Snakes and Ladders OWASP Newcastle 24 th November

Snakes and Ladders OWASP Newcastle 24 th November 2015
Web Risks 2013 17 th September 2014 https: //www. owasp. org/index. php/OWASP_T op_Ten_Project

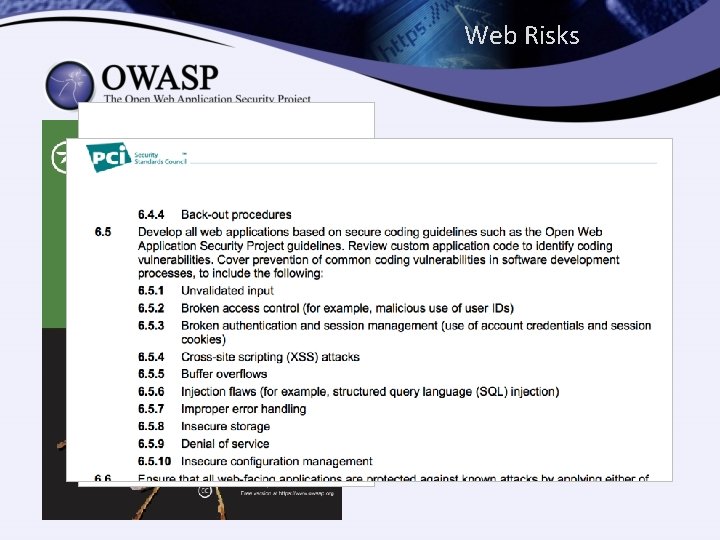
Well-Known List Top Ten Risks to Web Applications (2013) A 1 A 2 A 3 A 4 A 5 A 6 A 7 A 8 A 9 A 10 Injection Broken Authentication and Session Management Cross-Site Scripting (XSS) Insecure Direct Object References Security Misconfiguration Sensitive Data Exposure Missing Function Level Access Control Cross-Site Request Forgery (CSRF) Using Components with Known Vulnerabilities Unvalidated Redirects and Forwards

Proactive Controls Version 1 10 th March 2014 https: //www. owasp. org/index. php/OWASP_P roactive_Controls (version 2 in progress, due end 2015)

A Better List Top Ten Proactive Controls Web Applications C 1 C 2 C 3 C 4 C 5 C 6 C 7 C 8 C 9 C 10 Parameterize Queries Encode Data Validate All Inputs Implement Appropriate Access Controls Establish Identity and Authentication Controls Protect Data and Privacy Implement Logging, Error Handling & Intrusion Detection Leverage Security Features of Frameworks and Libraries Include Security-Specific Requirements Design and Architect Security In

Too Much Text! • • • Educate Move from risks to controls Make a game Learn Adobe Illustrator Christmas “cards”

Designs, Trademarks, Etc

Concept • 10 snakes • 10 ladders • 100 squares

Flat Design
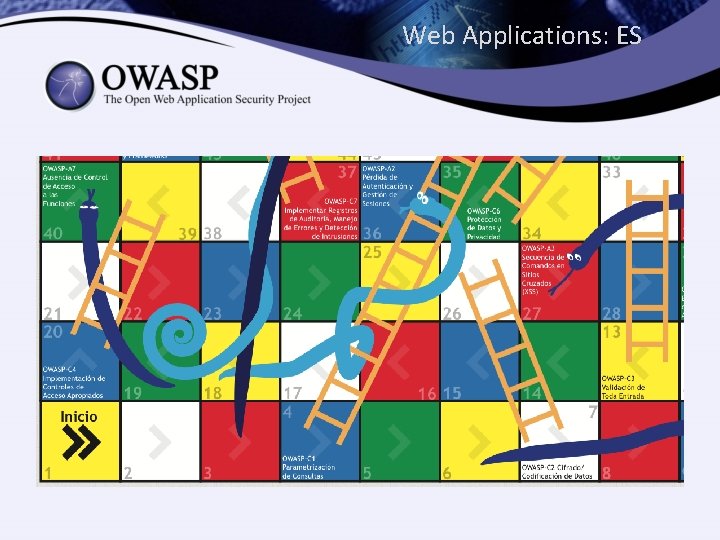
Web Applications: ES
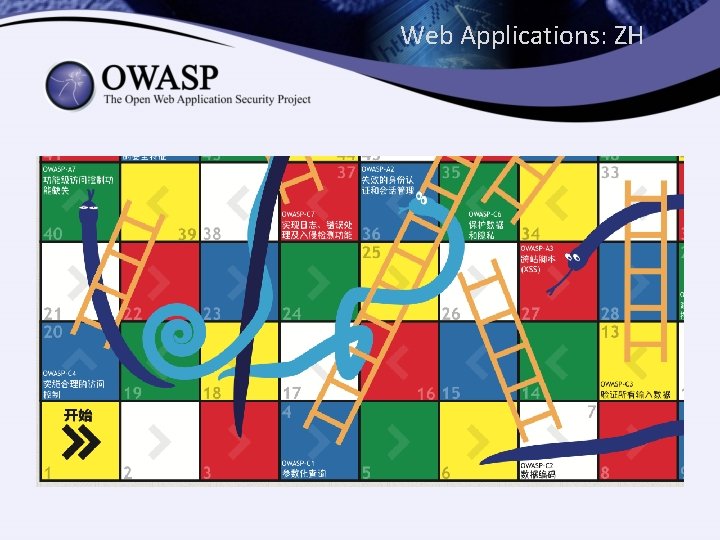
Web Applications: ZH
Web Applications: DE
Mobile Apps: JA

