Special Topic Wireless Security TWN First Generation AMPS










- Slides: 26

Special Topic: Wireless Security

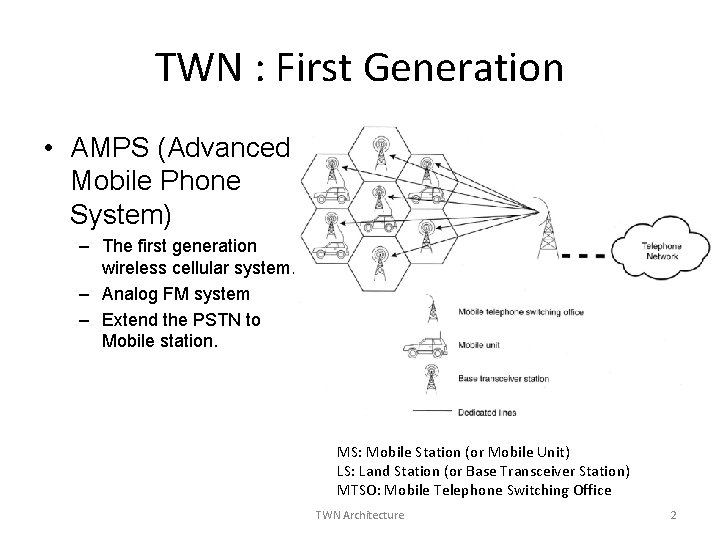
TWN : First Generation • AMPS (Advanced Mobile Phone System) – The first generation wireless cellular system. – Analog FM system – Extend the PSTN to Mobile station. MS: Mobile Station (or Mobile Unit) LS: Land Station (or Base Transceiver Station) MTSO: Mobile Telephone Switching Office TWN Architecture 2

Addresses in AMPS • Mobile Identification Number(MIN): 34 -bit (10 -digit) telephone number • Electronic Serial Number(ESN): 32 -bit number assigned by manufacturer, unique by mobile phone. • Station Class Mark(SCM): 4 -bit code in MS, capabilities in MS. • System Identifier (SID): 15 -bit code identify the service provider in a specific geographical area. Stored by each Land Station (LS). -> To determine if the LS is in its home network or is roaming. • Supervisory Audio Tone (SAT), Digital Color Code(DCC): distinguish between the various LSs of a service provider. Edward Jung TWN Architecture 3

TWNs: Second Generation • After the first generation, the following needs emerged: – Demand higher level of spectrum efficiency – More roaming services (example: traveling to a foreign network – your home is Germany, but traveling to Holland……. ) • GSM (Global Systems for Mobile-Communication) – Second generation cellular network standards in Europe. – “Digital” air interface. – Channel access: Frequency Division multiplexing (FDMA) + Time Division multiplexing (TDMA) • Logical channel: (Carrier Frequency , Time Slot) Edward Jung TWN Architecture 4

