SHA2 introduction David Groep Nikhef and EUGrid PMA


- Slides: 5

SHA-2 introduction David Groep Nikhef and EUGrid. PMA co-supported by the Dutch National e-Infrastructure coordinated by SURFsara, and EGI Core Services and the SHA-1 depreciation time line and status

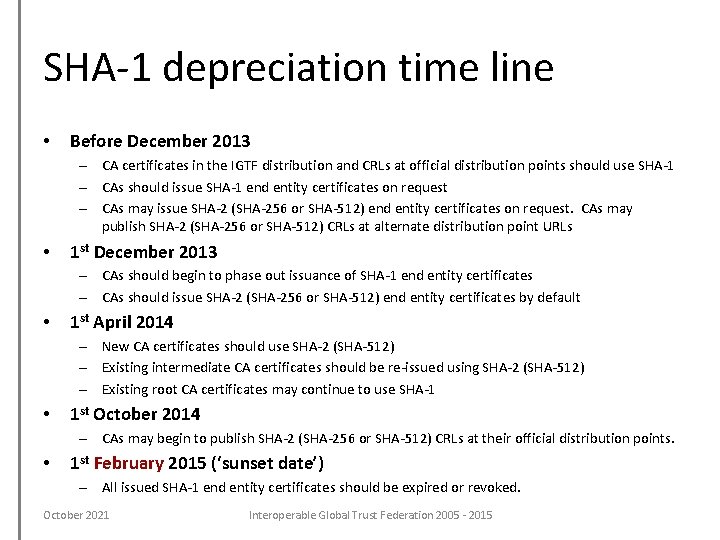
SHA-1 depreciation time line • Before December 2013 – CA certificates in the IGTF distribution and CRLs at official distribution points should use SHA-1 – CAs should issue SHA-1 end entity certificates on request – CAs may issue SHA-2 (SHA-256 or SHA-512) end entity certificates on request. CAs may publish SHA-2 (SHA-256 or SHA-512) CRLs at alternate distribution point URLs • 1 st December 2013 – CAs should begin to phase out issuance of SHA-1 end entity certificates – CAs should issue SHA-2 (SHA-256 or SHA-512) end entity certificates by default • 1 st April 2014 – New CA certificates should use SHA-2 (SHA-512) – Existing intermediate CA certificates should be re-issued using SHA-2 (SHA-512) – Existing root CA certificates may continue to use SHA-1 • 1 st October 2014 – CAs may begin to publish SHA-2 (SHA-256 or SHA-512) CRLs at their official distribution points. • 1 st February 2015 (‘sunset date’) – All issued SHA-1 end entity certificates should be expired or revoked. October 2021 Interoperable Global Trust Federation 2005 - 2015

Current state On the CA side • Almost all CAs issue SHA-2 family EECs • There are some SHA-2 roots • Not many intermediates have been re-written yet On the RP and client side • All known software now processes SHA-2 correctly We might use the Communication Challenge to get up-todate status reports (to be discussed) October 2021 Interoperable Global Trust Federation 2005 - 2015

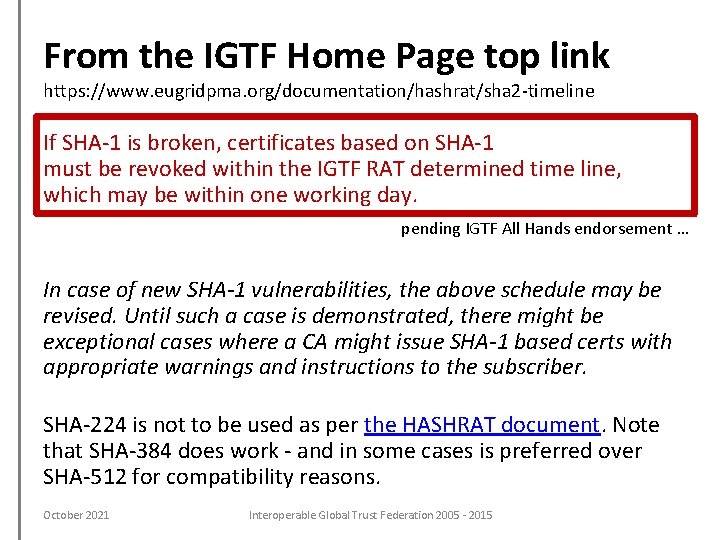
From the IGTF Home Page top link https: //www. eugridpma. org/documentation/hashrat/sha 2 -timeline If SHA-1 is broken, certificates based on SHA-1 must be revoked within the IGTF RAT determined time line, which may be within one working day. pending IGTF All Hands endorsement … In case of new SHA-1 vulnerabilities, the above schedule may be revised. Until such a case is demonstrated, there might be exceptional cases where a CA might issue SHA-1 based certs with appropriate warnings and instructions to the subscriber. SHA-224 is not to be used as per the HASHRAT document. Note that SHA-384 does work - and in some cases is preferred over SHA-512 for compatibility reasons. October 2021 Interoperable Global Trust Federation 2005 - 2015

Questions? BUILDING A GLOBAL TRUST FABRIC Interoperable Global Trust Federation 2005 - 2015