Smart Card Alliance Privacy and Secure ID Systems































- Slides: 46

Smart Card Alliance Privacy and Secure ID Systems Smart. Talk Teleconference June 26, 2003 1: 00 PM – 2: 15 PM Eastern time Sponsored by Property of Smart Card Alliance Copyright 2003 1

Smart Talk Call-in Number • To join the teleconference: – Call-in numbers: • 1 -888 -928 -9122 (US toll-free) • +1 -630 -395 -0017 (International callers) – Passcode: SMART CARD ID – Meeting leader: Mr. Mike Weekes • Smart Talk presentation available at: www. smartcardalliance. org/_private/Smart. Talk. Conference. cfm Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 2

Smart Card Alliance (Vanderhoof – Smart Card Alliance) • Smart Card Alliance mission To stimulate the understanding, adoption, use and widespread acceptance of single and multi-application smart card technology • The “voice” of the U. S. smart card industry • Secure Personal ID Task Force – Forum to generate a comprehensive body of knowledge regarding the role of smart cards in the identification and security industry and the implementation of smart cardbased systems. – Highly active initiative, with over 25 Alliance member organizations involved Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 3

Content of this Smart. Talk Teleconference (Vanderhoof – Smart Card Alliance) Ø An introduction of the concepts of privacy and security in the context of designing secure ID systems Ø A business perspective of the changing environment today that has lead to the increased focus on safety, security and privacy issues Ø Guidelines for a privacy-sensitive approach to the business practices and system designs of secure ID systems Ø A discussion on role smart cards have to reinforce business practices related to security and privacy rules Ø Some conclusions and perspectives on the needs and trends for privacy and security in secure ID systems and how an individual’s role affects requirements for and/or perceptions of privacy ØQ & A Sponsored by Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 4

Today’s Speakers (Vanderhoof – Smart Card Alliance) • Randy Vanderhoof, Executive Director, Smart Card Alliance • Kent Blossom, Director, IBM Safety & Security Services • Jeff Katz, Vice President of Marketing, Atmel Corporation • Gilles Lisimaque, Senior VP and Co-Founder, Gemplus • Phil Becker, Editor-in-Chief, Digital ID World Presented by Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 5

Introduction: Defining Privacy & Security (Vanderhoof – Smart Card Alliance) • Privacy can be defined as: – “the claim of individuals, groups or institutions to determine for themselves when, how and to what extent information about them is communicated to others” • Privacy protection parameters – When, how and why information is collected from an individual – When, how and why collected information is accessed by authorized entities. – When, how and why information is destroyed – How information is protected from disclosure to, or modification by unauthorized parties, throughout its life cycle – How an individual can control whether information is collected and how it is used and retransmitted – How an individual’s usage preferences are enforced Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 6

Introduction: Defining Privacy & Security (Vanderhoof – Smart Card Alliance) • Information security is a vital element in the design and implementation of a privacy-sensitive system. • Security includes: – Confidentiality: How is information entered, transmitted and stored so that an unauthorized entity cannot access or alter the information? – Integrity: How accurate is the information being held? How is information protected from tampering? How does the system ensure that information is correct and updated? – Availability: Who can access the information and how does the system control access? Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 7

Smart Card Alliance Security and Privacy in the New Era Kent Blossom Director IBM Safety and Security Services Property of Smart Card Alliance Copyright 2003 8

Headline News (Blossom – IBM) Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 9