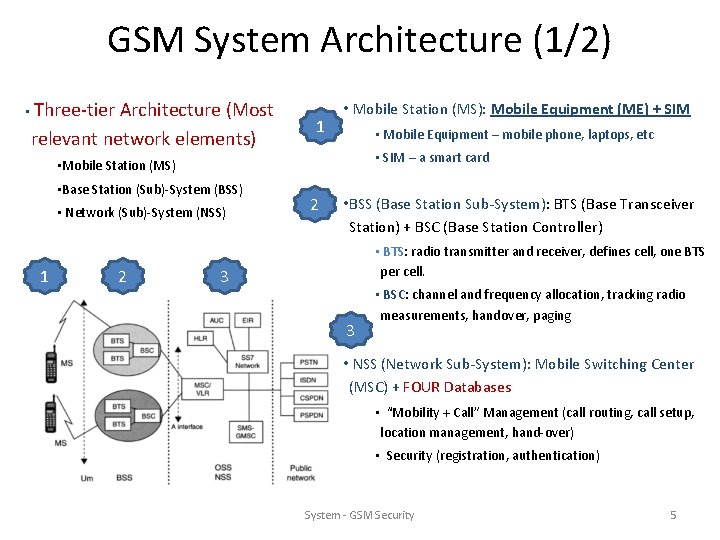
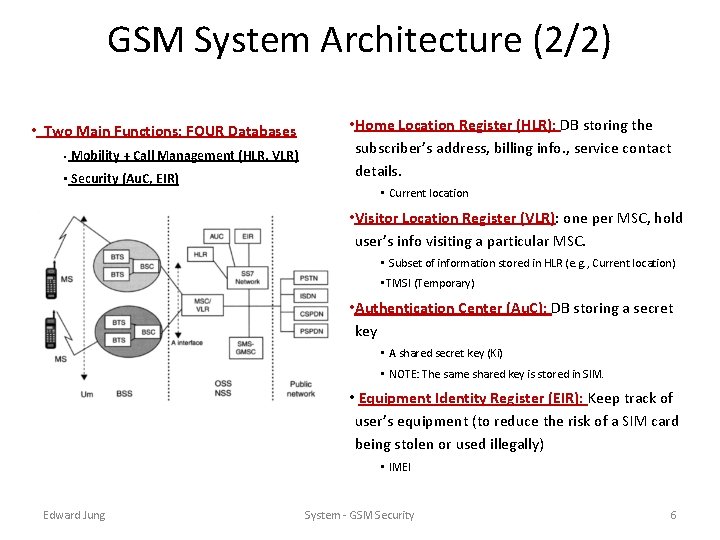
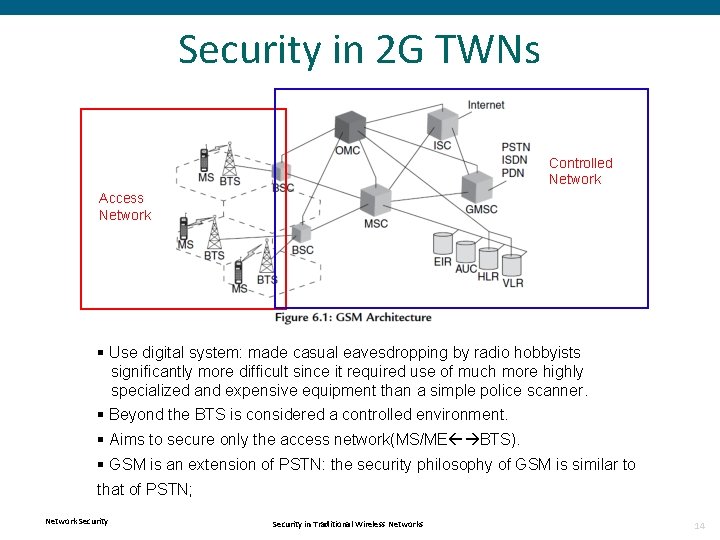
GSM System Architecture (1/2) • Three-tier Architecture (Most relevant network elements) 1 • Mobile Station (MS): Mobile Equipment (ME) + SIM • Mobile Equipment – mobile phone, laptops, etc • SIM – a smart card • Mobile Station (MS) • Base Station (Sub)-System (BSS) • Network (Sub)-System (NSS) 1 2 2 • BSS (Base Station Sub-System): BTS (Base Transceiver Station) + BSC (Base Station Controller) • BTS: radio transmitter and receiver, defines cell, one BTS per cell. 3 3 • BSC: channel and frequency allocation, tracking radio measurements, handover, paging • NSS (Network Sub-System): Mobile Switching Center (MSC) + FOUR Databases • “Mobility + Call” Management (call routing, call setup, location management, hand-over) • Security (registration, authentication) System - GSM Security 5

GSM System Architecture (2/2) • Two Main Functions: FOUR Databases • Mobility + Call Management (HLR, VLR) • Security (Au. C, EIR) • Home Location Register (HLR): DB storing the subscriber’s address, billing info. , service contact details. • Current location • Visitor Location Register (VLR): one per MSC, hold user’s info visiting a particular MSC. • Subset of information stored in HLR (e. g. , Current location) • TMSI (Temporary) • Authentication Center (Au. C): DB storing a secret key • A shared secret key (Ki) • NOTE: The same shared key is stored in SIM. • Equipment Identity Register (EIR): Keep track of user’s equipment (to reduce the risk of a SIM card being stolen or used illegally) • IMEI Edward Jung System - GSM Security 6

Addresses in GSM (1/2) • MSISDN (Mobile Subscriber Integrated Services Digital Network) – MS phone number, identity of the subscribe, stored in SIM. • IMSI (International Mobile Subscriber Identity) – Subscriber’s identity, stored in SIM. – Association of MSISDN and IMSI – stored in HLR, keeps in secret • SIM (Subscriber Identification Module) – Store MSSIDN, IMSI • IMEI (International Mobile-Station Equipment Identity) – Uniquely identifies the mobile equipment, allocated by the equipment manufacturer, stored in the EIR • TMSI (Temporary Mobile Subscriber Identity) – Assigned by VLR used in place of IMSI, restrict the transmission of IMSI over the air interfaces to protect IMSI. Edward Jung TWN Architecture 7

