Some integral properties of Rijndael Marine Minier CITI




![General principle of cryptanalysis [n bits] f n KX x’ = (X, KX) f General principle of cryptanalysis [n bits] f n KX x’ = (X, KX) f](https://slidetodoc.com/presentation_image/822e96eff449acb764e3c4a855cde949/image-8.jpg)





![Extension of 2 rounds at the end [Ferguson and al. -00]: partial sums n Extension of 2 rounds at the end [Ferguson and al. -00]: partial sums n](https://slidetodoc.com/presentation_image/822e96eff449acb764e3c4a855cde949/image-21.jpg)
![Extension at the beginning: 2 methods n [Ferguson and al. - 00]: one initial Extension at the beginning: 2 methods n [Ferguson and al. - 00]: one initial](https://slidetodoc.com/presentation_image/822e96eff449acb764e3c4a855cde949/image-22.jpg)



![[Knudsen – Rijmen 07] n Notion of Known Key Distinguisher ¨ Principle: create a [Knudsen – Rijmen 07] n Notion of Known Key Distinguisher ¨ Principle: create a](https://slidetodoc.com/presentation_image/822e96eff449acb764e3c4a855cde949/image-28.jpg)
![Theoritical model [Africacrypt 09] n Advantage of Distinguishers [Vaudenay 97]: Adv. E(A) n Two Theoritical model [Africacrypt 09] n Advantage of Distinguishers [Vaudenay 97]: Adv. E(A) n Two](https://slidetodoc.com/presentation_image/822e96eff449acb764e3c4a855cde949/image-29.jpg)
![Case of study: the AES [Knu-Rij 07] n Forward sense =0 =0 =0 n Case of study: the AES [Knu-Rij 07] n Forward sense =0 =0 =0 n](https://slidetodoc.com/presentation_image/822e96eff449acb764e3c4a855cde949/image-32.jpg)



- Slides: 43

Some integral properties of Rijndael Marine Minier CITI Laboratory INSA de Lyon Workshop MITACS - June 2009 1

Guideline n n Description of the AES and of its little brothers Integral properties of the AES Integral properties of the different Rijndael versions Deduced distinguishers ¨ With n n unknown keys LANE Conclusion Workshop MITACS - June 2009 2

The AES and its brothers Workshop MITACS - June 2009 3

AES and Rijndael (1/3) n Rijndael, created by J. Daemen and V. Rijmen, AES new standard block ciphers with a parallel structure. Plaintexts (128, 160 192, 224, 256 bits) Bytes matrix 4 x, 5 x, 6 x, 7 x, 8 x 4 initial Key addition K 0 Byte Sub Shift Row Mix Column ¨ Iterative K 1 Key Addition ¨ blocks sizes: 128, 160, 192, 224 or 256 bits. ¨ Key sizes: 128, 192 or 256 bits. Byte Sub Shift Row Mix Column Key Addition K 9 number of rounds vary between 10 and 14 according to the blocks sizes and the key sizes. round 1 ¨ The K 10 Byte Sub Shift Row Key Addition round 9, 11 ou 13 Last Round Ciphertexts (128, 160 192, 224, 256 bits) Bytes matrix 4 x, 5 x, 6 x, 7 x, 8 x 4 Workshop MITACS - June 2009 4

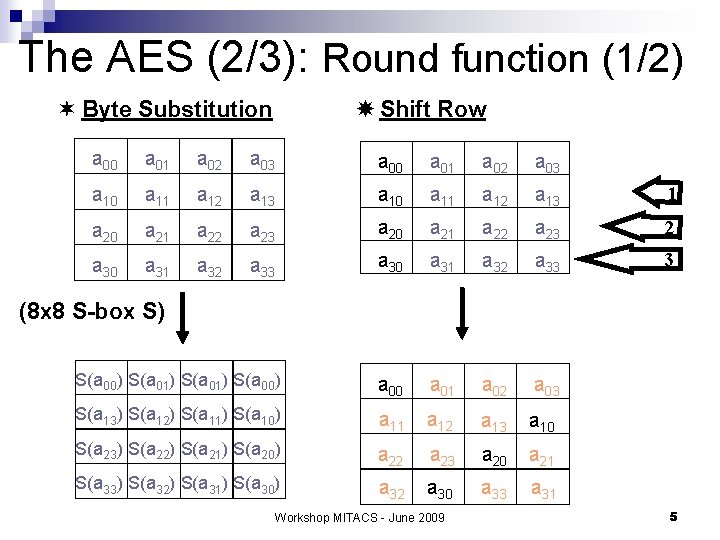
The AES (2/3): Round function (1/2) ¬ Byte Substitution Shift Row a 00 a 01 a 02 a 03 a 10 a 11 a 12 a 13 1 a 20 a 21 a 22 a 23 2 a 30 a 31 a 32 a 33 3 S(a 00) S(a 01) S(a 00) a 00 a 01 a 02 a 03 S(a 13) S(a 12) S(a 11) S(a 10) a 11 a 12 a 13 a 10 S(a 23) S(a 22) S(a 21) S(a 20) a 22 a 23 a 20 a 21 S(a 33) S(a 32) S(a 31) S(a 30) a 32 a 30 a 33 a 31 (8 x 8 S-box S) Workshop MITACS - June 2009 5

