Something Old Something New or is it New





















































- Slides: 64

Something Old & Something New (or is it New? ) A Trundle through Cyber Crime - 1986 to Present Information Security Group www. isg. rhul. ac. uk 1

Those Behind the Threats on the Internet • Hostile (National) Intelligence Agencies (information) • Hacktivists (political statements) • Professional Hackers & Groups (some for hire) • Organised Crime (for profit) • Detective Agencies & Competitive Intelligence (undercover operations for business) • Script Kiddies (amateur hackers) 2

Those Behind the Threats on the Internet • Hostile (National) Intelligence Agencies (information) • Hacktivists (political statements) 3

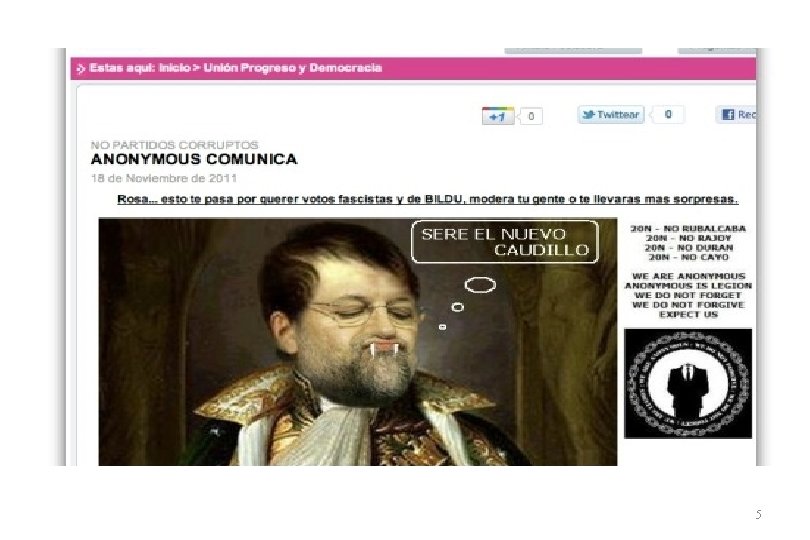
Lulzec 4

5

The Information Security Breaches Survey 2014 (Department of Business, Innovation & Skills & PWC). www. pwc. com Information Security Group www. isg. rhul. ac. uk 6

Summary – 2014 Results Show: (1) • Security Breaches remain at historically high levels, costing UK plc billions of pounds every year. A startling rise in the breaches against Small Businesses (<50 staff) • The number of significant hacking attacks on large organisations has doubled recently • Organisations are struggling to target their security expenditure. The key challenge is to evaluate & communicate the business benefits from investing in security controls. 7

Summary – 2014 Results Show: (2) • The cost of dealing with breaches and of the knee-jerk responses afterwards usually outweighs the cost of prevention • Social networks are growing in importance to business, and companies are rapidly opening up their systems to smart phones & tablets. Security controls are lagging behind the ate of technology adoption. • Unsurprisingly, most respondents expect the number of security breaches to increase in the future. 8

Increase to Cyber-Threats Keeps Cost of Breaches High (1) Breaches in the last year: 93% of large businesses (> 250 people) 87% of small businesses (<250 people) (up from 76%) 113 – the median no. of attacks by outsiders on each large organisation in the last year (up from 71 a year ago) • 23% - small businesses hit by Do. S attacks 39% large business • 20% - large organisations detected hackers had successfully penetrated their network in the last year – 15% small businesses • • 9

Increase to Cyber-Threats Keeps Cost of Breaches High (2) • £ 35 k to £ 65 k - average cost of small business worst security breach of the year • £ 450 k to £ 850 k – average cost of large organisation’s worst security breach of the year • £-Billions – is the total cost to UK plc of security breaches in the last year 10