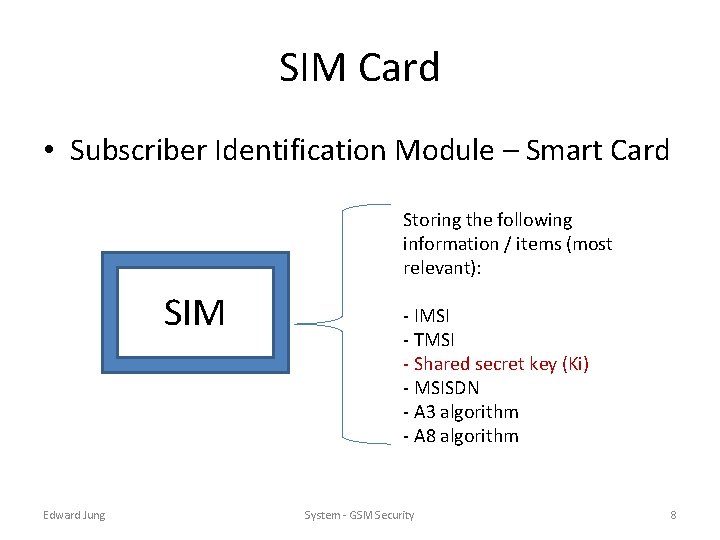
SIM Card • Subscriber Identification Module – Smart Card Storing the following information / items (most relevant): SIM Edward Jung - IMSI - TMSI - Shared secret key (Ki) - MSISDN - A 3 algorithm - A 8 algorithm System - GSM Security 8

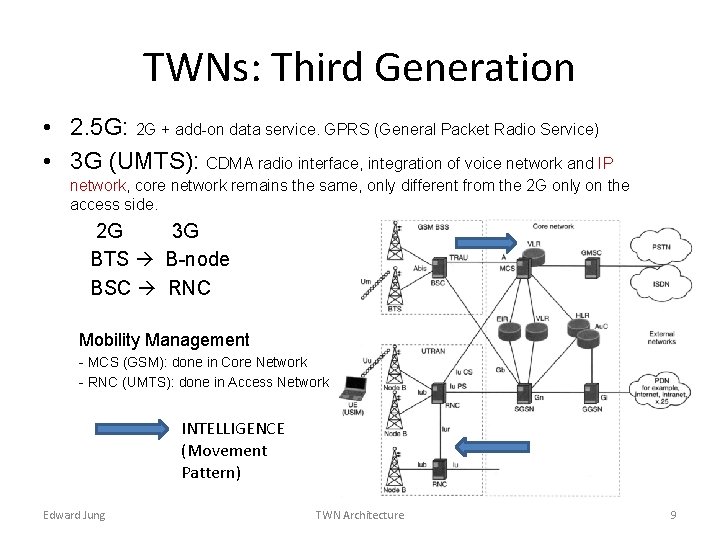
TWNs: Third Generation • 2. 5 G: 2 G + add-on data service. GPRS (General Packet Radio Service) • 3 G (UMTS): CDMA radio interface, integration of voice network and IP network, core network remains the same, only different from the 2 G only on the access side. 2 G 3 G BTS B-node BSC RNC Mobility Management - MCS (GSM): done in Core Network - RNC (UMTS): done in Access Network INTELLIGENCE (Movement Pattern) Edward Jung TWN Architecture 9

Security in 1 G TWNs Network Security in Traditional Wireless Networks 10

Security in 1 G TWNs • To the designer, they had too many other problems before security became a priority. • Since AMPS radio interface was analog and AMPS used no encryption. Network Security in Traditional Wireless Networks 11

Security in 1 G TWNs • Authentication – Mobile station sends ESN(Electronic Serial Number) to MTSO in clear text over the air interface. – Eavesdrop on cellular telephone conversation – Can capture valid ESN cloning. • Prompted cellular service providers to demand a higher level of security while designing 2 G TWNs. Network Security in Traditional Wireless Networks 12

