Solo Attacker Multi Attack Single Target Multiple Targets




























- Slides: 76






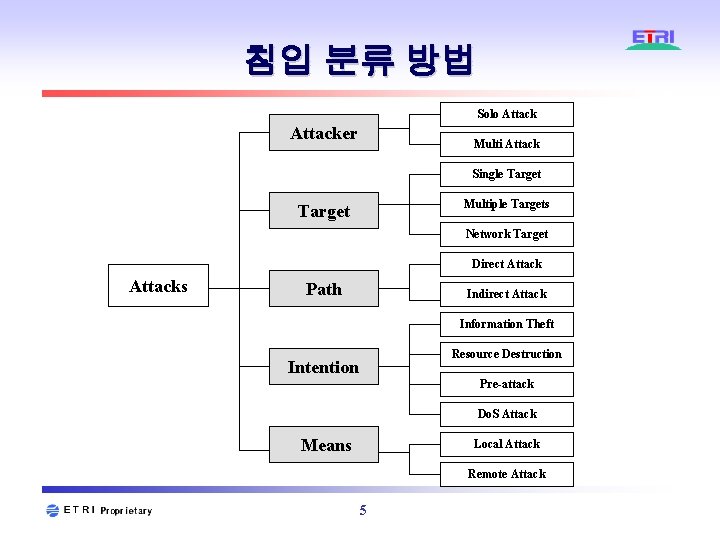
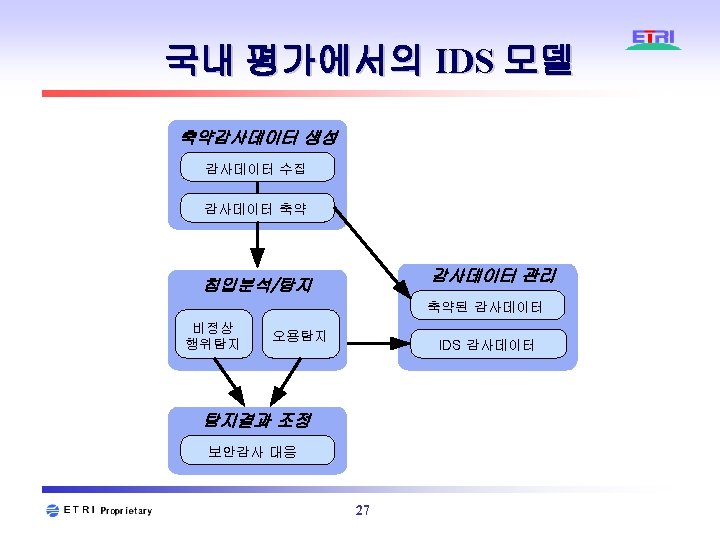
침입 분류 방법 Solo Attacker Multi Attack Single Target Multiple Targets Target Network Target Direct Attacks Path Indirect Attack Information Theft Resource Destruction Intention Pre-attack Do. S Attack Means Local Attack Remote Attack 5

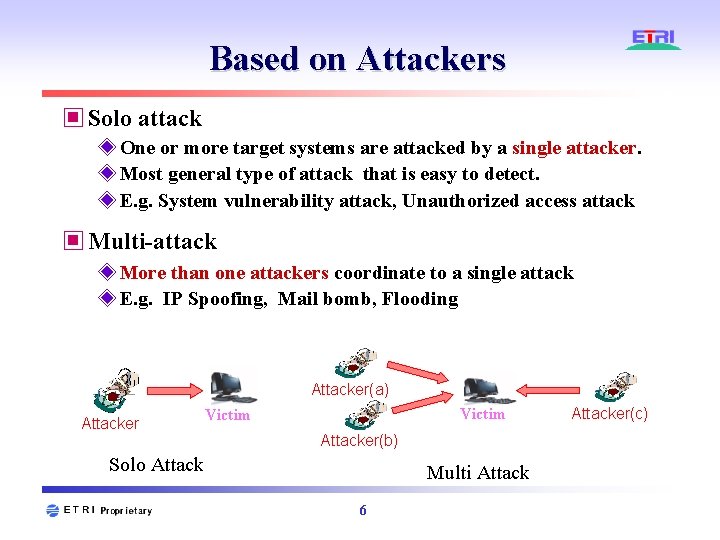
Based on Attackers ▣ Solo attack ◈ One or more target systems are attacked by a single attacker. ◈ Most general type of attack that is easy to detect. ◈ E. g. System vulnerability attack, Unauthorized access attack ▣ Multi-attack ◈ More than one attackers coordinate to a single attack ◈ E. g. IP Spoofing, Mail bomb, Flooding Attacker(a) Attacker Victim Attacker(b) Solo Attack Multi Attack 6 Attacker(c)

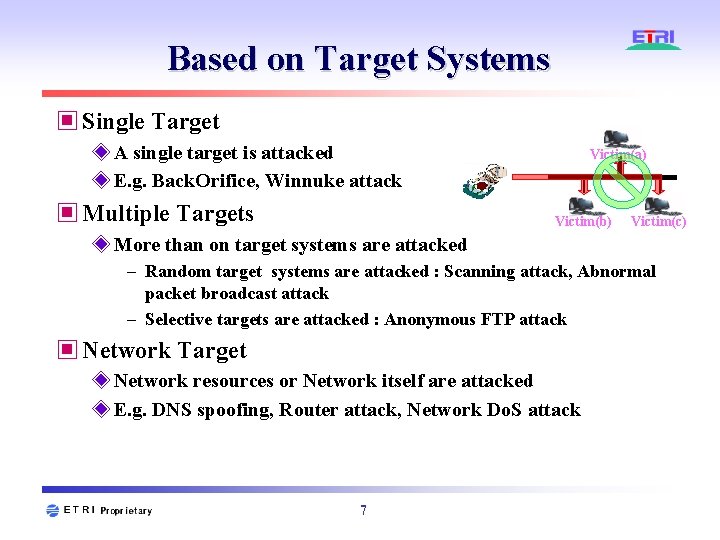
Based on Target Systems ▣ Single Target ◈ A single target is attacked ◈ E. g. Back. Orifice, Winnuke attack ▣ Multiple Targets Victim(a) Victim(b) Victim(c) ◈ More than on target systems are attacked – Random target systems are attacked : Scanning attack, Abnormal packet broadcast attack – Selective targets are attacked : Anonymous FTP attack ▣ Network Target ◈ Network resources or Network itself are attacked ◈ E. g. DNS spoofing, Router attack, Network Do. S attack 7

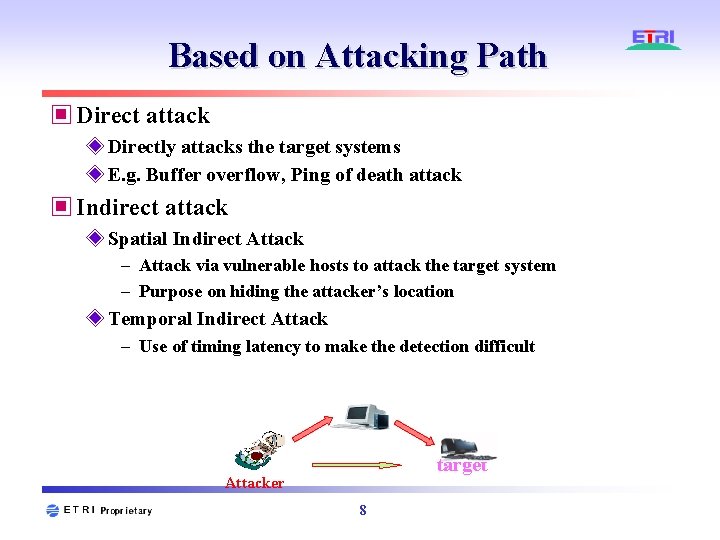
Based on Attacking Path ▣ Direct attack ◈ Directly attacks the target systems ◈ E. g. Buffer overflow, Ping of death attack ▣ Indirect attack ◈ Spatial Indirect Attack – Attack via vulnerable hosts to attack the target system – Purpose on hiding the attacker’s location ◈ Temporal Indirect Attack – Use of timing latency to make the detection difficult target Attacker 8

Other Types of Attacks ▣ Based on Intention ◈ Information Theft ◈ Resource Destruction ◈ Pre-attack ◈ Denial of Service Attack ▣ Based on Attacking Means ◈ Local Attack : attacks after login to the system ◈ Remote Attack : attack without login to the system for information theft or Do. S attack 9



