SOA Federated Identity Management How much do you











- Slides: 15

SOA Federated Identity Management How much do you really need? Andrew S. Townley Founder and Managing Director Archistry Limited Copyright 2006 Archistry Limited. All Rights Reserved.

Agenda Ø Definitions Ø Business drivers for federated identity Ø Approaches to providing federated identity Ø Technical considerations Ø Questions 10/31/2 020 2 Public Information Copyright 2006 Archistry Limited. All Rights Reserved.

Definitions Ø Federated system – integrates existing, possibly heterogeneous systems while preserving their autonomy Ø Association autonomy – the ability of a component system to decide whether and how to share its operations and resources with other systems Ø Federated identity – a shared name identifier agreed between partner services in order to share information about the user across organizational boundaries 10/31/2 020 3 Public Information Copyright 2006 Archistry Limited. All Rights Reserved.

Business Drivers Ø What are you trying to do? • Provide single sign-on (SSO)? • Support dynamic collaboration? • Provide a central point of access to distributed services? Ø Who are the other participants? • Services controlled by a single organization? • Services provided by trading partners? • Parties with whom you have no formal relationship? 10/31/2 020 4 Public Information Copyright 2006 Archistry Limited. All Rights Reserved.

Additional Considerations Ø Privacy and consent • Will the users use the system? • How will their privacy be protected? • How will you respond to a right to access request? Ø Accountability • What mechanisms will be used for identity proofing? • What mechanisms will ensure nonrepudiation of authentication? • How will you respond to claims of fraudulent access? 10/31/2 020 5 Public Information Copyright 2006 Archistry Limited. All Rights Reserved.

Approaches Ø Don’t federate Ø Federated identity Ø Chain of trust Ø Federated authorization 10/31/2 020 6 Public Information Copyright 2006 Archistry Limited. All Rights Reserved.

Federated Identities Ø Leverages the identification/authentication of a trusted member of the federation (e. g. SAML Id. P) Ø May or may not require local accounts at all service providers Ø Requires out-of-band business agreements between members of the federation Ø Does nothing more than assert a claim as to the identity of a user or request within a given context 10/31/2 020 7 Public Information Copyright 2006 Archistry Limited. All Rights Reserved.

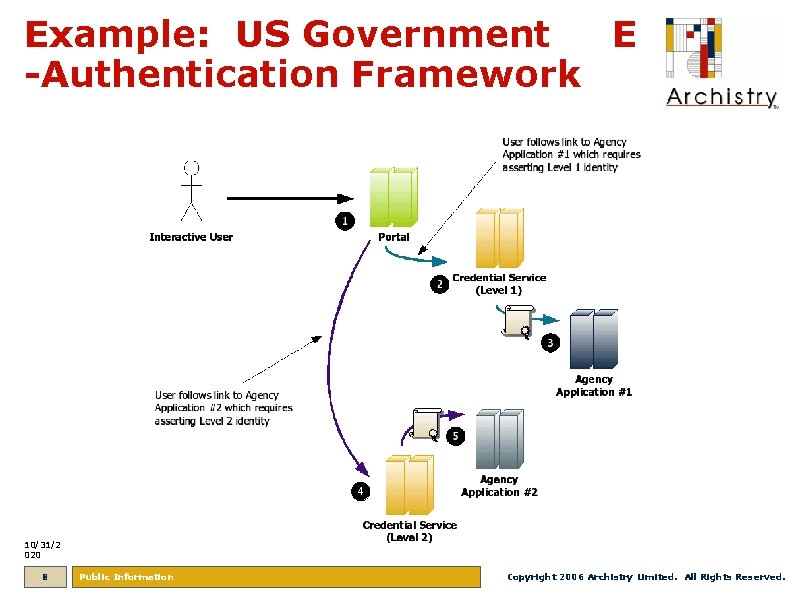
Example: US Government E -Authentication Framework 10/31/2 020 8 Public Information Copyright 2006 Archistry Limited. All Rights Reserved.

Chain of Trust Ø Each participant responsible for authenticating only the members directly communicating with it Ø Information integrity must be assured by the information producer Ø Requires out-of-band business agreements between members of the federation Ø Each member of the chain is authenticated to the next— any other credential information is opaque Ø Ensures a sequence of participants can exchange information, but does not directly authenticate (or may not even identify) the original information producer 10/31/2 020 9 Public Information Copyright 2006 Archistry Limited. All Rights Reserved.