Security in 2 G TWNs Network Security in Traditional Wireless Networks 13

Security in 2 G TWNs Controlled Network Access Network § Use digital system: made casual eavesdropping by radio hobbyists significantly more difficult since it required use of much more highly specialized and expensive equipment than a simple police scanner. § Beyond the BTS is considered a controlled environment. § Aims to secure only the access network(MS/ME BTS). § GSM is an extension of PSTN: the security philosophy of GSM is similar to that of PSTN; Network Security in Traditional Wireless Networks 14

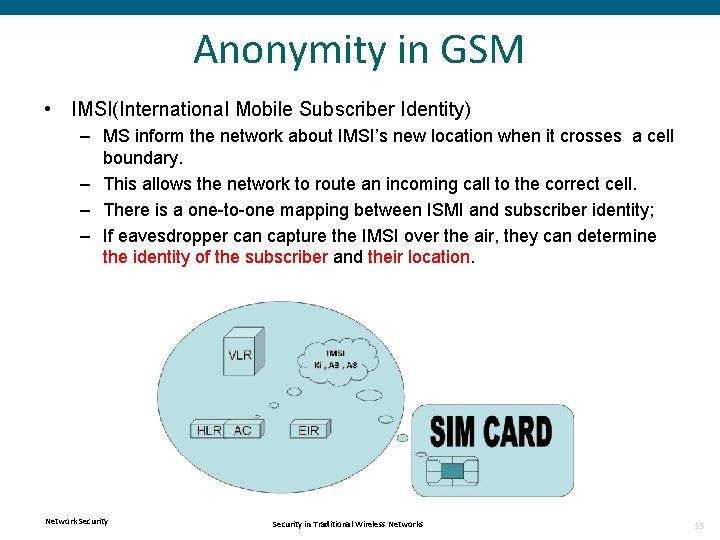
Anonymity in GSM • IMSI(International Mobile Subscriber Identity) – MS inform the network about IMSI’s new location when it crosses a cell boundary. – This allows the network to route an incoming call to the correct cell. – There is a one-to-one mapping between ISMI and subscriber identity; – If eavesdropper can capture the IMSI over the air, they can determine the identity of the subscriber and their location. Network Security in Traditional Wireless Networks 15

Anonymity in GSM • TMSI(temporary mobile Subscriber Identity) – When a ISMI has authenticated with the network, the VLR allocate a TMSI to the subscriber. – GSM protects against subscriber traceability by using TMSI. – Has only local significance. – IMSI-TMSI mapping is maintained in VLR/MSC • • • When it is switched off, the mobile station stores the TMSI on the SIM card to make sure it is available when it is switched on again; For all communication with the SIM, the network uses this TMSI to refer to the SIM. The use of a TMSI reduces the exposure of IMSI over the air interface to a minimum thus minimizing the probability that an eavesdropper may be able to identify and locate a subscriber. Network Security in Traditional Wireless Networks 16

Key Establishment in GSM • No key establishment protocol in the GSM security architecture model. • Use 128 -bit pre-shared key Ki ; • Each SIM is burnt or embedded with a unique Ki; that is, each subscriber has a unique Ki ; • Stored in SIM and Au. C (Authentication Center); Network Security in Traditional Wireless Networks 17

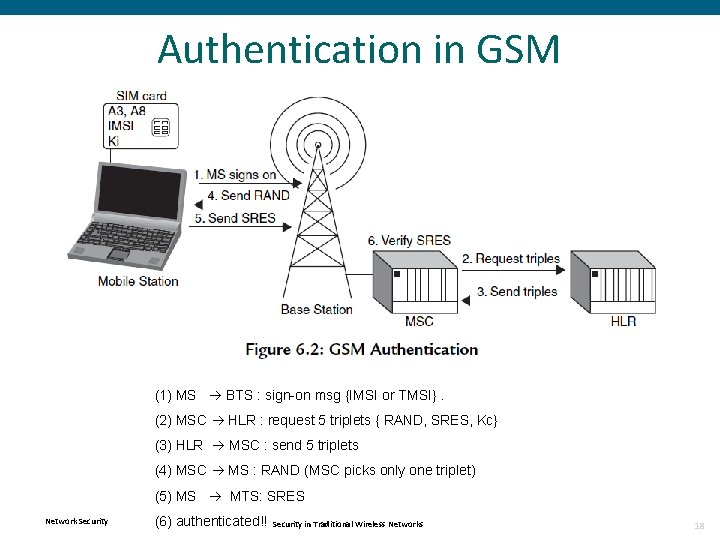
Authentication in GSM (1) MS BTS : sign-on msg {IMSI or TMSI}. (2) MSC HLR : request 5 triplets { RAND, SRES, Kc} (3) HLR MSC : send 5 triplets (4) MSC MS : RAND (MSC picks only one triplet) (5) MS MTS: SRES Network Security (6) authenticated!! Security in Traditional Wireless Networks 18