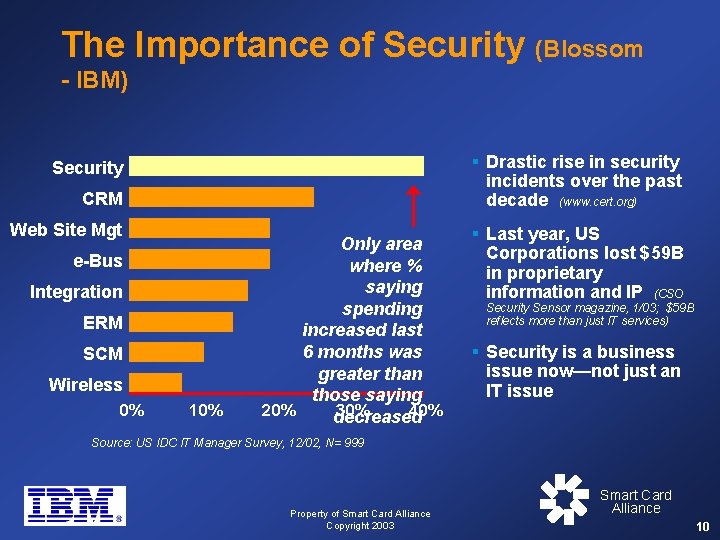
The Importance of Security (Blossom - IBM) § Drastic rise in security Security incidents over the past decade (www. cert. org) CRM Web Site Mgt e-Bus Integration ERM SCM Wireless 0% 10% Only area where % saying spending increased last 6 months was greater than those saying 20% 30% 40% decreased § Last year, US Corporations lost $59 B in proprietary information and IP (CSO Security Sensor magazine, 1/03; $59 B reflects more than just IT services) § Security is a business issue now—not just an IT issue Source: US IDC IT Manager Survey, 12/02, N= 999 Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 10

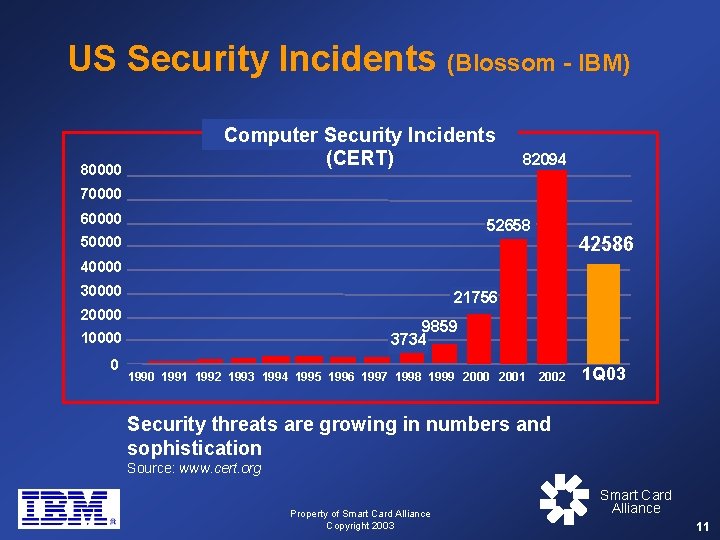
US Security Incidents (Blossom - IBM) 80000 Computer Security Incidents (CERT) 82094 70000 60000 52658 50000 42586 40000 30000 21756 20000 9859 3734 10000 0 1991 1992 1993 1994 1995 1996 1997 1998 1999 2000 2001 2002 1 Q 03 Security threats are growing in numbers and sophistication Source: www. cert. org Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 11

Identity Theft – A Growing Problem (Blossom - IBM) • In May 2002, 73 criminal prosecutions were brought against 135 individuals in 24 districts after a nationwide identity-theft sweep • A recent study by Meridian Research projects that by 2006 the financial institution sector alone will lose $8 billion to identity theft • An estimated 500, 000 to 700, 000 people a year become victims of identity theft • Federal Trade Commission data shows that nearly 86, 000 people filed identity theft complaints in 2001 Source: news. com/2010 -1075 -958328. html June, 2003 Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 12