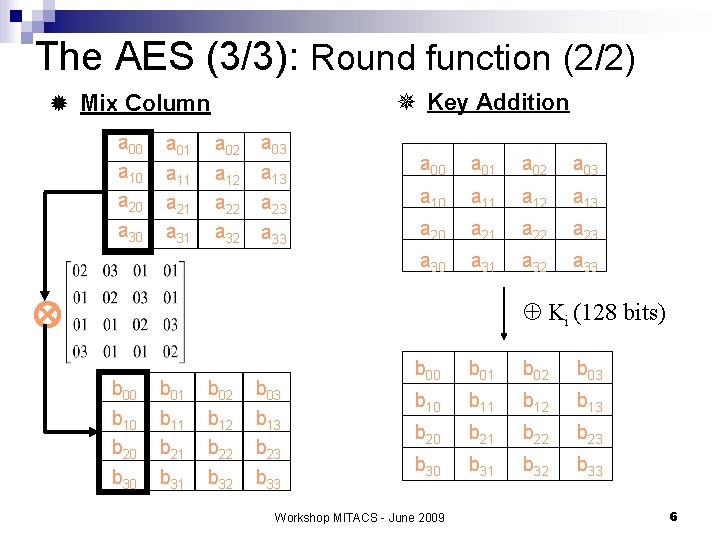
The AES (3/3): Round function (2/2) ¯ Key Addition ® Mix Column a 00 a 10 a 20 a 30 a 01 a 11 a 21 a 31 a 02 a 12 a 22 a 32 a 03 a 13 a 23 a 33 a 00 a 01 a 02 a 03 a 10 a 11 a 12 a 13 a 20 a 21 a 22 a 23 a 30 a 31 a 32 a 33 Ki (128 bits) b 00 b 10 b 20 b 30 b 01 b 11 b 21 b 31 b 02 b 12 b 22 b 32 b 03 b 13 b 23 b 33 b 00 b 01 b 02 b 03 b 10 b 11 b 12 b 13 b 20 b 21 b 22 b 23 b 30 b 31 b 32 b 33 Workshop MITACS - June 2009 6

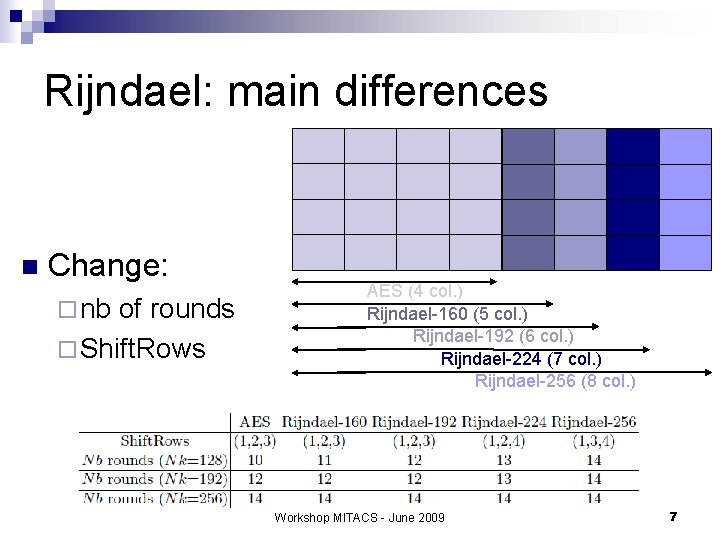
Rijndael: main differences n Change: ¨ nb of rounds ¨ Shift. Rows AES (4 col. ) Rijndael-160 (5 col. ) Rijndael-192 (6 col. ) Rijndael-224 (7 col. ) Rijndael-256 (8 col. ) Workshop MITACS - June 2009 7
![General principle of cryptanalysis n bits f n KX x X KX f General principle of cryptanalysis [n bits] f n KX x’ = (X, KX) f](https://slidetodoc.com/presentation_image/822e96eff449acb764e3c4a855cde949/image-8.jpg)
General principle of cryptanalysis [n bits] f n KX x’ = (X, KX) f . . . x’ [ n bits] f . . . rounds Final rounds Intermediate Initial rounds X R(x’, y’) Distinguisher A: To find a relation R(x’, y’) on intermediate states which has a probability p of happening as far as possible from the uniform probability p*: f . . . Kr y’ f Pr[A]=Adv(A)=|p-p*| [ n bits] KY y’ = (Y, KY) Y n Test over the keys sur (KX, KY) Workshop MITACS - June 2009 8

Integral properties Workshop MITACS - June 2009 9

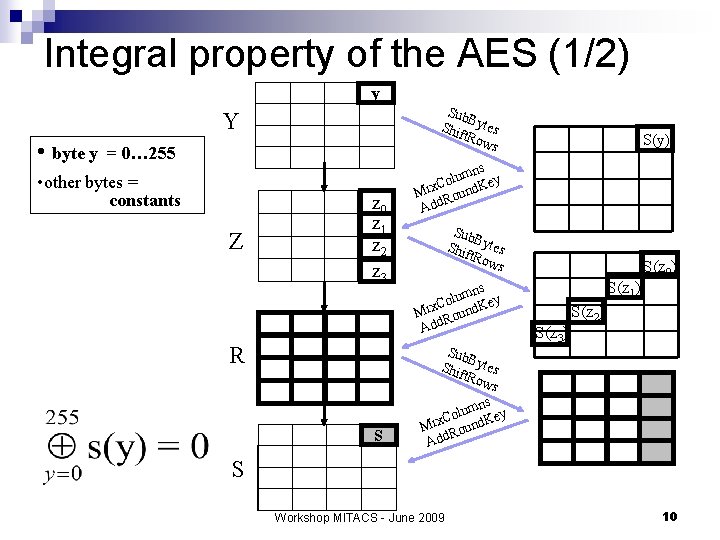
Integral property of the AES (1/2) y Sub B Shif ytes t. Ro ws Y • byte y = 0… 255 • other bytes = constants Z z 0 z 1 z 2 z 3 R s S(y) s umn ey l o C Mix ound. K R Add Sub B Shif ytes t. Ro ws s umn ey l o C Mix ound. K R Add S(z 1) S(z 3) S(z 0) S(z 2) S Workshop MITACS - June 2009 10

