Spring 2006 CS 155 Final Review Session Collin


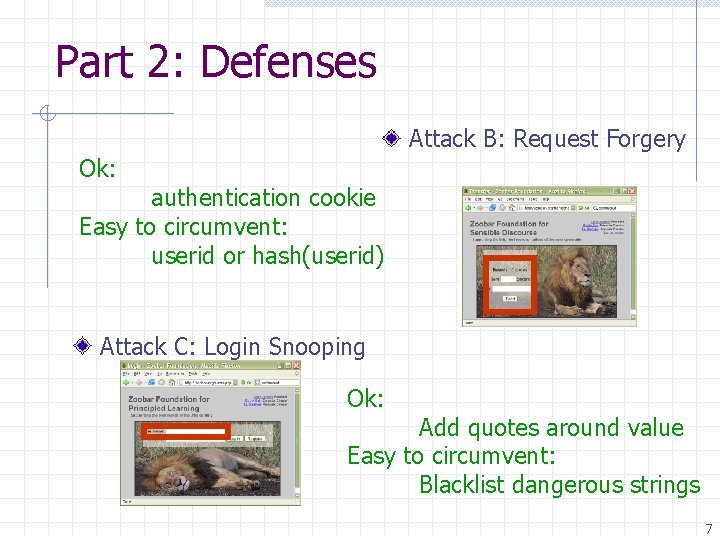



![SQL Syntax Four basic commands (plus many others) n n INSERT INTO [table] ([column], SQL Syntax Four basic commands (plus many others) n n INSERT INTO [table] ([column],](https://slidetodoc.com/presentation_image_h/28fcbcfb8d57a7ce3300dcb1dffbf5ca/image-11.jpg)
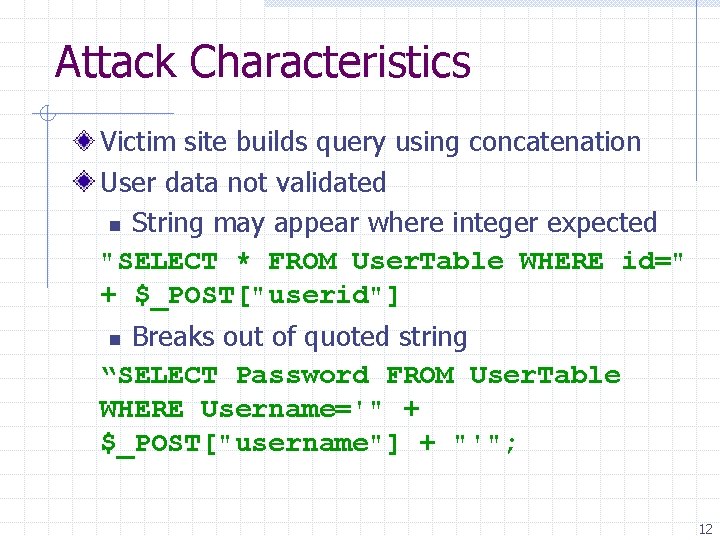







![TPM Functions Updating PCR n TPM_Extend(n, D): PCR[n] SHA-1 ( PCR[n] || D ) TPM Functions Updating PCR n TPM_Extend(n, D): PCR[n] SHA-1 ( PCR[n] || D )](https://slidetodoc.com/presentation_image_h/28fcbcfb8d57a7ce3300dcb1dffbf5ca/image-31.jpg)




- Slides: 38

Spring 2006 CS 155 Final Review Session Collin Jackson 1

Final Details Open book, open notes, closed laptop Main final (recommended) n 7 -10 PM on Tuesday, June 13 n Gates B 01 Alternate final n 3: 30 -6: 30 PM on Monday, June 12 n Gates B 03 Study suggestions: n Previous finals available on course webpage n Reading, slides, lectures, homework n Email cs 155 ta@cs. stanford. edu with questions 2

