SQL Injection NEITHNET Pank SQL Injection 20SQL Injection

















- Slides: 24

資安教室: SQL Injection NEITHNET騰曜網路科技 Pank

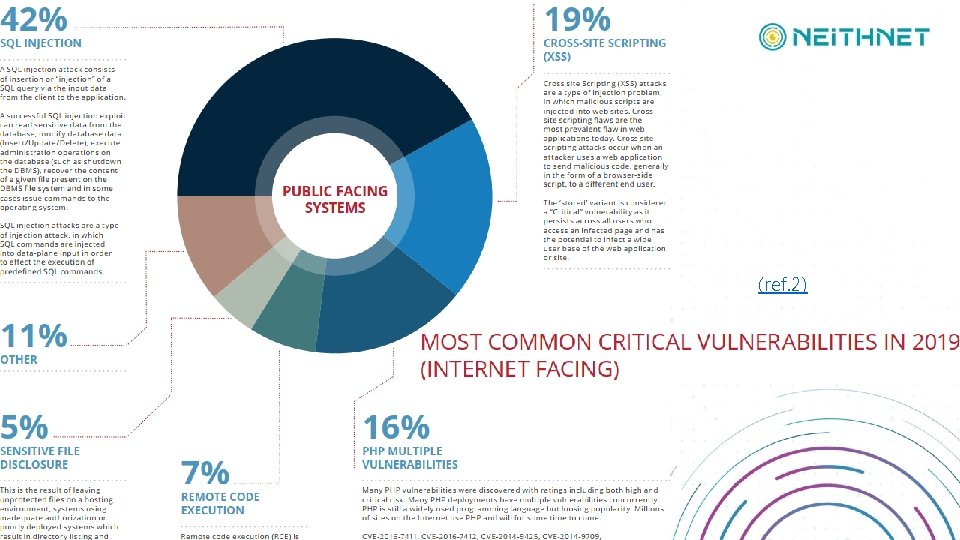
不老傳奇 SQL Injection • 20幾年過去,SQL Injection 仍然健在 • SQL Injection was first discovered in 1998 and still live • SQL Injection 攻擊佔了所有 Web 攻擊的 2/3 • SQL Injection Attacks Represent Two-Third of All Web App Attacks (ref. 1)

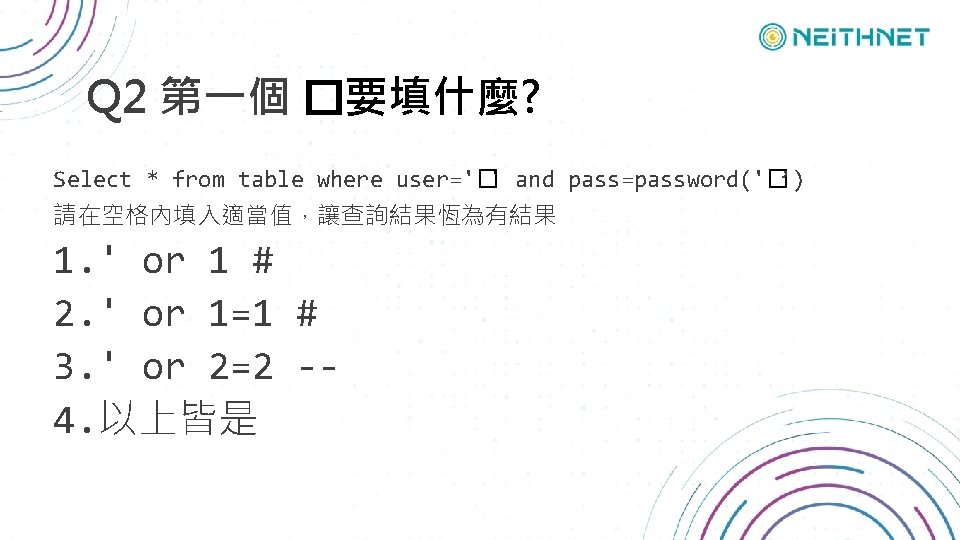
Q 1 那一項公開網站資安弱點佔比最高? 1. 2. 3. 4. SQL Injection XSS PHP multiple vulnerabilities Remote code execution

(ref. 2)

SQL Injection 仍然是Web弱點之王 • SQL Injection 在網際網路公開網站弱點佔比 42% • MOST COMMON CRITICAL VULNERABILITIES IN 2019 (INTERNET FACING) (ref. 2)



