SIRIUS COMPUTER SOLUTIONS Security Intelligence www siriuscom com

















- Slides: 47

SIRIUS COMPUTER SOLUTIONS Security Intelligence www. siriuscom. com 2/25/2021 1

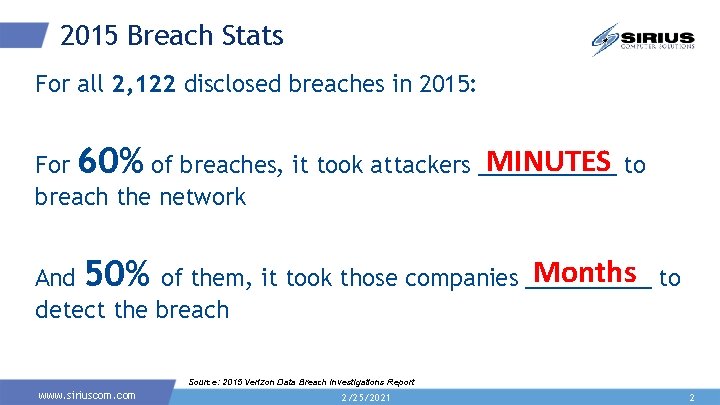
2015 Breach Stats For all 2, 122 disclosed breaches in 2015: MINUTES to For 60% of breaches, it took attackers ______ breach the network Months to And 50% of them, it took those companies _____ detect the breach Source: 2015 Verizon Data Breach Investigations Report www. siriuscom. com 2/25/2021 2

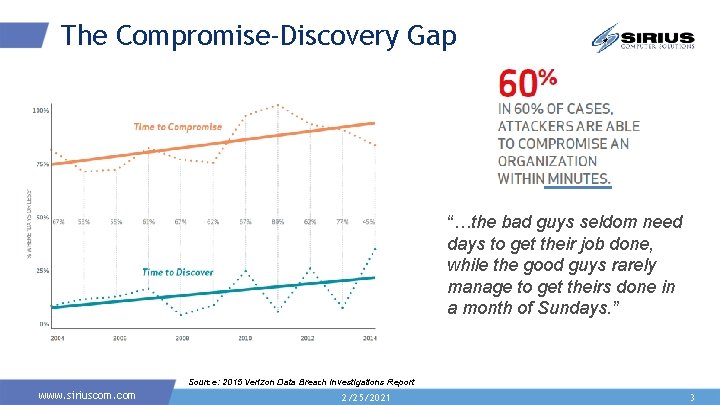
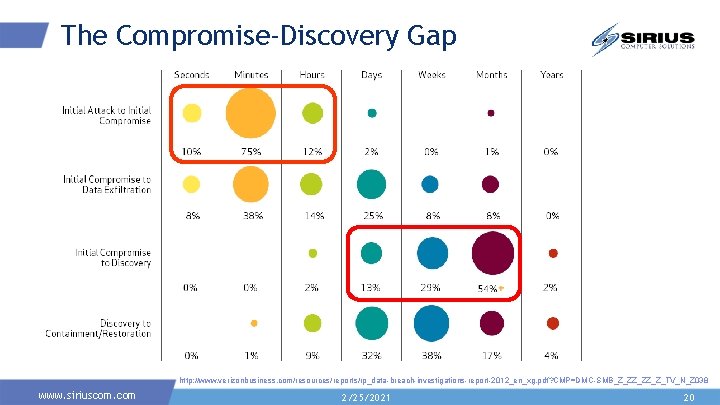
The Compromise-Discovery Gap “…the bad guys seldom need days to get their job done, while the good guys rarely manage to get theirs done in a month of Sundays. ” Source: 2015 Verizon Data Breach Investigations Report www. siriuscom. com 2/25/2021 3

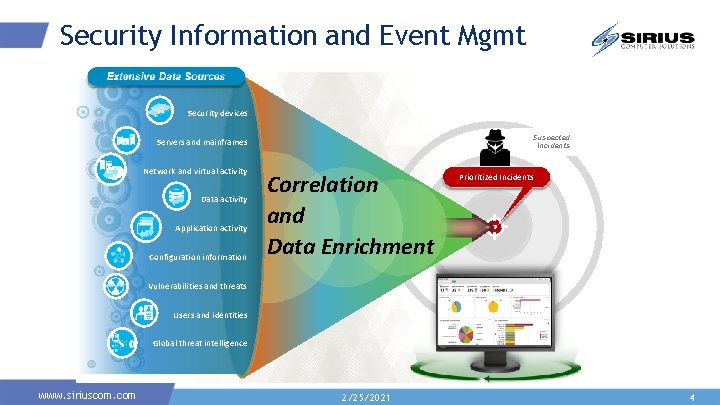
Security Information and Event Mgmt Security devices Suspected Incidents Servers and mainframes Network and virtual activity Data activity Application activity Configuration information Correlation and Data Enrichment Prioritized Incidents Vulnerabilities and threats Users and identities Global threat intelligence www. siriuscom. com 2/25/2021 4

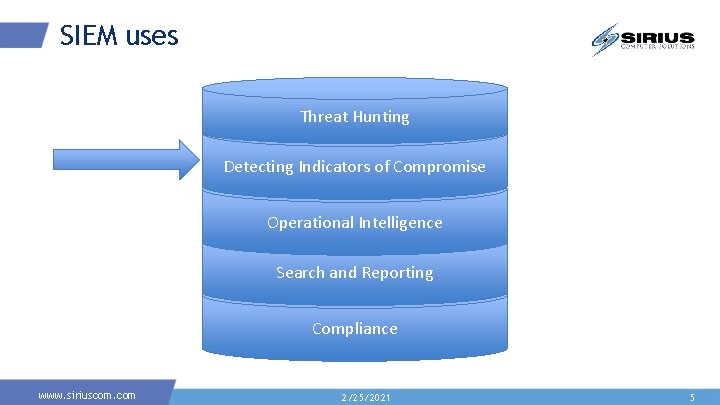
SIEM uses Threat Hunting Detecting Indicators of Compromise Operational Intelligence Search and Reporting Compliance www. siriuscom. com 2/25/2021 5

