State of NASA Cyber Security Valarie Burks August

State of NASA Cyber Security Valarie Burks August, 2011

• • • State of Cyber Security Accomplishments/Highlights Centers of Influence Cyber Security: The Big Picture Cyber Security Requirements Cyber Security Concerns Cyber Security Strategic Objectives Cyber Security: The Transformation Key Areas of Focus-Next Steps

State of NASA Cyber Security (1/2) • There are recognized problems and opportunities in the IT Security Program. • No Perfect Security – Threats and vulnerabilities change faster than our assurance posture – Tools and processes are by and large reactive – Nature of mission life cycle development extends into 10 -15 years; and the threat profile changes within this time frame – Nature of discipline suggests that there is always residual risk; key is to know it exists so that appropriate actions can be taken • Centers and Mission Directorates IT Security stakeholders are taking reactive actions to secure the enterprise IT infrastructure

State of NASA Cyber Security (2/2) • Increasing GAO and OIG Audit Findings • Cyber Security Incidents on the Rise • What’s underway: Active collaboration with stakeholders to improve NASA’s security posture – Drive and reinforce behaviors which protect the confidentiality, integrity and availability of NASA’s intellectual property and information assets – Link strategic security plan to mission objectives – Build and execute communications strategy – market/socialize security value proposition to the Agency – Realign one off Center-by-Center security solutions

Accomplishments/Highlights • Monitoring of NASA’s corporate, scientific, and technical information systems currently includes: – Expansion of Cyber Security Operations Center coverage to include Mission networks – Incident responders at NASA Centers promptly take action to mitigate the impact of incidents – Automated systems that identify the agency’s IT inventory – Role-based security awareness training that focuses on methods and requirements to protect NASA IT assets – Personal identity verification cards implementation
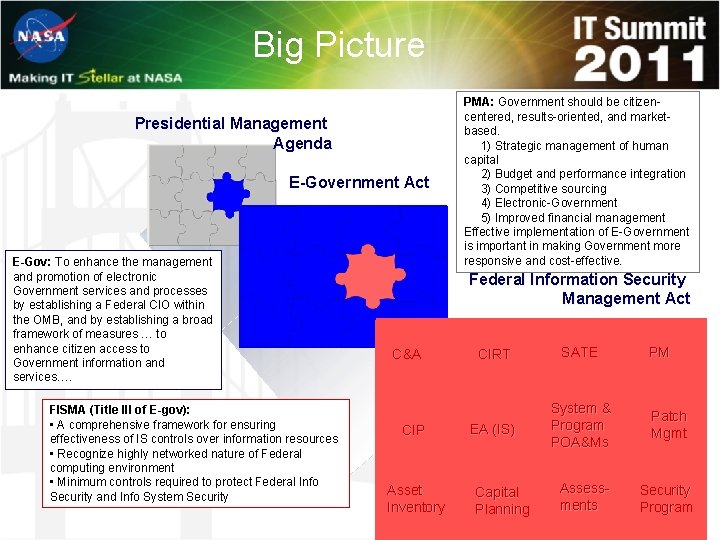
Big Picture Presidential Management Agenda E-Government Act E-Gov: To enhance the management and promotion of electronic Government services and processes by establishing a Federal CIO within the OMB, and by establishing a broad framework of measures … to enhance citizen access to Government information and services…. FISMA (Title III of E-gov): • A comprehensive framework for ensuring effectiveness of IS controls over information resources • Recognize highly networked nature of Federal computing environment • Minimum controls required to protect Federal Info Security and Info System Security PMA: Government should be citizencentered, results-oriented, and marketbased. 1) Strategic management of human capital 2) Budget and performance integration 3) Competitive sourcing 4) Electronic-Government 5) Improved financial management Effective implementation of E-Government is important in making Government more responsive and cost-effective. . Federal Information Security Management Act C&A CIP Asset Inventory CIRT SATE EA (IS) System & Program POA&Ms Patch Mgmt Assessments Security Program Capital Planning PM
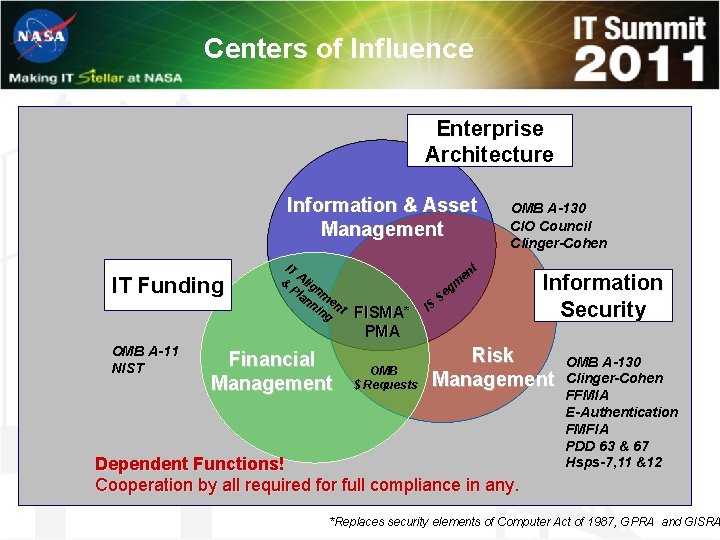
Centers of Influence Enterprise Architecture Information & Asset Management IT Funding OMB A-11 NIST IT & Alig Pl nm an ni ent ng Financial Management OMB A-130 CIO Council Clinger-Cohen t en gm FISMA* PMA OMB $ Requests IS Se Information Security Risk Management Dependent Functions! Cooperation by all required for full compliance in any. OMB A-130 Clinger-Cohen FFMIA E-Authentication FMFIA PDD 63 & 67 Hsps-7, 11 &12 *Replaces security elements of Computer Act of 1987, GPRA and GISRA

