Some Ethical Hacking Case Studies Peter Wood First



























- Slides: 49

Some “Ethical Hacking” Case Studies Peter Wood First • Base Technologies

How much damage can a security breach cause? • 44% of UK businesses suffered at least one malicious security breach in 2002 • The average cost was £ 30, 000 • Several cost more than £ 500, 000 • and these are just the reported incidents …! Source: The DTI Information Security Breaches survey Slide 2 © First Base Technologies 2003

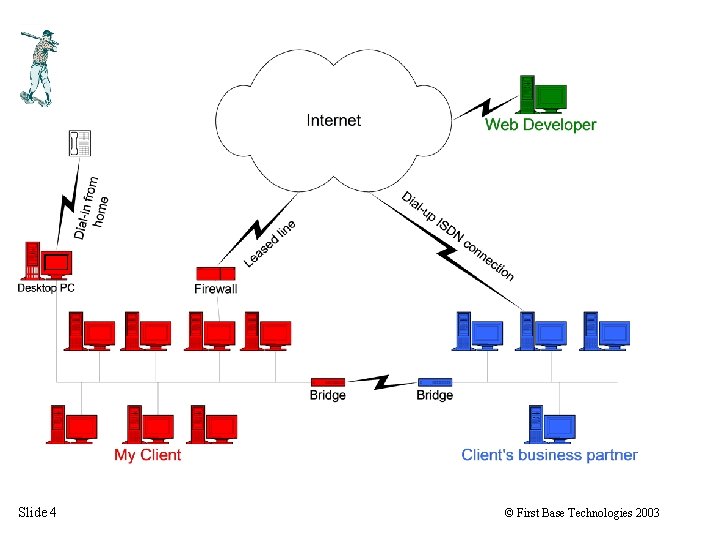
The External Hacker Slide 3 © First Base Technologies 2003

Slide 4 © First Base Technologies 2003

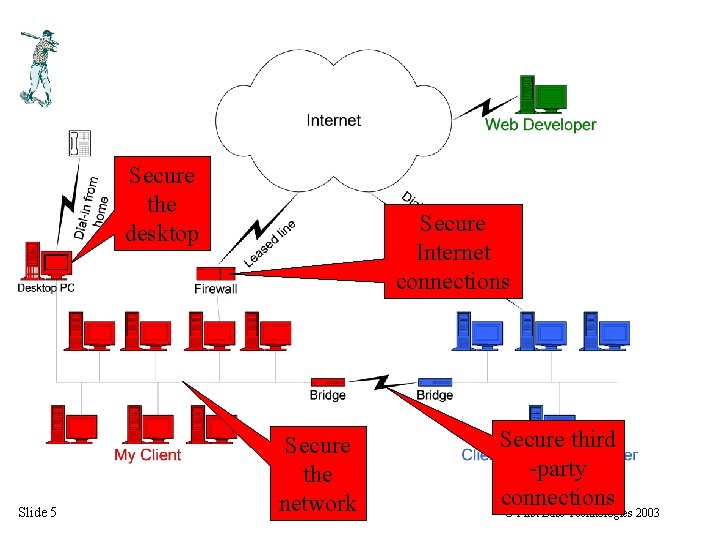
Secure the desktop Slide 5 Secure Internet connections Secure the network Secure third -party connections © First Base Technologies 2003

The Inside Hacker Slide 6 © First Base Technologies 2003

Plug and go Ethernet ports are never disabled …. … or just steal a connection from a desktop Net. BIOS tells you lots and lots …… …. And you don’t need to be logged on Slide 7 © First Base Technologies 2003

Get yourself an IP address • Use DHCP since almost everyone does! • Or … use a sniffer to see broadcast packets (even in a switched network) and try some suitable addresses Slide 8 © First Base Technologies 2003

