Shellcode CONTENTS INDEX 1 2 Shellcode 3 Shellcode






![02│ 필요한 부분만 어셈블리어 재작성(2) [willy@Null@Root]$ cat test 23. s. LC 0: . string 02│ 필요한 부분만 어셈블리어 재작성(2) [willy@Null@Root]$ cat test 23. s. LC 0: . string](https://slidetodoc.com/presentation_image_h2/4df7ece7ce5d99076f7c2f6d71f26b41/image-11.jpg)

![03│ NULL 이 포함된 바이너리코드 바꿔주기(3) [willy@Null@Root]$ cat test 42. c char print_code[] = 03│ NULL 이 포함된 바이너리코드 바꿔주기(3) [willy@Null@Root]$ cat test 42. c char print_code[] =](https://slidetodoc.com/presentation_image_h2/4df7ece7ce5d99076f7c2f6d71f26b41/image-16.jpg)


- Slides: 19

Shellcode 작성 김영성

CONTENTS INDEX 1 필요지식 2 Shellcode 작성방법 3 Shellcode 작성


01│ Stack, Register, Stack. Frame contants 01




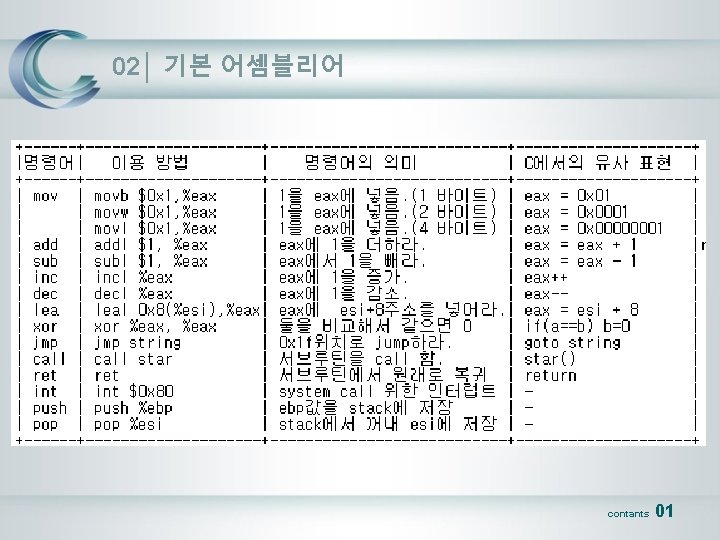
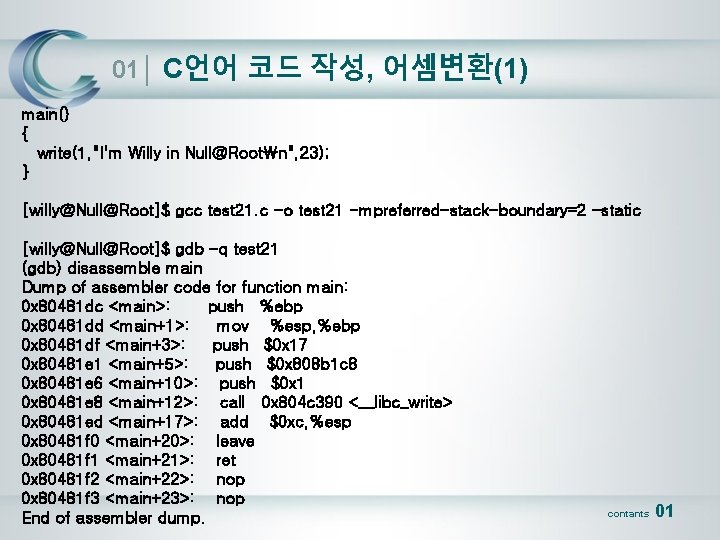
01│ C언어 코드 작성, 어셈변환(1) main() { write(1, "I'm Willy in Null@Rootn", 23); } [willy@Null@Root]$ gcc test 21. c -o test 21 -mpreferred-stack-boundary=2 -static [willy@Null@Root]$ gdb -q test 21 (gdb) disassemble main Dump of assembler code for function main: 0 x 80481 dc <main>: push %ebp 0 x 80481 dd <main+1>: mov %esp, %ebp 0 x 80481 df <main+3>: push $0 x 17 0 x 80481 e 1 <main+5>: push $0 x 808 b 1 c 8 0 x 80481 e 6 <main+10>: push $0 x 1 0 x 80481 e 8 <main+12>: call 0 x 804 c 390 <__libc_write> 0 x 80481 ed <main+17>: add $0 xc, %esp 0 x 80481 f 0 <main+20>: leave 0 x 80481 f 1 <main+21>: ret 0 x 80481 f 2 <main+22>: nop 0 x 80481 f 3 <main+23>: nop End of assembler dump. contants 01

