Simple efficient mutual anonymity protocols for peertopeer network






- Slides: 19

Simple efficient mutual anonymity protocols for peer-to-peer network based on primitive roots Source: Journal of Network and Computer Applications, vol. 30, pp. 662 -676, 2007. Authors: Chin-Chen Chang, Chih-Yang Lin, and Keng-Chu Lin Speaker: Shu-Fen Chiou (邱淑芬) 1

Outline n n Introduction Xiao et al. ’s protocols Proposed method Conclusion 2

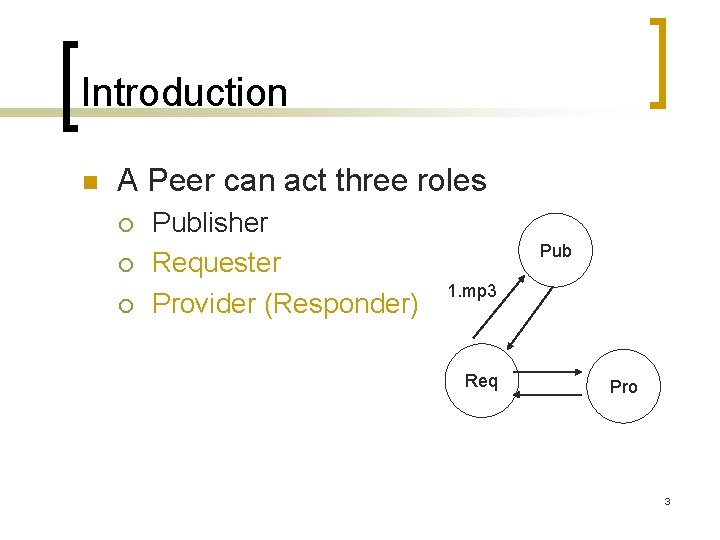
Introduction n A Peer can act three roles ¡ ¡ ¡ Publisher Requester Provider (Responder) Pub 1. mp 3 Req Pro 3

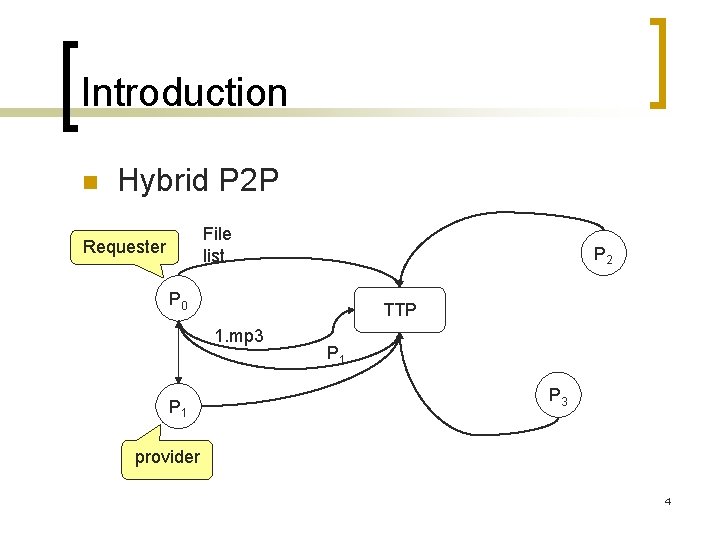
Introduction n Hybrid P 2 P File list Requester P 2 P 0 TTP 1. mp 3 P 1 P 3 provider 4

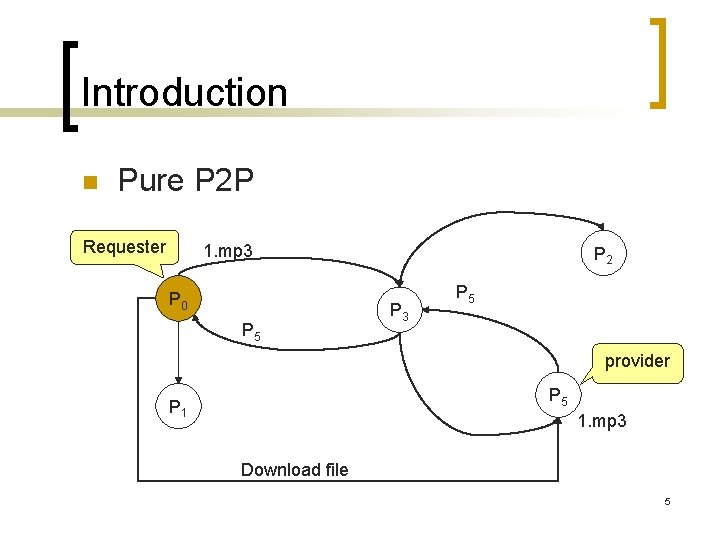
Introduction n Pure P 2 P Requester 1. mp 3 P 0 P 5 P 2 P 3 P 5 provider P 5 P 1 1. mp 3 Download file 5