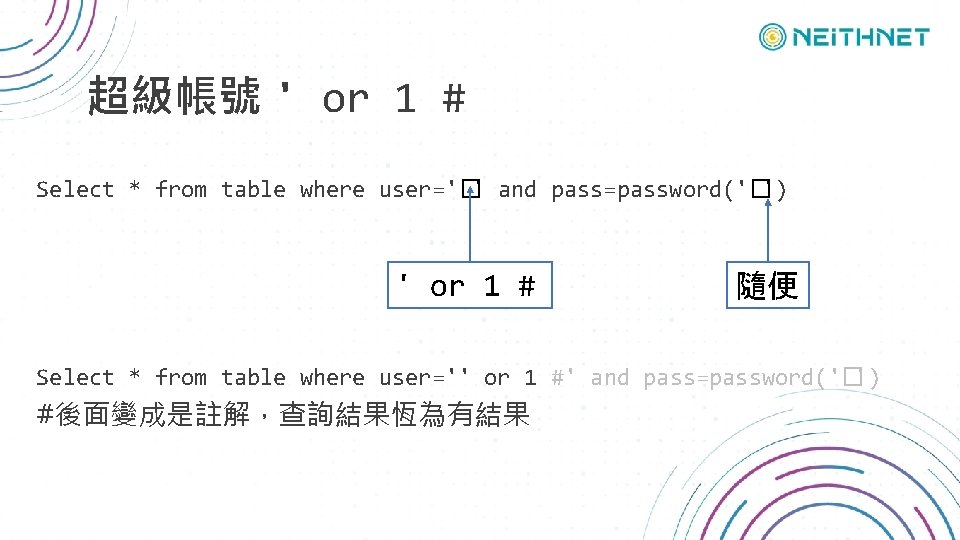
超級帳號 ' or 1 # Select * from table where user='�' and pass=password('�') ' or 1 # 隨便 Select * from table where user='' or 1 #' and pass=password('�') #後面變成是註解,查詢結果恆為有結果




Prepare/Execute Statement • Prepare Statement 準備語法 • $st=$dbh->prepare("select * from contact where user=: user_value and pass=password(: pass_value)"); • Execute Statement 執行語法,帶入變數 • $st->execute(array('user_value'=>'user 1', 'pass_value'=>'Hello@12345')); • 變數中帶進來的任何東西,都是值,沒有機會變成 SQL 語法


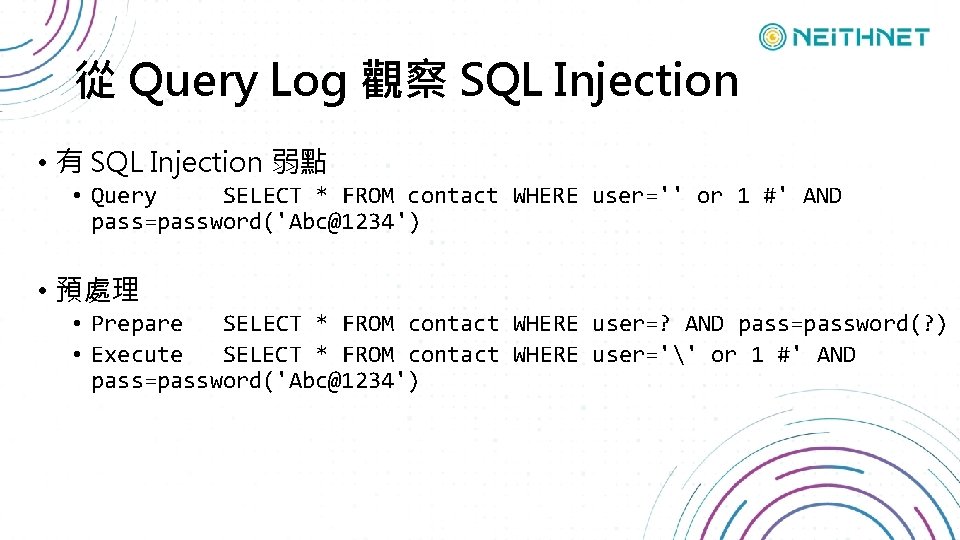
從 Query Log 觀察 SQL Injection • 有 SQL Injection 弱點 • Query SELECT * FROM contact WHERE user='' or 1 #' AND pass=password('Abc@1234') • 預處理 • Prepare SELECT * FROM contact WHERE user=? AND pass=password(? ) • Execute SELECT * FROM contact WHERE user='' or 1 #' AND pass=password('Abc@1234')

PHP PDO: : ATTR_EMULATE_PREPARES • PHP 的 PDO: : ATTR_EMULATE_PREPARES 預設開啟,它用模擬的方 式來處理 Prepare Statement,實際上還是使用一個 Query (如下), 但它算是安全的,因為它會 Escape 代入的變數 • Query select * from contact where user='' or 1 #' and pass=password('Abc@1234')

Live Demo https: //sqlinjection. cf 正常登入帳號 admin 1 ~ admin 5 user 1 ~ user 5 密碼均為 Hello@1234 Demo Site 預計下架時間 2021 -5 -31

