SSH Keystroke Timing Attacks Mike Hogye Thad Hughes










- Slides: 19

SSH Keystroke Timing Attacks Mike Hogye Thad Hughes Josh Sarfaty Joe Wolf


SSH The Secure SHell protocol was created by Tatu Ylönen and others to provide encrypted data transfers between remote machines Mmmm… SSH

SSH Weaknesses ÌSSH can leak information about passwords µApproximate length of password can be inferred by examining number of packets. µKeystroke Timing Analysis can reduce the search space for brute force attacks.

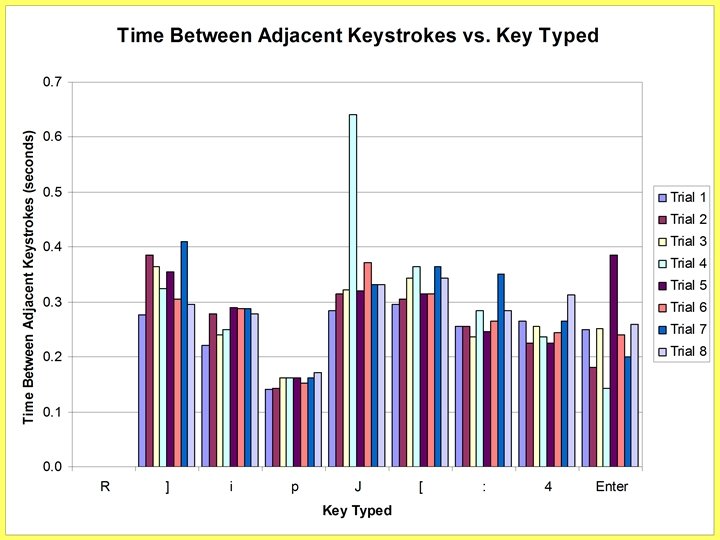
Password Keystroke Timing • Users type passwords often • Password keystrokes develop consistent rhythm due to optimized hand motion • This rhythm can be used to determine characteristics about the password



SSH Immediate Mode • Each keystroke is sent IMMEDIATELY from client to server, one character packet • Allows interactive user experience

Passwords & SSH • SSH login does NOT used immediate mode • Password (and username) packets are padded to fixed lengths • No problems, right? WRONG !! Maybe?

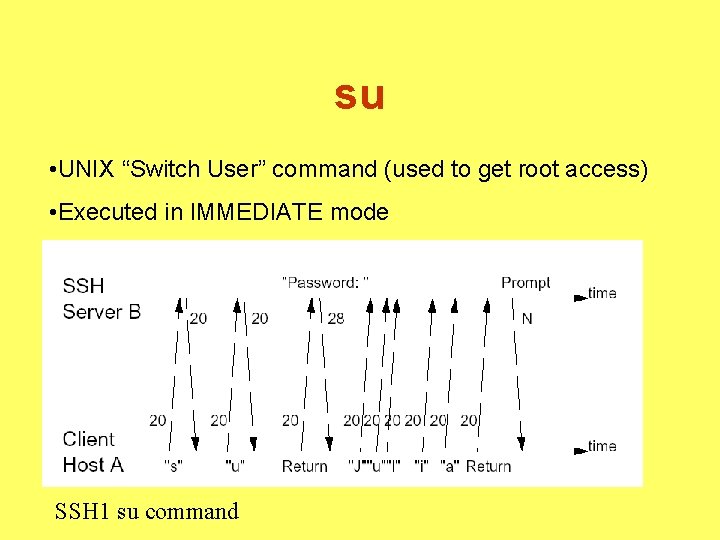
su • UNIX “Switch User” command (used to get root access) • Executed in IMMEDIATE mode SSH 1 su command

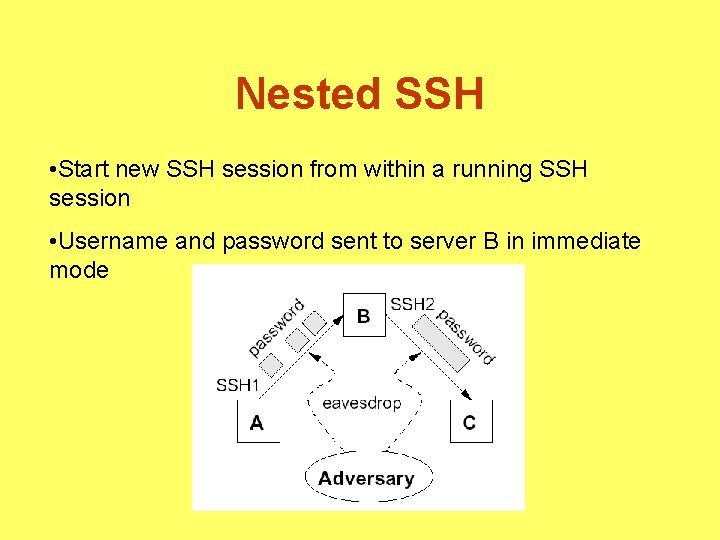
Nested SSH • Start new SSH session from within a running SSH session • Username and password sent to server B in immediate mode