Why Intrusion Detection System? ▣ The underlying systems have many vulnerabilities, but attacks are not effectively handled because of the limited technologies and economical reasons. ▣ It is difficult to reform the safe system due to high cost and already developed applications ▣ It is almost impossible to develop completely secure systems. ▣ Even secure systems have weak points to the inside attackers. 12

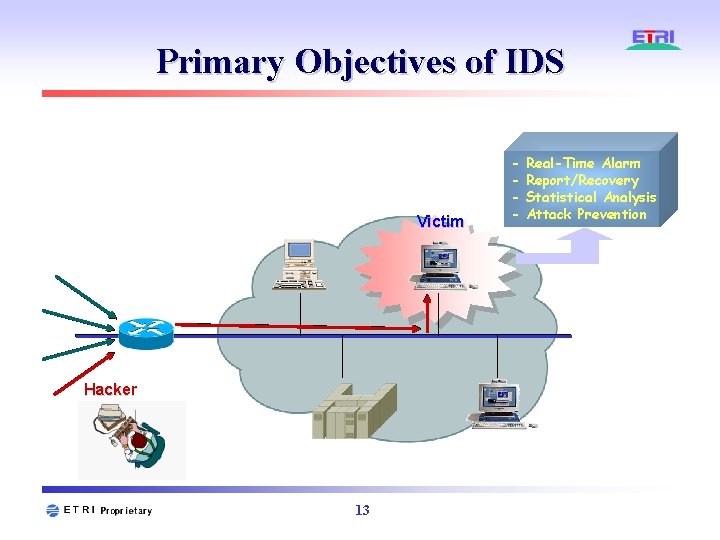
Primary Objectives of IDS Victim Hacker 13 - Real-Time Alarm Report/Recovery Statistical Analysis Attack Prevention

Real-Time Alarm and Response ▣Misused Action & Abnormal Behavior ◈ Denial of Service ◈Race Condition & Stack Overflow ◈Unauthorized System File Modification ◈Exposure to External or Internal Threats ◈Other Critical Intrusions ▣Alarm and Report via ◈System Console ◈E-mail ◈Web User Interface ▣Automated Responses 14

Statistical Analysis and Report ▣Generating Statistics Using ◈Audit log ◈Daily, weekly, monthly and yearly events ▣Statistics of ◈Intrusion attempts ◈Intrusion classes Statistics: IDS Audit Record 15

Building New Intrusion Types ▣Based on ◈Intrusion Event Collection and Analysis ◈Classification of Intrusion Attempts ▣Creating New Patterns of Abnormal Behaviors - Event Collection - & Analysis - Audit Log Analysis New Intrusion Pattern Generation 16


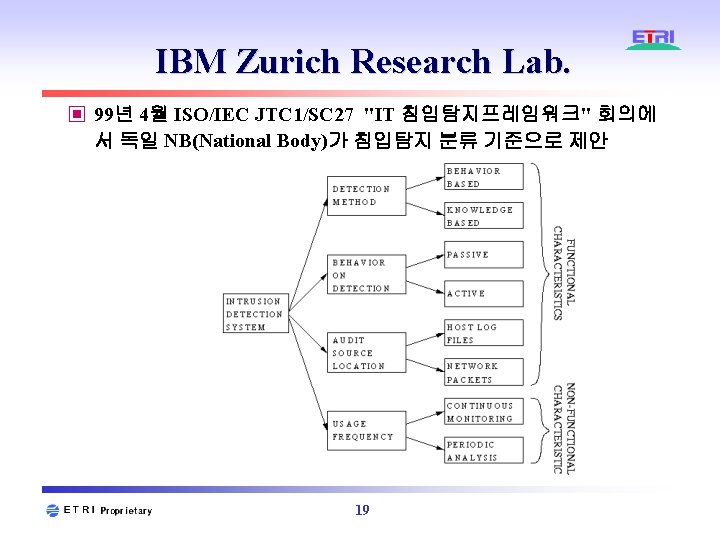
Purdue, COAST ▣ 국내에서 가장 많이 사용하는 분류 방식 ▣ 침입모델을 기반으로 하는 분류 ◈ Misuse Detection ◈ Anomaly Detection ◈ Hybrid Detection ▣ Data Source를 기반으로 하는 분류 ◈ Host Based Detection ◈ Multi-Host Based Detection ◈ Network Based 18


ICSA IDSC ▣ ICSA가 침입탐지시스템 평가를 준비하기 위하여 분류 ▣ 모니터링 접근방식에 따른 분류 ◈ Application Based ◈ Host Based ◈ Target Based ◈ Network Based ◈ Integrated ▣ 감사데이터의 분석 시점에 따른 분류 ◈ Batch/Interval Analysis ◈ Real Time Analysis ▣ 침입 분석 기법에 따른 분류 ◈ Signature Analysis ◈ Statistical Analysis ◈ Integrity Analysis 20

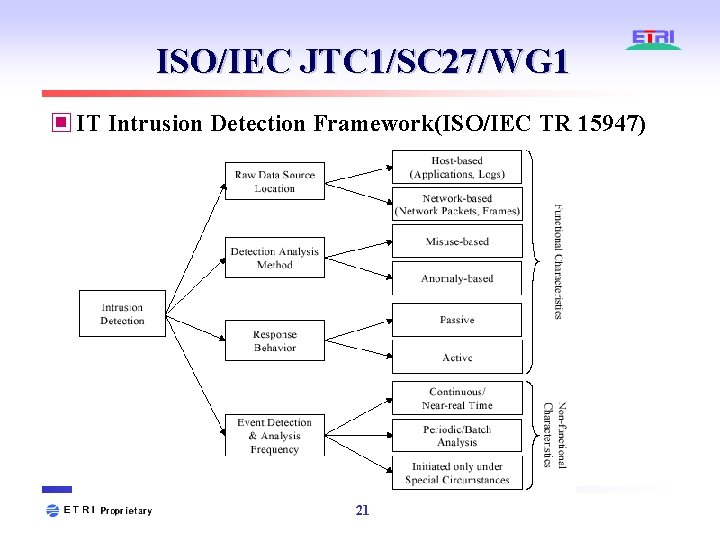
ISO/IEC JTC 1/SC 27/WG 1 ▣ IT Intrusion Detection Framework(ISO/IEC TR 15947) 21


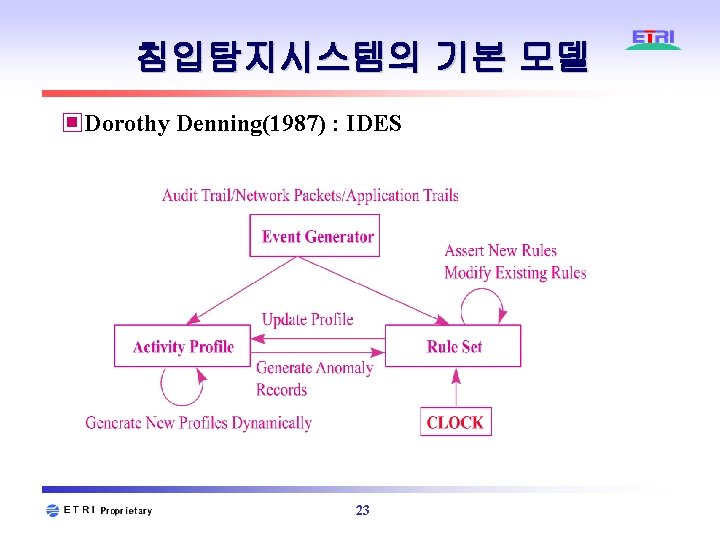
침입탐지시스템의 기본 모델 ▣Dorothy Denning(1987) : IDES 23