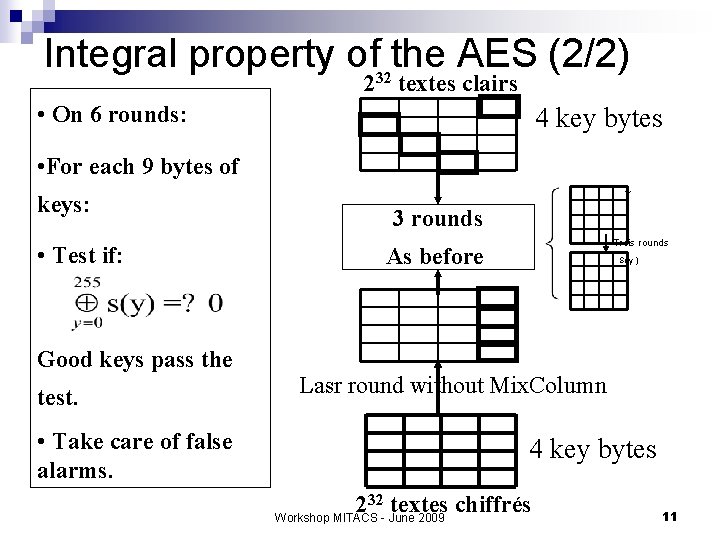
Integral property of the AES (2/2) 232 textes clairs • On 6 rounds: 4 key bytes • For each 9 bytes of keys: • Test if: Good keys pass the test. • Take care of false alarms. Y 3 rounds Trois rounds As before S( y ) Lasr round without Mix. Column 4 key bytes 32 textes chiffrés 2 Workshop MITACS - June 2009 11

Complexity of integral attacks n Improvement by Ferguson: ¨ Sum over the 232 values ¨ => Complexity for 6 rounds Nb plaintexts = 6*232 n Complexity = 246 using partial sum techniques n ¨ For 7 rounds: n Nb plaintexts = 2128 – 2119 (with herd technique) n Complexity = 2120 cipher operations Workshop MITACS - June 2009 12

For Rijndael The same kind of properties n But, due to the slower diffusion, => more rounds and better extensions n Workshop MITACS - June 2009 13

Rijndael-256: first remark y Note: SR: 1, 2, 4 Nb rounds: 14 (min) z 0 z 1 z 2 z 3 z 0 z 3 z 2 z 1 Sub. Bytes Shift. Rows a 0 a 1 a 2 a 3 b 0 b 1 b 2 b 3 z 2 z 1 umns Mix. Col y Add. Ke Workshop MITACS - June 2009 14

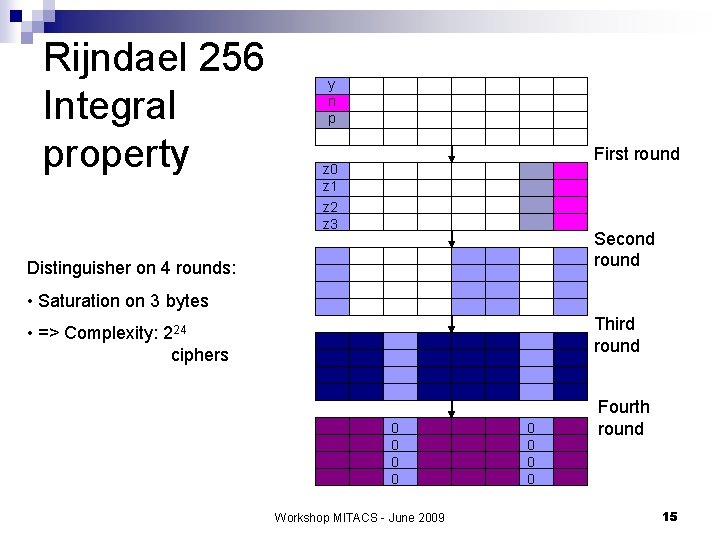
Rijndael 256 Integral property y n p First round z 0 z 1 z 2 z 3 Second round Distinguisher on 4 rounds: • Saturation on 3 bytes Third round • => Complexity: 224 ciphers 0 0 Workshop MITACS - June 2009 0 0 Fourth round 15

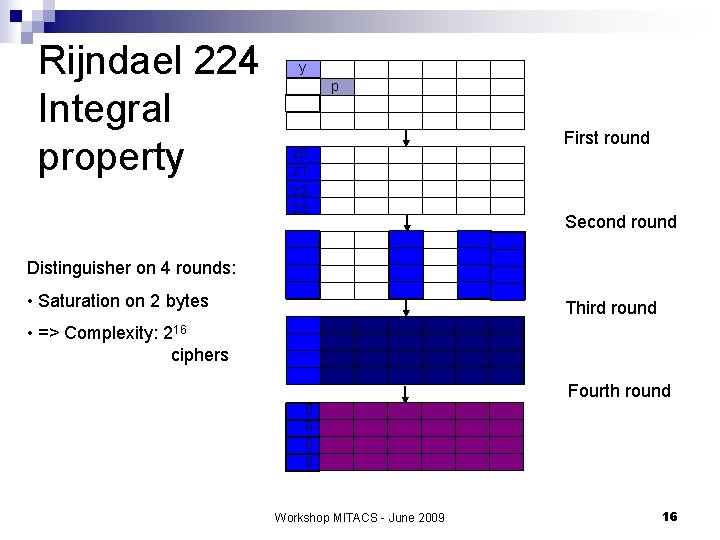
Rijndael 224 Integral property y p z 0 z 1 z 2 z 3 First round Second round Distinguisher on 4 rounds: • Saturation on 2 bytes Third round • => Complexity: 216 ciphers Fourth round 0 0 Workshop MITACS - June 2009 16