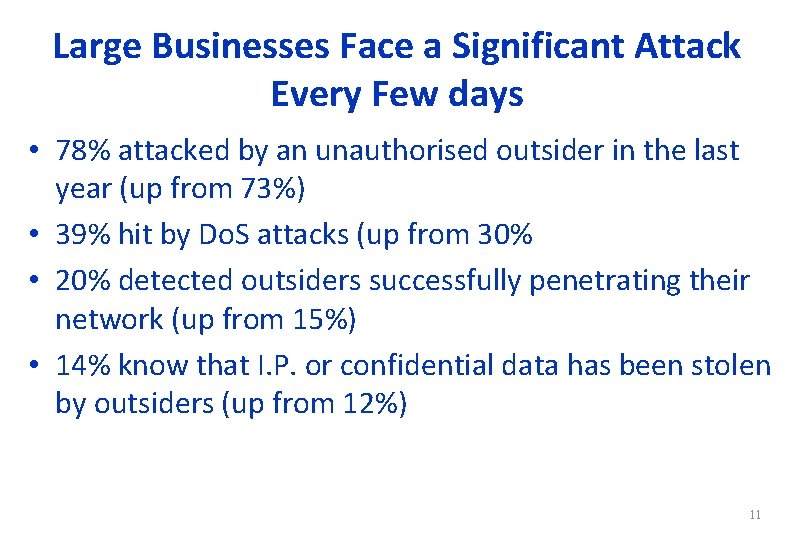
Large Businesses Face a Significant Attack Every Few days • 78% attacked by an unauthorised outsider in the last year (up from 73%) • 39% hit by Do. S attacks (up from 30% • 20% detected outsiders successfully penetrating their network (up from 15%) • 14% know that I. P. or confidential data has been stolen by outsiders (up from 12%) 11

Sophos Security Threat Reports 2012 & 2013 (first) – then January 2014 – following. Information Security Group www. isg. rhul. ac. uk 12

1. Cyber- Criminals becoming more Professional • More crime-ware kits available – the ‘Blackhole’ kit – resulting in a mass generation of new malicious code & exploits. • Volume of malware attacks & compromised websites grew – approximately 30, 000 new malicious URL’s every day – which is an increase of 50% from June 2011. • Due to failure of patching vulnerabilities, infections from compromised web-sites and ‘drive-by’ downloads are common. 13

2. Hacktivism takes Centre Stage • Typically hacking for political purposes – defacing websites, re-directing traffic, DDo. S attacks. • Lulz. Sec dominated first part of 2012 – attacks on Sony, PBS, U. S. Senate, CIA, FBI – disbanded after 50 days. • ‘Anonymous’ – initiating civil disobedience – DDo. S attacks on Salvador, Israel & Toronto. Released 90, 000 email addresses of U. S. military personnel in an attack on Booz Allen Hamilton (US Defence security consultants) • Some arrests – UK, US & Turkey, investigations in Italy & Switzerland 14

3. Targeted and Stealth Attacks • Targeted were Mitsubishi Heavy Industries, Lockheed Martin, L-3 Communications & Northrup Grumman (all involved with weapons systems) • Using targeted delivery systems – often a form of social engineering by spoofing emails to look as if they came from a colleague or friend with the objective of enticing people to open them (exploits & malware) 15

Looking Forward in 2012 -13 - Top 10 Trends • 1. Social media & the web – new attacks on social media platforms & integrated apps. • 2. More attacks on Non-Windows platforms e. g. Apple Mac OS X and Adobe. • 3. Mobile device attacks – e. g. Android • 4. New attack Vectors – possibly the move from HTML 5 to IPv 6. • 5. Shift to consumer devices (apps) may lead to less controls. 16

Looking Forward in 2012 -13 - Top 10 Trends • 6. More hacktivism – more will join. • 7. Data regulations increase – US Stopline Piracy (SOPA) & EU Data Protection Directive • 8. Mobile payment technology may be a new target (e. g. near field communication NFC in mobiles. • 9. Cloud Services – slow to start but now popular – more focus on encrypting data than protecting the device or the network • 10. The Basics are still wrong – (patching, password management) 17

2014 – Summary (1) • The trend is for Malware authors to camouflage attacks – stealth is now key. • In 2013 – Blackhole exploits were replaced by new exploit kits – borrowing the source code. • These new Botnets show a sharp increase in ‘Ransomware’ attacks (e. g. Cryptolocker) • APT’s (Advanced Persistent Threats) – target individuals, businesses or governments – they are skilled adversaries - & defence is complex as difficult to remove. 18