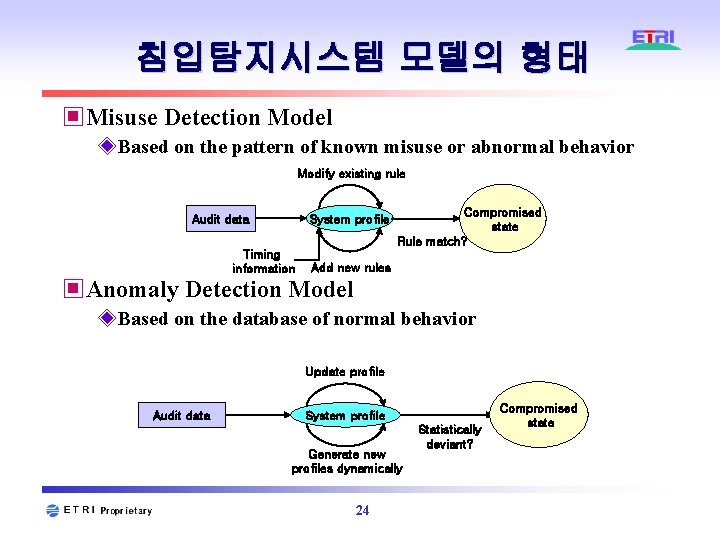
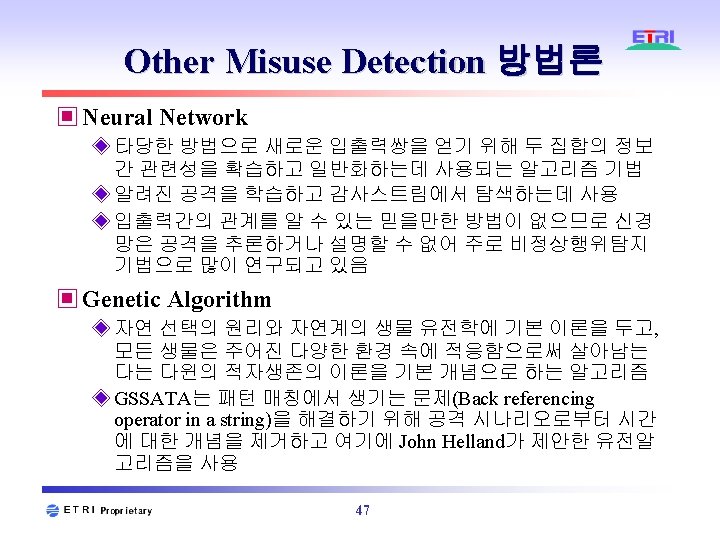
침입탐지시스템 모델의 형태 ▣Misuse Detection Model ◈Based on the pattern of known misuse or abnormal behavior Modify existing rule System profile Audit data Timing information Compromised state Rule match? Add new rules ▣Anomaly Detection Model ◈Based on the database of normal behavior Update profile Audit data System profile Generate new profiles dynamically 24 Statistically deviant? Compromised state

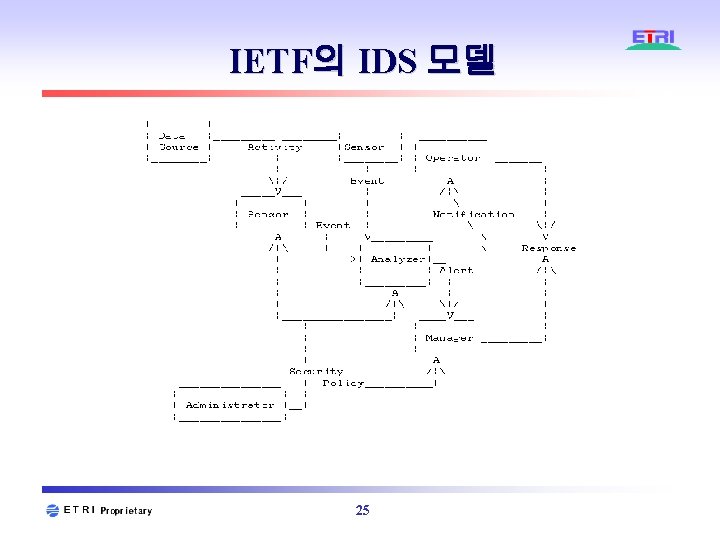
IETF의 IDS 모델 25

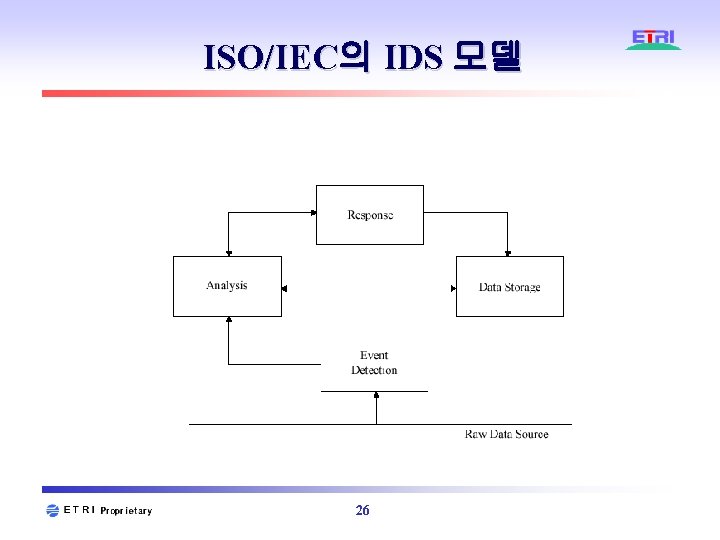
ISO/IEC의 IDS 모델 26



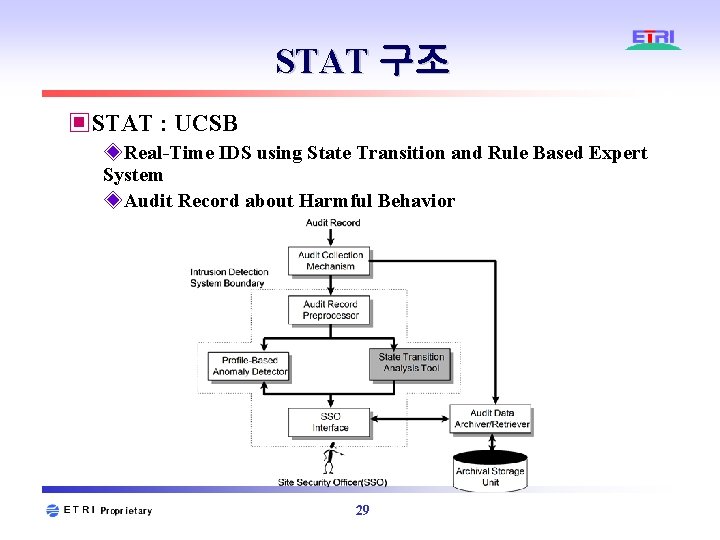
STAT 구조 ▣STAT : UCSB ◈Real-Time IDS using State Transition and Rule Based Expert System ◈Audit Record about Harmful Behavior 29

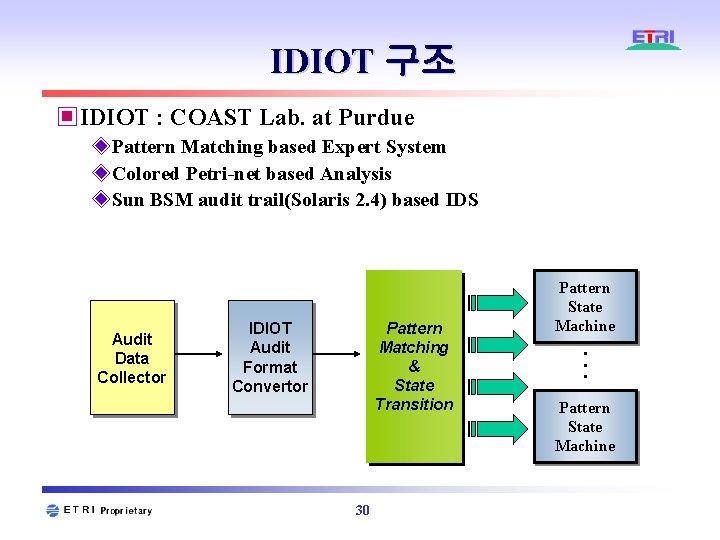
IDIOT 구조 ▣IDIOT : COAST Lab. at Purdue ◈Pattern Matching based Expert System ◈Colored Petri-net based Analysis ◈Sun BSM audit trail(Solaris 2. 4) based IDS Audit Data Collector Pattern Matching & State Transition IDIOT Audit Format Convertor 30 Pattern State Machine . . . Pattern State Machine