The Cyber Kill Chain Pre-Compromise Post-Compromise www. siriuscom. com 2/25/2021 6

Increasing risk and cost to contain and/or remediate The Cyber Kill Chain www. siriuscom. com 2/25/2021 7

www. siriuscom. com Increasing risk and cost to contain and/or remediate Opportunity for Detection Opportunity 2/25/2021 8

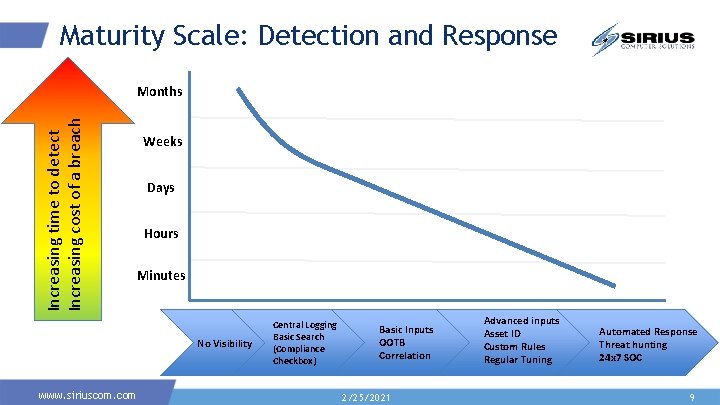
Maturity Scale: Detection and Response Increasing time to detect Increasing cost of a breach Months Weeks Days Hours Minutes No Visibility www. siriuscom. com Central Logging Basic Search (Compliance Checkbox) Basic Inputs OOTB Correlation 2/25/2021 Advanced inputs Asset ID Custom Rules Regular Tuning Automated Response Threat hunting 24 x 7 SOC 9

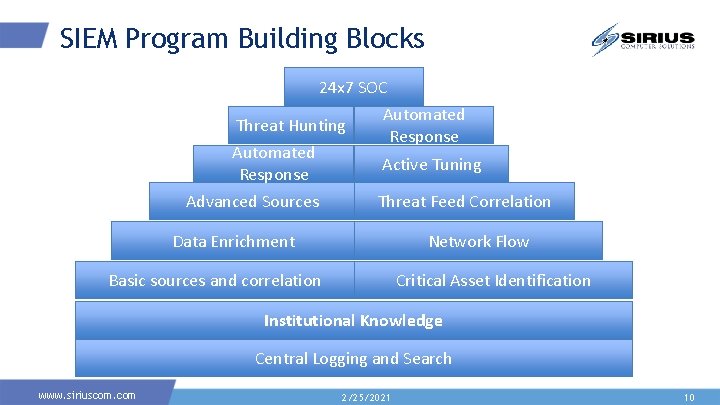
SIEM Program Building Blocks 24 x 7 SOC Threat Hunting Automated Response Advanced Sources Automated Response Active Tuning Threat Feed Correlation Data Enrichment Network Flow Basic sources and correlation Critical Asset Identification Institutional Knowledge Central Logging and Search www. siriuscom. com 2/25/2021 10

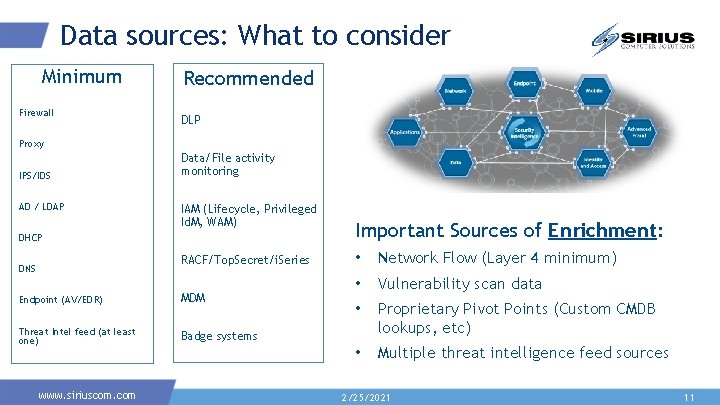
Data sources: What to consider Minimum Firewall Recommended DLP Proxy IPS/IDS AD / LDAP Data/File activity monitoring IAM (Lifecycle, Privileged Id. M, WAM) DHCP RACF/Top. Secret/i. Series DNS Endpoint (AV/EDR) MDM Threat Intel feed (at least one) Badge systems www. siriuscom. com Important Sources of Enrichment: • Network Flow (Layer 4 minimum) • Vulnerability scan data • Proprietary Pivot Points (Custom CMDB lookups, etc) • Multiple threat intelligence feed sources 2/25/2021 11

General SIEM “Best Practices” -Identify your High Business Impact assets (HBI) -Critical database servers, CFO’s laptop, etc -Define use cases around those assets -Based on use cases, determine what data you need and implement. www. siriuscom. com 2/25/2021 12

Shine a Spotlight on your critical assets and power users www. siriuscom. com 2/25/2021 13