Some Topics Project 2 recap SQL injection Access control TPM 3

Project 2 Recap w Part 1 w Part 2 w Grading 4

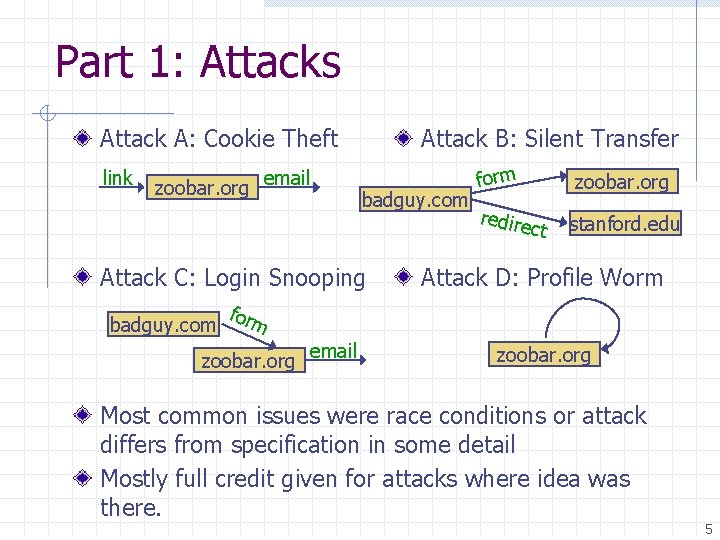
Part 1: Attacks Attack A: Cookie Theft link zoobar. org email Attack B: Silent Transfer badguy. com Attack C: Login Snooping badguy. com form redire zoobar. org ct stanford. edu Attack D: Profile Worm form zoobar. org email zoobar. org Most common issues were race conditions or attack differs from specification in some detail Mostly full credit given for attacks where idea was there. 5

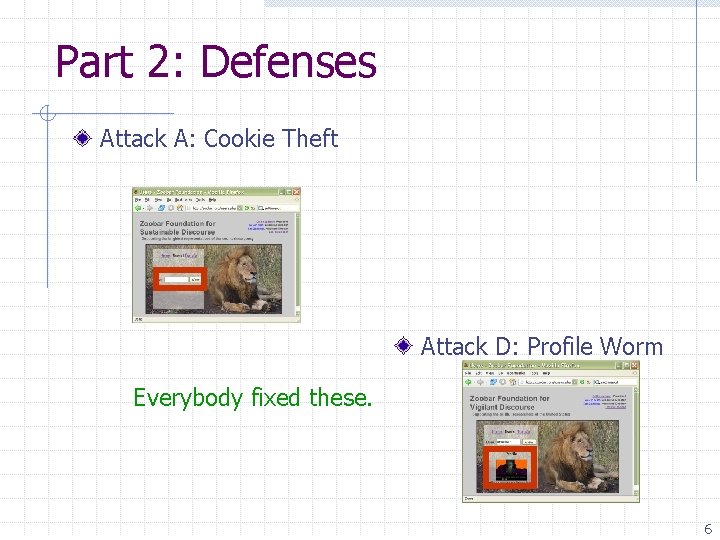
Part 2: Defenses Attack A: Cookie Theft Attack D: Profile Worm Everybody fixed these. 6

Part 2: Defenses Attack B: Request Forgery Ok: authentication cookie Easy to circumvent: userid or hash(userid) Attack C: Login Snooping Ok: Add quotes around value Easy to circumvent: Blacklist dangerous strings 7

Part 2: More XSS Tests index. php n Profile </textarea><script>…</script> n Exploitable? Depends on (optional) login CSRF defense users. php n Profile <img onload=…> n User </script><script>…<script> transfer. php n Recipient <script>…</script> n Exploitable? Depends on transfer CSRF defense 8

Part 2: Grading Key ideas: n Preferred approach is escaping n Alternate approach is whitelisting n Blacklisting is easy to get wrong Grades released sometime this weekend If you feel your project was misgraded n Contact TAs n Reserve right to regrade entire project 9