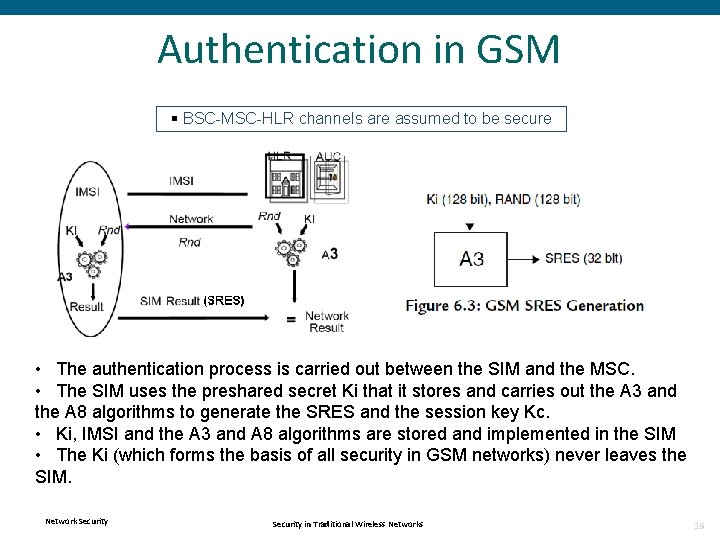
Authentication in GSM § BSC-MSC-HLR channels are assumed to be secure • The authentication process is carried out between the SIM and the MSC. • The SIM uses the preshared secret Ki that it stores and carries out the A 3 and the A 8 algorithms to generate the SRES and the session key Kc. • Ki, IMSI and the A 3 and A 8 algorithms are stored and implemented in the SIM • The Ki (which forms the basis of all security in GSM networks) never leaves the SIM. Network Security in Traditional Wireless Networks 19

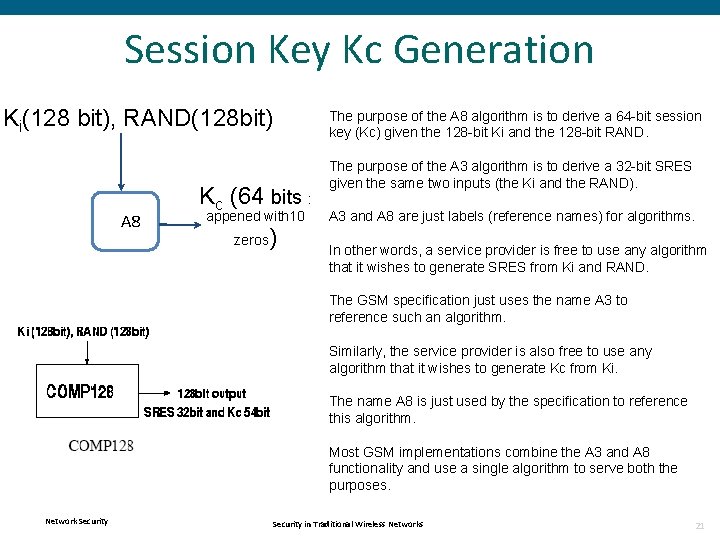
Authentication in GSM • Why 5 triplets request? • To improve roaming performance. • Instead of contacting the HLR for security triplets each time a ME roams into its coverage, the MSC gets five set of triplets : one for the current authentication process and four for future use. Network Security in Traditional Wireless Networks 20

Session Key Kc Generation Ki(128 bit), RAND(128 bit) A 8 The purpose of the A 8 algorithm is to derive a 64 -bit session key (Kc) given the 128 -bit Ki and the 128 -bit RAND. Kc (64 bits : appened with 10 zeros ) The purpose of the A 3 algorithm is to derive a 32 -bit SRES given the same two inputs (the Ki and the RAND). A 3 and A 8 are just labels (reference names) for algorithms. In other words, a service provider is free to use any algorithm that it wishes to generate SRES from Ki and RAND. The GSM specification just uses the name A 3 to reference such an algorithm. Similarly, the service provider is also free to use any algorithm that it wishes to generate Kc from Ki. The name A 8 is just used by the specification to reference this algorithm. Most GSM implementations combine the A 3 and A 8 functionality and use a single algorithm to serve both the purposes. Network Security in Traditional Wireless Networks 21

