Smart cards a fascinating and fruitful adventure Nguyen





- Slides: 12

Smart cards a fascinating and fruitful adventure Nguyen Quang Huy Gemalto Technology & Innovation

Smart Cards in the our life Secure transaction (banking, pay-TV) Telecom (SIM/USIM/RUIM, M 2 M, convergence, M-TV, M-banking, Mticket) Control Access (physical and logical resource) E-citizen (e-passport, e-ID, e-Heath, e-driving license, . . ) 2

Smart Card HW 25 mm 2 No internal timer, battery No keyboard, display, network interface Current generation § § § µ-processor: 16 -bits, <=10 MHz RAM: 4 K ROM: 100 K for code storage E 2 PROM (105 updates ): 64 K for data storage I/O: serial (9600 bps), – Contactless protocols: Mi. Fare, Feli. Ca, Calypso Next generation § µ-processor: 32 -bits, up to 100 MHz § Flash memory: more durable and more rapid § I/O: USB (12 Mbps) – Contactless open protocols: NFC, Zig. Bee 3

Smart Card SW Proprietary architecture § Undisclosed specification § Tedious application development § Closed configuration: no application can be added after issuance Open architecture § Open specification § High-level programming languages § Post-issuance applications are available Some open architectures § § Java Card MULTOS. NET Card Basic Card 4

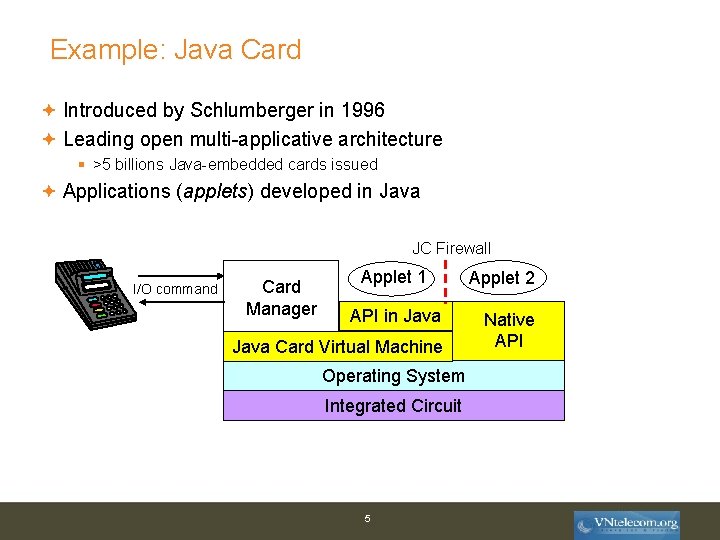
Example: Java Card Introduced by Schlumberger in 1996 Leading open multi-applicative architecture § >5 billions Java-embedded cards issued Applications (applets) developed in Java JC Firewall I/O command Card Manager Applet 1 API in Java Card Virtual Machine Operating System Integrated Circuit 5 Applet 2 Native API

Security threats No battery § Card tearing (or power failure ) may cause inconsistency data No internal timer § Logging for post-mortem analysis is not possible No keyboard, display, network device secure usage environment § Payment terminals (POS and ATM): security certification § Security of PC and handset: keyboard logger, false display (phishing), etc Contactless interface § Cardholder is not aware of malicious actions Physically owned by attackers § Vulnerable to both logical and physical attacks 6

Attacks Logical attacks: use I/O commands to exploit SW vulnerabilities buffer overflow, type confusion, covert channels, protocol attacks, etc Physical attacks: use physical phenomenon to exploit SW/HW vulnerabilities § Invasive attacks: destructive and require specific logistics HW reverse-engineering; disabling HW security features, etc § Non invasive attacks: affordable logistics – Side-channel: use the emitted signals (power consumption, execution time) to guess the secret (keys, PIN) Execution signature (E 2 PROM update, DES rounds, etc) may leak secret – Fault-injection attacks: use physical means (infrared heat, laser, X-ray) to flip some bits in the memory Modify code and runtime control flow, data: the consequence is hardly predictable Combined attacks 7

Counter-measures and beyond Detection § HW: (shield-removal, temperature, frequency, laser, light) sensors § SW: checksum, fault-trap Protection § HW: memory/bus encryption, redundancy, error-correcting code § SW: transaction mechanism (anti-tearing), random noise, protection of control flow Auditing § HW: security registers § SW: fault-counters, security exception Reaction § Muting (infinite loop) and clearing RAM No counter-measure is perfect Trade-off between security and performance (tender eligibility criterion) Use of mathematical techniques: formal methods 8

Mathematically proven security assurances 9

Vietnam: smart card deployment Mobile telecom § Low-end cards: <=64 K EEPROM Banking § Small-scale migrations to EMV standard: VP Bank, VCB, etc § Online banking (secure reader/authentication server): VCB § Why the banks are not keen on using smart cards ? – Cards mainly used for ATM withdrawal: rare (offline) POS payment fraud is limited – Card holders are usually paying for the fraud ! – Insfratructure cost for a migration (ATM, POS, servers, etc) E-government § e-passport project (since 2006) 10

Dosmetic industry Small market implies small players Few smart cards manufacturers § MK Technology JSC: 20 milions smart cards delivered in 2008 § Main products: SIM, USIM, RUIM – Sale representative of foreign products § Dosmetic share in final products – Card personalization for final clients – A first Vietnamese smart card OS ? MKCos (Sao Khue 2008) Even fewer application developers § Vietnamizing imported applications 11

Joining the adventure Expanding dosmetic market by SIM-based attractive applications e. g. , § M-payment, online payment § Value-added applications on mobile network § M-ticket for public transport Making E-Government come true § Healthcare card, ID-card, etc Education/Training § More training courses for – embeded programming: lucrative outsourcing market – security engineering: go beyond anti-virus § Support of overseas experts Enterprising § Win-win JV with foreign partners to learn technology 12
 Def hello()
Def hello() Chapter 4 python for everybody
Chapter 4 python for everybody Nguyen tan khoi nguyen
Nguyen tan khoi nguyen Source cards
Source cards Flower a fascinating organ of angiosperms
Flower a fascinating organ of angiosperms It's really fascinating
It's really fascinating It's really fascinating
It's really fascinating Fruitful function python
Fruitful function python Fruitful collision
Fruitful collision Fruitful functions in python
Fruitful functions in python Efficient signature generation by smart cards
Efficient signature generation by smart cards Street knowledge vs book knowledge
Street knowledge vs book knowledge Smart two men are
Smart two men are