2014 – Summary (2) • More attacks on critical infrastructures & control systems (remember Stuxnet? ) – these include grid systems. • Mobile devices used by attackers mean that the threats are now a moving target. • Web Servers increasingly coming under malware attacks – e. g. ‘Darkleech’. • Android devices – through ‘Apps’ – now 300 families of malware e. g. ‘Ginmaster’. 19

2014 – Summary (3) • Botnets – the leak of ‘Zeus’ source code – led to ‘Gameover’ – replaces C & C with peer to peer network devices – enables more widespread DDo. S attacks – also the attackers are using ‘Tor’ (the onion ring software) to resist surveillance & hide identities – now publicising Wikileaks & ‘Silk Road’ (black market economy). • The Cloud – more attacks expected on corporate & personal data. • NOW LET US GO BACK IN TIME 20

So, Looking Back in History -1986 - 1989 • Morris Worm launched in U. S. - the first worm • ‘WANK’ – Worms Against Nuclear Killers – probably the first hacktivist group – worm that defaced users login screens at the U. S. Dept. of Energy and NASA – the day before the Space Shuttle with the probe ‘Galileo’ was launched. • Phone Phreakers started groups & a type of gang warfare. 21

1992 - 1993 • Internet now over 1 million - Bulletin boards, pornography available on Internet • Michelangelo Virus causes panic (March 6) • Tim Berners-Lee developed www at CERN • Packet spoofing (accessing packets for passwords) & network sniffing found - hidden in file directories e. g. “/tmp” CERT reports 100. 000 systems attacked by this method • First firewalls developed 22

1994 • Kevin Mitnick hacked cell-phone companies - (the methodology of social engineering was uncovered) • Another hacktivist group – the ‘Zippies’ launched ‘Intervasion of the UK’ – email bombing – protest against the outlawing of ‘rave dance festivals’. • Organised Crime - Vladimir Levin(St. Petersburg) hacked Citibank systems (San Francisco) - transferred $10 million to Rotterdam. Arrested at Stanstead Airport (UK) in 1995 - 3 years in prison 23

1995 - Data-Stream Cowboy & Kuji attack U. S. Military Systems • Data-stream put sniffers on 30 systems at Rome Laboratories (Washington) - compromised 100 user accounts with logins & passwords • Also attacked Army Corps of Engineers - using a scanning attack also Goddard Space Centre, NASA, NATA, SHAPE & Wright Paterson Air Force Base. • Traced through web-sites they had set-up • Arrested May 1995 D. identified as Richard Price (16 yrs) from North London • Kuji identified June 1996 as Matthew Bevan (Cardiff) 24

1997 - 1998 • Kevin Mitnick sentenced to 22 months for cell phone attacks • The ‘hacktivists ‘Zapistas’ (Mexico) launch the Electronic Disturbance Theatre with a ‘Floodnet’ tools – protest against the Mexican Gov’t over the Chiapas Region. • CERTS and ‘FIRST’ report explosion in operating system and application vulnerabilities 25

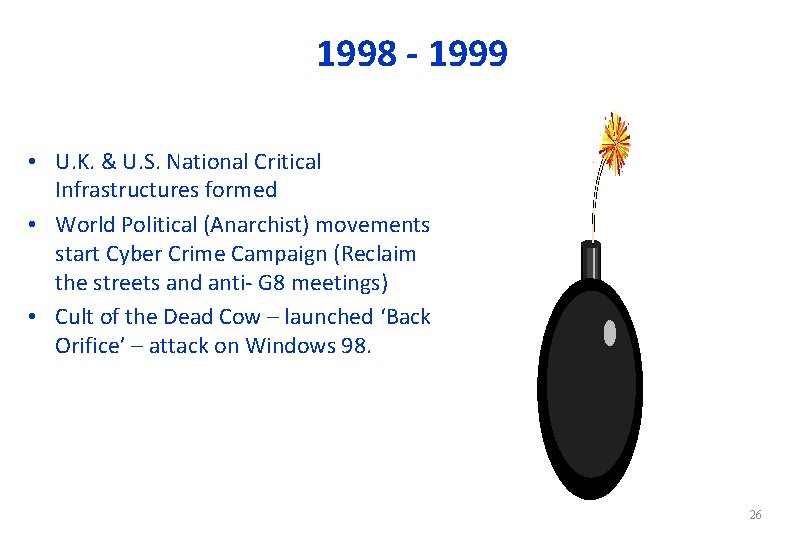
1998 - 1999 • U. K. & U. S. National Critical Infrastructures formed • World Political (Anarchist) movements start Cyber Crime Campaign (Reclaim the streets and anti- G 8 meetings) • Cult of the Dead Cow – launched ‘Back Orifice’ – attack on Windows 98. 26