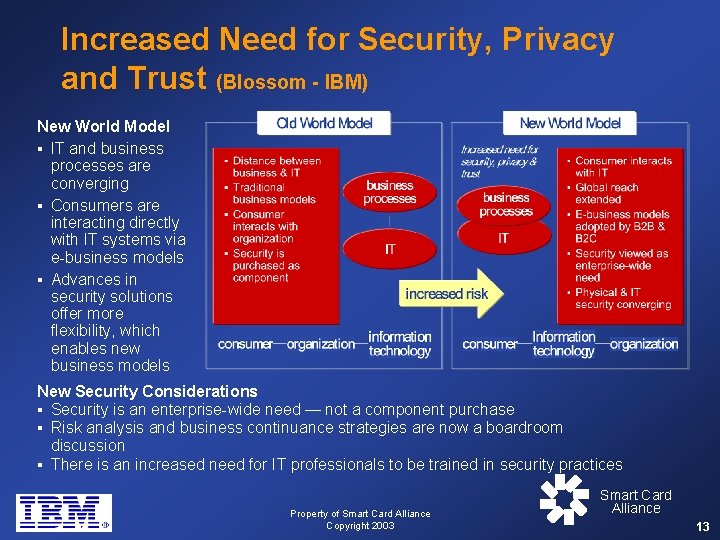
Increased Need for Security, Privacy and Trust (Blossom - IBM) New World Model § IT and business processes are converging § Consumers are interacting directly with IT systems via e-business models § Advances in security solutions offer more flexibility, which enables new business models New Security Considerations § Security is an enterprise-wide need — not a component purchase § Risk analysis and business continuance strategies are now a boardroom discussion § There is an increased need for IT professionals to be trained in security practices Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 13

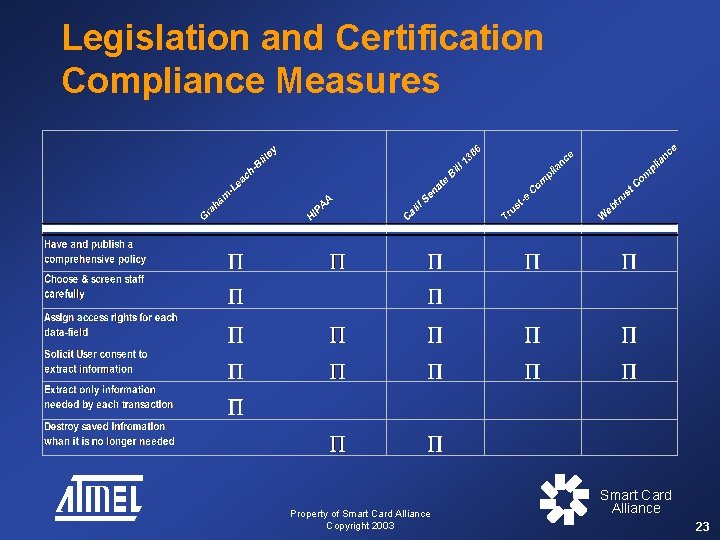
Legislative Trends (Blossom - IBM) • Gramm-Leach-Bliley Act: Privacy of consumer financial information • California Senate Bill 1386: Breach notification disclosure; effective 7/1/03 • Health Insurance Portability and Accountability Act (HIPAA) • Children’s Online Privacy Protection Act (COPPA) • Fair Credit Reporting Act (FCRA) • European Union’s Data Protection Directive Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 14

