Social Navigation as a Model for Usable Security

Social Navigation as a Model for Usable Security Paul Di. Gioia and Paul Dourish Presented by: Monika Akbar Usable Security – CS 6204 – Fall, 2009 – Dennis Kafura – Virginia Tech
![Background n n Bruce Schneier [15] has observed that “Security measures that aren’t understood Background n n Bruce Schneier [15] has observed that “Security measures that aren’t understood](http://slidetodoc.com/presentation_image_h2/d180f7e0e2158cd23e13118fc1e22d38/image-2.jpg)
Background n n Bruce Schneier [15] has observed that “Security measures that aren’t understood and agreed to by everyone don’t work. ” “The central concern here is that neither usability nor security can be added on to systems after the primary design work is done; rather, both need to be central aspects of the design effort. ” Usable Security – CS 6204 – Fall, 2009 – Dennis Kafura – Virginia Tech

Overview n n Social Navigation and Security Example Discussion Usable Security – CS 6204 – Fall, 2009 – Dennis Kafura – Virginia Tech
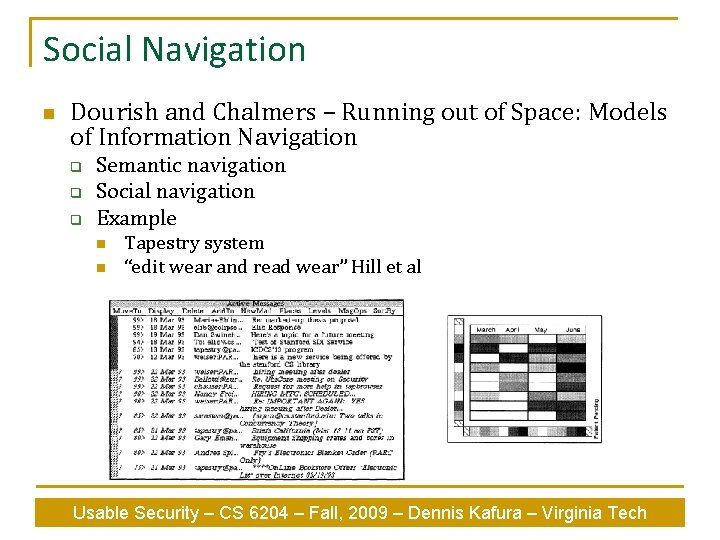
Social Navigation n Dourish and Chalmers – Running out of Space: Models of Information Navigation q q q Semantic navigation Social navigation Example n n Tapestry system “edit wear and read wear” Hill et al Usable Security – CS 6204 – Fall, 2009 – Dennis Kafura – Virginia Tech

Social Navigation “I took the one less traveled by, And that has made all the difference. ” – Robert Frost Usable Security – CS 6204 – Fall, 2009 – Dennis Kafura – Virginia Tech
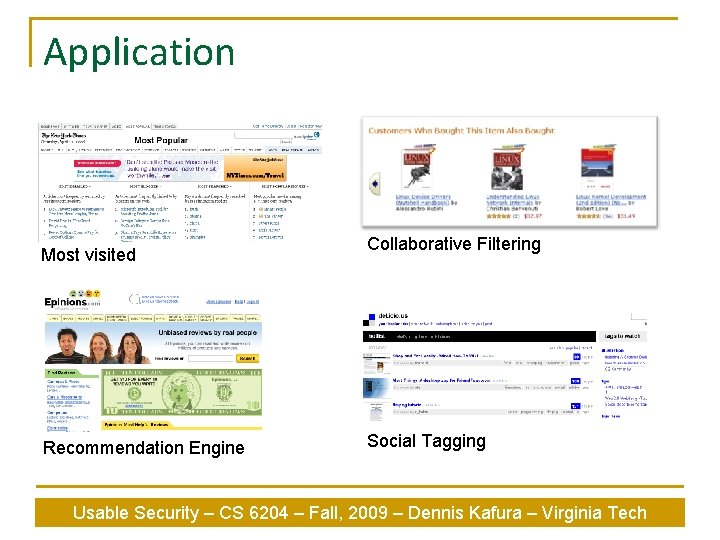
Application Most visited Recommendation Engine Collaborative Filtering Social Tagging Usable Security – CS 6204 – Fall, 2009 – Dennis Kafura – Virginia Tech