01│ C언어 코드 작성, 어셈변환(2) (gdb) disassemble __libc_write Dump of assembler code for function 0 x 804 c 390 <__libc_write>: push 0 x 804 c 391 <__libc_write+1>: mov 0 x 804 c 395 <__libc_write+5>: mov 0 x 804 c 399 <__libc_write+9>: mov 0 x 804 c 39 d <__libc_write+13>: mov 0 x 804 c 3 a 2 <__libc_write+18>: int 0 x 804 c 3 a 4 <__libc_write+20>: pop 0 x 804 c 3 a 5 <__libc_write+21>: cmp 0 x 804 c 3 aa <__libc_write+26>: jae 0 x 804 c 3 b 0 <__libc_write+32>: ret End of assembler dump. __libc_write: %ebx 0 x 10(%esp, 1), %edx 0 xc(%esp, 1), %ecx 0 x 8(%esp, 1), %ebx $0 x 4, %eax $0 x 80 %ebx $0 xfffff 001, %eax 0 x 804 cab 0 <__syscall_error> contants 01

![02 필요한 부분만 어셈블리어 재작성2 willyNullRoot cat test 23 s LC 0 string 02│ 필요한 부분만 어셈블리어 재작성(2) [willy@Null@Root]$ cat test 23. s. LC 0: . string](https://slidetodoc.com/presentation_image_h2/4df7ece7ce5d99076f7c2f6d71f26b41/image-11.jpg)
02│ 필요한 부분만 어셈블리어 재작성(2) [willy@Null@Root]$ cat test 23. s. LC 0: . string "I'm Willy in Null@Rootn". globl main: movl $0 x 04, %eax movl $0 x 01, %ebx movl $. LC 0, %ecx movl $0 x 17, %edx int $0 x 80 <--- write()를 위한 인터럽트 movl $0 x 01, %eax movl $0 x 00, %ebx int $0 x 80 <--- exit(0)을 위한 인터럽트 ret contants 01

02│ 필요한 부분만 어셈블리어 재작성(3). globl main: jmp strings start: popl %esi movl $0 x 04, %eax movl $0 x 01, %ebx movl %esi, %ecx movl $0 x 17, %edx int $0 x 80 movl $0 x 01, %eax movl $0 x 00, %ebx int $0 x 80 strings: call start. string "I'm Willy in Null@Rootn" contants 01

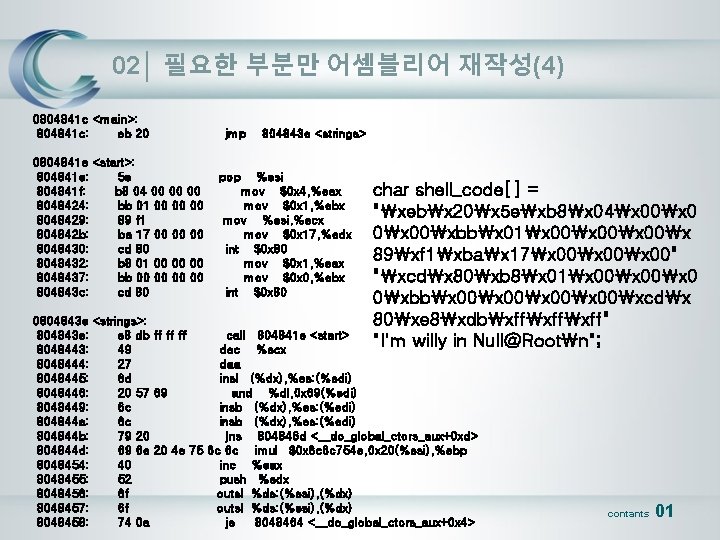
02│ 필요한 부분만 어셈블리어 재작성(4) 0804841 c <main>: 804841 c: eb 20 0804841 e <start>: 804841 e: 5 e 804841 f: b 8 04 00 00 00 8048424: bb 01 00 00 00 8048429: 89 f 1 804842 b: ba 17 00 00 00 8048430: cd 80 8048432: b 8 01 00 00 00 8048437: bb 00 00 804843 c: cd 80 jmp pop 804843 e <strings> %esi mov $0 x 4, %eax mov $0 x 1, %ebx mov %esi, %ecx mov $0 x 17, %edx int $0 x 80 mov $0 x 1, %eax mov $0 x 0, %ebx int $0 x 80 char shell_code[] = "xebx 20x 5 exb 8x 04x 00x 00xbbx 01x 00x 89xf 1xbax 17x 00x 00" "xcdx 80xb 8x 01x 00x 0 0xbbx 00xcdx 80xe 8xdbxffxff" "I'm willy in Null@Rootn"; 0804843 e <strings>: 804843 e: e 8 db ff ff ff call 804841 e <start> 8048443: 49 dec %ecx 8048444: 27 daa 8048445: 6 d insl (%dx), %es: (%edi) 8048446: 20 57 69 and %dl, 0 x 69(%edi) 8048449: 6 c insb (%dx), %es: (%edi) 804844 a: 6 c insb (%dx), %es: (%edi) 804844 b: 79 20 jns 804846 d <__do_global_ctors_aux+0 xd> 804844 d: 69 6 e 20 4 e 75 6 c 6 c imul $0 x 6 c 6 c 754 e, 0 x 20(%esi), %ebp 8048454: 40 inc %eax 8048455: 52 push %edx 8048456: 6 f outsl %ds: (%esi), (%dx) 8048457: 6 f outsl %ds: (%esi), (%dx) 8048458: 74 0 a je 8048464 <__do_global_ctors_aux+0 x 4> contants 01


