Software Change Controls Configuration Management and Computer Security










- Slides: 18

Software Change Controls, Configuration Management, and Computer Security Sed quis custodiet ipsos custodes? March 5, 2002 Federal Information Systems Security Educator's Association 1

Overview • Security program management auditing, FISCAM, and software change control • Typical findings for audits of change controls • Impacts of poor change controls • Configuration management and its importance in the lifecycle process to security efforts March 5, 2002 Federal Information Systems Security Educator's Association 2

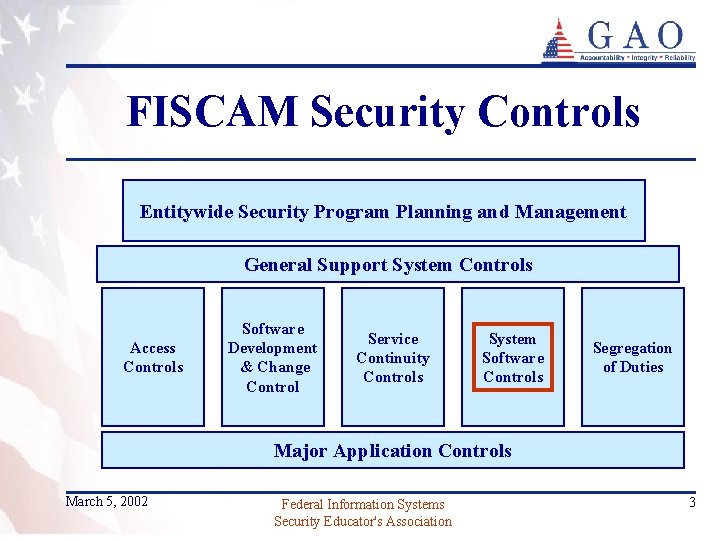
FISCAM Security Controls Entitywide Security Program Planning and Management General Support System Controls Access Controls Software Development & Change Control Service Continuity Controls System Software Controls Segregation of Duties Major Application Controls March 5, 2002 Federal Information Systems Security Educator's Association 3

Formal Policies and Procedures Lacking or Inadequate • Eight of 16 agencies had not established a formal agencywide policy or methodology for software change management. • Fourteen of 16 agencies delegated software management responsibilities to agency components that may further delegate to system owners. March 5, 2002 Federal Information Systems Security Educator's Association 4

Key Controls Not Addressed by Agencies • Documentation, approval, and testing of changes • Maintenance and protection of source code libraries • Separation of duties to prevent unauthorized changes • Labeling and inventory of software programs • Monitoring and addressing unusual activity • Managing changes to both system software and application software March 5, 2002 Federal Information Systems Security Educator's Association 5

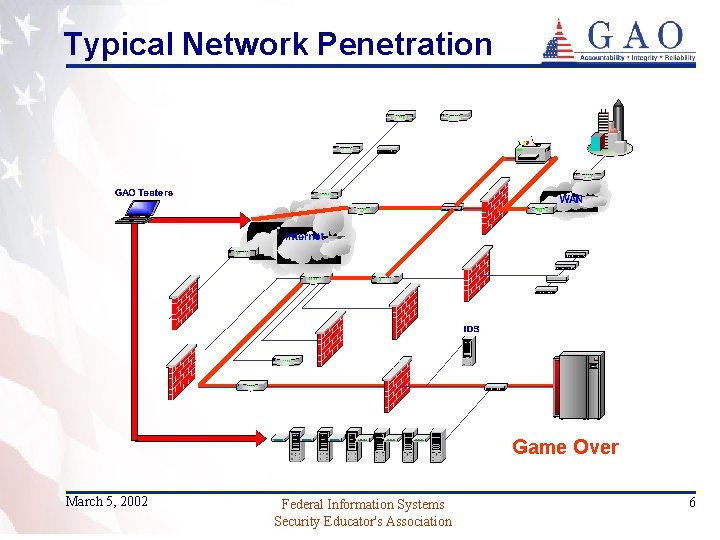
Typical Network Penetration Game Over March 5, 2002 Federal Information Systems Security Educator's Association 6