SQL Injection w Problem Overview w Good defenses w Bad defenses 10
![SQL Syntax Four basic commands plus many others n n INSERT INTO table column SQL Syntax Four basic commands (plus many others) n n INSERT INTO [table] ([column],](https://slidetodoc.com/presentation_image_h/28fcbcfb8d57a7ce3300dcb1dffbf5ca/image-11.jpg)
SQL Syntax Four basic commands (plus many others) n n INSERT INTO [table] ([column], …) VALUES ([value], …) SELECT [column], … FROM [table] WHERE [condition] UPDATE [table] SET [column]=[value], … WHERE [condition] DELETE FROM [table] WHERE [condition] Strings delimited with ' Statements separated with ; Comments start with -11

Attack Characteristics Victim site builds query using concatenation User data not validated n String may appear where integer expected "SELECT * FROM User. Table WHERE id=" + $_POST["userid"] Breaks out of quoted string “SELECT Password FROM User. Table WHERE Username='" + $_POST["username"] + "'"; n 12

Crafting an attack Spider site and look for input fields Put ' in each field and look for errors Try to determine the structure of the query n Guess and observe results n Error messages can be helpful Construct malicious attack query, e. g. n Return sensitive data from other rows or tables n Modify passwords file to give attacker access 13

Example Question Site form allows lookup by integer id: <input name=id><input type=submit> Fix this query: "SELECT * FROM User. Table WHERE id=“ + Request["id"]; Best: Parameterized SQL cmd. Command. Text = "SELECT * FROM User. Table WHERE id=@id"; cmd. Parameters. Add("@id", Request["id"]); cmd. Execute. Reader(); Okay: Escaping functions provided by language n Must always use right one, compose in right order Okay: Casting to numerical data type 14

Bad Defense: Manual Blacklist Check input for dangerous characters n Replace with harmless equivalents, or n Die without executing query Hard to get right n Easy to forget unusual corner cases n Alternate character encodings Escape handling may depend on db server software n May not match developer expectation n If server software changes, code is vulnerable 15

Bad Defense: Authentication Developer says: “Only administrators can view the vulnerable page and the admin already has full database access. Therefore, SQL injection is not a problem. ” Is this exploitable? Problem: Malicious content elsewhere can exploit site’s trust in the user to allow access to vulnerable page <img src="/admin/lookupuser. php? id='; UPDATE Person SET Password='x' WHERE username='admin"> 16

Access Control w w ACL version CL Bell-La Padula Biba Set. UID 17

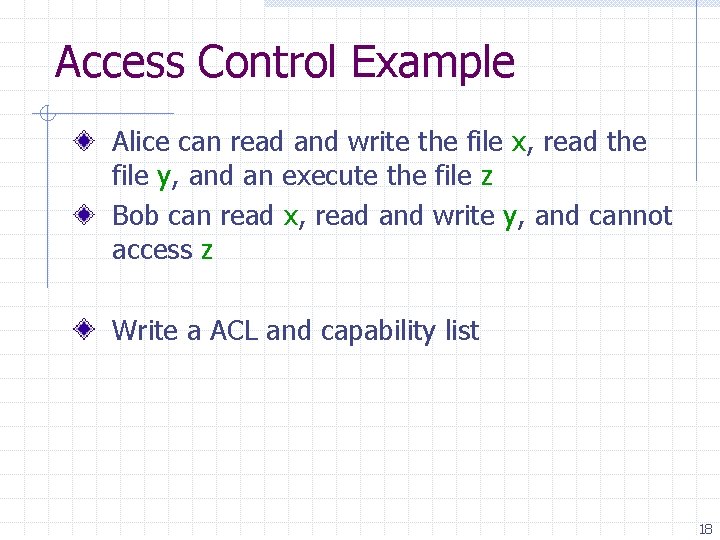
Access Control Example Alice can read and write the file x, read the file y, and an execute the file z Bob can read x, read and write y, and cannot access z Write a ACL and capability list 18

ACL File x n Alice: read, write n Bob: read File y n Alice: read n Bob: read, write File z n Alice: execute 19