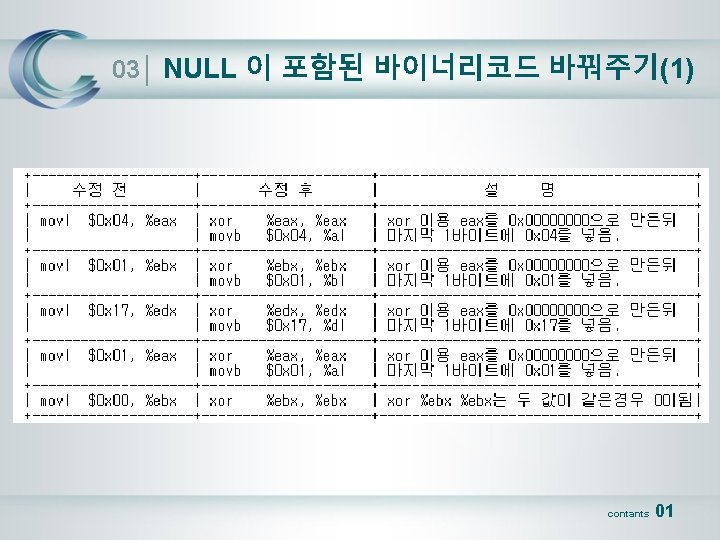
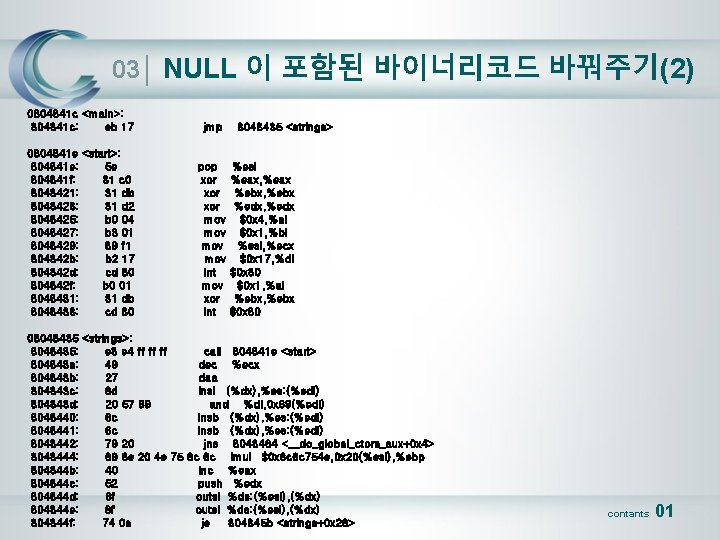
03│ NULL 이 포함된 바이너리코드 바꿔주기(2) 0804841 c <main>: 804841 c: eb 17 jmp 0804841 e <start>: 804841 e: 5 e 804841 f: 31 c 0 8048421: 31 db 8048423: 31 d 2 8048425: b 0 04 8048427: b 3 01 8048429: 89 f 1 804842 b: b 2 17 804842 d: cd 80 804842 f: b 0 01 8048431: 31 db 8048433: cd 80 pop xor xor mov mov int mov xor int 8048435 <strings> %esi %eax, %eax %ebx, %ebx %edx, %edx $0 x 4, %al $0 x 1, %bl %esi, %ecx $0 x 17, %dl $0 x 80 $0 x 1, %al %ebx, %ebx $0 x 80 08048435 <strings>: 8048435: e 8 e 4 ff ff ff call 804841 e <start> 804843 a: 49 dec %ecx 804843 b: 27 daa 804843 c: 6 d insl (%dx), %es: (%edi) 804843 d: 20 57 69 and %dl, 0 x 69(%edi) 8048440: 6 c insb (%dx), %es: (%edi) 8048441: 6 c insb (%dx), %es: (%edi) 8048442: 79 20 jns 8048464 <__do_global_ctors_aux+0 x 4> 8048444: 69 6 e 20 4 e 75 6 c 6 c imul $0 x 6 c 6 c 754 e, 0 x 20(%esi), %ebp 804844 b: 40 inc %eax 804844 c: 52 push %edx 804844 d: 6 f outsl %ds: (%esi), (%dx) 804844 e: 6 f outsl %ds: (%esi), (%dx) 804844 f: 74 0 a je 804845 b <strings+0 x 26> contants 01
![03 NULL 이 포함된 바이너리코드 바꿔주기3 willyNullRoot cat test 42 c char printcode 03│ NULL 이 포함된 바이너리코드 바꿔주기(3) [willy@Null@Root]$ cat test 42. c char print_code[] =](https://slidetodoc.com/presentation_image_h2/4df7ece7ce5d99076f7c2f6d71f26b41/image-16.jpg)
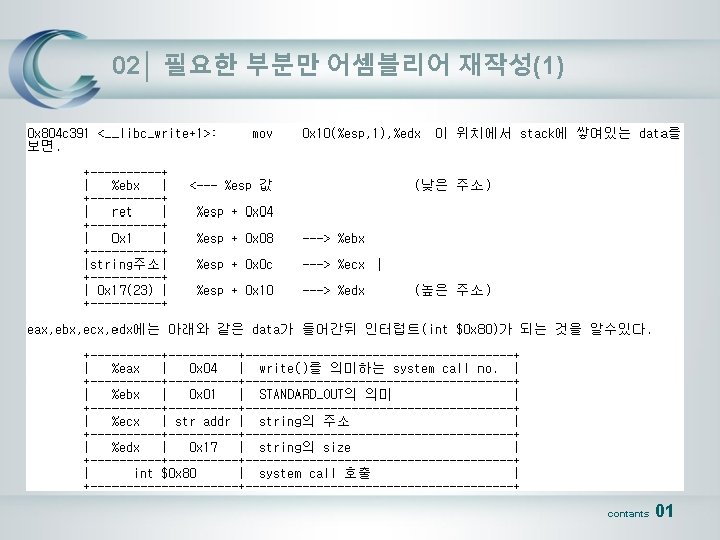
03│ NULL 이 포함된 바이너리코드 바꿔주기(3) [willy@Null@Root]$ cat test 42. c char print_code[] = "xebx 17x 5 ex 31xc 0x 31xdbx 31xd 2xb 0x 04xb 3x 01x 89xf 1" "xb 2x 17xcdx 80xb 0x 01x 31xdbxcdx 80xe 8xe 4xffxff" "I'm willy in Null@Rootn"; main() { int *ret; ret = (int *)&ret + 2; (*ret) = (int)print_code; } [willy@Null@Root]$ gcc test 42. c -o test 42 [willy@Null@Root]$. /test 42 I'm willy in Null@Root contants 01