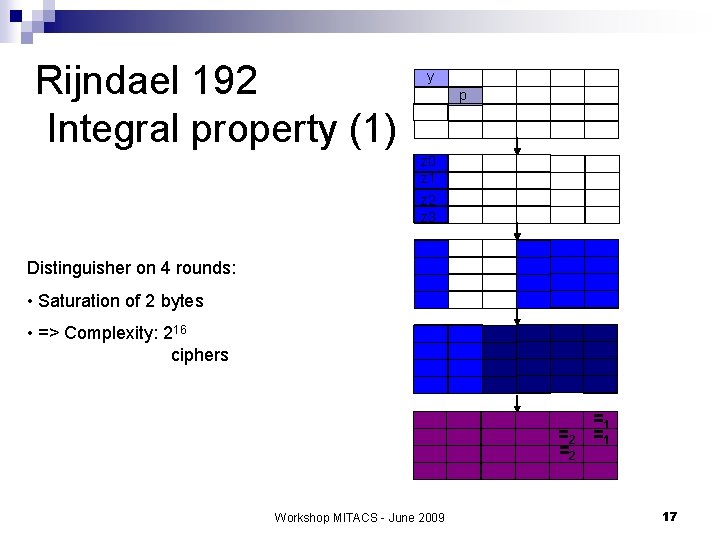
Rijndael 192 Integral property (1) y p z 0 z 1 z 2 z 3 Distinguisher on 4 rounds: • Saturation of 2 bytes • => Complexity: 216 ciphers =1 =2 Workshop MITACS - June 2009 17

Rijndael 192 Integral property y p n z 0 z 1 z 2 z 3 Distinguisher on 4 rounds: • Saturation on 3 bytes • => Complexity: 224 ciphers =1 =1 Workshop MITACS - June 2009 =2 =2 0 0 0 0 18

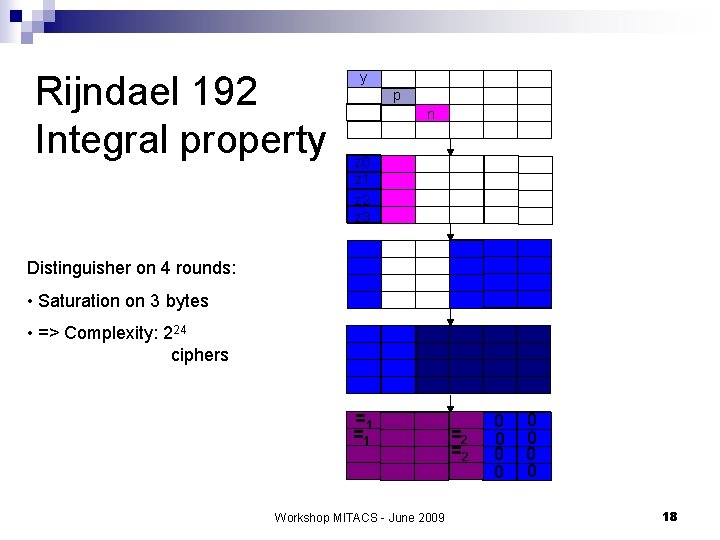
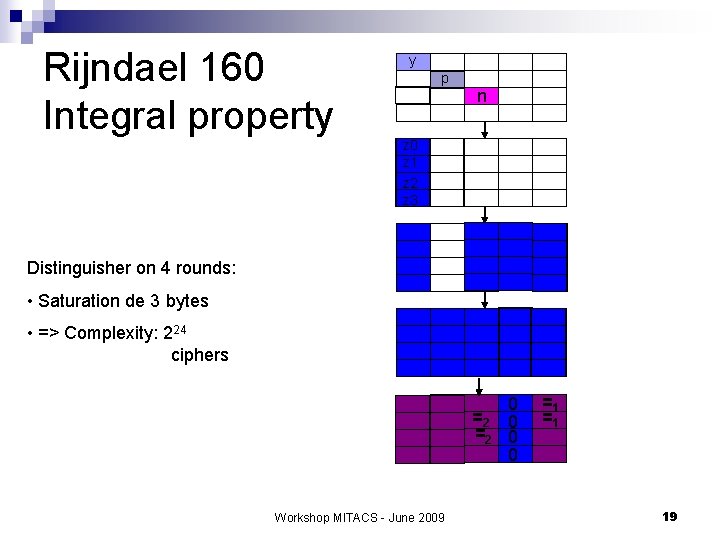
Rijndael 160 Integral property y p n z 0 z 1 z 2 z 3 Distinguisher on 4 rounds: • Saturation de 3 bytes • => Complexity: 224 ciphers =2 =2 Workshop MITACS - June 2009 0 0 =1 =1 19

Unknown keys Distinguishers Workshop MITACS - June 2009 20
![Extension of 2 rounds at the end Ferguson and al 00 partial sums n Extension of 2 rounds at the end [Ferguson and al. -00]: partial sums n](https://slidetodoc.com/presentation_image/822e96eff449acb764e3c4a855cde949/image-21.jpg)
Extension of 2 rounds at the end [Ferguson and al. -00]: partial sums n s directly deduced from ci, j n n For each ciphertext c, we associate the partial sum: n Use to sequentially determine kk => Share in 4 steps the key serach Workshop MITACS - June 2009 21
![Extension at the beginning 2 methods n Ferguson and al 00 one initial Extension at the beginning: 2 methods n [Ferguson and al. - 00]: one initial](https://slidetodoc.com/presentation_image/822e96eff449acb764e3c4a855cde949/image-22.jpg)
Extension at the beginning: 2 methods n [Ferguson and al. - 00]: one initial round n => attack on 5 rounds with 232 plaintexts Workshop MITACS - June 2009 22