Browse the network Slide 9 © First Base Technologies 2003

Pick a target machine Pick a target Slide 10 © First Base Technologies 2003

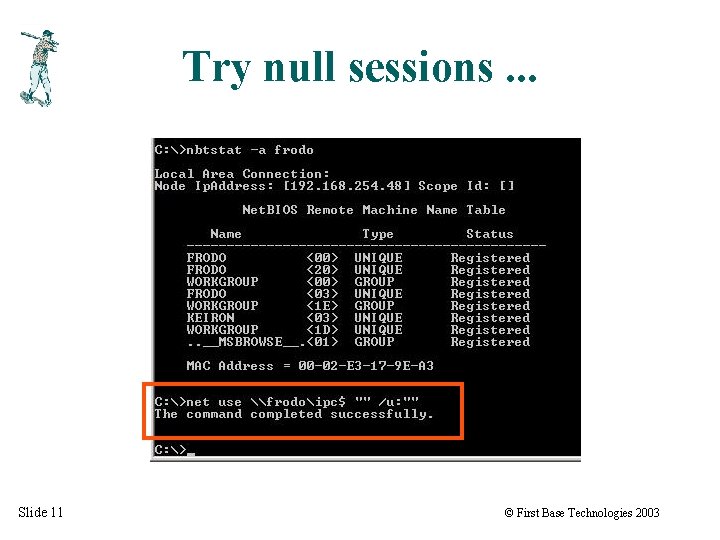
Try null sessions. . . Slide 11 © First Base Technologies 2003

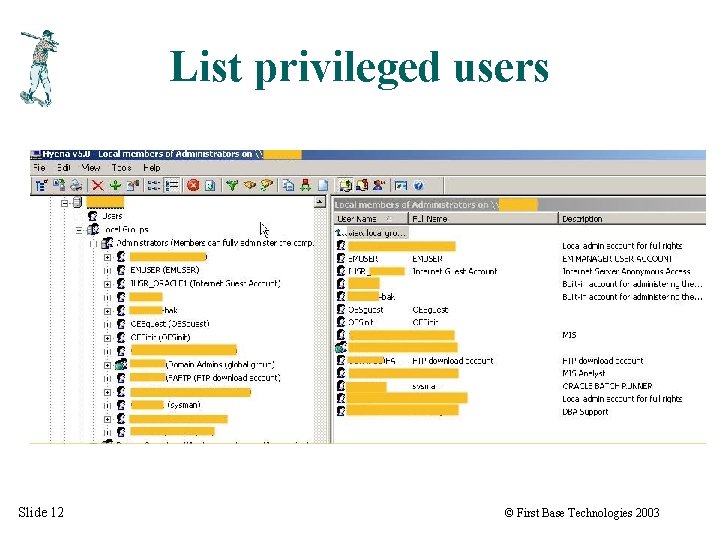
List privileged users Slide 12 © First Base Technologies 2003

Typical passwords • • • Slide 13 administrator arcserve test username backup tivoli backupexec smsservice … any service account null, password, administrator arcserve, backup test, password, monday, football backup tivoli backup smsservice … same as account name © First Base Technologies 2003

Game over! Slide 14 © First Base Technologies 2003

The Inside-Out Hacker Slide 15 © First Base Technologies 2003

Senior person - laptop at home Slide 16 © First Base Technologies 2003

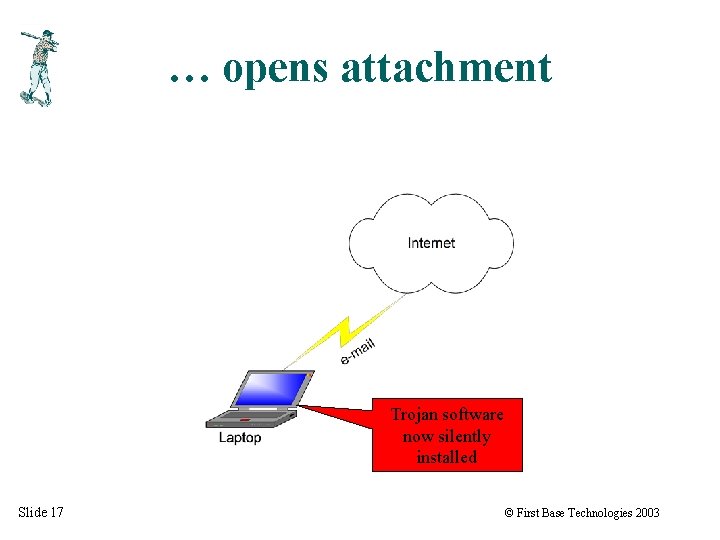
… opens attachment Trojan software now silently installed Slide 17 © First Base Technologies 2003