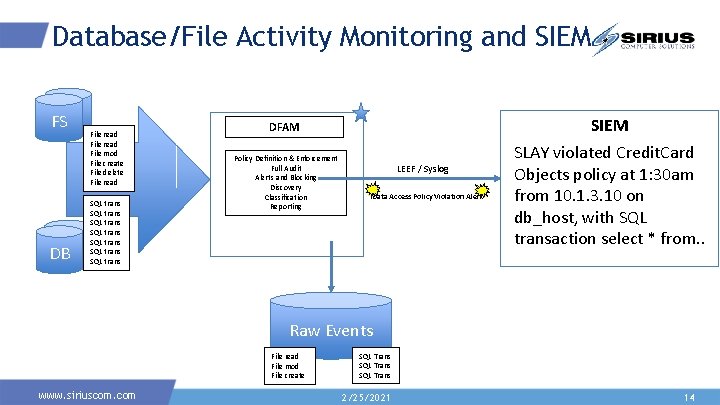
Database/File Activity Monitoring and SIEM FSFS DB DB File read File mod File create File delete File read SQL trans SQL trans SIEM DFAM Policy Definition & Enforcement Full Audit Alerts and Blocking Discovery Classification Reporting LEEF / Syslog Data Access Policy Violation Alert SLAY violated Credit. Card Objects policy at 1: 30 am from 10. 1. 3. 10 on db_host, with SQL transaction select * from. . Raw Events File read File mod File create www. siriuscom. com SQL Trans 2/25/2021 14

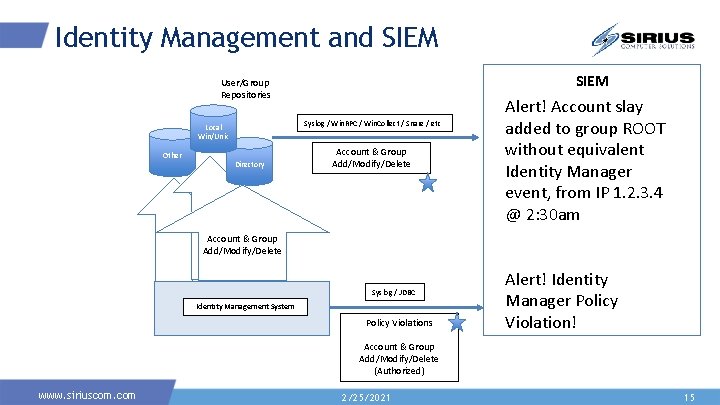
Identity Management and SIEM User/Group Repositories Syslog / Win. RPC / Win. Collect / Snare / etc Local Win/Unix Other Directory Account & Group Add/Modify/Delete Alert! Account slay added to group ROOT without equivalent Identity Manager event, from IP 1. 2. 3. 4 @ 2: 30 am Account & Group Add/Modify/Delete Syslog / JDBC Identity Management System Policy Violations Alert! Identity Manager Policy Violation! Account & Group Add/Modify/Delete (Authorized) www. siriuscom. com 2/25/2021 15

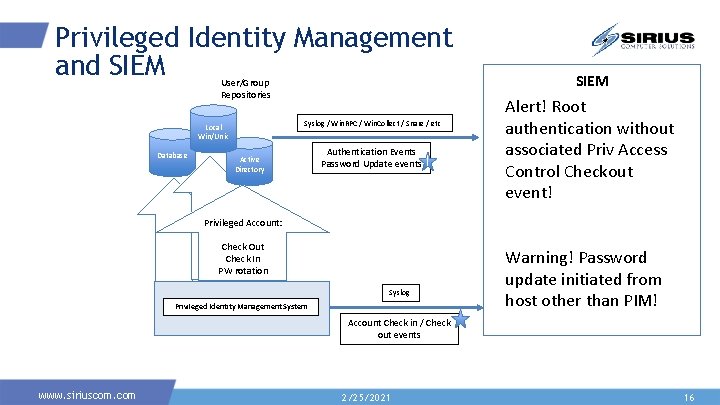
Privileged Identity Management and SIEM User/Group Repositories Syslog / Win. RPC / Win. Collect / Snare / etc Local Win/Unix Database Active Directory Authentication Events Password Update events SIEM Alert! Root authentication without associated Priv Access Control Checkout event! Privileged Account: Check Out Check In PW rotation Syslog Privileged Identity Management System Warning! Password update initiated from host other than PIM! Account Check in / Check out events www. siriuscom. com 2/25/2021 16

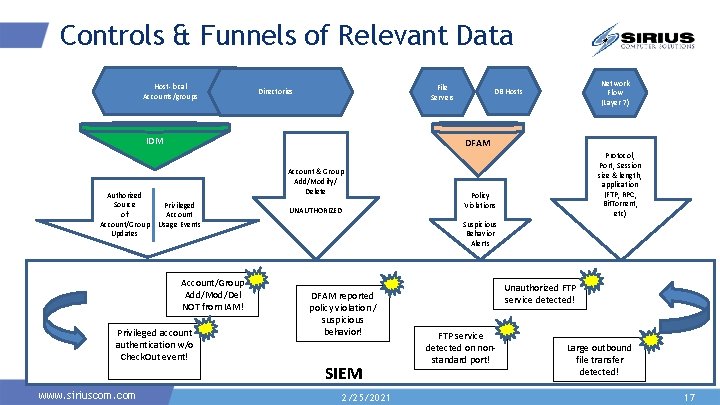
Controls & Funnels of Relevant Data Host-local Accounts/groups File Servers Directories IDM Authorized Source of Account/Group Updates DFAM Account & Group Add/Modify/ Delete Privileged Account Usage Events Account/Group Add/Mod/Del NOT from IAM! Privileged account authentication w/o Check. Out event! www. siriuscom. com Network Flow (Layer 7) DB Hosts UNAUTHORIZED Protocol, Port, Session size & length, application (FTP, RPC, Bit. Torrent, etc) Policy Violations Suspicious Behavior Alerts DFAM reported policy violation / suspicious behavior! SIEM 2/25/2021 Unauthorized FTP service detected! FTP service detected on nonstandard port! Large outbound file transfer detected! 17