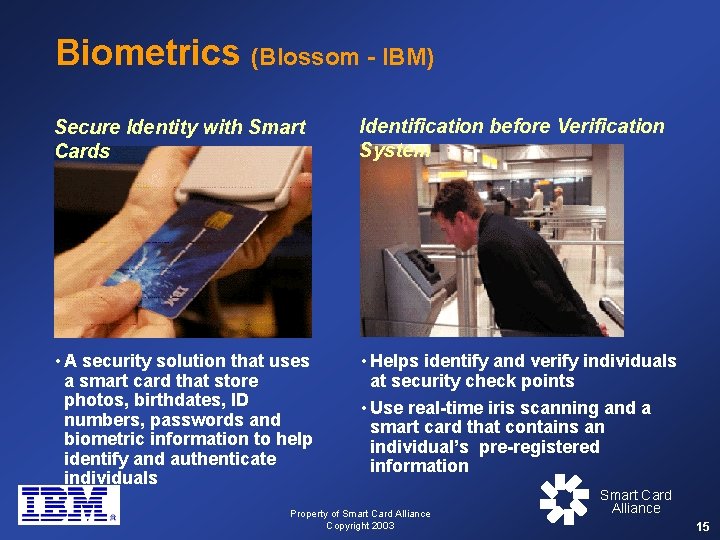
Biometrics (Blossom - IBM) Secure Identity with Smart Cards Identification before Verification System • A security solution that uses a smart card that store photos, birthdates, ID numbers, passwords and biometric information to help identify and authenticate individuals • Helps identify and verify individuals at security check points • Use real-time iris scanning and a smart card that contains an individual’s pre-registered information Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 15

Smart Card Alliance Privacy and Secure ID Systems Practical Guidelines for Privacy-Sensitive Business Practices and System Design Jeff Katz Atmel Corporation Property of Smart Card Alliance Copyright 2003 16

Privacy Protection Guidelines (Katz - Atmel) • Two Critical Objectives • Maximize protection of individuals’ private information • Instill confidence among users that private information is indeed being protected • Note overlap between Security and Privacy • Insecure data can hardly be private • Guidelines that follow are for Strong Privacy Protection • Some ID systems may have priorities that are higher than privacy protection. E. g. auditing who has accessed a bank vault. Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 17

Two Sets of Guidelines (Katz - Atmel) • Business Practice Guidelines • System Design Considerations and Guidelines Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 18

Part 1: Business Practice Guidelines (Katz - Atmel) – Develop and publish a comprehensive privacy policy, including information handling practices – Employee background checks – Staff training – Restriction of staff access to individuals’ personal information Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 19

Part 1: Business Practice Guidelines (Katz - Atmel) – Collection of minimum data required – No display of personal data – Individual notification before information collection: why it is being collected, what it will be used for, who will be able to see it, how it will be protected, consequences of not providing information and rights of redress – Keep personal information only as long as it is necessary to operate the enterprise. Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 20

Part 2: System Design Guidelines (Katz - Atmel) – Encrypt all personal information being stored on all media and destroy original unencrypted information after encryption – Transmit only encrypted information – Use template technology for biometrics – Remove any information captured by an ID card reader or at any intermediate transmission point when transaction is complete – Use individual data field checklists to specify access rights Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 21

Part 2: System Design Guidelines (cont’d) (Katz - Atmel) – Enable cardholders to authorize information extraction with password, PIN or biometric verification – Maximize the off-line portion of transactions, performing on-card verification of identity where possible – Construct ID verification applications that extract only the information required for the transaction – Construct applications so that transaction records cannot be used as surveillance tools Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 22

Legislation and Certification Compliance Measures Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 23

Smart Card Alliance The Role of Smart Cards as a Privacy-Enabling Technology Gilles Lisimaque Senior Vice President Business Development Group Gemplus Corporation Property of Smart Card Alliance Copyright 2003 24