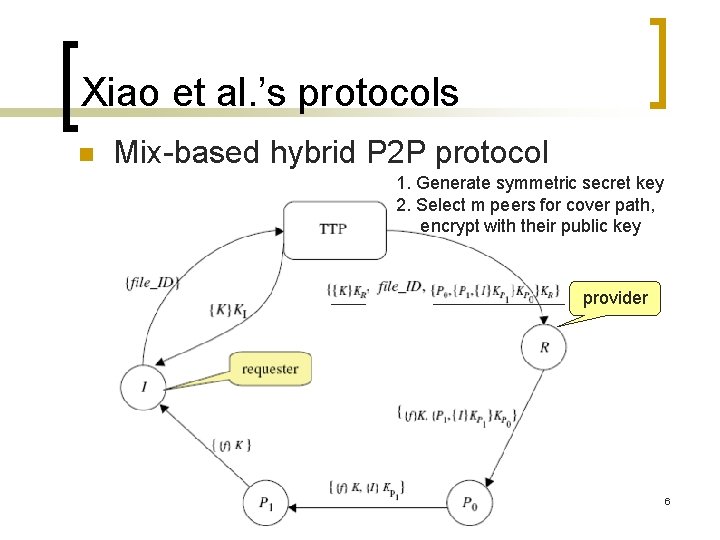
Xiao et al. ’s protocols n Mix-based hybrid P 2 P protocol 1. Generate symmetric secret key 2. Select m peers for cover path, encrypt with their public key provider 6

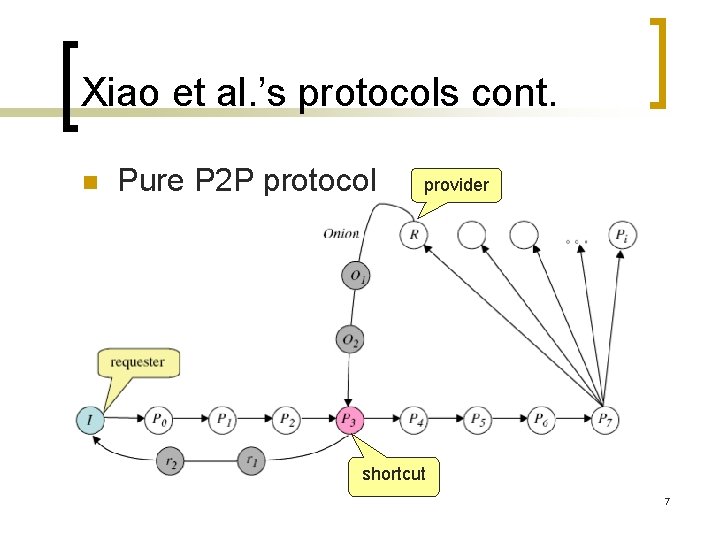
Xiao et al. ’s protocols cont. n Pure P 2 P protocol provider shortcut 7

Xiao et al. ’s protocols cont. n Disadvantage ¡ ¡ Scalability TTP know the details of providers and requesters. 8

Primitive roots {1, 3, 7, 9} 2 is a primitive root 9

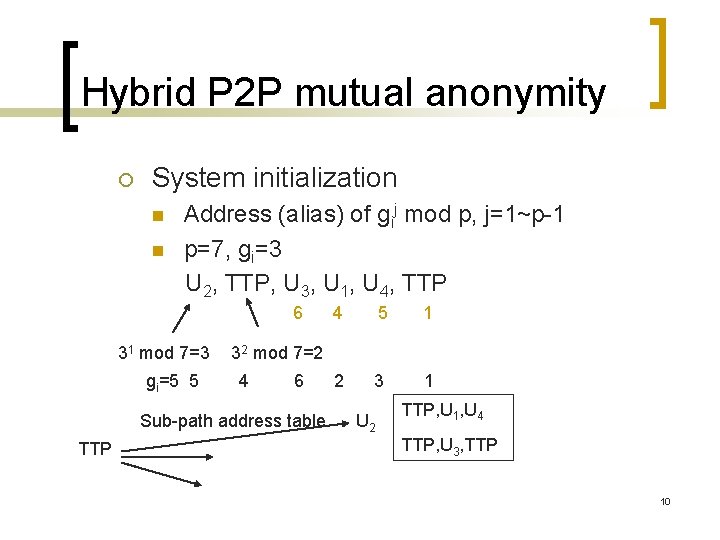
Hybrid P 2 P mutual anonymity ¡ System initialization n n Address (alias) of gij mod p, j=1~p-1 p=7, gi=3 U 2, TTP, U 3, U 1, U 4, TTP 6 31 mod 7=3 gi=5 5 5 1 2 3 1 32 mod 7=2 4 6 Sub-path address table TTP 4 U 2 TTP, U 1, U 4 TTP, U 3, TTP 10