General Patterns of Success An effective SIEM should enable the use of intuition and institutional knowledge of the IT infrastructure. -Know what you want out of a SIEM! What are your priorities? Compliance Clear visibility and rapid response Threat hunting Operational intelligence -Deploy around use cases, aligned with organizational priorities: -Detecting IOCs / Policy violations -Dashboards, reports for various interested parties (C-level, directors, IT, Op/Infosec, community) -Threat hunting -Identifying Shadow IT activity: unapproved servers, services, directories, and so on www. siriuscom. com 2/25/2021 general user 18

THANK YOU www. siriuscom. com

The Compromise-Discovery Gap Time span of events by percent of breaches http: //www. verizonbusiness. com/resources/reports/rp_data-breach-investigations-report-2012_en_xg. pdf? CMP=DMC-SMB_Z_ZZ_ZZ_Z_TV_N_Z 038 www. siriuscom. com 2/25/2021 20

Wrap up with SIEM Best Practice Series Short, basic description of best practice series SIEM general, not vendor specific SIEM general, w/ lite vendor specific health check Splunk, QRadar SIEM decision criteria development (We also have paid services for deep dive health checks, tuning, and support) www. siriuscom. com 2/25/2021 21

Wrap up here Thanks, anything else? Q&A? www. siriuscom. com 2/25/2021 22

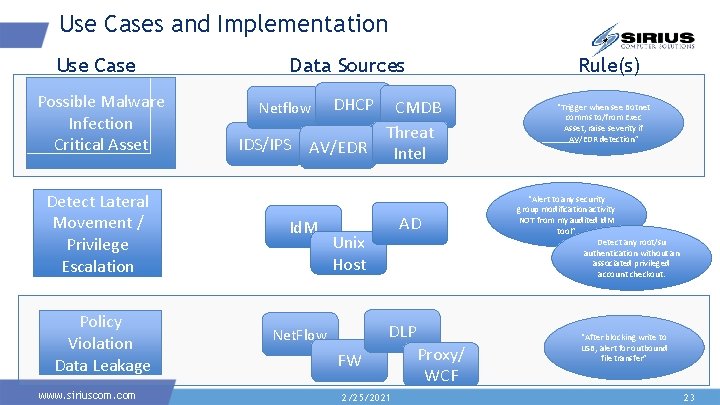
Use Cases and Implementation Use Case Possible Malware Infection Critical Asset Detect Lateral Movement / Privilege Escalation Policy Violation Data Leakage www. siriuscom. com Data Sources Netflow IDS/IPS DHCP AV/EDR Id. M Rule(s) CMDB Threat Intel AD Unix Host DLP Net. Flow FW 2/25/2021 Proxy/ WCF “Trigger when see Botnet comms to/from Exec Asset, raise severity if AV/EDR detection” “Alert to any security group modification activity NOT from my audited Id. M tool” Detect any root/su authentication without an associated privileged account checkout. “After blocking write to USB, alert for outbound file transfer” 23

Degrees of Visibility www. siriuscom. com 2/25/2021 24

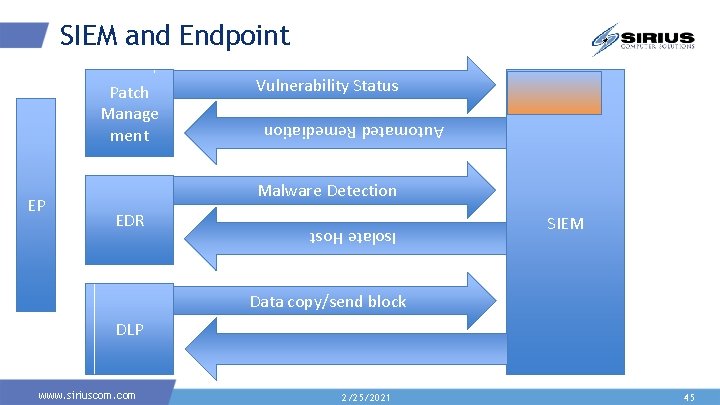
SIEM and Endpoint *IMPROVE THIS* Endpoint Raw Data: Process activity Open Services Adv Malware / EDR DLP SIEM and E The Host www. siriuscom. com 2/25/2021 25

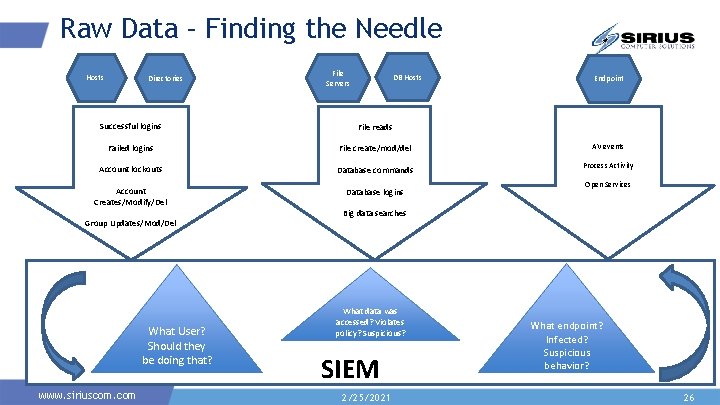
Raw Data – Finding the Needle Hosts Directories File Servers DB Hosts Endpoint Successful logins File reads Failed logins File create/mod/del AV events Account lockouts Database commands Process Activity Account Creates/Modify/Del Database logins Group Updates/Mod/Del What User? Should they be doing that? www. siriuscom. com Open Services Big data searches What data was accessed? Violates policy? Suspicious? SIEM 2/25/2021 What endpoint? Infected? Suspicious behavior? 26