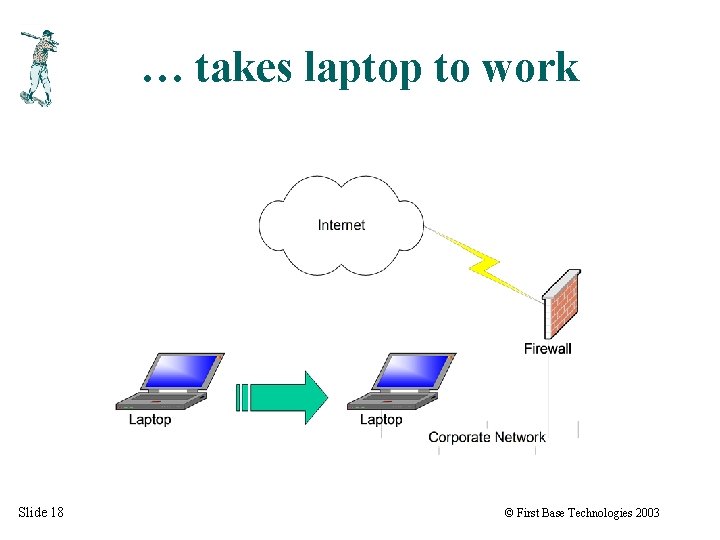
… takes laptop to work Slide 18 © First Base Technologies 2003

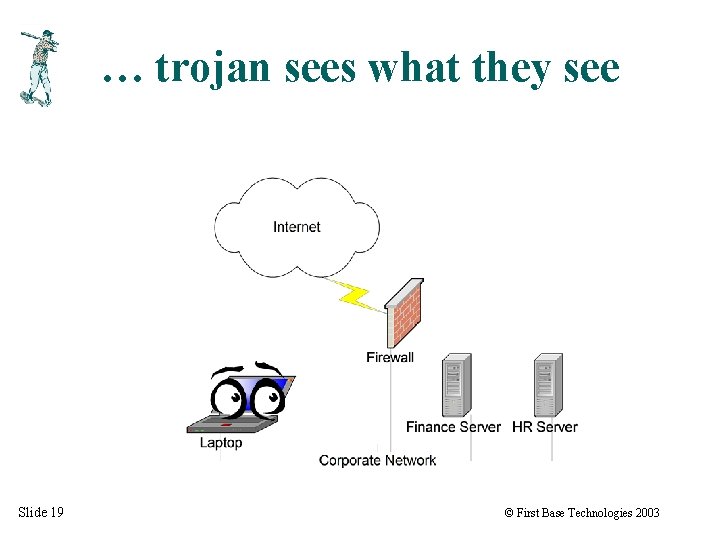
… trojan sees what they see Slide 19 © First Base Technologies 2003

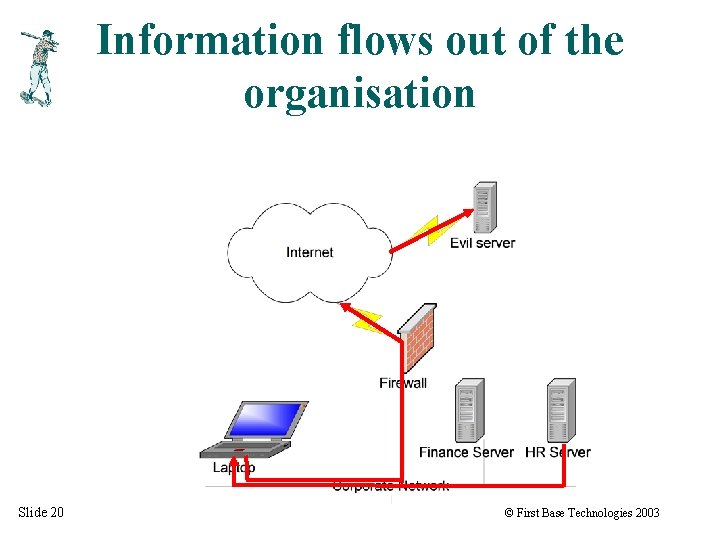
Information flows out of the organisation Slide 20 © First Base Technologies 2003