Mobile Apps: EN

Relationships 1/3 • Is the placement of snakes and ladders meaningful? • Do nearby ladders fix adjacent snakes? • No

Relationships 2/3 Top Ten Risks Top Ten Proactive Controls A 1 Injection A 2 Broken Authentication and Session Management A 3 Cross-Site Scripting (XSS) A 4 Insecure Direct Object References A 5 Security Misconfiguration A 6 Sensitive Data Exposure A 7 Missing Function Level Access Control A 8 Cross-Site Request Forgery (CSRF) A 9 Using Components with Known Vulnerabilities A 10 Unvalidated Redirects and Forwards C 1 Parameterize Queries C 2 Encode Data C 3 Validate All Inputs C 4 Implement Appropriate Access Controls C 5 Establish Identity and Authentication Controls C 6 Protect Data and Privacy C 7 Implement Logging, Error Handling and Intrusion Detection C 8 Leverage Security Features of Frameworks and Security Libraries C 9 Include Security-Specific Requirements C 10 Design and Architect Security In
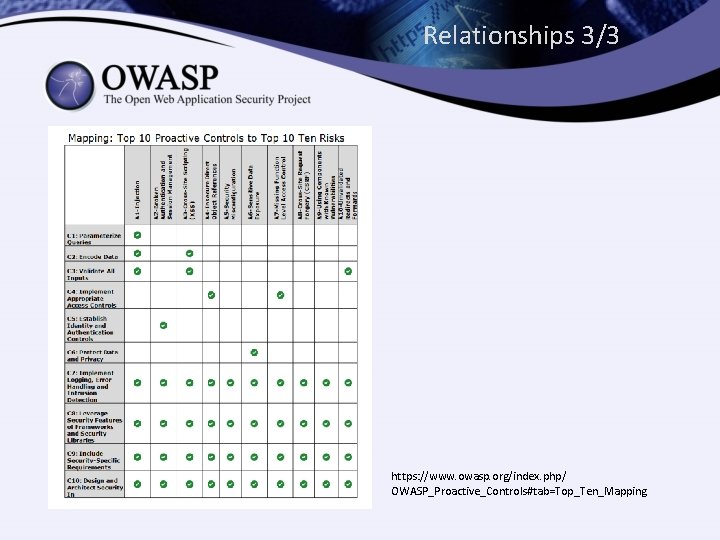
Relationships 3/3 https: //www. owasp. org/index. php/ OWASP_Proactive_Controls#tab=Top_Ten_Mapping

Print Your Own • Adobe PDF A 2 print quality • Web Applications BR, DE, EN, ES, FR, JA, ZH • Adobe Illustrator Source • Mobile Apps EN, JA

From Lists to Threat Modelling • Not just 10 issues • Build security in from the start, and throughout processes • In depth application security requirements
Staying in Touch Project page https: //www. owasp. org/index. php/OWASP_Snakes_and_Ladders Mailing list https: //lists. owasp. org/mailman/listinfo/owasp_snakes_and_ladders Twitter (Web) (Mobile) @OWASPSnakes. Web @OWASPSnakes. Mob Full world tour 2014 -15 Singapore, Cambridge, London Docklands, London Shoreditch, Bristol, Amsterdam, San Francisco, Newcastle upon Tyne

Q&A • colin. watson@owasp. org
- Slides: 22