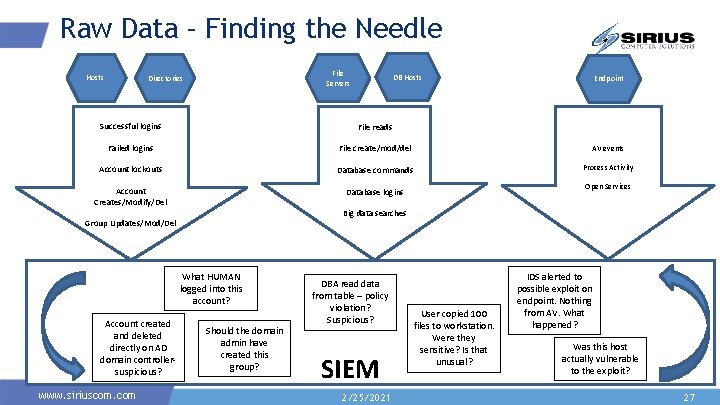
Raw Data – Finding the Needle Hosts File Servers Directories DB Hosts Endpoint Successful logins File reads Failed logins File create/mod/del AV events Account lockouts Database commands Process Activity Account Creates/Modify/Del Database logins Big data searches Group Updates/Mod/Del What HUMAN logged into this account? Account created and deleted directly on AD domain controllersuspicious? www. siriuscom. com Open Services Should the domain admin have created this group? DBA read data from table – policy violation? Suspicious? SIEM 2/25/2021 User copied 100 files to workstation. Were they sensitive? Is that unusual? IDS alerted to possible exploit on endpoint. Nothing from AV. What happened? Was this host actually vulnerable to the exploit? 27

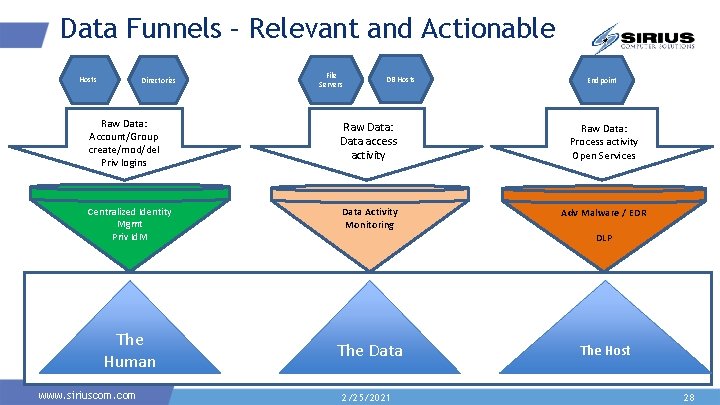
Data Funnels – Relevant and Actionable Hosts Directories File Servers DB Hosts Endpoint Raw Data: Account/Group create/mod/del Priv logins Raw Data: Data access activity Raw Data: Process activity Open Services Centralized Identity Mgmt Priv Id. M Data Activity Monitoring Adv Malware / EDR The Human www. siriuscom. com DLP The Data 2/25/2021 The Host 28

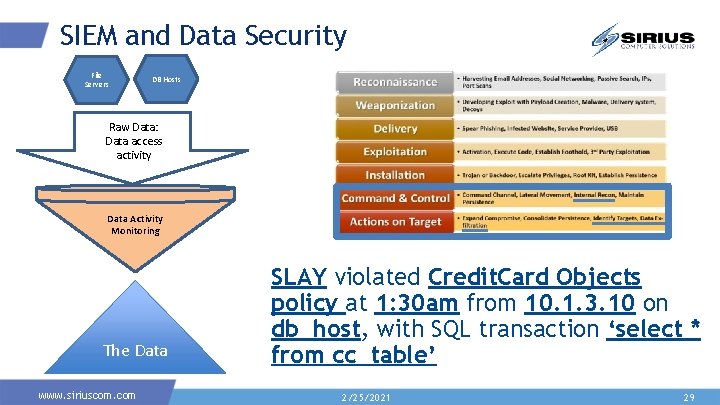
SIEM and Data Security File Servers DB Hosts Raw Data: Data access activity Data Activity Monitoring The Data www. siriuscom. com SLAY violated Credit. Card Objects policy at 1: 30 am from 10. 1. 3. 10 on db_host, with SQL transaction ‘select * from cc_table’ 2/25/2021 29

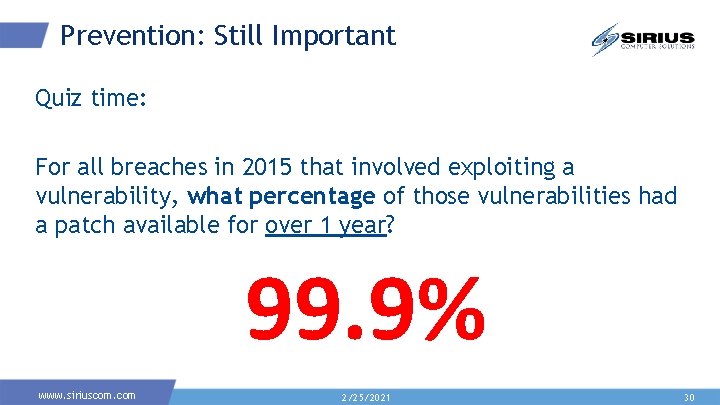
Prevention: Still Important Quiz time: For all breaches in 2015 that involved exploiting a vulnerability, what percentage of those vulnerabilities had a patch available for over 1 year? 99. 9% www. siriuscom. com 2/25/2021 30