Overview n n Social Navigation and Security Example Discussion Usable Security – CS 6204 – Fall, 2009 – Dennis Kafura – Virginia Tech
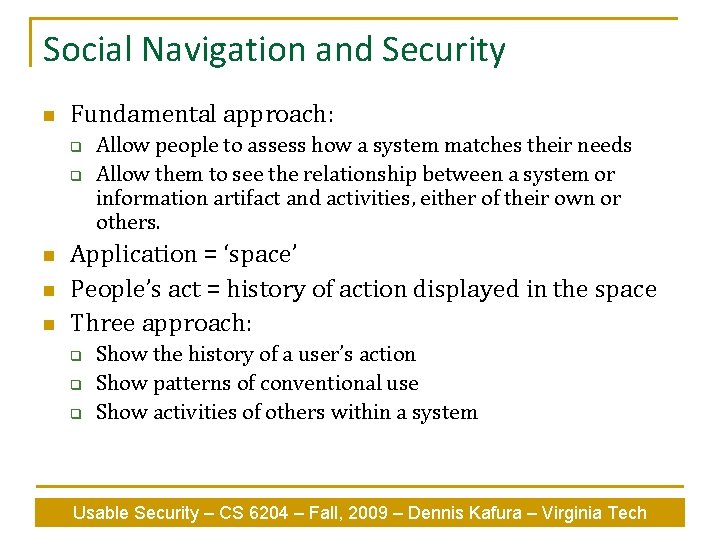
Social Navigation and Security n Fundamental approach: q q n n n Allow people to assess how a system matches their needs Allow them to see the relationship between a system or information artifact and activities, either of their own or others. Application = ‘space’ People’s act = history of action displayed in the space Three approach: q q q Show the history of a user’s action Show patterns of conventional use Show activities of others within a system Usable Security – CS 6204 – Fall, 2009 – Dennis Kafura – Virginia Tech

Overview n n Social Navigation and Security q q q n n Show the history of a user’s action Show patterns of conventional use Show activities of others within a system Example Discussion Usable Security – CS 6204 – Fall, 2009 – Dennis Kafura – Virginia Tech

Show Patterns of Use – two metaphor n n Good and Krekelberg’s study of potential security issues in the Kazaa peer to peer file sharing application Mander et al, ‘pile’ metaphor for the informal grouping of files Usable Security – CS 6204 – Fall, 2009 – Dennis Kafura – Virginia Tech
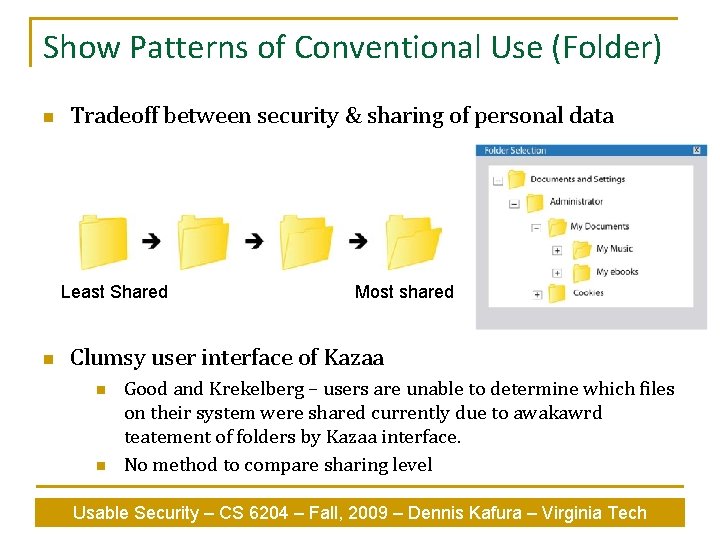
Show Patterns of Conventional Use (Folder) n Tradeoff between security & sharing of personal data Least Shared n Most shared Clumsy user interface of Kazaa n n Good and Krekelberg – users are unable to determine which files on their system were shared currently due to awakawrd teatement of folders by Kazaa interface. No method to compare sharing level Usable Security – CS 6204 – Fall, 2009 – Dennis Kafura – Virginia Tech
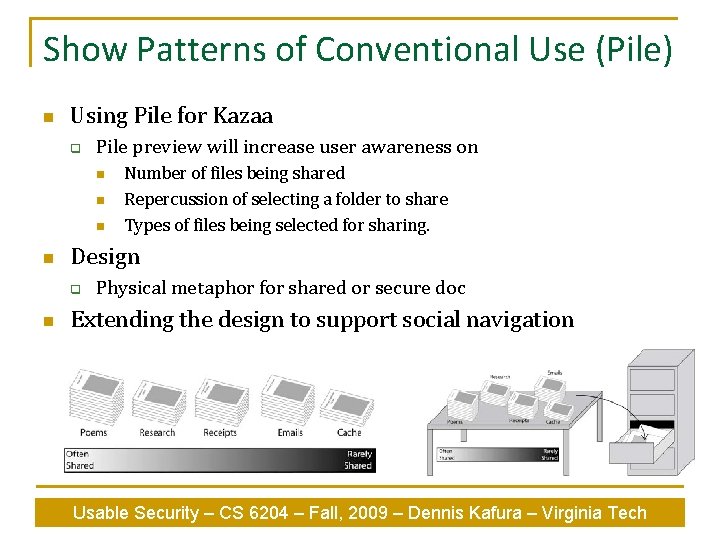
Show Patterns of Conventional Use (Pile) n Using Pile for Kazaa q Pile preview will increase user awareness on n n Design q n Number of files being shared Repercussion of selecting a folder to share Types of files being selected for sharing. Physical metaphor for shared or secure doc Extending the design to support social navigation Usable Security – CS 6204 – Fall, 2009 – Dennis Kafura – Virginia Tech