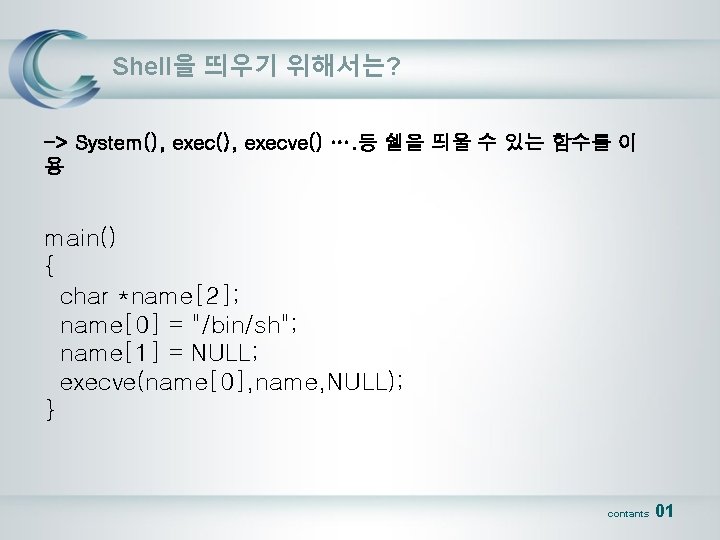
Shell을 띄우기 위해서는? -> System(), execve() …. 등 쉘을 띄울 수 있는 함수를 이 용 main() { char *name[2]; name[0] = "/bin/sh"; name[1] = NULL; execve(name[0], name, NULL); } contants 01

참고자료 *** How to make shellcode in linux for beginners *** by Willy in Null@Root contants 01

THANK YOU