Capability list Alice: n File Bob: n File x: read, write y: read z: execute x: read y: read, write 20

Comparison Q: Which access control mechanism is better at containing a Trojan horse virus? Capability model allows capability owner to reduce capability inherited by process Trojan horse process can be run without write access to file y (for example) Can this stop all Trojans? 21

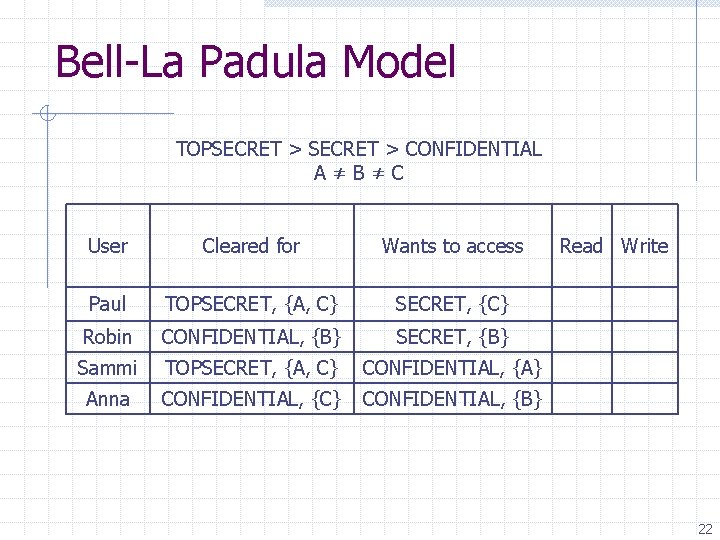