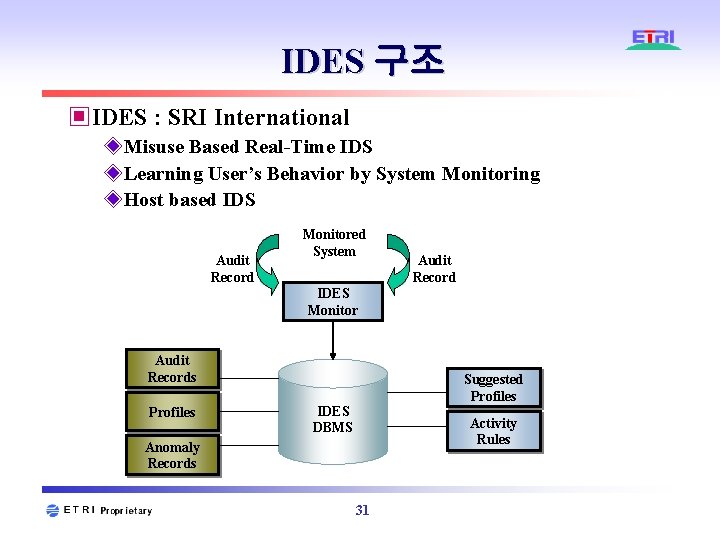
IDES 구조 ▣IDES : SRI International ◈Misuse Based Real-Time IDS ◈Learning User’s Behavior by System Monitoring ◈Host based IDS Audit Record Monitored System Audit Record IDES Monitor Audit Records Profiles Suggested Profiles IDES DBMS Activity Rules Anomaly Records 31

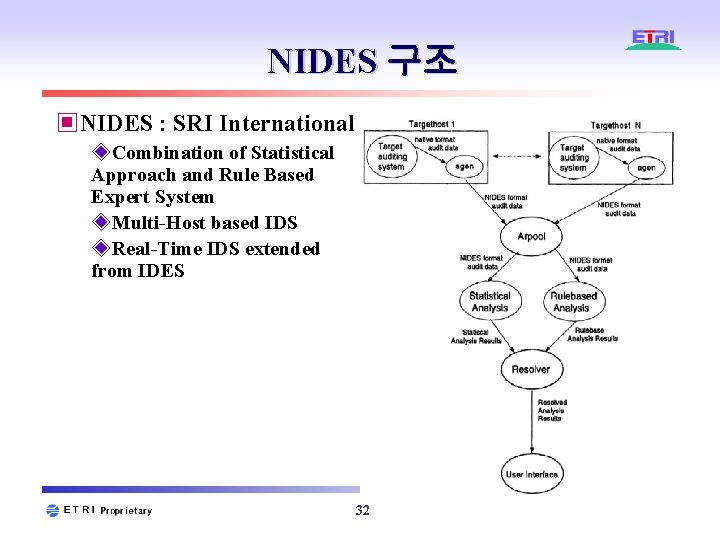
NIDES 구조 ▣NIDES : SRI International ◈Combination of Statistical Approach and Rule Based Expert System ◈Multi-Host based IDS ◈Real-Time IDS extended from IDES 32

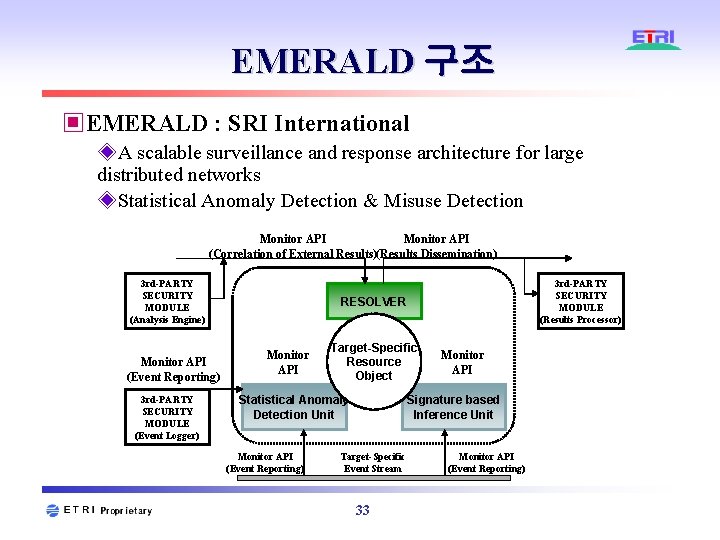
EMERALD 구조 ▣EMERALD : SRI International ◈A scalable surveillance and response architecture for large distributed networks ◈Statistical Anomaly Detection & Misuse Detection Monitor API (Correlation of External Results)(Results Dissemination) 3 rd-PARTY SECURITY MODULE (Analysis Engine) Monitor API (Event Reporting) 3 rd-PARTY SECURITY MODULE (Event Logger) 3 rd-PARTY SECURITY MODULE (Results Processor) RESOLVER Monitor API Target-Specific Resource Object Statistical Anomaly Detection Unit Monitor API (Event Reporting) Monitor API Signature based Inference Unit Target-Specific Event Stream 33 Monitor API (Event Reporting)

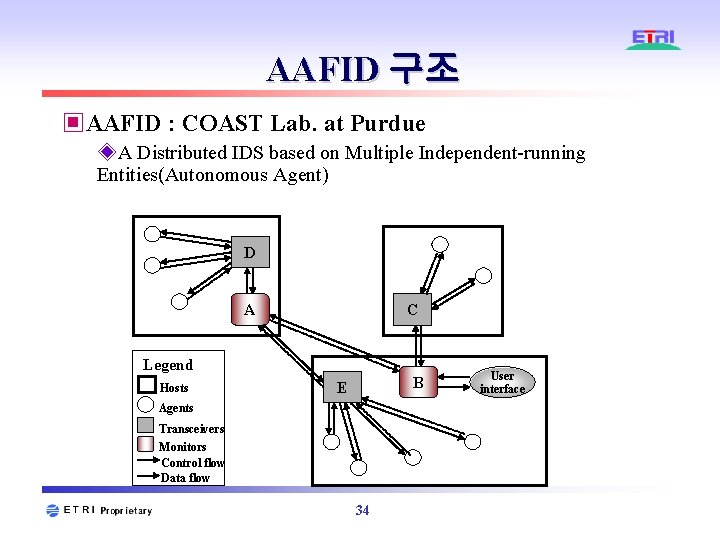
AAFID 구조 ▣AAFID : COAST Lab. at Purdue ◈A Distributed IDS based on Multiple Independent-running Entities(Autonomous Agent) D A C Legend Hosts B E Agents Transceivers Monitors Control flow Data flow 34 User interface

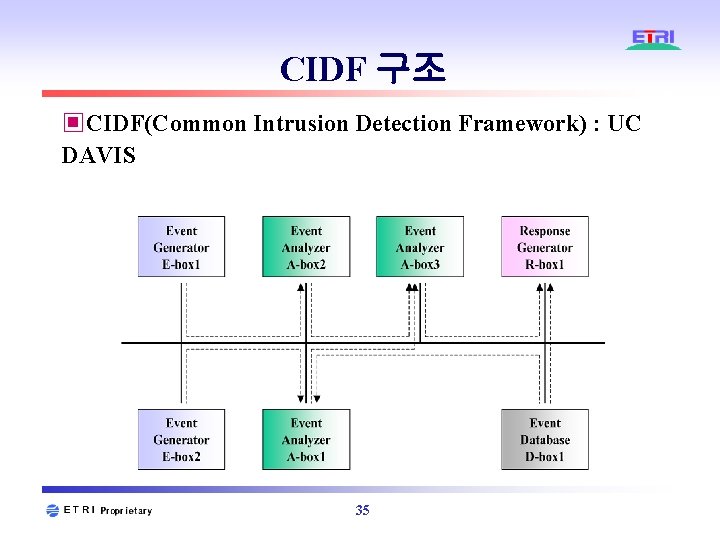
CIDF 구조 ▣CIDF(Common Intrusion Detection Framework) : UC DAVIS 35