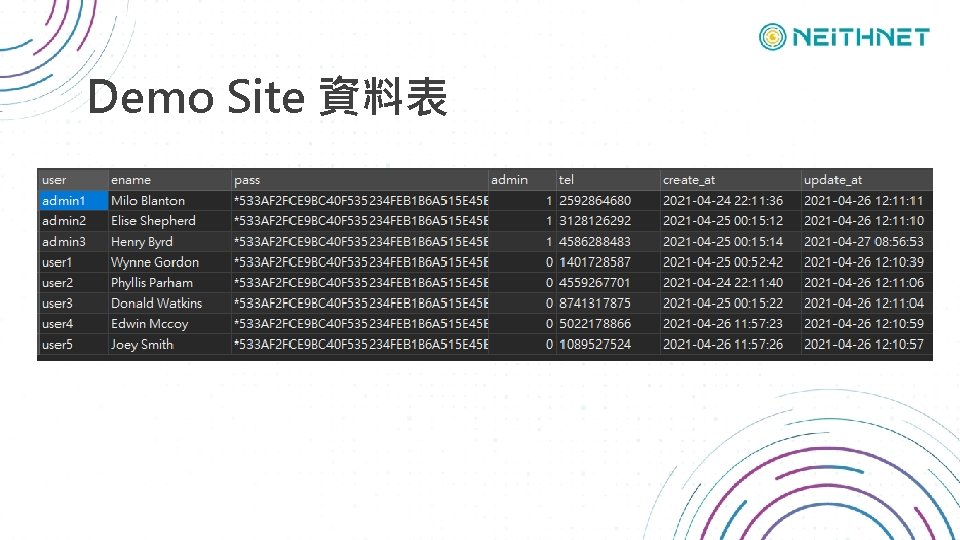
Demo Site 資料表

Demo Site 語法 登入驗證語法,有結果算是通過 $result = mysqli_query($con, "SELECT * FROM contact WHERE user='$username' AND pass=password('$password')"); 透過 Injection,可以達到登入 bypass 內頁搜尋語法,只能搜尋到 user 帳號 (admin=0) $result = mysqli_query($con, "SELECT * FROM contact WHERE (user LIKE '%$keyword%' OR ename LIKE '%$keyword%' OR tel LIKE '%$keyword%') and admin=0 ORDER BY user"); 透過 Injection,可以提升權限,撈到所有帳號資料

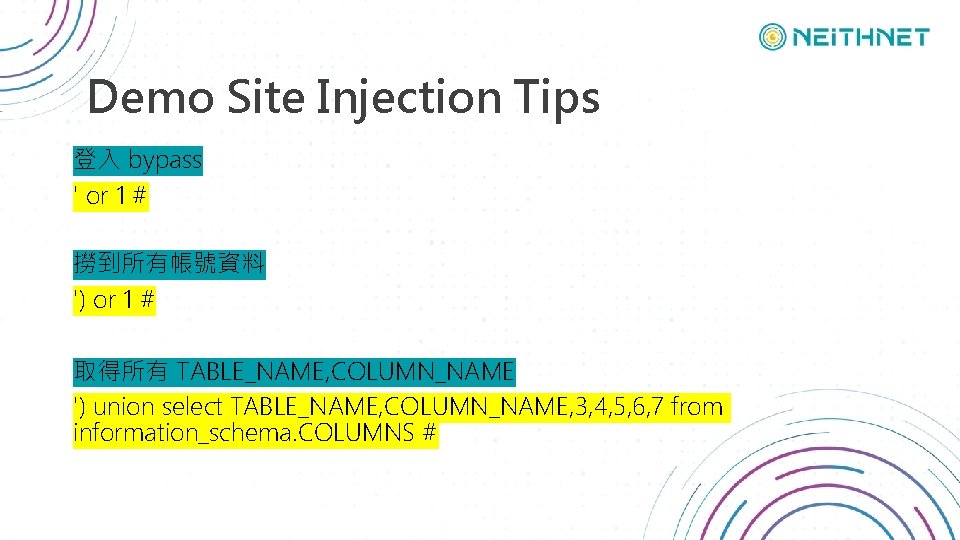
Demo Site Injection Tips 登入 bypass ' or 1 # 撈到所有帳號資料 ') or 1 # 取得所有 TABLE_NAME, COLUMN_NAME ') union select TABLE_NAME, COLUMN_NAME, 3, 4, 5, 6, 7 from information_schema. COLUMNS #




Reference 1. https: //www. darkreading. com/attacks-breaches/sql-injection-attacks-represent-two-third-of-all-web-appattacks/d/d-id/1334960 2. https: //cdn 2. hubspot. net/hubfs/4118561/BCC 030%20 Vulnerability%20 Stats%20 Report%20(2020)_WEB. pdf 3. https: //sucuri. net/guides/what-is-sql-injection/ 4. https: //www. youtube. com/watch? v=Og. Gnihq. Ehjk

感謝聆聽 網路威脅問題,請找NEITHNET info@neithnet. com