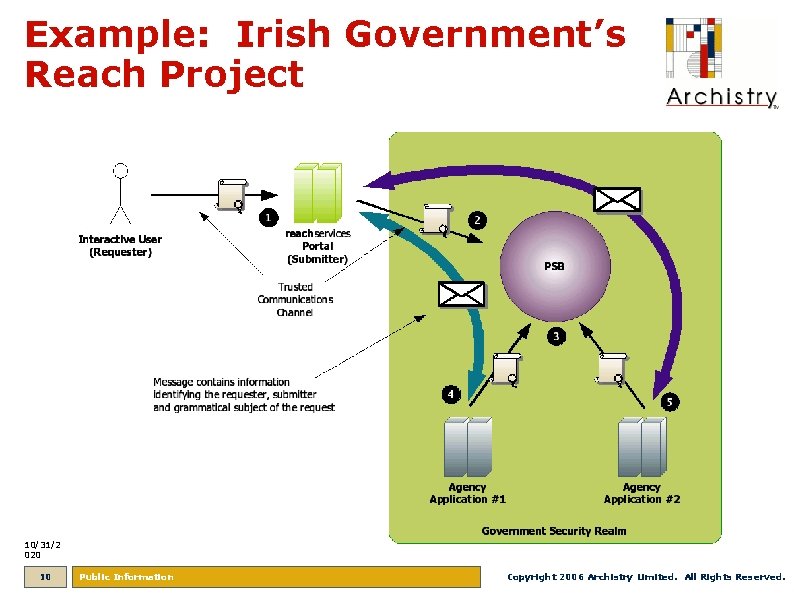
Example: Irish Government’s Reach Project 10/31/2 020 10 Public Information Copyright 2006 Archistry Limited. All Rights Reserved.

Federated Authorization Ø Federation defines the semantics of a particular set of profile attributes Ø Service provider association and access control is based on the presence of one or more attributes Ø Can be used in conjunction with federated identities or without them for dynamic collaboration Ø Still requires out-of-band business agreements between members of the federation Ø Can be used for more flexible and dynamic collaborations, but attribute negotiation may have privacy implications 10/31/2 020 11 Public Information Copyright 2006 Archistry Limited. All Rights Reserved.

Example: EU Driving License Regulations 10/31/2 020 12 Public Information Copyright 2006 Archistry Limited. All Rights Reserved.

Technical Considerations Ø How will the business agreements be managed electronically (Proprietary XML, SAML, XACML, WS-Policy or something else)? Ø Are the services provided asynchronously or synchronously? Ø What is the temporal coupling between the services? Ø Are the services provided to interactive users or automated agents? Ø How much information is necessary to identify the user to the local service? Ø Will the local services also support authentication and management of their own user identities? Ø Which is most important: the identity of the principal making the request or the identity of the principal to which the request refers? Ø Who (or what) is actually making the request? 10/31/2 020 13 Public Information Copyright 2006 Archistry Limited. All Rights Reserved.

References Ø US E-Government Authentication Framework and Programs, IT Professional, May/June 2003, http: //csdl 2. computer. org/persagen/DLAbs. Toc. jsp? resource. Path=/dl/mags/it/&toc=comp/mags/it/2003 /03/f 3 toc. xml&DOI=10. 1109/MITP. 2003. 1202230 Ø Technical Approach for the Authentication Service Component, Version 1. 0. 0, GSA (2004), http: //www. cio. gov/eauthentication/documents/Tech. Approach. pdf Ø SAML V 2. 0 Technical Overview, Working Draft 10, http: //www. oasis- open. org/committees/download. php/20645/sstc-saml-tech-overview-2%200 -draft-10. pdf Ø Liberty ID-WSF Web Services Framework Overview, Version 2. 0, http: //www. projectliberty. org/liberty/content/download/889/6243/file/liberty-idwsf-overview-v 2. 0. pdf Ø Access Control Management in a Distributed Environment Supporting Dynamic Collaboration, Shafiq, B. et al (2005), http: //portal. acm. org/citation. cfm? id=1102503 Ø Implementing a Federated Architecture to Support Supply Chains, Chadha, B. (2003), http: //www. coensys. com/files/federation%20 white%20 paper%2003. PDF Ø A Distributed Trust Model, Abdul-Rahman, A. , S. Hailes (1997), http: //portal. acm. org/citation. cfm? id=283739 Ø Access Control in Federated Systems, De Capitani di Vimercati, S. and Samarati, P. (1996), http: //portal. acm. org/citation. cfm? id=304871 10/31/2 020 14 Public Information Copyright 2006 Archistry Limited. All Rights Reserved.

Archistry Limited 33 Pearse Street Suite 115 Dublin 2, Ireland www. archistry. com Phone +353 86 996 2490 Fax +353 865 996 2490 Email info@archistry. com Turning innovation into business value TM 10/31/2 020 15 Public Information Copyright 2006 Archistry Limited. All Rights Reserved.