Physical Attacks Slide 21 © First Base Technologies 2003

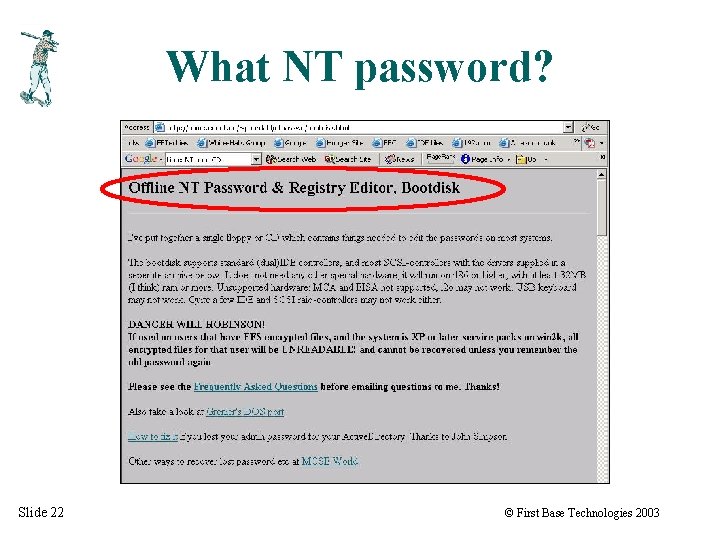
What NT password? Slide 22 © First Base Technologies 2003

NTFSDOS Slide 23 © First Base Technologies 2003

Keyghost Slide 24 © First Base Technologies 2003

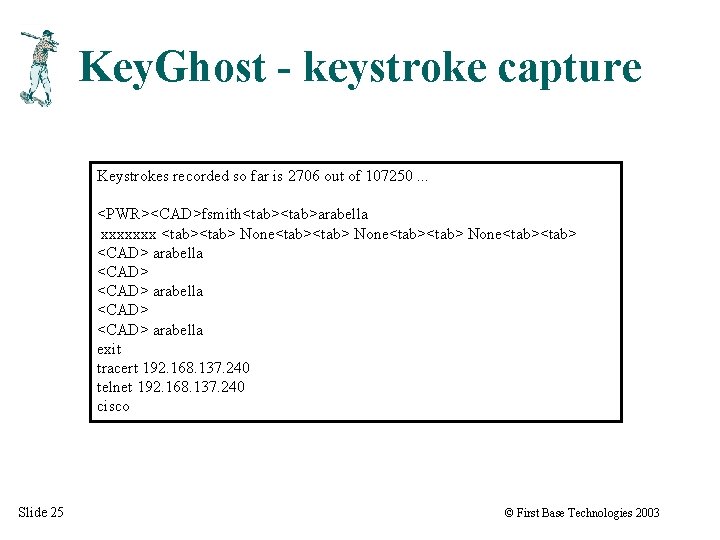
Key. Ghost - keystroke capture Keystrokes recorded so far is 2706 out of 107250. . . <PWR><CAD>fsmith<tab>arabella xxxxxxx <tab><tab> None<tab> <CAD> arabella <CAD> arabella exit tracert 192. 168. 137. 240 telnet 192. 168. 137. 240 cisco Slide 25 © First Base Technologies 2003

Viewing Password-Protected Files Slide 26 © First Base Technologies 2003

Office Documents Slide 27 © First Base Technologies 2003

Zip Files Slide 28 © First Base Technologies 2003

Plain Text Passwords Slide 29 © First Base Technologies 2003

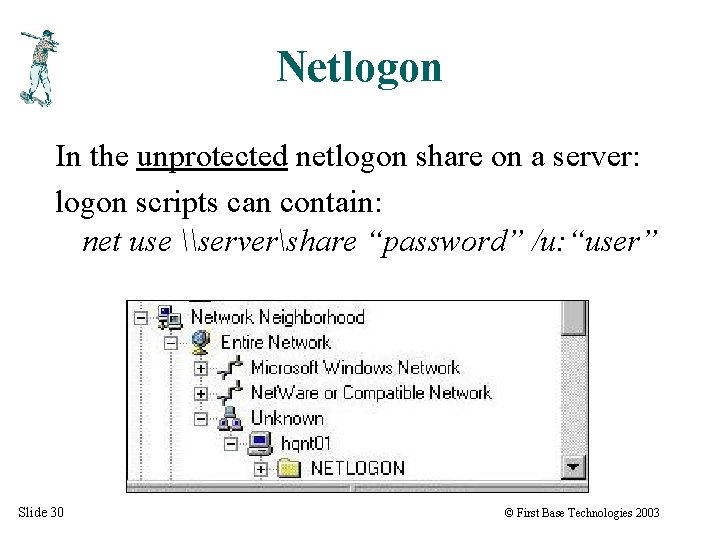
Netlogon In the unprotected netlogon share on a server: logon scripts can contain: net use \servershare “password” /u: “user” Slide 30 © First Base Technologies 2003