Why Are We Concerned About Cyber Security? High Risk Threats • Well-resourced, highly-motivated groups of cyber-warriors • Numerous attack vectors including email, social media, and apparent trust paths like those with contractor facilities • Use of zero-day attacks and exploitation of weak credentials are common • Often referred to as the Advanced Persistent Threat in public media Medium Risk Threats • Criminals targeting identity and money • Varying levels of technical sophistication • Botnets and Bot Herders Low Risk Threats • Standard Internet Pollution • Threats against every user • Unsophisticated

Why Are We Concerned About Cyber Security? • Cyber Security Incidents on the Rise (2010): – 93% increase in web attacks – 260, 000 identities exposed per data breach caused by hacking – 42% more mobile vulnerabilities – 14 new Zero-Day Vulnerabilities were found in widely used applications. Source: Symantec Corporation : Internet Security Threat Report – Trends for 2010

Why Are We Concerned About Cyber Security? • Industrial Theft or Economic Espionage – These are targeted compromises • Non-Targeted Compromise of NASA Systems – NASA has evidence of non-targeted NASA system attacks • Spear phishing attacks – Threat sources include hackers, criminals, and botnets. • Insiders – NASA is susceptible to the threat of data loss, via subversion or vulnerabilities accidentally triggered by trusted NASA users or partners.

