SQL injection Figure 1 By Kaveri Bhasin Motive

SQL injection Figure 1 By Kaveri Bhasin
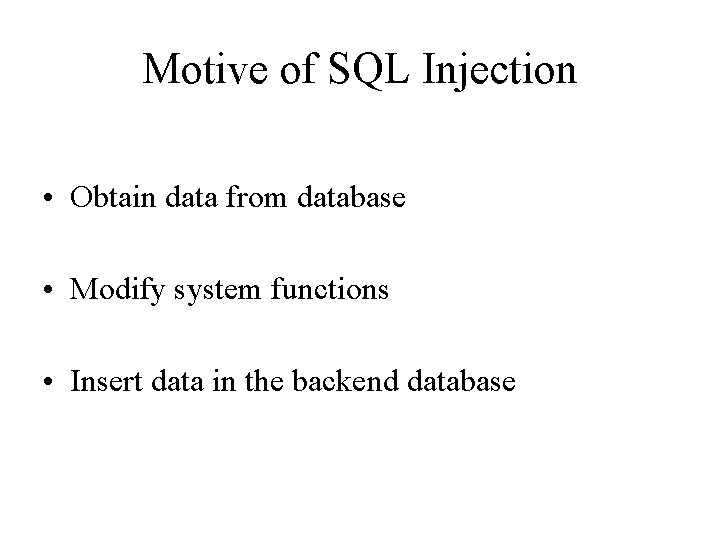
Motive of SQL Injection • Obtain data from database • Modify system functions • Insert data in the backend database
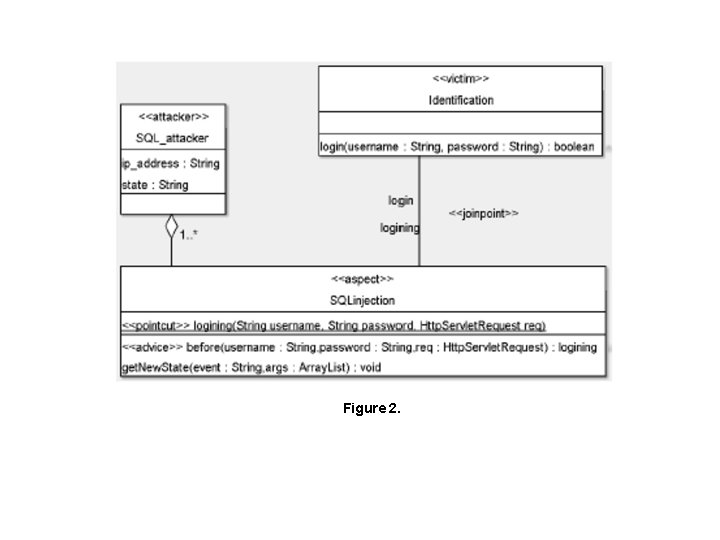
Figure 2.
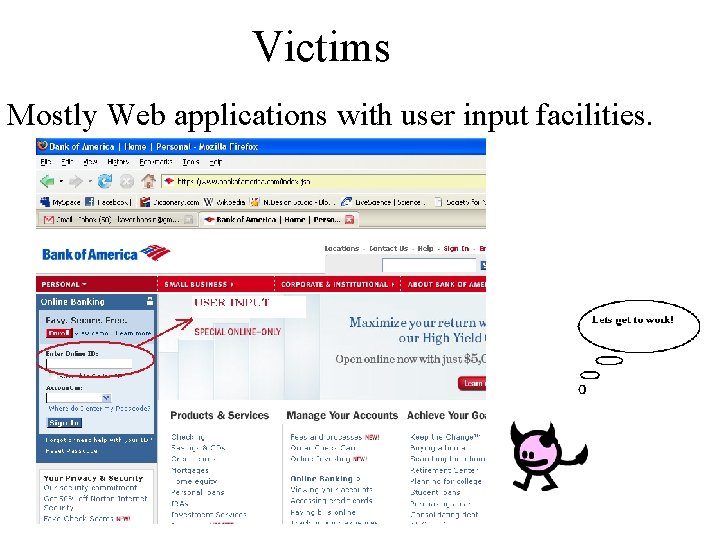
Victims Mostly Web applications with user input facilities.
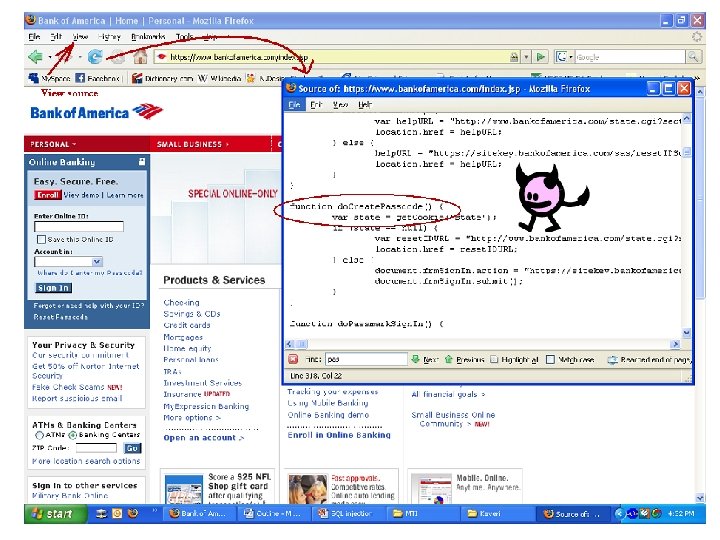
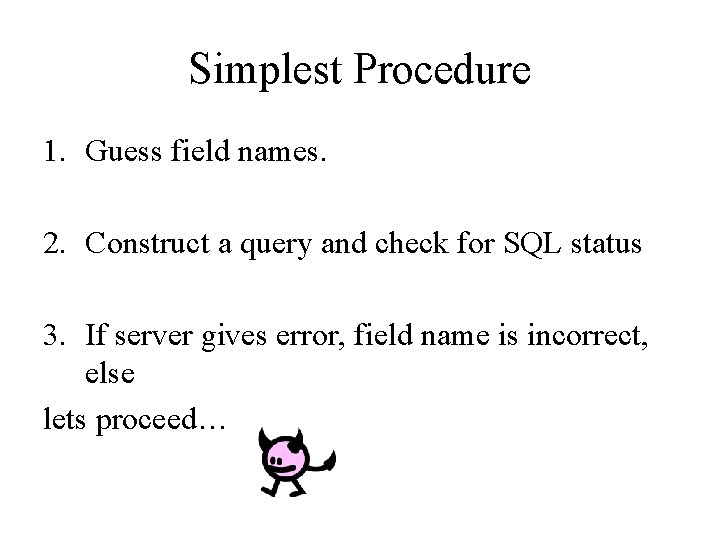
Simplest Procedure 1. Guess field names. 2. Construct a query and check for SQL status 3. If server gives error, field name is incorrect, else lets proceed…

