Shared Responsibility Model in Cloud Computing A data

Shared Responsibility Model in Cloud Computing A data protection and security perspective 5 March 2021 Annabel Lee, Head of Data Policy (APJ) lennbe@amazon. com © 2021, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Confidential and Trademark.

Introduction to Personal Data Protection in the Cloud © 2021, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Confidential and Trademark.
What is Cloud Computing? “Cloud computing” is the on-demand delivery of IT resources via the internet with pay-as-you-go pricing. © 2021, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Confidential and Trademark.
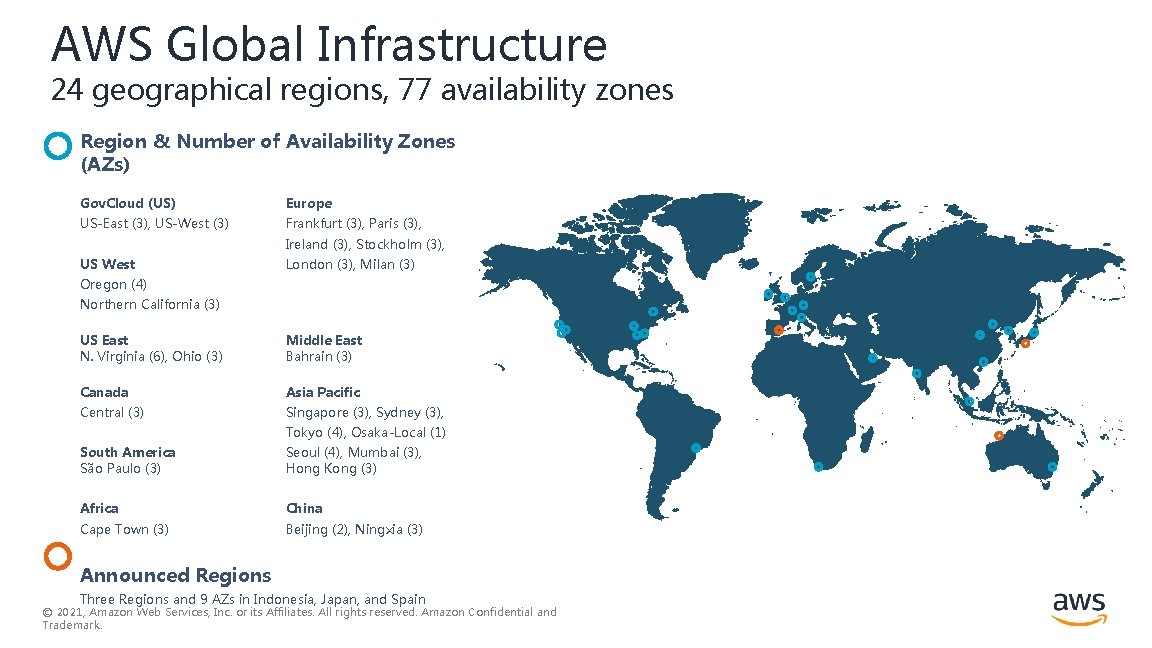
AWS Global Infrastructure 24 geographical regions, 77 availability zones Region & Number of Availability Zones (AZs) Gov. Cloud (US) Europe US-East (3), US-West (3) Frankfurt (3), Paris (3), Ireland (3), Stockholm (3), US West London (3), Milan (3) Oregon (4) Northern California (3) US East N. Virginia (6), Ohio (3) Middle East Bahrain (3) Canada Asia Pacific Central (3) Singapore (3), Sydney (3), Tokyo (4), Osaka-Local (1) South America São Paulo (3) Seoul (4), Mumbai (3), Hong Kong (3) Africa China Cape Town (3) Beijing (2), Ningxia (3) Announced Regions Three Regions and 9 AZs in Indonesia, Japan, and Spain © 2021, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Confidential and Trademark.