c. Dc 27

2003 -2004 • World. Pay – (large financial) – attacked by DDo. S – halted for 3 days – also in Feb. 2004 ‘Paddy. Power’ on-line gambling site hit by same attack. • Nimda, So Big. F, Slammer and MS Blast worms and malware costs billions. The I. S. industry was not ready for it, and fairly impotent to act. • Law enforcement launch worldwide successful sting operations against paedophiles, they have so many to arrest that they cannot cope with the work. 28

2005 – 2006 (1) • Spam reaches epidemic proportions, most e-mail addresses are in the possession of spammers – domains are now well known. People can be identified by their e-mail addresses, and malware continues to be introduced by this medium. • Phishing & Pharming cause huge losses to the financial industry in Western Europe – although the figures are not released. • Bots and Zombies (in one form or another) are now thought to infect a high percentage of home PC’s, and most business workstations 29

2005 – 2006 (2) • Hacking reports have diminished, but they are not reported to anybody – yet fraud and on-line fraud has increased. • Anti-virus vendors appear to have caught up with historical viruses – detection rates are higher. • Identity Fraud escalates on an international scale – passports, immigration, and benefit (social security) fraud reaches ever increasing figures. • Operating System vendors now agree that there are problems with buffer overflows. 30

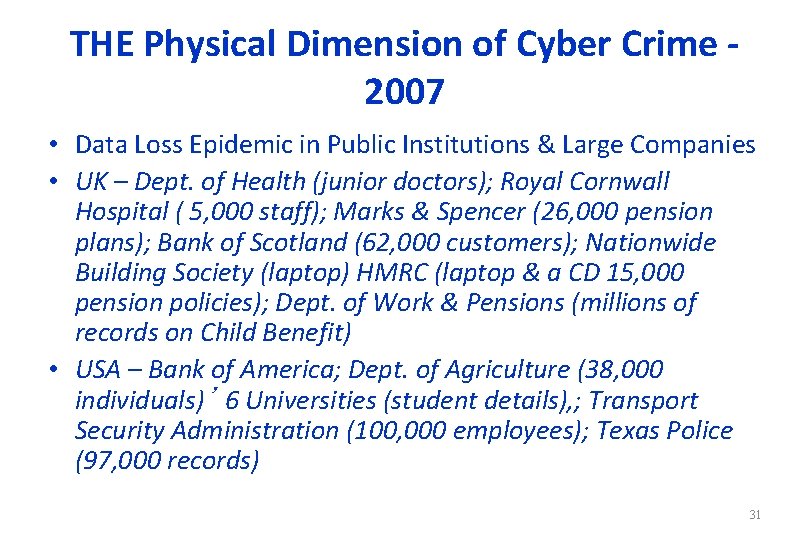
THE Physical Dimension of Cyber Crime 2007 • Data Loss Epidemic in Public Institutions & Large Companies • UK – Dept. of Health (junior doctors); Royal Cornwall Hospital ( 5, 000 staff); Marks & Spencer (26, 000 pension plans); Bank of Scotland (62, 000 customers); Nationwide Building Society (laptop) HMRC (laptop & a CD 15, 000 pension policies); Dept. of Work & Pensions (millions of records on Child Benefit) • USA – Bank of America; Dept. of Agriculture (38, 000 individuals)’ 6 Universities (student details), ; Transport Security Administration (100, 000 employees); Texas Police (97, 000 records) 31

Key-loggers • Key-loggers are devices to capture keystrokes from a work station. • They come in the form of: • Physical devices (so access is needed to a work station). . . And • Logical devices 32