Authentication • GSM : assume the core network beyond the BSC is secure. – – BTS BSC link is not part of core. GSM does not specify how to this link need to be connected. In practice, connected by microwave. susceptible to attacks. • Protection against equipment theft. – Authenticate SIM card and not the subscriber of the SIM card. – When a ME was stolen, the user of the ME reports it to the service provider. – The service provider maintain the compromised SIM card. Network Security in Traditional Wireless Networks 22

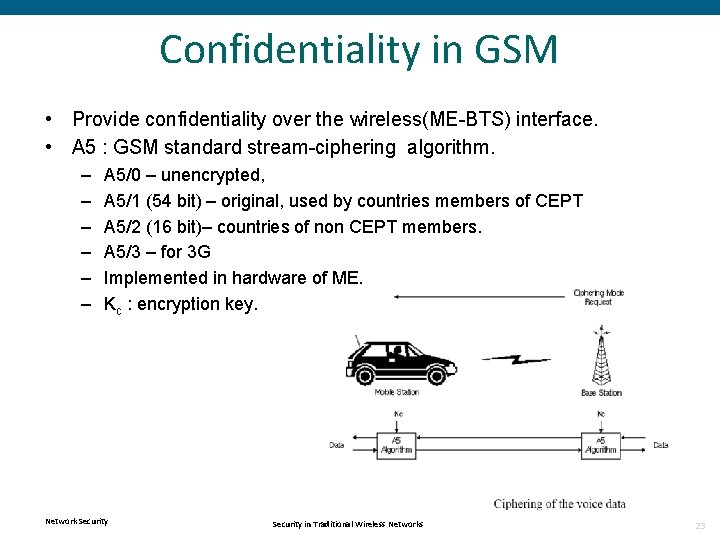
Confidentiality in GSM • Provide confidentiality over the wireless(ME-BTS) interface. • A 5 : GSM standard stream-ciphering algorithm. – – – A 5/0 – unencrypted, A 5/1 (54 bit) – original, used by countries members of CEPT A 5/2 (16 bit)– countries of non CEPT members. A 5/3 – for 3 G Implemented in hardware of ME. Kc : encryption key. Network Security in Traditional Wireless Networks 23

Confidentiality in GSM • • A 3 and A 8 are just names used by the GSM standard to reference operatorspecific algorithms; A 5 is actually an encryption algorithm specified by the GSM standard. The need to support seamless roaming across networks of different service providers. The choice of A 3 and A 8 could be left to the operator since the authentication process is carried out between the SIM and the service providers HLR. The process of encryption on the other hand must necessarily be carried out between the BTS and ME without involving the home network. All service providers use the same encryption algorithm achieving seamless roaming between different networks; There is therefore provision in GSM to change the ciphering key Kc: thus making the system more resistant to eavesdropping. The ciphering key may be changed at regular intervals or as required by the service provider. Network Security in Traditional Wireless Networks 24

What’s wrong with GSM Security? • No provision for any integrity protection of data and message. – Open to man-in-the-middle attack. • Only securing the ME-BTS interface. – BTS-BSC interface is not cryptographically protected. – Sometimes this link is wireless attractive target for attacks. • Cipher algorithms(A 5 family) are not published along with the GSM standards. does not allow public review. • Small key length - Kc : 64 bits (54 bits + 10 zeros) – Big enough to protect against real-time attack, but weak to offline attack. – GSM security architecture is inflexible - difficult to replace. Network Security in Traditional Wireless Networks 25

What’s wrong with GSM Security? • SIM cloning – recover Ki from SIM card – Chosen plaintext attack – (RAND, SRES) pair, 8 adaptively chosen plaintexts within a minute. – Recover Ki using differential cryptanalysis or side channel attack. – (1)Physical access to SIM card and communicate with SIM through smartcard reader. • Recover in a matter of few hours. – (2)Wireless contact over the air interface. • Must be capable of masquerading as a rouge BTS • ME is moving, not enough time to collect enough (chosenplaintext, cipher text) pairs Network Security in Traditional Wireless Networks 26