Registry scripts In shared directories you may find. reg files like this: [HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrent. VersionWinlogon] "Default. User. Name"="username" "Default. Password"="password" "Auto. Admin. Logon"="1" Slide 31 © First Base Technologies 2003

Passwords in procedures & documents Slide 32 © First Base Technologies 2003

Packet sniffing • Leave the sniffer running • Capture all packets to port 23 or 21 Generated by : TCP. demux V 1. 02 Input File: carol. cap Output File: TB 000463. txt Summary File: summary. txt Date Generated: Thu Jan 27 08: 43: 08 2000 10. 1. 1. 82 1036 10. 1. 2. 205 23 (telnet) Unix. Ware 2. 1. 3 (mikew) (pts/31). login: cl_Carol Password: • The result. . . carol 1 zz Unix. Ware 2. 1. 3. mikew. Copyright 1996 The Santa Cruz Operation, Inc. All Rights Reserved. . Copyright 1984 -1995 Novell, Inc. All Rights Reserved. . Copyright 1987, 1988 Microsoft Corp. All Rights Reserved. . U. S. Pat. No. 5, 349, 642. Slide 33 © First Base Technologies 2003

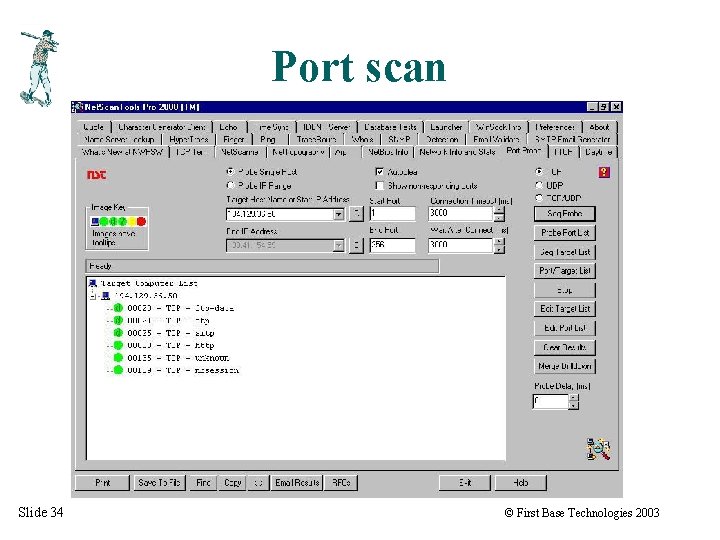
Port scan Slide 34 © First Base Technologies 2003

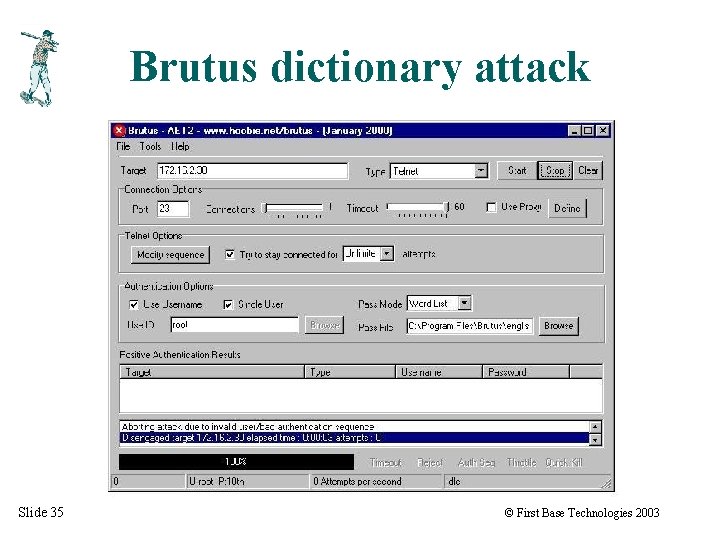
Brutus dictionary attack Slide 35 © First Base Technologies 2003