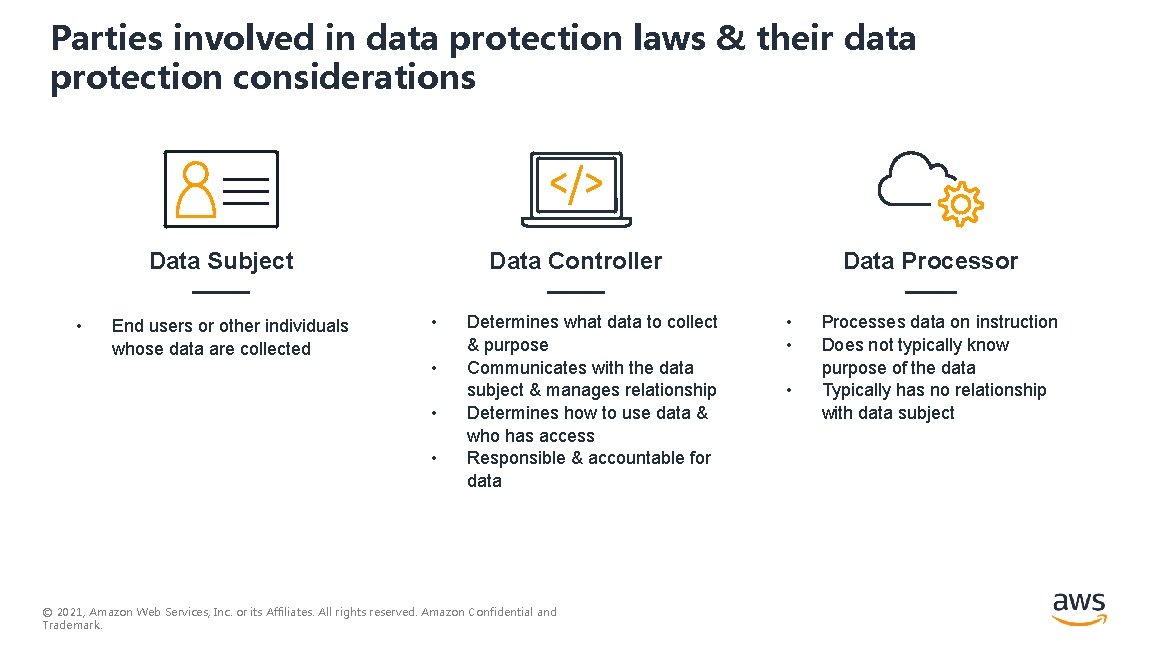
Parties involved in data protection laws & their data protection considerations Data Subject • End users or other individuals whose data are collected Data Controller • • Determines what data to collect & purpose Communicates with the data subject & manages relationship Determines how to use data & who has access Responsible & accountable for data © 2021, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Confidential and Trademark. Data Processor • • • Processes data on instruction Does not typically know purpose of the data Typically has no relationship with data subject
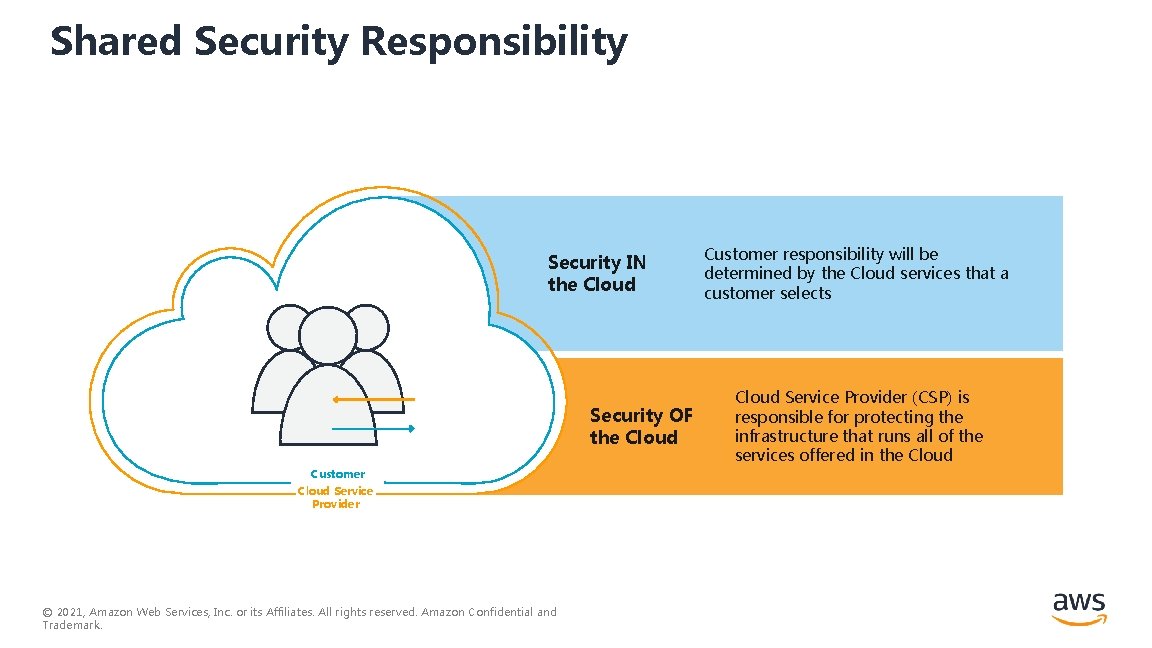
Shared Security Responsibility Security IN the Cloud Security OF the Cloud Customer Cloud Service Provider © 2021, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Confidential and Trademark. Customer responsibility will be