Why Are We Concerned About Cyber Security? • Mobile devices extend NASA infrastructure • Corporate and personal devices allow data to be accessed and moved easily – Another data gold mine when lost or stolen • Smart Phones • PDAs • Memory cards • The continued shift to an environment where data is available to everyone, from any location on any device creates security risk to the enterprise
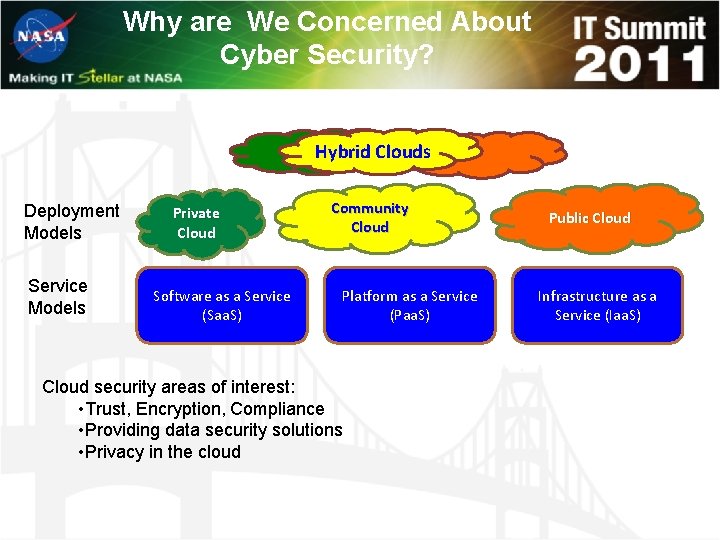
Why are We Concerned About Cyber Security? Hybrid Clouds Deployment Models Service Models Private Cloud Software as a Service (Saa. S) Community Cloud Platform as a Service (Paa. S) Cloud security areas of interest: • Trust, Encryption, Compliance • Providing data security solutions • Privacy in the cloud Public Cloud Infrastructure as a Service (Iaa. S)

Why Are We Concerned About Cyber Security The Advanced Persistent Threat • NASA faces sophisticated attacks which target the Agency’s critical infrastructure. • Attackers employ a variety of methods to obtain unauthorized access to systems, intellectual property, and email accounts of key Agency officials and scientific leaders. Challenges • Attackers use various paths to attack NASA’s targets including: – Trojans, malware, phishing emails, and – Complex attacks on common applications.

Why Are We Concerned About Cyber Security • Numerous Types of Risk Exposure – Loss of sensitive information related to advanced technology, engineering designs, and program planning, – Loss of system integrity and availability, and – Disruption to NASA Scientific and Partner Programs • Potential impacts include: – – – Damage to NASA’s reputation, Loss of position as the world’s premiere space agency, Inability to control space craft or launch vehicle, Exposure of export control data (ITAR/EAR), Disruption of the science processing pipeline, which could impact other agencies (e. g. USGS and NOAA/NWS), and – Financial losses 14

IT Security Vision • ITSD Vision: Develop and employ a unified continuous monitoring framework to respond to cyber security incidents and threats impacting NASA’s personnel, intellectual property, corporate and customer information, networks and computing resources. 15