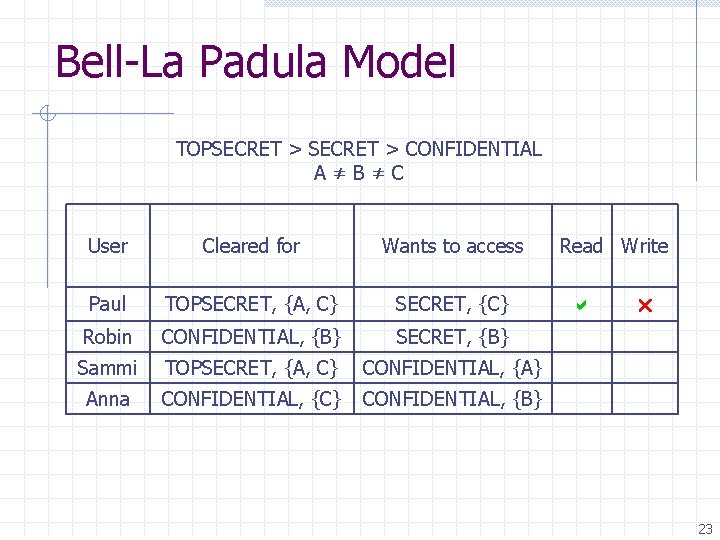
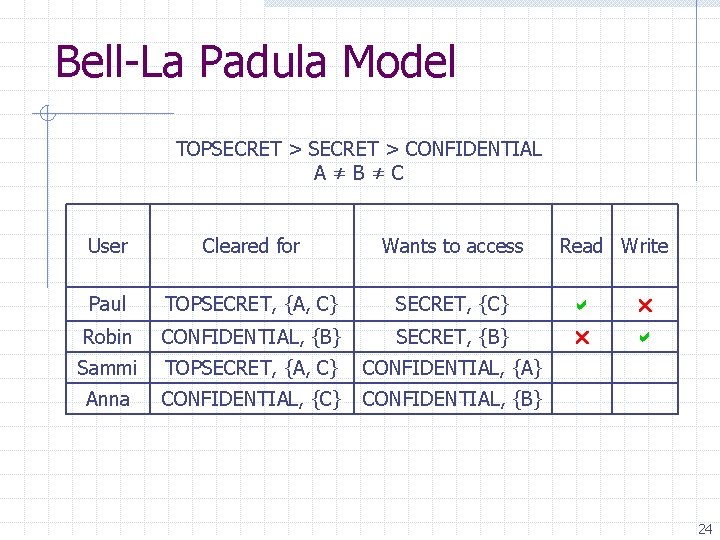
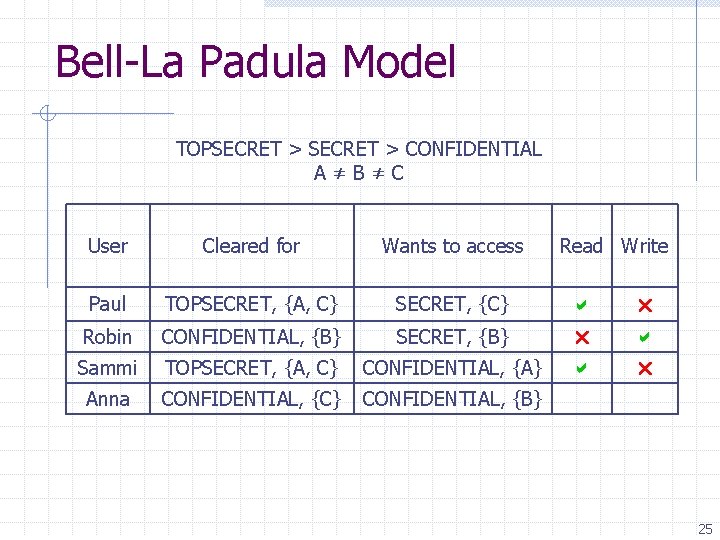
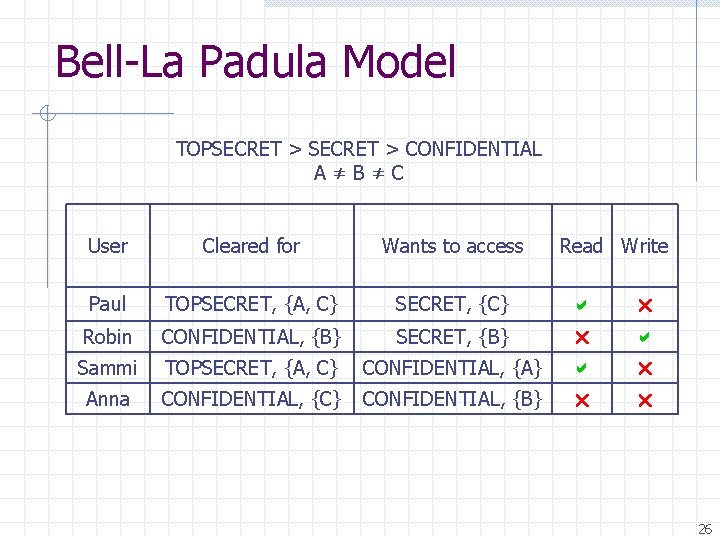
Bell-La Padula Model TOPSECRET > CONFIDENTIAL A≠B≠C User Cleared for Wants to access Paul TOPSECRET, {A, C} SECRET, {C} Robin CONFIDENTIAL, {B} SECRET, {B} Sammi TOPSECRET, {A, C} CONFIDENTIAL, {A} Anna CONFIDENTIAL, {C} CONFIDENTIAL, {B} Read Write 22