So What? • Password lengths can be determined • Reveals timing information of password keystrokes • Academically speaking, this is a lot of information

Is This Practical? • How to detect an “su” command? • How to detect a nested SSH session? • Network latency

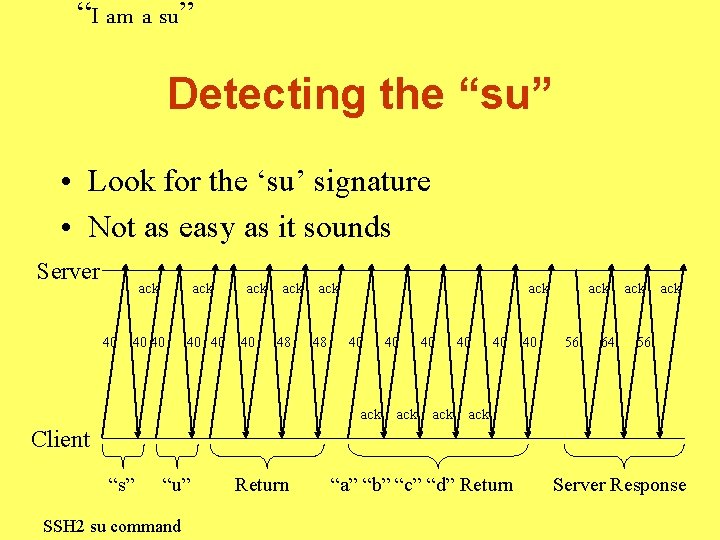
“I am a su” Detecting the “su” • Look for the ‘su’ signature • Not as easy as it sounds Server 40 ack 40 ack 48 ack 40 40 40 ack 56 64 ack 56 ack Client “s” “u” SSH 2 su command Return “a” “b” “c” “d” Return Server Response

SSH! (nested) • Theoretically similar to detecting ‘su’ • In practice, much harder to detect • No definite packet signature for calling ‘ssh’

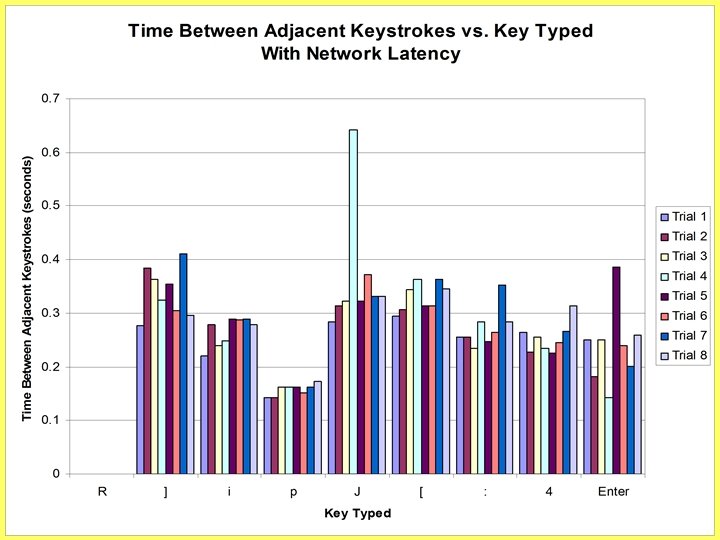
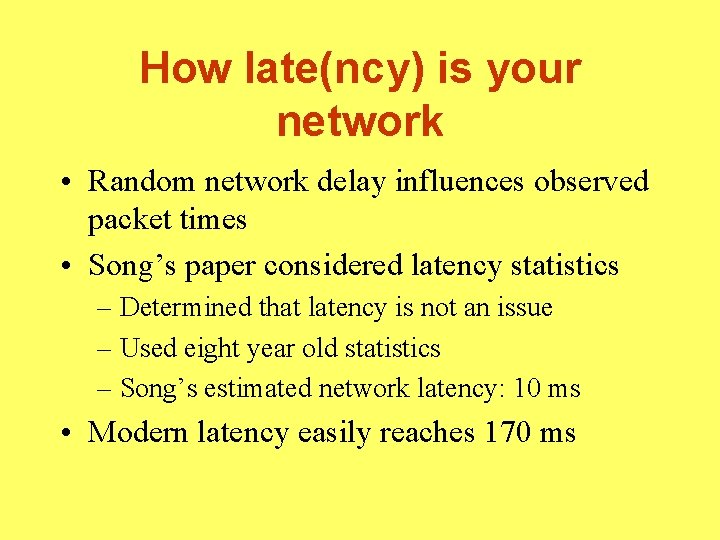
How late(ncy) is your network • Random network delay influences observed packet times • Song’s paper considered latency statistics – Determined that latency is not an issue – Used eight year old statistics – Song’s estimated network latency: 10 ms • Modern latency easily reaches 170 ms

Internet Latency

Conclusions • Song: Timing analysis can reduce bruteforce password search by a factor of 50 • In practice, this is unlikely • Use SSH 2 – Pu. TTY defaults to SSH 1