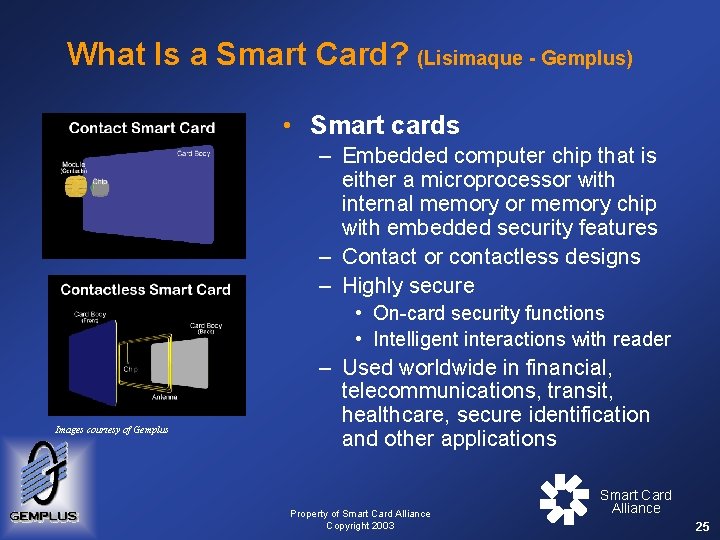
What Is a Smart Card? (Lisimaque - Gemplus) • Smart cards – Embedded computer chip that is either a microprocessor with internal memory or memory chip with embedded security features – Contact or contactless designs – Highly secure • On-card security functions • Intelligent interactions with reader Images courtesy of Gemplus – Used worldwide in financial, telecommunications, transit, healthcare, secure identification and other applications Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 25

A Smart Card Is an Active Intelligent Programmed Device (Lisimaque - Gemplus) • Being able to execute application programs, Smart Cards not only protect information by ciphering them when stored or transferred, they also verify the rights of who asks for it. it Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 26

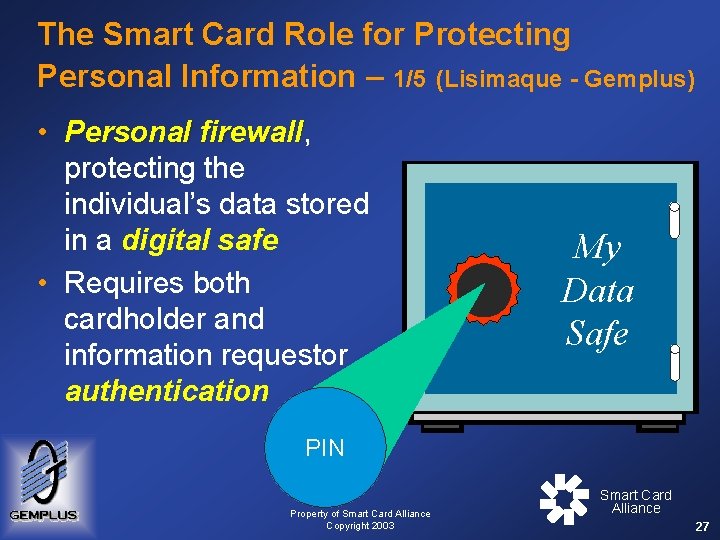
The Smart Card Role for Protecting Personal Information – 1/5 (Lisimaque - Gemplus) • Personal firewall, firewall protecting the individual’s data stored in a digital safe • Requires both cardholder and information requestor authentication My Data Safe PIN Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 27

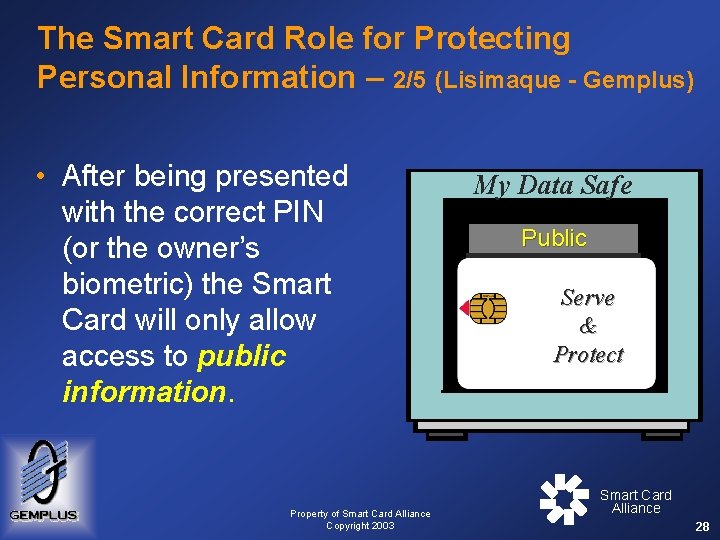
The Smart Card Role for Protecting Personal Information – 2/5 (Lisimaque - Gemplus) • After being presented with the correct PIN (or the owner’s biometric) the Smart Card will only allow access to public information. Property of Smart Card Alliance Copyright 2003 My Data Safe Public Information Serve & Protect Smart Card Alliance 28

