (…) 8907. 69 Hw 9. . net. DS 7834 3 1 ab 15… SIG DS (…). 2983 $ORIGIN ripe. net. $ORIGIN net. KEY (…) q 3 d. Ew… (7834) KEY (…) 5 TQ 3 s… (5612) SIG KEY (…) 7834 net. c. Maso 3 Ud. . . ripe. net. DS 4252 3 1 ab 15… SIG DS (…) net. 5612 ripe. net. KEY (…) sov. P 242… (1234) KEY (…) rwx 002… (4252) SIG KEY (…) 4252 ripe. net. 5 t. Ucw. U. . . www. ripe. net. A 193. 0. 0. 202 SIG A (…) 1234 ripe. net. a 3 Ud. . . Olaf M. Kolkman . Apricot 2003 , February 2003, Amsterdam . http: //www. ripe. net/disi

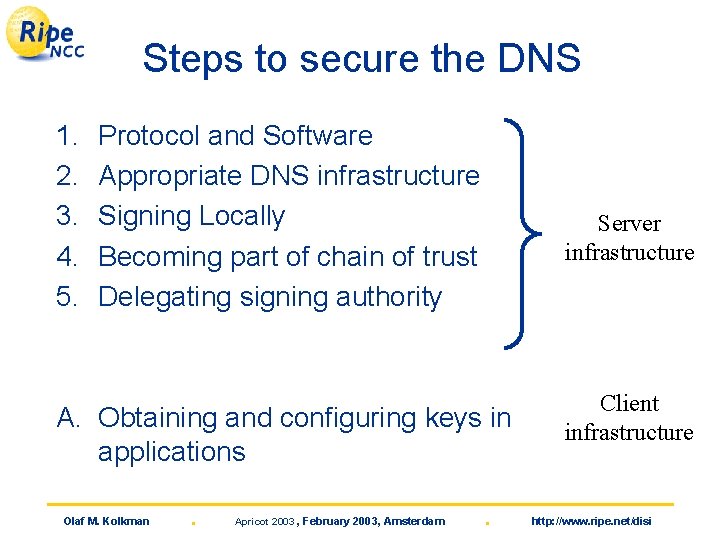
Steps to secure the DNS 1. 2. 3. 4. 5. Protocol and Software Appropriate DNS infrastructure Signing Locally Becoming part of chain of trust Delegating signing authority Server infrastructure A. Obtaining and configuring keys in applications Olaf M. Kolkman . Apricot 2003 , February 2003, Amsterdam . Client infrastructure http: //www. ripe. net/disi

Step 1: Protocol and Software • DNSSEC specs still not finished. – DS identified corner cases that are being addressed – OPT-IN is being tested – Wildcard handling may need some clarification • Most people agree these are no show stoppers – Try not to add new protocol features to DNSSEC – Bind 9 snapshot reflects current state – Production quality in about 6 months from now (? !) Olaf M. Kolkman . Apricot 2003 , February 2003, Amsterdam . http: //www. ripe. net/disi

Step 1: Protocol and Software @RIPE NCC • We have been actively involved in the IETF process – Cooperated and hosted workshops for software and protocol tests (January 21 -23, tests of OPT-IN and tests of possible solutions to current problems) – Published 2 drafts • drafr-ietf-dnsext-keyrr-key-signing-flag • draft-olaf-dnsext-dnssec-wildcard-optimization • Continued work on Net: : DNS: : SEC – Perl module that adds DNSSEC support to Net: : DNS – Turned out to be very handy for writing little support scripts • Collaborate with NLnet Labs on development of DNSSEC aware NSD. – Version 1. 2 will have DNSSEC support Olaf M. Kolkman . Apricot 2003 , February 2003, Amsterdam . http: //www. ripe. net/disi

Intermezzo: Shameless NSD plug • Name Server Daemon – Authoritative only high performance name server • Order 30000 queries per second… • K. root-servers. net runs NSD. – Fully RFC conformant – Regression tested against the bind implementation • Version 1. 0. 2 available and more info at http: //www. nlnetlabs. nl/nsd Olaf M. Kolkman . Apricot 2003 , February 2003, Amsterdam . http: //www. ripe. net/disi

Step 2: Appropriate DNSSEC infrastructure • All authoritative servers for a zone will need to be DNSSEC aware – Either bind 9 or, in the near future NSD • Be aware: Zone sizes will grow by factor 5 -10 – Memory and disk usage on your servers – Network traffic will increase • Contact your ‘slaves’ as soon as possible – If one of your slaves is not DNSSEC aware this will cause lameness problems – Same considerations with respect to hardware • Consider DNSSEC if you plan an upgrade of your infrastructure in the near future! Olaf M. Kolkman . Apricot 2003 , February 2003, Amsterdam . http: //www. ripe. net/disi