determined by the Cloud services that a customer selects Cloud Service Provider (CSP) is responsible for protecting the infrastructure that runs all of the services offered in the Cloud
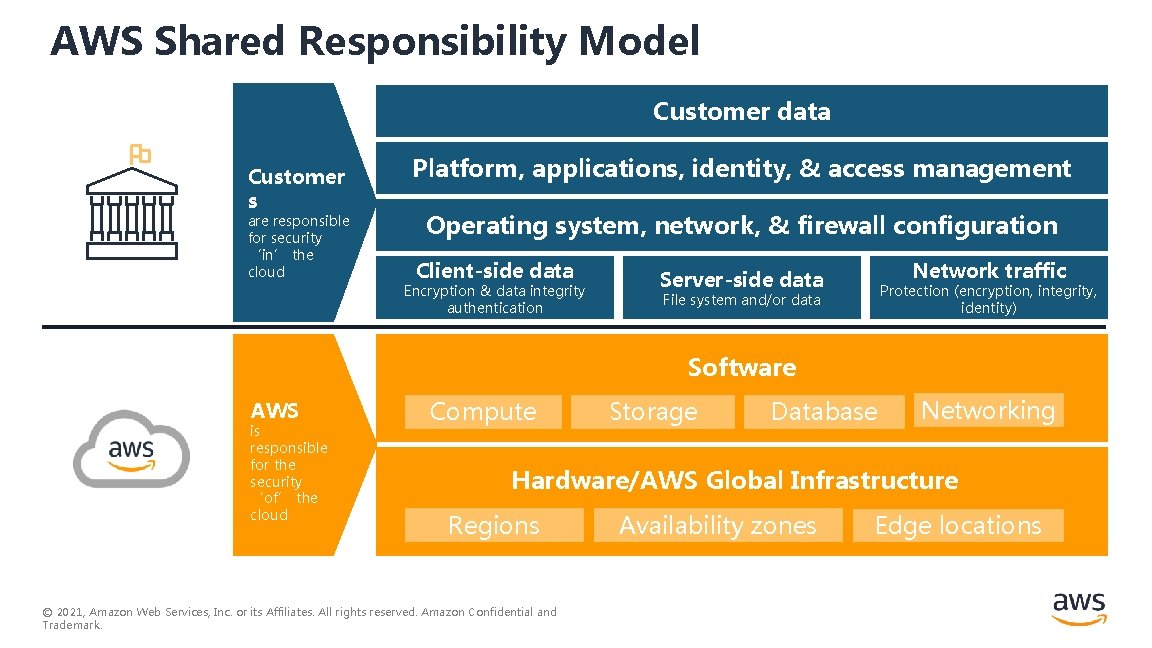
AWS Shared Responsibility Model Customer data Customer s are responsible for security ‘in’ the cloud Platform, applications, identity, & access management Operating system, network, & firewall configuration Client-side data Encryption & data integrity authentication Network traffic Server-side data Protection (encryption, integrity, identity) File system and/or data Software AWS is responsible for the security ‘of’ the cloud Compute Storage Database Networking Hardware/AWS Global Infrastructure Regions © 2021, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Confidential and Trademark. Availability zones Edge locations
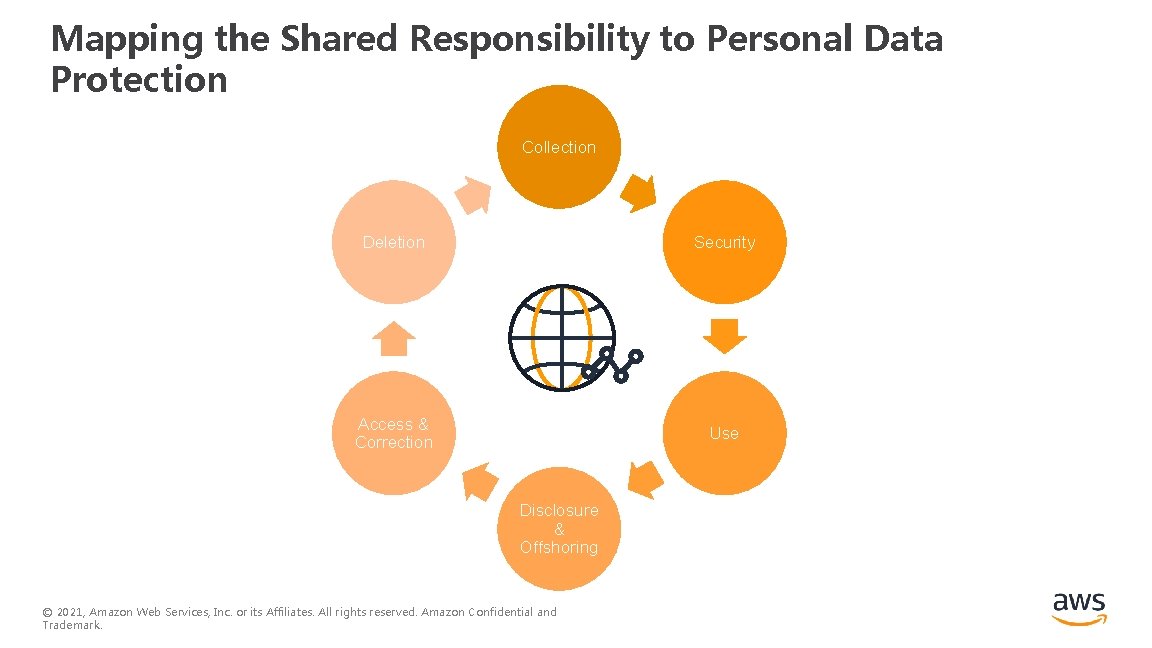
