Shell Protocols Elly Bornstein Hiral Patel Pranav Patel
Shell Protocols Elly Bornstein Hiral Patel Pranav Patel Priyank Desai Swar Shah
Agenda l l l l l Introduction R* Utilities Secure Shell Protocol Architecture of SSH How SSH works Features and Advantages Limitations Security Concerns Tools Conclusion

Introduction l What is Shell? l What are Shell Protocols? l R* Utilities
R* Utilities l Rlogin - allows users to log in remotely l Rcp - provides remote file transfer. l Rsh - executes a remote command through the rshd daemon l Rexec - executes a remote command through the rexecd daemon l R* Utilities Security Concerns
Secure Shell Protocol (SSH) What is SSH? • Why SSH? • Different versions of SSH • • • SSH-1 SSH-2
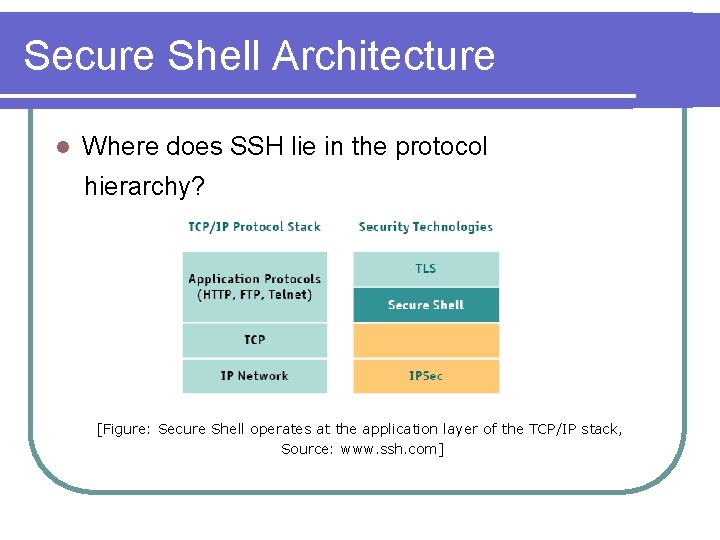
Secure Shell Architecture l Where does SSH lie in the protocol hierarchy? [Figure: Secure Shell operates at the application layer of the TCP/IP stack, Source: www. ssh. com]
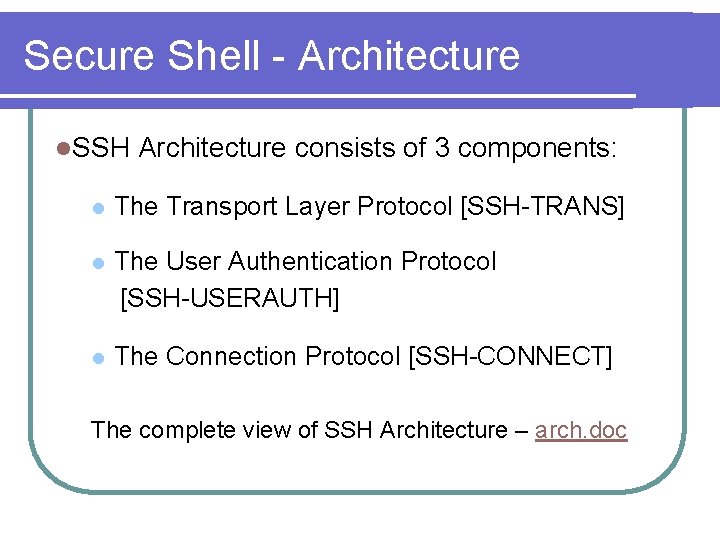
Secure Shell - Architecture l. SSH Architecture consists of 3 components: l The Transport Layer Protocol [SSH-TRANS] l The User Authentication Protocol [SSH-USERAUTH] l The Connection Protocol [SSH-CONNECT] The complete view of SSH Architecture – arch. doc
SSH Layers l SSH-TRANS l Server Authentication Each Server must have a Host Key l Client must have prior knowledge of host keys – local database, trusted certification authority l Danger – Man in the middle attack l l l Confidentiality Integrity Key-Exchange Compression [optional]
![SSH Layers – [contd. ] l SSH-USERAUTH l Authenticates Client-Side User Authentication Methods: 1. SSH Layers – [contd. ] l SSH-USERAUTH l Authenticates Client-Side User Authentication Methods: 1.](http://slidetodoc.com/presentation_image_h2/9e5c85a155c9a2ee36da21a2ee7411b3/image-9.jpg)
SSH Layers – [contd. ] l SSH-USERAUTH l Authenticates Client-Side User Authentication Methods: 1. Password-Based Authentication 2. Public-Key Based Authentication 3. Host-Based Authentication 4. GSSAPI Authentication Methods
![SSH Layers – [contd. ] l SSH-CONN Multiplexes Encrypted Channel into several logical channels SSH Layers – [contd. ] l SSH-CONN Multiplexes Encrypted Channel into several logical channels](http://slidetodoc.com/presentation_image_h2/9e5c85a155c9a2ee36da21a2ee7411b3/image-10.jpg)
SSH Layers – [contd. ] l SSH-CONN Multiplexes Encrypted Channel into several logical channels l Provides services such as: l q q Multiple interactive and non-interactive sessions Managing X, Port and Agent forwarding Terminal handling Remote program execution

How SSH works? l Host Identification l Encryption l User Authentication l Access to desired services Relate back to arch. doc
Features and Advantages l l l SSH and SFTP for secure file transfer SSH and SCP for alternative to RCP Port forwarding and Tunneling Support terminal protocols for remote administration Secure proxy connection for Internet browsing Authentication methods: Kerberos, Secure. ID, RSA, etc.
Limitations l Port ranges can’t be forwarded l Poor performance on older computers l Graphical applications can be started, but cannot be seen l Child processes are not killed when the user logs out
Security Concerns l Man-in-the-middle l Denial attack of Service l Message replay attack l Data integrity
Tools l Multi-platform Pu. TTy l Conch l l Windows Secure. CRT l Win. SCP l l Unix-like OS LSH l Open. SSH l
Conclusion l Provides secure data transfer across the network l Provides the space for extensibility and options for using different algorithms l Most of the limitations and probable threats can be avoided by using proper algorithms and policies
Thank You
- Slides: 17