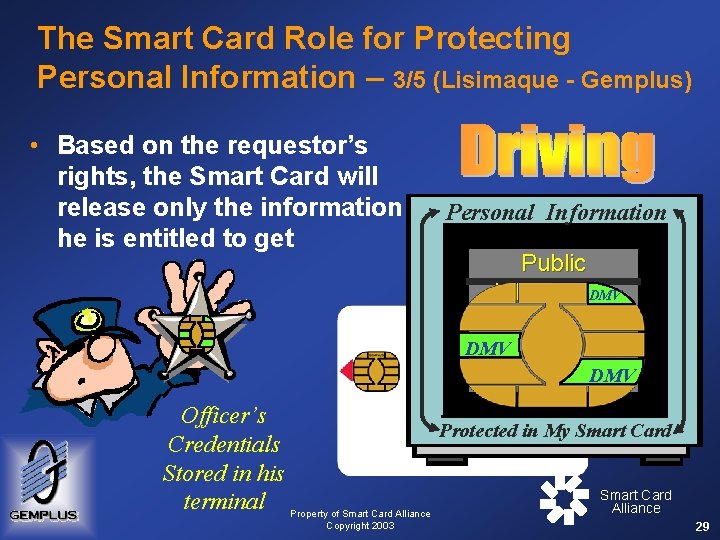
The Smart Card Role for Protecting Personal Information – 3/5 (Lisimaque - Gemplus) • Based on the requestor’s rights, the Smart Card will release only the information he is entitled to get Personal Information Public Information DMV & Serve Protect DMV Officer’s Protected in My Smart Card Credentials Stored in his Smart Card terminal Property of Smart Card Alliance Copyright 2003 29

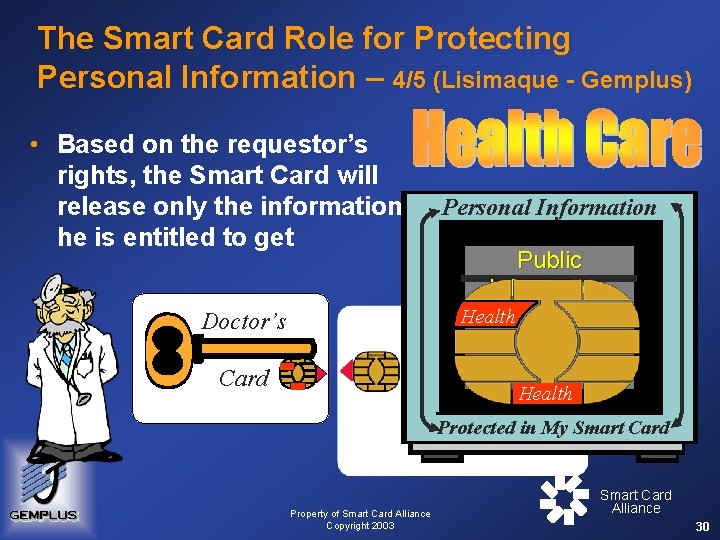
The Smart Card Role for Protecting Personal Information – 4/5 (Lisimaque - Gemplus) • Based on the requestor’s rights, the Smart Card will release only the information he is entitled to get Personal Information Public Information Health Doctor’s Serve & Protect Health Card Protected in My Smart Card Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 30