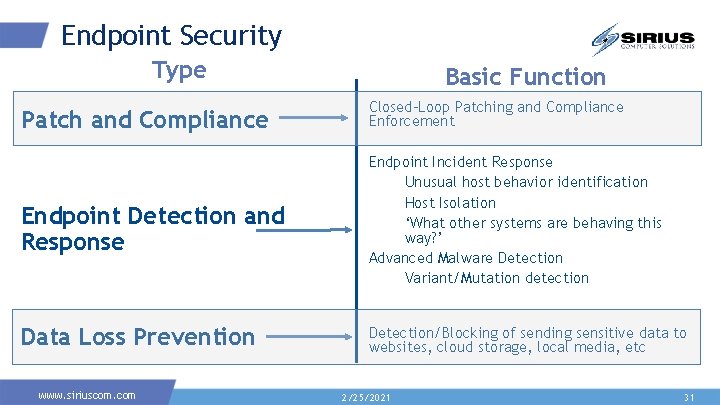
Endpoint Security Type Patch and Compliance Endpoint Detection and Response Data Loss Prevention www. siriuscom. com Basic Function Closed-Loop Patching and Compliance Enforcement Endpoint Incident Response Unusual host behavior identification Host Isolation ‘What other systems are behaving this way? ’ Advanced Malware Detection Variant/Mutation detection Detection/Blocking of sending sensitive data to websites, cloud storage, local media, etc 2/25/2021 31

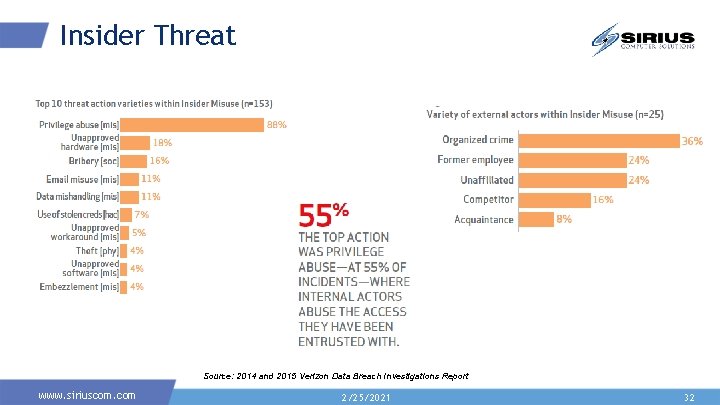
Insider Threat Source: 2014 and 2015 Verizon Data Breach Investigations Report www. siriuscom. com 2/25/2021 32

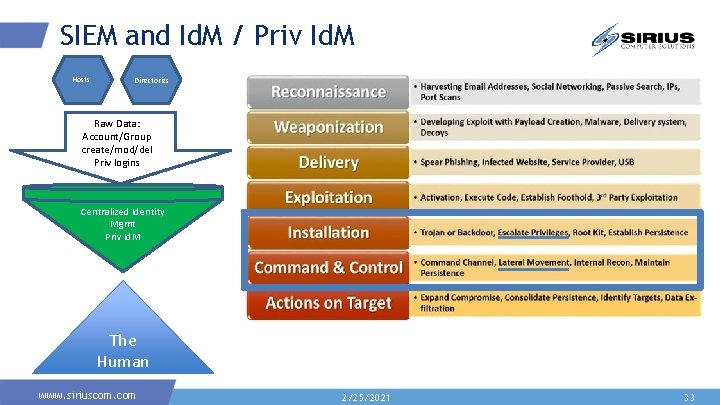
SIEM and Id. M / Priv Id. M Hosts Directories Raw Data: Account/Group create/mod/del Priv logins Centralized Identity Mgmt Priv Id. M The Human www. siriuscom. com 2/25/2021 33

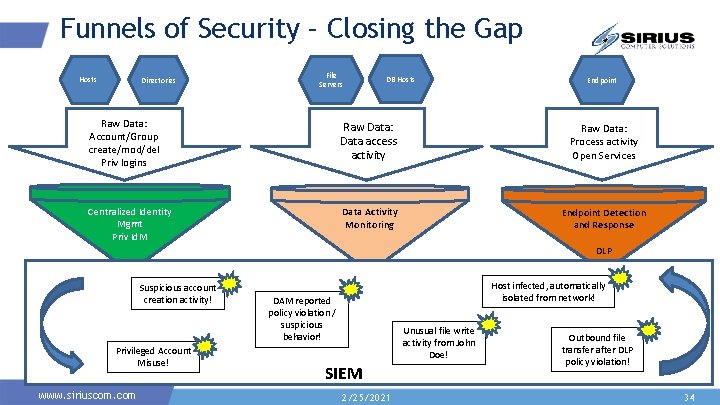
Funnels of Security – Closing the Gap Hosts Directories File Servers DB Hosts Endpoint Raw Data: Account/Group create/mod/del Priv logins Raw Data: Data access activity Raw Data: Process activity Open Services Centralized Identity Mgmt Priv Id. M Data Activity Monitoring Endpoint Detection and Response DLP Suspicious account creation activity! Privileged Account Misuse! www. siriuscom. com Host infected, automatically isolated from network! DAM reported policy violation / suspicious behavior! Unusual file write activity from John Doe! SIEM 2/25/2021 Outbound file transfer after DLP policy violation! 34