Physical Key-Loggers • Captures keystrokes (including BIOS password) • Hardware logger plug-ins stored in non-volatile memory flash • Data can be recovered either by un-lugging the device or from a program e. g. a text editor • Volume restricted by memory 33

USB Key Logger • Key Carbon key logger • For PC & MAC • Records 2 million keystrokes (2 Mb) • Cost £ 180 • 128 bit encryption • Cannot be detected by antivirus or anti-spy software • They were used to steal £ 220 from the Mitsui Bank in London in April 2005. 34

Replacement (Key-logger) Keyboards • Key-logger built-in • Device completely hidden from the user • Slightly larger than a standard keyboard 35

‘Key Ghost’ Security Keyboard • Available for purchase • This picture shows it unscrewed 36

‘Key Ghost’ Security Keyboard • This shows white material covering the cable in a heatshrink bundle. 37

‘Key Ghost’ Security Keyboard • Uncovering the white material – shows the key-logger device 38

2007 Cyber-warfare on Estonia • Tension with Russia over Soldier’s statue & blocked gas line • DDo. S attack using Storm Worm Botnet – 1 million zombie computers. Attacks on News Agencies & Banks with pings & SQL injection to overload sites • Mostly message flooding rather than attack on Networks 39

2008 Cyber-warfare on South Ossetia • Georgia v Russia – suppressed news agencies & paralysed Georgian Network infrastructure – mostly by so-called ‘Russian Business Network’. • Used CPU exhaustion, overloaded web scripts & SQL by sending heavy queries • Georgia switched to U. S. IP sites • Most attacks co-ordinated thro’ ‘Stopgeorgia. ru. ’ 40

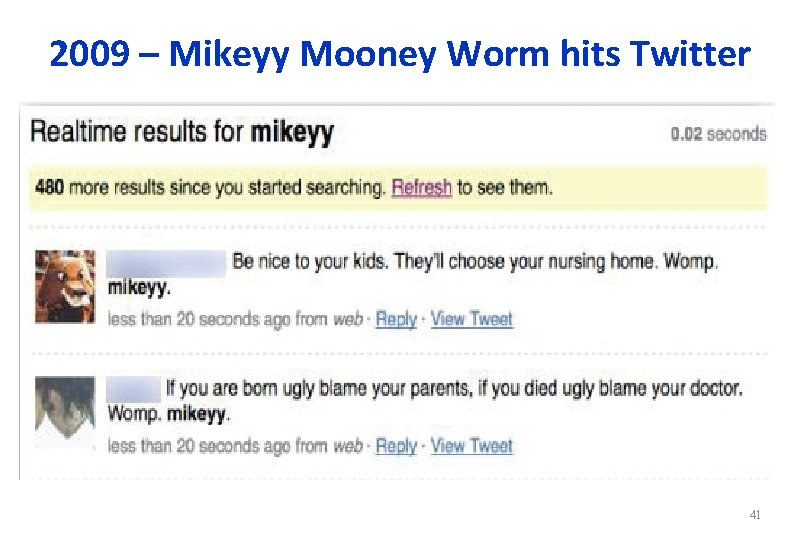
2009 – Mikeyy Mooney Worm hits Twitter 41

2010 – Main Issues • April – First convictions in UK for ‘Botnet-for-Hire’ (Edwards & Smith). • Mumba Botnet infects 35 k systems containing the ‘Zeus’ Trojan. • July – ‘Stuxnet’ worm used to infect SCADA systems (Supervisory Control & Data Aquisition) – collects data from various sensors in a factory. Sophisticated malware – affects Iranian nuclear systems. • ‘Kroxxus’ Botnet infects 100 k domains (steals FTP passwords) 42

2010 – Main Issues • Keystroke logger on Twitter (from false I. Phone app. ) • ‘Zbot’ – mimics Credit Card Secure Code System (injects pages into it) – Visa & Master. Card • Google Android smart-phones discovered with Trojan – sends SMS to premium rate numbers • Wikileaks revealed. • Zeroll worm spreads to Instant Messaging (by clicking on link that claims to be a picture) • SPAM – Pushdo botnet – servers taken down – represented 10% of worldwide spam. • Arrests in UK & US over use of the Zeus trojan & botnet £ 160 million stolen 43