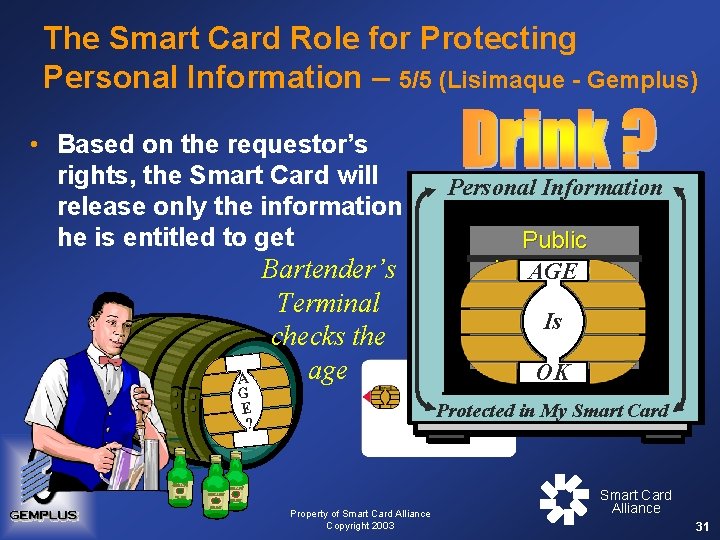
The Smart Card Role for Protecting Personal Information – 5/5 (Lisimaque - Gemplus) • Based on the requestor’s rights, the Smart Card will release only the information he is entitled to get A G E ? Bartender’s Terminal checks the age Personal Information Public Information AGE Information Serve Is & Protect OK Protected in My Smart Card Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 31

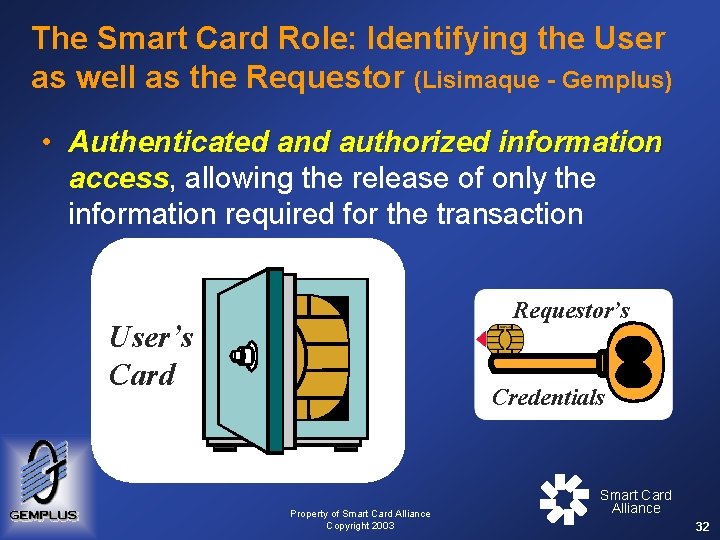
The Smart Card Role: Identifying the User as well as the Requestor (Lisimaque - Gemplus) • Authenticated and authorized information access, access allowing the release of only the information required for the transaction Requestor’s User’s Card Credentials Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 32

Smart Cards Are Packed with Security Features (Lisimaque - Gemplus) • Strong ID card security – Tamper-resistance – Extreme difficulty of duplicating or forging cards • Data security, ensuring the privacy, authenticity and integrity of data encoded on the ID card – Encryption – Digital signatures – Prevention of information sharing among applications • System challenges, authenticating the legitimacy of system components Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 33

The Smart Card Privacy Role for Personal Identification (Lisimaque - Gemplus) • Convenient identity verification, with the smart card containing all information needed to confirm the cardholder’s identity in the role he is at a given time (Driving, Patient, Taxpayer, etc. ) • On-card match, with all identity information and processing done on the smart ID card and only results sent to external devices – Information released only on a need to know basis • Cost-effective offline verification – Small, secure, portable and low cost smart card readers at multiple locations where identity needs to be verified Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 34