IT Security Strategic Objectives • Strategic Objectives: Protect NASA’s information and information systems to ensure that the confidentiality, integrity, and availability of all information is protected commensurate with mission needs, and associated threats – Reduce risk of loss, unauthorized disclosure, or unauthorized modification of NASA information and information systems – Protect information by recognizing and responding to threats, vulnerabilities, and deficiencies; ensuring that all systems and networks are capable of self-defense – Establish and maintain NASA’s enterprise IT Security Continuous Monitoring architecture 16
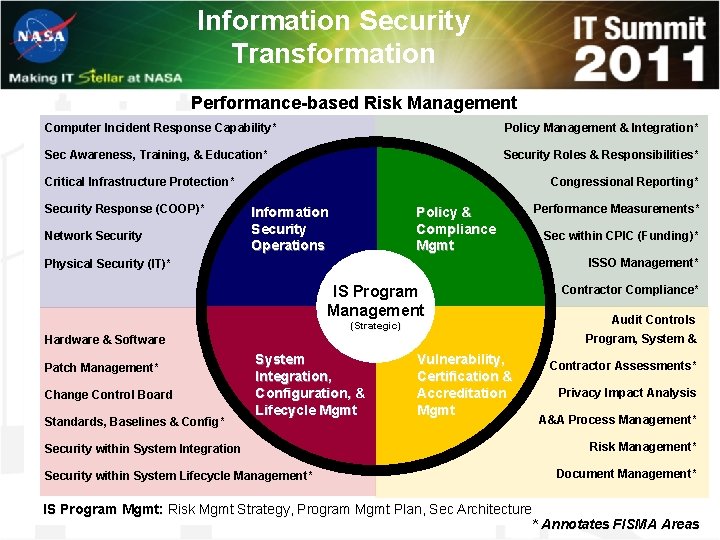
Information Security Transformation Performance-based Risk Management Computer Incident Response Capability* Policy Management & Integration* Sec Awareness, Training, & Education* Security Roles & Responsibilities* Critical Infrastructure Protection* Security Response (COOP)* Network Security Congressional Reporting* Information Security Operations Policy & Compliance Mgmt IS Program Management (Strategic) Standards, Baselines & Config* Contractor Compliance* Audit Controls Program, System & Hardware & Software Change Control Board Sec within CPIC (Funding)* ISSO Management* Physical Security (IT)* Patch Management* Performance Measurements* System Integration, Configuration, & Lifecycle Mgmt Security within System Integration Security within System Lifecycle Management* Vulnerability, Certification & Accreditation Mgmt Contractor Assessments* Privacy Impact Analysis A&A Process Management* Risk Management* Document Management* IS Program Mgmt: Risk Mgmt Strategy, Program Mgmt Plan, Sec Architecture * Annotates FISMA Areas
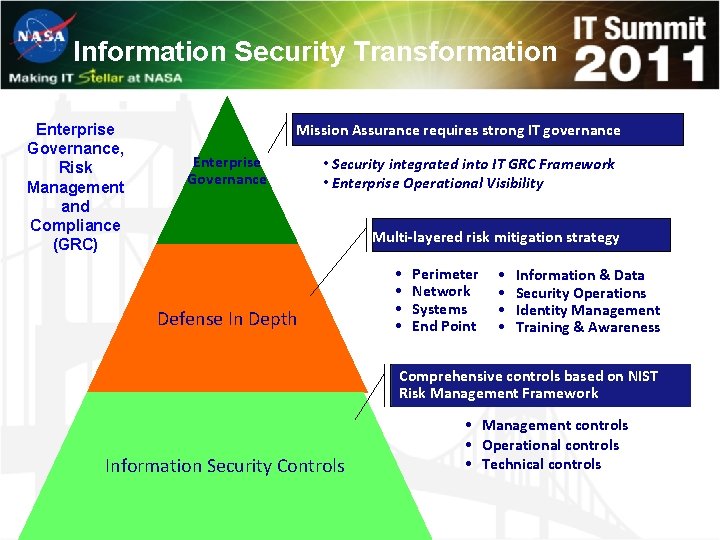
Information Security Transformation Enterprise Governance, Risk Management and Compliance (GRC) Mission Assurance requires strong IT governance Enterprise Governance • Security integrated into IT GRC Framework • Enterprise Operational Visibility Multi-layered risk mitigation strategy Defense In Depth • • Perimeter Network Systems End Point • • Information & Data Security Operations Identity Management Training & Awareness Comprehensive controls based on NIST Risk Management Framework Information Security Controls • Management controls • Operational controls • Technical controls
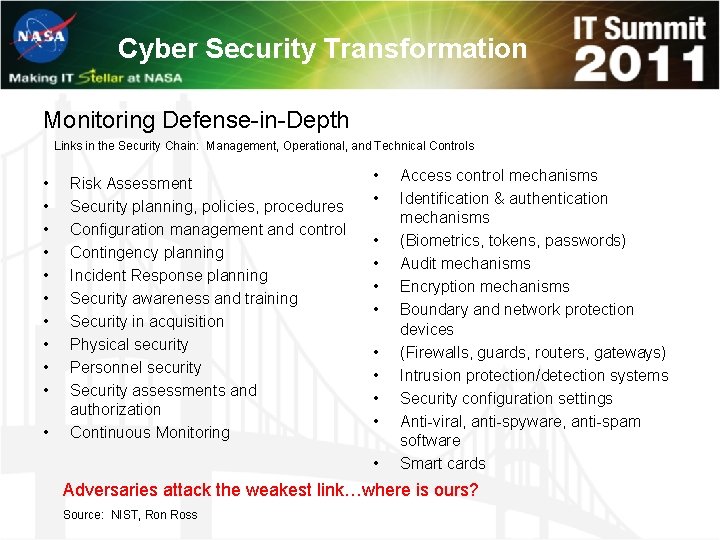
Cyber Security Transformation Monitoring Defense-in-Depth Links in the Security Chain: Management, Operational, and Technical Controls • • • Risk Assessment Security planning, policies, procedures Configuration management and control Contingency planning Incident Response planning Security awareness and training Security in acquisition Physical security Personnel security Security assessments and authorization Continuous Monitoring • • • Access control mechanisms Identification & authentication mechanisms (Biometrics, tokens, passwords) Audit mechanisms Encryption mechanisms Boundary and network protection devices (Firewalls, guards, routers, gateways) Intrusion protection/detection systems Security configuration settings Anti-viral, anti-spyware, anti-spam software Smart cards Adversaries attack the weakest link…where is ours? Source: NIST, Ron Ross