2011 Attacks (1) • Hacking Group ‘Anonymous’ attacked Pay. Pal & Visa sites – arrests followed. • Cisco 2010 report stated that Cyber Crime moving from Windows to mobile systems. Spam dropped. • Rustock botnet taken out by Microsoft. “Steamy Windows’ malware in Android systems. • ‘Spyeye’ malware used from Botnets (harvests online banking credentials) 44

2011 Attacks (2) • More Botnets identified – ‘Coreflood’ ‘TDSS’, ‘Kelihos’ & ‘Mutulji’. • ‘Lulzsec’ hacking group hacktivists) – arrest of one ‘member’ for attack on ‘Sony’ – used SQL Injection attack (to collect members data). 45

The Zeu. S Fraud (or Zbot, Wsnpoem, Gorhax) • Crime kit first detected in 2007, enables the kit owner to build & administer a botnet. • Botnet is a host infected with a Trojan – connected to Internet • Infected host is controlled by a Command & Control Server (C&C) • A Botnet can be used for Spam, Identity Theft, DDo. S attacks • Zeu. S used for Banking Information 46

2012 • Verizon reports that 58% of data ‘stolen’ (unauthorised access) was by hacktivists. • Microsoft take down Zeus & Spy-eye sites • The Honeypot project, Kaspersky & Dell take down Kelihos botnet (again) due to the amount of DDo. S & spam attacks on Windows XP & Windows 7. (but back up again later) • SOCA (UK Serious Crime Agency) website attacked from Norway after it took investigated credit card scam sites. 47

2013 -14 – Botnets & Trojans • A spike in the number of ‘Tor’ users (the anonymising network) blamed on the Botnet known as Mevade A. • Beta Bot – steals (copies) login credentials from Social Networks & on-line transactions & disables anti-virus • Zero. Access Botnet has 1. 9 million computers under control – earned operators $700, 000 in fraudulent advertising – user P 2 P architecture – Symantec tried to take it down & reduced some capacity. • Advanced Power Botnet – uses SQL injection on websites – pretends to be a Firefox add-on – operational since May 2013. 48

2013 -14 – Botnets & Trojans • FBI & Microsoft take down Citadel Botnet (June 2013) with the help of 80 police forces – Citadel responsible for $500 million in theft from online bank accounts. • Hesperbot Trojan – key-stroke logger, takes screenshots & records from video cameras – downloaded from pdf attachments on email • Russian Police arrest ‘Blackhole’ malware author (but variants are still around. • Obad Trojan targets Android devices – send messages to premium rate numbers & infects with malware – uses bluetooth & Wi-Fi to infect other devices. 49

2013 -14 • Bitcoin – Danish company hit by DDo. S attack then disabled security to remove bitcoin. (November 2013) – also more break-ins & arrests in Germany and China. • Nat. West bank the target of DDo. S in December 2013. • Arrests of organised crime on cyber thefts at Barclays & Santander Banks in the UK – planted devices on routers. • ‘Snowden’ Reports – allegations of State intrusion into privacy. • Ransomeware – Cryptolocker, Powerlocker & Prisonlocker used for blackmail & distributed as a malware kit. 50

Some of the Recent Malware • TDL family of rootkits – hides presence of other malware – some store files in a secret encrypted partition at the end of the hard disk. • Conficker worm – average no. of infected computers on a network is 32. 8 (Sophos). • 85% of malware now comes from the web – ‘driveby downloads’ are the top threat (exploits flaws in browser software to install malware just by visiting a web page. 51

Ransomeware • Cryptolocker is the latest ransomware version that surfaced in 2013. It blocks access to the affected system and encrypts certain files. • The latest version was used as a payload in malicious spam from the downloader TROJ_UPATRE and Zeus/ZBOT variant. • Affected users not only had important files encrypted, their online banking credentials were obtained as well. • Victim no’s have increased in USA, Canada & UK. 52