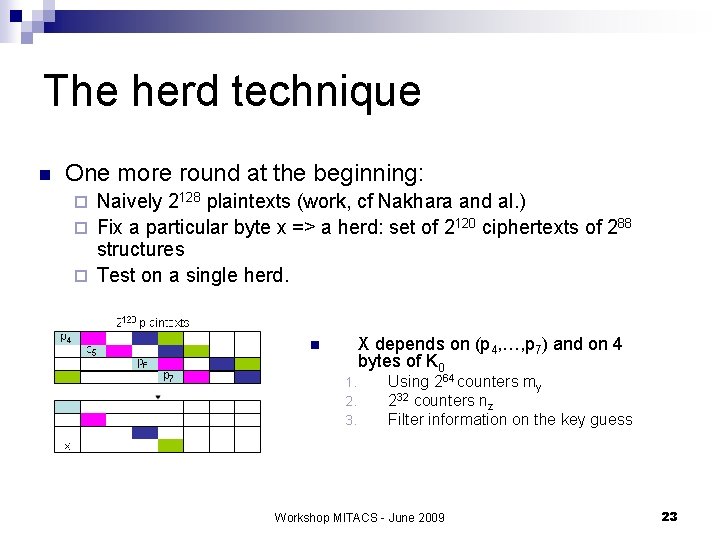
The herd technique n One more round at the beginning: Naively 2128 plaintexts (work, cf Nakhara and al. ) ¨ Fix a particular byte x => a herd: set of 2120 ciphertexts of 288 structures ¨ Test on a single herd. ¨ X depends on (p 4, …, p 7) and on 4 bytes of K 0 n 1. 2. 3. Using 264 counters my 232 counters nz Filter information on the key guess Workshop MITACS - June 2009 23

Combine those extensions n attack over 2+4+2=8 rounds (for Rijndael-256) 1. 2. 3. 4. 5. n n Increment the 64 bits (c 0, …, c 3, p 4, …, p 7) Guess the 4 bytes of K 0, compute x, separate counters into herds. Choose a single herd, nz en ajoutant (c 0, …, c 3) pour chaque y correct Guess the 5 bytes of K 7 and of K 6 of the two last rounds to decipher each z on one byte. Sum this value over the 232 values of z and look at the 0 s. Repeat this point for each value of the. K 0 bytes. => The 4 bytes (p 4, …, p 7) and the 4 bytes of K 0 give 4 bytes => 224 smaller herds => reduce the exhaustive search to 2128 -2119 plaintexts. Workshop MITACS - June 2009 24

Complexity and attacks on 9 rounds n Total cost: ¨ 2128 -2119 plaintexts ¨ 2120 cipher operations n => Add one round at the end using a complete exhaustive search on the subkey K 9 Workshop MITACS - June 2009 25

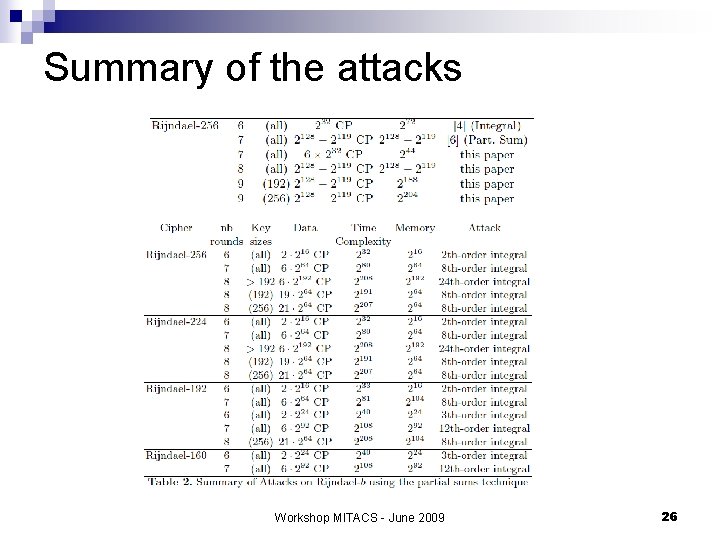
Summary of the attacks Workshop MITACS - June 2009 26

Known Keys Distinguishers Workshop MITACS - June 2009 27
![Knudsen Rijmen 07 n Notion of Known Key Distinguisher Principle create a [Knudsen – Rijmen 07] n Notion of Known Key Distinguisher ¨ Principle: create a](https://slidetodoc.com/presentation_image/822e96eff449acb764e3c4a855cde949/image-28.jpg)
[Knudsen – Rijmen 07] n Notion of Known Key Distinguisher ¨ Principle: create a distinguisher beginning at the middle of the cipher ¨ Then, determine a particular property linking plaintexts and ciphertexts ¨ Comparison withe complexity required to find such a structure for a random permutation n Interest: create distinguishers when block ciphers are used as hash functions Workshop MITACS - June 2009 28
![Theoritical model Africacrypt 09 n Advantage of Distinguishers Vaudenay 97 Adv EA n Two Theoritical model [Africacrypt 09] n Advantage of Distinguishers [Vaudenay 97]: Adv. E(A) n Two](https://slidetodoc.com/presentation_image/822e96eff449acb764e3c4a855cde949/image-29.jpg)
Theoritical model [Africacrypt 09] n Advantage of Distinguishers [Vaudenay 97]: Adv. E(A) n Two more cases: non-adaptative, adaptative Workshop MITACS - June 2009 29

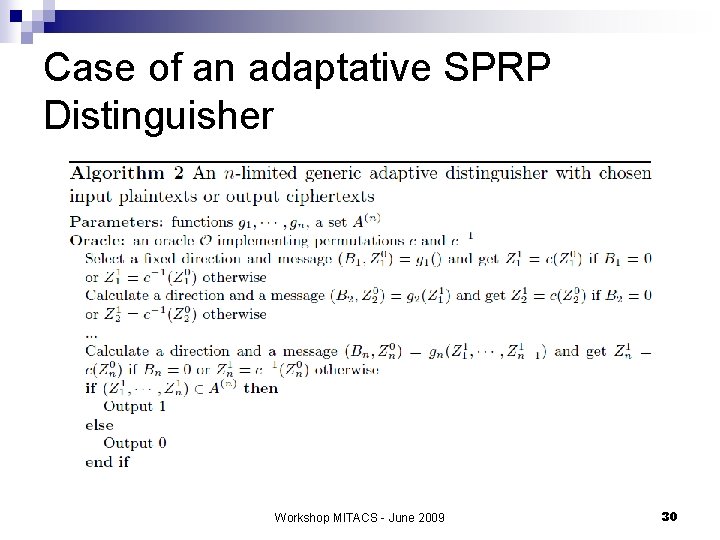
Case of an adaptative SPRP Distinguisher Workshop MITACS - June 2009 30