Network Change Control Problems • Major Application and General Support System Plans and Procedures (security, contingency, incident) are inconsistent with each other. • Functional owners don’t know where their applications move or are located in general support systems. • Systems are not segregated by risk. • Vulnerabilities are not uniformly fixed. March 5, 2002 Federal Information Systems Security Educator's Association ? s sk Ri ? Plans ? ? 7

Results of Poor Change Controls (Based on Network Audits) • Firewall settings vary among network owners. ØInconsistent settings that fail to provide a suitable barrier to the Internet ØBypassed by known and unknown dialups • Password implementation varies by platform. ØNot required in some cases ØVarying length (too short in many cases) ØInconsistently tested ØNot changed on a regular basis March 5, 2002 Federal Information Systems Security Educator's Association 8

Examples of Poor Software Change Controls (Based on Mainframe Audits) • Weak controls on critical system libraries which could allow unauthorized personnel to subvert security controls • Poor separation between testing and production • Procedures for migrating new releases to production are not coordinated, documented, or formalized • Security over library management software is not consistent with overall security policy March 5, 2002 Federal Information Systems Security Educator's Association 9

Overall Impacts of Inadequate Change Controls • Operational costs are increased. • The usefulness of risk assessments and security plans is diminished. • Logical controls to prevent or detect unauthorized access are hard to establish. • It is difficult to monitor access, investigate apparent security violations, and implement effective security patches. March 5, 2002 Federal Information Systems Security Educator's Association 10

Solution: Implement Good Change Controls and Configuration Management • OPM IT Security Policy V. 1, p. 32 defines Configuration Management as follows: “Configuration management is the process that is used to monitor the installation of and updates to system hardware, operating system software, and the software to ensure that hardware and software function as expected, and that an historical record of application changes is maintained. ” March 5, 2002 Federal Information Systems Security Educator's Association 11

Component Parts of Configuration Management • Configuration Identification - What are the systems and their sub-elements for your current world (production baseline) and proposed or development baseline? • Configuration Control- What are your baselines and how do you control changes to the various baselines you are using? • Configuration Status Accounting- How do you track changes to your baselines ? • Configuration Auditing- How do you verify that approved changes were made correctly and completely? March 5, 2002 Federal Information Systems Security Educator's Association 12

Configuration Identification • Define baselines associated with current and projected work and assign responsibility for their management. • Establish rules for partitioning information into baselines to maintain traceability and control. • Accept information into the configuration control process and update it once it has been baselined. • Define linkages between major applications and general support systems. March 5, 2002 Federal Information Systems Security Educator's Association 13

Configuration Control • Manage and integrate Configuration Control Boards (CCBs) that have been formally established for the various production and development baselines • Define and use impact analysis procedures designed for making changes to baselined information • Ensure that control procedures are enforced and are standardized throughout the agency March 5, 2002 Federal Information Systems Security Educator's Association 14

Configuration Status Accounting • Track the status and currency of the release as it moves through the change control process • Ensure that information about the release (location in the change process, contents of the release, linkages, etc. ) is available to all participants in a timely manner • Ensure that impacts between current and future releases for the various Configuration Control Boards (CCBs) are synchronized with architectural control efforts March 5, 2002 Federal Information Systems Security Educator's Association 15

Configuration Auditing • Ensure that there is a review of the various baselines to ensure accuracy, consistency, and completeness. • Conduct formal audits to verify that products are developed and installed in conformance with approved requirements and specifications. March 5, 2002 Federal Information Systems Security Educator's Association 16

Questions? March 5, 2002 Federal Information Systems Security Educator's Association 17

Answers Bill Wadsworth. W@gao. gov 202 -512 -6234 March 5, 2002 Federal Information Systems Security Educator's Association 18