Ransomeware (2) • Typical threat starts as a spammed message with a malicious attachment (detected as the Trojan). If executed, the attachment downloads & executes cjkienn. exe which is a ZBOT variant detected as TSPY_ZBOT. VNA • This variant downloads Cryptolocker onto the system, namely TROJ_CRILOCK. NS • Once executed, Crypto locker connects to randomly generated domains to download the public key for encryption 53

Ransomeware (3) • Cryptolocker then searches for files with certain extensions to encrypt – these include. doc, . docx. xls, &. pdf among others. • It then changes the system’s wallpaper with a notice that informs users that their important files are encrypted – (using AES-265 and RSA encryption) - and that they have to purchase the private key. 54

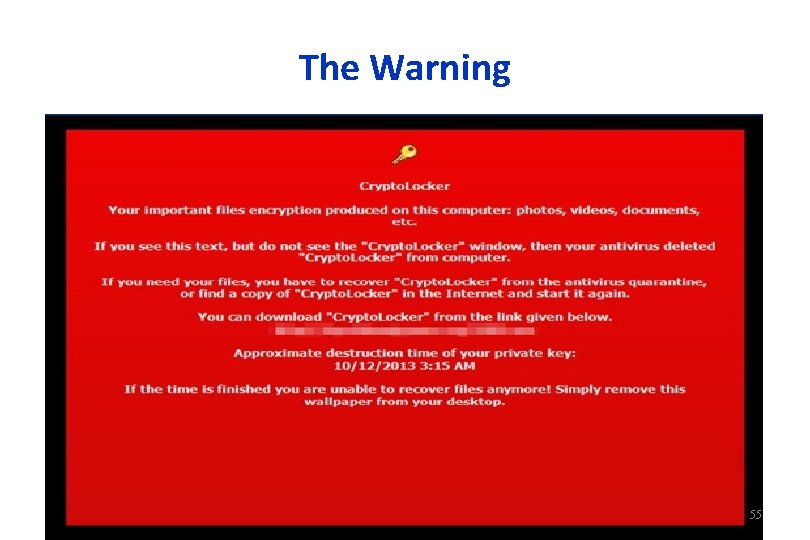
The Warning 55

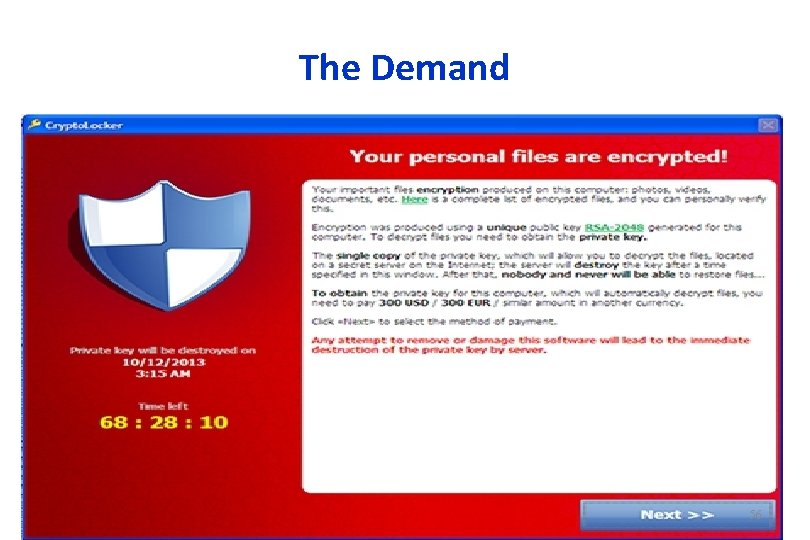
The Demand 56

Have We Seen This Before? – This is a Trojan/Blackmail on the Aids Diskette Case of 1989 • • Start your computer Insert this disk in Drive A: At the C> prompt, type A: install Press ENTER Installation in progress Please Wait 57