General Patterns of Success -Know what you want out of a SIEM! -What are your priorities? Compliance? Effective visibility and response? Threat hunting? Operational intelligence? -Align your decision criteria with: -Your immediate and long term priorities -Your resource constraints -Level of product-proprietary skillset required -An effective SIEM should enable the use of intuition and institutional knowledge of the IT infrastructure to rapidly and effectively identify what is occurring, users/assets involved, and to take immediate action. -Accept that tuning is iterative, and a way of life in the security world -Signal to noise ratio direct impacts tool effectiveness and resource requirements -The more information sent to the SIEM, the better www. siriuscom. com 2/25/2021 35

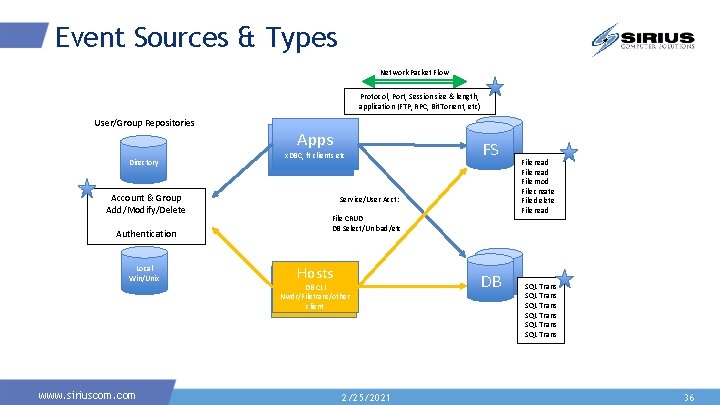
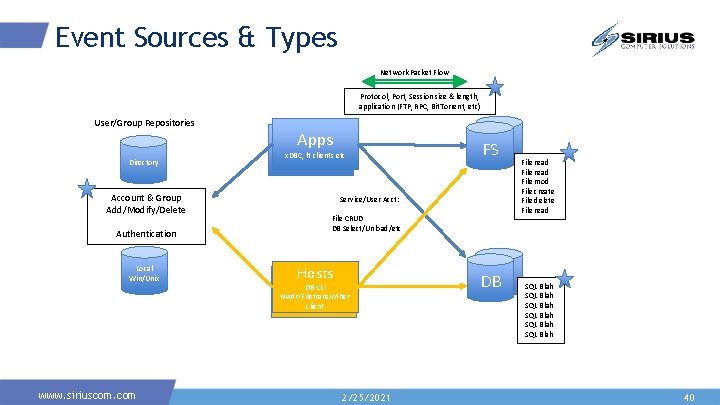
Event Sources & Types Network Packet Flow Protocol, Port, Session size & length, application (FTP, RPC, Bit. Torrent, etc) User/Group Repositories Directory Account & Group Add/Modify/Delete Authentication Local Win/Unix www. siriuscom. com Apps x. DBC, ft clients etc FSFS Service/User Acct: File CRUD DB Select/Unload/etc Hosts DB CLI Nwdr/Filetrans/other client 2/25/2021 DB DB File read File mod File create File delete File read SQL Trans SQL Trans 36

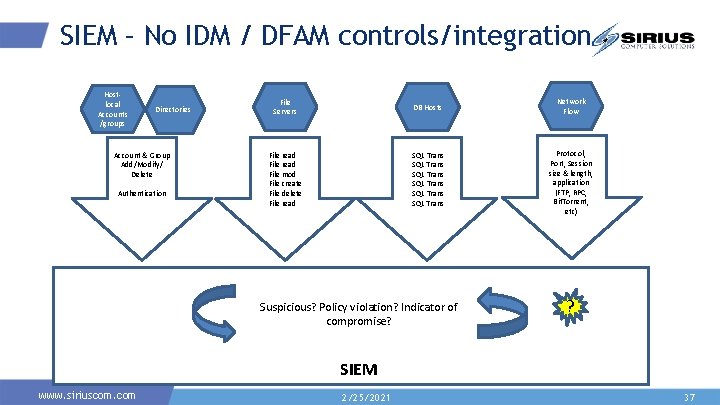
SIEM – No IDM / DFAM controls/integration Hostlocal Accounts /groups Directories Account & Group Add/Modify/ Delete Authentication File Servers DB Hosts Network Flow File read File mod File create File delete File read SQL Trans SQL Trans Protocol, Port, Session size & length, application (FTP, RPC, Bit. Torrent, etc) Suspicious? Policy violation? Indicator of compromise? ? SIEM www. siriuscom. com 2/25/2021 37

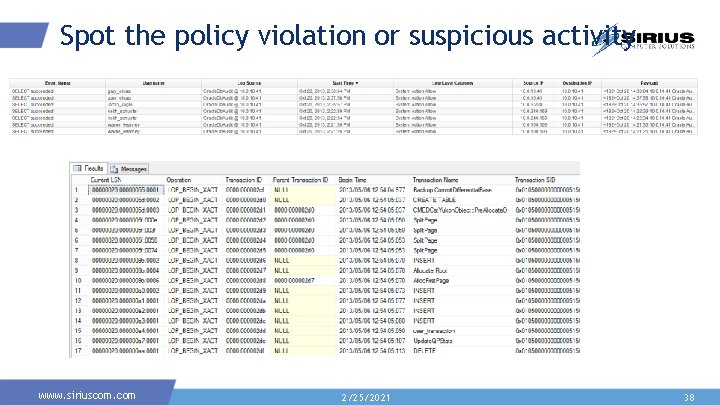
Spot the policy violation or suspicious activity www. siriuscom. com 2/25/2021 38