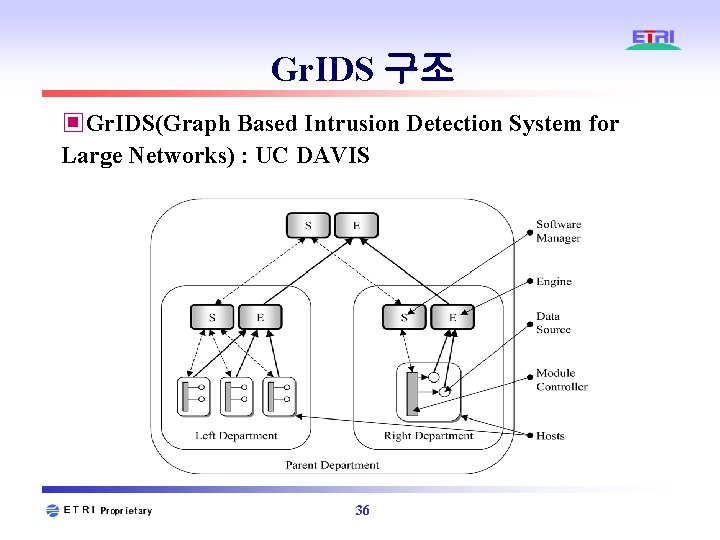
Gr. IDS 구조 ▣Gr. IDS(Graph Based Intrusion Detection System for Large Networks) : UC DAVIS 36

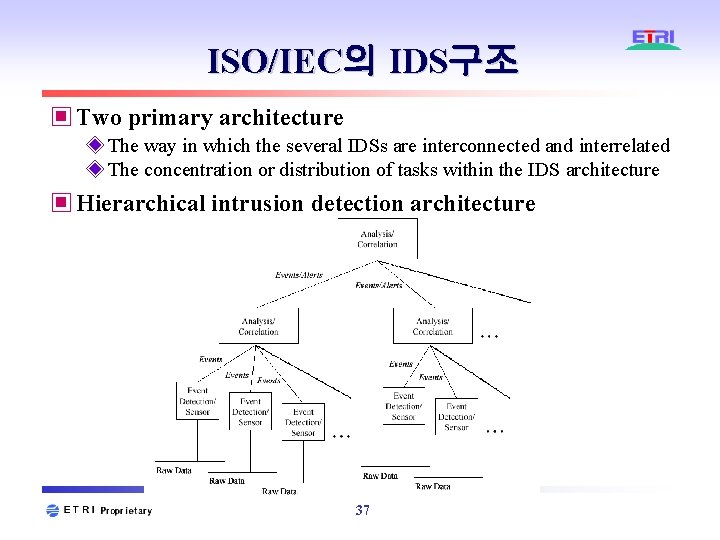
ISO/IEC의 IDS구조 ▣ Two primary architecture ◈ The way in which the several IDSs are interconnected and interrelated ◈ The concentration or distribution of tasks within the IDS architecture ▣ Hierarchical intrusion detection architecture 37

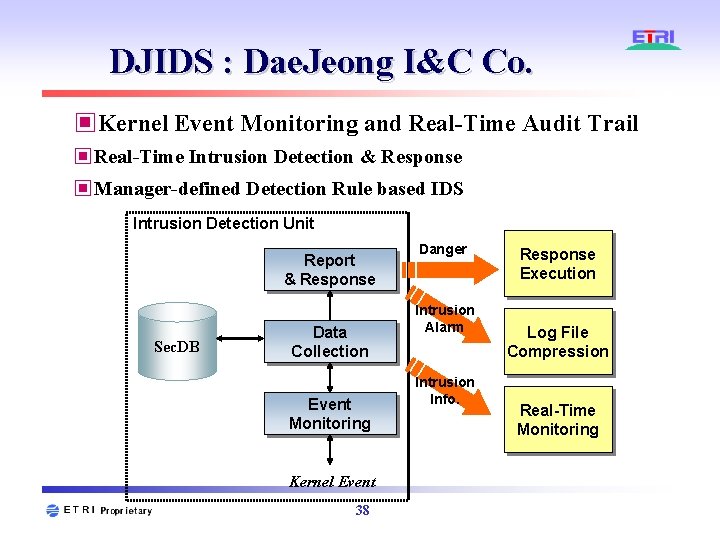
DJIDS : Dae. Jeong I&C Co. ▣Kernel Event Monitoring and Real-Time Audit Trail ▣Real-Time Intrusion Detection & Response ▣Manager-defined Detection Rule based IDS Intrusion Detection Unit Report & Response Sec. DB Data Collection Event Monitoring Kernel Event 38 Danger Intrusion Alarm Intrusion Info. Response Execution Log File Compression Real-Time Monitoring

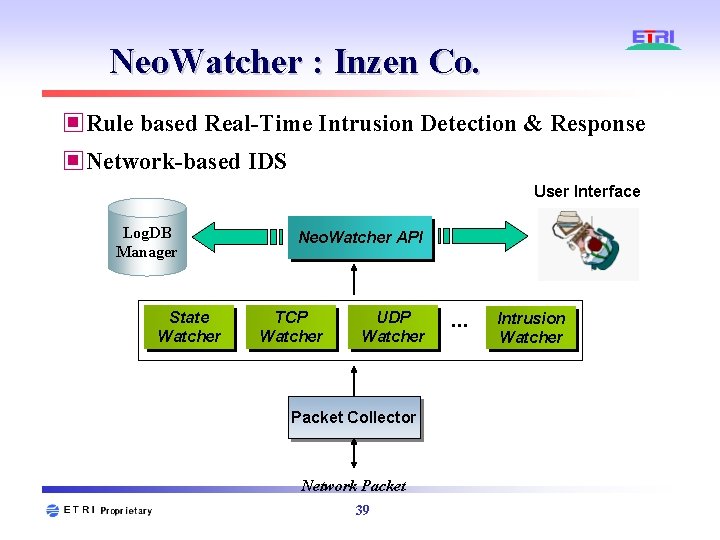
Neo. Watcher : Inzen Co. ▣Rule based Real-Time Intrusion Detection & Response ▣Network-based IDS User Interface Log. DB Manager State Watcher Neo. Watcher API TCP Watcher UDP Watcher Packet Collector Network Packet 39 . . . Intrusion Watcher

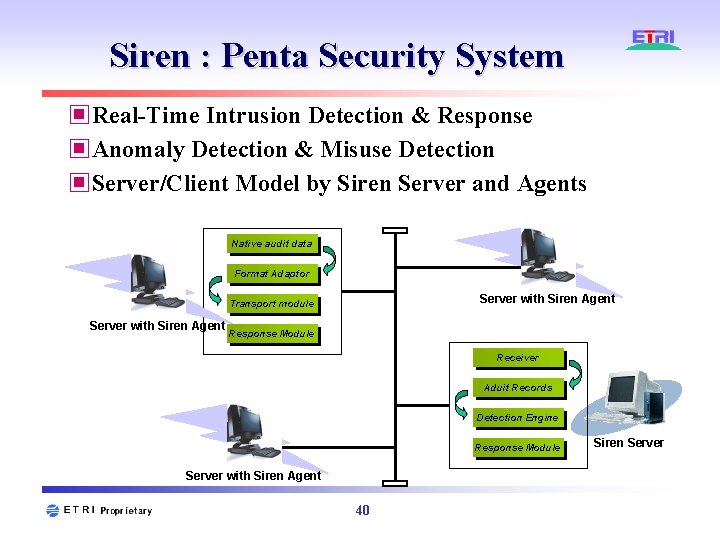
Siren : Penta Security System ▣Real-Time Intrusion Detection & Response ▣Anomaly Detection & Misuse Detection ▣Server/Client Model by Siren Server and Agents Native audit data Format Adaptor Server with Siren Agent Transport module Server with Siren Agent Response Module Receiver Aduit Records Detection Engine Response Module Server with Siren Agent 40 Siren Server