Step 2: Appropriate DNSSEC infrastructure @RIPE NCC • Operations department is aware of requirements – We currently run Bind 9. 2, DNSSEC is not enabled • We’ll be contacting secondaries to make an inventory of possibilities. – Awareness of DNSSEC? – Architectural considerations at secondary? – The requirement of all slaves being DNSSEC aware may well be the most delaying factor in deployment of DNSSEC Olaf M. Kolkman . Apricot 2003 , February 2003, Amsterdam . http: //www. ripe. net/disi

Step 3: Signing Locally • Design and document policies – Consider: Key length, zone vs key signing keys, algorithm, signing frequency, key storage, emergency (compromise) procedure. • Design and implement a key maintenance system – Based on above policies • Set up the procedures and cron jobs to resign – Forgetting to sign causes problems. Olaf M. Kolkman . Apricot 2003 , February 2003, Amsterdam . http: //www. ripe. net/disi

Step 3: Signing Locally @RIPE NCC • Detailed procedures have not yet crystallized. • A key maintenance tool that allows for easy key creation, rollover etc is in alpha stage. – Front end to the bind tools – Will be available to the community • Mail olaf@ripe. net if you want to do alpha testing • Some ‘non-production’ zones are signed and resigned using the tools. – dig secret-wg. org SOA +dnssec (assuming your dig is dnssec aware) Olaf M. Kolkman . Apricot 2003 , February 2003, Amsterdam . http: //www. ripe. net/disi

Step 4: Becoming part of chain of trust • Contact your parent, and upload your key. – Adapt your key management to their policies Olaf M. Kolkman . Apricot 2003 , February 2003, Amsterdam . http: //www. ripe. net/disi

Step 4: Becoming part of chain of trust @RIPE NCC • RIPE NCC participates in on-line experiments – Signed disi. nl, for details of the experiment: • http: //secreg. nlnetlabs. nl/index. html • Most of our zones are below in-addr. arpa – Signing in-addr. arpa has similar problems as signing root. – Also see draft-ihren-dnsop-interim-signed-root-01. txt – Brainstorming about possible requirements and solutions in RIR context • The before mentioned key maintenance tool is used for maintenance of disi. nl – Automatic resigning of the zone – Occasional key-rollover Olaf M. Kolkman . Apricot 2003 , February 2003, Amsterdam . http: //www. ripe. net/disi

Step 5: Delegating signing authority • Adapt your registry system to allow for keyupload • Design procedures for initial key exchange – How do establish that the public key you obtained came from the child zones. – Document procedures Olaf M. Kolkman . Apricot 2003 , February 2003, Amsterdam . http: //www. ripe. net/disi

Step 5: Delegating signing authority @RIPE NCC Requirements for signing the in-addr. arpa namespace • Technical – make key exchange procedure independent of other registry procedure – Light weight and flexible – Allow for future incorporation into tools and policies • Start has been made writing software libraries – Needs most work – Prototype registry build by ISI/EAST based on that • Procedures and policies that do not put a large burden on the ‘client’ and that are, if possible, consistent over the 4 regions – First brainstorm meeting with the RIRs on steps forward during IETF 55 Olaf M. Kolkman . Apricot 2003 , February 2003, Amsterdam . http: //www. ripe. net/disi

Step a: Configuring Client Applications • Clients need to configure ‘secure entry points’ – Need to obtain keys • Application available: – bind 9: caching forwarder and LWRES library – Central caches running DNSSEC would secure a large customer base against DNSSEC spoofs. • Chicken and egg problem. – Without infrastructure few applications will develop – API will need more work Olaf M. Kolkman . Apricot 2003 , February 2003, Amsterdam . http: //www. ripe. net/disi

Step a: Configuring Client Applications @RIPE NCC • Little we can do in this arena. • Net: : DNS: : SEC may be used to put DNSSEC support into your perl code e. g. for troubleshooting tools Olaf M. Kolkman . Apricot 2003 , February 2003, Amsterdam . http: //www. ripe. net/disi

Other DISI efforts w. r. t. DNSSEC Important aspects of DISI is raising awareness • DNSSEC trainings have moved from New Projects to the training dept. – About 10 -12 trainings per year – Constantly updated with new developments – Goal: Awareness with technology, be ready to deploy as soon as production code servers are available • Training material such as slides and examples are available through the website and on request Olaf M. Kolkman . Apricot 2003 , February 2003, Amsterdam . http: //www. ripe. net/disi

Questions? ? ? • Slides will be available from http: //www. ripe. net/disi • DNSSEC resources: – http: //www. nlnetlabs. nl/dnssec/ – http: //www. dnssec. org/ (portal) • Questions: okolkman@ripe. net Olaf M. Kolkman . Apricot 2003 , February 2003, Amsterdam . http: //www. ripe. net/disi