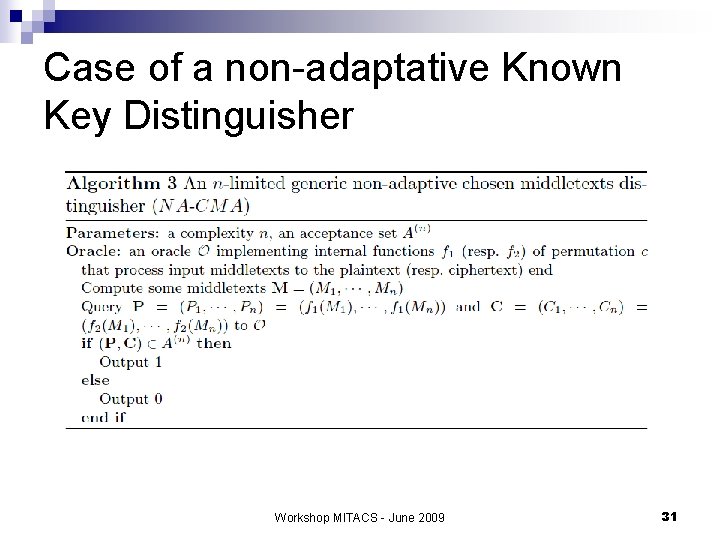
Case of a non-adaptative Known Key Distinguisher Workshop MITACS - June 2009 31
![Case of study the AES KnuRij 07 n Forward sense 0 0 0 n Case of study: the AES [Knu-Rij 07] n Forward sense =0 =0 =0 n](https://slidetodoc.com/presentation_image/822e96eff449acb764e3c4a855cde949/image-32.jpg)
Case of study: the AES [Knu-Rij 07] n Forward sense =0 =0 =0 n Backward sense =0 =0 =0 =0 =0 Workshop MITACS - June 2009 32

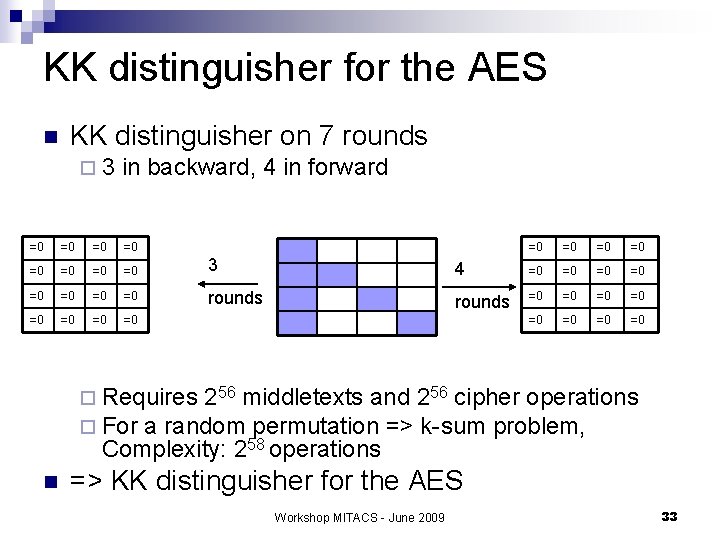
KK distinguisher for the AES n KK distinguisher on 7 rounds ¨ 3 in backward, 4 in forward =0 =0 3 =0 =0 rounds =0 =0 4 =0 =0 rounds =0 =0 ¨ Requires 256 middletexts and 256 cipher operations ¨ For a random permutation => k-sum problem, Complexity: 258 operations n => KK distinguisher for the AES Workshop MITACS - June 2009 33

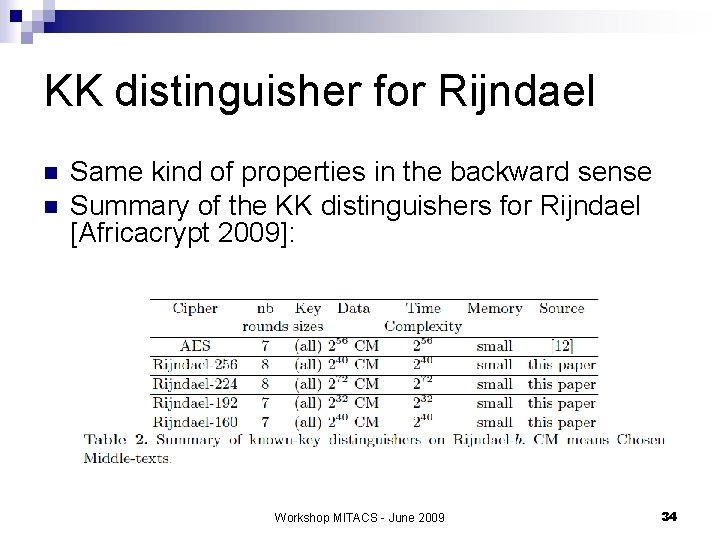
KK distinguisher for Rijndael n n Same kind of properties in the backward sense Summary of the KK distinguishers for Rijndael [Africacrypt 2009]: Workshop MITACS - June 2009 34

A last idea… Workshop MITACS - June 2009 35

LANE: SHA 3 hash function Hi = h 0 ||h 1 = 256 bits n Mi = m 0 ||m 1 ||m 2 ||m 3 = 512 bits n Pi = 6 modified AES rounds n Qi = 3 modified AES rounds n Workshop MITACS - June 2009 36