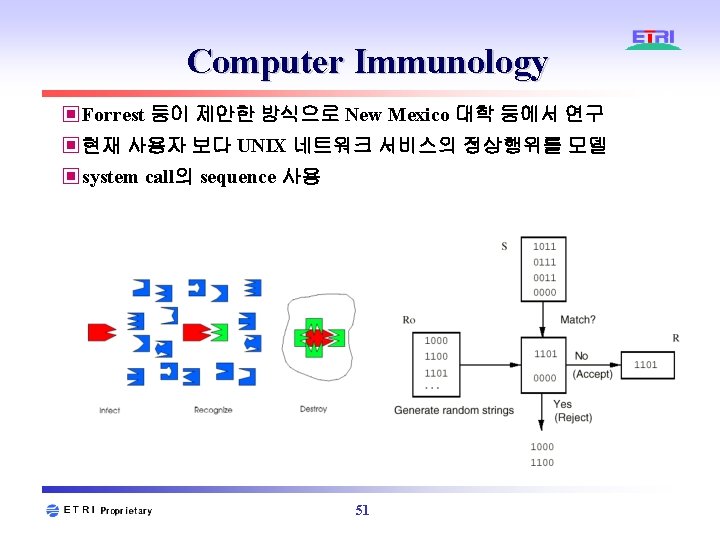
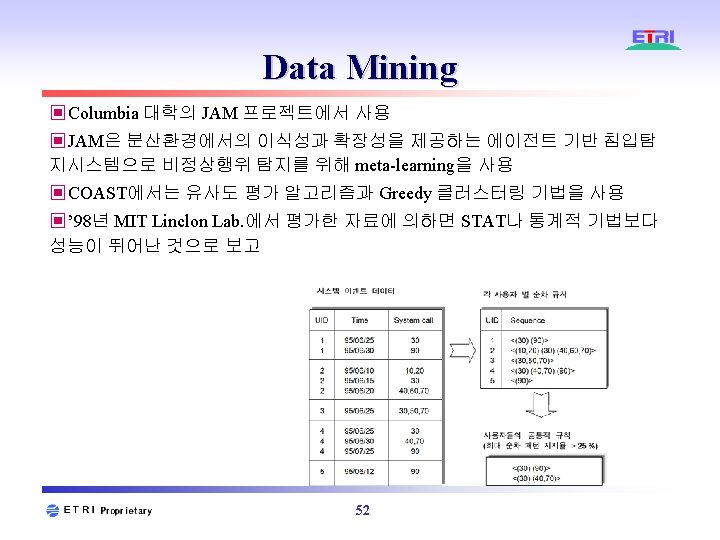
침입탐지 방법론 ▣ Misuse Detection ◈ Signature Analysis ◈ Expert Systems ◈ State-Transition Analysis ◈ Petri-nets 등 ▣ Anomaly Detection ◈ Statistics ◈ Expert Systems ◈ Computer Immunology ◈ Data Mining ◈ HMM 등 42

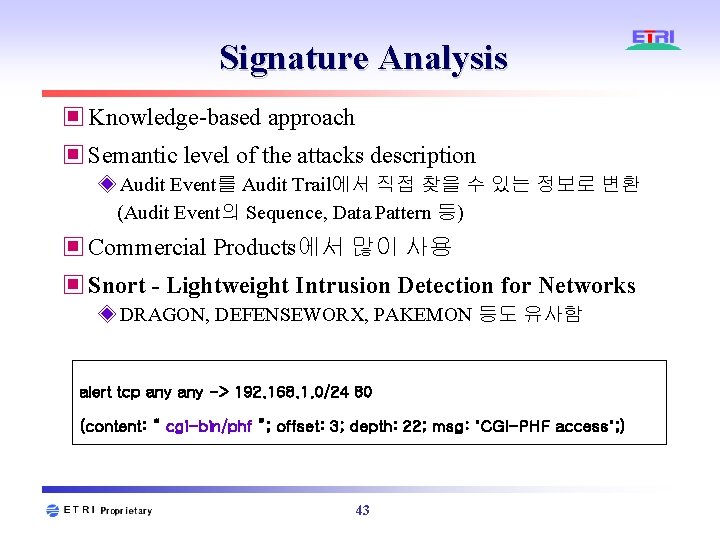
Signature Analysis ▣ Knowledge-based approach ▣ Semantic level of the attacks description ◈ Audit Event를 Audit Trail에서 직접 찾을 수 있는 정보로 변환 (Audit Event의 Sequence, Data Pattern 등) ▣ Commercial Products에서 많이 사용 ▣ Snort - Lightweight Intrusion Detection for Networks ◈ DRAGON, DEFENSEWORX, PAKEMON 등도 유사함 alert tcp any -> 192. 168. 1. 0/24 80 (content: “ cgi-bin/phf ”; offset: 3; depth: 22; msg: "CGI-PHF access"; ) 43

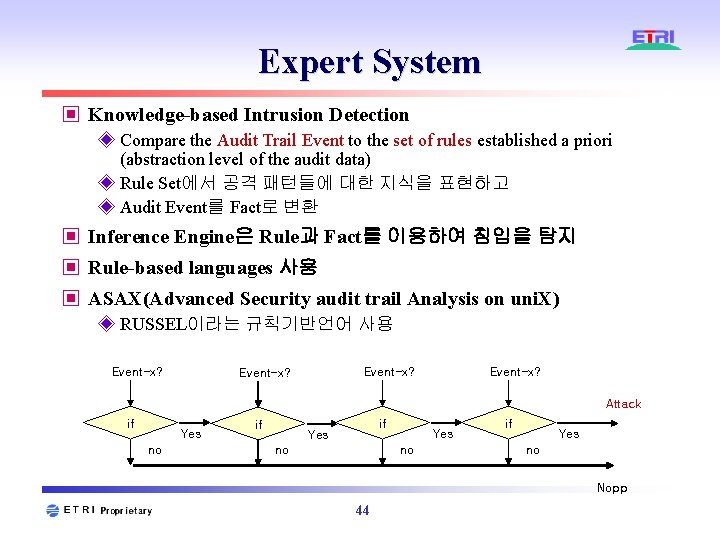
Expert System ▣ Knowledge-based Intrusion Detection ◈ Compare the Audit Trail Event to the set of rules established a priori (abstraction level of the audit data) ◈ Rule Set에서 공격 패턴들에 대한 지식을 표현하고 ◈ Audit Event를 Fact로 변환 ▣ Inference Engine은 Rule과 Fact를 이용하여 침입을 탐지 ▣ Rule-based languages 사용 ▣ ASAX(Advanced Security audit trail Analysis on uni. X) ◈ RUSSEL이라는 규칙기반언어 사용 Event-x? Attack if Yes no if if Yes no no if Yes no Nopp 44

State Transition Analysis ▣ State Transition을 이용하여 해킹을 표현, UCSB에서 개 발 ▣ USTAT, Net. STAT 등 45

Colored Petri-Net ▣ Knowledge-based Intrusion Detection ▣ Colored Petri Nets(CPN)을 사용하여 Purdue University에서 개발 ▣ 개념적 단순화, 그래픽한 표현 가능 ▣ 복잡한 Signature를 쉽게 표기 ▣ Purdue의 IDIOT 46



Expert System ▣ Rule-based Anomaly Detection ▣ usage pattern을 표현하는 rule set 사용 ▣ Wisdom & Sense ◈ 주기적 사용자 activity 기록 ® inconsistant behavior를 탐지 ◈ 사용자 행위를 통계적으로 표현 ▣ Computer. Watch ◈ usage policy를 표현한 rule set 사용 49





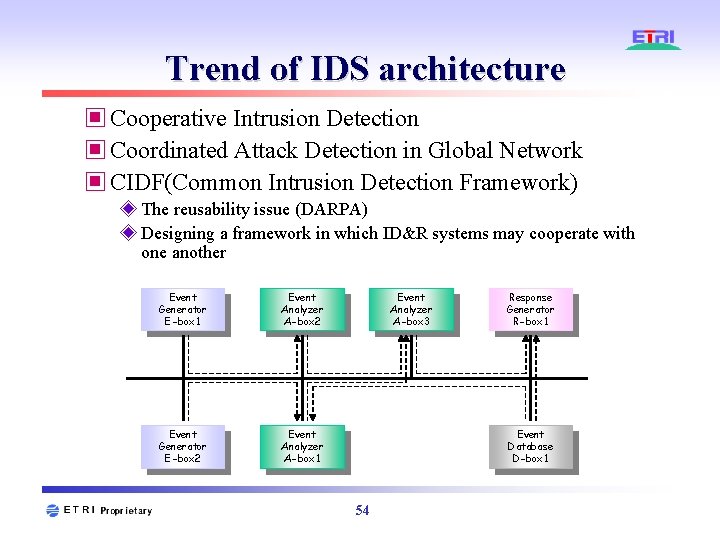
Trend of IDS architecture ▣ Cooperative Intrusion Detection ▣ Coordinated Attack Detection in Global Network ▣ CIDF(Common Intrusion Detection Framework) ◈ The reusability issue (DARPA) ◈ Designing a framework in which ID&R systems may cooperate with one another Event Generator E-box 1 Event Analyzer A-box 2 Event Generator E-box 2 Event Analyzer A-box 1 Event Analyzer A-box 3 Response Generator R-box 1 Event Database D-box 1 54