Overview n n Social Navigation and Security q q q n n Show the history of a user’s action Show patterns of conventional use Show activities of others within a system Example Discussion Usable Security – CS 6204 – Fall, 2009 – Dennis Kafura – Virginia Tech
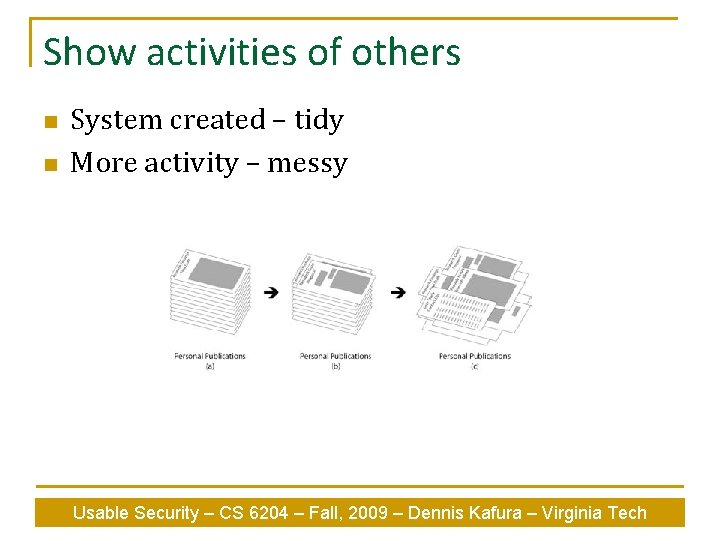
Show activities of others n n System created – tidy More activity – messy Usable Security – CS 6204 – Fall, 2009 – Dennis Kafura – Virginia Tech

Overview n n Social Navigation and Security q q q n n Show the history of a user’s action Show patterns of conventional use Show activities of others within a system Example Discussion Usable Security – CS 6204 – Fall, 2009 – Dennis Kafura – Virginia Tech
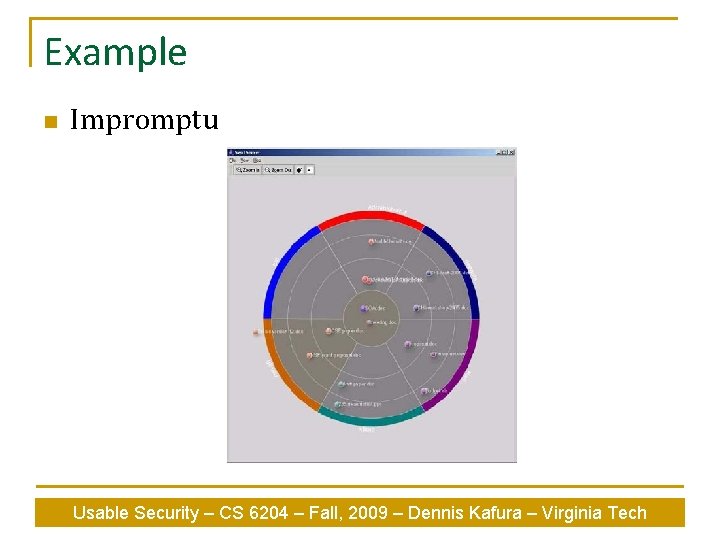
Example n Impromptu Usable Security – CS 6204 – Fall, 2009 – Dennis Kafura – Virginia Tech

Discussion n Visualization based approach q q n Application as a space populated by user Artifacts carry the evidence of activities over them Issues q q How to cope with the varying level of trust on the recipient side? Missing – Context Usable Security – CS 6204 – Fall, 2009 – Dennis Kafura – Virginia Tech

Thank you. Usable Security – CS 6204 – Fall, 2009 – Dennis Kafura – Virginia Tech
- Slides: 18