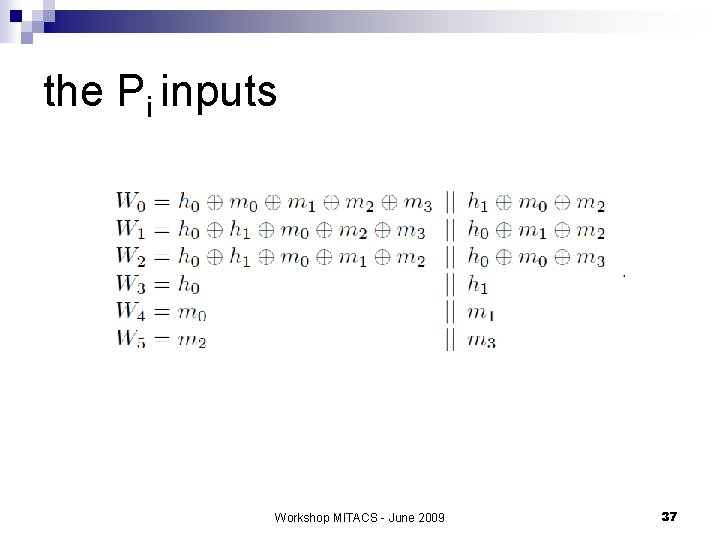
the Pi inputs Workshop MITACS - June 2009 37

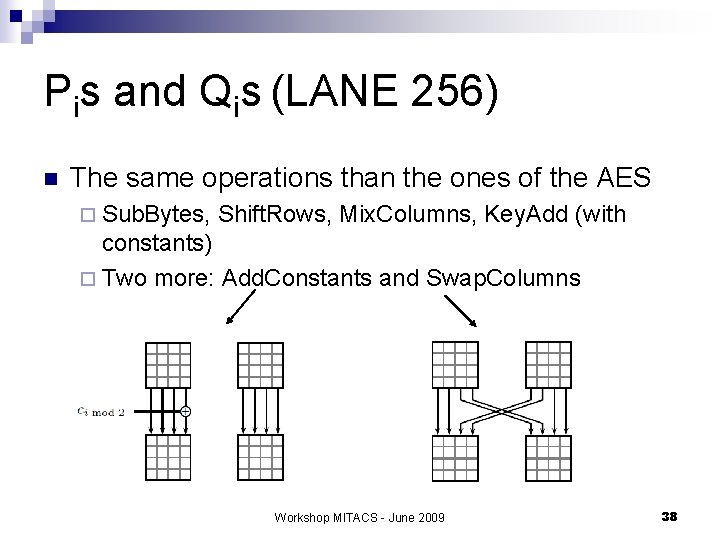
Pis and Qis (LANE 256) n The same operations than the ones of the AES ¨ Sub. Bytes, Shift. Rows, Mix. Columns, Key. Add (with constants) ¨ Two more: Add. Constants and Swap. Columns Workshop MITACS - June 2009 38

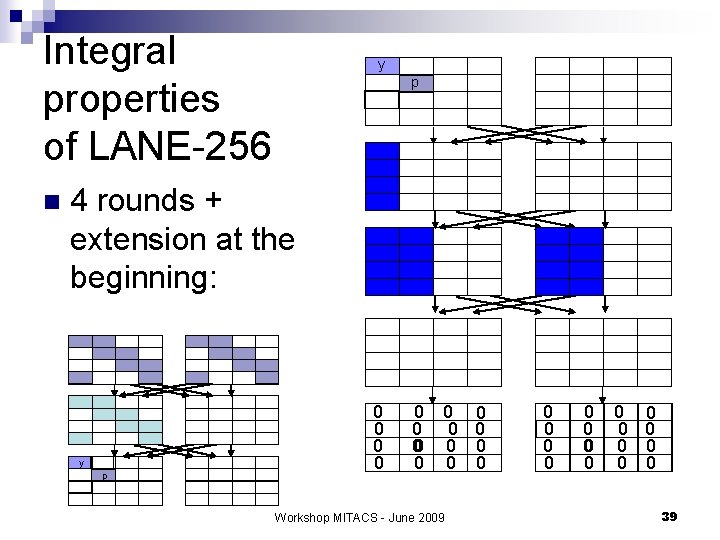
Integral properties of LANE-256 n y p 4 rounds + extension at the beginning: y p 0 0 0 0 Workshop MITACS - June 2009 0 0 0 0 39

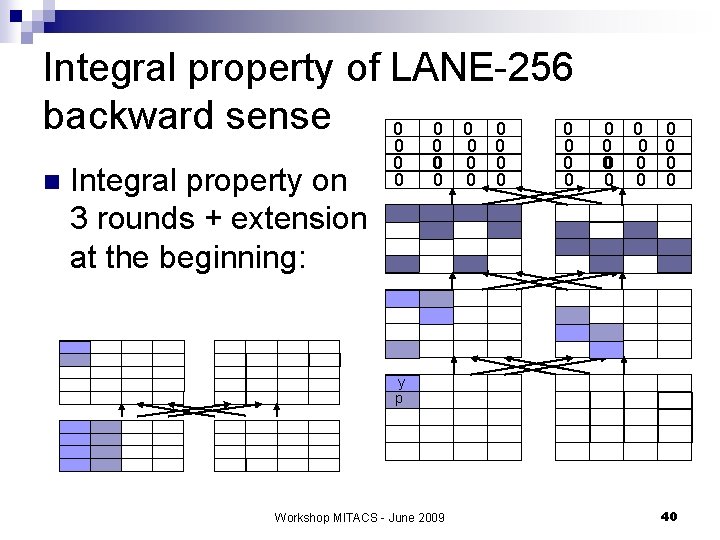
Integral property of LANE-256 backward sense 0 0 0 n Integral property on 3 rounds + extension at the beginning: 0 0 0 0 0 0 0 y p Workshop MITACS - June 2009 40