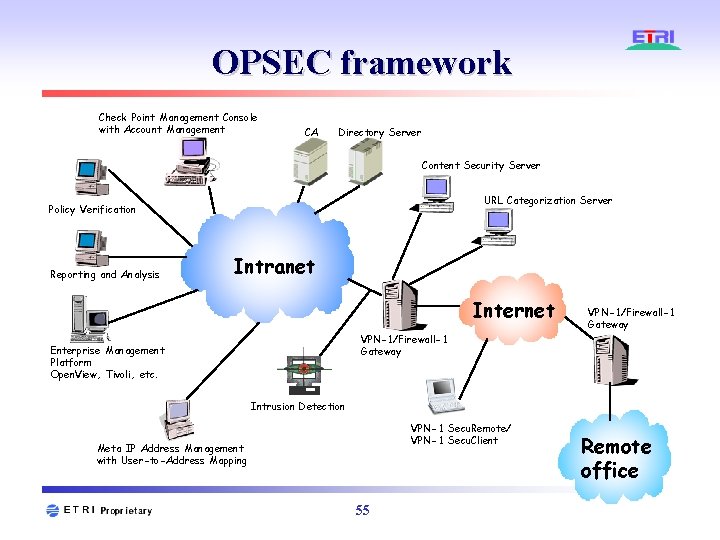
OPSEC framework Check Point Management Console with Account Management CA Directory Server Content Security Server URL Categorization Server Policy Verification Reporting and Analysis Intranet Internet VPN-1/Firewall-1 Gateway Enterprise Management Platform Open. View, Tivoli, etc. Intrusion Detection VPN-1 Secu. Remote/ VPN-1 Secu. Client Meta IP Address Management with User-to-Address Mapping 55 Remote office

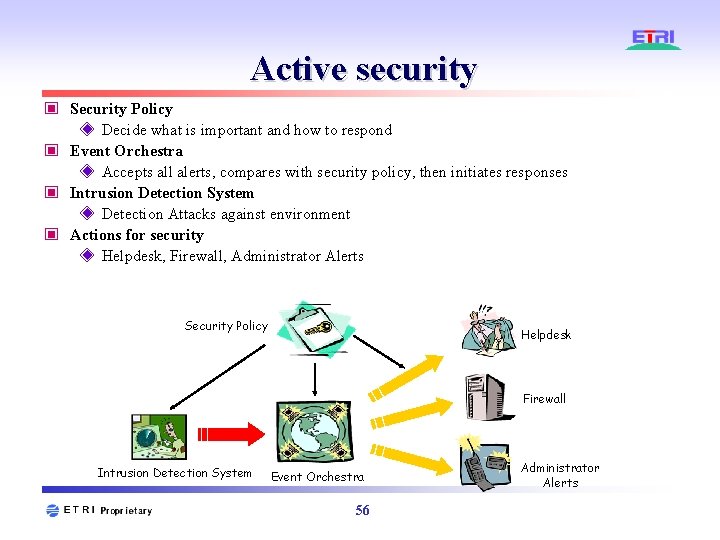
Active security ▣ Security Policy ◈ Decide what is important and how to respond ▣ Event Orchestra ◈ Accepts all alerts, compares with security policy, then initiates responses ▣ Intrusion Detection System ◈ Detection Attacks against environment ▣ Actions for security ◈ Helpdesk, Firewall, Administrator Alerts Security Policy Helpdesk Firewall Intrusion Detection System Event Orchestra 56 Administrator Alerts

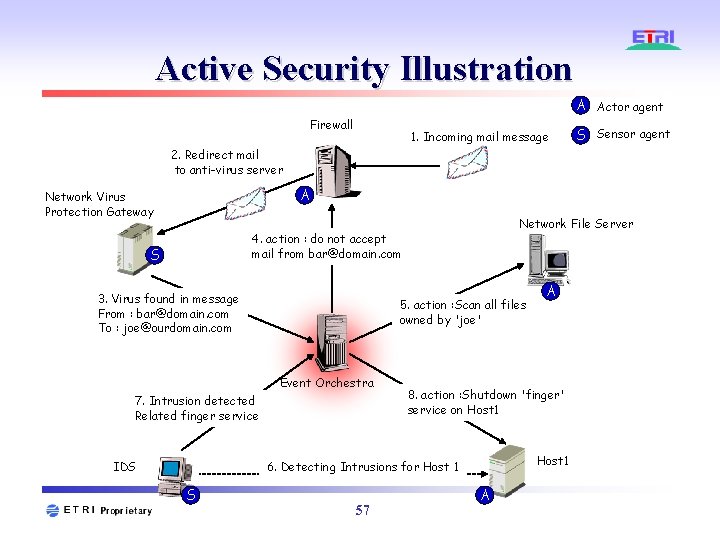
Active Security Illustration A Actor agent Firewall 1. Incoming mail message S Sensor agent 2. Redirect mail to anti-virus server A Network Virus Protection Gateway Network File Server 4. action : do not accept mail from bar@domain. com S 3. Virus found in message From : bar@domain. com To : joe@ourdomain. com 5. action : Scan all files owned by 'joe' Event Orchestra 7. Intrusion detected Related finger service IDS 8. action : Shutdown 'finger' service on Host 1 6. Detecting Intrusions for Host 1 S 57 A A

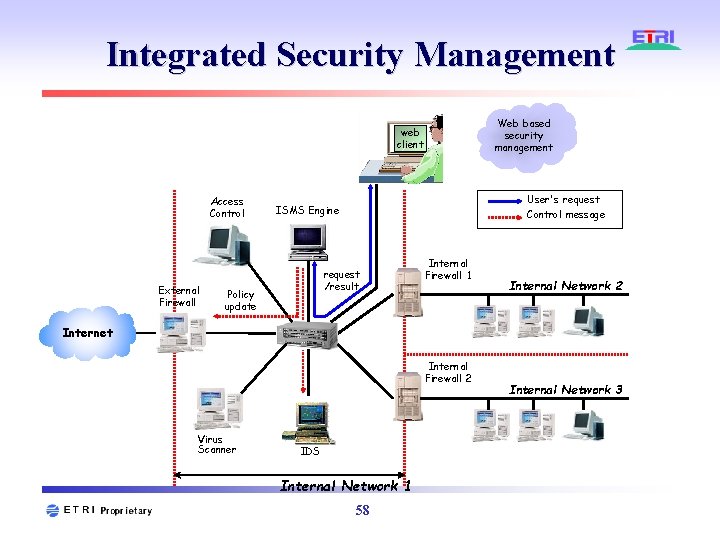
Integrated Security Management Web based security management web client Access Control External Firewall User's request Control message ISMS Engine request /result Policy update Internal Firewall 1 Internal Network 2 Internet Internal Firewall 2 Virus Scanner IDS Internal Network 1 58 Internal Network 3

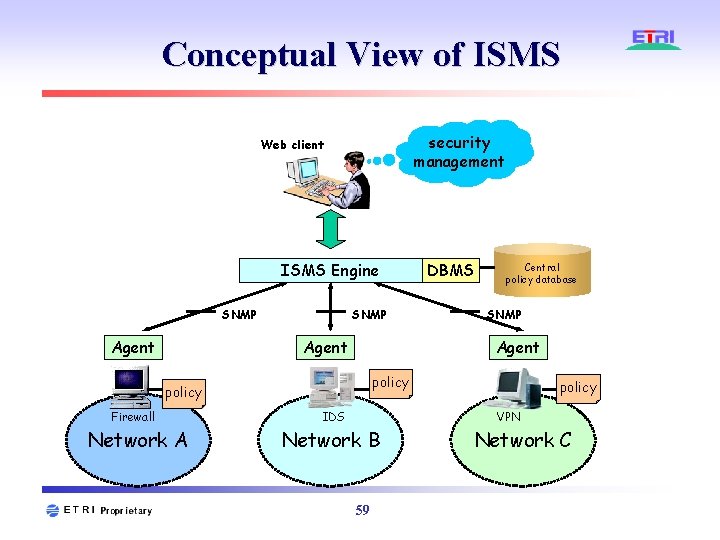
Conceptual View of ISMS security management Web client ISMS Engine SNMP Agent Network A Central policy database SNMP Agent policy Firewall DBMS IDS policy VPN Network B 59 Network C