Bell-La Padula Model TOPSECRET > CONFIDENTIAL A≠B≠C User Cleared for Wants to access Paul TOPSECRET, {A, C} SECRET, {C} Robin CONFIDENTIAL, {B} SECRET, {B} Sammi TOPSECRET, {A, C} CONFIDENTIAL, {A} Anna CONFIDENTIAL, {C} CONFIDENTIAL, {B} Read Write 23

Bell-La Padula Model TOPSECRET > CONFIDENTIAL A≠B≠C User Cleared for Wants to access Read Write Paul TOPSECRET, {A, C} SECRET, {C} Robin CONFIDENTIAL, {B} SECRET, {B} Sammi TOPSECRET, {A, C} CONFIDENTIAL, {A} Anna CONFIDENTIAL, {C} CONFIDENTIAL, {B} 24

Bell-La Padula Model TOPSECRET > CONFIDENTIAL A≠B≠C User Cleared for Wants to access Read Write Paul TOPSECRET, {A, C} SECRET, {C} Robin CONFIDENTIAL, {B} SECRET, {B} Sammi TOPSECRET, {A, C} CONFIDENTIAL, {A} Anna CONFIDENTIAL, {C} CONFIDENTIAL, {B} 25

Bell-La Padula Model TOPSECRET > CONFIDENTIAL A≠B≠C User Cleared for Wants to access Read Write Paul TOPSECRET, {A, C} SECRET, {C} Robin CONFIDENTIAL, {B} SECRET, {B} Sammi TOPSECRET, {A, C} CONFIDENTIAL, {A} Anna CONFIDENTIAL, {C} CONFIDENTIAL, {B} 26

Biba Policy How would a virus spread if: n The virus were places in the system at system low (the compartment which all other compartments dominate) Could only infect lowest compartment n The virus were places in the system at system high (the compartment which dominates all other compartments) Could infect all other compartments 27

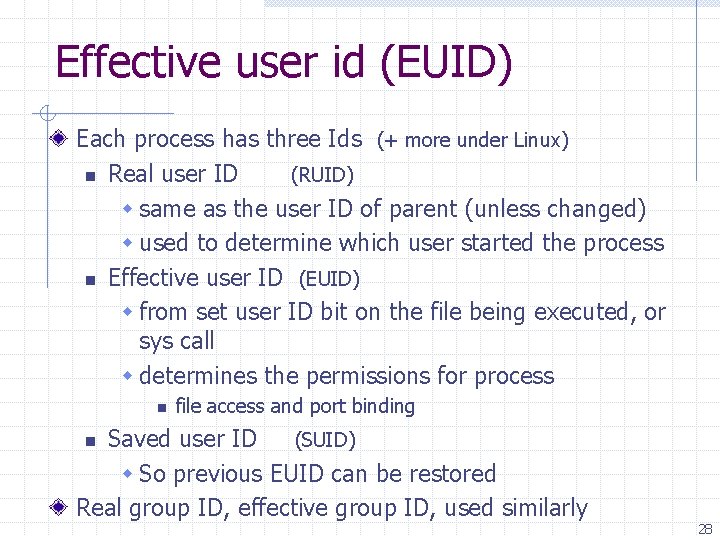
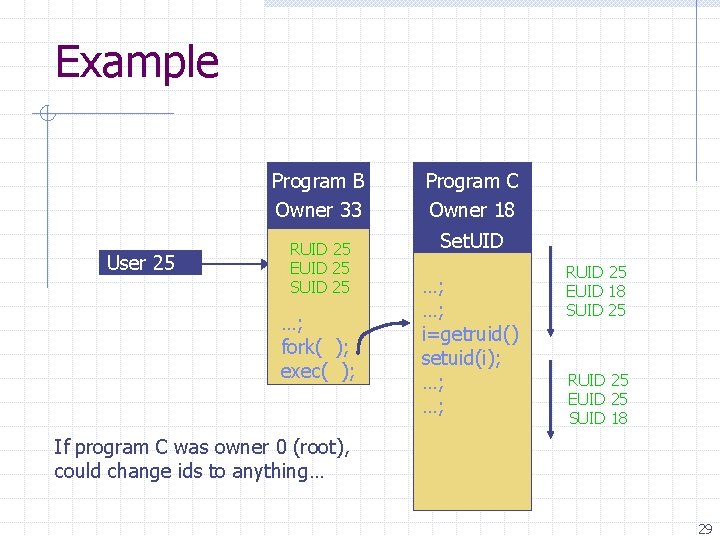
Effective user id (EUID) Each process has three Ids (+ more under Linux) n Real user ID (RUID) w same as the user ID of parent (unless changed) w used to determine which user started the process n Effective user ID (EUID) w from set user ID bit on the file being executed, or sys call w determines the permissions for process n file access and port binding Saved user ID (SUID) w So previous EUID can be restored Real group ID, effective group ID, used similarly n 28