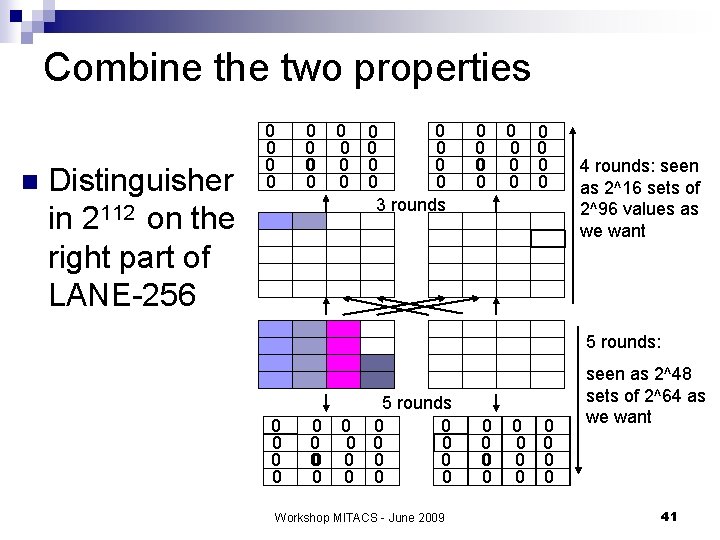
Combine the two properties n Distinguisher in 2112 on the right part of LANE-256 0 0 0 0 0 3 rounds 0 0 0 4 rounds: seen as 2^16 sets of 2^96 values as we want 5 rounds: 0 0 0 0 5 rounds 0 0 0 Workshop MITACS - June 2009 0 0 0 seen as 2^48 sets of 2^64 as we want 41

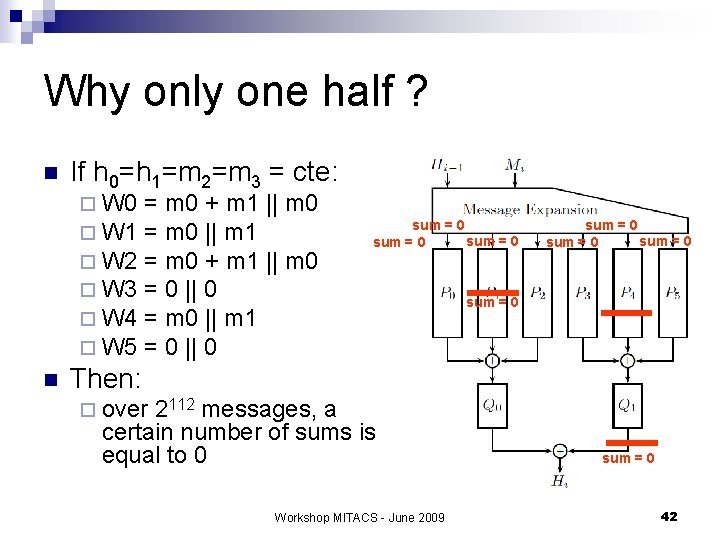
Why only one half ? n If h 0=h 1=m 2=m 3 = cte: ¨ W 0 ¨ W 1 ¨ W 2 ¨ W 3 ¨ W 4 ¨ W 5 n = m 0 + m 1 || m 0 = m 0 || m 1 = m 0 + m 1 || m 0 = 0 || 0 = m 0 || m 1 = 0 || 0 sum = 0 sum = 0 Then: ¨ over 2112 messages, a certain number of sums is equal to 0 Workshop MITACS - June 2009 sum = 0 42

Conclusion n Integral properties of Rijndael were not well studied ¨ Unknown Keys Distinguishers ¨ Known Keys Distinguishers n The last model is really useful to create distinguishers for the SHA-3 competition (cf: LANE) Workshop MITACS - June 2009 43
 Marine minier
Marine minier [email protected]
[email protected] Pigpen cipher creator
Pigpen cipher creator Aes proposal: rijndael
Aes proposal: rijndael Pauline minier
Pauline minier Vincent minier
Vincent minier Sponges invertebrates
Sponges invertebrates Integral berpangkat
Integral berpangkat Integral citation
Integral citation Integral garis dan integral permukaan
Integral garis dan integral permukaan Indefinite integrals vs definite
Indefinite integrals vs definite Integral foreign operation meaning
Integral foreign operation meaning Integral citation
Integral citation Negative integral exponent
Negative integral exponent What are some contact forces and some noncontact forces?
What are some contact forces and some noncontact forces? Some say the world will end in fire some say in ice
Some say the world will end in fire some say in ice God when you choose to leave mountains unmovable
God when you choose to leave mountains unmovable Sometimes you win some sometimes you lose some
Sometimes you win some sometimes you lose some Some say the world will end in fire some say in ice
Some say the world will end in fire some say in ice Cake countable or uncountable noun
Cake countable or uncountable noun Some may trust in horses
Some may trust in horses Chemical properties of matter
Chemical properties of matter Some properties of glass
Some properties of glass Nugrant
Nugrant Ucd irb
Ucd irb Purdue irb
Purdue irb Drexel citi training
Drexel citi training Msu irb
Msu irb Citi training ucf
Citi training ucf Citi bike data analysis
Citi bike data analysis Drexel citi training
Drexel citi training Protopatické čití
Protopatické čití Citi training wake forest
Citi training wake forest Balcon authorization citi
Balcon authorization citi Citi gtcc
Citi gtcc Nrff citi
Nrff citi Janki chudgar
Janki chudgar Carnegie mellon university research participants
Carnegie mellon university research participants Uvm citi training
Uvm citi training Istar chla
Istar chla Citi training uci
Citi training uci Ce înseamnă a citi
Ce înseamnă a citi Citi mission statement
Citi mission statement Cassandra stein
Cassandra stein