IETF의 IDS 표준 ▣ 침입탐지 표준화 그룹 ◈ IETF IDWG(Intrusion Detection Working Group) ◈ 1998년 12월에 조직 ▣ 목적 ◈ IDS와 대응 시스템, 그리고 이들과 상호 작동하는 관리시스템 사이의 정보를 공유하기 위한 데이터 포맷 및 교환 절차 정의 ▣ The outputs of IDWG ◈ A requirements documents ◈ A common intrusion language specification ◈ A framework document 61

▣ Internet-Drafts: ◈ Intrusion Detection Mesage Exchange Requirements ◈ IAP: Intrusion Alert Protocol ◈ Intrusion Detection Message Exchange Format Extensible Markup Language (XML) Document Type Definition ◈ Intrusion Detection Message Exchange Format Comparison of SMI and XML Implementations ◈ The TUNNEL Profile Registration ◈ The Intrusion Detection Exchange Protocol (IDXP) ▣ No Request For Comments 62


▣ 다른 표준과의 관계 ◈ ISO/IEC TR 13335 -1, 2, 3, 4, 5 Ø Guidelines for the management of IT Security(GMITS) ◈ ITU-T Recommendation X. 816 | ISO/IEC TR 10181 -7 Ø Security audit and alarms framework ◈ ISO/IEC 15408 -2 : 1999 Ø Evaluation criteria for IT security - Security functional requirements ▣ 개발 연혁 ◈ WD 1998 -12 ◈ PDTR 1999 -10 ◈ (DTR 2000 -05) ◈ (TR 2000 -11) ▣ 표준화 문서명 ◈ ISO/IEC TR 15947 - IT intrusion detection framework 64




침입탐지와 대응 ▣ 침입탐지시스템에서의 대응 기술(ICSA) ◈ 수동적 대응 – Alert – Logging ◈ 능동적 대응 – Network Base – Hijacking/Termination – Firewall/Router/Switch Reconfiguration – Host base – Log off/ lock out a user – Shutdown and AP or system – Vulnerability Correction 68

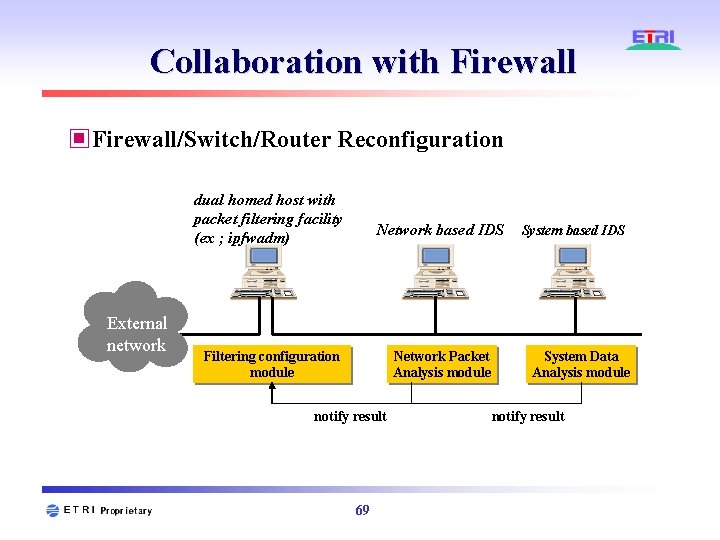
Collaboration with Firewall ▣Firewall/Switch/Router Reconfiguration dual homed host with packet filtering facility (ex ; ipfwadm) External network Network based IDS Filtering configuration module Network Packet Analysis module notify result 69 System based IDS System Data Analysis module notify result

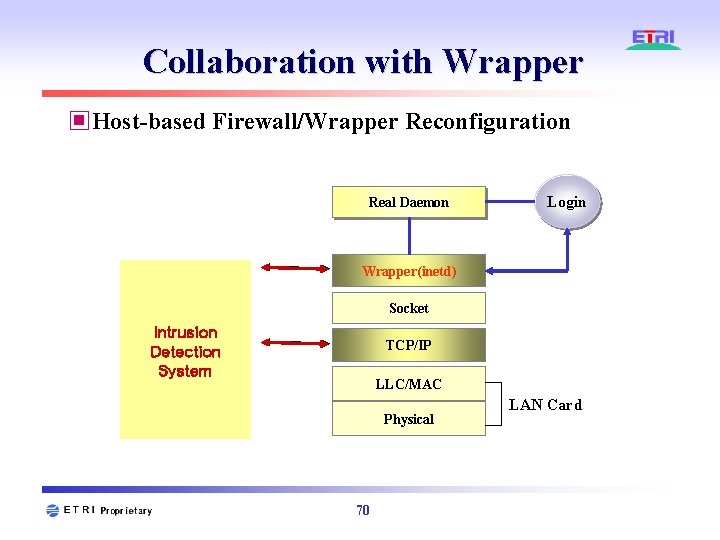
Collaboration with Wrapper ▣Host-based Firewall/Wrapper Reconfiguration Real Daemon Login Wrapper(inetd) Socket Intrusion Detection System TCP/IP LLC/MAC Physical 70 LAN Card

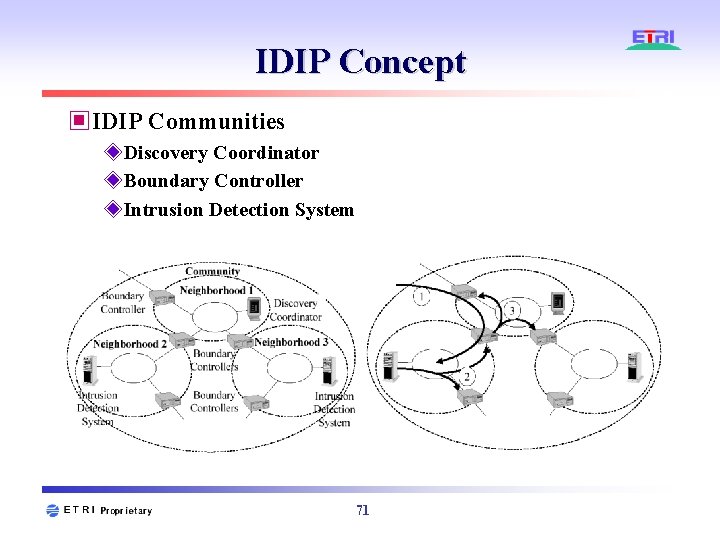
IDIP Concept ▣IDIP Communities ◈Discovery Coordinator ◈Boundary Controller ◈Intrusion Detection System 71

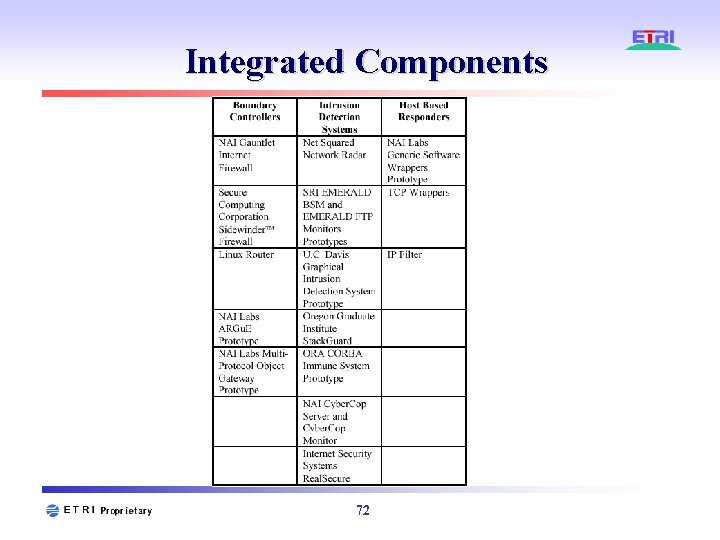
Integrated Components 72



침입탐지 ISSUE ▣ Privacy ▣ Host vs Network Based ▣ Misuse vs Anomaly Detection ▣ Burglar Alarms ▣ Honey Pots ▣ Fooling IDS ▣ IDS and Firewall/Switch/VPN ▣ IDS Performance ▣ IDS and Forensics ▣ Large Scale Networks 75