Cyber Security Transformation Your Role in the Transformation: • Protect Yourself and the NASA IT infrastructure including mobile devices • Be Aware • Guard your personal data • Think before you click
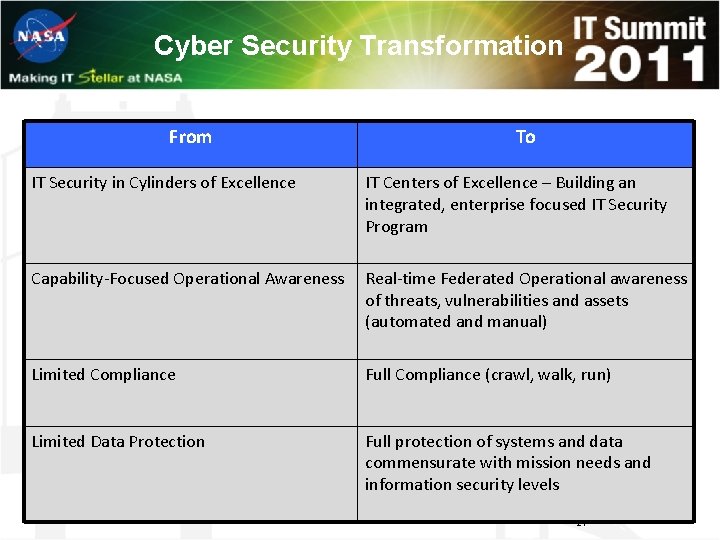
Cyber Security Transformation From To IT Security in Cylinders of Excellence IT Centers of Excellence – Building an integrated, enterprise focused IT Security Program Capability-Focused Operational Awareness Real-time Federated Operational awareness of threats, vulnerabilities and assets (automated and manual) Limited Compliance Full Compliance (crawl, walk, run) Limited Data Protection Full protection of systems and data commensurate with mission needs and information security levels 21

Key Areas of Focus – Next Steps • Enterprise integration of IT Security Services – Breakdown Silos of Excellence • Outreach/Communication with Internal and External Partners • Enterprise Risk Assessment and Management • Reconciliation and Mitigation of Audit Findings/Recommendations • Establish Portfolio of NASA’s IT Security Functions and Services • Establish Pro-active defensive security posture • FISMA/DHS – Cyber. Stat and Cyber. Scope • Enterprise Architecture – IT Security Continuous Monitoring • Staff and Capabilities to Support NASA’s IT Security Program • Sensitive but Unclassified information (SBU) / Controlled Unclassified Information (CUI) 22

Questions 23
- Slides: 23