The Smart Card Is Only a Piece of a Puzzle in Protecting Privacy (Lisimaque - Gemplus) • As for a house, where the key and the locks are important elements protecting the homeowner, the Smart Card’s inherent security makes sense only when integrated as part of a whole system designed to protect privacy and provide security. • Smart Cards play an important role in being able to enforce the security and privacy rules of the application. • The system as a whole (terminals, communications, back end systems and policies) needs to be considered in order to evaluate the real security and privacy provided to the user. Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 35

Smart Card Alliance Needs/Trends for Privacy and Security in Secure ID Systems Phil Becker Editor-in-Chief Digital ID World Property of Smart Card Alliance Copyright 2003 36

Security Drivers (Becker – Digital ID World) • Dramatic Rise in Security “Incidents” • Protection of Proprietary Information & IP • Identity Theft rapidly increasing Networking has fundamentally altered the security challenge requiring identity in the solution Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 37

How Networking Changed Things (Becker – Digital ID World) • Virtually links formerly distributed operations • Distributes formerly single location operations • Physical location security doesn’t translate automatically to computer network security • Identity must become embedded part of network transactions to assure security Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 38

Identity Privacy Drivers (Becker – Digital ID World) • Legal and Regulatory Compliance • Citizen Concerns and Trust • Business Customer Confidence Networking has dramatically increased opportunity for personal data to be aggregated and compromised Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 39

Privacy Perception Differs by Role (Becker – Digital ID World) • Employee – Most relevant personal data is considered company property, so privacy is a much smaller issue • Private Citizen – Most relevant personal data is considered the citizen’s property, so privacy is a much larger issue • Public Citizen – Interacting with government or regulated services citizen is required to present private data and needs assurance of its protection from inappropriate distribution Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 40

Identity and Privacy (Becker – Digital ID World) • Use of Identity is required for transaction security • Using Identity raises privacy issues • The role of each person changes the implications of these privacy issues Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 41

Identity and Privacy (Becker – Digital ID World) • Regulatory/Legal compliance forces privacy consideration • Network infrastructure must thus be designed to leverage identity without compromising it • Smart Cards allow great flexibility in designing a privacy enhancing secure identity system Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 42

References and Supporting Documents (Vanderhoof – Smart Card Alliance) • Smart Card Alliance White Paper: Privacy and Secure Identification Systems: The Role of Smart Cards as a Privacy-Enabling Technology – February, 2003 • Smart Card Alliance White Paper: Smart Cards and Biometrics in a Privacy-Sensitive Secure ID System – May, 2002 • Smart Card Alliance White Paper: Secure Personal ID Systems: Policy, Process and Technology Choices for a Privacy-Sensitive Solution – February, 2002 http: //www. smartcardalliance. org Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 43

Future Smart Card Alliance Activities (Vanderhoof – Smart Card Alliance) Conferences: Smart Cards in Government - 2003: July 15 -17, 2003, Sheraton National Hotel – Arlington, VA Smart Cards In Motion Conference: October 14 -16, 2003 Sawgrass Marriott Resort – Ponte Vedra Beach, FL Smart. Talk Teleconferences: “Ask the Experts” Roundtable – December, 2003 Secure Personal ID Task Force To subscribe to the monthly Smart Card Talk Newsletter, send email to info@smartcardalliance. org Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 44

Smart Card Alliance Questions & Answers To ask a question, please press *1 and an operator will open your line for questions. Property of Smart Card Alliance Copyright 2003 45

For More Information Randy Vanderhoof, Smart Card Alliance (800) 556 - 6828 rvanderhoof@smartcardalliance. org www. smartcardalliance. org Kent Blossom, IBM Safety & Security Services kblossom@us. ibm. com www. ibm. com/services/security Jeff Katz, Atmel Corp. jkatz@atmel. com www. atmel. com Gilles Lisimaque, Gemplus gilles. lisimaque@gemplus. com www. istpa. org Phil Becker, Digital ID World phil@digitalidworld. com www. digitalidworld. com Property of Smart Card Alliance Copyright 2003 Smart Card Alliance 46