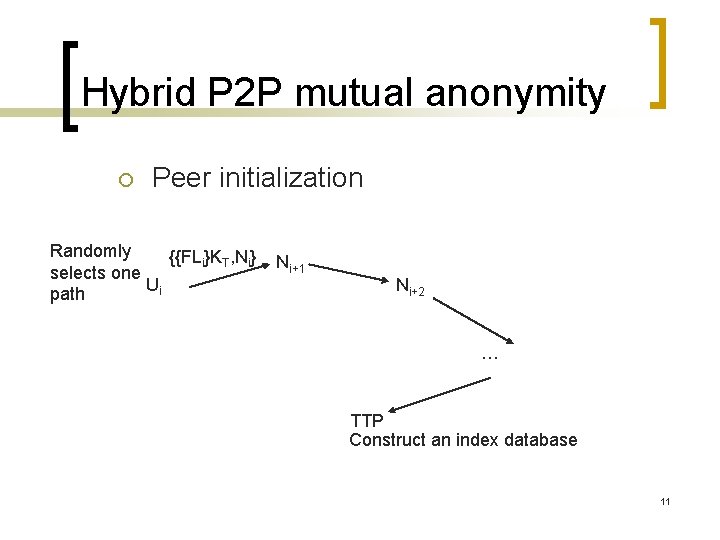
Hybrid P 2 P mutual anonymity ¡ Peer initialization Randomly {{FLi}KT, Ni} selects one Ui path Ni+1 Ni+2 … TTP Construct an index database 11

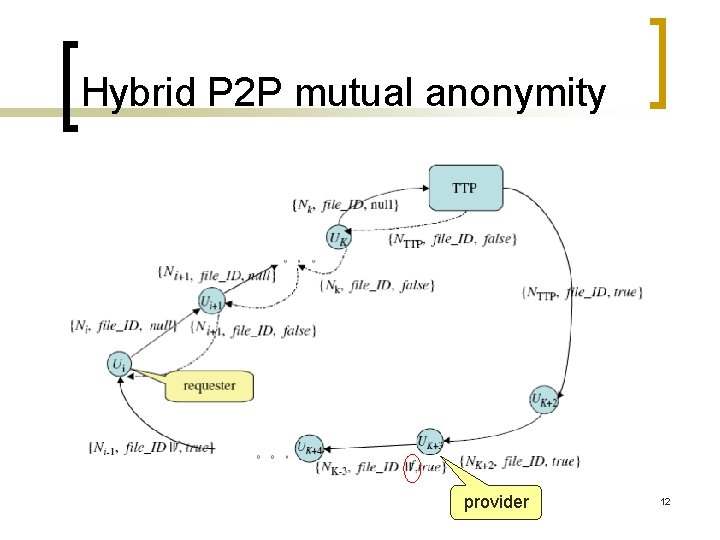
Hybrid P 2 P mutual anonymity provider 12

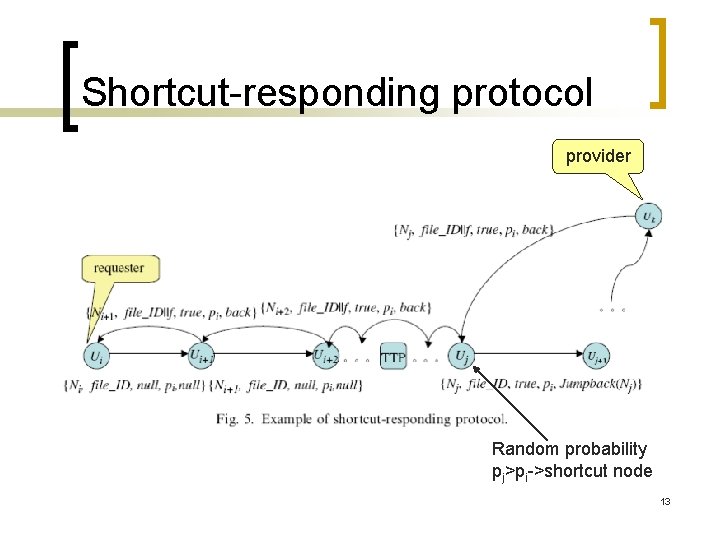
Shortcut-responding protocol provider Random probability pj>pi->shortcut node 13