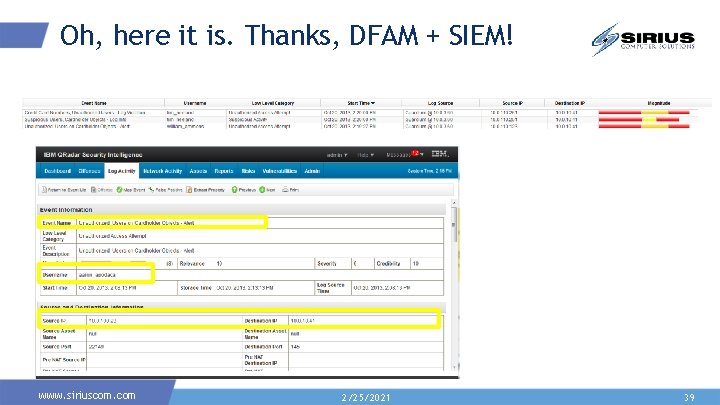
Oh, here it is. Thanks, DFAM + SIEM! www. siriuscom. com 2/25/2021 39

Event Sources & Types Network Packet Flow Protocol, Port, Session size & length, application (FTP, RPC, Bit. Torrent, etc) User/Group Repositories Directory Account & Group Add/Modify/Delete Authentication Local Win/Unix www. siriuscom. com Apps x. DBC, ft clients etc FSFS Service/User Acct: File CRUD DB Select/Unload/etc Hosts DB CLI Nwdr/Filetrans/other client 2/25/2021 DB DB File read File mod File create File delete File read SQL Blah SQL Blah 40

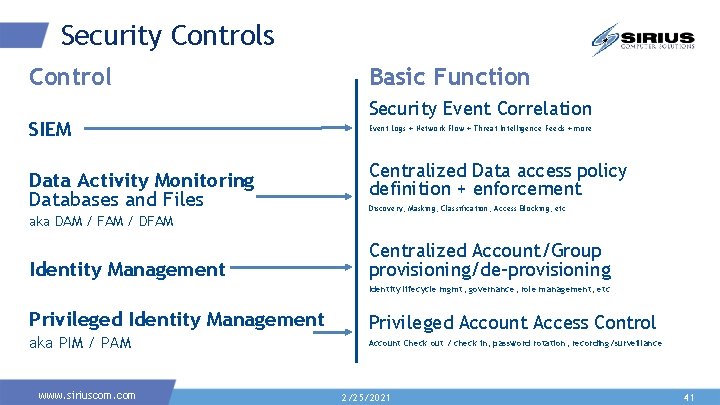
Security Controls Control SIEM Data Activity Monitoring Databases and Files Basic Function Security Event Correlation Event Logs + Network Flow + Threat Intelligence Feeds + more Centralized Data access policy definition + enforcement Discovery, Masking, Classification, Access Blocking, etc aka DAM / FAM / DFAM Identity Management Centralized Account/Group provisioning/de-provisioning Identity lifecycle mgmt, governance, role management, etc Privileged Identity Management aka PIM / PAM www. siriuscom. com Privileged Account Access Control Account Check out / check in, password rotation, recording/surveillance 2/25/2021 41

SIEM and Incident Response -IBM leading the way and investing heavily -Acquired Resilient Systems for incident response tracking -Partnership with Carbon Black, leading EDR solution -Native features support effective, timely incident response -Chained incidents and data enrichment -Fully integrated security intelligence platform -Vulnerability management -Risk management -Incident forensics “Incident Response is one of the most overlooked areas of INFOSEC” Forrester Research www. siriuscom. com 2/25/2021 42

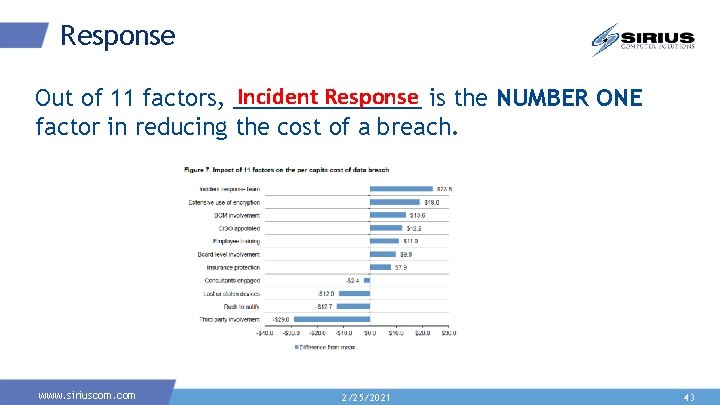
Response Incident Response is the NUMBER ONE Out of 11 factors, ________ factor in reducing the cost of a breach. www. siriuscom. com 2/25/2021 43

Importance of Incident Response <Ponemon codb stat> <fireman analogy. Have great preventative measures in place- building is up to code, sprinkler systems. Have great alerting capabilities in place- alarms at every door, smoke detectors. But if it takes the fire dept 5 hours to show up at the doorstep, what is any of the rest really worth? Or if they show up quickly, without the necessary tools? Think there’s a difference between a part time volunteer fire dept and a city dept with full time seasoned vets? > DO not underestimate the importance to incident response planning, team, and incident response tracking TOOL. Gives your team a way to effective implement the plan that is in place. www. siriuscom. com 2/25/2021 44

SIEM and Endpoint Malware Detection EDR Isolate Host EP Vulnerability Status Automated Remediation Patch Manage ment SIEM Data copy/send block DLP www. siriuscom. com 2/25/2021 45

Matrix Sample matrix: IOCs/Policy Violations -> Sources -> Rules / dependencies <High level> <Consumable by business to understand gaps in visibility and associated risk> <HINT: We can help you do this!> www. siriuscom. com 2/25/2021 46

Examples of current challenges Where is my data, who has access to it, who is accessing it? Lacking visibility Detection / defense against cryptoware Detecting the hidden threats. “What are we NOT seeing? ” Meeting these challenges with resource strapped teams www. siriuscom. com 2/25/2021 47