Example Program B Owner 33 User 25 RUID 25 EUID 25 SUID 25 …; fork( ); exec( ); Program C Owner 18 Set. UID …; …; i=getruid() setuid(i); …; …; RUID 25 EUID 18 SUID 25 RUID 25 EUID 25 SUID 18 If program C was owner 0 (root), could change ids to anything… 29

TPM w Functions w Keys 30
![TPM Functions Updating PCR n TPMExtendn D PCRn SHA1 PCRn D TPM Functions Updating PCR n TPM_Extend(n, D): PCR[n] SHA-1 ( PCR[n] || D )](https://slidetodoc.com/presentation_image_h/28fcbcfb8d57a7ce3300dcb1dffbf5ca/image-31.jpg)
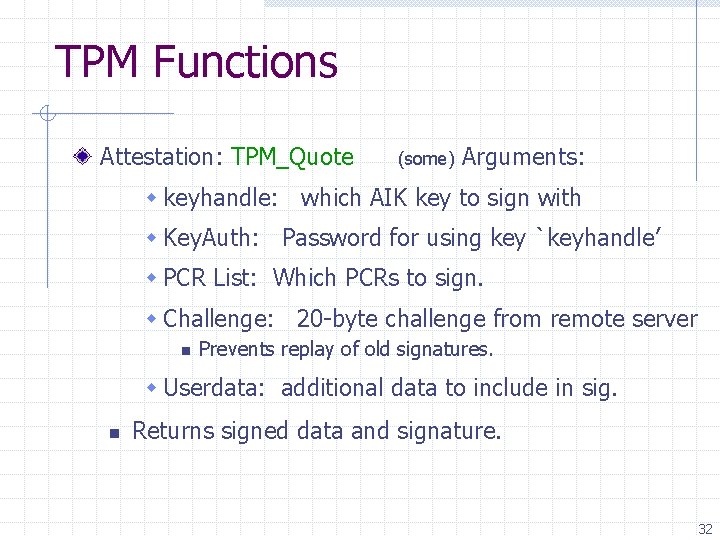
TPM Functions Updating PCR n TPM_Extend(n, D): PCR[n] SHA-1 ( PCR[n] || D ) TPM_Pcr. Read(n): returns value(PCR(n)) n TPM_Save. State and TPM_Startup(ST_STATE) Encrypted storage n TPM_Take. Ownership( Owner. Password, … ) n TPM_Create. Wrap. Key n n TPM_Seal(keyhandle, Key. Auth, Pcr. Values, data) n TPM_Unseal only when PCR matches blob PCR 31

TPM Functions Attestation: TPM_Quote (some) Arguments: w keyhandle: which AIK key to sign with w Key. Auth: Password for using key `keyhandle’ w PCR List: Which PCRs to sign. w Challenge: 20 -byte challenge from remote server n Prevents replay of old signatures. w Userdata: additional data to include in sig. n Returns signed data and signature. 32

TPM Keys Data encrypted by TPM_Seal (usually AES key) n Only key not hidden inside TPM Storage Root Key (SRK): certifies wrap keys n Created by TPM_Take. Ownership Wrap keys: encrypts data with TPM_Seal n Created by TPM_Create. Wrap. Key Attestation Identity Key (AIK) for use with TPM_Quote n Creation details “not important” Endorsement key (EK) for endorsing AIK n Certificate issued once for TPM by vendor 33

34

Malware w Example question 35

Example Question The Earlybird worm signature generation system only finds worm signatures that consist of a consecutive sequence of characters. Give an example of a vulnerability that a worm can exploit that cannot be detected using such signatures. 36

Follow up Suppose Earlybird was able to generate signatures that contain wild cards (for example, "script/*. cgi"). Give an example of a vulnerability that a worm can exploit that cannot be detected using such signatures. 37

38