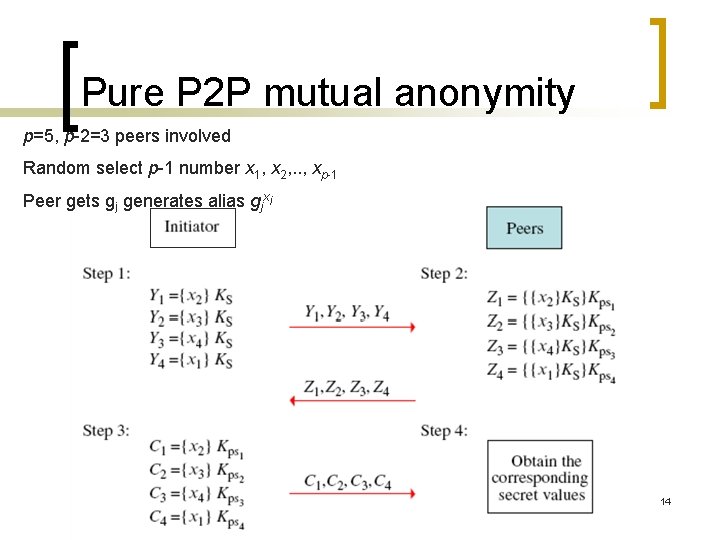
Pure P 2 P mutual anonymity p=5, p-2=3 peers involved Random select p-1 number x 1, x 2, . . , xp-1 Peer gets gj generates alias gjxi 14

Anonymity analysis TTP n n TTP Total n peers Between two consecutive aliases of TTP ¡ ¡ n . . . sn: smallest numbers of peers ln: largest number of peers TTP: guess requester -> 1/sn guess provider -> 1/n-ln 15

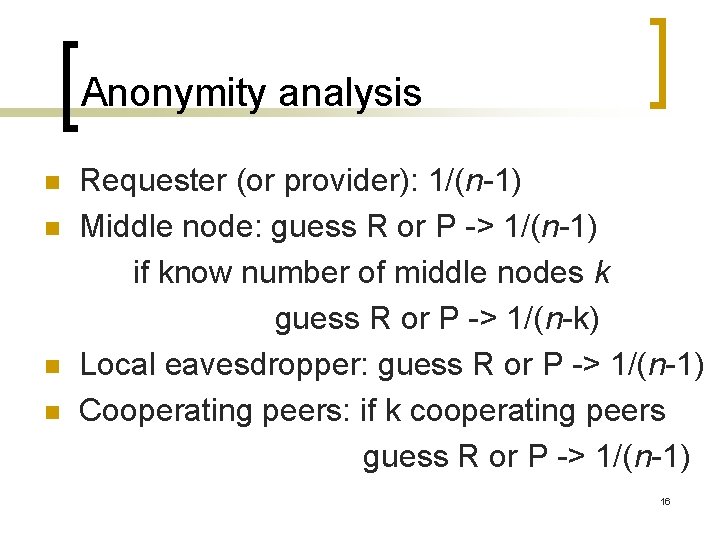
Anonymity analysis n n Requester (or provider): 1/(n-1) Middle node: guess R or P -> 1/(n-1) if know number of middle nodes k guess R or P -> 1/(n-k) Local eavesdropper: guess R or P -> 1/(n-1) Cooperating peers: if k cooperating peers guess R or P -> 1/(n-1) 16

Conclusions n n n The covert paths can be dynamically generated. It is guaranteed that all the peers and the TTP can pass any of the covert paths. Different primitive roots generate different covert paths, which raises the level of flexibility and anonymity of the protocol. 17

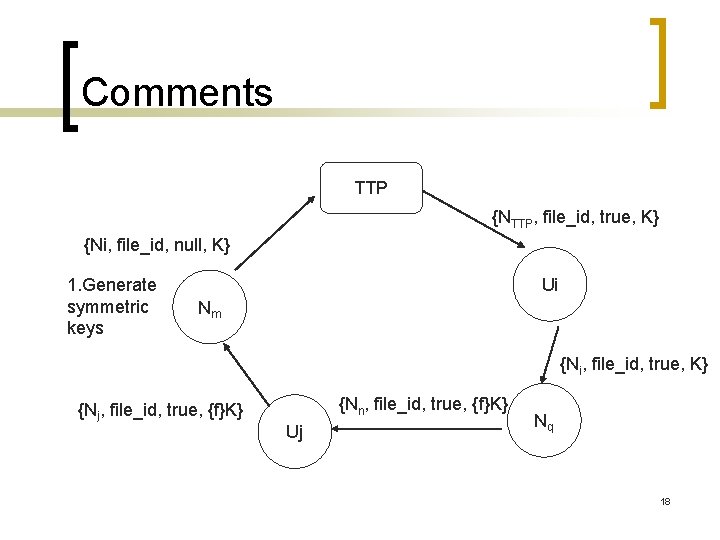
Comments TTP {NTTP, file_id, true, K} {Ni, file_id, null, K} 1. Generate symmetric keys Ui Nm {Ni, file_id, true, K} {Nj, file_id, true, {f}K} {Nn, file_id, true, {f}K} Uj Nq 18

Comments n Pure P 2 P ¡ Initiator generates peers’ aliases and transmits them to peers. 19