Mapping the Shared Responsibility to Personal Data Protection Collection Deletion Security Access & Correction Use Disclosure & Offshoring © 2021, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Confidential and Trademark.
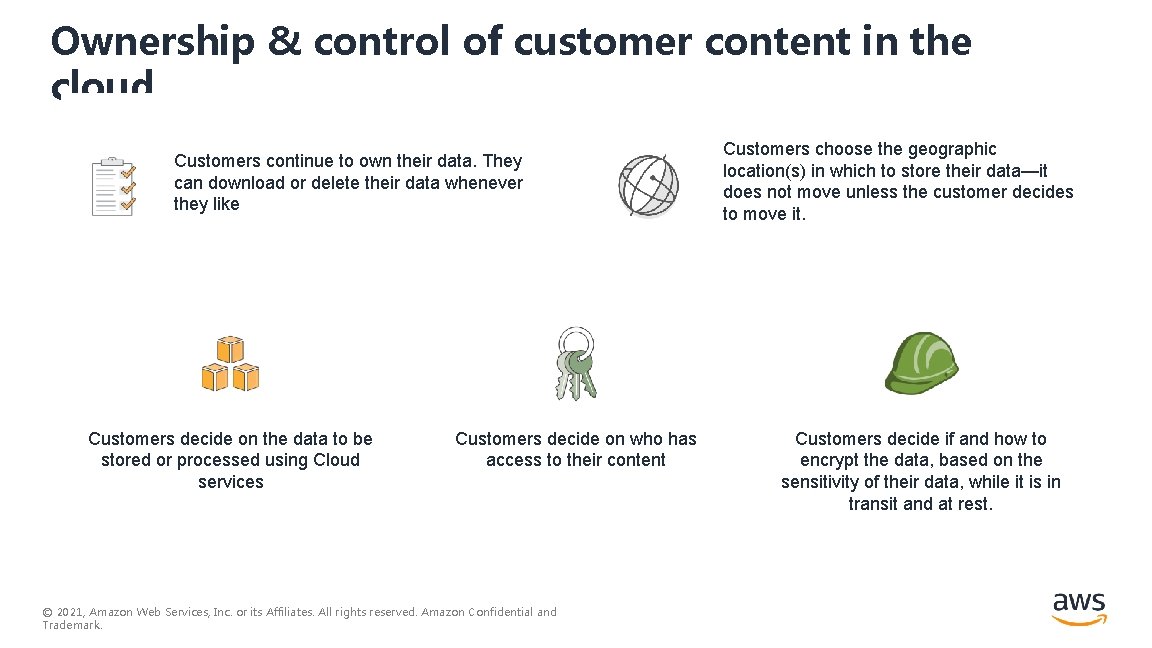
Ownership & control of customer content in the cloud Customers continue to own their data. They can download or delete their data whenever they like Customers decide on the data to be stored or processed using Cloud services Customers decide on who has access to their content © 2021, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Confidential and Trademark. Customers choose the geographic location(s) in which to store their data—it does not move unless the customer decides to move it. Customers decide if and how to encrypt the data, based on the sensitivity of their data, while it is in transit and at rest.