NT Password Cracking Slide 36 © First Base Technologies 2003

How to get the NT SAM • On any NT/W 2 K machine: - In memory (registry) c: winntrepairsam (invoke rdisk? ) Emergency Repair Disk Backup tapes Sniffing (L 0 phtcrack) • Run L 0 phtcrack on the SAM …. Slide 37 © First Base Technologies 2003

End of part one! Slide 38 © First Base Technologies 2003

And how to prevent it! Peter Wood First • Base Technologies

Prevention is better. . . • • Slide 40 Harden the servers Monitor alerts (e. g. www. sans. org) Scan, test and apply patches Monitor logs Good physical security Intrusion detection systems Train the technical staff on security Serious policy and procedures! © First Base Technologies 2003

Server hardening • • Slide 41 Hard. NT 40 rev 1. pdf (www. fbtechies. co. uk) Harden. W 2 K 101. pdf (www. fbtechies. co. uk) FAQ for How to Secure Windows NT (www. sans. org) Fundamental Steps to Harden Windows NT 4_0 (www. sans. org) ISF NT Checklist v 2 (www. securityforum. org) http: //www. microsoft. com/technet/ security/bestprac/default. asp Lockdown. pdf (www. iss. net) • • • Windows NT Security Guidelines (nsa 1. www. conxion. com) NTBugtraq FAQs (http: //ntbugtraq. ntadvice. com/defa ult. asp? pid=37&sid=1) Securing Windows 2000 (www. sans. org) Securing Windows 2000 Server (www. sans. org) Windows 2000 Known Vulnerabilities and Their Fixes (www. sans. org) SANS step-by-step guides © First Base Technologies 2003

Alerts • • Slide 42 www. sans. org www. cert. org www. microsoft. com/security www. ntbugtraq. com www. winnetmag. com razor. bindview. com eeye. com Security Pro News (ientrymail. com) © First Base Technologies 2003

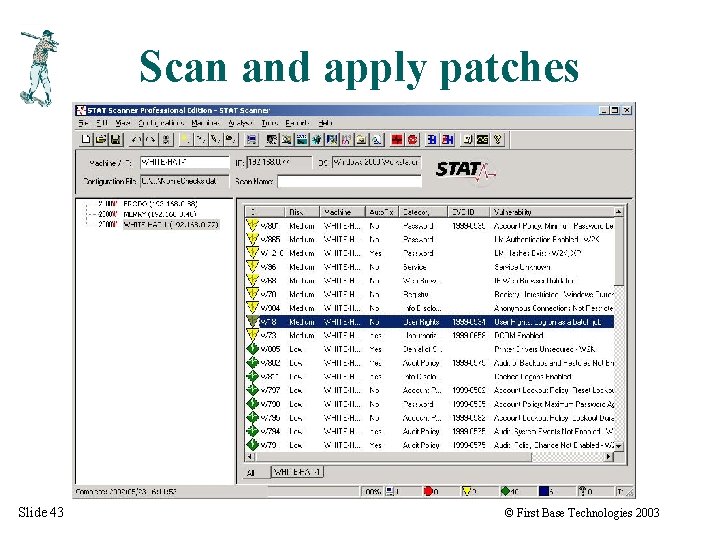
Scan and apply patches Slide 43 © First Base Technologies 2003

Monitor logs Slide 44 © First Base Technologies 2003

Good physical security • • • Slide 45 Perimeter security Computer room security Desktop security Close monitoring of admin’s work areas No floppy drives? No bootable CDs? © First Base Technologies 2003

Intrusion detection • • • Slide 46 Real. Secure Tripwire Dragon Snort www. networkintrusion. co. uk for guidance © First Base Technologies 2003

Security Awareness • • Slide 47 Sharing admin accounts Service accounts Account naming conventions Server naming conventions Hardening Passwords (understand NT passwords!) Two-factor authentication? © First Base Technologies 2003

Serious Policy & Procedures • • • Slide 48 Top-down commitment Investment Designed-in security Regular audits Regular penetration testing Education & awareness © First Base Technologies 2003

Need more information? Peter Wood peterw@firstbase. co. uk www. fbtechies. co. uk Slide 49 © First Base Technologies 2003