Cont. • With the correct field, construct SQL query and inject Example: 101 AND Len(( SELECT first_name FROM user_data WHERE userid =15613)) = 6

Paper overview • Types of Vulnerabilities • Measures • Tools (Webgoat)
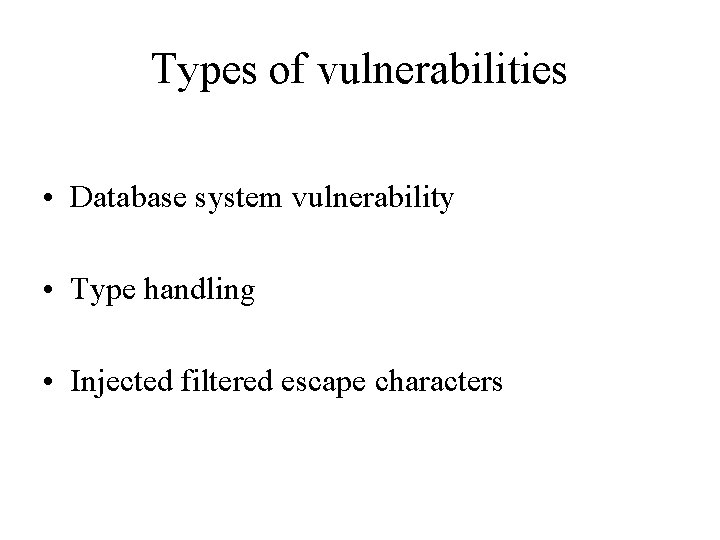
Types of vulnerabilities • Database system vulnerability • Type handling • Injected filtered escape characters
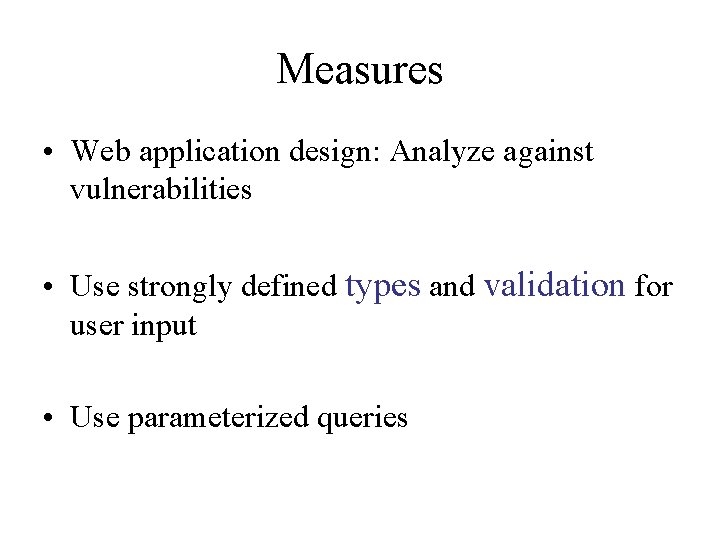
Measures • Web application design: Analyze against vulnerabilities • Use strongly defined types and validation for user input • Use parameterized queries

Tools • Webgoat Developed by OWASP. org Free source to experiment and learnt about SQL injection

Conclusion SQL injection is a serious concern A single design error can be disastrous for the security of sensitive information
References • Figure 1. http: //ocliteracy. com/techtips/sql-injection. html • Figure 2. “Towards an Aspect-Oriented Intrusion Detection Framework” • Zhi Jian Zhu and Mohammad Zulkernine • http: //www. owasp. org/ • http: //www. spidynamics. com/papers/SQLInjection. White. Paper. pdf
- Slides: 13