How cloud services can help with security © 2021, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Confidential and Trademark.
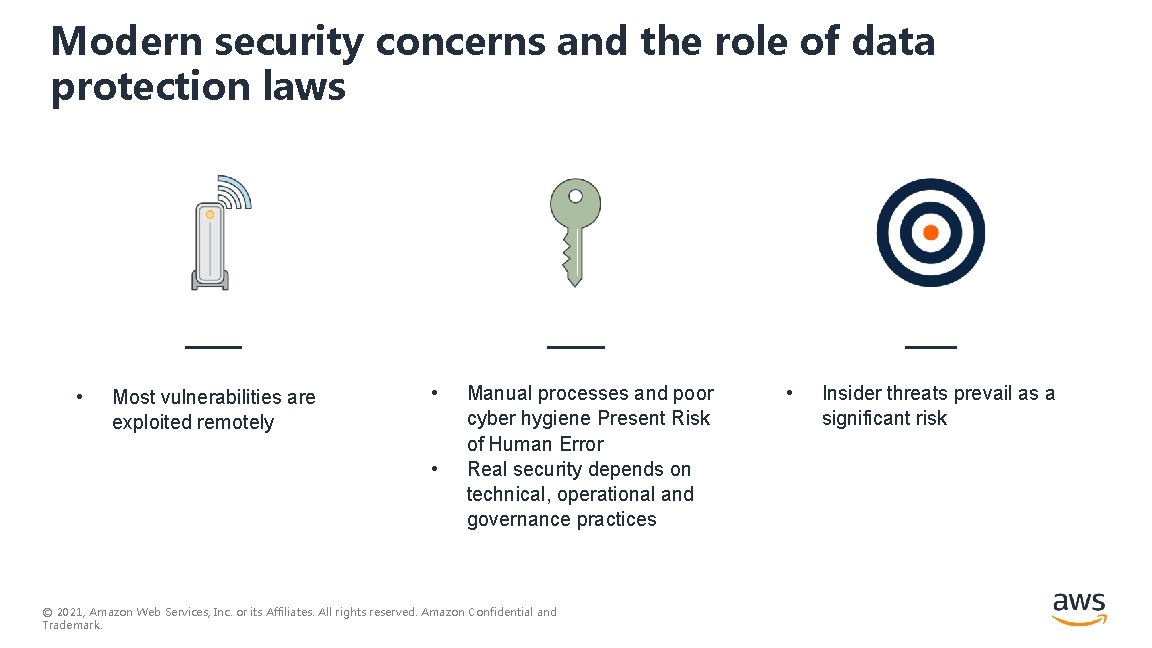
Modern security concerns and the role of data protection laws • Most vulnerabilities are exploited remotely • • Manual processes and poor cyber hygiene Present Risk of Human Error Real security depends on technical, operational and governance practices © 2021, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Confidential and Trademark. • Insider threats prevail as a significant risk
Tools for mitigating unauthorized access Encryption Tokenization Data Decomposition Cyber Deception Defense Appropriately encrypting data can make the data unreadable Defining a sequence of data to represent an otherwise sensitive piece of information Reduces data sets into unrecognizable elements that have no significance on their own Deception solutions use highly sophisticated traps and decoys against attackers © 2021, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Confidential and Trademark.

What does this mean collectively? • Companies need to learn how to create data governance frameworks to ensure that appropriate techniques are applied to the whole data lifecycle. • Companies can outsource some of this – relying on CSPs like AWS who have attained certification (including ISO 27001, 270018 and SOC 2 Privacy Certification) – this helps companies know that the security of the CSP’s side of the shared responsibility is covered. • Governments can help with SME capacity building. Examples include: • Nymity Privacy Management Framework (https: //iapp. org/resources/nymityworkbook-tool/) • Singapore PDPC Guide to Developing a Data Protection Management Programme (https: //www. pdpc. gov. sg/-/media/Files/PDPC/PDF-Files/Other. Guides/DPMP/Guide-to-Developing-a-Data-Protection-Management. Programme-(18 -Nov-2020). pdf? la=en) © 2021, Amazon Web Services, Inc. or its Affiliates. All rights reserved. Amazon Confidential and Trademark.
- Slides: 13