The Sequence 2. TURN ON THE PRINTER and then press ENTER or RETURN key, 58

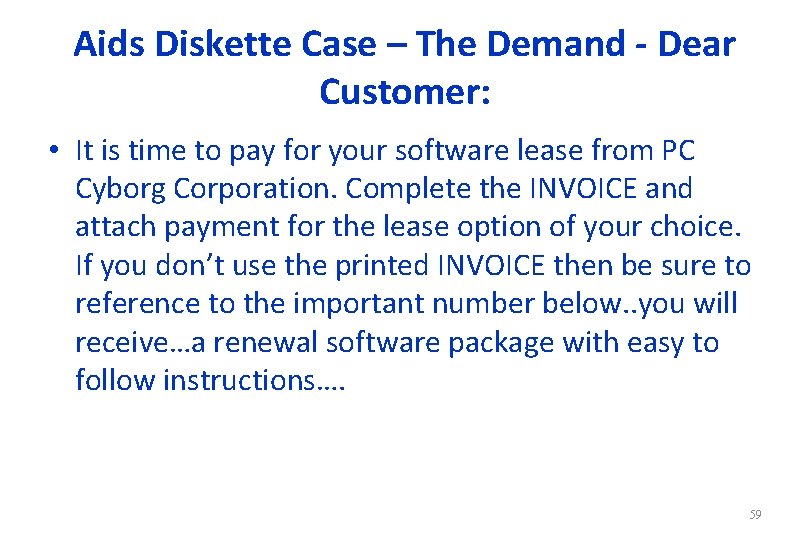
Aids Diskette Case – The Demand - Dear Customer: • It is time to pay for your software lease from PC Cyborg Corporation. Complete the INVOICE and attach payment for the lease option of your choice. If you don’t use the printed INVOICE then be sure to reference to the important number below. . you will receive…a renewal software package with easy to follow instructions…. 59

Price • The price of 365 user applications is US$189. The price of a lease for the lifetime of your hard disk is US$378. You must enclose a bankers draft, cashiers check or international money order payable to PC CYBORG CORPORATION for the full amount. Mail your order to PO Box 87 -14 -44, Panama 7 , Panama. 60

Please Wait While Printing to Parallel Printer • The Installation is completed. You are now required to complete the invoice and send full payment for this software. Please do so immediately to avoid an inconvenient interruption of service. When you want to use the program, type AIDS at the c>prompt. You will not need the original disk again, so give it to a friend……. . 61

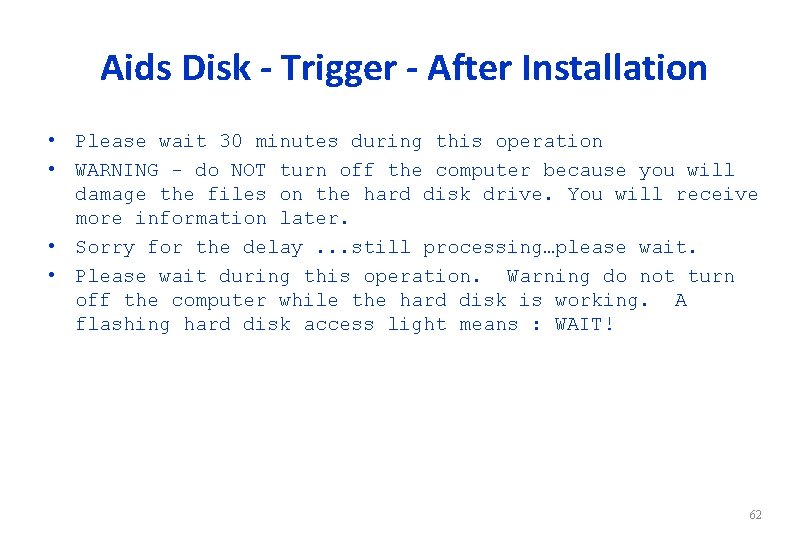
Aids Disk - Trigger - After Installation • Please wait 30 minutes during this operation • WARNING - do NOT turn off the computer because you will damage the files on the hard disk drive. You will receive more information later. • Sorry for the delay. . . still processing…please wait. • Please wait during this operation. Warning do not turn off the computer while the hard disk is working. A flashing hard disk access light means : WAIT! 62

And Finally! After Triggering • WARNING! you risk destroying all the files on drive C. The lease for a key software package has expired. Renew the lease before you attempt any further file manipulation or other use of this computer. Do not ignore this message! 63

End Information Security Group www. isg. rhul. ac. uk 64