SMS Mobile Botnet Detection Using A MultiAgent System
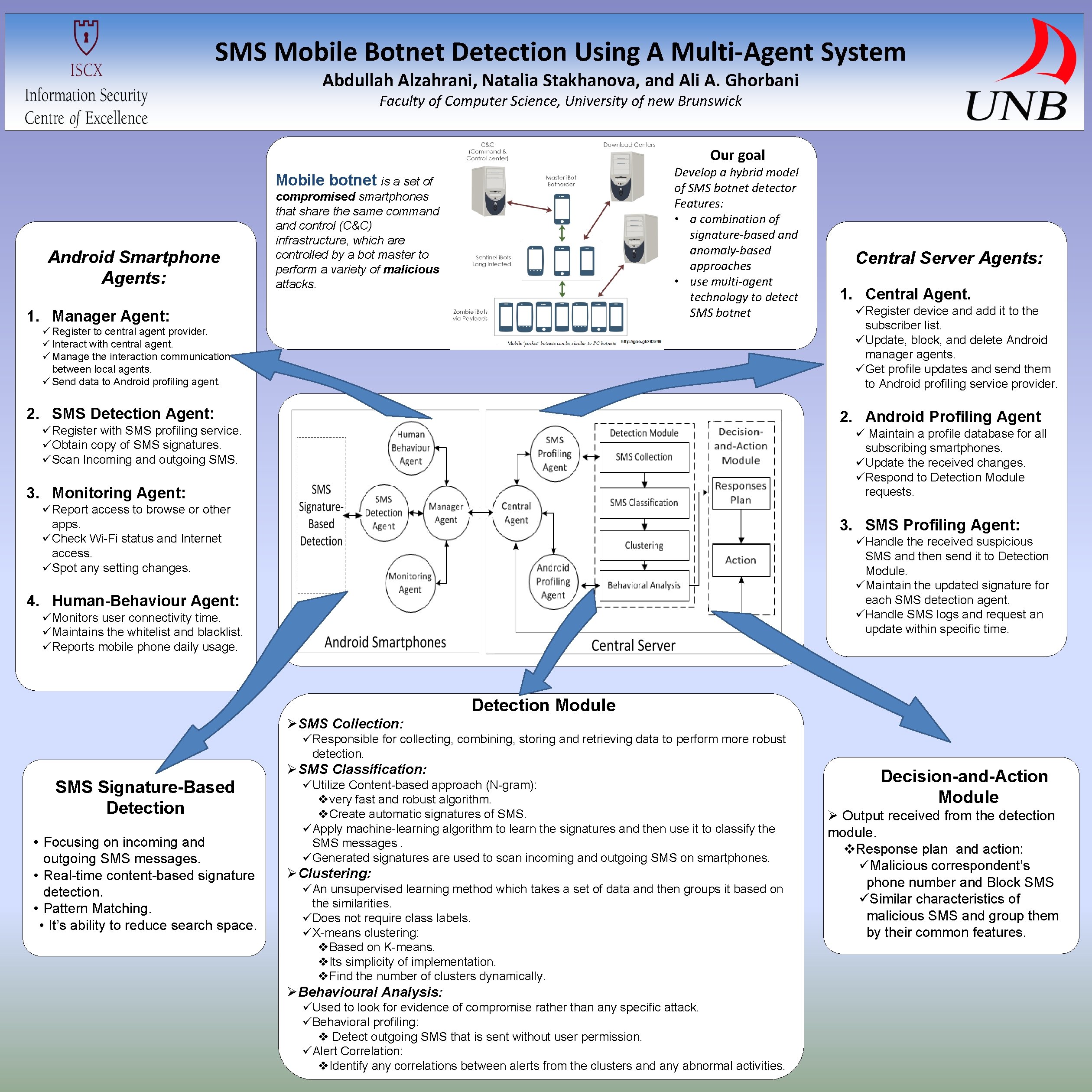
SMS Mobile Botnet Detection Using A Multi-Agent System Abdullah Alzahrani, Natalia Stakhanova, and Ali A. Ghorbani Faculty of Computer Science, University of new Brunswick Our goal Develop a hybrid model of SMS botnet detector Features: • a combination of signature-based anomaly-based approaches • use multi-agent technology to detect SMS botnet Mobile botnet is a set of Android Smartphone Agents: compromised smartphones that share the same command control (C&C) infrastructure, which are controlled by a bot master to perform a variety of malicious attacks. 1. Manager Agent: ü Register to central agent provider. ü Interact with central agent. ü Manage the interaction communication between local agents. ü Send data to Android profiling agent. 2. SMS Detection Agent: Central Server Agents: 1. Central Agent. üRegister device and add it to the subscriber list. üUpdate, block, and delete Android manager agents. üGet profile updates and send them to Android profiling service provider. 2. Android Profiling Agent üRegister with SMS profiling service. üObtain copy of SMS signatures. üScan Incoming and outgoing SMS. ü Maintain a profile database for all subscribing smartphones. üUpdate the received changes. üRespond to Detection Module requests. 3. Monitoring Agent: üReport access to browse or other apps. üCheck Wi-Fi status and Internet access. üSpot any setting changes. 3. SMS Profiling Agent: üHandle the received suspicious SMS and then send it to Detection Module. üMaintain the updated signature for each SMS detection agent. üHandle SMS logs and request an update within specific time. 4. Human-Behaviour Agent: üMonitors user connectivity time. üMaintains the whitelist and blacklist. üReports mobile phone daily usage. Detection Module ØSMS Collection: üResponsible for collecting, combining, storing and retrieving data to perform more robust detection. ØSMS Classification: SMS Signature-Based Detection • Focusing on incoming and outgoing SMS messages. • Real-time content-based signature detection. • Pattern Matching. • It’s ability to reduce search space. üUtilize Content-based approach (N-gram): vvery fast and robust algorithm. v. Create automatic signatures of SMS. üApply machine-learning algorithm to learn the signatures and then use it to classify the SMS messages. üGenerated signatures are used to scan incoming and outgoing SMS on smartphones. ØClustering: üAn unsupervised learning method which takes a set of data and then groups it based on the similarities. üDoes not require class labels. üX-means clustering: v. Based on K-means. v. Its simplicity of implementation. v. Find the number of clusters dynamically. ØBehavioural Analysis: üUsed to look for evidence of compromise rather than any specific attack. üBehavioral profiling: v Detect outgoing SMS that is sent without user permission. üAlert Correlation: v. Identify any correlations between alerts from the clusters and any abnormal activities. Decision-and-Action Module Ø Output received from the detection module. v. Response plan and action: üMalicious correspondent’s phone number and Block SMS üSimilar characteristics of malicious SMS and group them by their common features.
- Slides: 1